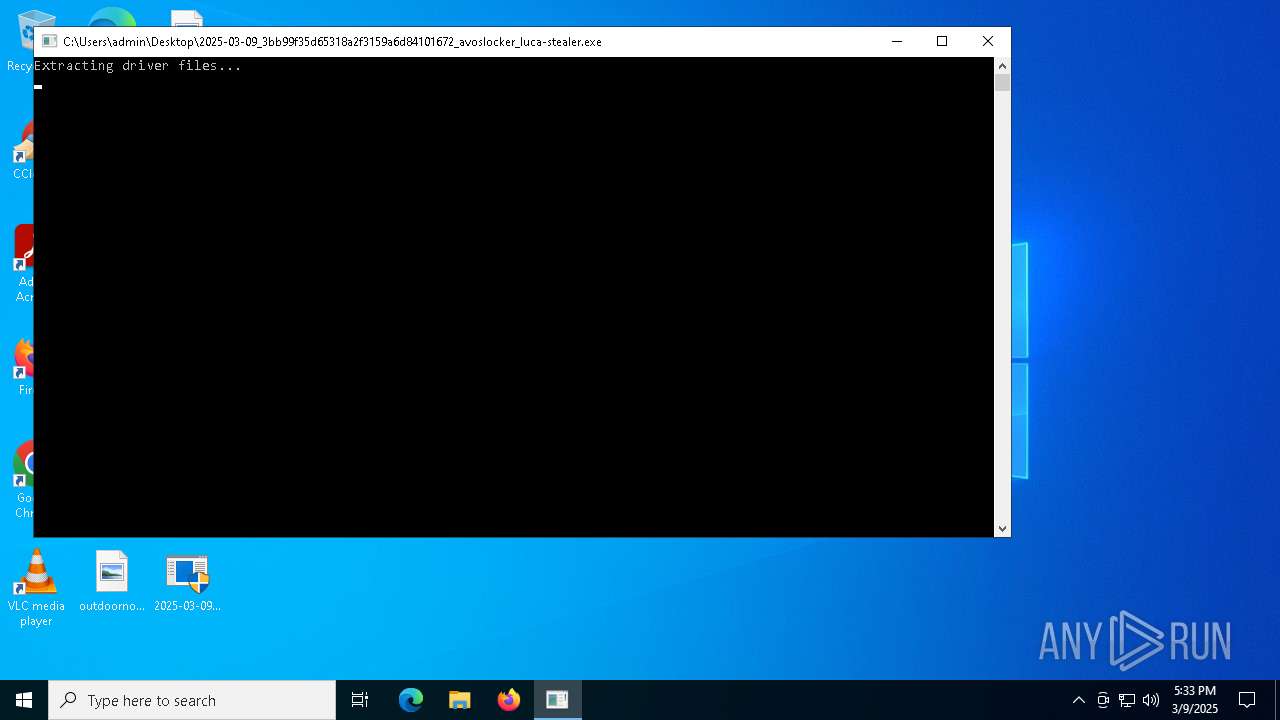
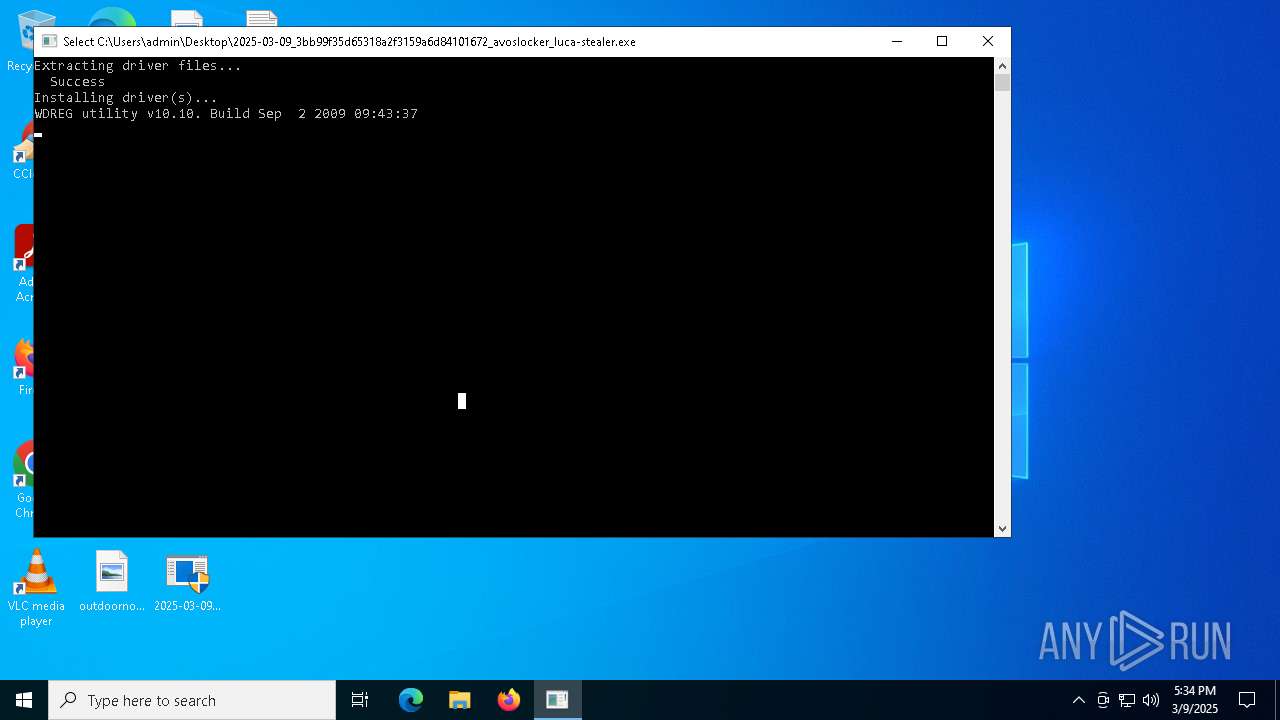
| File name: | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer |
| Full analysis: | https://app.any.run/tasks/c2315f3d-54c0-4a4e-94c8-95177e170536 |
| Verdict: | Malicious activity |
| Analysis date: | March 09, 2025, 17:33:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 6 sections |
| MD5: | 3BB99F35D65318A2F3159A6D84101672 |
| SHA1: | 044265ABD95D3847682D442D3FFD44752A268F68 |
| SHA256: | C2063DA42DF4FACC442411C95F145E88C58A9D704040DD709C910B7EFC98D37C |
| SSDEEP: | 49152:vgnKM5UnUK20RWf31vsu1UTHNGCPUsR6BMnJA:vgnv5WUkFu0HfcsTJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
- wdreg.exe (PID: 8012)
- drvinst.exe (PID: 8080)
- drvinst.exe (PID: 8176)
Executable content was dropped or overwritten
- wdreg.exe (PID: 8012)
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
- drvinst.exe (PID: 8080)
- drvinst.exe (PID: 8176)
Starts CMD.EXE for commands execution
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
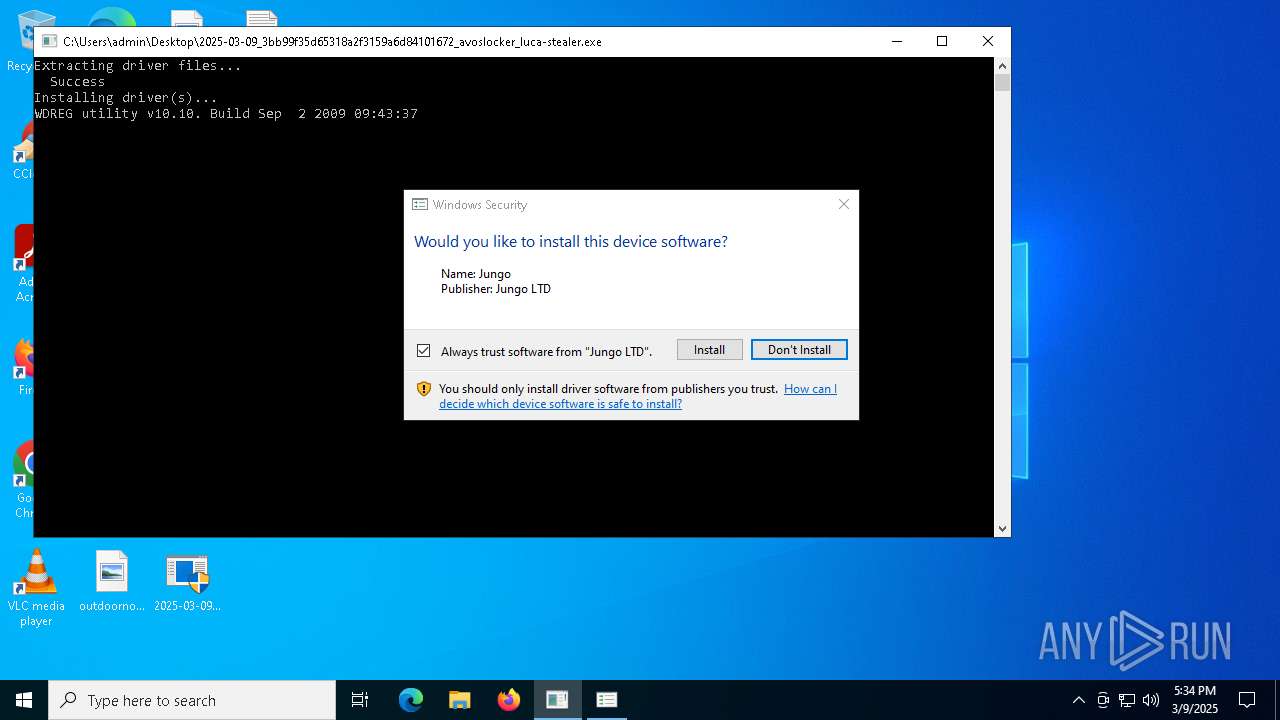
Adds/modifies Windows certificates
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
- wdreg.exe (PID: 8012)
Creates files in the driver directory
- drvinst.exe (PID: 8080)
- drvinst.exe (PID: 8176)
Creates or modifies Windows services
- drvinst.exe (PID: 8176)
The executable file from the user directory is run by the CMD process
- wdreg.exe (PID: 8012)
Reads security settings of Internet Explorer
- wdreg.exe (PID: 8012)
INFO
Checks supported languages
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
- wdreg.exe (PID: 8012)
- drvinst.exe (PID: 8080)
- drvinst.exe (PID: 8176)
Create files in a temporary directory
- wdreg.exe (PID: 8012)
Creates files in the program directory
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
Reads the computer name
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
- drvinst.exe (PID: 8080)
- drvinst.exe (PID: 8176)
- wdreg.exe (PID: 8012)
The sample compiled with english language support
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
- drvinst.exe (PID: 8080)
- wdreg.exe (PID: 8012)
- drvinst.exe (PID: 8176)
Reads the machine GUID from the registry
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
- drvinst.exe (PID: 8080)
- wdreg.exe (PID: 8012)
Reads the software policy settings
- 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe (PID: 7852)
- rundll32.exe (PID: 8108)
- drvinst.exe (PID: 8080)
- slui.exe (PID: 7244)
- wdreg.exe (PID: 8012)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 8108)
Adds/modifies Windows certificates
- drvinst.exe (PID: 8080)
Checks proxy server information
- slui.exe (PID: 7244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (49.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.7) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.8) |
| .exe | | | Win32 Executable (generic) (5.3) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:04:25 23:20:47+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.26 |
| CodeSize: | 134144 |
| InitializedDataSize: | 1243648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x153141 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
132
Monitored processes
9
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7244 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7744 | "C:\Users\admin\Desktop\2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe" | C:\Users\admin\Desktop\2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7852 | "C:\Users\admin\Desktop\2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe" | C:\Users\admin\Desktop\2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 7864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7996 | C:\WINDOWS\system32\cmd.exe /c C:\Users\admin\usb_driver\64\wdreg.exe -silent -log TNMWDlog.txt -inf C:\Users\admin\usb_driver\64\windrvr6.inf install | C:\Windows\SysWOW64\cmd.exe | — | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8012 | C:\Users\admin\usb_driver\64\wdreg.exe -silent -log TNMWDlog.txt -inf C:\Users\admin\usb_driver\64\windrvr6.inf install | C:\Users\admin\usb_driver\64\wdreg.exe | cmd.exe | ||||||||||||
User: admin Company: Jungo Integrity Level: HIGH Description: WDREG Installation Utility 10.10 Exit code: 0 Version: 10.10 Modules
| |||||||||||||||
| 8080 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{15c6789e-200a-8746-acdb-e91877c78d60}\windrvr6.inf" "9" "46706724b" "00000000000000EC" "WinSta0\Default" "00000000000001E0" "208" "C:\Users\admin\usb_driver\64" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8108 | rundll32.exe C:\WINDOWS\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{3c0276ba-ef9d-eb48-928c-451afeb62769} Global\{79cdc44c-dcda-2f4a-9564-abf18d916586} C:\WINDOWS\System32\DriverStore\Temp\{7da14258-aefe-724c-8a8a-5d5b915513b8}\windrvr6.inf C:\WINDOWS\System32\DriverStore\Temp\{7da14258-aefe-724c-8a8a-5d5b915513b8}\wd1010.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8176 | DrvInst.exe "2" "211" "ROOT\JUNGO\0000" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:ed86ca11620928ee:DriverInstall:10.1.0.0:*windrvr6," "42c2a9b4f" "00000000000001DC" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 553
Read events
22 502
Write events
28
Delete events
23
Modification events
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
Value: | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
| Operation: | write | Name: | Blob |
Value: 03000000010000001400000093F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D02000000010000004C0000001C0000000000000001000000200000000000000000000000020000006C006900620077006400690020006B0065007900200063006F006E007400610069006E006500720000000000000000000B000000010000000E0000006C0069006200770064006900000020000000010000008D0500003082058930820371A00302010202103CB2DD6A44BF0C9647593DBDA9170B13300D06092A864886F70D01010B05003041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E0065007200610074006500640029301E170D3235303330393137333335395A170D3239303130313030303030305A3041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E006500720061007400650064002930820222300D06092A864886F70D01010105000382020F003082020A0282020100D6BF152424557212C0D3EDBC5DF6B36ACD7D7FF459706538EB39844CC7738B3A2BFE7A70038F7323A78DE0BC50D829687707240F44D5658E58B85E908B1A95FC01C128BC370AD2121CC0069130D25089D51AF69CA1B73BEFD809EDCE68D8FC1C72085139A98B1C5D2C588A968479B9915F2FE7C673D1A465326FA7C29C74111A321B08FFFE0F3A1D2E09A79827C5B82D9492A93606C1E2F70DDA380582CED0FB75C29DF0C93E54050FA467C2874AE674AEA6B479F7FA06F6ABFEE84A940CF8AAB9B62E7B0E4ED070E4055394ED53F6DC51B2864615E4B3F5BC4FF9A99D7ECD0AFA756088AD61D29C0715A09B771331168758D0D4616A9654F5E4524651BFD1C531BCCC1663052B1BD01EB19F244123EF37411CF055488876077FF2FA58AC1039B93BB7E16E42E347978322B6EE0DF707715944FDAC058259A6FA65B1055D5E5286B9754C94D94468B4700A8E0E52872B4F33A84BB636A0A6CF9069C1ABDD3C824BC65728EFB10C6C20C0ECCABB25E3A422110D81661963C284D7E32668076628EC8D26E56453C2C9244A37F5FE1C464B7DD0600425E6EB6E6F633E03AF01012E45F8198622D17070979187F40FBCED572E8D40768F129C2781E416E3FF6D70012E5E1177260272EBDDDAB74830A2A94505C2D8A0BF476BE272D531864AE6454C5D3AA5EA1663DB07EA1512DC27818E570C2CFD4FB4CE04F0197F266D48B9DF290203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D01010B050003820201002C3ECFECC4694AD4534420FAAA2B81180556B583F044192FC99593D247B354243ED810610509200A78D071AE59793D01AF3247262EADAECA003577178383A6B5AC60F02AD7FD5E06D5F5D31581EDB5DB05B8B10C166A0E17DF932119C675148A1E9D6E6937A01BD5FD693348DE92B62812BB9F70B6CB1ADD4A298246A78D3017527D8A94BB3F5ED0CE11BBDA6CD2C021EDD0550767B8F11648F46FE6ED9253FE67A06E43A38B02ABF910D1515E1D423B54844DCA9322A0B683D99D9EB8BF7E20F59E620F00BC715AF7F3B48928B292EEE0667DFE34148EFB0C79D977DDE569247BC7CE05797A4C562A689FD1AF83E08257AB8502A8DFB29DCD732D5F3D0B3F7485A5183D325D5B99930D0C57DAE8C519A3AD2B7303FF6DD8C515D0B808463FD0535A4F4A5EBDBE0536791BBA7AEF1D82605FE5DCEFDC77E667C575DC71190C7740030456809B626ABCCF0F9A93782CB854A828EA6EA34C09980A892298105D5E52D18E6A0E3ECB5EC61BD053B32395925D1FFEE566D693FEC34900AA8647807C7BBB68C85203CC4ECE214BCBF36DAFD3207187663771C4931A135CADB26244BBECC2151F61C967A157DFEB2441E4A5DF5F061B63FCC79DB905A5376DED5774F998AF0C3B668C378D73F4A7CBEAEBCA8696FBF4908DD59B70F7676CD14F70B42442EC1BC3A653D6A220E932D77DEF6626D42A7F0DD25BE39053D421AC564EDCFD | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates |
| Operation: | delete value | Name: | 93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
Value: | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
| Operation: | write | Name: | Blob |
Value: 03000000010000001400000093F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D02000000010000004C0000001C0000000000000001000000200000000000000000000000020000006C006900620077006400690020006B0065007900200063006F006E007400610069006E006500720000000000000000000B000000010000000E0000006C0069006200770064006900000020000000010000008D0500003082058930820371A00302010202103CB2DD6A44BF0C9647593DBDA9170B13300D06092A864886F70D01010B05003041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E0065007200610074006500640029301E170D3235303330393137333335395A170D3239303130313030303030305A3041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E006500720061007400650064002930820222300D06092A864886F70D01010105000382020F003082020A0282020100D6BF152424557212C0D3EDBC5DF6B36ACD7D7FF459706538EB39844CC7738B3A2BFE7A70038F7323A78DE0BC50D829687707240F44D5658E58B85E908B1A95FC01C128BC370AD2121CC0069130D25089D51AF69CA1B73BEFD809EDCE68D8FC1C72085139A98B1C5D2C588A968479B9915F2FE7C673D1A465326FA7C29C74111A321B08FFFE0F3A1D2E09A79827C5B82D9492A93606C1E2F70DDA380582CED0FB75C29DF0C93E54050FA467C2874AE674AEA6B479F7FA06F6ABFEE84A940CF8AAB9B62E7B0E4ED070E4055394ED53F6DC51B2864615E4B3F5BC4FF9A99D7ECD0AFA756088AD61D29C0715A09B771331168758D0D4616A9654F5E4524651BFD1C531BCCC1663052B1BD01EB19F244123EF37411CF055488876077FF2FA58AC1039B93BB7E16E42E347978322B6EE0DF707715944FDAC058259A6FA65B1055D5E5286B9754C94D94468B4700A8E0E52872B4F33A84BB636A0A6CF9069C1ABDD3C824BC65728EFB10C6C20C0ECCABB25E3A422110D81661963C284D7E32668076628EC8D26E56453C2C9244A37F5FE1C464B7DD0600425E6EB6E6F633E03AF01012E45F8198622D17070979187F40FBCED572E8D40768F129C2781E416E3FF6D70012E5E1177260272EBDDDAB74830A2A94505C2D8A0BF476BE272D531864AE6454C5D3AA5EA1663DB07EA1512DC27818E570C2CFD4FB4CE04F0197F266D48B9DF290203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D01010B050003820201002C3ECFECC4694AD4534420FAAA2B81180556B583F044192FC99593D247B354243ED810610509200A78D071AE59793D01AF3247262EADAECA003577178383A6B5AC60F02AD7FD5E06D5F5D31581EDB5DB05B8B10C166A0E17DF932119C675148A1E9D6E6937A01BD5FD693348DE92B62812BB9F70B6CB1ADD4A298246A78D3017527D8A94BB3F5ED0CE11BBDA6CD2C021EDD0550767B8F11648F46FE6ED9253FE67A06E43A38B02ABF910D1515E1D423B54844DCA9322A0B683D99D9EB8BF7E20F59E620F00BC715AF7F3B48928B292EEE0667DFE34148EFB0C79D977DDE569247BC7CE05797A4C562A689FD1AF83E08257AB8502A8DFB29DCD732D5F3D0B3F7485A5183D325D5B99930D0C57DAE8C519A3AD2B7303FF6DD8C515D0B808463FD0535A4F4A5EBDBE0536791BBA7AEF1D82605FE5DCEFDC77E667C575DC71190C7740030456809B626ABCCF0F9A93782CB854A828EA6EA34C09980A892298105D5E52D18E6A0E3ECB5EC61BD053B32395925D1FFEE566D693FEC34900AA8647807C7BBB68C85203CC4ECE214BCBF36DAFD3207187663771C4931A135CADB26244BBECC2151F61C967A157DFEB2441E4A5DF5F061B63FCC79DB905A5376DED5774F998AF0C3B668C378D73F4A7CBEAEBCA8696FBF4908DD59B70F7676CD14F70B42442EC1BC3A653D6A220E932D77DEF6626D42A7F0DD25BE39053D421AC564EDCFD | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
| Operation: | write | Name: | Blob |
Value: 03000000010000001400000093F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D20000000010000008D0500003082058930820371A00302010202103CB2DD6A44BF0C9647593DBDA9170B13300D06092A864886F70D01010B05003041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E0065007200610074006500640029301E170D3235303330393137333335395A170D3239303130313030303030305A3041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E006500720061007400650064002930820222300D06092A864886F70D01010105000382020F003082020A0282020100D6BF152424557212C0D3EDBC5DF6B36ACD7D7FF459706538EB39844CC7738B3A2BFE7A70038F7323A78DE0BC50D829687707240F44D5658E58B85E908B1A95FC01C128BC370AD2121CC0069130D25089D51AF69CA1B73BEFD809EDCE68D8FC1C72085139A98B1C5D2C588A968479B9915F2FE7C673D1A465326FA7C29C74111A321B08FFFE0F3A1D2E09A79827C5B82D9492A93606C1E2F70DDA380582CED0FB75C29DF0C93E54050FA467C2874AE674AEA6B479F7FA06F6ABFEE84A940CF8AAB9B62E7B0E4ED070E4055394ED53F6DC51B2864615E4B3F5BC4FF9A99D7ECD0AFA756088AD61D29C0715A09B771331168758D0D4616A9654F5E4524651BFD1C531BCCC1663052B1BD01EB19F244123EF37411CF055488876077FF2FA58AC1039B93BB7E16E42E347978322B6EE0DF707715944FDAC058259A6FA65B1055D5E5286B9754C94D94468B4700A8E0E52872B4F33A84BB636A0A6CF9069C1ABDD3C824BC65728EFB10C6C20C0ECCABB25E3A422110D81661963C284D7E32668076628EC8D26E56453C2C9244A37F5FE1C464B7DD0600425E6EB6E6F633E03AF01012E45F8198622D17070979187F40FBCED572E8D40768F129C2781E416E3FF6D70012E5E1177260272EBDDDAB74830A2A94505C2D8A0BF476BE272D531864AE6454C5D3AA5EA1663DB07EA1512DC27818E570C2CFD4FB4CE04F0197F266D48B9DF290203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D01010B050003820201002C3ECFECC4694AD4534420FAAA2B81180556B583F044192FC99593D247B354243ED810610509200A78D071AE59793D01AF3247262EADAECA003577178383A6B5AC60F02AD7FD5E06D5F5D31581EDB5DB05B8B10C166A0E17DF932119C675148A1E9D6E6937A01BD5FD693348DE92B62812BB9F70B6CB1ADD4A298246A78D3017527D8A94BB3F5ED0CE11BBDA6CD2C021EDD0550767B8F11648F46FE6ED9253FE67A06E43A38B02ABF910D1515E1D423B54844DCA9322A0B683D99D9EB8BF7E20F59E620F00BC715AF7F3B48928B292EEE0667DFE34148EFB0C79D977DDE569247BC7CE05797A4C562A689FD1AF83E08257AB8502A8DFB29DCD732D5F3D0B3F7485A5183D325D5B99930D0C57DAE8C519A3AD2B7303FF6DD8C515D0B808463FD0535A4F4A5EBDBE0536791BBA7AEF1D82605FE5DCEFDC77E667C575DC71190C7740030456809B626ABCCF0F9A93782CB854A828EA6EA34C09980A892298105D5E52D18E6A0E3ECB5EC61BD053B32395925D1FFEE566D693FEC34900AA8647807C7BBB68C85203CC4ECE214BCBF36DAFD3207187663771C4931A135CADB26244BBECC2151F61C967A157DFEB2441E4A5DF5F061B63FCC79DB905A5376DED5774F998AF0C3B668C378D73F4A7CBEAEBCA8696FBF4908DD59B70F7676CD14F70B42442EC1BC3A653D6A220E932D77DEF6626D42A7F0DD25BE39053D421AC564EDCFD | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
| Operation: | write | Name: | Blob |
Value: 0B000000010000000E0000006C0069006200770064006900000003000000010000001400000093F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D20000000010000008D0500003082058930820371A00302010202103CB2DD6A44BF0C9647593DBDA9170B13300D06092A864886F70D01010B05003041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E0065007200610074006500640029301E170D3235303330393137333335395A170D3239303130313030303030305A3041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E006500720061007400650064002930820222300D06092A864886F70D01010105000382020F003082020A0282020100D6BF152424557212C0D3EDBC5DF6B36ACD7D7FF459706538EB39844CC7738B3A2BFE7A70038F7323A78DE0BC50D829687707240F44D5658E58B85E908B1A95FC01C128BC370AD2121CC0069130D25089D51AF69CA1B73BEFD809EDCE68D8FC1C72085139A98B1C5D2C588A968479B9915F2FE7C673D1A465326FA7C29C74111A321B08FFFE0F3A1D2E09A79827C5B82D9492A93606C1E2F70DDA380582CED0FB75C29DF0C93E54050FA467C2874AE674AEA6B479F7FA06F6ABFEE84A940CF8AAB9B62E7B0E4ED070E4055394ED53F6DC51B2864615E4B3F5BC4FF9A99D7ECD0AFA756088AD61D29C0715A09B771331168758D0D4616A9654F5E4524651BFD1C531BCCC1663052B1BD01EB19F244123EF37411CF055488876077FF2FA58AC1039B93BB7E16E42E347978322B6EE0DF707715944FDAC058259A6FA65B1055D5E5286B9754C94D94468B4700A8E0E52872B4F33A84BB636A0A6CF9069C1ABDD3C824BC65728EFB10C6C20C0ECCABB25E3A422110D81661963C284D7E32668076628EC8D26E56453C2C9244A37F5FE1C464B7DD0600425E6EB6E6F633E03AF01012E45F8198622D17070979187F40FBCED572E8D40768F129C2781E416E3FF6D70012E5E1177260272EBDDDAB74830A2A94505C2D8A0BF476BE272D531864AE6454C5D3AA5EA1663DB07EA1512DC27818E570C2CFD4FB4CE04F0197F266D48B9DF290203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D01010B050003820201002C3ECFECC4694AD4534420FAAA2B81180556B583F044192FC99593D247B354243ED810610509200A78D071AE59793D01AF3247262EADAECA003577178383A6B5AC60F02AD7FD5E06D5F5D31581EDB5DB05B8B10C166A0E17DF932119C675148A1E9D6E6937A01BD5FD693348DE92B62812BB9F70B6CB1ADD4A298246A78D3017527D8A94BB3F5ED0CE11BBDA6CD2C021EDD0550767B8F11648F46FE6ED9253FE67A06E43A38B02ABF910D1515E1D423B54844DCA9322A0B683D99D9EB8BF7E20F59E620F00BC715AF7F3B48928B292EEE0667DFE34148EFB0C79D977DDE569247BC7CE05797A4C562A689FD1AF83E08257AB8502A8DFB29DCD732D5F3D0B3F7485A5183D325D5B99930D0C57DAE8C519A3AD2B7303FF6DD8C515D0B808463FD0535A4F4A5EBDBE0536791BBA7AEF1D82605FE5DCEFDC77E667C575DC71190C7740030456809B626ABCCF0F9A93782CB854A828EA6EA34C09980A892298105D5E52D18E6A0E3ECB5EC61BD053B32395925D1FFEE566D693FEC34900AA8647807C7BBB68C85203CC4ECE214BCBF36DAFD3207187663771C4931A135CADB26244BBECC2151F61C967A157DFEB2441E4A5DF5F061B63FCC79DB905A5376DED5774F998AF0C3B668C378D73F4A7CBEAEBCA8696FBF4908DD59B70F7676CD14F70B42442EC1BC3A653D6A220E932D77DEF6626D42A7F0DD25BE39053D421AC564EDCFD | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
| Operation: | write | Name: | Blob |
Value: 03000000010000001400000093F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D20000000010000008D0500003082058930820371A00302010202103CB2DD6A44BF0C9647593DBDA9170B13300D06092A864886F70D01010B05003041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E0065007200610074006500640029301E170D3235303330393137333335395A170D3239303130313030303030305A3041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E006500720061007400650064002930820222300D06092A864886F70D01010105000382020F003082020A0282020100D6BF152424557212C0D3EDBC5DF6B36ACD7D7FF459706538EB39844CC7738B3A2BFE7A70038F7323A78DE0BC50D829687707240F44D5658E58B85E908B1A95FC01C128BC370AD2121CC0069130D25089D51AF69CA1B73BEFD809EDCE68D8FC1C72085139A98B1C5D2C588A968479B9915F2FE7C673D1A465326FA7C29C74111A321B08FFFE0F3A1D2E09A79827C5B82D9492A93606C1E2F70DDA380582CED0FB75C29DF0C93E54050FA467C2874AE674AEA6B479F7FA06F6ABFEE84A940CF8AAB9B62E7B0E4ED070E4055394ED53F6DC51B2864615E4B3F5BC4FF9A99D7ECD0AFA756088AD61D29C0715A09B771331168758D0D4616A9654F5E4524651BFD1C531BCCC1663052B1BD01EB19F244123EF37411CF055488876077FF2FA58AC1039B93BB7E16E42E347978322B6EE0DF707715944FDAC058259A6FA65B1055D5E5286B9754C94D94468B4700A8E0E52872B4F33A84BB636A0A6CF9069C1ABDD3C824BC65728EFB10C6C20C0ECCABB25E3A422110D81661963C284D7E32668076628EC8D26E56453C2C9244A37F5FE1C464B7DD0600425E6EB6E6F633E03AF01012E45F8198622D17070979187F40FBCED572E8D40768F129C2781E416E3FF6D70012E5E1177260272EBDDDAB74830A2A94505C2D8A0BF476BE272D531864AE6454C5D3AA5EA1663DB07EA1512DC27818E570C2CFD4FB4CE04F0197F266D48B9DF290203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D01010B050003820201002C3ECFECC4694AD4534420FAAA2B81180556B583F044192FC99593D247B354243ED810610509200A78D071AE59793D01AF3247262EADAECA003577178383A6B5AC60F02AD7FD5E06D5F5D31581EDB5DB05B8B10C166A0E17DF932119C675148A1E9D6E6937A01BD5FD693348DE92B62812BB9F70B6CB1ADD4A298246A78D3017527D8A94BB3F5ED0CE11BBDA6CD2C021EDD0550767B8F11648F46FE6ED9253FE67A06E43A38B02ABF910D1515E1D423B54844DCA9322A0B683D99D9EB8BF7E20F59E620F00BC715AF7F3B48928B292EEE0667DFE34148EFB0C79D977DDE569247BC7CE05797A4C562A689FD1AF83E08257AB8502A8DFB29DCD732D5F3D0B3F7485A5183D325D5B99930D0C57DAE8C519A3AD2B7303FF6DD8C515D0B808463FD0535A4F4A5EBDBE0536791BBA7AEF1D82605FE5DCEFDC77E667C575DC71190C7740030456809B626ABCCF0F9A93782CB854A828EA6EA34C09980A892298105D5E52D18E6A0E3ECB5EC61BD053B32395925D1FFEE566D693FEC34900AA8647807C7BBB68C85203CC4ECE214BCBF36DAFD3207187663771C4931A135CADB26244BBECC2151F61C967A157DFEB2441E4A5DF5F061B63FCC79DB905A5376DED5774F998AF0C3B668C378D73F4A7CBEAEBCA8696FBF4908DD59B70F7676CD14F70B42442EC1BC3A653D6A220E932D77DEF6626D42A7F0DD25BE39053D421AC564EDCFD | |||
| (PID) Process: | (7852) 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\TrustedPublisher\Certificates\93F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D |
| Operation: | write | Name: | Blob |
Value: 0B000000010000000E0000006C0069006200770064006900000003000000010000001400000093F9AE9D3FF9C10BB8AD877535C9C1A8D0184B0D20000000010000008D0500003082058930820371A00302010202103CB2DD6A44BF0C9647593DBDA9170B13300D06092A864886F70D01010B05003041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E0065007200610074006500640029301E170D3235303330393137333335395A170D3239303130313030303030305A3041313F303D06035504031E36005500530042005C00200028006C006900620077006400690020006100750074006F00670065006E006500720061007400650064002930820222300D06092A864886F70D01010105000382020F003082020A0282020100D6BF152424557212C0D3EDBC5DF6B36ACD7D7FF459706538EB39844CC7738B3A2BFE7A70038F7323A78DE0BC50D829687707240F44D5658E58B85E908B1A95FC01C128BC370AD2121CC0069130D25089D51AF69CA1B73BEFD809EDCE68D8FC1C72085139A98B1C5D2C588A968479B9915F2FE7C673D1A465326FA7C29C74111A321B08FFFE0F3A1D2E09A79827C5B82D9492A93606C1E2F70DDA380582CED0FB75C29DF0C93E54050FA467C2874AE674AEA6B479F7FA06F6ABFEE84A940CF8AAB9B62E7B0E4ED070E4055394ED53F6DC51B2864615E4B3F5BC4FF9A99D7ECD0AFA756088AD61D29C0715A09B771331168758D0D4616A9654F5E4524651BFD1C531BCCC1663052B1BD01EB19F244123EF37411CF055488876077FF2FA58AC1039B93BB7E16E42E347978322B6EE0DF707715944FDAC058259A6FA65B1055D5E5286B9754C94D94468B4700A8E0E52872B4F33A84BB636A0A6CF9069C1ABDD3C824BC65728EFB10C6C20C0ECCABB25E3A422110D81661963C284D7E32668076628EC8D26E56453C2C9244A37F5FE1C464B7DD0600425E6EB6E6F633E03AF01012E45F8198622D17070979187F40FBCED572E8D40768F129C2781E416E3FF6D70012E5E1177260272EBDDDAB74830A2A94505C2D8A0BF476BE272D531864AE6454C5D3AA5EA1663DB07EA1512DC27818E570C2CFD4FB4CE04F0197F266D48B9DF290203010001A37D307B30160603551D250101FF040C300A06082B0601050507030330200603551D07041930178615687474703A2F2F6C69627764692E616B656F2E6965303F0603551D2004383036303406082B060105050702013028302606082B06010505070201161A687474703A2F2F6C69627764692D6370732E616B656F2E696500300D06092A864886F70D01010B050003820201002C3ECFECC4694AD4534420FAAA2B81180556B583F044192FC99593D247B354243ED810610509200A78D071AE59793D01AF3247262EADAECA003577178383A6B5AC60F02AD7FD5E06D5F5D31581EDB5DB05B8B10C166A0E17DF932119C675148A1E9D6E6937A01BD5FD693348DE92B62812BB9F70B6CB1ADD4A298246A78D3017527D8A94BB3F5ED0CE11BBDA6CD2C021EDD0550767B8F11648F46FE6ED9253FE67A06E43A38B02ABF910D1515E1D423B54844DCA9322A0B683D99D9EB8BF7E20F59E620F00BC715AF7F3B48928B292EEE0667DFE34148EFB0C79D977DDE569247BC7CE05797A4C562A689FD1AF83E08257AB8502A8DFB29DCD732D5F3D0B3F7485A5183D325D5B99930D0C57DAE8C519A3AD2B7303FF6DD8C515D0B808463FD0535A4F4A5EBDBE0536791BBA7AEF1D82605FE5DCEFDC77E667C575DC71190C7740030456809B626ABCCF0F9A93782CB854A828EA6EA34C09980A892298105D5E52D18E6A0E3ECB5EC61BD053B32395925D1FFEE566D693FEC34900AA8647807C7BBB68C85203CC4ECE214BCBF36DAFD3207187663771C4931A135CADB26244BBECC2151F61C967A157DFEB2441E4A5DF5F061B63FCC79DB905A5376DED5774F998AF0C3B668C378D73F4A7CBEAEBCA8696FBF4908DD59B70F7676CD14F70B42442EC1BC3A653D6A220E932D77DEF6626D42A7F0DD25BE39053D421AC564EDCFD | |||
Executable files
13
Suspicious files
18
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\32\Mup.cat.in | text | |
MD5:6DE338260493FDBB027B2DBAF72C2109 | SHA256:94A70336F2CCDC9A2A1B2E10D8B66BA79C85BDEE7129D68BFE49F624DAC27E3F | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\32\wdreg.exe | executable | |
MD5:8290F16499614F1D94CAA6047E0627F4 | SHA256:51666BF624D81D1F7F7429A8D1748138CBE477E4C12BE68561D9F8F09D92AD57 | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\32\installer_x86.exe | executable | |
MD5:077CBE013EFE92F46B4138A145ED63A3 | SHA256:D8B175245CC79193957099CAD03B8A205F09F1816A53989DB34236F57077FE0F | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\64\windrvr6.inf | binary | |
MD5:D8119783E76170A72F703D1D146B2EAC | SHA256:327175D40EEA4A00365FA0F8E150A86EA80AF901E6B094417A589002ECBF0DC3 | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\64\MUP.inf | binary | |
MD5:82D612CA4CC278F3C04173BCEFAD7F0C | SHA256:9A349E0389F8CD3B0EC8AD26CA6C7B71D929C121D0970213BD4A7EC6F0AFC088 | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\32\wd1010.cat | binary | |
MD5:4045DDD3E224E7013B108C74345CBCEB | SHA256:DC6149601AB10D9C466DAEE1672538E6F15378CDAA813AD64BC8C9E992A24BE8 | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\32\Mup.inf | binary | |
MD5:82D612CA4CC278F3C04173BCEFAD7F0C | SHA256:9A349E0389F8CD3B0EC8AD26CA6C7B71D929C121D0970213BD4A7EC6F0AFC088 | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\32\windrvr6.inf | binary | |
MD5:D8119783E76170A72F703D1D146B2EAC | SHA256:327175D40EEA4A00365FA0F8E150A86EA80AF901E6B094417A589002ECBF0DC3 | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\64\MUP.cat.in | text | |
MD5:6DE338260493FDBB027B2DBAF72C2109 | SHA256:94A70336F2CCDC9A2A1B2E10D8B66BA79C85BDEE7129D68BFE49F624DAC27E3F | |||
| 7852 | 2025-03-09_3bb99f35d65318a2f3159a6d84101672_avoslocker_luca-stealer.exe | C:\Users\admin\usb_driver\64\wd1010.cat | binary | |
MD5:695F526D6F771D4F164E7B16BEF5AAEA | SHA256:AA38BC1CB130F9E8E44035980AE33040342CF7F09D77A8698859BF2F0C4C30D0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
19
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
7448 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7244 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |