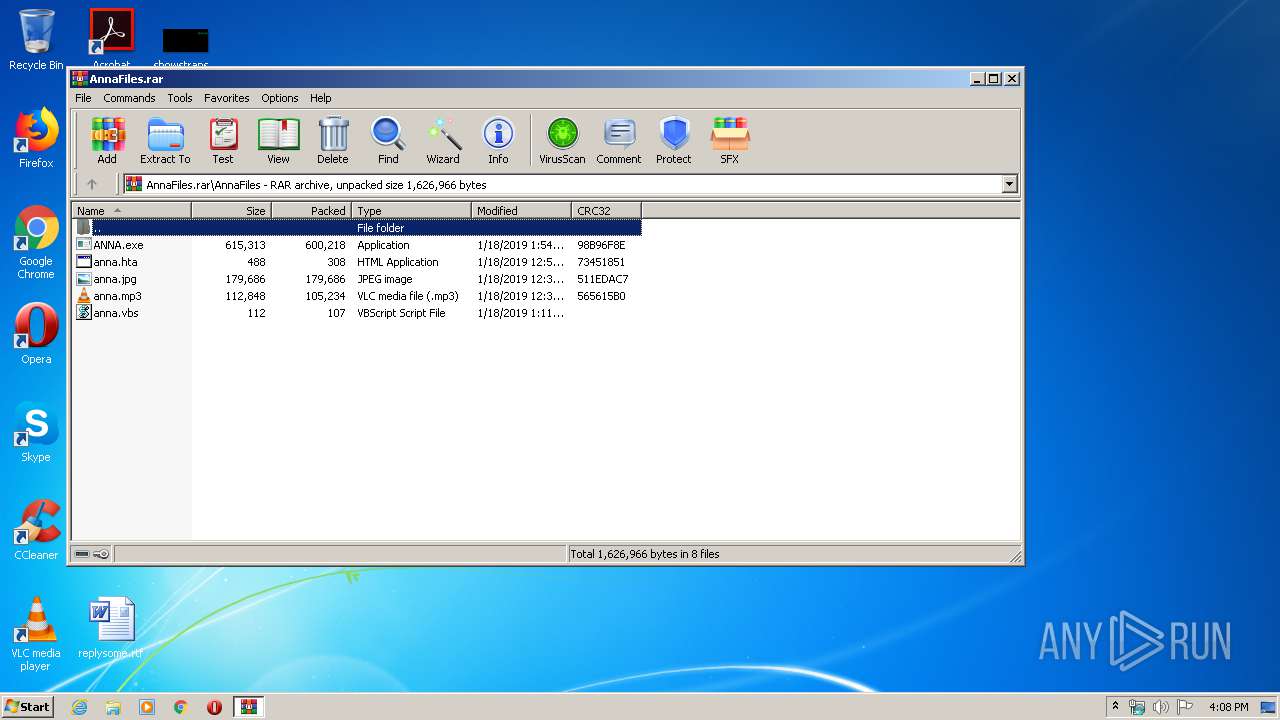
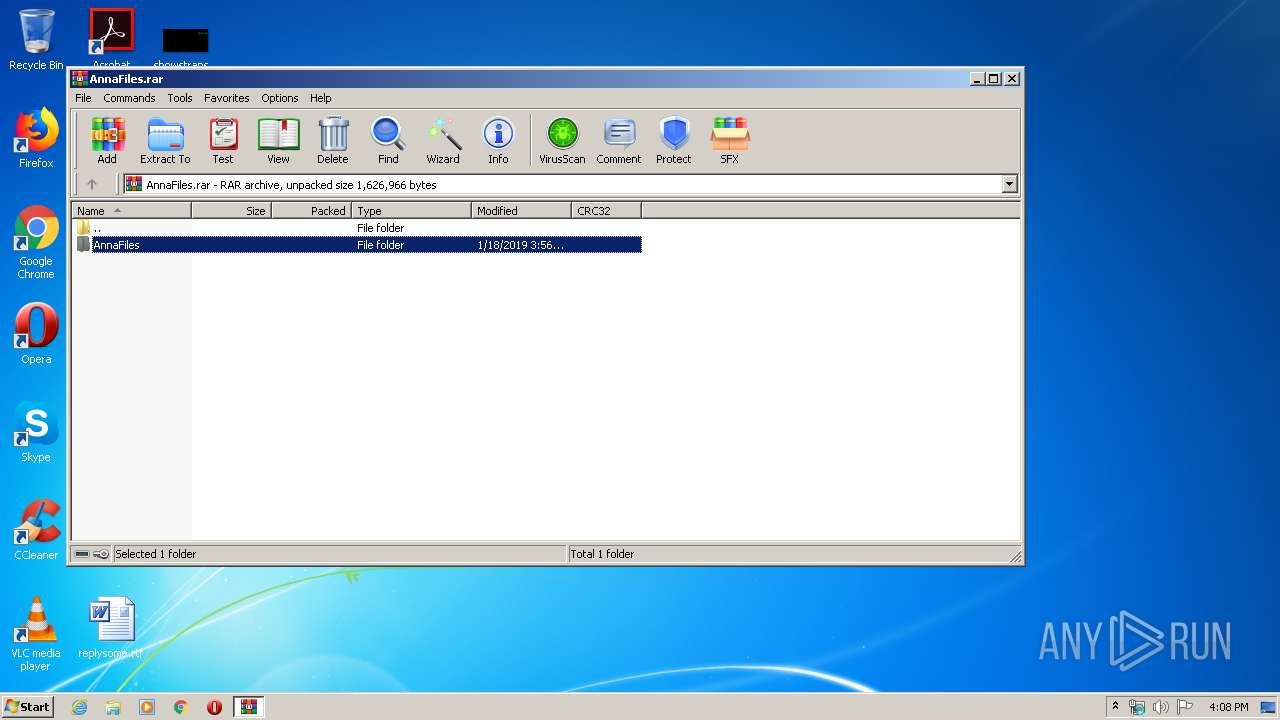
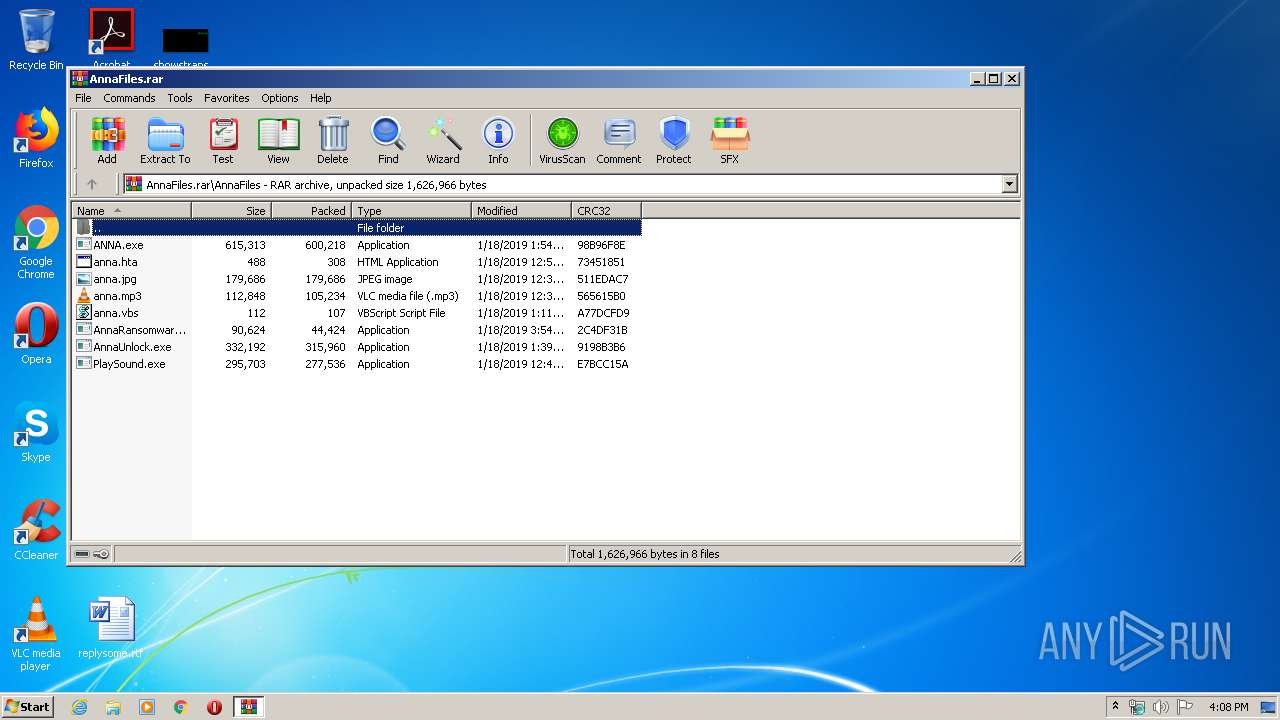
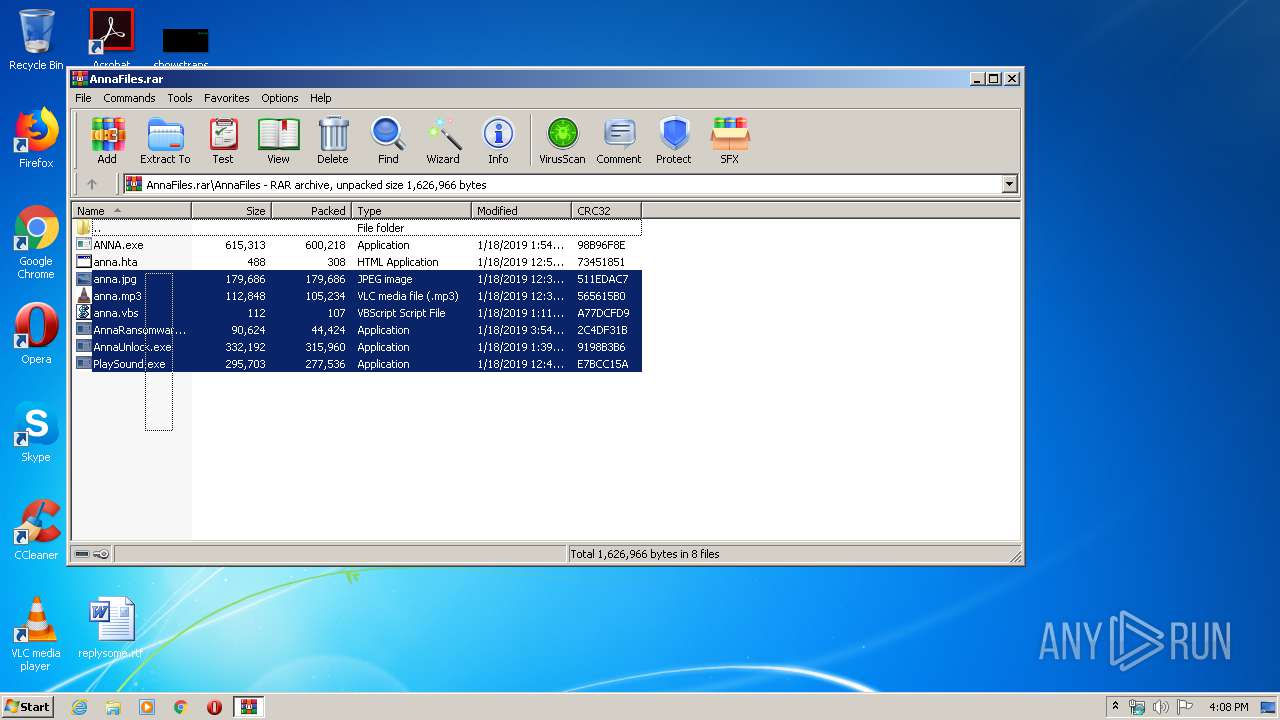
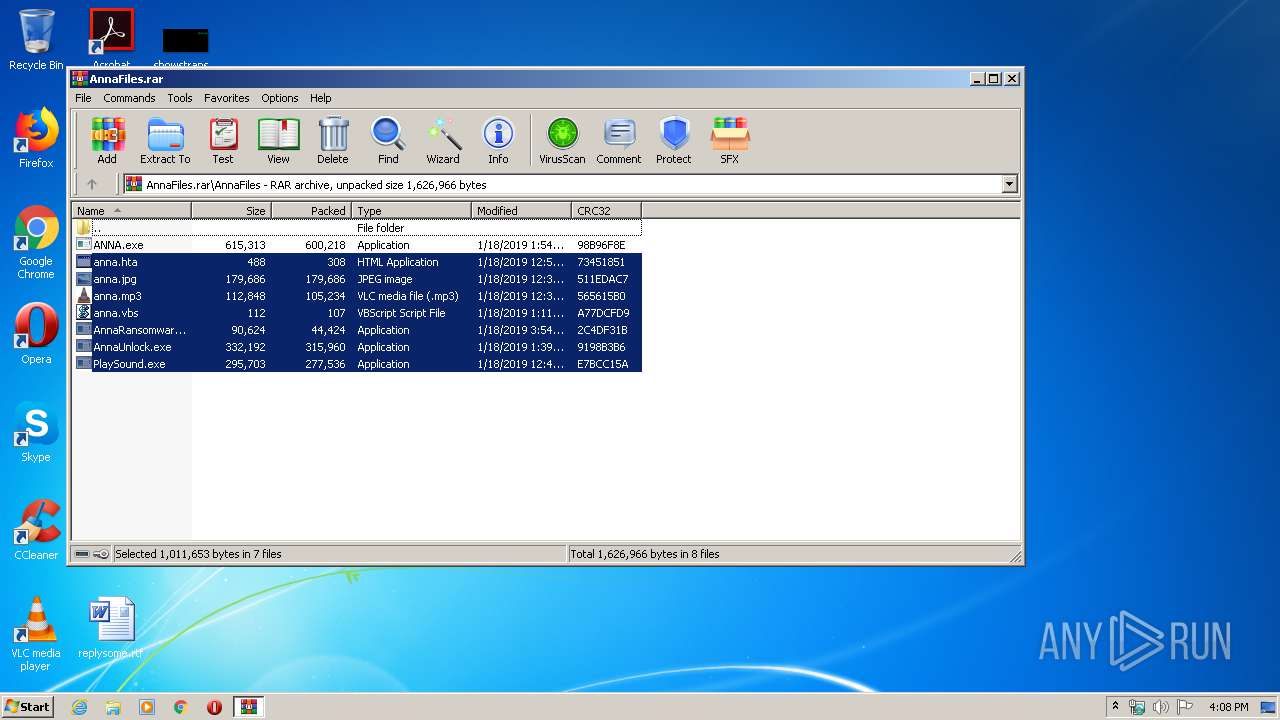
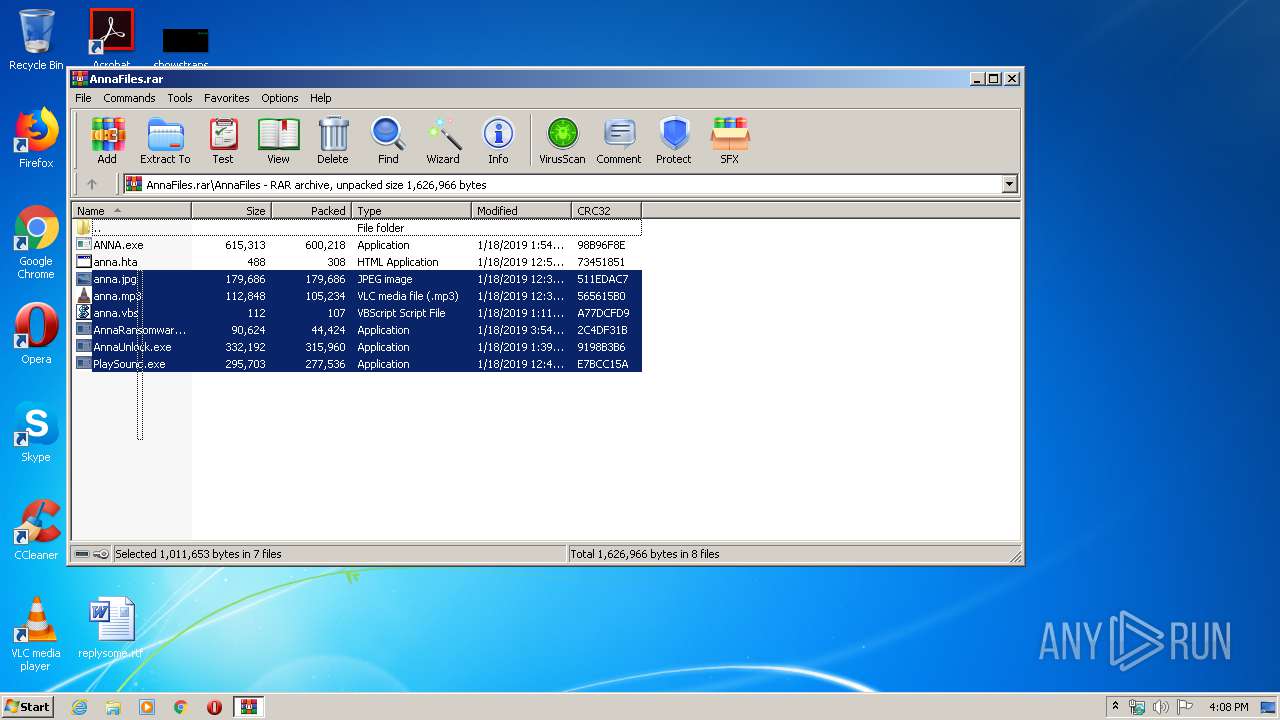
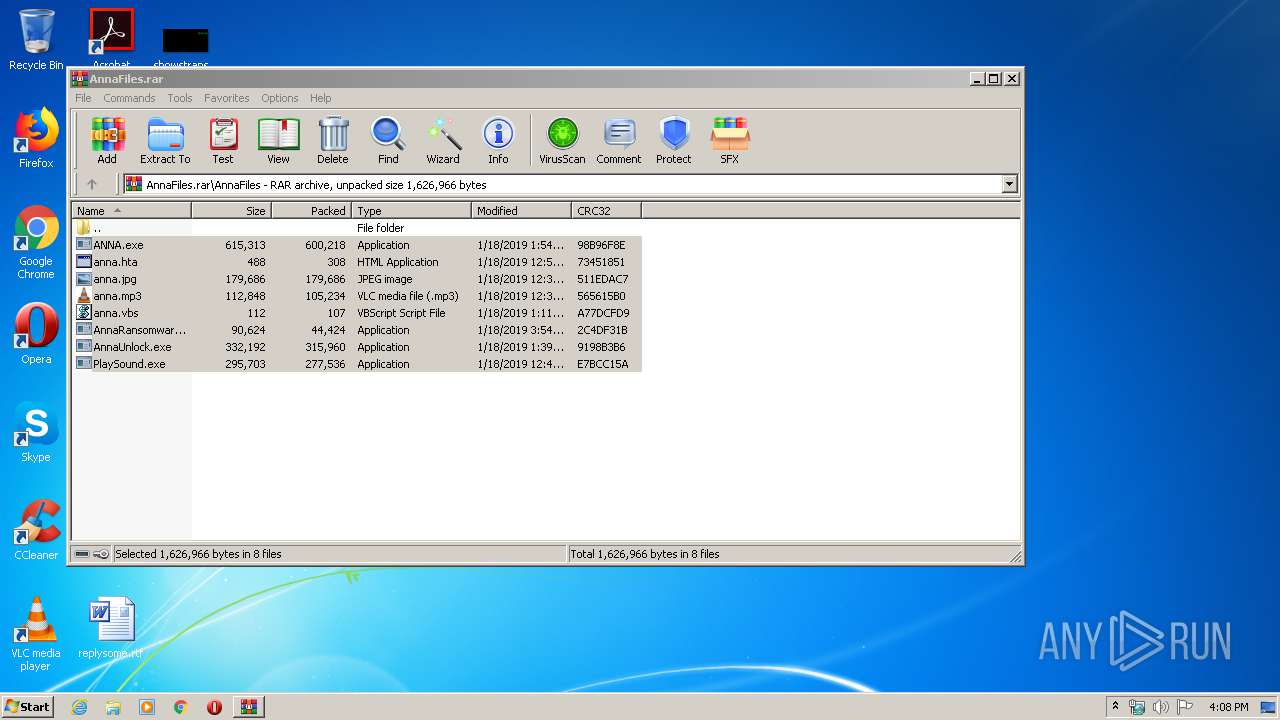
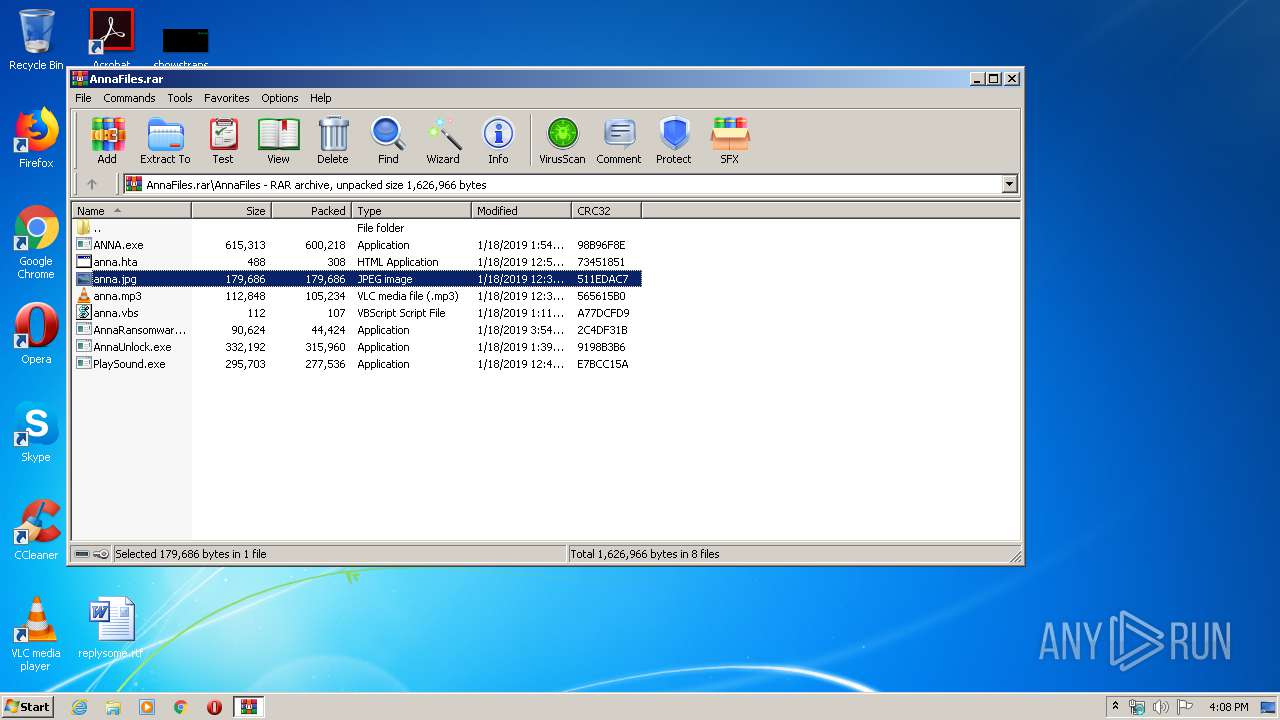
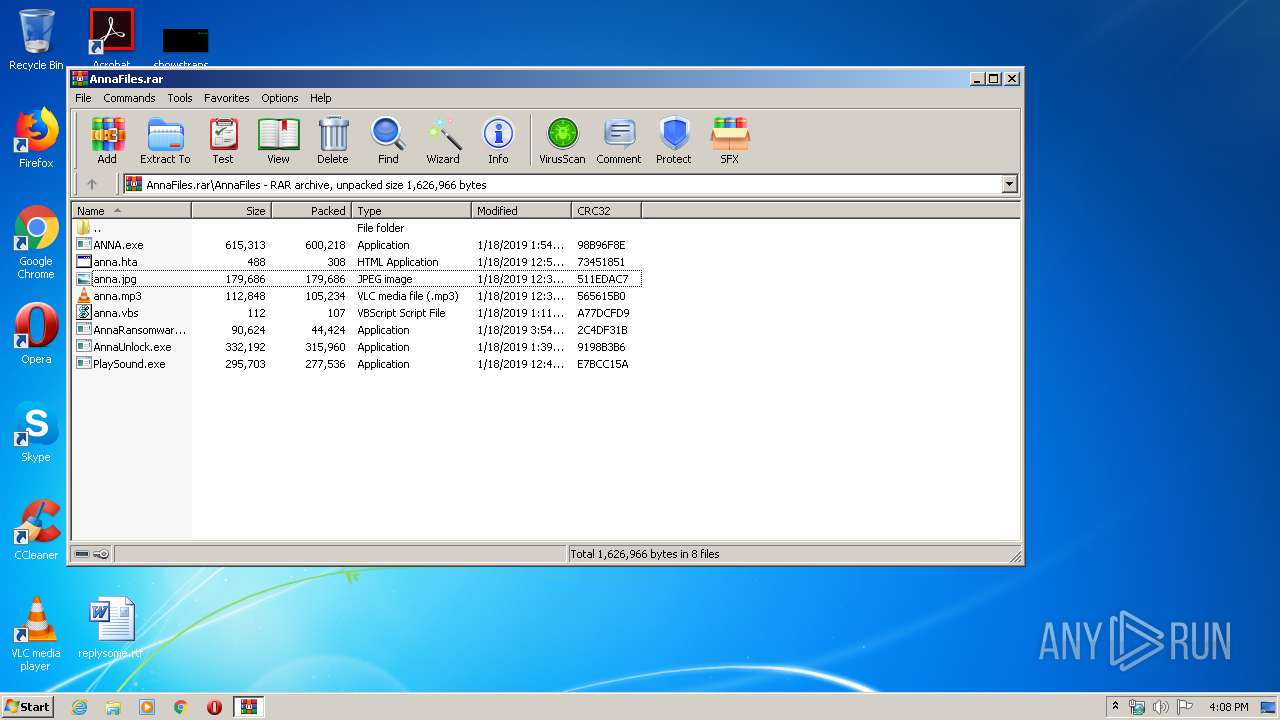
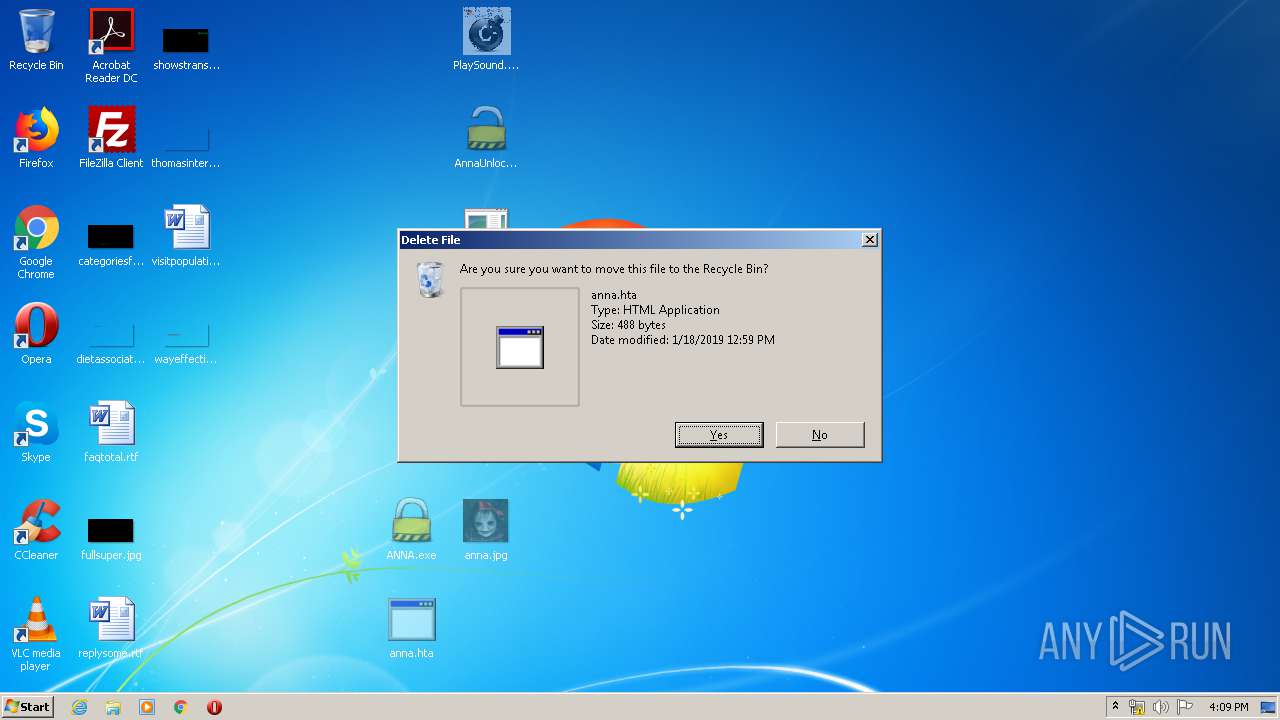
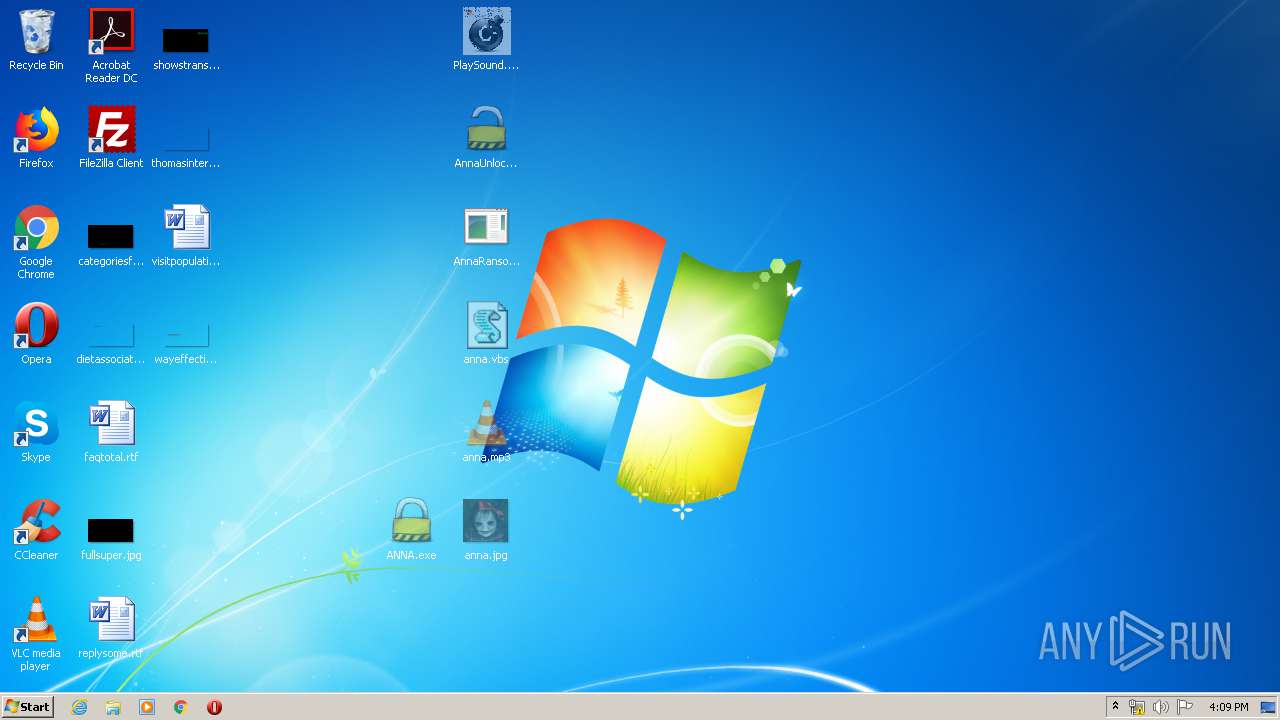
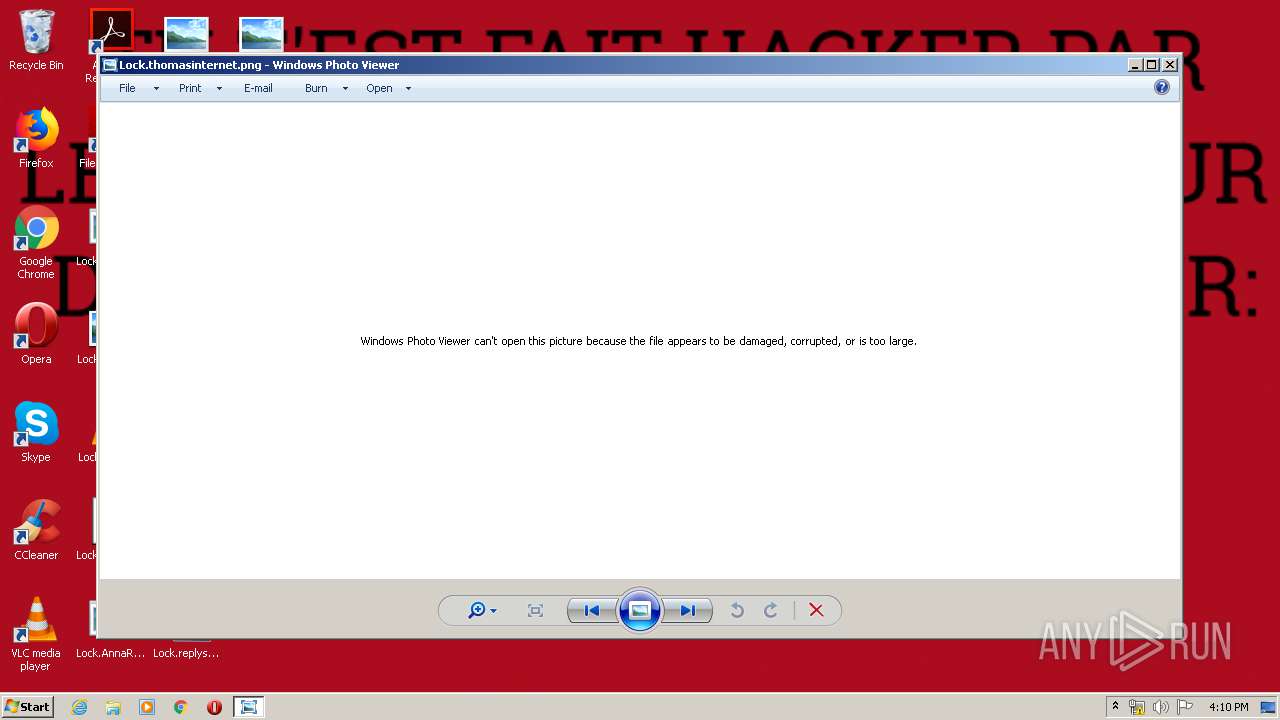
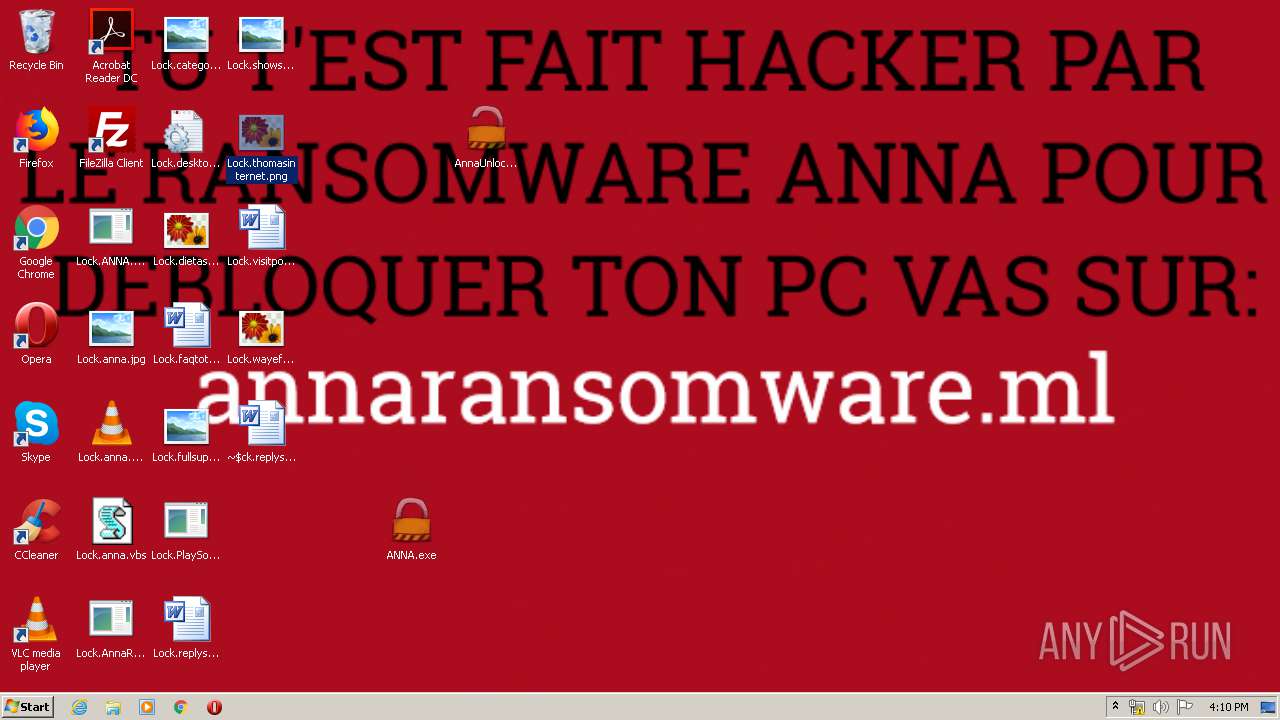
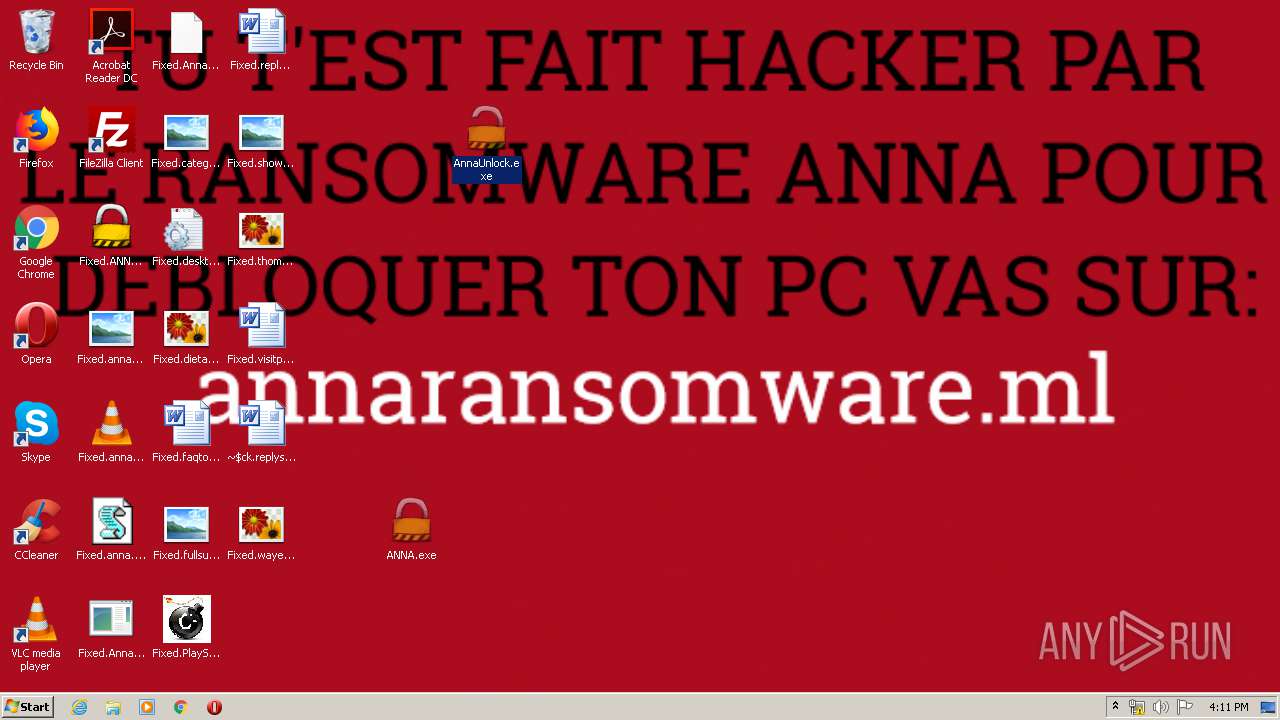
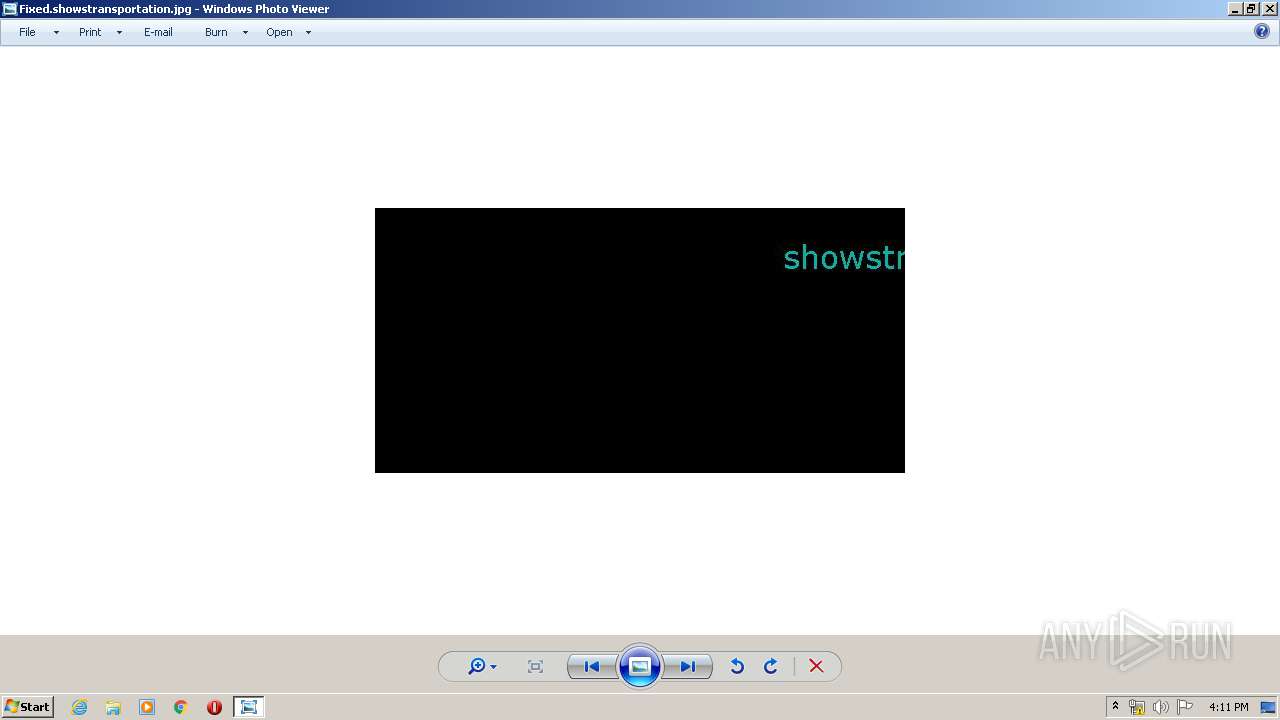
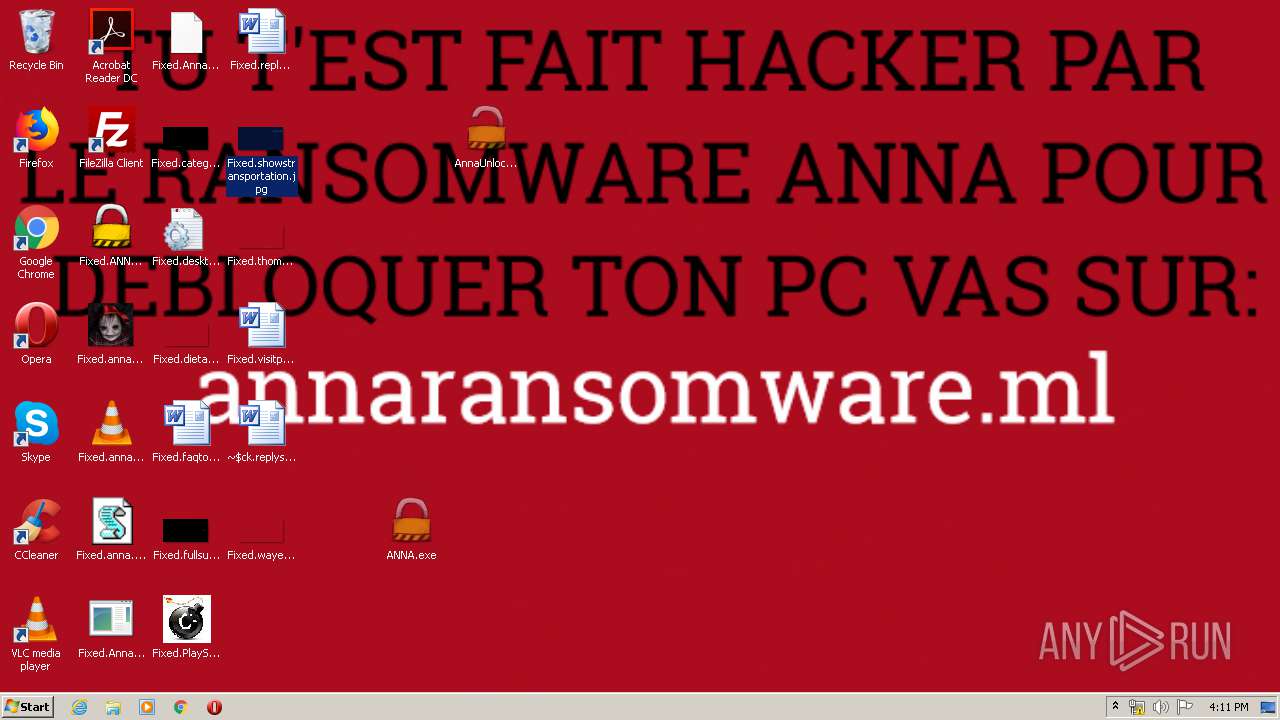
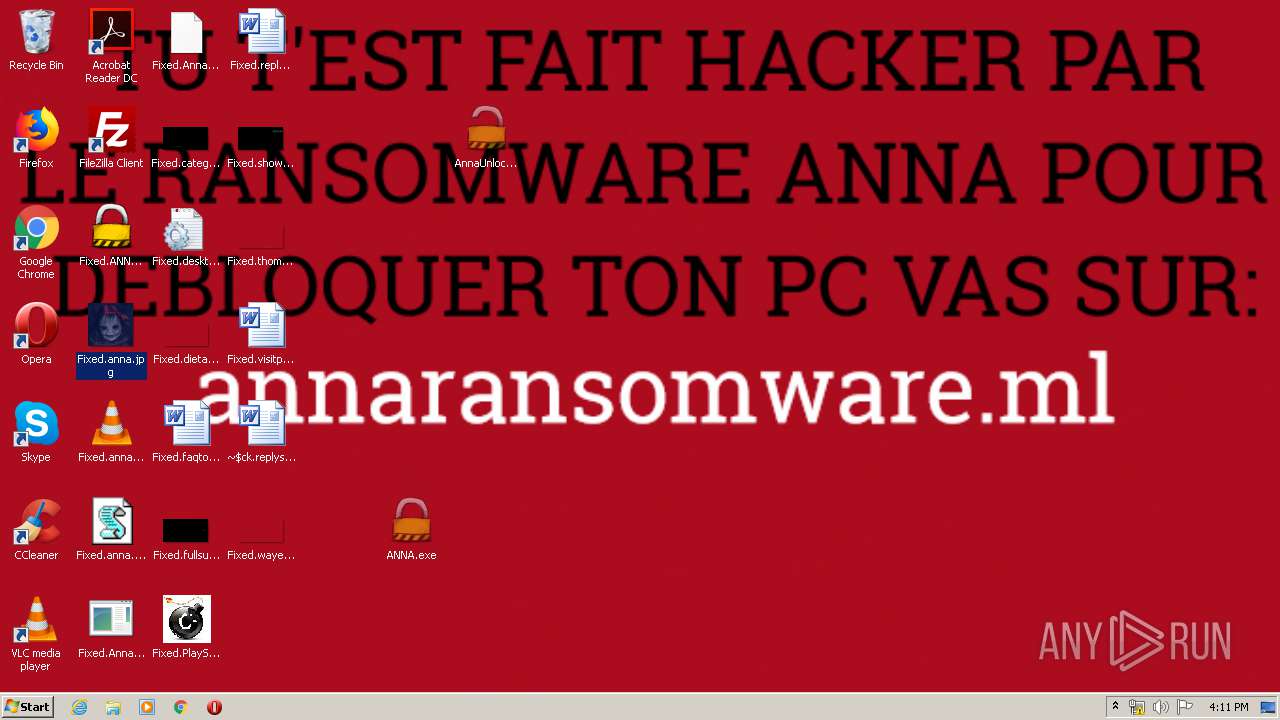
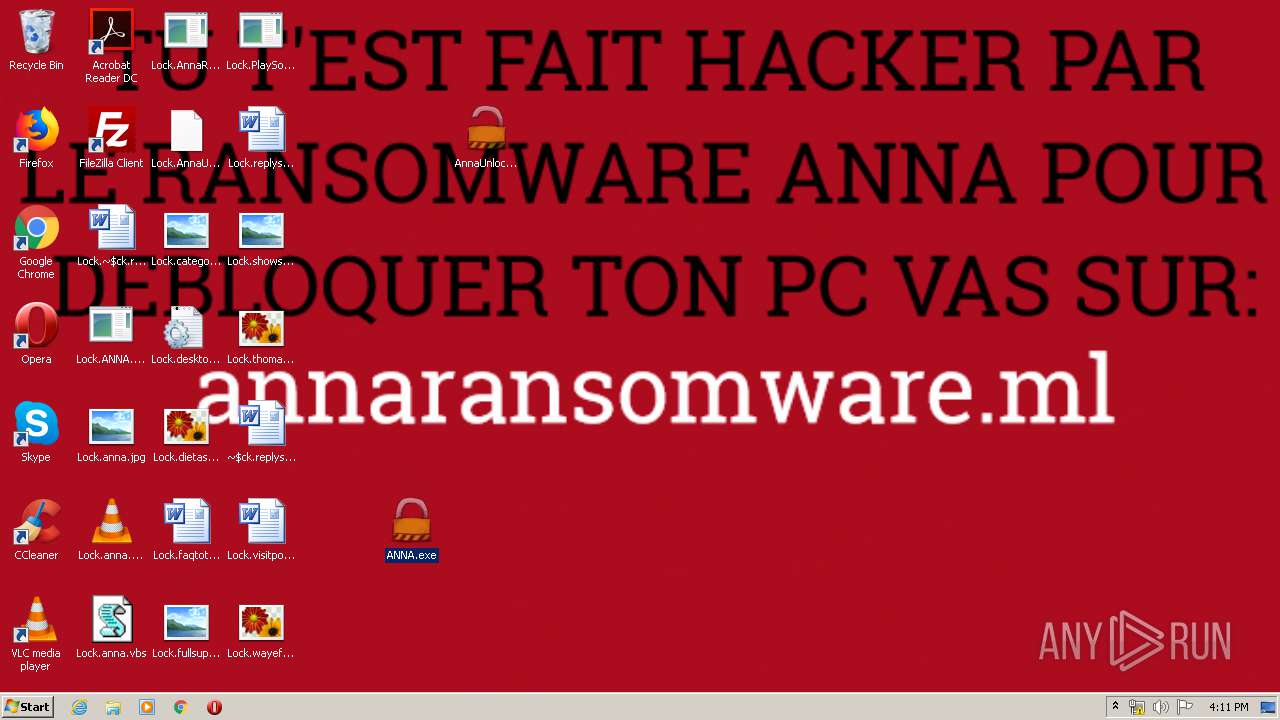
| File name: | AnnaFiles.rar |
| Full analysis: | https://app.any.run/tasks/3f0afb3f-ad1e-4dbe-93ca-c18f6986a109 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 15:07:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 56821674504A524718BE28502C0204AE |
| SHA1: | F61293224B7D50E4A112767EE25A9FAE5EC3C464 |
| SHA256: | C1253A3614B07A7E5380158CEA625597662177EC58551E884BB284CD51A6A195 |
| SSDEEP: | 24576:M2oAUeQnhJMkyDUo5n91glEtNLE3e6faWshBmn725w4384fQVB3Rhqp4DxEsRC56:M25UeQLlS591zLE3rfaDhcn725w43Pez |
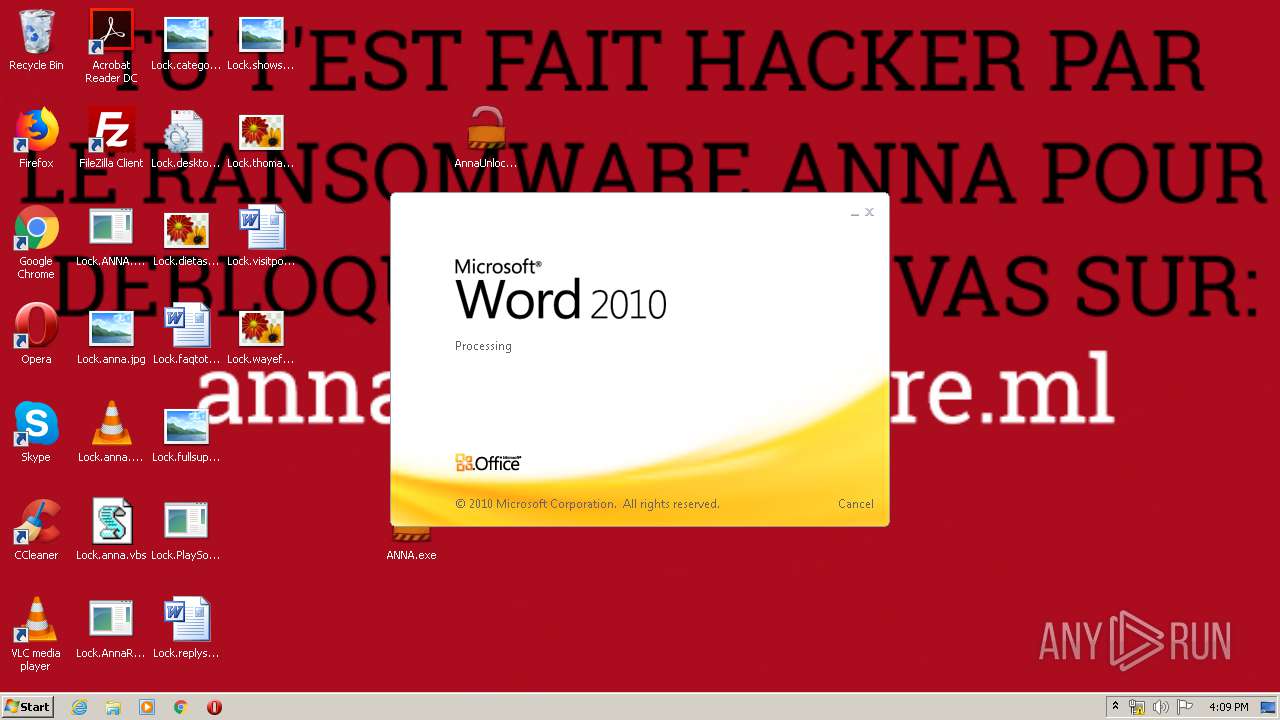
MALICIOUS
Application was dropped or rewritten from another process
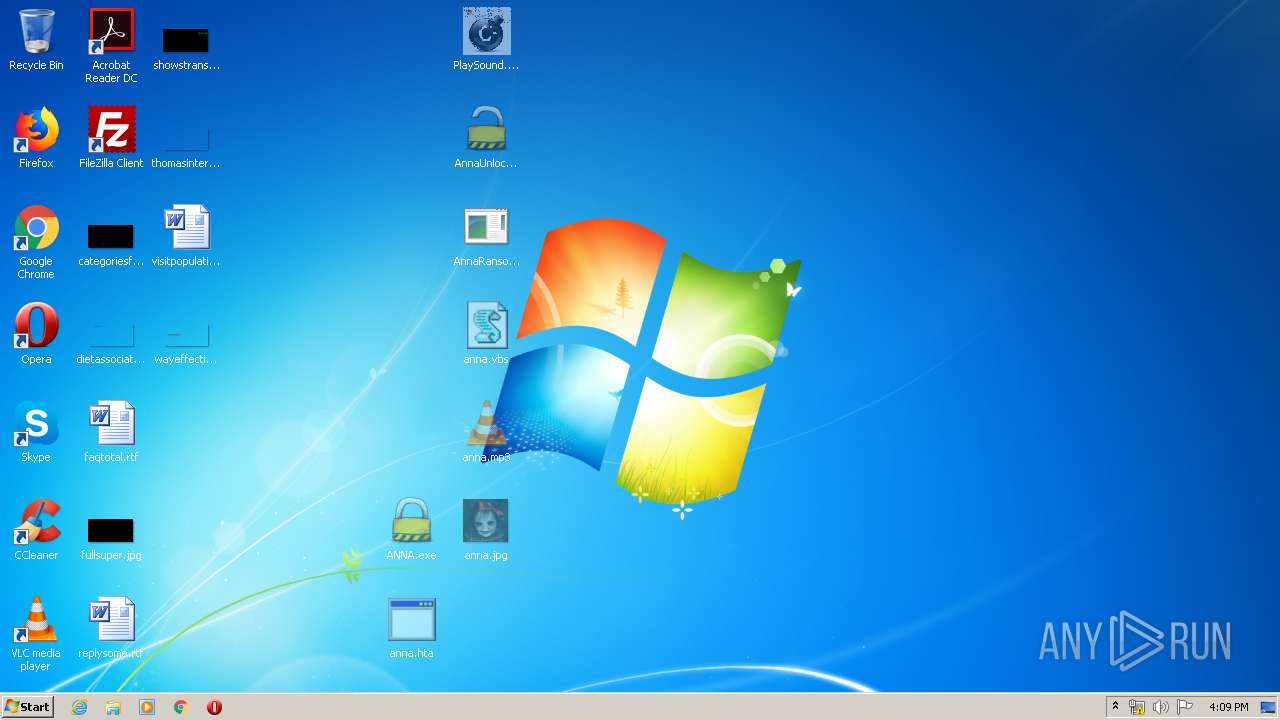
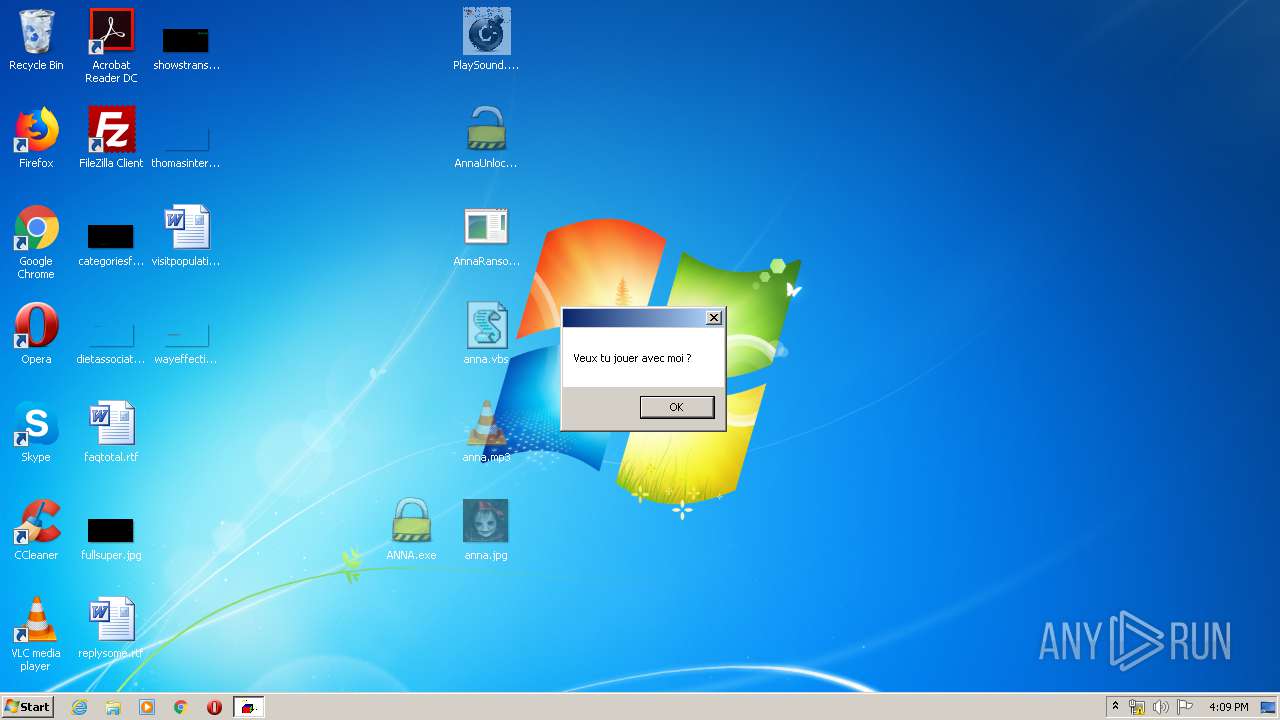
- AnnaRansomware.exe (PID: 1632)
- ANNA.exe (PID: 2840)
- ANNA.exe (PID: 332)
- AnnaUnlock.exe (PID: 2408)
- AnnaUnlock.exe (PID: 2580)
- PlaySound.exe (PID: 3612)
Loads dropped or rewritten executable
- migwiz.exe (PID: 3912)
- migwiz.exe (PID: 2636)
UAC/LUA settings modification
- reg.exe (PID: 3764)
- reg.exe (PID: 1392)
SUSPICIOUS
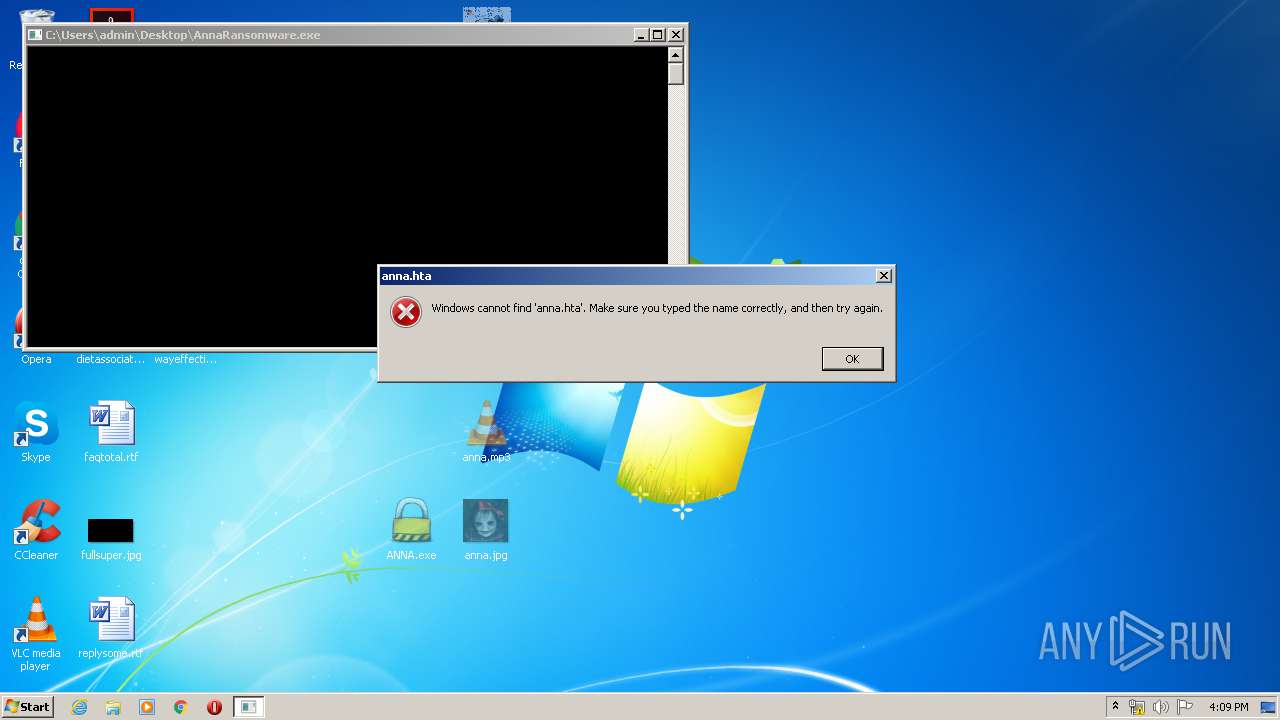
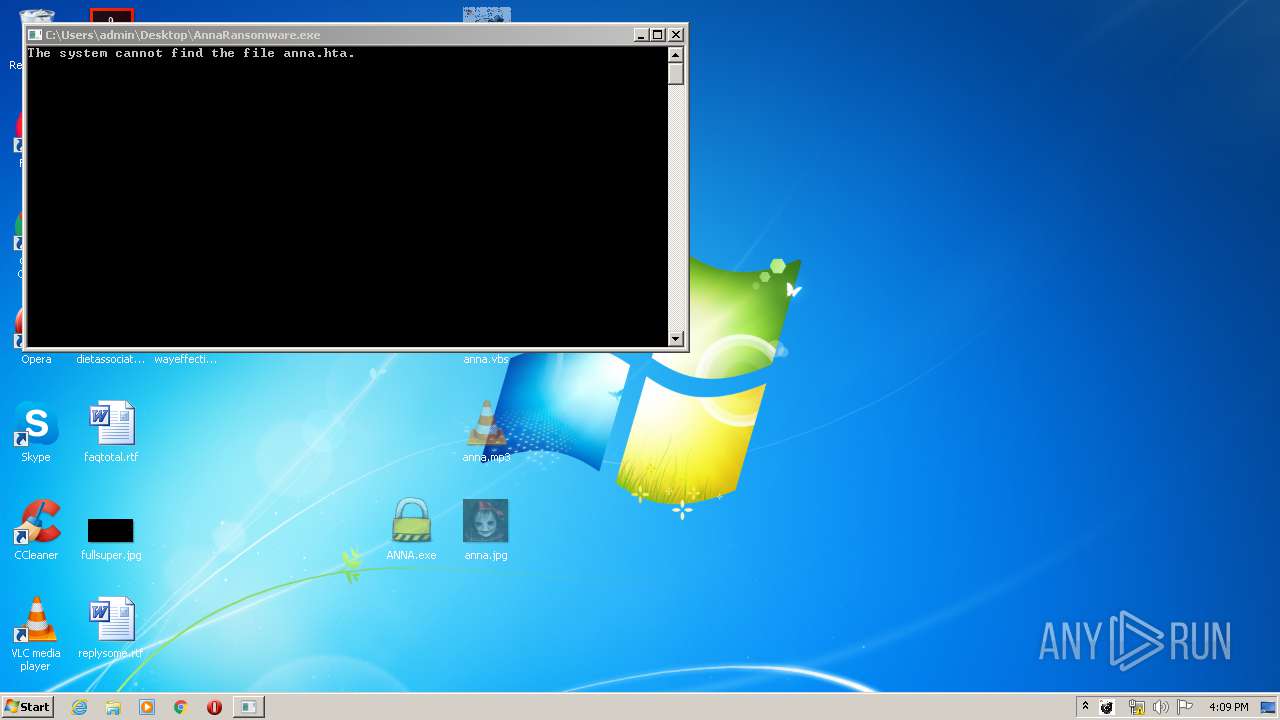
Starts CMD.EXE for commands execution
- AnnaRansomware.exe (PID: 1632)
- ANNA.exe (PID: 2840)
- migwiz.exe (PID: 3912)
- ANNA.exe (PID: 332)
- migwiz.exe (PID: 2636)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 660)
- wusa.exe (PID: 1448)
- AnnaUnlock.exe (PID: 2408)
- AnnaUnlock.exe (PID: 2580)
- wusa.exe (PID: 2452)
Executes scripts
- cmd.exe (PID: 852)
- ANNA.exe (PID: 2840)
- ANNA.exe (PID: 332)
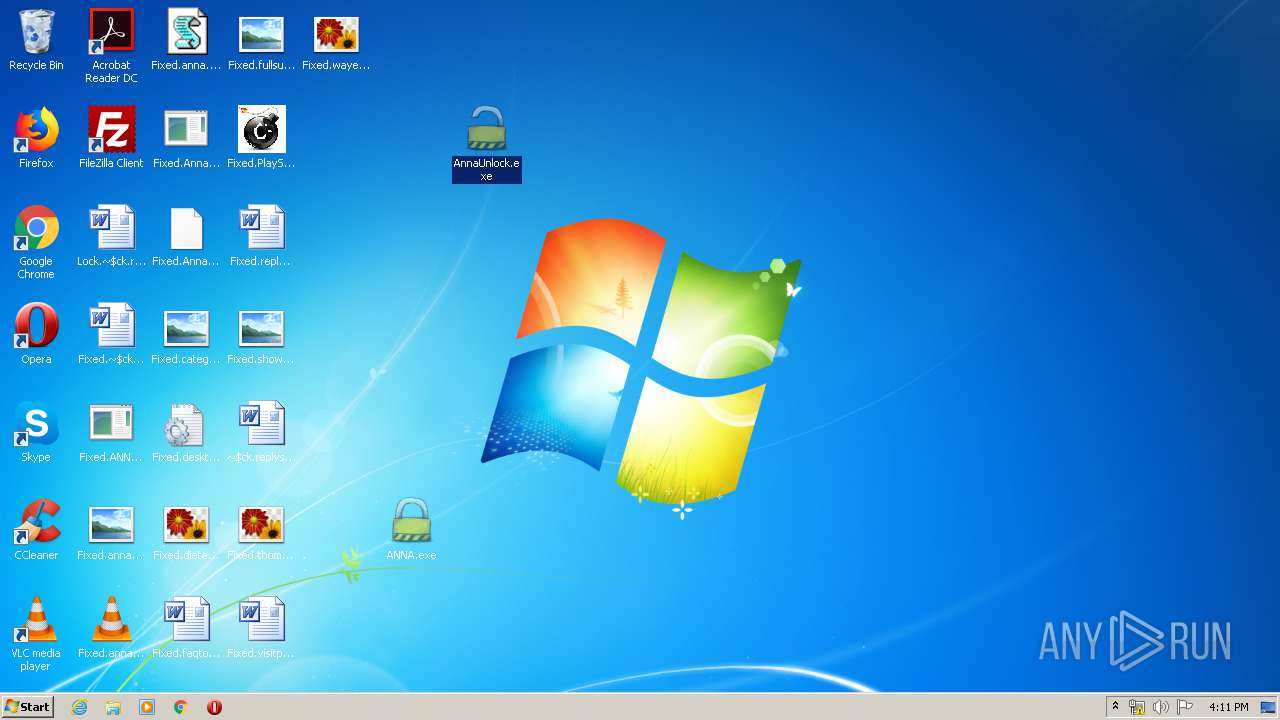
Creates files in the Windows directory
- wusa.exe (PID: 1448)
- wusa.exe (PID: 2452)
Removes files from Windows directory
- wusa.exe (PID: 1448)
- wusa.exe (PID: 2452)
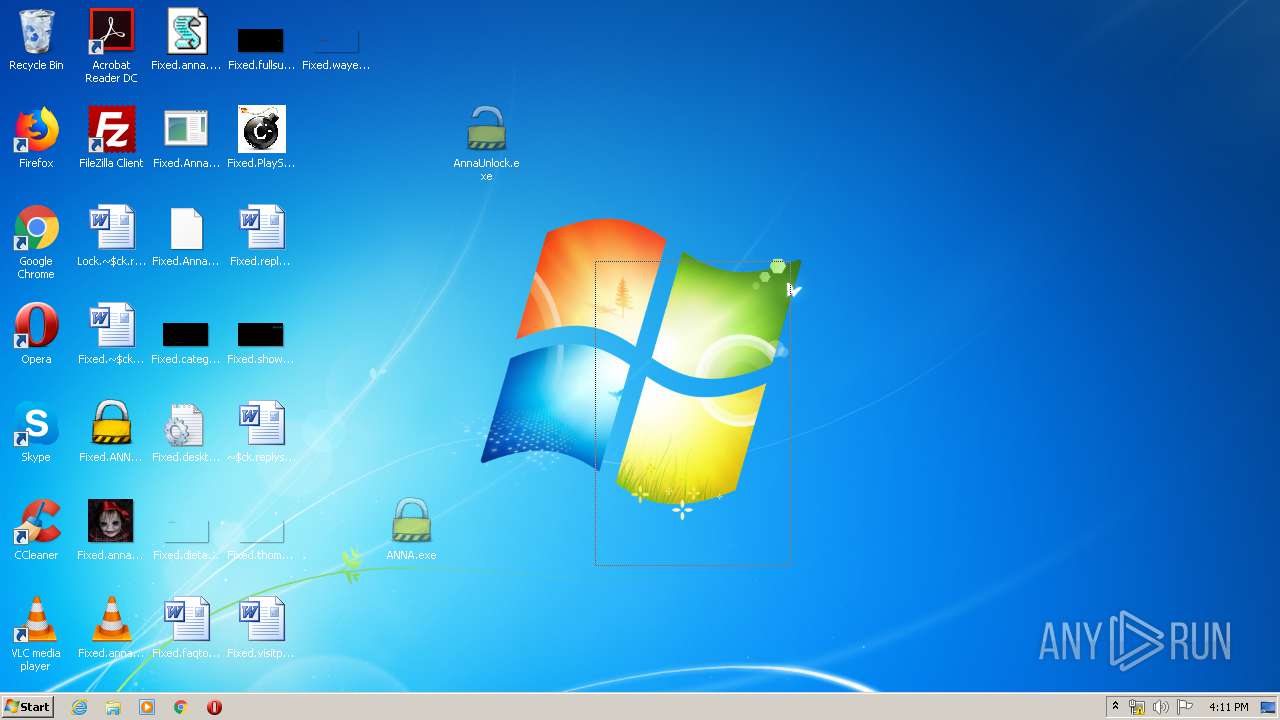
Writes to a desktop.ini file (may be used to cloak folders)
- ANNA.exe (PID: 2840)
- AnnaUnlock.exe (PID: 2408)
- ANNA.exe (PID: 332)
- AnnaUnlock.exe (PID: 2580)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 1356)
- cmd.exe (PID: 3820)
Executed via COM
- DllHost.exe (PID: 1748)
- DllHost.exe (PID: 3976)
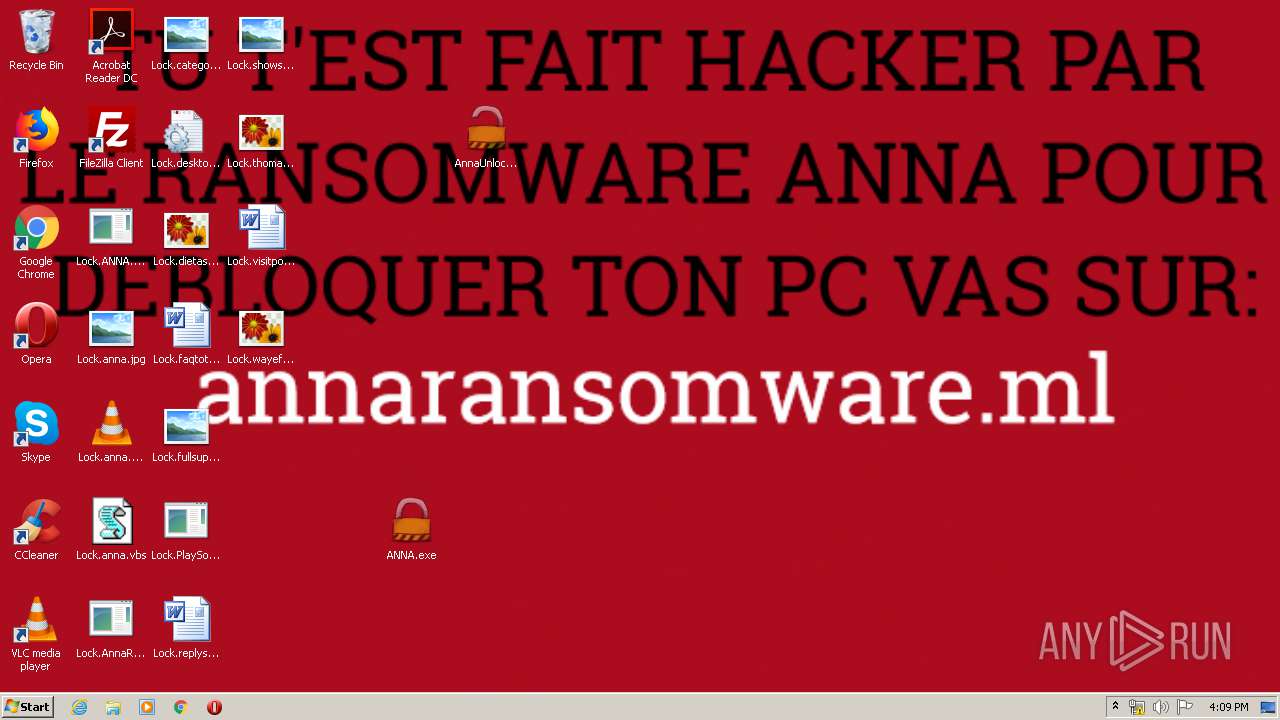
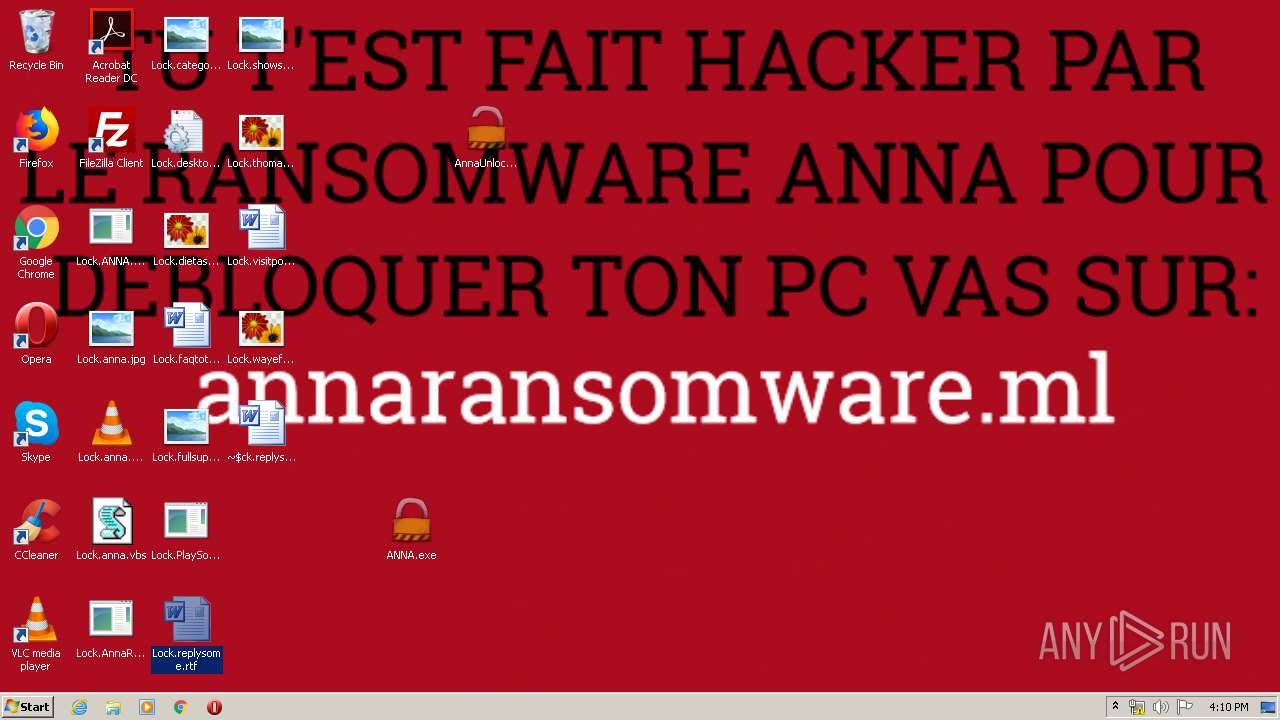
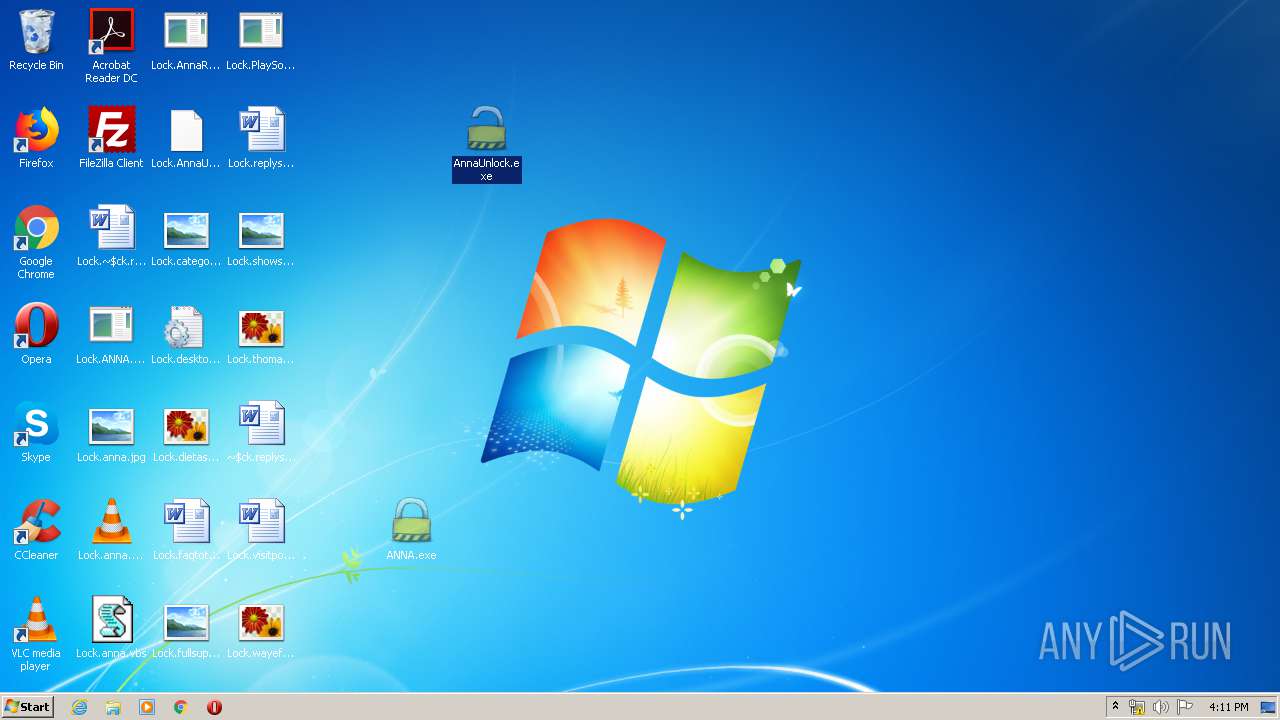
Changes the desktop background image
- AnnaUnlock.exe (PID: 2408)
- ANNA.exe (PID: 332)
- AnnaUnlock.exe (PID: 2580)
- ANNA.exe (PID: 2840)
INFO
Manual execution by user
- AnnaRansomware.exe (PID: 1632)
- WINWORD.EXE (PID: 2768)
- chrome.exe (PID: 404)
- ANNA.exe (PID: 332)
- AnnaUnlock.exe (PID: 2408)
- WINWORD.EXE (PID: 2780)
- AnnaUnlock.exe (PID: 2580)
Application launched itself
- chrome.exe (PID: 404)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2768)
- WINWORD.EXE (PID: 2780)
Creates files in the user directory
- WINWORD.EXE (PID: 2768)
- WINWORD.EXE (PID: 2780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
93
Monitored processes
34
Malicious processes
5
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | "C:\Users\admin\Desktop\ANNA.exe" | C:\Users\admin\Desktop\ANNA.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | explorer.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 660 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\AnnaFiles.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 852 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\795A.tmp\795B.tmp\795C.bat C:\Users\admin\Desktop\AnnaRansomware.exe" | C:\Windows\system32\cmd.exe | — | AnnaRansomware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1228 | "C:\Windows\system32\wusa.exe" C:\Users\admin\AppData\Local\Temp\32.cab /quiet /extract:C:\Windows\system32\migwiz\ | C:\Windows\system32\wusa.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Update Standalone Installer Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | C:\Windows\System32\cmd.exe /c C:\Windows\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\cmd.exe | — | migwiz.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1392 | C:\Windows\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1448 | "C:\Windows\system32\wusa.exe" C:\Users\admin\AppData\Local\Temp\32.cab /quiet /extract:C:\Windows\system32\migwiz\ | C:\Windows\system32\wusa.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Standalone Installer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1632 | "C:\Users\admin\Desktop\AnnaRansomware.exe" | C:\Users\admin\Desktop\AnnaRansomware.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1748 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 872
Read events
2 963
Write events
514
Delete events
395
Modification events
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AnnaFiles.rar | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\mshta.exe,-6412 |
Value: HTML Application | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
12
Suspicious files
79
Text files
76
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | ANNA.exe | C:\Users\admin\AppData\Local\Temp\autB384.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | ANNA.exe | C:\Users\admin\AppData\Local\Temp\ynoldsx | — | |
MD5:— | SHA256:— | |||
| 2840 | ANNA.exe | C:\Users\admin\AppData\Local\Temp\autB395.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | ANNA.exe | C:\Users\admin\AppData\Local\Temp\autB3A6.tmp | — | |
MD5:— | SHA256:— | |||
| 1448 | wusa.exe | C:\Windows\system32\migwiz\$dpx$.tmp\a3cd2847f701704fa1fa9ceecf2092a7.tmp | — | |
MD5:— | SHA256:— | |||
| 1448 | wusa.exe | C:\Windows\Logs\DPX\setuperr.log | — | |
MD5:— | SHA256:— | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.27332\AnnaFiles\ANNA.exe | executable | |
MD5:— | SHA256:— | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.27332\AnnaFiles\AnnaRansomware.exe | executable | |
MD5:— | SHA256:— | |||
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.27332\AnnaFiles\anna.vbs | text | |
MD5:— | SHA256:— | |||
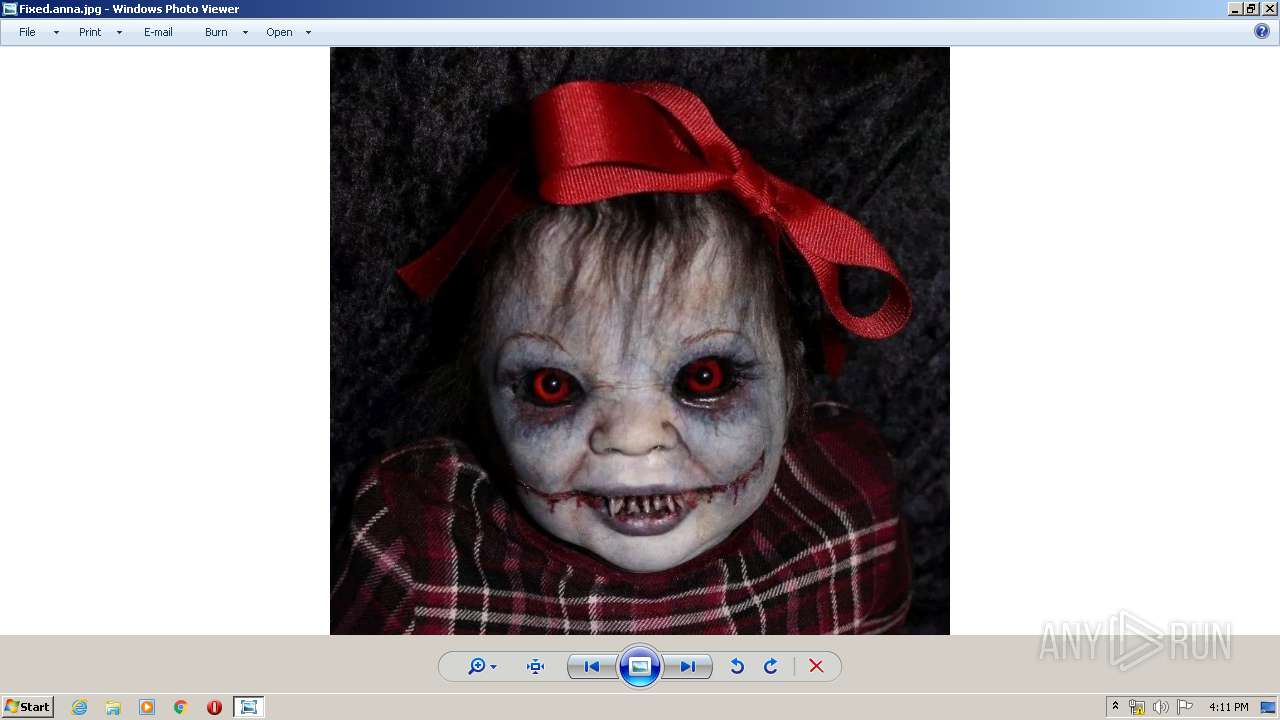
| 660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa660.27332\AnnaFiles\anna.jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report