analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
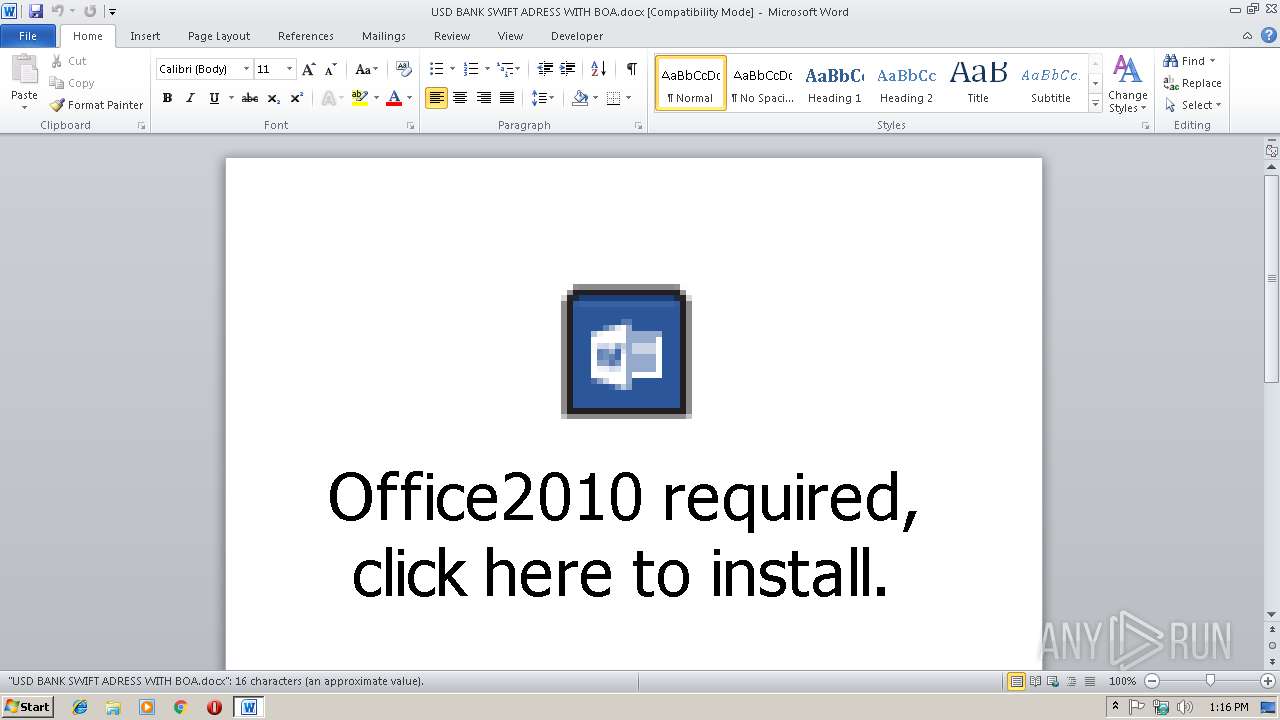
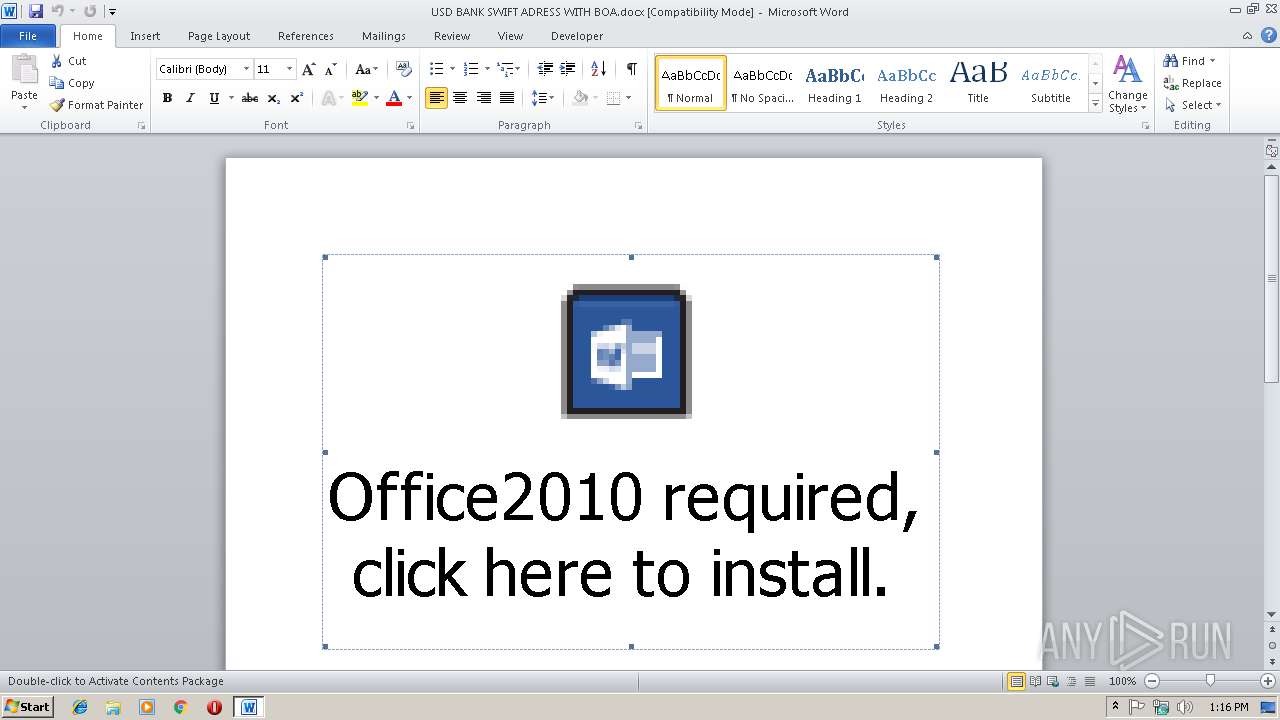
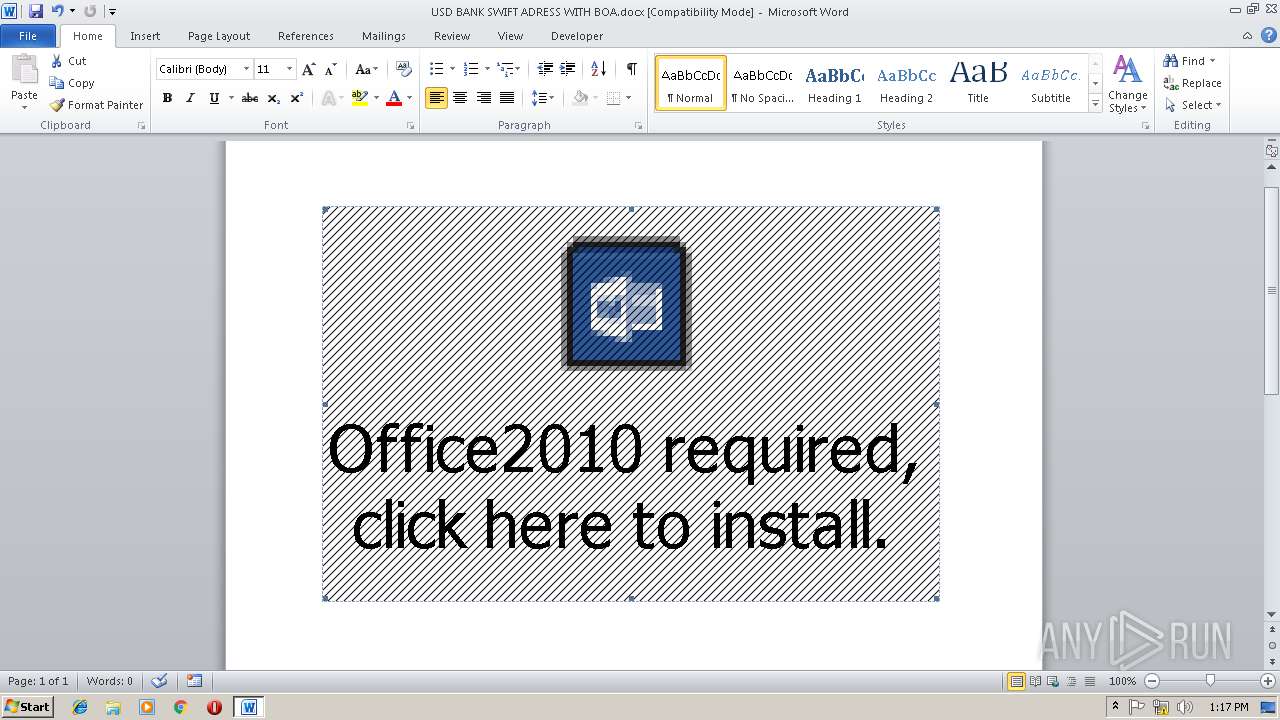
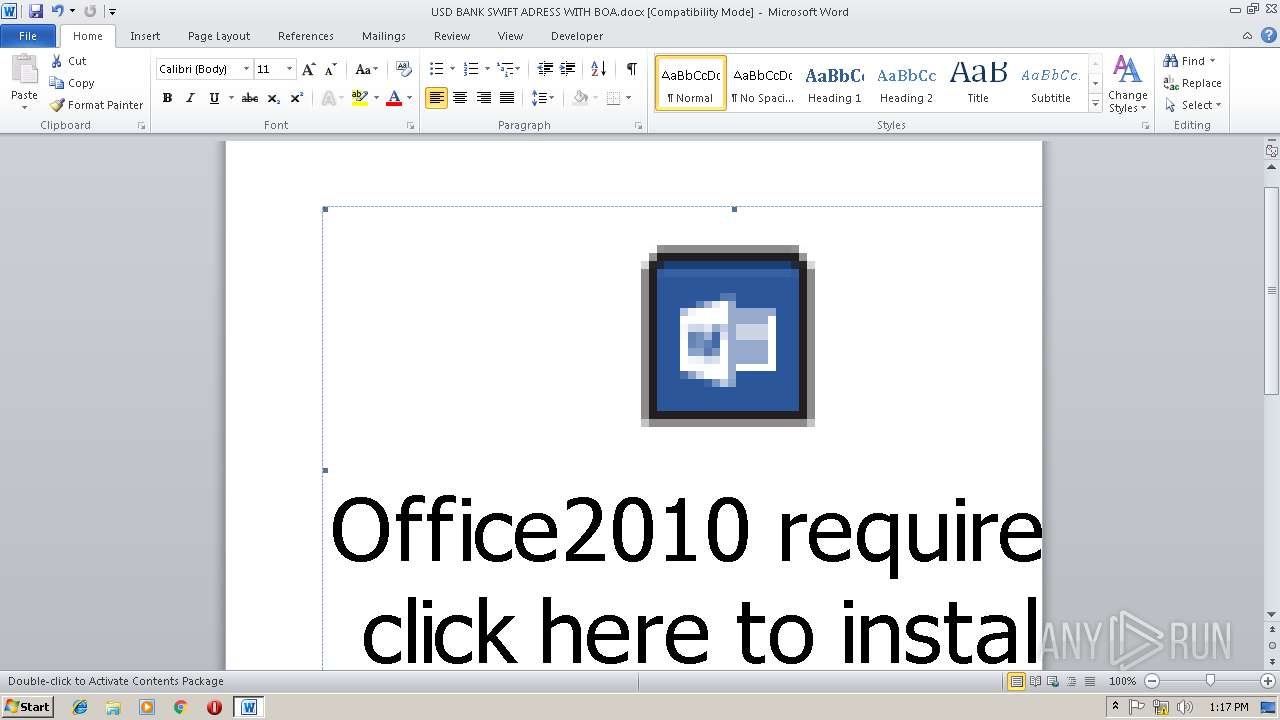
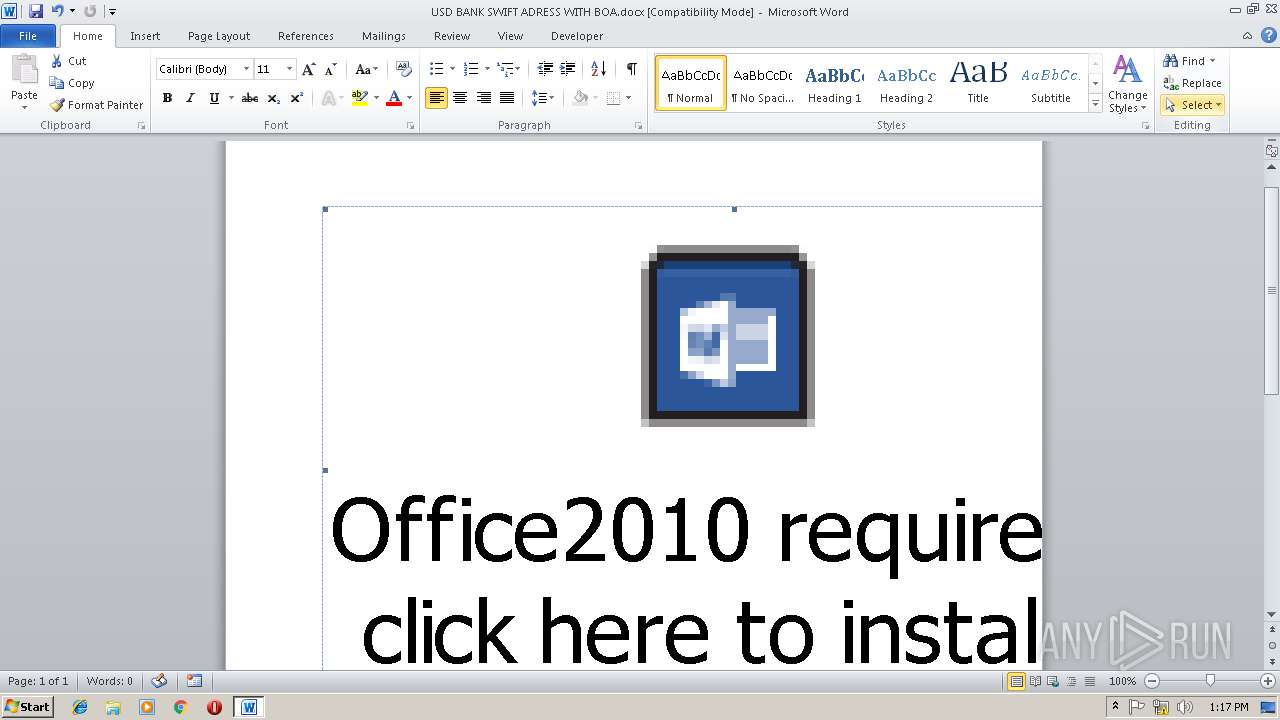
| File name: | USD BANK SWIFT ADRESS WITH BOA.docx |
| Full analysis: | https://app.any.run/tasks/3e630481-0df1-4f9d-a1d6-7084ee4137dc |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | November 15, 2018, 13:16:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 12DC8660E10EC3145FA07CF78452C958 |
| SHA1: | 1A15CEAE12287898701ECBEE6B9D7B7DB541A6AA |
| SHA256: | C197C72A7F29986AD48CD3B70C2CC9E12ABF1A639F5532085D9C9D0A33EBEFE4 |
| SSDEEP: | 6144:M03lRTD6bJ255/20iNFaxraRIEcdPq1m1besX4bIqZJRhQ1iPMUrh+haljyPU3EA:BDTDoa2wxeS4mKstcZQkz0hml3EA |
MALICIOUS
Application was dropped or rewritten from another process
- Microsoft Office Word 2010.exe (PID: 2332)
- Microsoft Office Word 2010.exe (PID: 4052)
- Microsoft Office Word 2010.exe (PID: 2244)
- Microsoft Office Word 2010.exe (PID: 2920)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3864)
- schtasks.exe (PID: 2792)
Known privilege escalation attack
- Microsoft Office Word 2010.exe (PID: 4052)
- Microsoft Office Word 2010.exe (PID: 2244)
Uses Task Scheduler to run other applications
- Microsoft Office Word 2010.exe (PID: 2332)
- Microsoft Office Word 2010.exe (PID: 2920)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3040)
AGENTTESLA was detected
- MSBuild.exe (PID: 452)
- MSBuild.exe (PID: 3428)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 452)
- MSBuild.exe (PID: 3428)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2316)
- Microsoft Office Word 2010.exe (PID: 2332)
- Microsoft Office Word 2010.exe (PID: 2920)
Creates files in the Windows directory
- Microsoft Office Word 2010.exe (PID: 2332)
Checks for external IP
- MSBuild.exe (PID: 452)
- MSBuild.exe (PID: 3428)
Modifies the open verb of a shell class
- Microsoft Office Word 2010.exe (PID: 2244)
- Microsoft Office Word 2010.exe (PID: 4052)
Loads DLL from Mozilla Firefox
- MSBuild.exe (PID: 452)
- MSBuild.exe (PID: 3428)
Connects to SMTP port
- MSBuild.exe (PID: 452)
- MSBuild.exe (PID: 3428)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3040)
Creates files in the user directory
- WINWORD.EXE (PID: 3040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
XML
| AppVersion: | 12 |
|---|---|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| CharactersWithSpaces: | 20 |
| LinksUpToDate: | No |
| Company: | - |
| ScaleCrop: | No |
| Paragraphs: | 1 |
| Lines: | 1 |
| DocSecurity: | None |
| Application: | Microsoft Office Word |
| Characters: | 18 |
| Words: | 3 |
| Pages: | 1 |
| TotalEditTime: | 2 minutes |
| Template: | Normal.dotm |
| ModifyDate: | 2018:11:15 04:17:00Z |
| CreateDate: | 2018:11:15 04:15:00Z |
| RevisionNumber: | 1 |
| LastModifiedBy: | USER |
XMP
| Creator: | USER |
|---|
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 1460 |
| ZipCompressedSize: | 386 |
| ZipCRC: | 0x7fcf3406 |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0006 |
| ZipRequiredVersion: | 20 |
Total processes
57
Monitored processes
15
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3040 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\USD BANK SWIFT ADRESS WITH BOA.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 | ||||
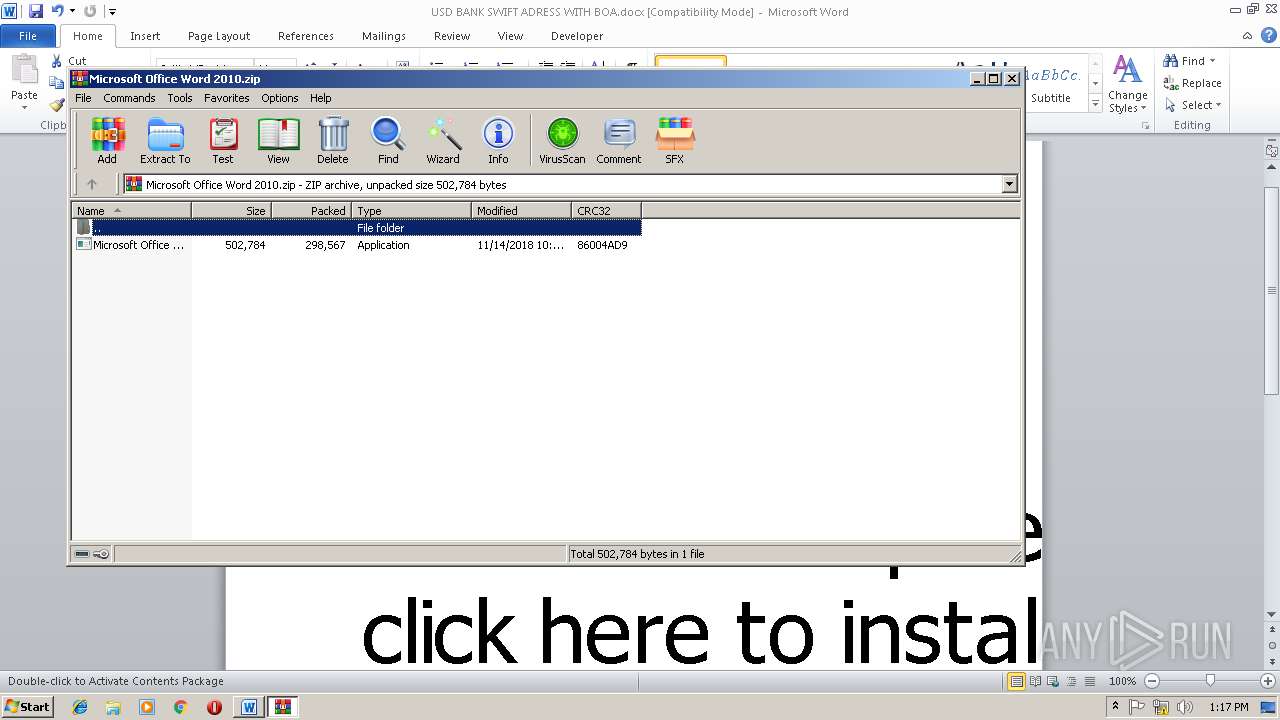
| 2316 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Microsoft Office Word 2010.zip" | C:\Program Files\WinRAR\WinRAR.exe | WINWORD.EXE | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 | ||||
| 2244 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2316.32620\Microsoft Office Word 2010.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2316.32620\Microsoft Office Word 2010.exe | — | WinRAR.exe |
User: admin Company: Adobe Solutions Integrity Level: MEDIUM Description: ExtenderScript Toolkit Exit code: 0 Version: 2.0.0.0 | ||||
| 2780 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Microsoft Office Word 2010.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | WINWORD.EXE |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 | ||||
| 2416 | "C:\Windows\System32\eventvwr.exe" | C:\Windows\System32\eventvwr.exe | — | Microsoft Office Word 2010.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Event Viewer Snapin Launcher Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3864 | "C:\Windows\System32\eventvwr.exe" | C:\Windows\System32\eventvwr.exe | Microsoft Office Word 2010.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Event Viewer Snapin Launcher Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2332 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2316.32620\Microsoft Office Word 2010.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2316.32620\Microsoft Office Word 2010.exe | eventvwr.exe | |
User: admin Company: Adobe Solutions Integrity Level: HIGH Description: ExtenderScript Toolkit Exit code: 0 Version: 2.0.0.0 | ||||
| 4052 | "C:\Users\admin\Desktop\Microsoft Office Word 2010.exe" | C:\Users\admin\Desktop\Microsoft Office Word 2010.exe | — | explorer.exe |
User: admin Company: Adobe Solutions Integrity Level: MEDIUM Description: ExtenderScript Toolkit Exit code: 0 Version: 2.0.0.0 | ||||
| 3864 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\DSiyRR" /XML "C:\Users\admin\AppData\Local\Temp\tmp218A.tmp" | C:\Windows\System32\schtasks.exe | — | Microsoft Office Word 2010.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 452 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\MSBuild.exe | Microsoft Office Word 2010.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 4294967295 Version: 2.0.50727.5420 built by: Win7SP1 | ||||
Total events
2 486
Read events
2 019
Write events
0
Delete events
0
Modification events
Executable files
4
Suspicious files
1
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9637.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$D BANK SWIFT ADRESS WITH BOA.docx | pgc | |
MD5:A418191B65717F930C09A21727D4D1A4 | SHA256:900E91D80F8FDFA1EFDFE435625EDCA8E30B2823CEC589E8464C433AD643E307 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:D1CDE0F58001C8533671964B1309424E | SHA256:09EDED9BC01BC3FEB59CBB8149843817FCD3BDDAA94B3596A9B87CAA4FF66F81 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\E45DB185.emf | emf | |
MD5:67A1632E377E7EBD698BD98FE3177712 | SHA256:2C1943F369C49CBD20BACEEDEC3DCAD7E9894F9EA08D782D659D3140A2361AC2 | |||
| 3040 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Microsoft Office Word 2010.zip | compressed | |
MD5:A0C26AD322890355B25029EBD1AE2C00 | SHA256:651CFE56BA454A94CD8A014A16231A67D18EA750928F19EC1A9A280A67C4395E | |||
| 2316 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft Office Word 2010.exe | executable | |
MD5:081485D72E742DBC78C0D4962D0E3C22 | SHA256:413295ABBD5D0B523CEFACEC92783DE513F1797BD80C354B7A303938D4151A09 | |||
| 2920 | Microsoft Office Word 2010.exe | C:\Users\admin\AppData\Local\Temp\tmpA9E4.tmp | xml | |
MD5:F94EFED2E5BBEB169EF6B1998C807CF3 | SHA256:36090ACB2356D01E2421E044D09FACFB657C4B690D447CB88F36FD7EB9B3F86E | |||
| 2316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2316.32620\Microsoft Office Word 2010.exe | executable | |
MD5:081485D72E742DBC78C0D4962D0E3C22 | SHA256:413295ABBD5D0B523CEFACEC92783DE513F1797BD80C354B7A303938D4151A09 | |||
| 2332 | Microsoft Office Word 2010.exe | C:\Windows\debug\WIA\DSiyRR.exe | executable | |
MD5:081485D72E742DBC78C0D4962D0E3C22 | SHA256:413295ABBD5D0B523CEFACEC92783DE513F1797BD80C354B7A303938D4151A09 | |||
| 2920 | Microsoft Office Word 2010.exe | C:\Windows\debug\WIA\DSiyRR.exe | executable | |
MD5:081485D72E742DBC78C0D4962D0E3C22 | SHA256:413295ABBD5D0B523CEFACEC92783DE513F1797BD80C354B7A303938D4151A09 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
452 | MSBuild.exe | GET | 200 | 162.88.100.200:80 | http://checkip.dyndns.org/ | US | html | 106 b | shared |
3428 | MSBuild.exe | GET | 200 | 162.88.100.200:80 | http://checkip.dyndns.org/ | US | html | 106 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
452 | MSBuild.exe | 192.185.129.64:587 | mail.signaturebrokers.in | CyrusOne LLC | US | malicious |
452 | MSBuild.exe | 162.88.100.200:80 | checkip.dyndns.org | Dynamic Network Services, Inc. | US | shared |
3428 | MSBuild.exe | 192.185.129.64:587 | mail.signaturebrokers.in | CyrusOne LLC | US | malicious |
3428 | MSBuild.exe | 162.88.100.200:80 | checkip.dyndns.org | Dynamic Network Services, Inc. | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
checkip.dyndns.org |
| shared |
mail.signaturebrokers.in |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
452 | MSBuild.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup - checkip.dyndns.org |
452 | MSBuild.exe | Potentially Bad Traffic | ET POLICY DynDNS CheckIp External IP Address Server Response |
452 | MSBuild.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
452 | MSBuild.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla Exfiltration via SMTP |
452 | MSBuild.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla.Spy Exfiltration Passwords via SMTP |
452 | MSBuild.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla Exfiltration via SMTP |
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
3428 | MSBuild.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup - checkip.dyndns.org |
3428 | MSBuild.exe | Potentially Bad Traffic | ET POLICY DynDNS CheckIp External IP Address Server Response |
4 ETPRO signatures available at the full report