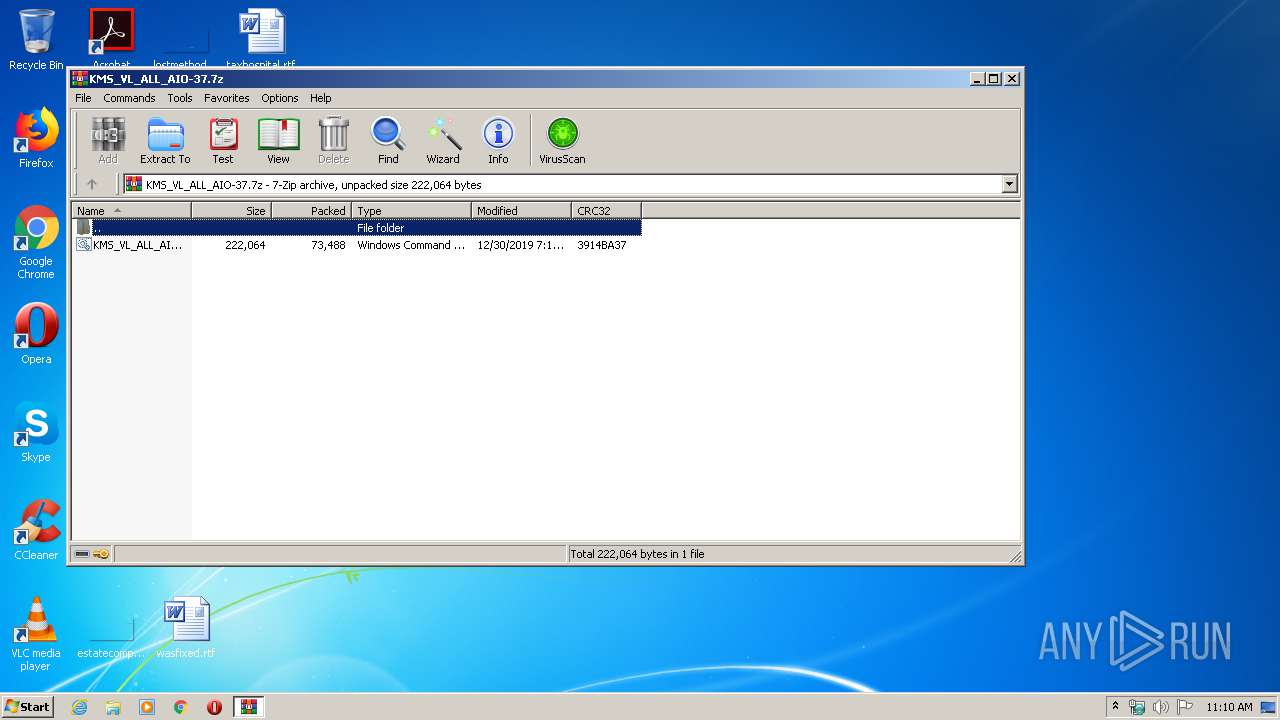
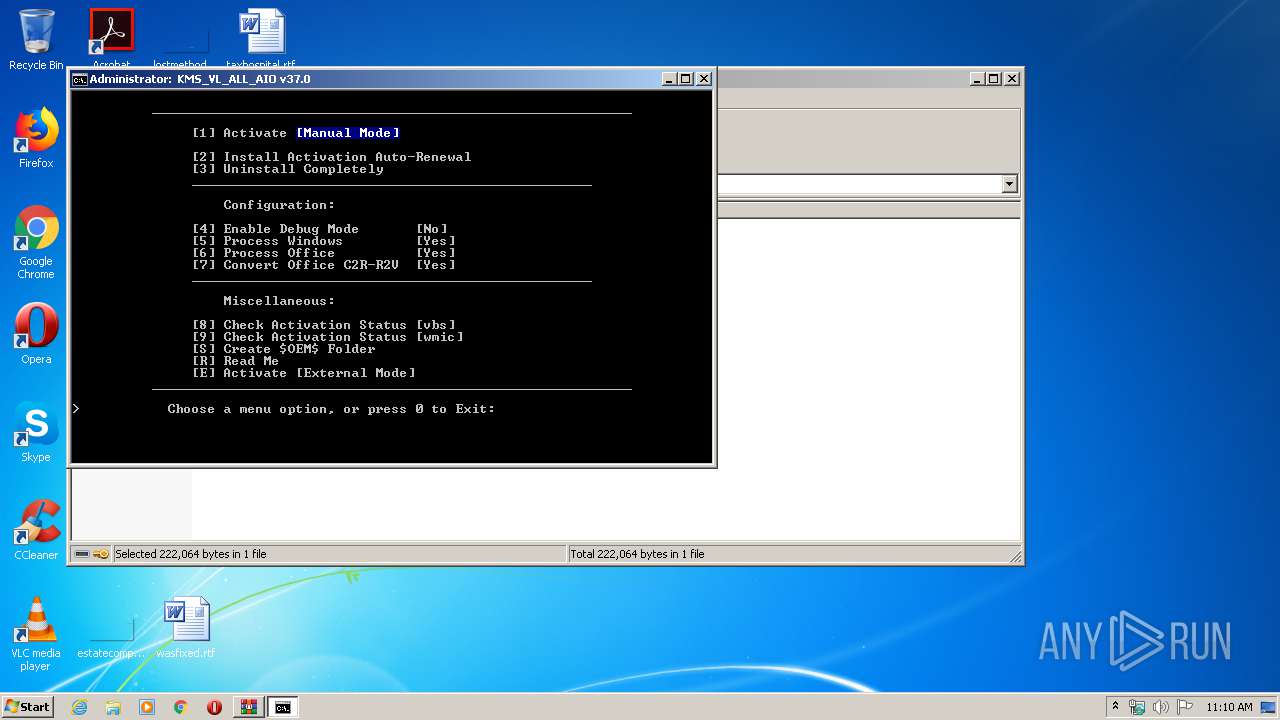
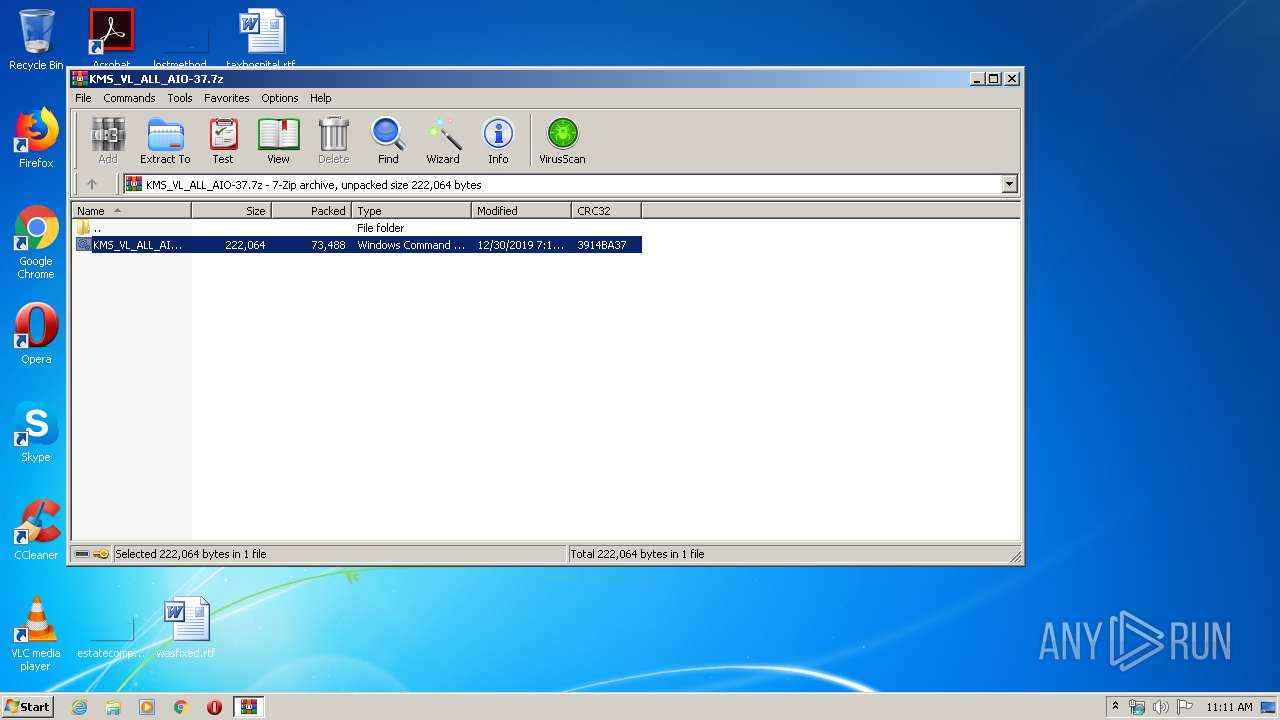
| File name: | KMS_VL_ALL_AIO-37.7z |
| Full analysis: | https://app.any.run/tasks/8835dd04-9cd7-4d8e-adca-e778bf9c03f8 |
| Verdict: | Malicious activity |
| Analysis date: | February 05, 2020, 11:10:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 242254A93493D5A4E62FF2A5B4CC66E6 |
| SHA1: | 9271A629F461331FB3020568FC05C7298E03ACD0 |
| SHA256: | C17C382C99BD7EF78E98518126CF68F63E81B2B3B9AA3AD9FC31BB7500B68678 |
| SSDEEP: | 1536:zFu5LKufxlbdymJwFHEfslCEqcCktrCPhnQIdep1WPYnh:zFu9zfxZjwFBCExptInQIdep1GW |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 956)
Starts Visual C# compiler
- powershell.exe (PID: 256)
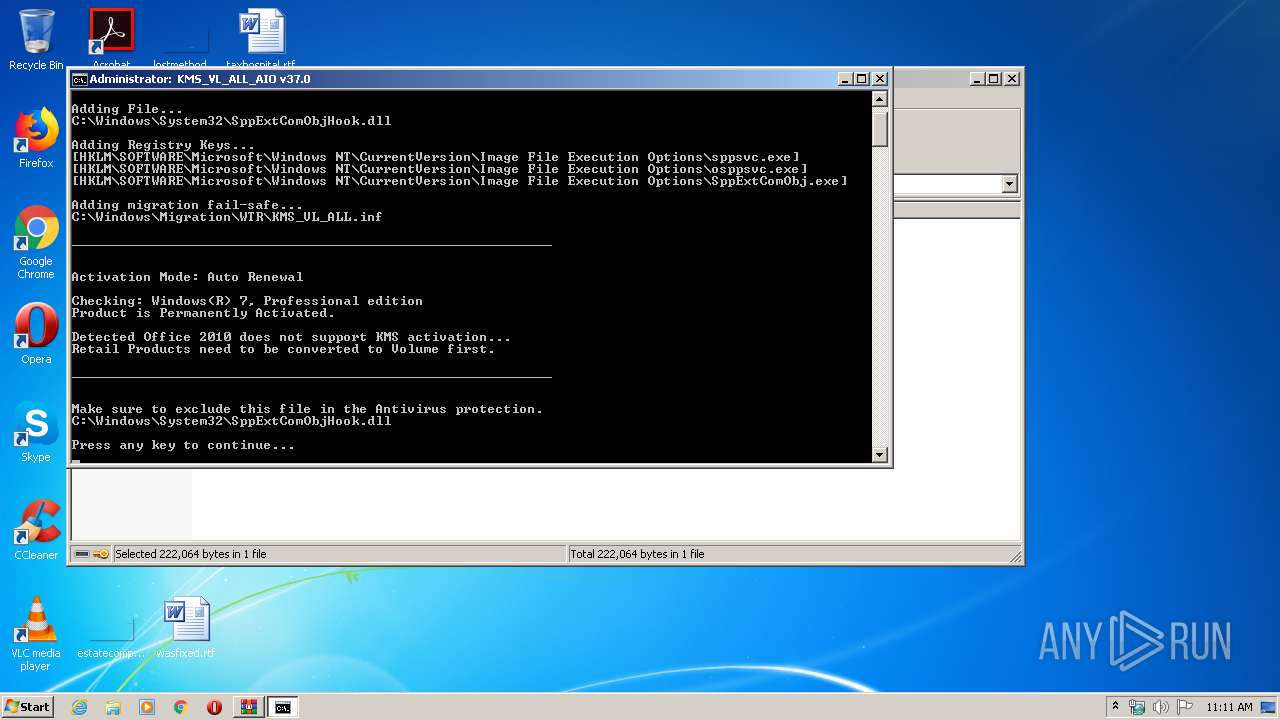
Loads the Task Scheduler COM API
- OSPPSVC.EXE (PID: 3716)
- sppsvc.exe (PID: 2544)
- sppsvc.exe (PID: 2628)
Starts NET.EXE for service management
- cmd.exe (PID: 956)
Loads dropped or rewritten executable
- OSPPSVC.EXE (PID: 3716)
- sppsvc.exe (PID: 2544)
- sppsvc.exe (PID: 2628)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cscript.exe (PID: 1792)
- WinRAR.exe (PID: 2524)
- cmd.exe (PID: 956)
Uses RUNDLL32.EXE to load library
- cscript.exe (PID: 1792)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 956)
- cmd.exe (PID: 2412)
- cmd.exe (PID: 348)
- cmd.exe (PID: 2568)
- cmd.exe (PID: 1604)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 2880)
- cmd.exe (PID: 2988)
- cmd.exe (PID: 3980)
- cmd.exe (PID: 4052)
Executes scripts
- cmd.exe (PID: 2412)
Application launched itself
- cmd.exe (PID: 956)
Starts SC.EXE for service management
- cmd.exe (PID: 956)
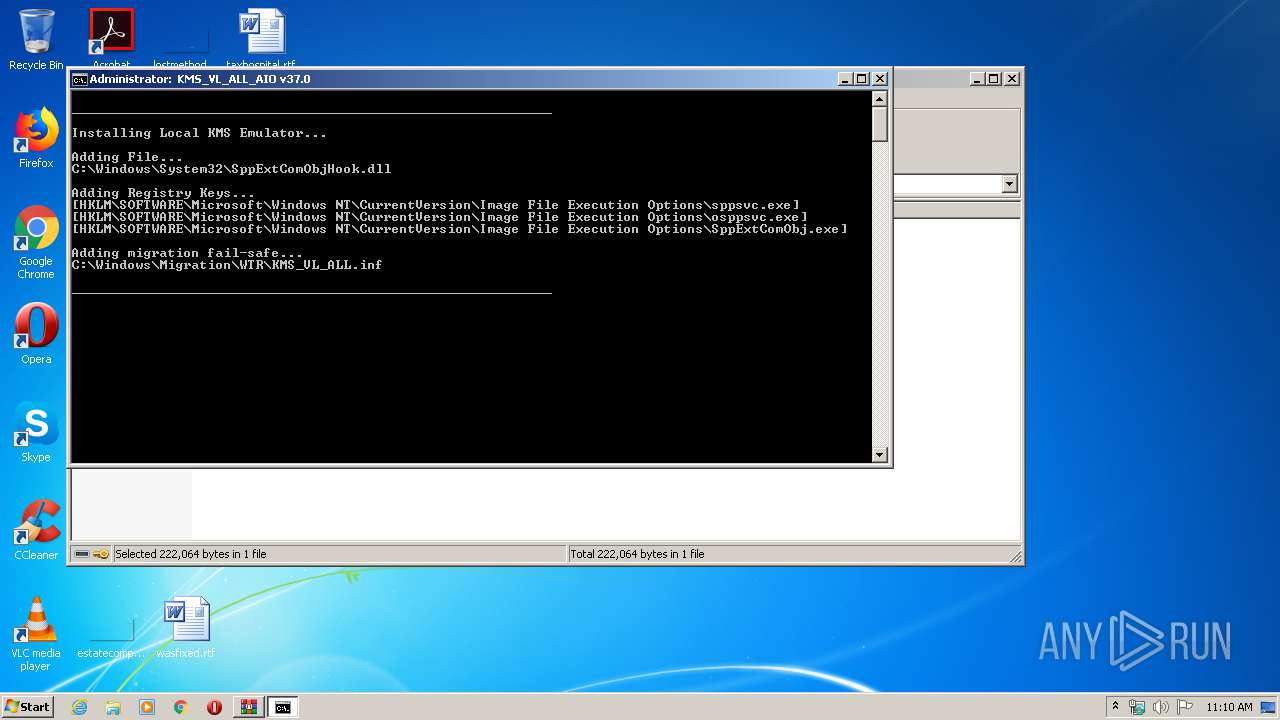
Creates files in the Windows directory
- cmd.exe (PID: 956)
- powershell.exe (PID: 256)
Starts CHOICE.EXE (used to create a delay)
- cmd.exe (PID: 956)
Creates files in the user directory
- powershell.exe (PID: 3436)
- powershell.exe (PID: 256)
- powershell.exe (PID: 3684)
Executable content was dropped or overwritten
- powershell.exe (PID: 256)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 956)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 1748)
Removes files from Windows directory
- cmd.exe (PID: 956)
INFO
Dropped object may contain Bitcoin addresses
- sppsvc.exe (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
180
Monitored processes
141
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
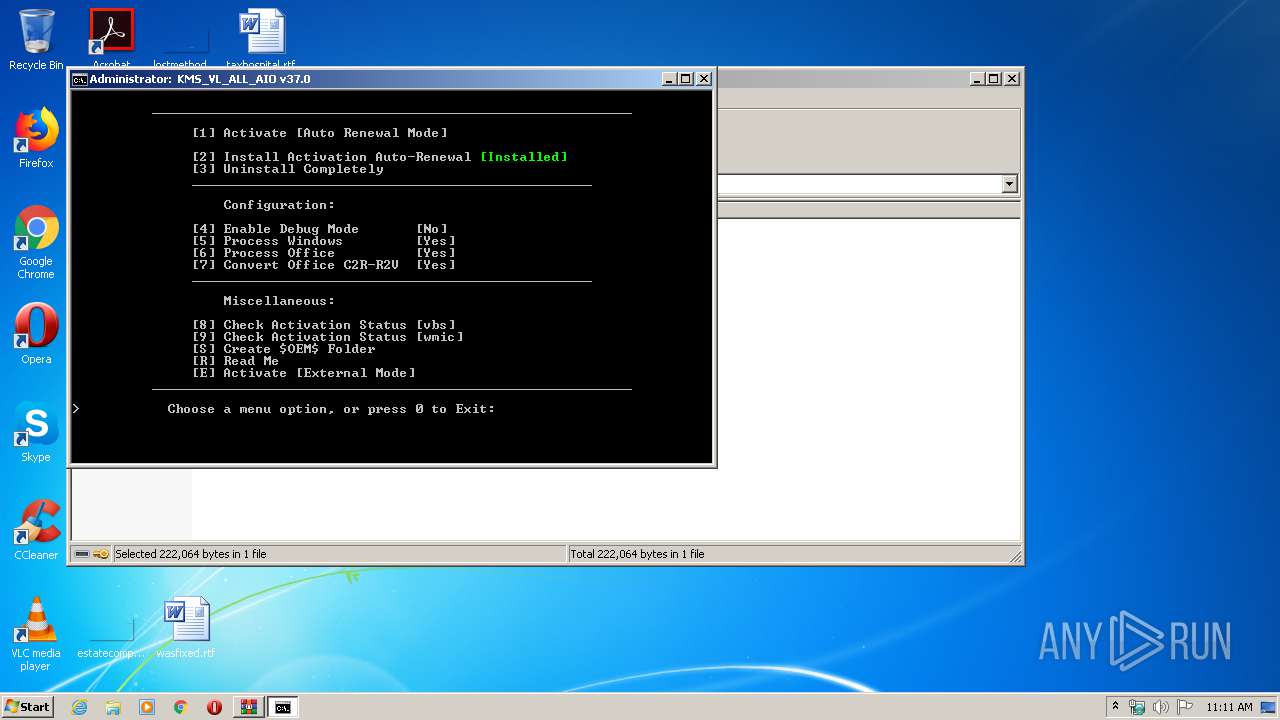
| 256 | powershell -nop -ep bypass -c "$f=[io.file]::ReadAllText('C:\Users\admin\AppData\Local\Temp\Rar$DIb2524.4243\KMS_VL_ALL_AIO.cmd') -split ':x86dll\:.*';iex ($f[1]);X 1;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 348 | C:\Windows\system32\cmd.exe /c reg query "HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /v Desktop | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 404 | find /i "STOPPED" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 404 | wmic path SoftwareLicensingProduct where ID='b92e9980-b9d5-4821-9c94-140f632f6312' get LicenseStatus | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 536 | wmic path SoftwareLicensingProduct where (ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f' and Description like '%KMSCLIENT%' and PartialProductKey is not NULL) get Name | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | sc query osppsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | findstr /i "b92e9980-b9d5-4821-9c94-140f632f6312" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 772 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 872 | reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f /v Debugger | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 872 | find /i "Office 14" "C:\Windows\Temp\sppchk.txt" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 652
Read events
1 431
Write events
221
Delete events
0
Modification events
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMS_VL_ALL_AIO-37.7z | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2524) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6003 |
Value: Windows Command Script | |||
Executable files
1
Suspicious files
10
Text files
8
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3436 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\19J84OA4Y6MVA8X6EYX5.temp | — | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\V0S6L8UI9DBL1DRBEFC0.temp | — | |
MD5:— | SHA256:— | |||
| 3332 | csc.exe | C:\Users\admin\AppData\Local\Temp\iroct2qk.dll | — | |
MD5:— | SHA256:— | |||
| 3332 | csc.exe | C:\Users\admin\AppData\Local\Temp\iroct2qk.out | — | |
MD5:— | SHA256:— | |||
| 3684 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\P427TGUN4CWFNJ9QVGGR.temp | — | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\AppData\Local\Temp\iroct2qk.cmdline | text | |
MD5:— | SHA256:— | |||
| 3436 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2628 | sppsvc.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Roaming\Microsoft\SoftwareProtectionPlatform\Cache\cache.dat | binary | |
MD5:— | SHA256:— | |||
| 3332 | csc.exe | C:\Users\admin\AppData\Local\Temp\iroct2qk.pdb | pdb | |
MD5:— | SHA256:— | |||
| 3684 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFa6d22d.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|