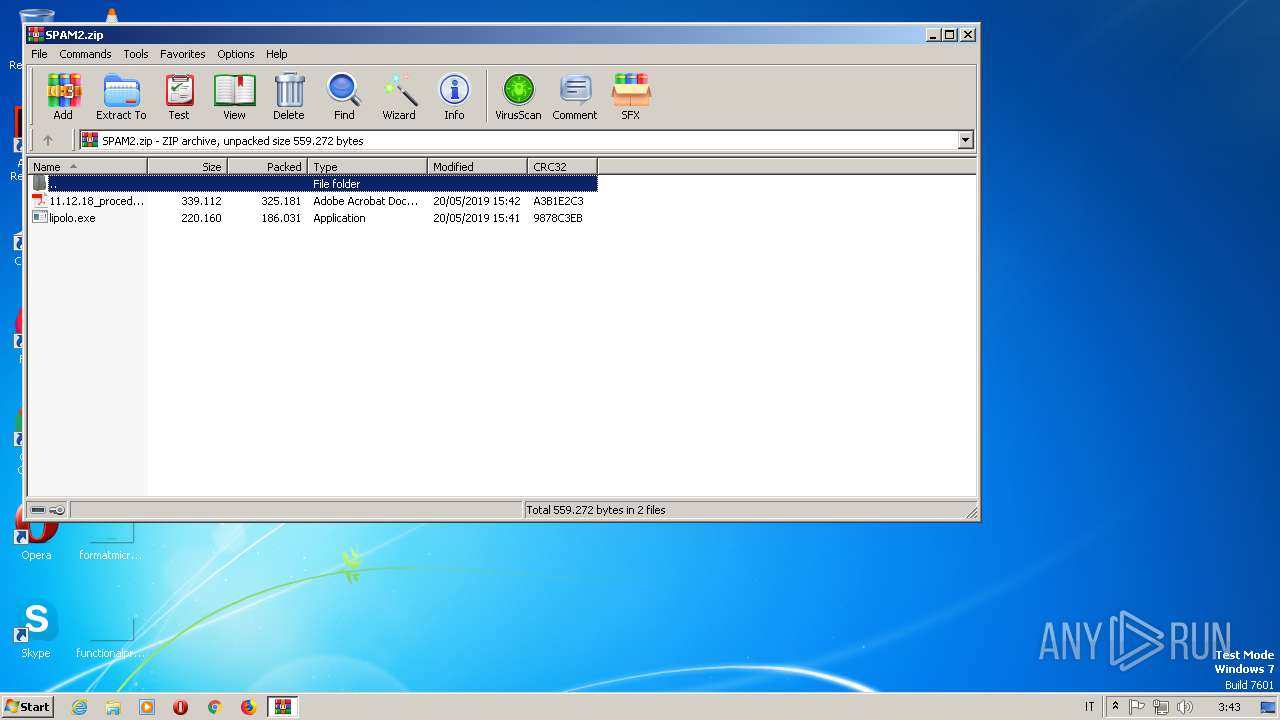
| File name: | SPAM2.zip |
| Full analysis: | https://app.any.run/tasks/ac4cc708-e349-48cc-8a8f-0f8d63732949 |
| Verdict: | Malicious activity |
| Threats: | Gootkit is an advanced banking trojan. It is extremely good at evading detection and has an incredibly effective persistence mechanism, making it a dangerous malware that researchers and organizations should be aware of. |
| Analysis date: | May 20, 2019, 13:43:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 96F69993CF78E6D919C79E5C601A91FD |
| SHA1: | F0CD51CF3096B24C2C5627D6EEDC0DE9BBA3BCA0 |
| SHA256: | C1F5EB5ACEBDE3F4B1C779EFD0C7794CA31744E9EEADB843C045FBCECE0A24F9 |
| SSDEEP: | 12288:+Gfva9euEQb+rkDIQGAhXBbAwW6A4jdrC4vj2xvC:+Gfva9eJmfDBcwW6A4xbS8 |
MALICIOUS
Application was dropped or rewritten from another process
- lipolo.exe (PID: 2064)
- lipolo.exe (PID: 2652)
Changes settings of System certificates
- lipolo.exe (PID: 2652)
GOOTKIT detected
- lipolo.exe (PID: 2064)
Changes internet zones settings
- lipolo.exe (PID: 2064)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2324)
Application launched itself
- lipolo.exe (PID: 2064)
Reads the machine GUID from the registry
- WinRAR.exe (PID: 2324)
Creates files in the program directory
- AdobeARM.exe (PID: 1416)
INFO
Manual execution by user
- lipolo.exe (PID: 2064)
Application launched itself
- RdrCEF.exe (PID: 1960)
Creates files in the user directory
- AcroRd32.exe (PID: 2524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:05:20 15:42:12 |
| ZipCRC: | 0xa3b1e2c3 |
| ZipCompressedSize: | 325181 |
| ZipUncompressedSize: | 339112 |
| ZipFileName: | 11.12.18_procedure_esecutive.pdf |
Total processes
44
Monitored processes
10
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1416 | "C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.821.13.2315 Modules
| |||||||||||||||
| 1420 | "C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-delegated-renderer --disable-desktop-notifications --disable-file-system --disable-shared-workers --disable-speech-input --disable-threaded-compositing --disable-webaudio --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.7.20033 Chrome/35.0.1916.138" --disable-accelerated-compositing --disable-accelerated-video-decode --enable-software-compositing --disable-gpu-compositing --channel="1960.0.867369406\1707999927" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.7.20033.133275 Modules
| |||||||||||||||
| 1960 | "C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" | C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.7.20033.133275 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\lipolo.exe" | C:\Users\admin\Desktop\lipolo.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2324 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SPAM2.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2524 | "C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2324.32398\11.12.18_procedure_esecutive.pdf" | C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | WinRAR.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.7.20033.133275 Modules
| |||||||||||||||
| 2652 | C:\Users\admin\Desktop\lipolo.exe --vwxyz | C:\Users\admin\Desktop\lipolo.exe | lipolo.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2720 | "C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --channel=2524.0.804394056 --type=renderer "C:\Users\admin\AppData\Local\Temp\Rar$DIa2324.32398\11.12.18_procedure_esecutive.pdf" | C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.7.20033.133275 Modules
| |||||||||||||||
| 3008 | "C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-delegated-renderer --disable-desktop-notifications --disable-file-system --disable-shared-workers --disable-speech-input --disable-threaded-compositing --disable-webaudio --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.7.20033 Chrome/35.0.1916.138" --disable-accelerated-compositing --disable-accelerated-video-decode --enable-software-compositing --disable-gpu-compositing --channel="1960.1.300570771\1189661388" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.7.20033.133275 Modules
| |||||||||||||||
| 3048 | "C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.7.20033.133275 Modules
| |||||||||||||||
Total events
1 097
Read events
607
Write events
489
Delete events
1
Modification events
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\65\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SPAM2.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2064) lipolo.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0 |
| Operation: | write | Name: | 2500 |
Value: 3 | |||
| (PID) Process: | (2064) lipolo.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1 |
| Operation: | write | Name: | 2500 |
Value: 3 | |||
Executable files
1
Suspicious files
3
Text files
19
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2720 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 1960 | RdrCEF.exe | C:\Users\admin\AppData\Local\Temp\scoped_dir1960_11019\index | — | |
MD5:— | SHA256:— | |||
| 1960 | RdrCEF.exe | C:\Users\admin\AppData\Local\Temp\scoped_dir1960_11019\data_0 | — | |
MD5:— | SHA256:— | |||
| 1960 | RdrCEF.exe | C:\Users\admin\AppData\Local\Temp\scoped_dir1960_11019\data_1 | — | |
MD5:— | SHA256:— | |||
| 1960 | RdrCEF.exe | C:\Users\admin\AppData\Local\Temp\scoped_dir1960_11019\data_2 | — | |
MD5:— | SHA256:— | |||
| 1960 | RdrCEF.exe | C:\Users\admin\AppData\Local\Temp\scoped_dir1960_11019\data_3 | — | |
MD5:— | SHA256:— | |||
| 2720 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R4F58.tmp | — | |
MD5:— | SHA256:— | |||
| 2720 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R4F57.tmp | — | |
MD5:— | SHA256:— | |||
| 2720 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R4F5A.tmp | — | |
MD5:— | SHA256:— | |||
| 2720 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R4F59.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
8
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2652 | lipolo.exe | GET | — | 185.158.249.144:443 | https://fila.heathercrowe.ca/rbody320 | NL | — | — | malicious |
2652 | lipolo.exe | GET | — | 185.158.249.144:443 | https://fila.heathercrowe.ca/rbody320 | NL | — | — | malicious |
— | — | HEAD | 200 | 2.18.233.74:443 | https://armmf.adobe.com/arm-manifests/win/ReaderDCManifest.msi | unknown | — | — | whitelisted |
2652 | lipolo.exe | GET | — | 185.158.249.144:443 | https://fila.heathercrowe.ca/rbody320 | NL | — | — | malicious |
— | — | HEAD | 200 | 2.16.186.83:80 | http://ardownload.adobe.com/pub/adobe/reader/win/AcrobatDC/1502320070/AcroRdrDCUpd1502320070_MUI.msp | unknown | — | — | whitelisted |
— | — | GET | 206 | 2.16.186.83:80 | http://ardownload.adobe.com/pub/adobe/reader/win/AcrobatDC/1502320070/AcroRdrDCUpd1502320070_MUI.msp | unknown | txt | 10.6 Kb | whitelisted |
— | — | GET | 206 | 2.16.186.83:80 | http://ardownload.adobe.com/pub/adobe/reader/win/AcrobatDC/1502320070/AcroRdrDCUpd1502320070_MUI.msp | unknown | dbf | 10.6 Kb | whitelisted |
— | — | GET | 206 | 2.18.233.74:443 | https://armmf.adobe.com/arm-manifests/win/ReaderDCManifest.msi | unknown | binary | 4.70 Kb | whitelisted |
2524 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281.zip | unknown | — | — | whitelisted |
2524 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280.zip | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2652 | lipolo.exe | 185.158.249.144:443 | fila.heathercrowe.ca | easystores GmbH | NL | malicious |
1960 | RdrCEF.exe | 52.4.212.147:443 | cloud.acrobat.com | Amazon.com, Inc. | US | suspicious |
— | — | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 2.16.186.83:80 | ardownload.adobe.com | Akamai International B.V. | — | whitelisted |
2524 | AcroRd32.exe | 2.16.186.33:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fila.heathercrowe.ca |
| malicious |
cloud.acrobat.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ardownload.adobe.com |
| whitelisted |
Threats
Process | Message |
|---|---|
lipolo.exe | MP3 file corrupted |
lipolo.exe | WMA 0 |
lipolo.exe | OGG 0 |