| File name: | bc8c794b9e5bcf4d359f2b4d8fa3e6ad_JaffaCakes118 |
| Full analysis: | https://app.any.run/tasks/022475f3-b898-4d62-88b6-6d25722e469b |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2025, 14:02:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | BC8C794B9E5BCF4D359F2B4D8FA3E6AD |
| SHA1: | F39DBC6C2223D22B92253A96A5F353E089CF6F26 |
| SHA256: | C247A2458292BBD0226F6CCAA12777C4FC81059EDB6C6E150333D52743E04742 |
| SSDEEP: | 49152:MiejPV/lT6vc4lQgREX1eE+KZxV822fc21vIJEp/kGabMwOjrOY8uY2FfnlukES2:LejPNFwlRO1erYD72R1vXp/223OY8IF2 |
MALICIOUS
Generic archive extractor
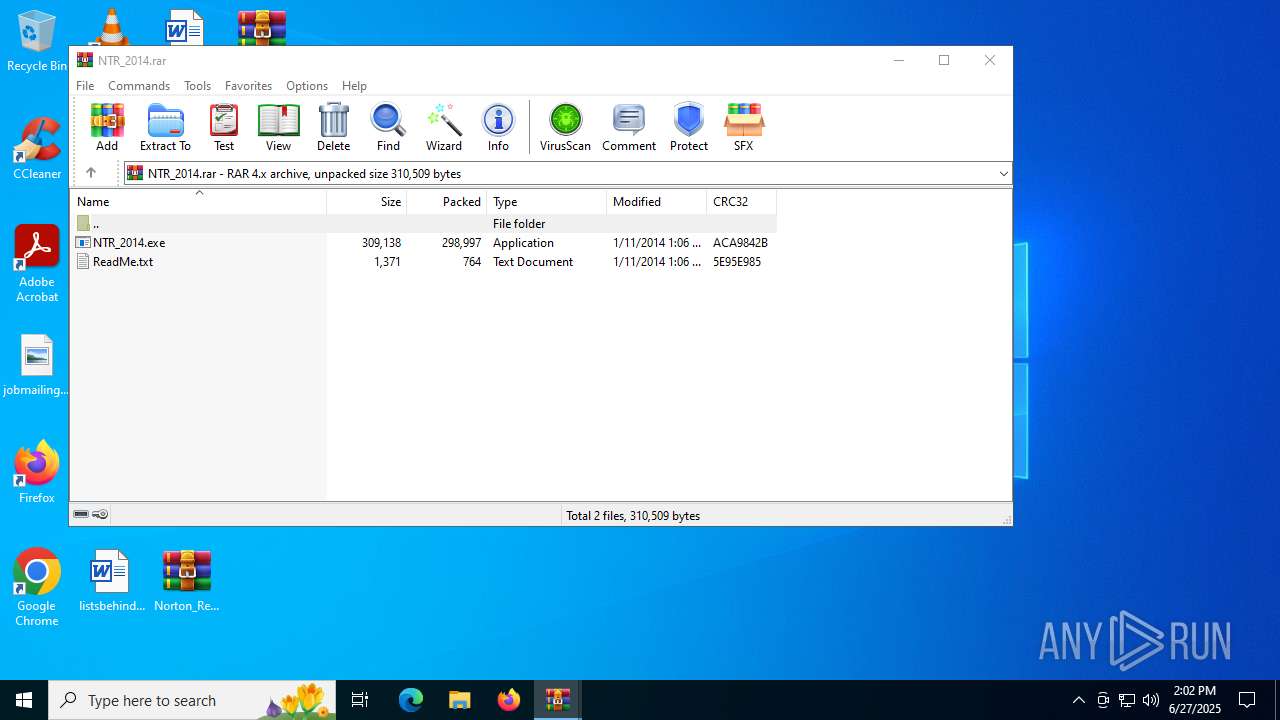
- WinRAR.exe (PID: 5456)
Executing a file with an untrusted certificate
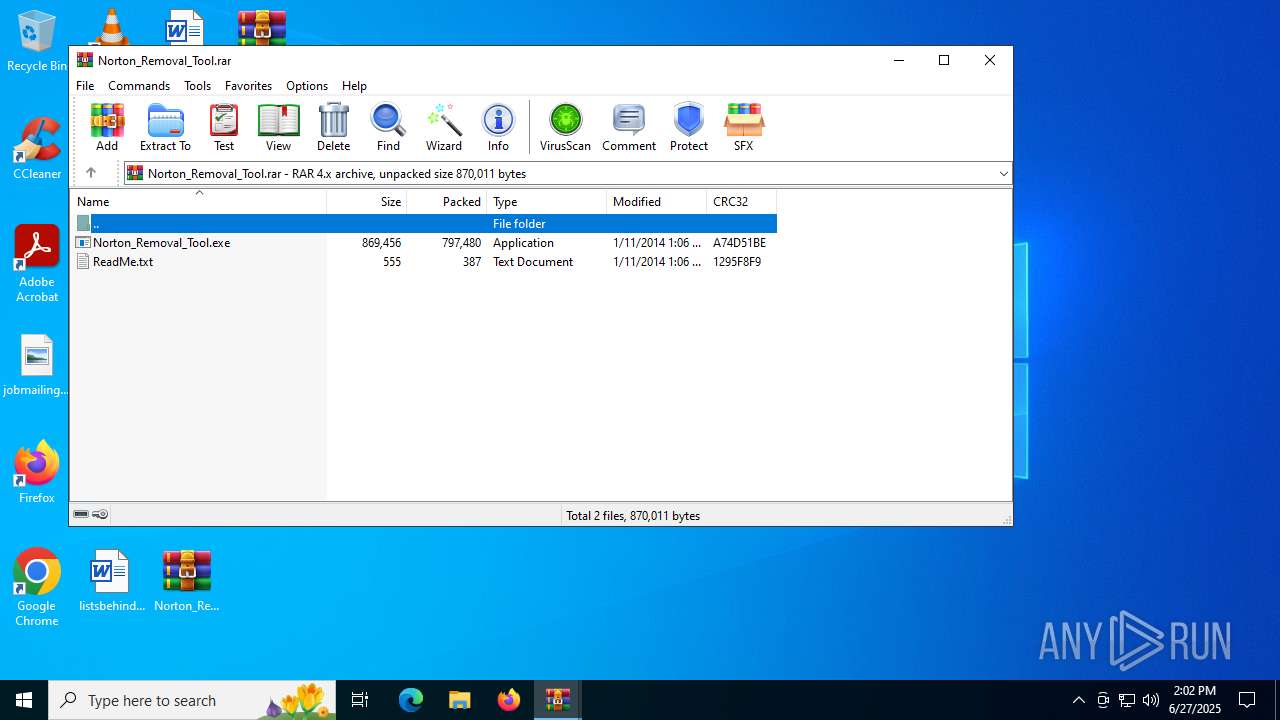
- Norton_Removal_Tool.exe (PID: 6380)
- Norton_Removal_Tool.exe (PID: 5560)
- SymNRT.exe (PID: 6388)
SUSPICIOUS
Executable content was dropped or overwritten
- Norton_Removal_Tool.exe (PID: 6380)
Reads security settings of Internet Explorer
- Norton_Removal_Tool.exe (PID: 6380)
- SymNRT.exe (PID: 6388)
- NTR_2014.exe (PID: 5116)
Adds/modifies Windows certificates
- SymNRT.exe (PID: 6388)
The process verifies whether the antivirus software is installed
- SymNRT.exe (PID: 6388)
Application launched itself
- NTR_2014.exe (PID: 5116)
INFO
Reads the computer name
- Norton_Removal_Tool.exe (PID: 6380)
- SymNRT.exe (PID: 6388)
- NTR_2014.exe (PID: 2132)
- NTR_2014.exe (PID: 5116)
Manual execution by a user
- Norton_Removal_Tool.exe (PID: 6380)
- WinRAR.exe (PID: 6420)
- Norton_Removal_Tool.exe (PID: 5560)
- WinRAR.exe (PID: 6900)
- notepad.exe (PID: 1936)
- NTR_2014.exe (PID: 5116)
- notepad.exe (PID: 2276)
The sample compiled with english language support
- Norton_Removal_Tool.exe (PID: 6380)
Process checks computer location settings
- Norton_Removal_Tool.exe (PID: 6380)
- NTR_2014.exe (PID: 5116)
Create files in a temporary directory
- Norton_Removal_Tool.exe (PID: 6380)
- SymNRT.exe (PID: 6388)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1936)
- notepad.exe (PID: 2276)
Checks supported languages
- Norton_Removal_Tool.exe (PID: 6380)
- SymNRT.exe (PID: 6388)
- NTR_2014.exe (PID: 5116)
- NTR_2014.exe (PID: 2132)
Reads the machine GUID from the registry
- SymNRT.exe (PID: 6388)
Reads the software policy settings
- SymNRT.exe (PID: 6388)
- slui.exe (PID: 4880)
Reads mouse settings
- NTR_2014.exe (PID: 5116)
- NTR_2014.exe (PID: 2132)
Checks proxy server information
- slui.exe (PID: 4880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 798050 |
| UncompressedSize: | 798001 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2014:10:13 13:07:30 |
| PackingMethod: | Stored |
| ArchivedFileName: | Norton_Removal_Tool.rar |
Total processes
147
Monitored processes
11
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1936 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\ReadMe.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | "C:\Users\admin\Desktop\NTR_2014.exe" | C:\Users\admin\Desktop\NTR_2014.exe | NTR_2014.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2276 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\ReadMe.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | "C:\Users\admin\Desktop\NTR_2014.exe" | C:\Users\admin\Desktop\NTR_2014.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5456 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\bc8c794b9e5bcf4d359f2b4d8fa3e6ad_JaffaCakes118.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5560 | "C:\Users\admin\Desktop\Norton_Removal_Tool.exe" | C:\Users\admin\Desktop\Norton_Removal_Tool.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6380 | "C:\Users\admin\Desktop\Norton_Removal_Tool.exe" | C:\Users\admin\Desktop\Norton_Removal_Tool.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6388 | "C:\Users\admin\AppData\Local\Temp\7zS6E3A.tmp\SymNRT.exe" | C:\Users\admin\AppData\Local\Temp\7zS6E3A.tmp\SymNRT.exe | Norton_Removal_Tool.exe | ||||||||||||
User: admin Company: Symantec Corporation Integrity Level: HIGH Description: Norton Removal Tool Version: 21.0.0.14 Modules
| |||||||||||||||
| 6420 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\NTR_2014.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
12 717
Read events
12 683
Write events
31
Delete events
3
Modification events
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\bc8c794b9e5bcf4d359f2b4d8fa3e6ad_JaffaCakes118.rar | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
2
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6380 | Norton_Removal_Tool.exe | C:\Users\admin\AppData\Local\Temp\7zS6E3A.tmp\SymNRT.exe | executable | |
MD5:F5027D2D7B5FA12A8D55C8BA40E3AE74 | SHA256:4964B7C7190020D48CA7E48478599C030296756A34D430B75F15F136AC002113 | |||
| 6388 | SymNRT.exe | C:\Users\admin\AppData\Local\Temp\all.cpr | ini | |
MD5:A0F8D392E9E7494BEEE4557D15CFECF9 | SHA256:30A007F76F6E2B27979CEA28A304988C3B432DFA2FCBE3ED504FCBF7375F022C | |||
| 6380 | Norton_Removal_Tool.exe | C:\Users\admin\AppData\Local\Temp\7zS6E3A.tmp\SymNRT.loc | executable | |
MD5:72D95AF5F7C52FFED388230E36C849B3 | SHA256:21BAC423AFBE740E88B83AD540DDFAD42FF79EC04086DAAF99F0C8E6BD83EEF4 | |||
| 6388 | SymNRT.exe | C:\Users\admin\AppData\Local\Temp\Sym71D4.tmp | compressed | |
MD5:3DDC1ECD4F02A565F486F84C71D1B117 | SHA256:904542C7F62E440FFA1B36021E2F34FAEE9D3C08E43E1C9CA2A0C55245F697B3 | |||
| 6380 | Norton_Removal_Tool.exe | C:\Users\admin\AppData\Local\Temp\7zS6E3A.tmp\isolate.ini | text | |
MD5:EA1B0C3A3EBF4159D4205EA7E0205C80 | SHA256:5191B6B4FC72FEF2492B8289142B0CFDE30F2362BFF9E9AFDA09C6D88C07EE56 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
37
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5352 | SIHClient.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5352 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5352 | SIHClient.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5352 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5352 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.109.210.53:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
5352 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6376 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2292 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
Process | Message |
|---|---|
SymNRT.exe |
---- SymNRT LOG START ----
|
SymNRT.exe | Using REGULAR timer.
|
SymNRT.exe | Friday, 27 June 2025 Time: 14:02
|
SymNRT.exe | RELEASE Version: 21.0.0.14
|
SymNRT.exe | |
SymNRT.exe | 0001: < 1 ENTER> WinMain
|
SymNRT.exe | 0002: < 1 INFO > WinMain -> Firewall enabled.
|
SymNRT.exe | 0003: < 2 ENTER> CCprApp::Run()
|
SymNRT.exe | CIsolation::GetRegistryHive(): RegOpenKeyEx() returned ERROR_FILE_NOT_FOUND |
SymNRT.exe | 0021: < 3 LEAVE> IsMSIInstallationValid() [00:00:001]
|