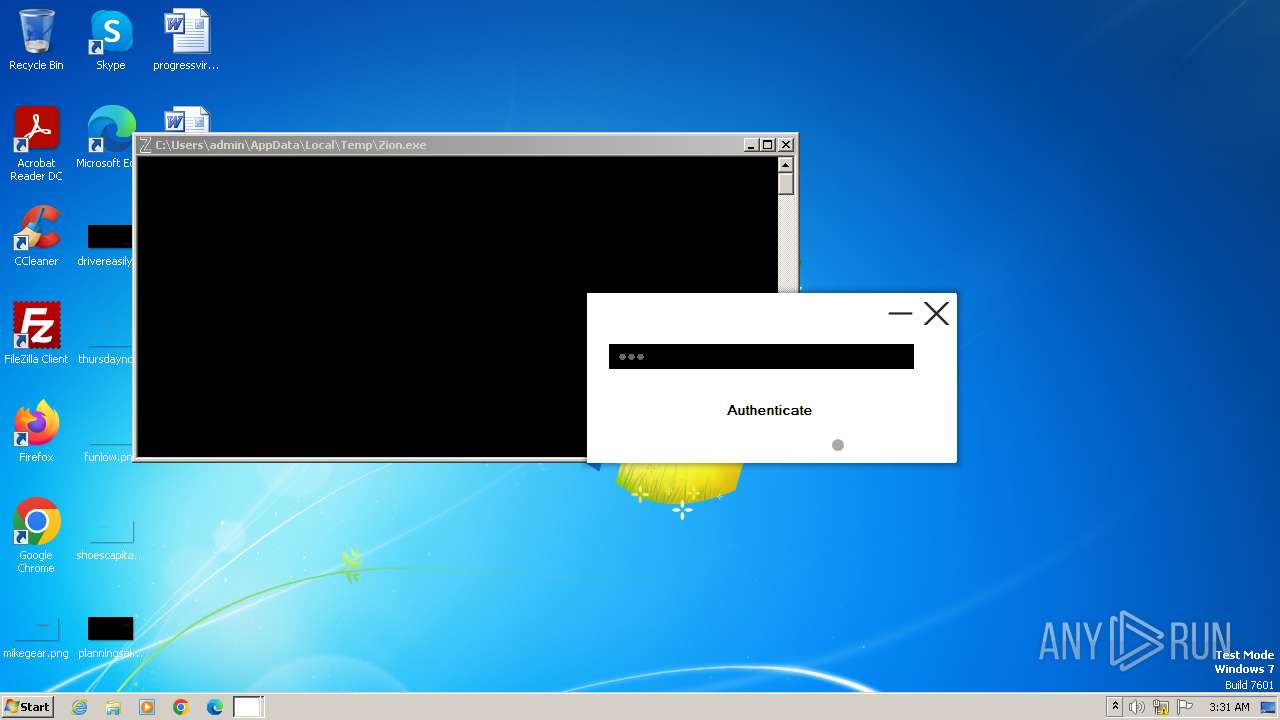
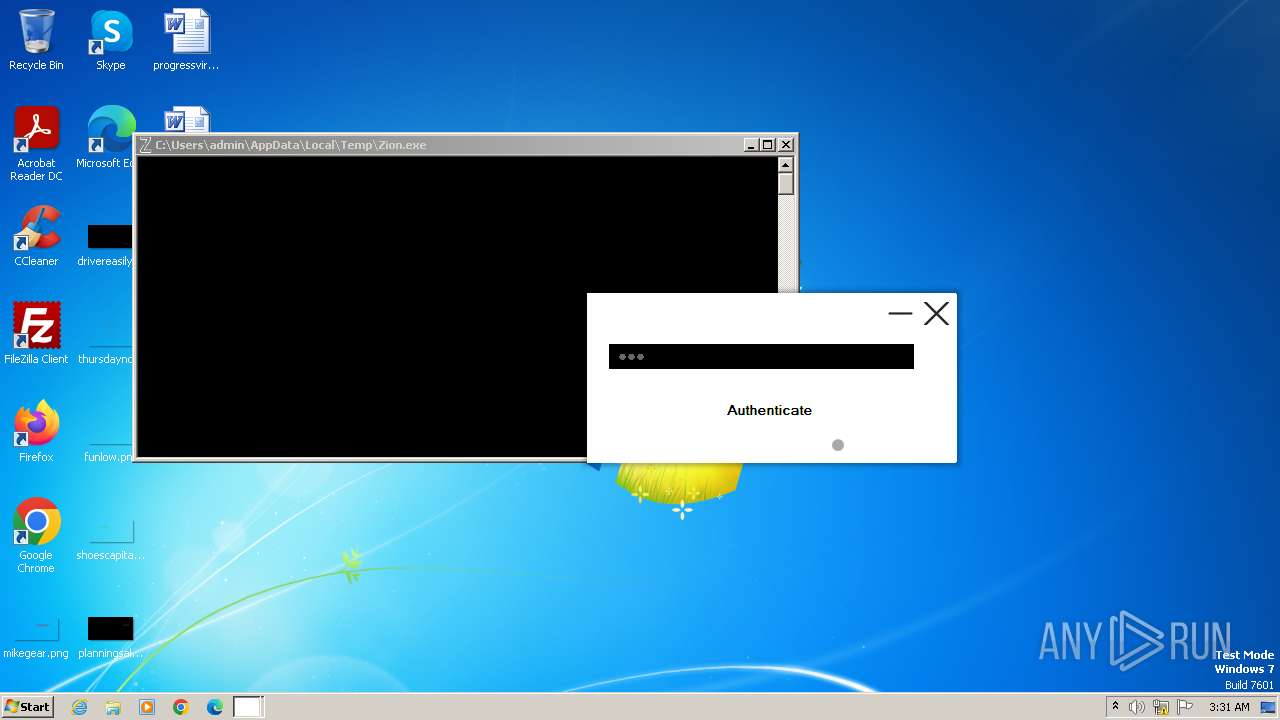
| File name: | Zion.exe |
| Full analysis: | https://app.any.run/tasks/9cc43f41-bb8a-453f-a52b-99abc24d182c |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2024, 02:30:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | F38AFED70B7B5E48C81E8DA6386C2342 |
| SHA1: | 2CE73C1D06AD77F234EB55A152141920EEEA3D73 |
| SHA256: | C12ADB6239A97DC8E068714B9BF5A3234592EF9D75188CD896B5A412F5F395DE |
| SSDEEP: | 98304:yg8tqJ+HYdDyvKi8rB8GrBtV4ifnHZb8TrWfm7gcTRmyo/s6m5APH9hsp1RnWMRf:RUZ4htpDD |
MALICIOUS
Drops the executable file immediately after the start
- Zion.exe (PID: 4064)
SUSPICIOUS
Reads the Internet Settings
- Zion.exe (PID: 4064)
Reads settings of System Certificates
- Zion.exe (PID: 4064)
Adds/modifies Windows certificates
- Zion.exe (PID: 4064)
INFO
Checks supported languages
- Zion.exe (PID: 4064)
Reads the computer name
- Zion.exe (PID: 4064)
Reads Environment values
- Zion.exe (PID: 4064)
Reads the machine GUID from the registry
- Zion.exe (PID: 4064)
Reads the software policy settings
- Zion.exe (PID: 4064)
Create files in a temporary directory
- Zion.exe (PID: 4064)
Creates files in the program directory
- Zion.exe (PID: 4064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2065:09:29 12:48:59+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1869312 |
| InitializedDataSize: | 2653696 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x45a00a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 6.9.6.9 |
| ProductVersionNumber: | 6.9.6.9 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | discord.gg/ware |
| CompanyName: | discord.gg/ware |
| FileDescription: | Zion |
| FileVersion: | 6.9.6.9 |
| InternalName: | Zion.exe |
| LegalCopyright: | Copyright @ Soda |
| LegalTrademarks: | Copyright @ Soda |
| OriginalFileName: | Zion.exe |
| ProductName: | Zion Spoofer |
| ProductVersion: | 6.9.6.9 |
| AssemblyVersion: | 6.9.6.9 |
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3960 | "C:\Users\admin\AppData\Local\Temp\Zion.exe" | C:\Users\admin\AppData\Local\Temp\Zion.exe | — | explorer.exe | |||||||||||
User: admin Company: discord.gg/ware Integrity Level: MEDIUM Description: Zion Exit code: 3221226540 Version: 6.9.6.9 Modules
| |||||||||||||||
| 4064 | "C:\Users\admin\AppData\Local\Temp\Zion.exe" | C:\Users\admin\AppData\Local\Temp\Zion.exe | explorer.exe | ||||||||||||
User: admin Company: discord.gg/ware Integrity Level: HIGH Description: Zion Version: 6.9.6.9 Modules
| |||||||||||||||
Total events
6 545
Read events
6 509
Write events
31
Delete events
5
Modification events
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4064) Zion.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Zion_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
0
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4064 | Zion.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 4064 | Zion.exe | C:\Users\admin\AppData\Local\Temp\Cab43C1.tmp | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 4064 | Zion.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:282EE48EAB19FEF38D77F13B18A894FE | SHA256:4A93B75C6C5F19B63A8C21554E4857ADD7128816195794C81AC2F07978B26477 | |||
| 4064 | Zion.exe | C:\Users\admin\AppData\Local\Temp\Tar43C2.tmp | binary | |
MD5:435A9AC180383F9FA094131B173A2F7B | SHA256:67DC37ED50B8E63272B49A254A6039EE225974F1D767BB83EB1FD80E759A7C34 | |||
| 4064 | Zion.exe | C:\ProgramData\KeyAuth\debug\Zion\May_15_2024_logs.txt | text | |
MD5:FC3EC2AA97779D2D63279F538BB6E91E | SHA256:3C2954334CA39256AC92B0EFB32B692DF9A802F2BD32120E4D4FDEAB5341BBB0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4064 | Zion.exe | GET | 200 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7744cd105b3a9c8c | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4064 | Zion.exe | 104.26.1.5:443 | keyauth.win | CLOUDFLARENET | US | unknown |
4064 | Zion.exe | 23.32.238.219:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
keyauth.win |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain in DNS Lookup (keyauth .win) |
4064 | Zion.exe | Potentially Bad Traffic | ET INFO Fake Game Cheat Related Domain (keyauth .win) in TLS SNI |