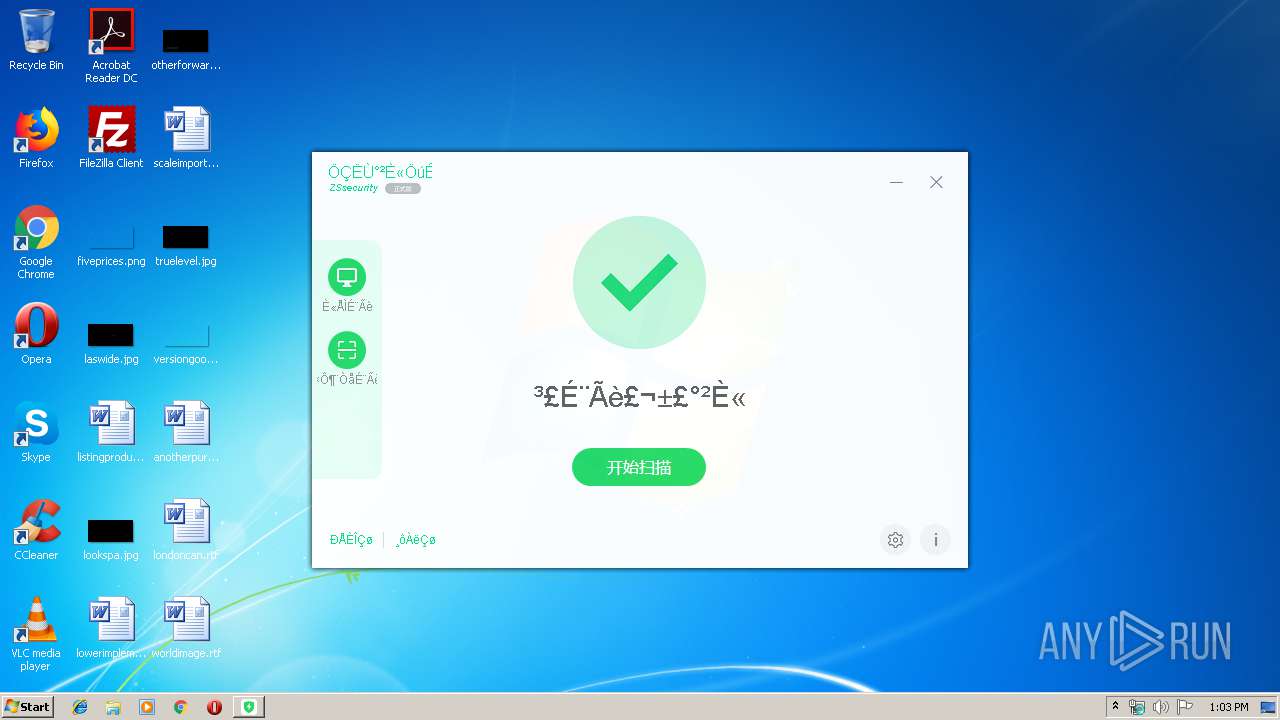
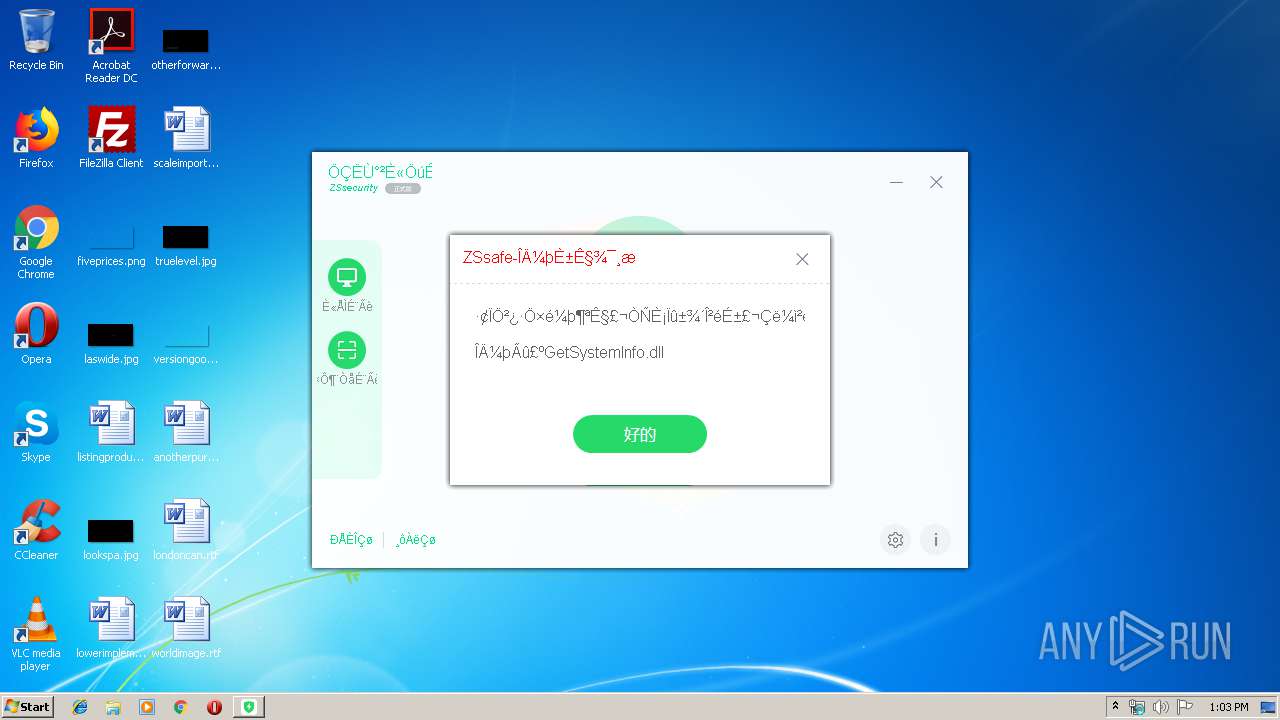
| File name: | ZSsafe.exe |
| Full analysis: | https://app.any.run/tasks/4793f1ea-1dbb-4c69-9f2b-7f26f93e393d |
| Verdict: | Malicious activity |
| Analysis date: | August 19, 2019, 12:02:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 78CC1FBAA1A89984591C90218E9D8806 |
| SHA1: | 400D6F503BA76129E9D2F9FE77C65F6CCEB24F47 |
| SHA256: | C1F8A2BE52E1739A4D8475F97F73DAEAE71AF56BCD5BF468862B38B5F7E4A10B |
| SSDEEP: | 49152:7fkH7Ag+ZNBaX5FvI6zZDQ6Y3eqa3rpq9nBmuT+xahqg2ryR7KmBS2RBokBF45ck:Dr9aX5l83f0rcBtTUao7yq27okBa5oA |
MALICIOUS
Changes settings of System certificates
- ctfmon.exe (PID: 3344)
Loads dropped or rewritten executable
- ZSsafe.exe (PID: 4092)
SUSPICIOUS
Executable content was dropped or overwritten
- ZSsafe.exe (PID: 4092)
Adds / modifies Windows certificates
- ctfmon.exe (PID: 3344)
Creates files in the user directory
- ctfmon.exe (PID: 3344)
Reads Internet Cache Settings
- ctfmon.exe (PID: 3344)
Reads internet explorer settings
- ctfmon.exe (PID: 3344)
INFO
Reads settings of System Certificates
- ctfmon.exe (PID: 3344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE Yoda's Crypter (63.7) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.7) |
| .exe | | | Win32 Executable (generic) (10.8) |
| .exe | | | Generic Win/DOS Executable (4.8) |
| .exe | | | DOS Executable Generic (4.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1972:12:25 06:33:23+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 5.12 |
| CodeSize: | - |
| InitializedDataSize: | - |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 25-Dec-1972 05:33:23 |
| Detected languages: |
|
| FileVersion: | 1.1.6.8 |
| FileDescription: | ZSsafe主程序 |
| ProductName: | ZSsafe |
| ProductVersion: | 1.1.6.8 |
| CompanyName: | 逝去的青春 |
| LegalCopyright: | 逝去的青春 版权所有 |
| Comments: | 本程序使用易语言编写(http://www.eyuyan.com) |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000B0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 2 |
| Time date stamp: | 25-Dec-1972 05:33:23 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.UPX1 | 0x001C7000 | 0x0014CA75 | 0x001485B3 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.88471 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.02094 | 697 | Latin 1 / Western European | Chinese - PRC | RT_MANIFEST |
129 | 2.01924 | 20 | Latin 1 / Western European | Chinese - PRC | RT_GROUP_ICON |
Imports
kernel32.dll |
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3344 | ctfmon.exe | C:\Windows\system32\ctfmon.exe | ZSsafe.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3572 | "C:\Users\admin\AppData\Local\Temp\ZSsafe.exe" | C:\Users\admin\AppData\Local\Temp\ZSsafe.exe | — | explorer.exe | |||||||||||
User: admin Company: 逝去的青春 Integrity Level: MEDIUM Description: ZSsafe主程序 Exit code: 3221226540 Version: 1.1.6.8 Modules
| |||||||||||||||
| 4092 | "C:\Users\admin\AppData\Local\Temp\ZSsafe.exe" | C:\Users\admin\AppData\Local\Temp\ZSsafe.exe | explorer.exe | ||||||||||||
User: admin Company: 逝去的青春 Integrity Level: HIGH Description: ZSsafe主程序 Exit code: 0 Version: 1.1.6.8 Modules
| |||||||||||||||
Total events
189
Read events
149
Write events
39
Delete events
1
Modification events
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ctfmon_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ctfmon_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ctfmon_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ctfmon_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ctfmon_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ctfmon_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ctfmon_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3344) ctfmon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ctfmon_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
12
Suspicious files
0
Text files
88
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\16a26f.tmp | — | |
MD5:— | SHA256:— | |||
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\16a27f.tmp | — | |
MD5:— | SHA256:— | |||
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\16a280.tmp | — | |
MD5:— | SHA256:— | |||
| 3344 | ctfmon.exe | C:\Users\admin\AppData\Local\Temp\4OCh7YM.sys | — | |
MD5:— | SHA256:— | |||
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\iext2.fne | executable | |
MD5:— | SHA256:— | |||
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\krnln.fnr | executable | |
MD5:— | SHA256:— | |||
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\EThread.fne | executable | |
MD5:— | SHA256:— | |||
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\iext.fnr | executable | |
MD5:— | SHA256:— | |||
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\spec.fne | executable | |
MD5:— | SHA256:— | |||
| 4092 | ZSsafe.exe | C:\Users\admin\AppData\Local\Temp\E_N60005\shell.fne | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
77
TCP/UDP connections
41
DNS requests
29
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3344 | ctfmon.exe | GET | 302 | 123.58.180.39:80 | http://mojunxie521.blog.163.com/blog/static/27250327320174622243849/ | CN | — | — | malicious |
3344 | ctfmon.exe | GET | — | 218.11.8.232:80 | http://leyun-1251032746.file.myqcloud.com/404/style.css?3 | CN | — | — | malicious |
3344 | ctfmon.exe | GET | 404 | 139.99.98.4:80 | http://www.mojunxie.win/cansu521.txt | SG | html | 1.16 Kb | malicious |
3344 | ctfmon.exe | GET | 200 | 139.99.98.4:80 | http://www.mojunyy.cn/css/index.css | SG | text | 2.76 Kb | malicious |
3344 | ctfmon.exe | GET | 200 | 139.99.98.4:80 | http://www.mojunyy.cn/ | SG | html | 8.98 Kb | malicious |
3344 | ctfmon.exe | GET | 200 | 139.99.98.4:80 | http://www.mojunyy.cn/css/style.css | SG | text | 11.2 Kb | malicious |
3344 | ctfmon.exe | GET | 200 | 139.99.98.4:80 | http://www.mojunyy.cn/images/logo.png | SG | image | 4.43 Kb | malicious |
3344 | ctfmon.exe | GET | 200 | 139.99.98.4:80 | http://www.mojunyy.cn/fonts/icomoon.eot?ozi1xj | SG | eot | 781 b | malicious |
3344 | ctfmon.exe | GET | 200 | 139.99.98.4:80 | http://www.mojunyy.cn/images/qrcode.png | SG | image | 49.3 Kb | malicious |
3344 | ctfmon.exe | GET | 200 | 139.99.98.4:80 | http://www.mojunyy.cn/js/view-history.js | SG | text | 58.3 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3344 | ctfmon.exe | 123.58.180.39:80 | mojunxie521.blog.163.com | Guangzhou NetEase Computer System Co., Ltd. | CN | malicious |
3344 | ctfmon.exe | 218.11.8.232:80 | leyun-1251032746.file.myqcloud.com | CHINA UNICOM China169 Backbone | CN | unknown |
3344 | ctfmon.exe | 119.146.74.49:80 | apps.bdimg.com | Guangdong | CN | suspicious |
3344 | ctfmon.exe | 139.99.98.4:80 | www.mojunxie.win | OVH SAS | SG | suspicious |
3344 | ctfmon.exe | 64.32.8.138:80 | pic.youku778.com | Sharktech | US | suspicious |
3344 | ctfmon.exe | 163.171.133.124:80 | b.bst.126.net | — | US | malicious |
3344 | ctfmon.exe | 172.247.253.198:443 | img.yongjiu7.com | CNSERVERS LLC | US | unknown |
3344 | ctfmon.exe | 122.114.130.31:80 | yuanlin.6600.org | CHINA UNICOM China169 Backbone | CN | unknown |
3344 | ctfmon.exe | 172.247.253.140:443 | img.yongjiu7.com | CNSERVERS LLC | US | unknown |
3344 | ctfmon.exe | 172.247.253.131:443 | img.yongjiu7.com | CNSERVERS LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mojunxie521.blog.163.com |
| malicious |
blog.163.com |
| whitelisted |
b.bst.126.net |
| malicious |
www.mojunxie.win |
| malicious |
leyun-1251032746.file.myqcloud.com |
| malicious |
yuanlin.6600.org |
| unknown |
www.mojunyy.cn |
| malicious |
apps.bdimg.com |
| whitelisted |
img.yongjiu7.com |
| unknown |
pic.youku778.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3344 | ctfmon.exe | Misc activity | ET INFO DYNAMIC_DNS HTTP Request to a 3322.net Domain *.6600.org |