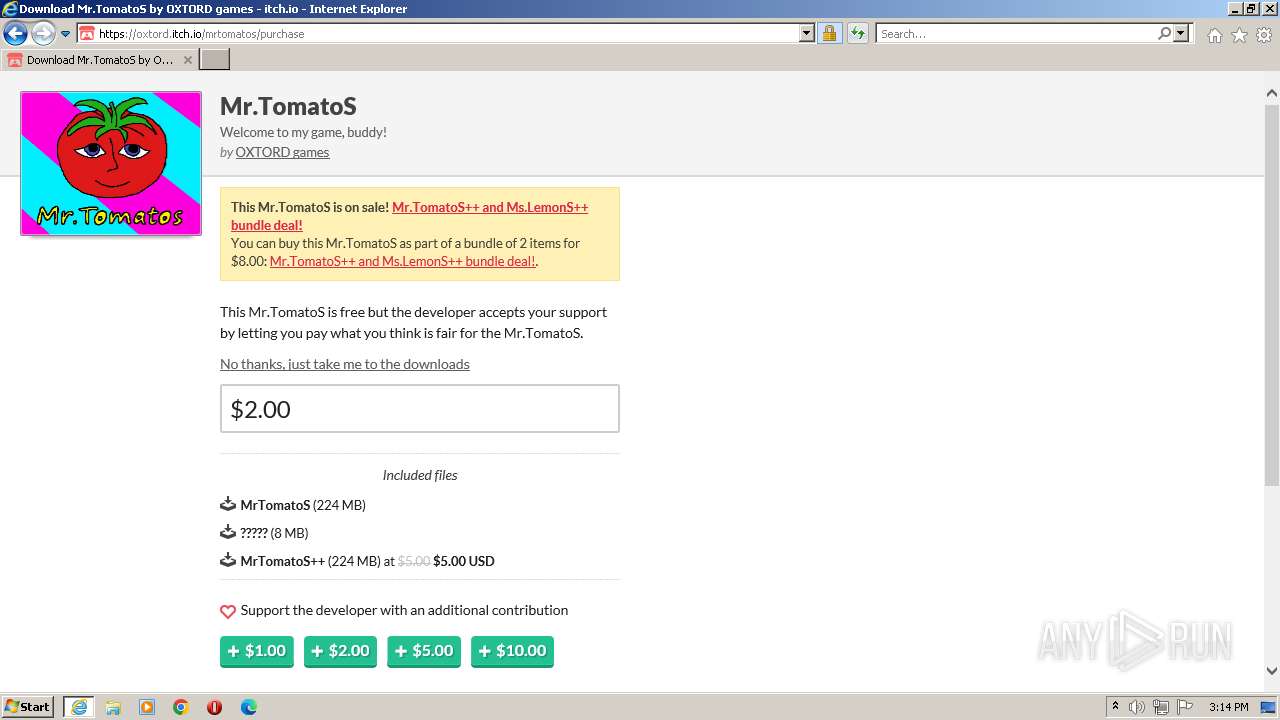
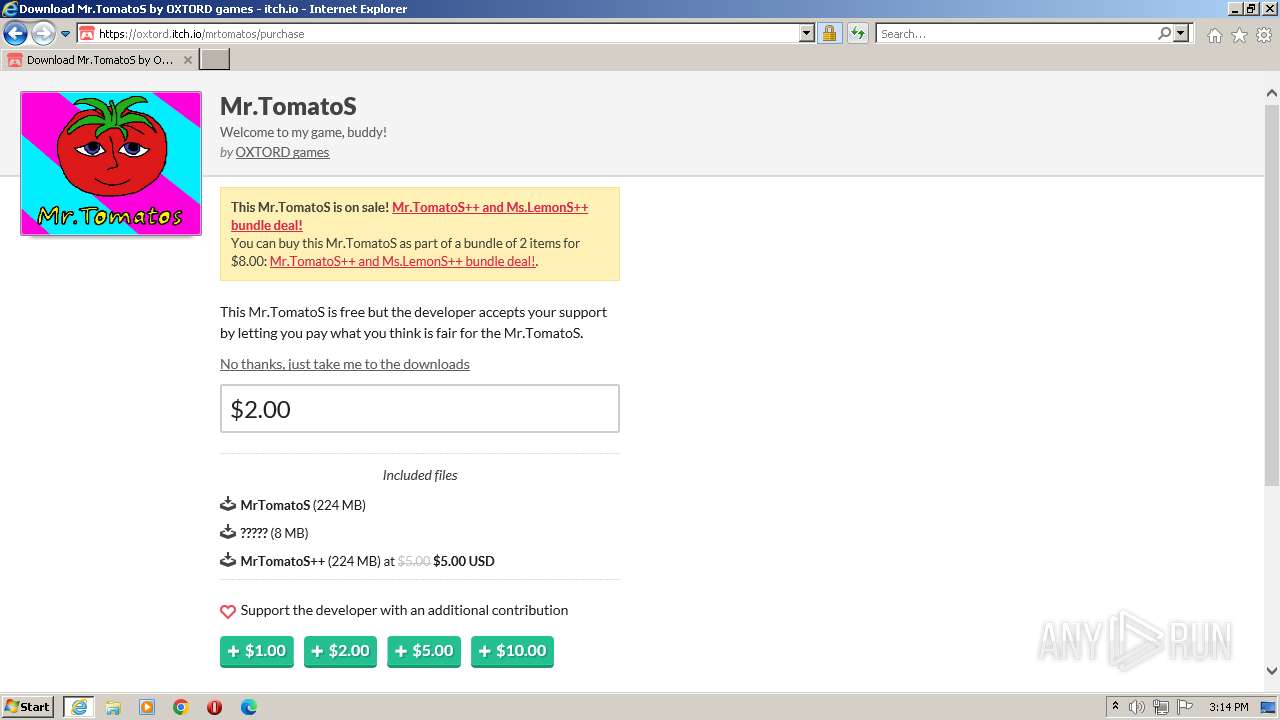
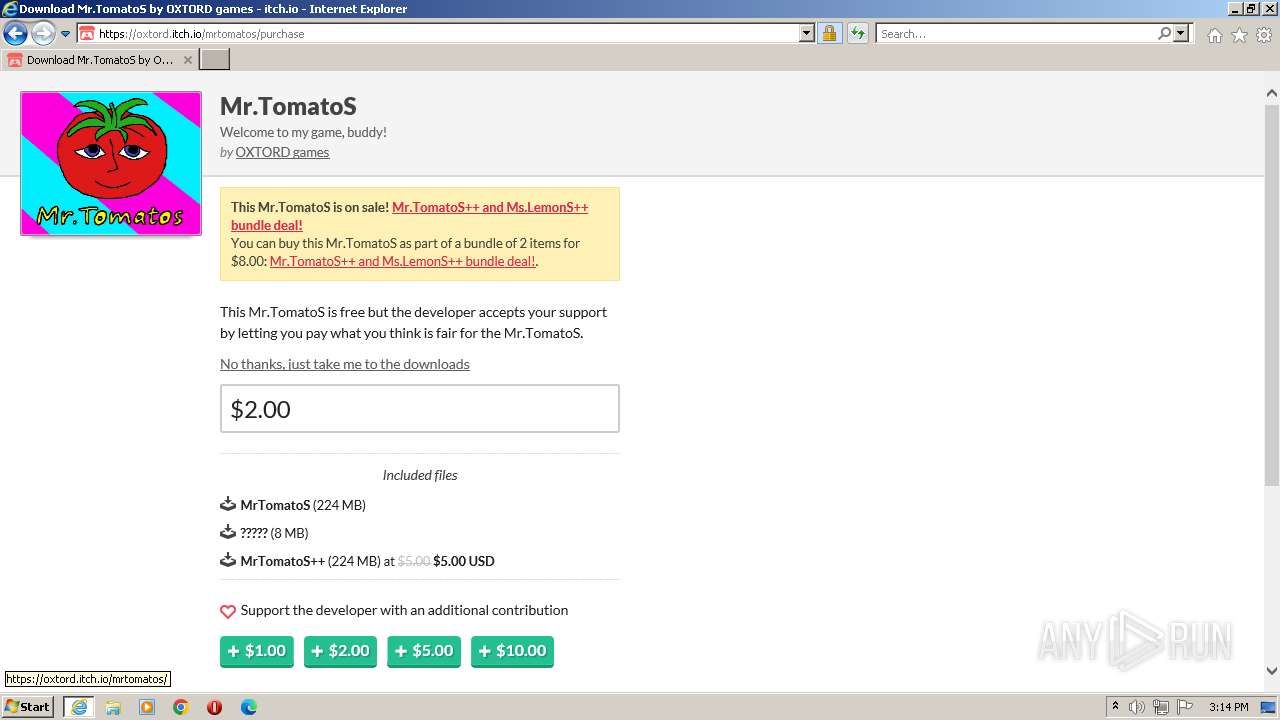
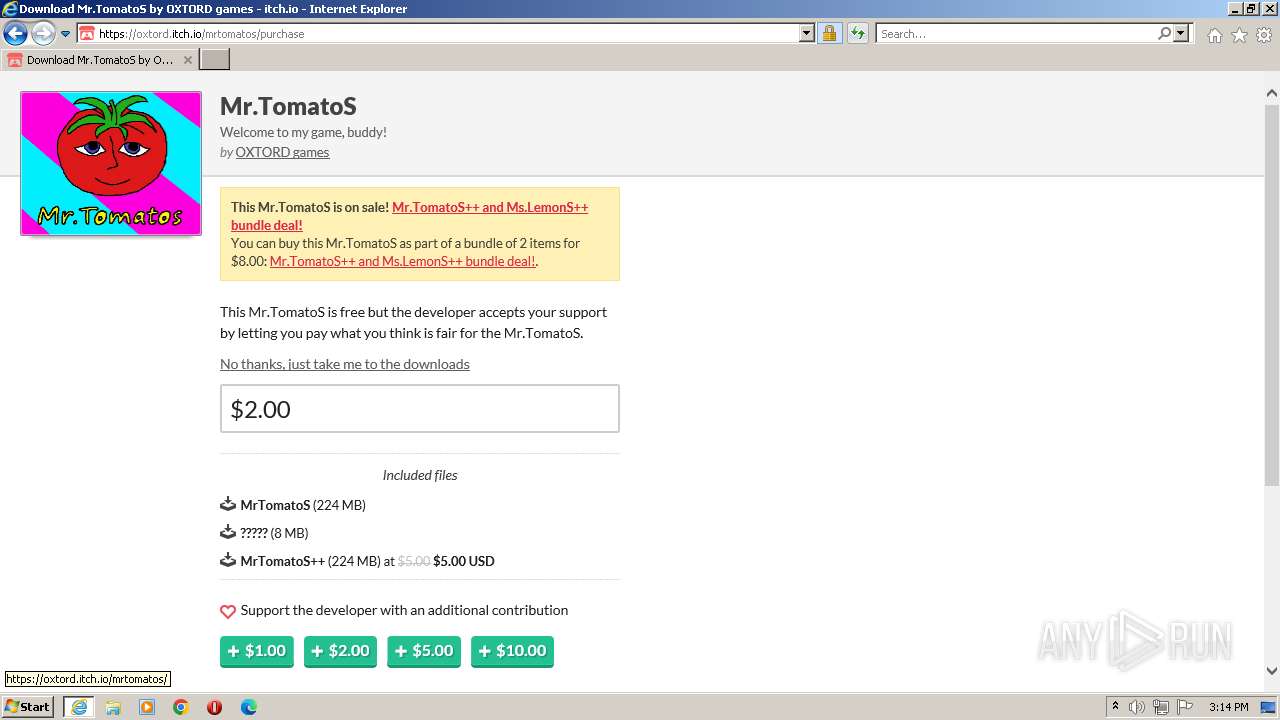
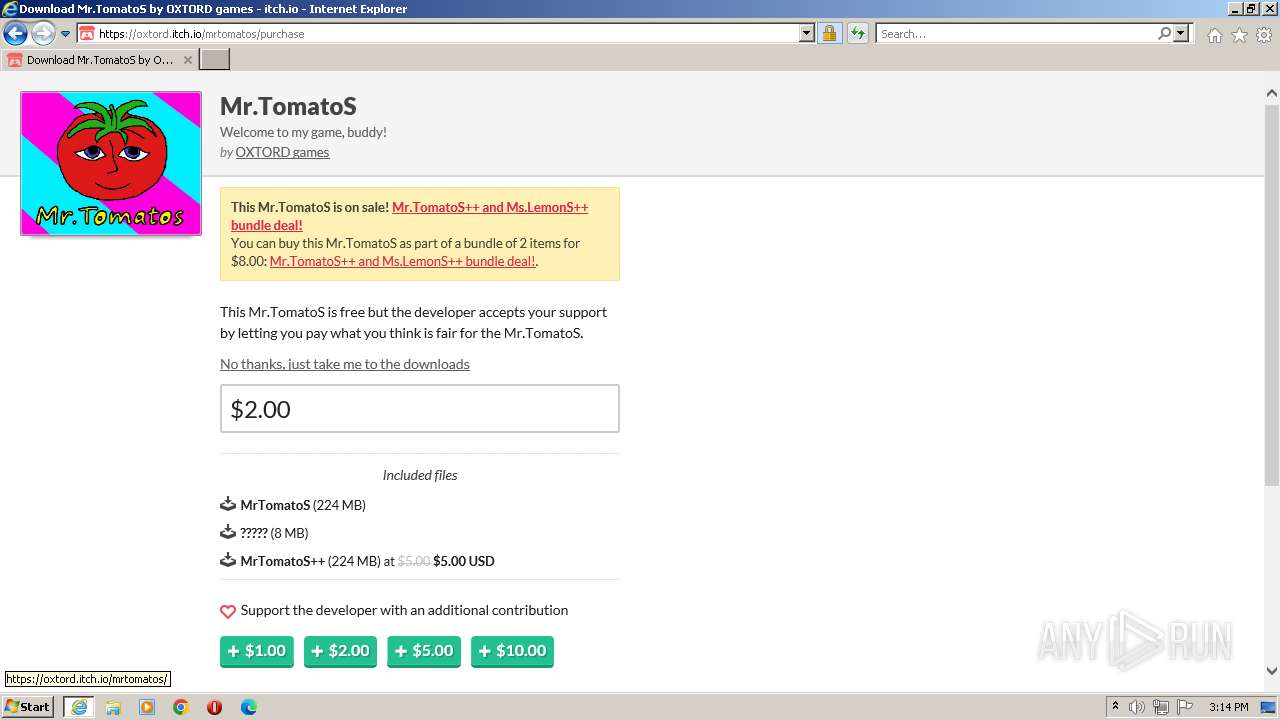
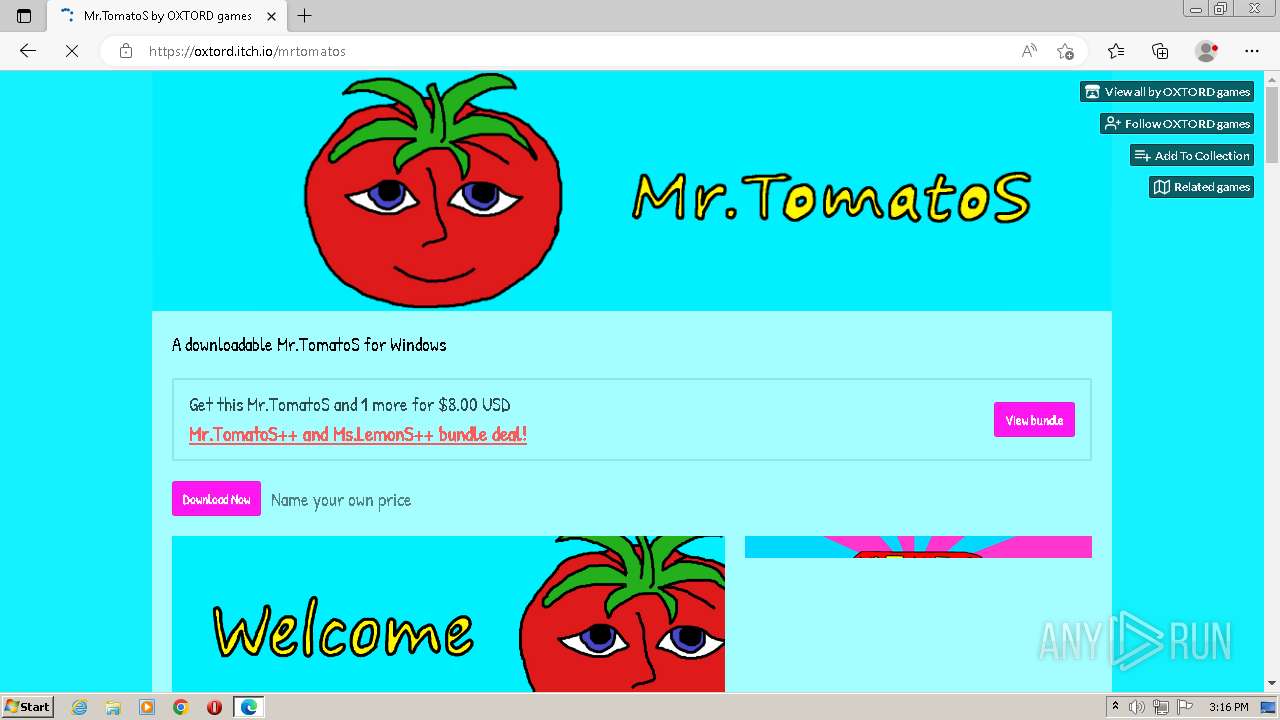
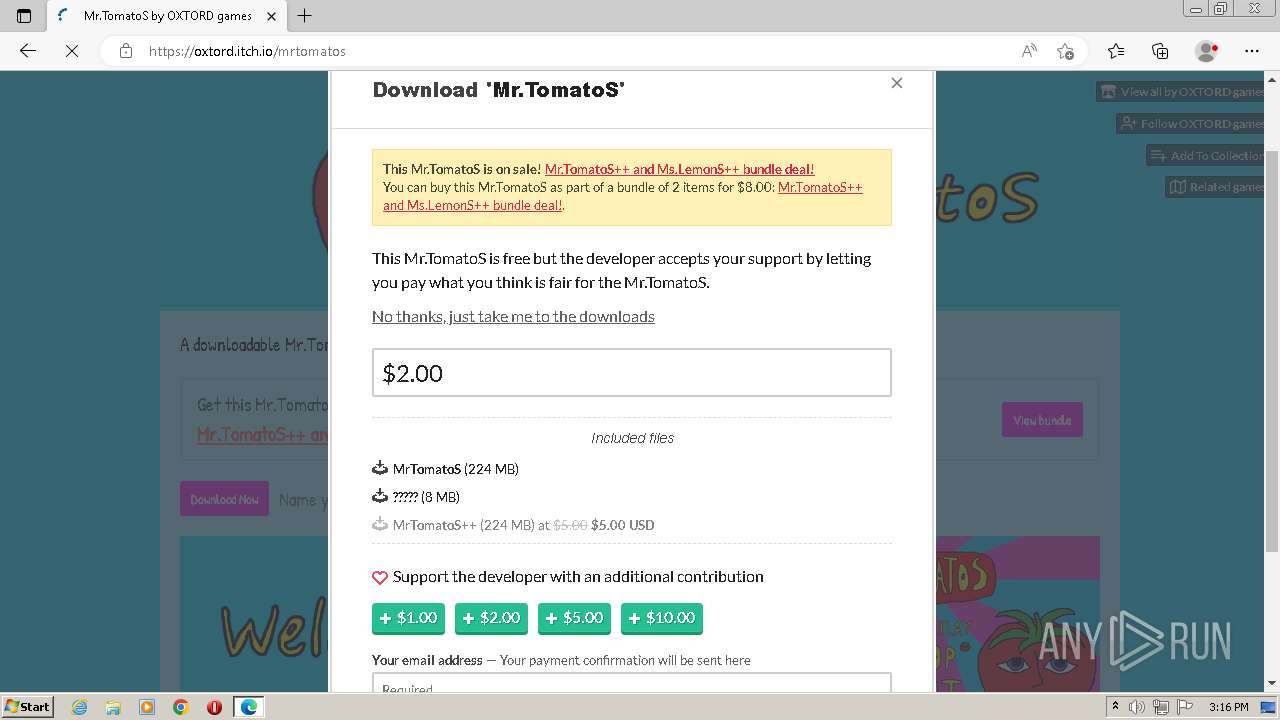
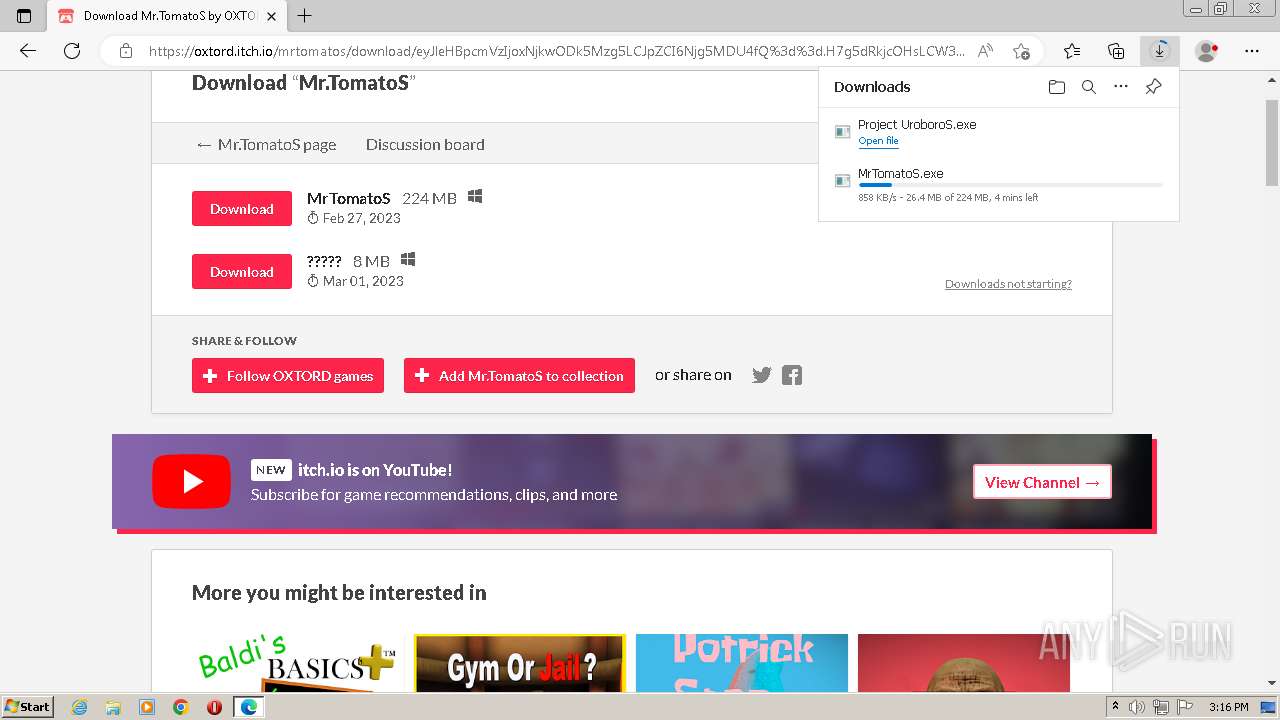
| URL: | https://oxtord.itch.io/mrtomatos/download/eyJleHBpcmVzIjoxNjkwODk4OTY1LCJpZCI6Njg5MDU4fQ%3d%3d.hT6azVa95%2bPQljZkEgYKEJVw2ZI%3d |
| Full analysis: | https://app.any.run/tasks/1b60e78d-e8bf-4acc-973e-198d6bb734d6 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2023, 14:12:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6748A11282364CAE4DDA8AAD6688161B |
| SHA1: | 6C9785FB1C76B49291AF6B1F526B30A7A62A8FEB |
| SHA256: | C156C98B3F9761CEABB8851A50029534996BB5BB4B4966BDFC20DAA0123BA98A |
| SSDEEP: | 3:N8UsXzL3XRTE6B45vcGOfFdb/Jw1yr69hwRdWoEQH2HOg7Zn:2UsnZE6BOvcGOf9w1yr7UfOgd |
MALICIOUS
Application was dropped or rewritten from another process
- Project UroboroS.exe (PID: 3460)
- Project UroboroS.exe (PID: 3596)
SUSPICIOUS
Executable content was dropped or overwritten
- Project UroboroS.exe (PID: 3596)
INFO
The process uses the downloaded file
- msedge.exe (PID: 2744)
- msedge.exe (PID: 3452)
Checks supported languages
- Project UroboroS.exe (PID: 3596)
Create files in a temporary directory
- Project UroboroS.exe (PID: 3596)
Executable content was dropped or overwritten
- msedge.exe (PID: 3452)
- msedge.exe (PID: 2872)
- msedge.exe (PID: 2060)
Reads the computer name
- Project UroboroS.exe (PID: 3596)
Loads dropped or rewritten executable
- Project UroboroS.exe (PID: 3596)
The process checks LSA protection
- Project UroboroS.exe (PID: 3596)
Creates files or folders in the user directory
- Project UroboroS.exe (PID: 3596)
Application launched itself
- iexplore.exe (PID: 1896)
- msedge.exe (PID: 3452)
Manual execution by a user
- msedge.exe (PID: 3452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
82
Monitored processes
41
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=29 --mojo-platform-channel-handle=5056 --field-trial-handle=1160,i,4872842912810894895,13698572897784548896,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 300 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=4208 --field-trial-handle=1160,i,4872842912810894895,13698572897784548896,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --mojo-platform-channel-handle=4024 --field-trial-handle=1160,i,4872842912810894895,13698572897784548896,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=5572 --field-trial-handle=1160,i,4872842912810894895,13698572897784548896,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1896 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1648 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1240 --field-trial-handle=1160,i,4872842912810894895,13698572897784548896,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1804 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --mojo-platform-channel-handle=4948 --field-trial-handle=1160,i,4872842912810894895,13698572897784548896,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1896 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://oxtord.itch.io/mrtomatos/download/eyJleHBpcmVzIjoxNjkwODk4OTY1LCJpZCI6Njg5MDU4fQ%3d%3d.hT6azVa95%2bPQljZkEgYKEJVw2ZI%3d" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5556 --field-trial-handle=1160,i,4872842912810894895,13698572897784548896,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=4472 --field-trial-handle=1160,i,4872842912810894895,13698572897784548896,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
20 710
Read events
20 533
Write events
169
Delete events
8
Modification events
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
74
Suspicious files
1 098
Text files
239
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E4E343CD89B4ADD15E2BF910C90475C0 | SHA256:9DBA6047BEEC8651C338AC9C8F050BD9143E4D761685917B62F19EC5E8ED6DF8 | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:872572F958F9F706E28DF08F13CC73BA | SHA256:54F379D80C11003CF99FF9E77EA518F61C0ECC1D0FC45AC2A5CAB7DC4B40E76D | |||
| 1896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:194E8A49A4FE92969550403CEDF772B6 | SHA256:B1F40400639633B314D4DC48AA1868FFA2CC0CF6D99E103AB90691CD10BBC7B7 | |||
| 1896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0191BD0916F68CA4567ECCD1C97DA084 | binary | |
MD5:ACB1393DE9A4188B110867617A13A6E0 | SHA256:35D2F432572FCCAF8F2C58B5963DC1127A5F7739CA1D0977E3058ADFE6C764A7 | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:C72C71DA685E914409670AE9A1F12EEB | SHA256:EF86035E4DE7F6AE0275864012E6D8DCCBD0862147A95E9AC5BC6D968DA1CF2C | |||
| 1896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:1326A444042D567829772111FB1159F1 | SHA256:03D7C3E49ADE471C5A1E814D8B59E70D0122184A065083BC4A744C13F764A68B | |||
| 1584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:F15CC7F1027A56B71D5895C4897E916F | SHA256:B658D543CA7A49216BC5D8A20C50855CBB72BB6D5C9D59067CA459EB5B726537 | |||
| 1896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
137
DNS requests
131
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1584 | iexplore.exe | GET | — | 23.201.254.55:80 | http://x1.c.lencr.org/ | CH | — | — | whitelisted |
1584 | iexplore.exe | GET | — | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | — | — | whitelisted |
860 | svchost.exe | GET | — | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d9a961cd-afbe-4cd8-8aee-c21eaf7d7c04?P1=1691180469&P2=404&P3=2&P4=LcHUz%2bpVhlNU6h4icC45hpIdyrB7E8eTYHWwX2rSxz8n6BQwa61jsRKddqd5ZQzqWN76xbeF7eUEQ0v73KB74Q%3d%3d | US | — | — | whitelisted |
860 | svchost.exe | GET | — | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d9a961cd-afbe-4cd8-8aee-c21eaf7d7c04?P1=1691180469&P2=404&P3=2&P4=LcHUz%2bpVhlNU6h4icC45hpIdyrB7E8eTYHWwX2rSxz8n6BQwa61jsRKddqd5ZQzqWN76xbeF7eUEQ0v73KB74Q%3d%3d | US | — | — | whitelisted |
1584 | iexplore.exe | GET | 200 | 8.238.190.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a6868112caa1ee05 | US | compressed | 4.70 Kb | whitelisted |
1896 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
— | — | GET | 200 | 8.238.190.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6f2f97553d122ba7 | US | compressed | 4.70 Kb | whitelisted |
1088 | svchost.exe | GET | 304 | 8.238.190.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d4b6a0774c81be40 | US | compressed | 62.3 Kb | whitelisted |
1584 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGPef2tM%2FnYdCoqO9D1VE%2BU%3D | US | binary | 471 b | whitelisted |
1584 | iexplore.exe | GET | 200 | 104.18.14.101:80 | http://crl.comodoca.com/AAACertificateServices.crl | US | binary | 506 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1584 | iexplore.exe | 173.255.250.29:443 | oxtord.itch.io | Linode, LLC | US | suspicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1584 | iexplore.exe | 8.238.190.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
1896 | iexplore.exe | 2.23.209.193:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1896 | iexplore.exe | 8.238.190.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
1584 | iexplore.exe | 104.18.14.101:80 | ocsp.comodoca.com | CLOUDFLARENET | — | unknown |
1896 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |