| File name: | HawkTuah.exe |
| Full analysis: | https://app.any.run/tasks/bf109f5c-b231-4772-a437-6fb2792e0349 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 00:15:44 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | A90F95FB8C9452A830AD00907B32A4FA |
| SHA1: | 733F2ABE52BF11AC8C67BD46884696FEC2E108F9 |
| SHA256: | C17EA114B183F3B03F174005581738E012078374118C289FF754FBB3E55CB3BE |
| SSDEEP: | 98304:5cBPGrlVqmhLirnac+wyKhHpgFs/DrVCKCaBIzxcg7KIA8pnN+cBIKJACH09Br+N:v+ZW/WnAz9dJGVXNEJG7fVRIpye |
MALICIOUS
JEEFO has been detected
- HawkTuah.exe (PID: 7988)
- icsys.icn.exe (PID: 4180)
- explorer.exe (PID: 6476)
- svchost.exe (PID: 4040)
Changes the autorun value in the registry
- explorer.exe (PID: 6476)
- svchost.exe (PID: 4040)
SUSPICIOUS
Executable content was dropped or overwritten
- HawkTuah.exe (PID: 7988)
- explorer.exe (PID: 6476)
- spoolsv.exe (PID: 7312)
- icsys.icn.exe (PID: 4180)
Starts application with an unusual extension
- HawkTuah.exe (PID: 7988)
Starts CMD.EXE for commands execution
- hawktuah.exe (PID: 8016)
- cmd.exe (PID: 7388)
Application launched itself
- cmd.exe (PID: 7388)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4756)
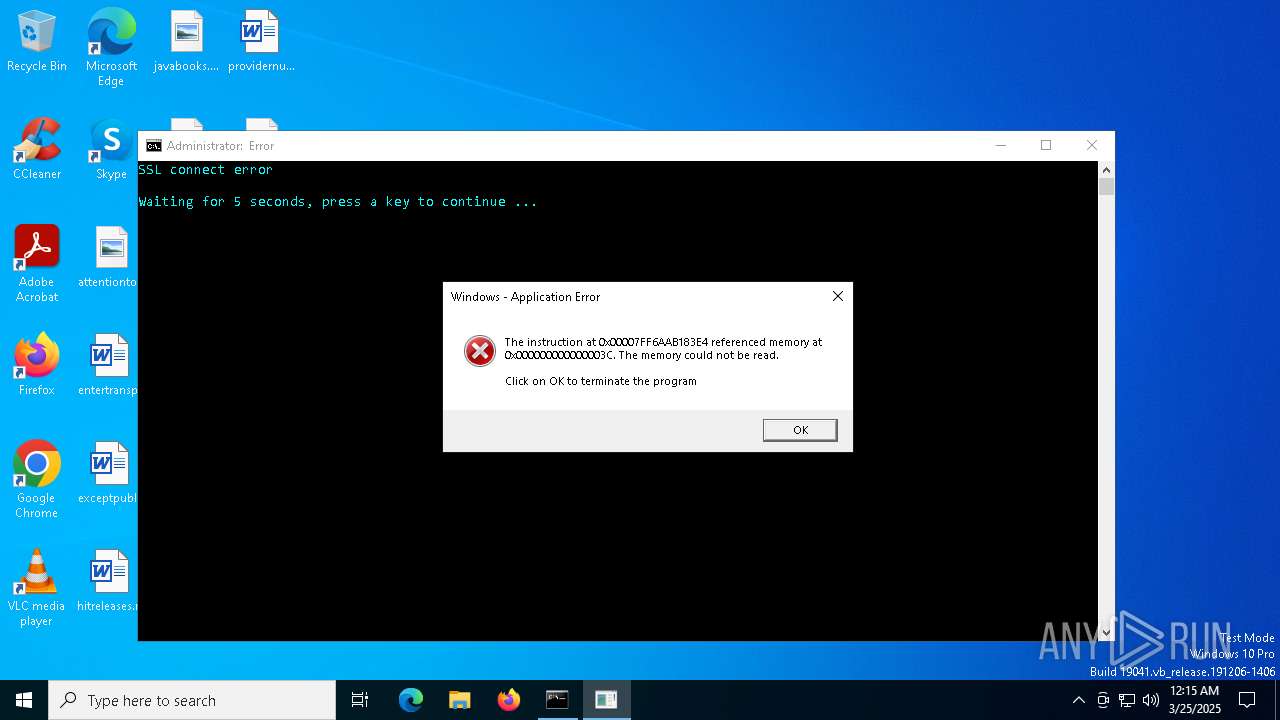
Executes application which crashes
- hawktuah.exe (PID: 8016)
Starts itself from another location
- HawkTuah.exe (PID: 7988)
- explorer.exe (PID: 6476)
- spoolsv.exe (PID: 7312)
- icsys.icn.exe (PID: 4180)
- svchost.exe (PID: 4040)
The process creates files with name similar to system file names
- spoolsv.exe (PID: 7312)
- icsys.icn.exe (PID: 4180)
Creates or modifies Windows services
- svchost.exe (PID: 4040)
INFO
Checks supported languages
- hawktuah.exe (PID: 8016)
- HawkTuah.exe (PID: 7988)
- icsys.icn.exe (PID: 4180)
- spoolsv.exe (PID: 7312)
- svchost.exe (PID: 4040)
- explorer.exe (PID: 6476)
- spoolsv.exe (PID: 5772)
Reads the computer name
- hawktuah.exe (PID: 8016)
- svchost.exe (PID: 4040)
- HawkTuah.exe (PID: 7988)
The sample compiled with english language support
- HawkTuah.exe (PID: 7988)
Create files in a temporary directory
- HawkTuah.exe (PID: 7988)
- icsys.icn.exe (PID: 4180)
- explorer.exe (PID: 6476)
- svchost.exe (PID: 4040)
- spoolsv.exe (PID: 7312)
- spoolsv.exe (PID: 5772)
Checks proxy server information
- slui.exe (PID: 7012)
Reads the software policy settings
- slui.exe (PID: 7012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
139
Monitored processes
17
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | c:\windows\resources\svchost.exe | C:\Windows\Resources\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 4180 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | HawkTuah.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 4756 | cmd /C "color b && title Error && echo SSL connect error && timeout /t 5" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5304 | C:\WINDOWS\system32\WerFault.exe -u -p 8016 -s 932 | C:\Windows\System32\WerFault.exe | — | hawktuah.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 2147942405 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5772 | c:\windows\resources\spoolsv.exe PR | C:\Windows\Resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 6476 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | icsys.icn.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 6620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7012 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 388
Read events
4 369
Write events
15
Delete events
4
Modification events
| (PID) Process: | (7988) HawkTuah.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (4180) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (4040) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (4040) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (4040) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (4040) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (6476) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (6476) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (6476) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (6476) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
Executable files
5
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4180 | icsys.icn.exe | C:\Windows\Resources\Themes\explorer.exe | executable | |
MD5:4E719298848C9776185A59D311C27EC6 | SHA256:79A844FE3E1D09EB017CD1C194EE91D4C9CC26E20AC5B2134D5F5BBFCF020FE3 | |||
| 7988 | HawkTuah.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:B4AF7F5E9AD36AA61F1166A20037E2B7 | SHA256:68ADFD92C8972A2DF57EA51812C1E8D4E42CFAD860C4DBBC2F1E1F6D72688996 | |||
| 7988 | HawkTuah.exe | C:\Users\admin\AppData\Local\Temp\~DF0F725530613FDF95.TMP | binary | |
MD5:4316AEED0F45FDF7C513EDF14A8E4189 | SHA256:2746C7DC32F55F864836159EC6880056D6E1A69DFBB328EFAE3A7C671B1D724A | |||
| 4180 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DF5489C17A21503B76.TMP | binary | |
MD5:7692356A16D50EC7D8F6E586C0E487CF | SHA256:146E326B5CA54600E81C97B21938A8F6E51EBC0326871AF4E976BD0C260DED6D | |||
| 6476 | explorer.exe | C:\Windows\Resources\spoolsv.exe | executable | |
MD5:C8D065A658EC61F515B2C2A7CC374AA5 | SHA256:ACC436CFC9C4027FCC20DB89DB7BE508A39E3BB6F1E6899AF04C350911B1DDDE | |||
| 7988 | HawkTuah.exe | C:\Users\admin\Desktop\hawktuah.exe | executable | |
MD5:BDCC8462FEE79FF2F4C57A3EE9C6C962 | SHA256:F71C2795AA99D923FA970B2DEC7C11B1E7A7787130179CD7F4C9EA0C905F6E4A | |||
| 7312 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF8E383C6B6B955DDA.TMP | binary | |
MD5:6A41BF22E9E10C1930FC910C9DF00A31 | SHA256:AA014607B1B12BD2218A098D3712C2EBD3D55A8B6C97BC032DD67532EC3ED4C2 | |||
| 7312 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:C4440993CA81057CCCC16B67F4CBE316 | SHA256:F2C07F0FB4227C0E937FE07EE30105E7CBB58466B0EF4F9B692487D0AC6E79A7 | |||
| 5772 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF61574B37A59E07E6.TMP | binary | |
MD5:E11D579C042E5D0A2A0B6BDE6FD863F1 | SHA256:04192E50C124335279AF2B938FB95E9B40514B7202A10D156E8EC5F9ABBF4CC4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
21
DNS requests
6
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
8016 | hawktuah.exe | 104.26.1.5:443 | keyauth.win | CLOUDFLARENET | US | unknown |
7560 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7012 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
google.com |
| unknown |
keyauth.win |
| unknown |
activation-v2.sls.microsoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain in DNS Lookup (keyauth .win) |
8016 | hawktuah.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |