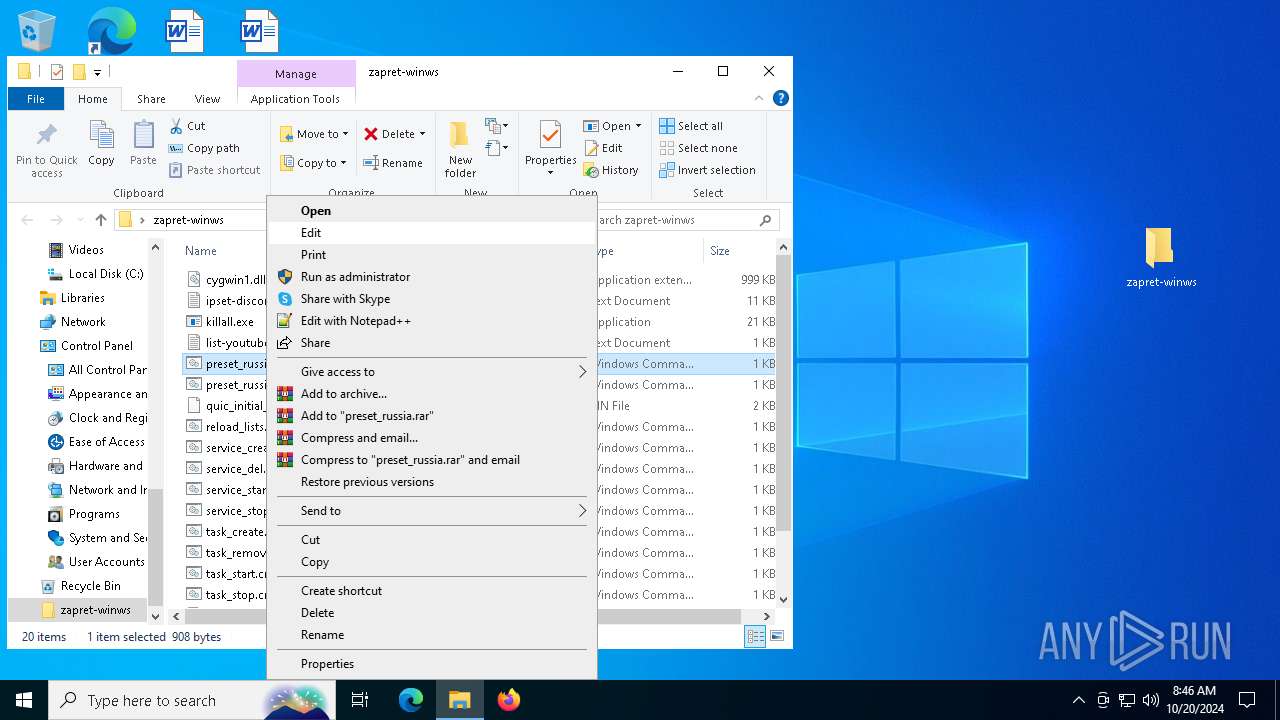
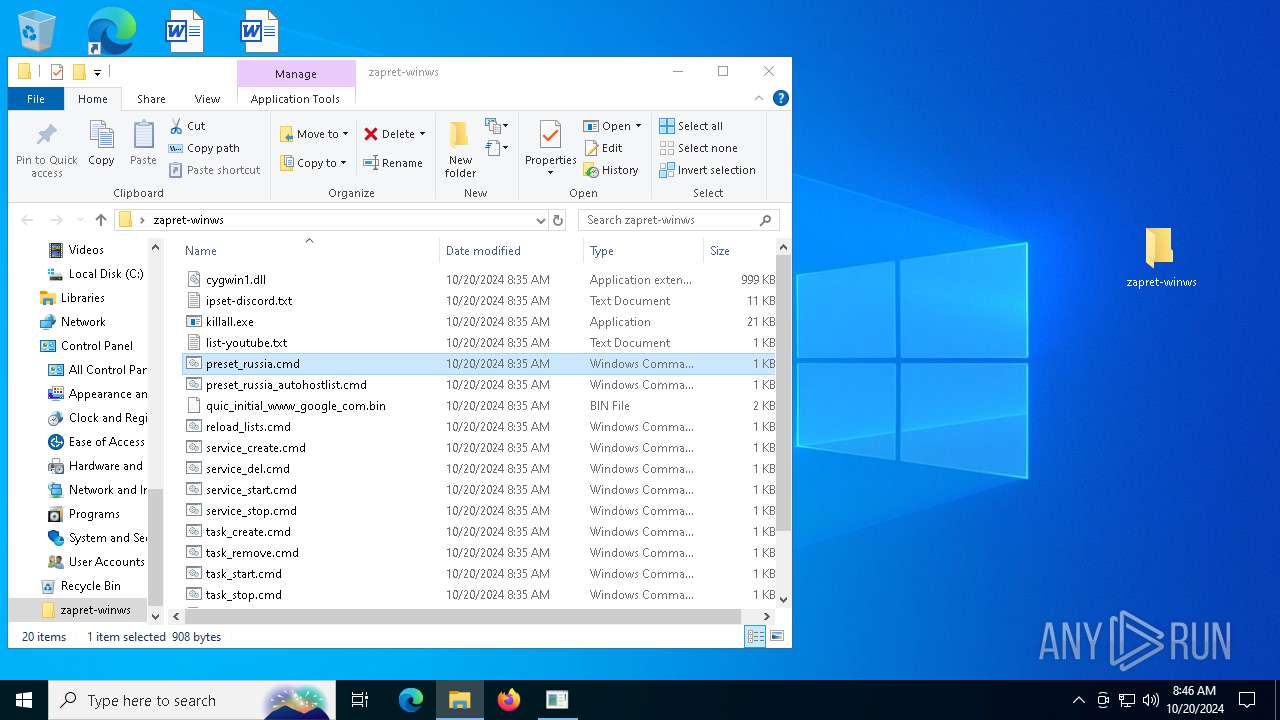
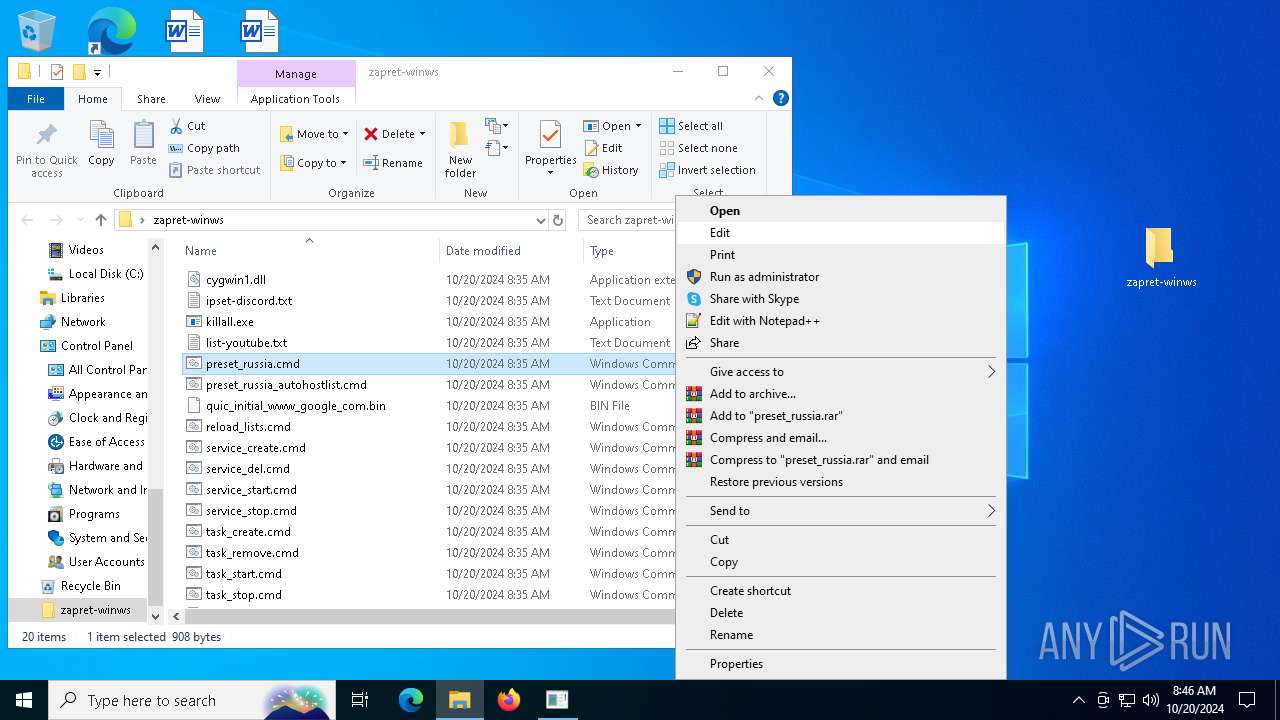
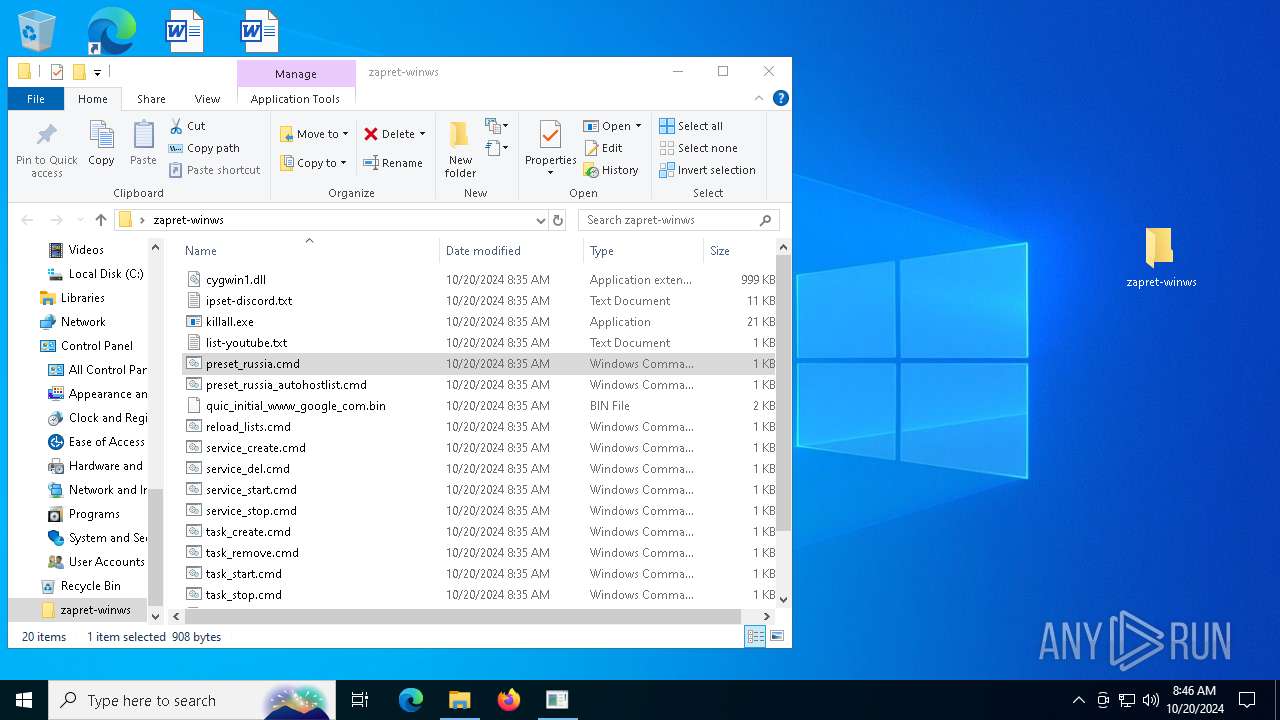
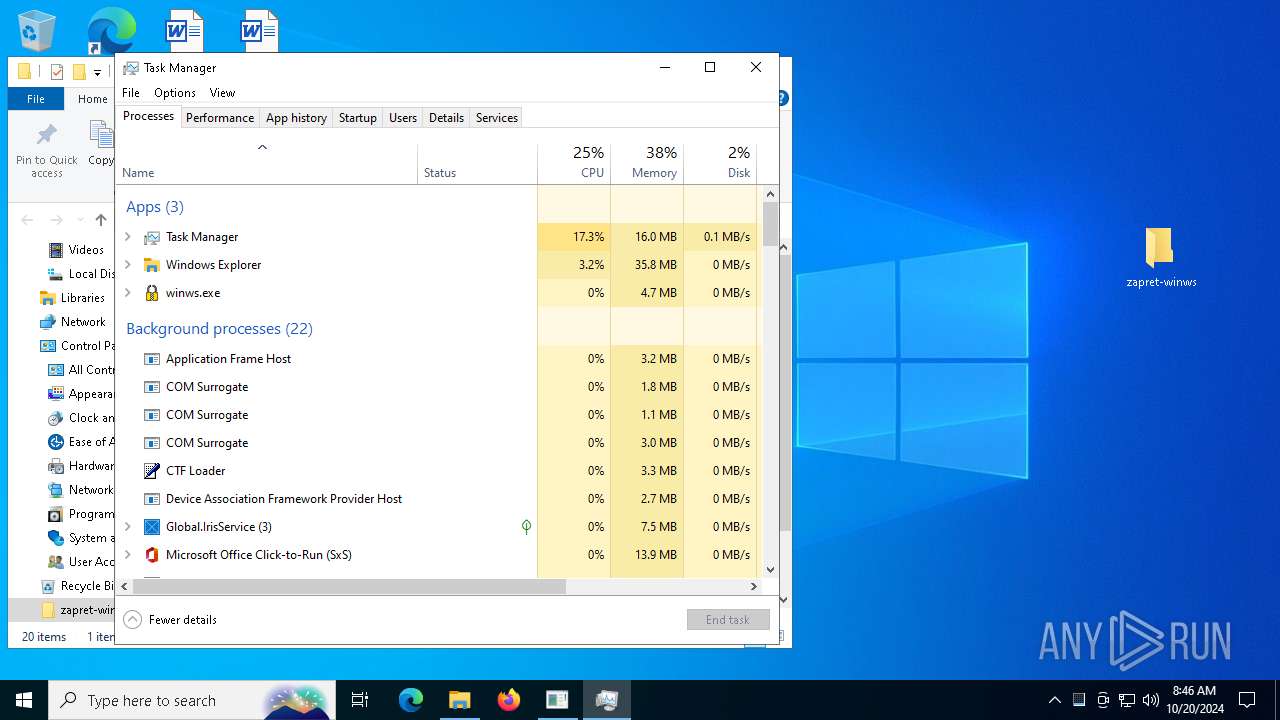
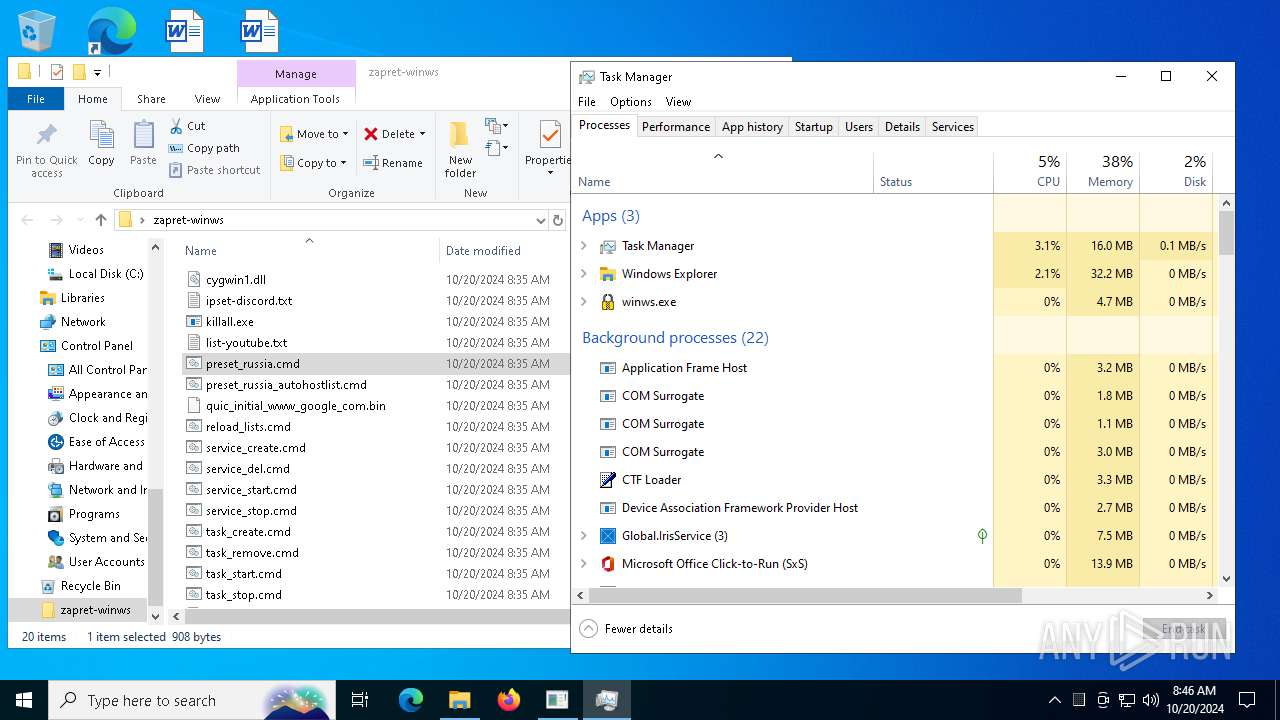
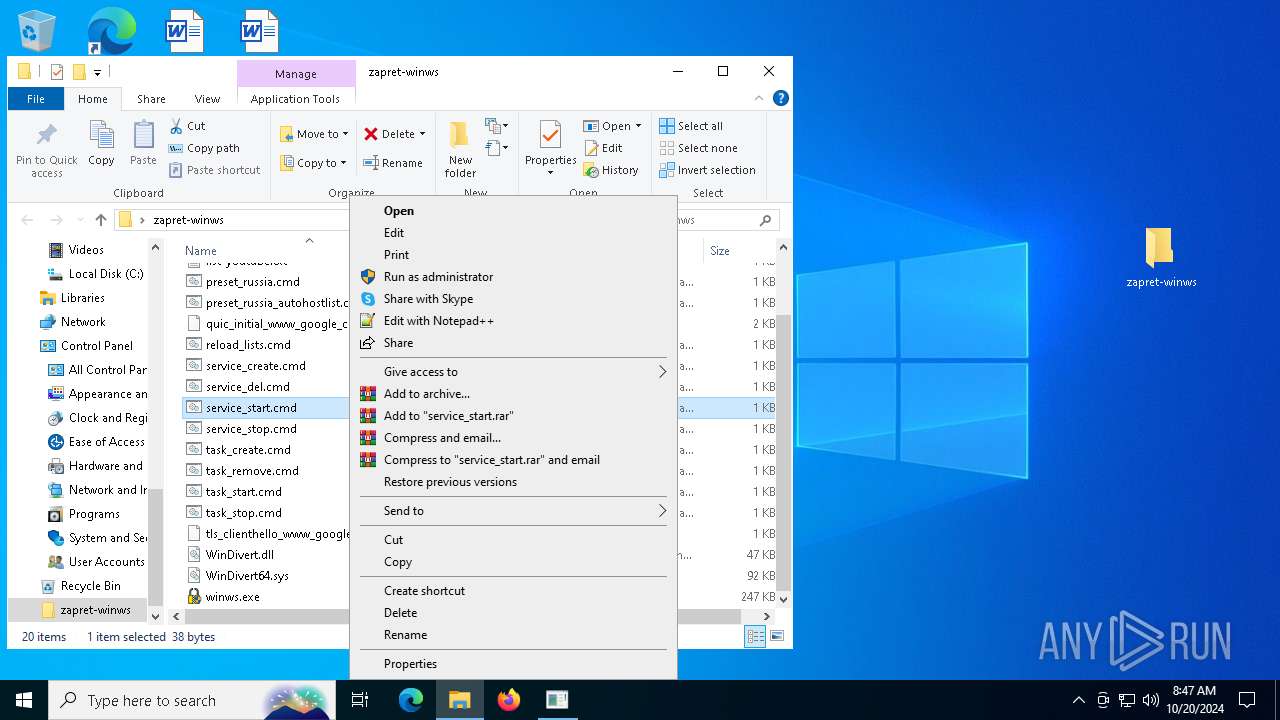
| File name: | zapret-winws.rar |
| Full analysis: | https://app.any.run/tasks/bb89b4aa-a14c-4959-b6d2-1ee76e2b419c |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2024, 08:46:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EB601747B6FE7C81C2B50B98C4E1184F |
| SHA1: | 25C2857D18C0A309310C211E284F5568C30EC921 |
| SHA256: | C13C1BEEEF9027FA73FC166CBD1924EE3A14886CA78BE07478CB058CC3E307FB |
| SSDEEP: | 49152:uD2pC3Hq/Qa+bvovv3j4q0ZftsQ7ep4E1Nw7USAbd0M1Odwq4QJoRv0oKP3zWQf4:Kx3K/Qa+Eh0BuW+4kVv6j4KCv01f6QXw |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1168)
Detects Cygwin installation
- WinRAR.exe (PID: 1168)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 1168)
INFO
Manual execution by a user
- Taskmgr.exe (PID: 1112)
- cmd.exe (PID: 6572)
- notepad.exe (PID: 4232)
- Taskmgr.exe (PID: 2708)
The process uses the downloaded file
- WinRAR.exe (PID: 1168)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
139
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1112 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\zapret-winws.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1344 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winws.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3864 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4232 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\zapret-winws\preset_russia.cmd | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
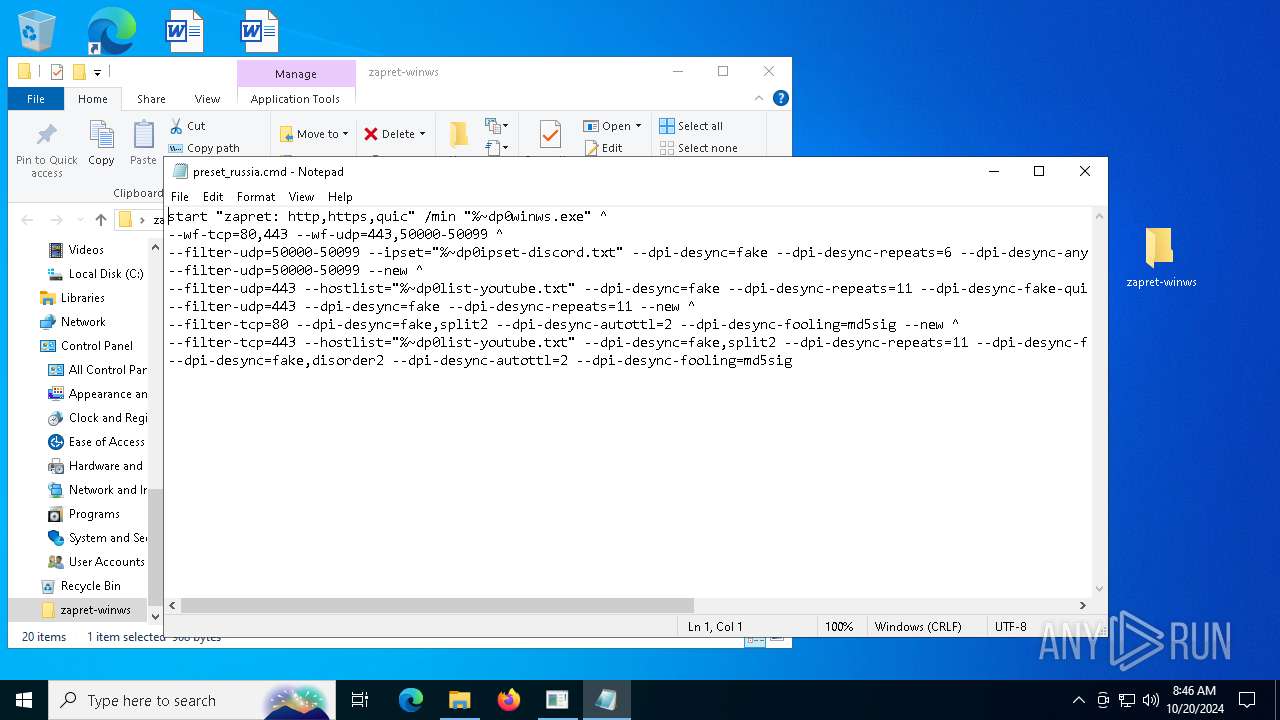
| 6208 | "C:\Users\admin\Desktop\zapret-winws\winws.exe" --wf-tcp=80,443 --wf-udp=443,50000-50099 --filter-udp=50000-50099 --ipset="C:\Users\admin\Desktop\zapret-winws\ipset-discord.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-any-protocol --dpi-desync-cutoff=n2 --new --filter-udp=50000-50099 --new --filter-udp=443 --hostlist="C:\Users\admin\Desktop\zapret-winws\list-youtube.txt" --dpi-desync=fake --dpi-desync-repeats=11 --dpi-desync-fake-quic="C:\Users\admin\Desktop\zapret-winws\quic_initial_www_google_com.bin" --new --filter-udp=443 --dpi-desync=fake --dpi-desync-repeats=11 --new --filter-tcp=80 --dpi-desync=fake,split2 --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="C:\Users\admin\Desktop\zapret-winws\list-youtube.txt" --dpi-desync=fake,split2 --dpi-desync-repeats=11 --dpi-desync-fooling=md5sig --dpi-desync-fake-tls="C:\Users\admin\Desktop\zapret-winws\tls_clienthello_www_google_com.bin" --new --dpi-desync=fake,disorder2 --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig | C:\Users\admin\Desktop\zapret-winws\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6572 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\zapret-winws\preset_russia.cmd" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6688 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 494
Read events
3 472
Write events
21
Delete events
1
Modification events
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zapret-winws.rar | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
5
Suspicious files
2
Text files
14
Unknown types
0
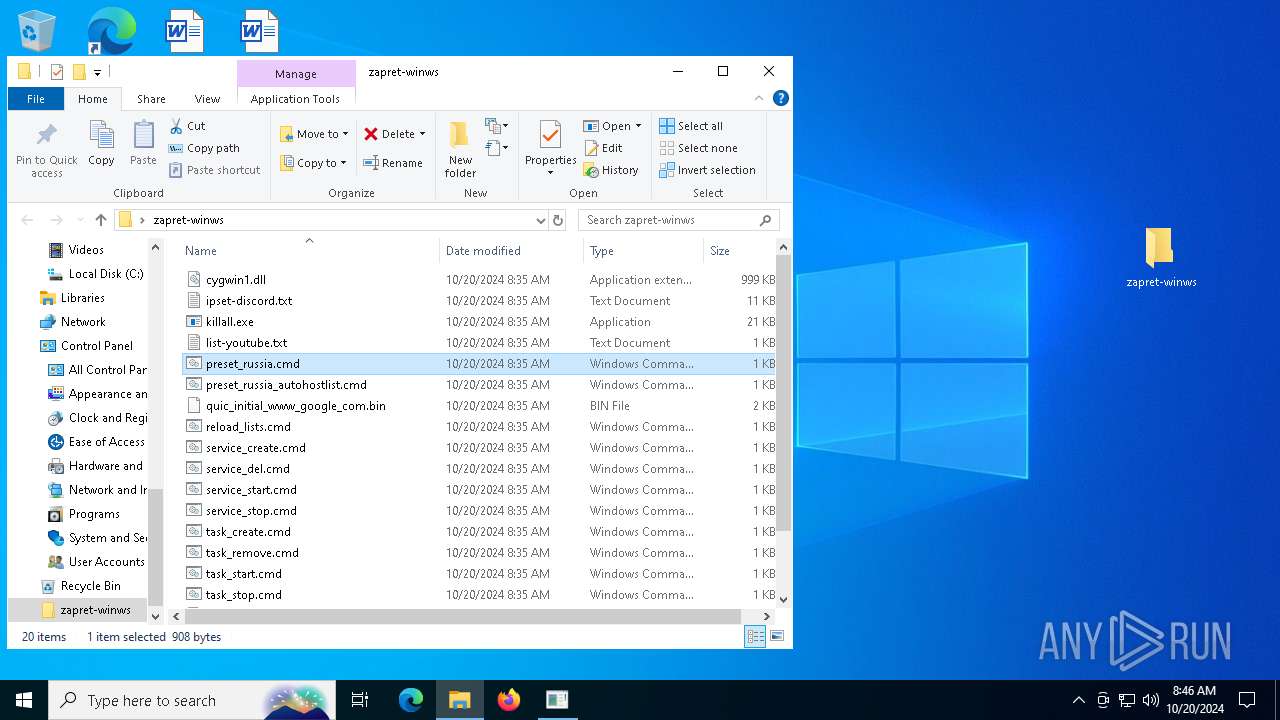
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\quic_initial_www_google_com.bin | binary | |
MD5:312526D39958D89B1F8AB67789AB985F | SHA256:F4589C57749F956BB30538197A521D7005F8B0A8723B4707E72405E51DDAC50A | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\reload_lists.cmd | text | |
MD5:6C5F6C934A3CE77D6DA02F5B288E587F | SHA256:2DD6A181F2A0E6707792B930AAB32DE2BAE4C37AB10F47BC7C6092B5F578A91E | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\cygwin1.dll | executable | |
MD5:C50B50303FAE4AFE7248307339A00D13 | SHA256:712C39A069541AFA69CFCBE01B422BD67B4201EEE7E94CC1327D4ED8B4FA2167 | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\list-youtube.txt | text | |
MD5:79E35DF62B0D1AE455D0A7E04C4CECAC | SHA256:BB0E0289015FC6E7A81D7ADAA0B43356A881759C6ACE0A014AEA89C6FF8D7530 | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\preset_russia.cmd | text | |
MD5:B849624B503B63C795CC695255E1BA43 | SHA256:B0179116F9C4B6B028A2674C61CB51EF5C0388931929183F7EE083B922BB3918 | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\service_start.cmd | text | |
MD5:D1C3C45DA175B318FE11BDD65EC96913 | SHA256:F396EB4C1C1C2801F294BDFD4E19C89D6B7ED7B0C5512AEBD89D965A3FE46C8A | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\WinDivert64.sys | executable | |
MD5:89ED5BE7EA83C01D0DE33D3519944AA5 | SHA256:8DA085332782708D8767BCACE5327A6EC7283C17CFB85E40B03CD2323A90DDC2 | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\ipset-discord.txt | text | |
MD5:40C75BA0A3C07F51CFC98082739C28E1 | SHA256:FA0CA1ECB60EAE74C343B2975280F6A6CB6CB44D965ACB33AC5B9502F1C9E3DC | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\preset_russia_autohostlist.cmd | text | |
MD5:7724154CA89DF1A704ACF85AD67CF980 | SHA256:206A592440FEBD894E976662E159C82D34C7B1AB07AB2FBFB4C70D911B5B6873 | |||
| 1168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1168.28605\zapret-winws\service_stop.cmd | text | |
MD5:5533593BF6AAE9330B67E0AE8C68B3F4 | SHA256:1D5DD1EF31643BC269BBFA3886CEB45ACDE1612840C3501535B09E6240B8C7D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
53
DNS requests
19
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
692 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.iana.org/ | unknown | — | — | whitelisted |
4 | System | GET | 200 | 192.229.221.95:80 | http://www.iana.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1752 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4360 | SearchApp.exe | 92.123.104.62:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
816 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
692 | svchost.exe | Generic Protocol Command Decode | SURICATA TLS invalid record version |
692 | svchost.exe | Generic Protocol Command Decode | SURICATA TLS invalid record version |
4 | System | Generic Protocol Command Decode | SURICATA TLS handshake invalid length |
4 | System | Generic Protocol Command Decode | SURICATA TLS handshake invalid length |