| URL: | https://wingetgui.com/apps/Tencent-WeType |
| Full analysis: | https://app.any.run/tasks/49d41b95-9dd9-4dc9-8df3-1b934e1dd5a0 |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2024, 13:12:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 03041988DA978E274F66D565B08CA5EF |
| SHA1: | 70DC4B652CAEB81C997763756913CB20CB9AFC5A |
| SHA256: | C12BF1FF76AF6526150E5A307B110B97416C37A19855069FF1C16773833B8751 |
| SSDEEP: | 3:N8dygdaVA:2AIeA |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- WeTypeSetup_1.2.6.784_3.exe (PID: 7060)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- WeTypeSetup_1.2.6.784_3.exe (PID: 7152)
- WeTypeSetup_1.2.6.784_3.exe (PID: 7060)
Executable content was dropped or overwritten
- WeTypeSetup_1.2.6.784_3.exe (PID: 7152)
- WeTypeSetup_1.2.6.784_3.exe (PID: 7060)
Process drops legitimate windows executable
- WeTypeSetup_1.2.6.784_3.exe (PID: 7060)
Executes as Windows Service
- wetype_service.exe (PID: 1612)
INFO
Executable content was dropped or overwritten
- chrome.exe (PID: 5316)
- chrome.exe (PID: 5728)
Application launched itself
- chrome.exe (PID: 5728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
172
Monitored processes
38
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5332 --field-trial-handle=1664,i,11214683061317465268,2850650137619826150,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Tencent\WeType\1.2.6.784\wetype_service.exe" start | C:\Program Files\Tencent\WeType\1.2.6.784\wetype_service.exe | — | WeTypeSetup_1.2.6.784_3.exe | |||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: WeType Management Service Exit code: 0 Version: 1.2.6.784 Modules
| |||||||||||||||
| 1544 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wetype_server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1612 | "C:\Program Files\Tencent\WeType\1.2.6.784\wetype_service.exe" | C:\Program Files\Tencent\WeType\1.2.6.784\wetype_service.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Tencent Integrity Level: SYSTEM Description: WeType Management Service Version: 1.2.6.784 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5448 --field-trial-handle=1664,i,11214683061317465268,2850650137619826150,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
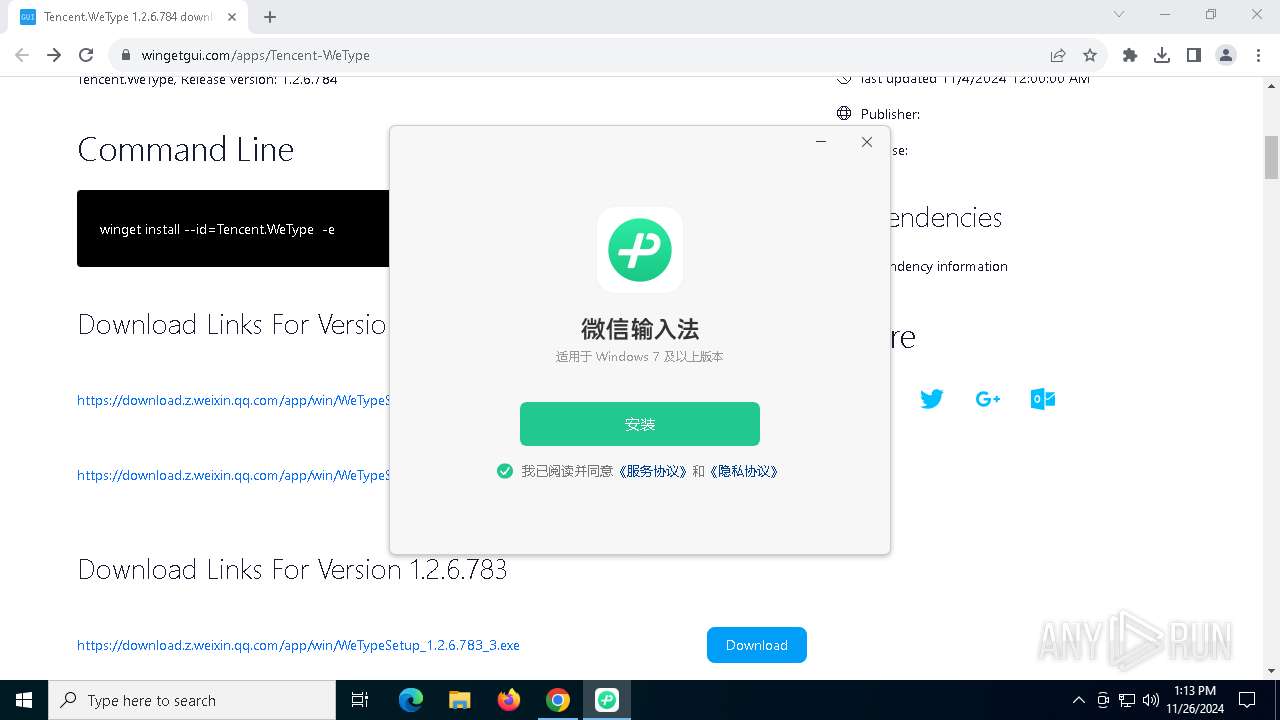
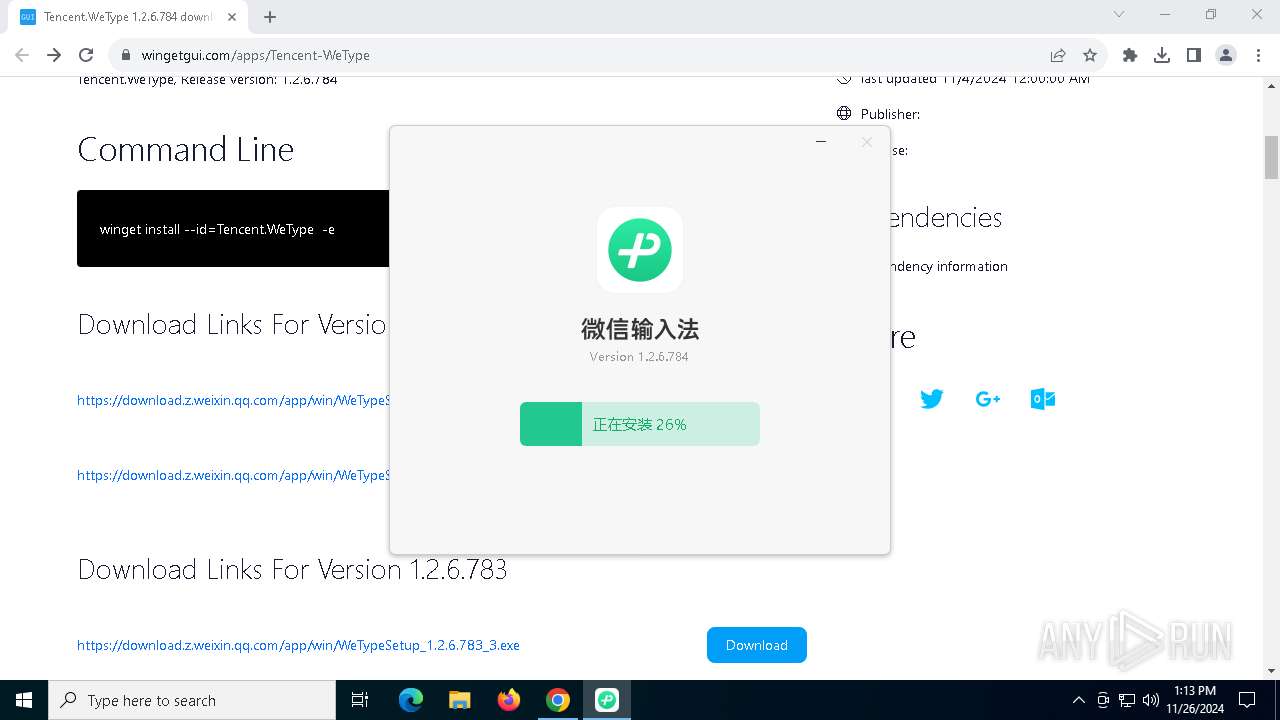
| 1864 | "C:\Users\admin\Downloads\WeTypeSetup_1.2.6.784_3.exe" | C:\Users\admin\Downloads\WeTypeSetup_1.2.6.784_3.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 微信输入法 Exit code: 3221226540 Version: 1.2.6.784 Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Tencent\WeType\1.2.6.784\wetype_update.exe" | C:\Program Files\Tencent\WeType\1.2.6.784\wetype_update.exe | wetype_service.exe | ||||||||||||
User: admin Company: Tencent Integrity Level: MEDIUM Description: 微信输入法 Version: 1.2.6.784 Modules
| |||||||||||||||
| 1988 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wetype_service.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5240 --field-trial-handle=1664,i,11214683061317465268,2850650137619826150,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5620 --field-trial-handle=1664,i,11214683061317465268,2850650137619826150,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
18 501
Read events
18 393
Write events
90
Delete events
18
Modification events
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (624) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000230F64EB0440DB01 | |||
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
| (PID) Process: | (5728) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1S |
Value: 1 | |||
Executable files
58
Suspicious files
331
Text files
264
Unknown types
138
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF135d46.TMP | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF135d46.TMP | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF135d46.TMP | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF135d46.TMP | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF135d56.TMP | — | |
MD5:— | SHA256:— | |||
| 5728 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
102
DNS requests
80
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6204 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6968 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5652 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5652 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5652 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5652 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3884 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5728 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6392 | chrome.exe | 104.21.61.37:443 | wingetgui.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
wingetgui.com |
| unknown |
accounts.google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6392 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6392 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
Process | Message |
|---|---|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:284 7060-03816)-i/WeTypeSetup@2864:
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:284 7152-06536)-i/WeTypeSetup@2864:
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:315 7060-03816)-i/WeTypeSetup@194:RegOpenKeyEx result = 2
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:315 7060-03816)-i/WeTypeSetup@190:getValueFromReg: Software\Tencent\WeType InstallDir
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:315 7060-03816)-i/WeTypeSetup@3597:InitGlobalVariables mutex: 800, GetLastError(): 0
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:315 7060-03816)-i/WeTypeSetup@3595:init engine, wnd_type = 0, lan = 0, ins_type = 0
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:315 7152-06536)-i/WeTypeSetup@3597:InitGlobalVariables mutex: 812, GetLastError(): 183
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:315 7060-03816)-i/WeTypeSetup@194:RegOpenKeyEx result = 2
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:315 7060-03816)-i/WeTypeSetup@190:getValueFromReg: Software\Microsoft\Windows\CurrentVersion\Uninstall\WeType InstallLocation
|
WeTypeSetup_1.2.6.784_3.exe | (2024-11-26:13:13:04:315 7152-06536)-i/WeTypeSetup@3595:init engine, wnd_type = 0, lan = 0, ins_type = 0
|