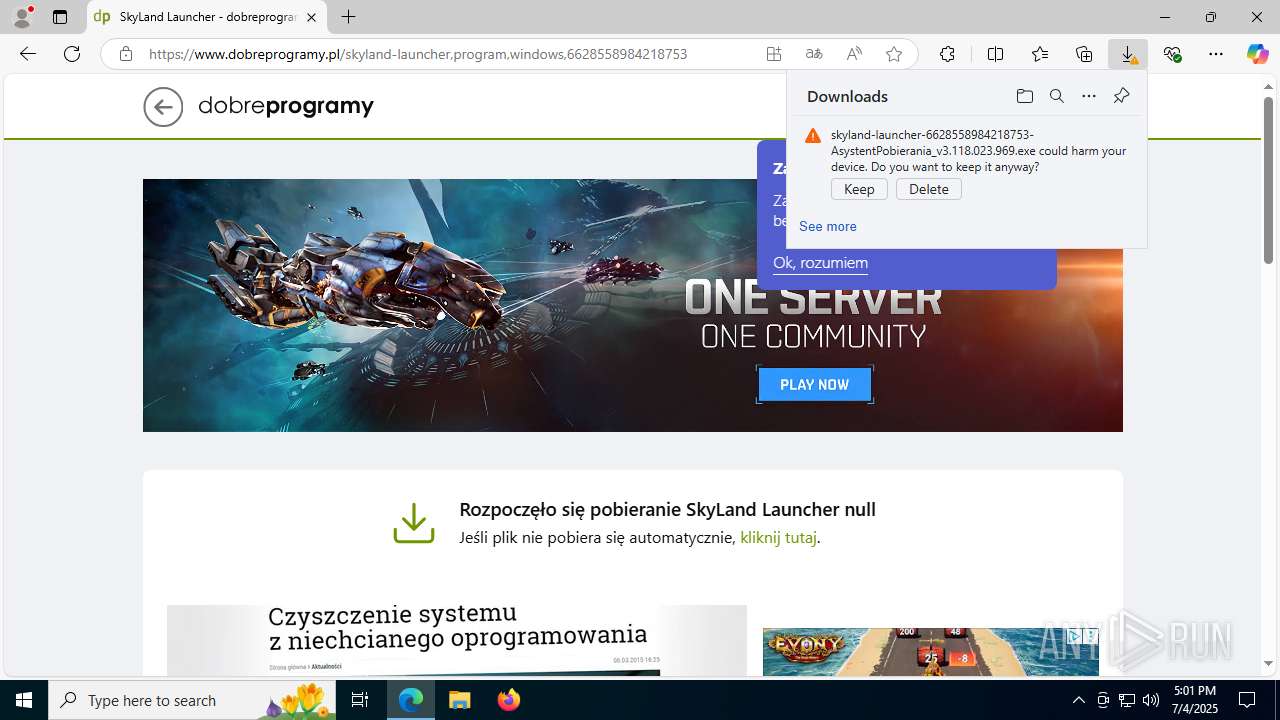
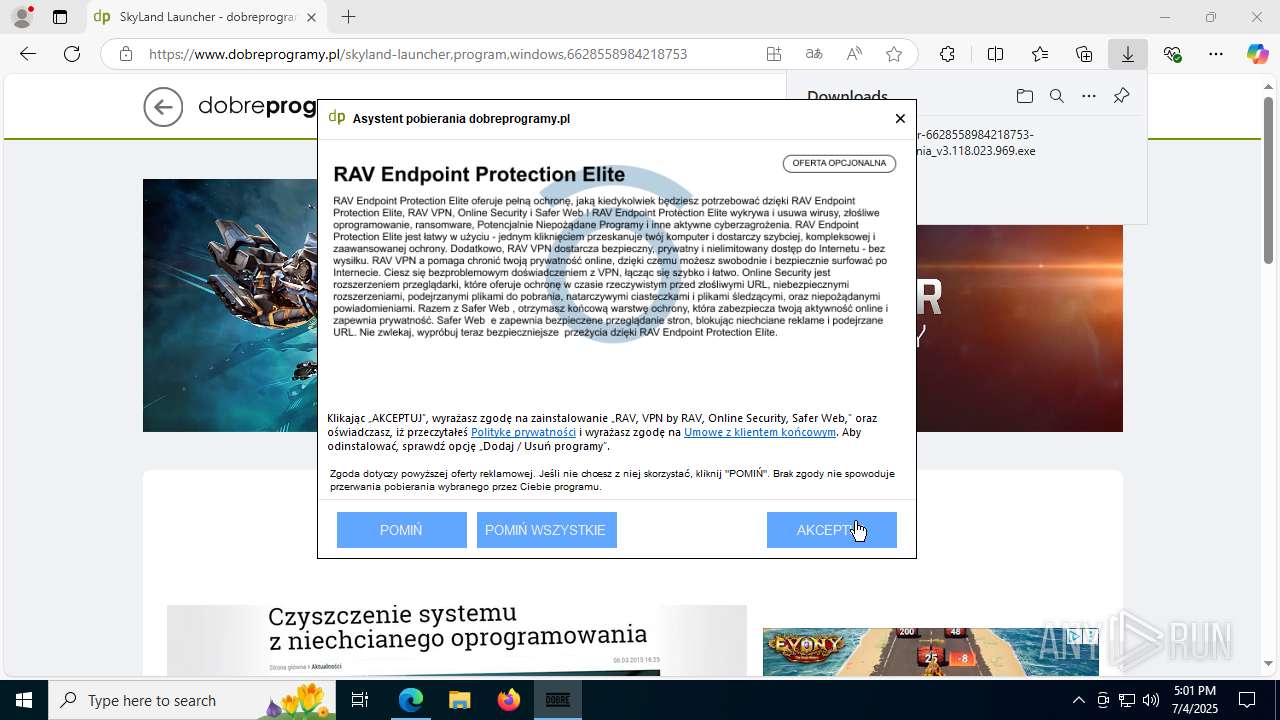
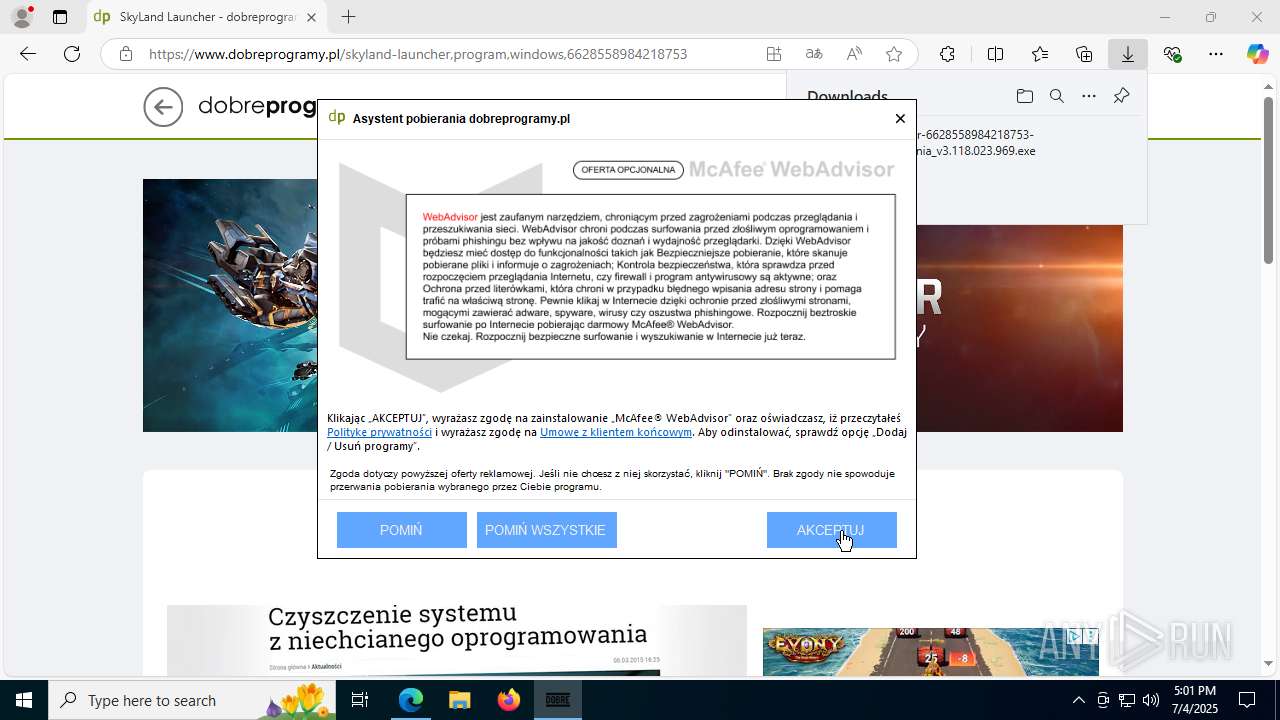
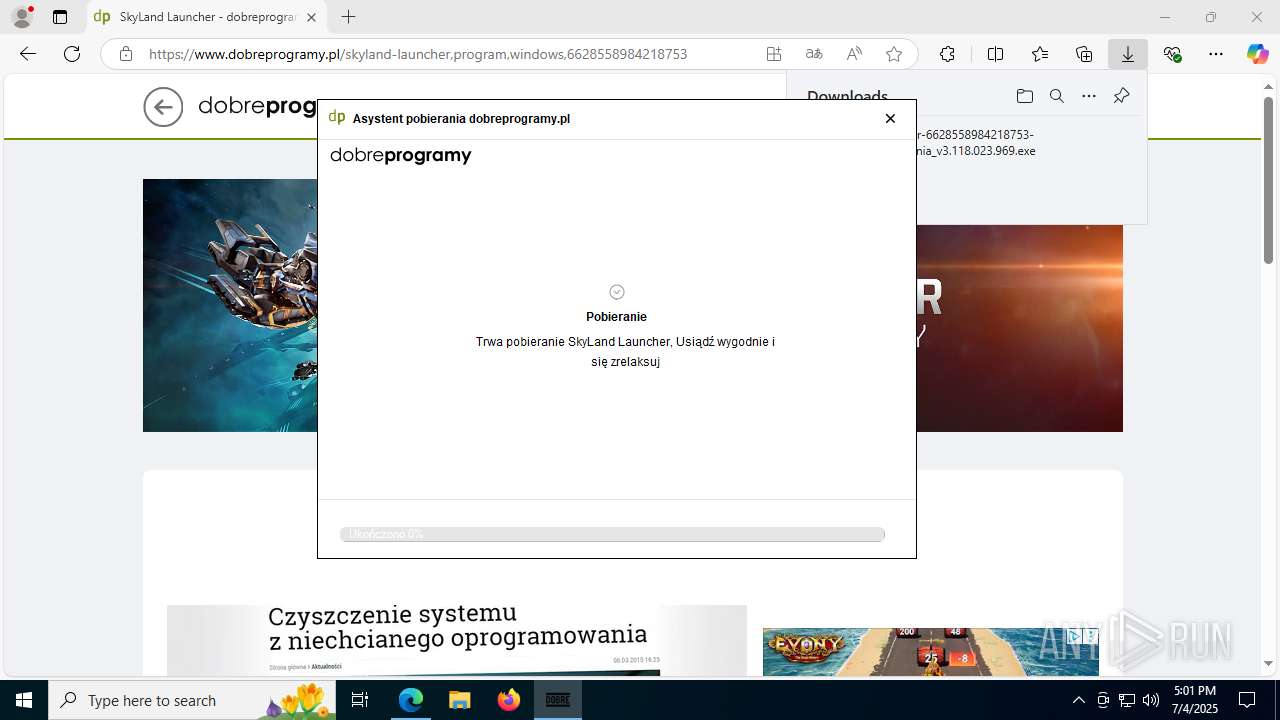
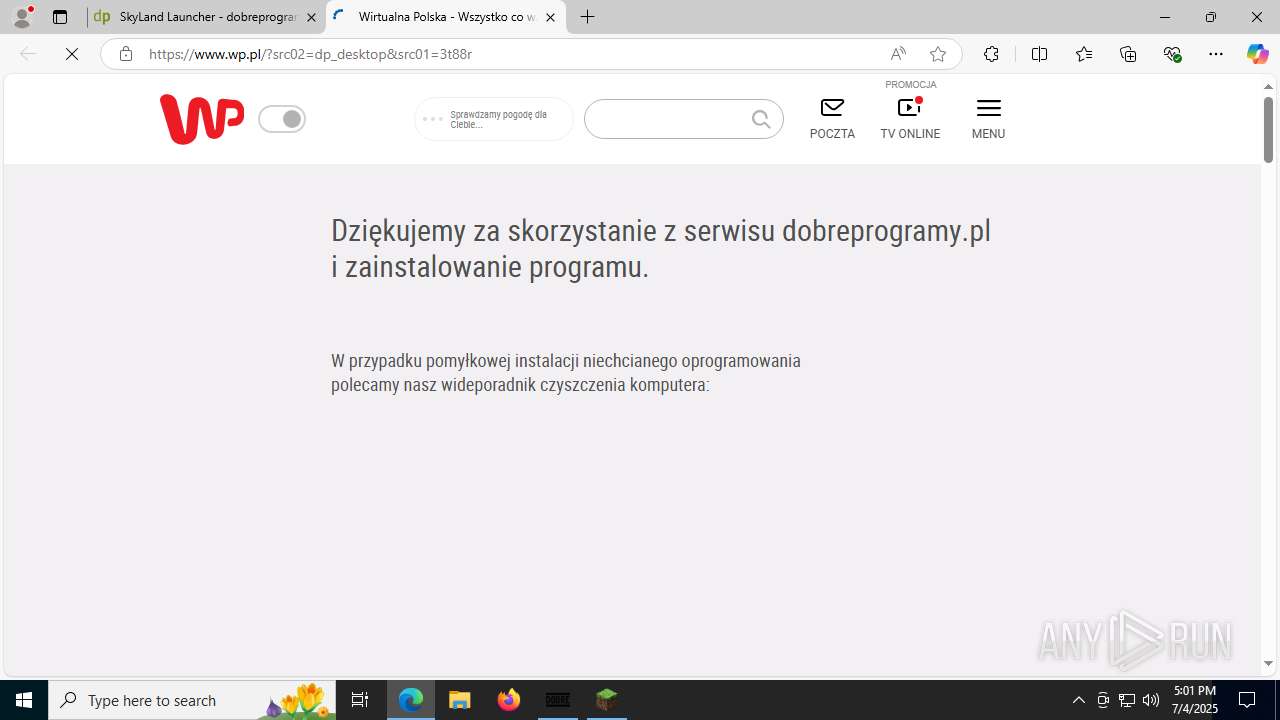
| URL: | https://www.dobreprogramy.pl/skyland-launcher,program,windows,6628558984218753 |
| Full analysis: | https://app.any.run/tasks/8c8b1790-725a-400b-98d7-0936e583dc0f |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2025, 17:01:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6AFFEA0570F843F58EE05E73E16FFF1A |
| SHA1: | 54D984D0B217B23D7BF67F9A95953BD54CBA0AA4 |
| SHA256: | C1BC224BA781CA87A8CF0C272648161FF76857798EACB600DC203FDCF515F18C |
| SSDEEP: | 3:N8DSLhRcLjKJcJ+ADKKJ/LgT6dxUFW:2OLbcLhZ9sFFW |
MALICIOUS
No malicious indicators.SUSPICIOUS
Adds/modifies Windows certificates
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- saBSI.exe (PID: 9864)
- UnifiedStub-installer.exe (PID: 10180)
- servicehost.exe (PID: 10268)
Reads security settings of Internet Explorer
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- saBSI.exe (PID: 9864)
- rsStubActivator.exe (PID: 9880)
- saBSI.exe (PID: 10040)
- installer.exe (PID: 2680)
- rsWSC.exe (PID: 4648)
- UnifiedStub-installer.exe (PID: 10180)
- rsEngineSvc.exe (PID: 1392)
- uihost.exe (PID: 10640)
Executable content was dropped or overwritten
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- rsStubActivator.exe (PID: 9880)
- yrsxtl2r.exe (PID: 10000)
- saBSI.exe (PID: 9864)
- UnifiedStub-installer.exe (PID: 10180)
- saBSI.exe (PID: 10040)
- installer.exe (PID: 9820)
- installer.exe (PID: 2680)
Process drops legitimate windows executable
- yrsxtl2r.exe (PID: 10000)
- UnifiedStub-installer.exe (PID: 10180)
- installer.exe (PID: 2680)
Reads the date of Windows installation
- rsStubActivator.exe (PID: 9880)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 10180)
- installer.exe (PID: 2680)
- servicehost.exe (PID: 10268)
Checks for Java to be installed
- SkyLand.exe (PID: 9224)
Searches for installed software
- UnifiedStub-installer.exe (PID: 10180)
The process verifies whether the antivirus software is installed
- installer.exe (PID: 9820)
- saBSI.exe (PID: 10040)
- installer.exe (PID: 2680)
- servicehost.exe (PID: 10268)
- uihost.exe (PID: 10640)
Executes as Windows Service
- rsSyncSvc.exe (PID: 8544)
- rsClientSvc.exe (PID: 2136)
- rsEngineSvc.exe (PID: 9000)
- rsWSC.exe (PID: 9388)
- servicehost.exe (PID: 10268)
Executes application which crashes
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
Creates/Modifies COM task schedule object
- installer.exe (PID: 2680)
The process creates files with name similar to system file names
- installer.exe (PID: 2680)
- UnifiedStub-installer.exe (PID: 10180)
The process drops C-runtime libraries
- UnifiedStub-installer.exe (PID: 10180)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 10180)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 10180)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 10180)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 10180)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 10180)
Reads Mozilla Firefox installation path
- servicehost.exe (PID: 10268)
- uihost.exe (PID: 10640)
INFO
Checks supported languages
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- identity_helper.exe (PID: 7944)
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 1760)
- rsStubActivator.exe (PID: 9880)
- saBSI.exe (PID: 9864)
- yrsxtl2r.exe (PID: 10000)
- UnifiedStub-installer.exe (PID: 10180)
- saBSI.exe (PID: 10040)
- javaw.exe (PID: 8048)
- SkyLand.exe (PID: 9224)
- rsSyncSvc.exe (PID: 9276)
- rsSyncSvc.exe (PID: 8544)
- installer.exe (PID: 9820)
- installer.exe (PID: 2680)
- rsWSC.exe (PID: 4648)
- rsClientSvc.exe (PID: 9032)
- rsClientSvc.exe (PID: 2136)
- rsEngineSvc.exe (PID: 1392)
- rsEngineSvc.exe (PID: 9000)
- rsWSC.exe (PID: 9388)
- servicehost.exe (PID: 10268)
- uihost.exe (PID: 10640)
Application launched itself
- msedge.exe (PID: 4788)
- msedge.exe (PID: 9356)
- msedge.exe (PID: 4156)
Reads Environment values
- identity_helper.exe (PID: 7944)
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 1760)
- rsStubActivator.exe (PID: 9880)
- UnifiedStub-installer.exe (PID: 10180)
- rsEngineSvc.exe (PID: 9000)
Reads the computer name
- identity_helper.exe (PID: 7944)
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 1760)
- saBSI.exe (PID: 9864)
- rsStubActivator.exe (PID: 9880)
- saBSI.exe (PID: 10040)
- UnifiedStub-installer.exe (PID: 10180)
- javaw.exe (PID: 8048)
- rsSyncSvc.exe (PID: 9276)
- rsSyncSvc.exe (PID: 8544)
- installer.exe (PID: 2680)
- rsWSC.exe (PID: 4648)
- rsWSC.exe (PID: 9388)
- rsClientSvc.exe (PID: 9032)
- rsClientSvc.exe (PID: 2136)
- rsEngineSvc.exe (PID: 1392)
- servicehost.exe (PID: 10268)
- uihost.exe (PID: 10640)
- rsEngineSvc.exe (PID: 9000)
Executable content was dropped or overwritten
- msedge.exe (PID: 4788)
- msedge.exe (PID: 6368)
Reads the machine GUID from the registry
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 1760)
- saBSI.exe (PID: 9864)
- rsStubActivator.exe (PID: 9880)
- saBSI.exe (PID: 10040)
- UnifiedStub-installer.exe (PID: 10180)
- javaw.exe (PID: 8048)
- installer.exe (PID: 2680)
- rsWSC.exe (PID: 4648)
- rsWSC.exe (PID: 9388)
- rsEngineSvc.exe (PID: 1392)
- servicehost.exe (PID: 10268)
- uihost.exe (PID: 10640)
- rsEngineSvc.exe (PID: 9000)
Disables trace logs
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- rsStubActivator.exe (PID: 9880)
- UnifiedStub-installer.exe (PID: 10180)
Checks proxy server information
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- rsStubActivator.exe (PID: 9880)
- saBSI.exe (PID: 9864)
- saBSI.exe (PID: 10040)
- UnifiedStub-installer.exe (PID: 10180)
- rsWSC.exe (PID: 4648)
- WerFault.exe (PID: 10056)
Reads the software policy settings
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- rsStubActivator.exe (PID: 9880)
- saBSI.exe (PID: 9864)
- saBSI.exe (PID: 10040)
- UnifiedStub-installer.exe (PID: 10180)
- installer.exe (PID: 2680)
- rsWSC.exe (PID: 4648)
- uihost.exe (PID: 10640)
- servicehost.exe (PID: 10268)
- WerFault.exe (PID: 10056)
Creates files or folders in the user directory
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- javaw.exe (PID: 8048)
- UnifiedStub-installer.exe (PID: 10180)
- rsWSC.exe (PID: 4648)
- WerFault.exe (PID: 10056)
Create files in a temporary directory
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- rsStubActivator.exe (PID: 9880)
- yrsxtl2r.exe (PID: 10000)
- javaw.exe (PID: 8048)
- saBSI.exe (PID: 10040)
- UnifiedStub-installer.exe (PID: 10180)
- installer.exe (PID: 2680)
The sample compiled with english language support
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
- rsStubActivator.exe (PID: 9880)
- yrsxtl2r.exe (PID: 10000)
- saBSI.exe (PID: 9864)
- installer.exe (PID: 9820)
- UnifiedStub-installer.exe (PID: 10180)
- installer.exe (PID: 2680)
Creates files in the program directory
- saBSI.exe (PID: 9864)
- javaw.exe (PID: 8048)
- UnifiedStub-installer.exe (PID: 10180)
- saBSI.exe (PID: 10040)
- installer.exe (PID: 9820)
- installer.exe (PID: 2680)
- rsWSC.exe (PID: 4648)
- rsEngineSvc.exe (PID: 1392)
- rsEngineSvc.exe (PID: 9000)
- servicehost.exe (PID: 10268)
- uihost.exe (PID: 10640)
.NET Reactor protector has been detected
- skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe (PID: 8248)
Process checks computer location settings
- rsStubActivator.exe (PID: 9880)
- servicehost.exe (PID: 10268)
Application based on Java
- javaw.exe (PID: 8048)
SQLite executable
- UnifiedStub-installer.exe (PID: 10180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
236
Monitored processes
92
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=39 --always-read-main-dll --field-trial-handle=10532,i,8582080788480303765,813646075689657545,262144 --variations-seed-version --mojo-platform-channel-handle=8620 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 892 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --always-read-main-dll --field-trial-handle=8220,i,8582080788480303765,813646075689657545,262144 --variations-seed-version --mojo-platform-channel-handle=8320 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\ReasonLabs\EPP\rsEngineSvc.exe" -i | C:\Program Files\ReasonLabs\EPP\rsEngineSvc.exe | UnifiedStub-installer.exe | ||||||||||||
User: admin Company: Reason Cybersecurity Ltd. Integrity Level: HIGH Description: rsEngineSvc Exit code: 0 Version: 4.0.0.0 Modules
| |||||||||||||||
| 1688 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3624,i,8582080788480303765,813646075689657545,262144 --variations-seed-version --mojo-platform-channel-handle=3636 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
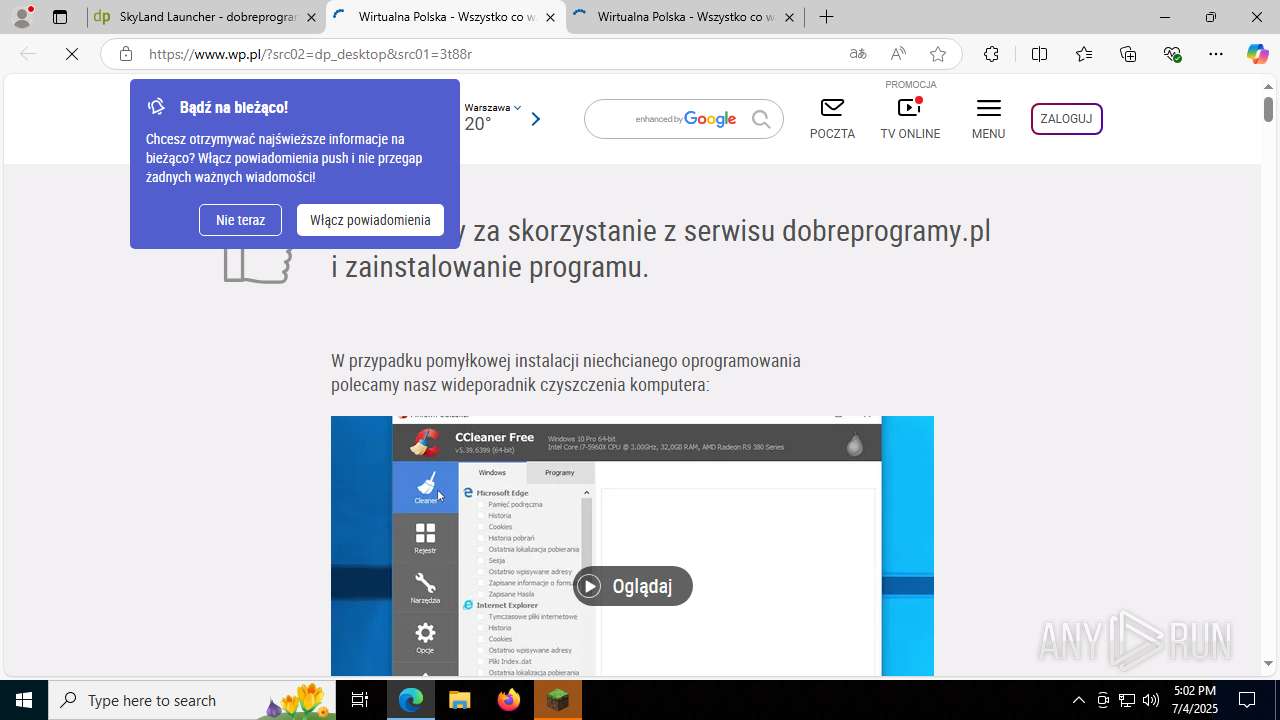
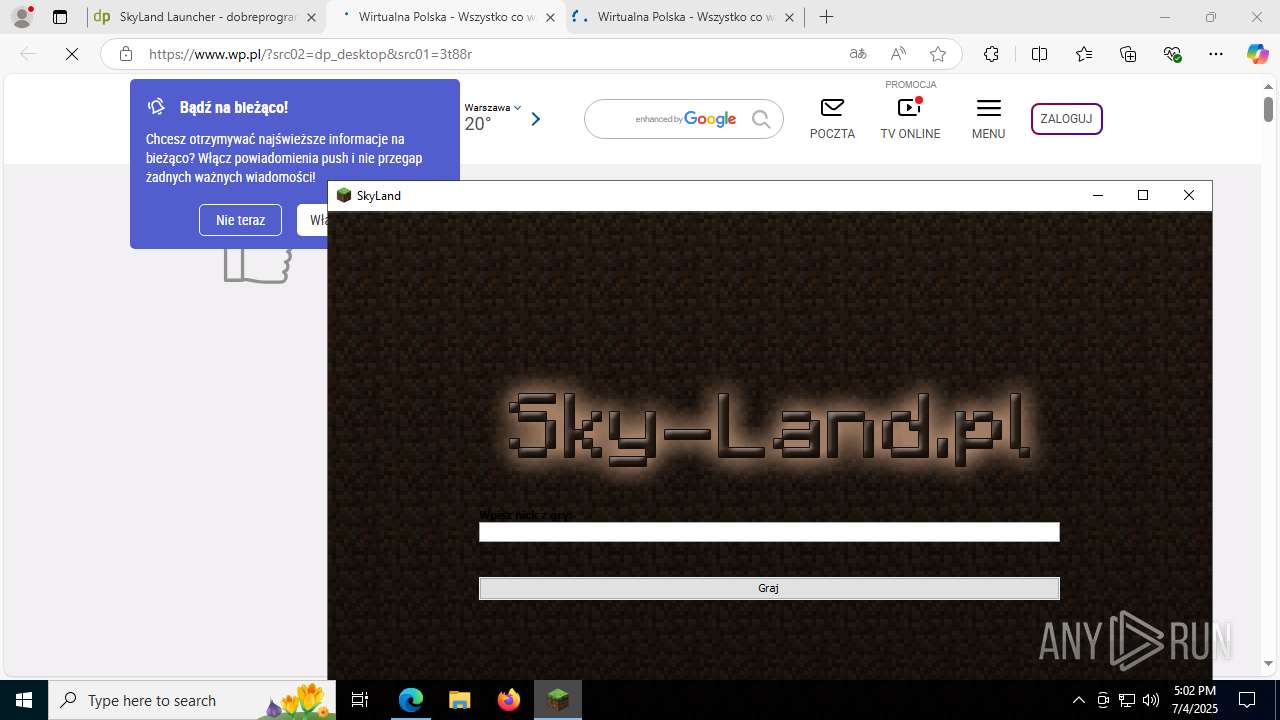
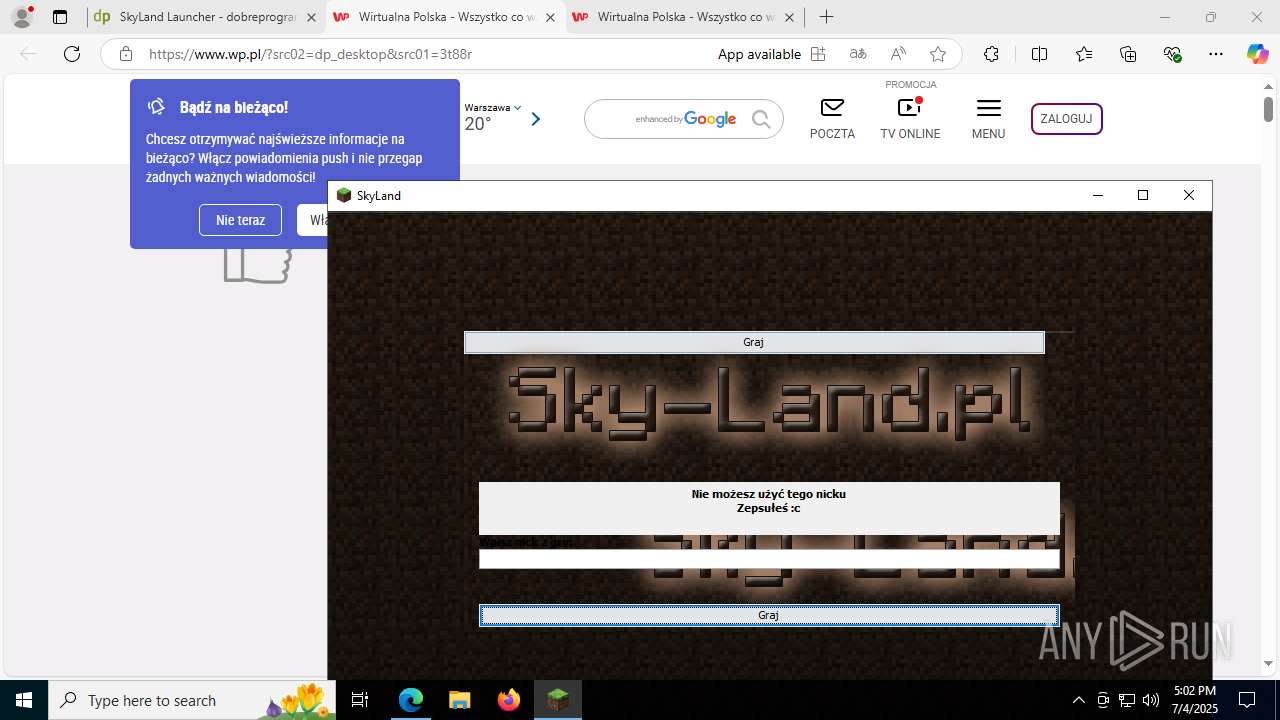
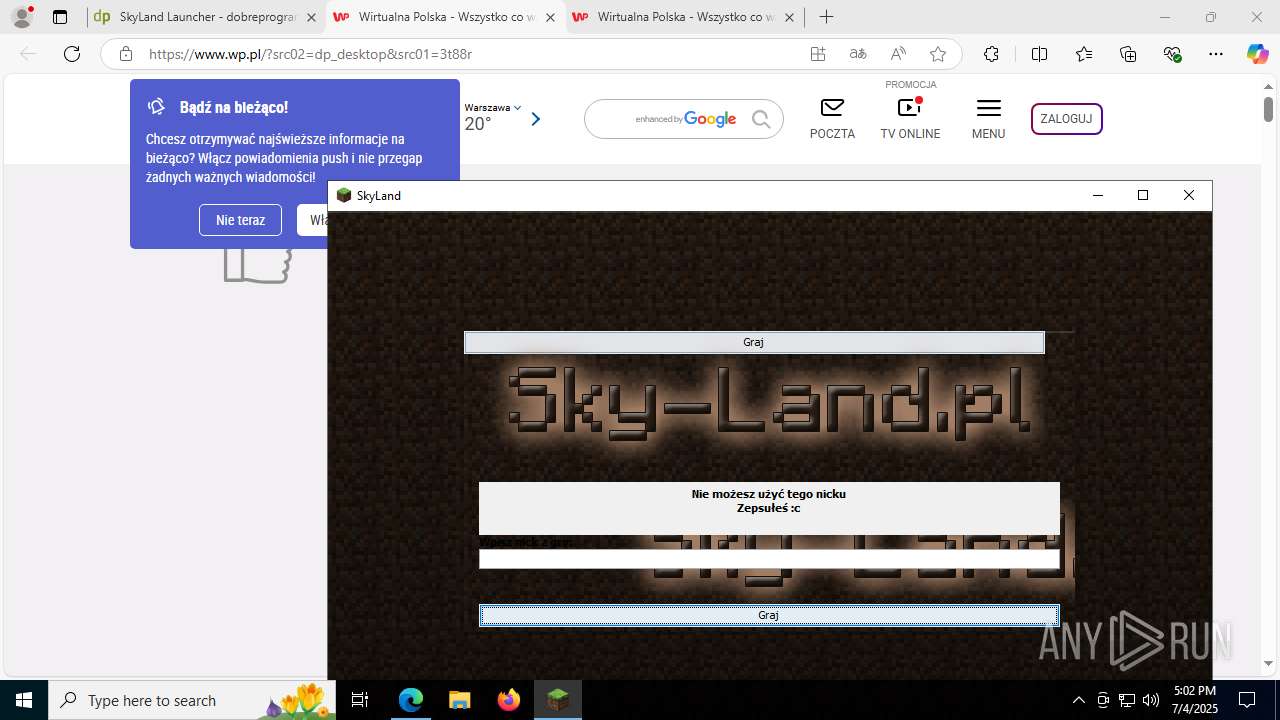
| 1760 | "C:\Users\admin\Downloads\skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe" | C:\Users\admin\Downloads\skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe | msedge.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Wirtualna Polska Media SA Exit code: 0 Version: 5.0.0.111 Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3652,i,8582080788480303765,813646075689657545,262144 --variations-seed-version --mojo-platform-channel-handle=3660 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\ReasonLabs\EPP\rsClientSvc.exe" | C:\Program Files\ReasonLabs\EPP\rsClientSvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: Reason Client Service Version: 6.2.5 Modules
| |||||||||||||||
| 2160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2128,i,8582080788480303765,813646075689657545,262144 --variations-seed-version --mojo-platform-channel-handle=2824 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2384,i,8582080788480303765,813646075689657545,262144 --variations-seed-version --mojo-platform-channel-handle=2380 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2320 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --edge-skip-compat-layer-relaunch --single-argument https://www.wp.pl/?src02=dp_desktop&src01=3t88r | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
50 076
Read events
49 643
Write events
377
Delete events
56
Modification events
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D72E3DBAB3972F00 | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721714 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6C2185D3-21AB-4449-B686-F926F7C0E50B} | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721714 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {EA0A75AA-949D-432F-AC0B-5FBDAA325474} | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721714 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {978C1703-10CF-44A8-A7C4-08D582F60185} | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721714 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {DE44DAE2-E270-4F46-90DA-0073E210FF4F} | |||
| (PID) Process: | (4788) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721714 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {81E9FEA1-A20A-4992-956C-1FAA2AA861A5} | |||
Executable files
503
Suspicious files
742
Text files
795
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF175709.TMP | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF175728.TMP | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF175747.TMP | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF175757.TMP | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF175767.TMP | — | |
MD5:— | SHA256:— | |||
| 4788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
431
DNS requests
577
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6368 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:GzUuue6dI50897j98g8AenwmjdpwgyD1h-N207RKj6Y&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6700 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8248 | skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
8248 | skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
8248 | skyland-launcher-6628558984218753-AsystentPobierania_v3.118.023.969.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVD%2BnGf79Hpedv3mhy6uKMVZkPCQQUDyrLIIcouOxvSK4rVKYpqhekzQwCEQCe8zMkTEPvBnz58daf%2FV5z | unknown | — | — | whitelisted |
9548 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
9548 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8048 | javaw.exe | GET | 200 | 164.132.161.204:80 | http://news.sky-land.pl/ | unknown | — | — | unknown |
8048 | javaw.exe | GET | 301 | 74.114.154.18:80 | http://mcupdate.tumblr.com/ | unknown | — | — | whitelisted |
8048 | javaw.exe | GET | 200 | 164.132.161.204:80 | http://news.sky-land.pl/logo.png | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6256 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6368 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6368 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6368 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6368 | msedge.exe | 2.16.241.224:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
6368 | msedge.exe | 212.77.98.131:443 | www.dobreprogramy.pl | Wirtualna Polska Media S.A. | PL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.dobreprogramy.pl |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.wp.pl |
| whitelisted |
v.wpimg.pl |
| whitelisted |
www.googletagservices.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8048 | javaw.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |
8048 | javaw.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |
Process | Message |
|---|---|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\_files\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\_files\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\_files\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\_files\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\_files\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\_files\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|