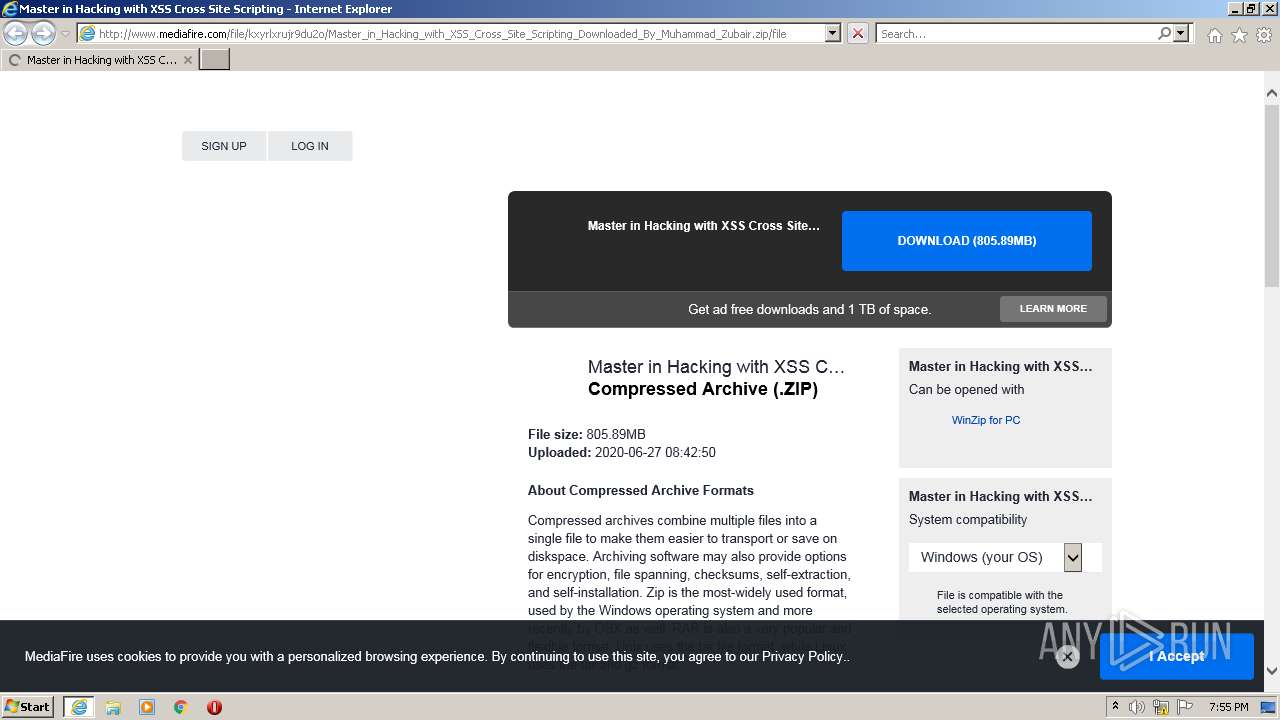
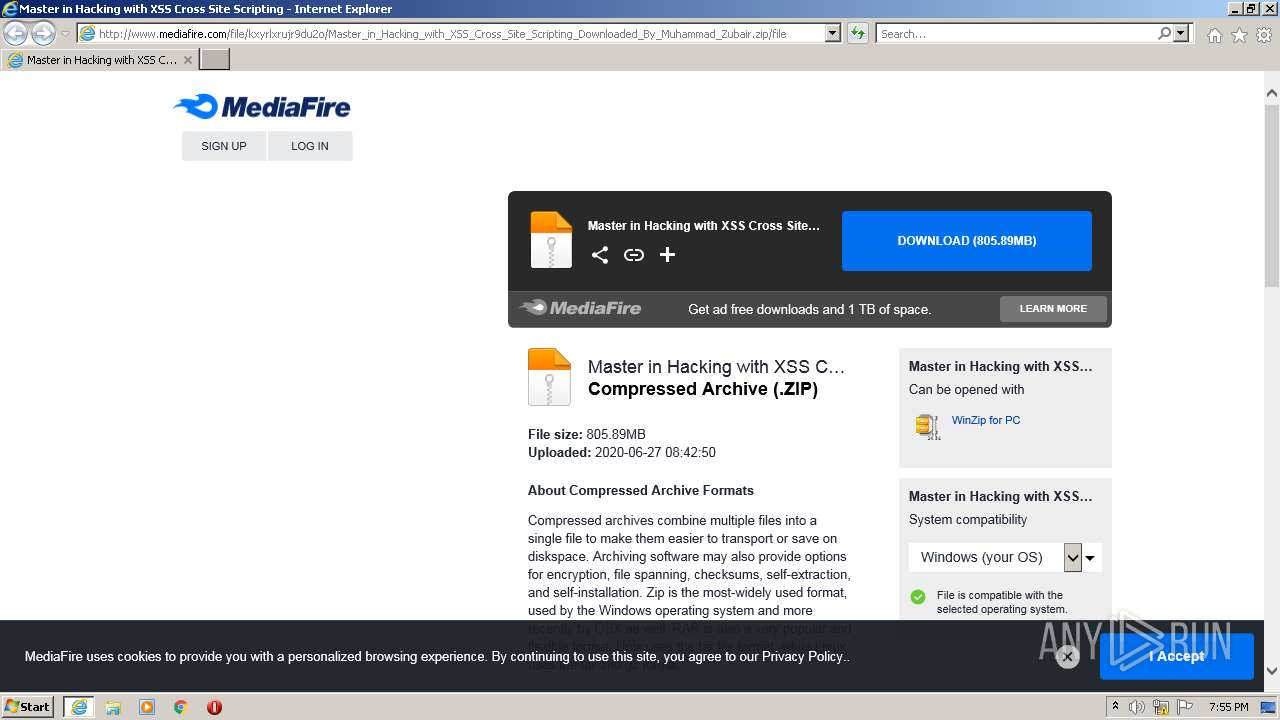
| URL: | http://www.mediafire.com/file/kxyrlxrujr9du2o/Master_in_Hacking_with_XSS_Cross_Site_Scripting_Downloaded_By_Muhammad_Zubair.zip/file |
| Full analysis: | https://app.any.run/tasks/0440ae4c-58c6-4171-bb30-39b972253a28 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 19:55:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | EA6F6A3080EEB488914807B2D6DFEC82 |
| SHA1: | 71E1BBACBD964F505FD50188ECE1C8DF54C87604 |
| SHA256: | C190FBECAEF081BD6768486E99C69D37EFE2583F6B1091162A7075FA6BE0744F |
| SSDEEP: | 3:N1KJS4w3eGUoPXJV8Bhmy5QgcuWdV66kz2BdDYEaHlIVY9:Cc4w3eGDJgP5idVzkzWFM7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3736)
INFO
Checks supported languages
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 3736)
Application launched itself
- iexplore.exe (PID: 2220)
Reads the computer name
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 3736)
Changes internet zones settings
- iexplore.exe (PID: 2220)
Reads settings of System Certificates
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 3736)
Reads internet explorer settings
- iexplore.exe (PID: 3736)
Creates files in the user directory
- iexplore.exe (PID: 3736)
Checks Windows Trust Settings
- iexplore.exe (PID: 3736)
- iexplore.exe (PID: 2220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2220 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://www.mediafire.com/file/kxyrlxrujr9du2o/Master_in_Hacking_with_XSS_Cross_Site_Scripting_Downloaded_By_Muhammad_Zubair.zip/file" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3736 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2220 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
20 989
Read events
20 884
Write events
105
Delete events
0
Modification events
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937436 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937436 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
12
Text files
21
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3736 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\52MGEK67.txt | text | |
MD5:— | SHA256:— | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8VO4EV34.txt | text | |
MD5:— | SHA256:— | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_F105773D1FB0AC7088EC8BBEDEF850B8 | der | |
MD5:— | SHA256:— | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\dl_promo_logo[1].png | image | |
MD5:6C600D768576CAC11D18FBFCACE25277 | SHA256:174D0CE23DDAA3923575AF7A8E047E1DBF75199EBEE7DF1ACA5E5713C4A1DD62 | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\file[1].htm | html | |
MD5:— | SHA256:— | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\mf_logo_full_color[1].svg | image | |
MD5:B3BB5BF9102F80054D199F293046DB84 | SHA256:8539C91AE0A82F8CAB27D481EA38AC4E66D1E5B36701FE295BCBA4399B9255BD | |||
| 3736 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\tag[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
59
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3736 | iexplore.exe | GET | 301 | 142.250.185.78:80 | http://translate.google.com/translate_a/element.js?cb=googFooterTranslate | US | — | — | whitelisted |
3736 | iexplore.exe | GET | — | 104.16.202.237:80 | http://static.mediafire.com/images/backgrounds/download/social/fb_16x16.png | US | — | — | shared |
3736 | iexplore.exe | GET | 200 | 104.16.203.237:80 | http://www.mediafire.com/file/kxyrlxrujr9du2o/Master_in_Hacking_with_XSS_Cross_Site_Scripting_Downloaded_By_Muhammad_Zubair.zip/file | US | html | 83.1 Kb | shared |
2220 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3736 | iexplore.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3736 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAEC9RywYwyihLibdTfI1sk%3D | US | der | 280 b | whitelisted |
3736 | iexplore.exe | GET | 200 | 104.16.202.237:80 | http://static.mediafire.com/images/backgrounds/download/dl_promo_logo.png | US | image | 2.19 Kb | shared |
3736 | iexplore.exe | GET | 200 | 104.16.202.237:80 | http://static.mediafire.com/images/filetype/file-zip-v3.png | US | image | 1.83 Kb | shared |
3736 | iexplore.exe | GET | 200 | 104.16.202.237:80 | http://static.mediafire.com/images/backgrounds/header/mf_logo_full_color.svg | US | image | 1.51 Kb | shared |
3736 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?96aecf7cc0c275e5 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.2:53 | — | — | — | whitelisted |
3736 | iexplore.exe | 104.16.203.237:80 | www.mediafire.com | Cloudflare Inc | US | unknown |
3736 | iexplore.exe | 104.16.94.65:443 | static.cloudflareinsights.com | Cloudflare Inc | US | shared |
3736 | iexplore.exe | 142.250.185.78:443 | translate.google.com | Google Inc. | US | whitelisted |
3736 | iexplore.exe | 142.250.185.78:80 | translate.google.com | Google Inc. | US | whitelisted |
3736 | iexplore.exe | 18.66.242.149:443 | cdn.amplitude.com | Massachusetts Institute of Technology | US | unknown |
3736 | iexplore.exe | 104.16.202.237:80 | www.mediafire.com | Cloudflare Inc | US | unknown |
2220 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3736 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3736 | iexplore.exe | 8.248.119.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
www.mediafire.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
btloader.com |
| whitelisted |
translate.google.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
cdn.amplitude.com |
| whitelisted |