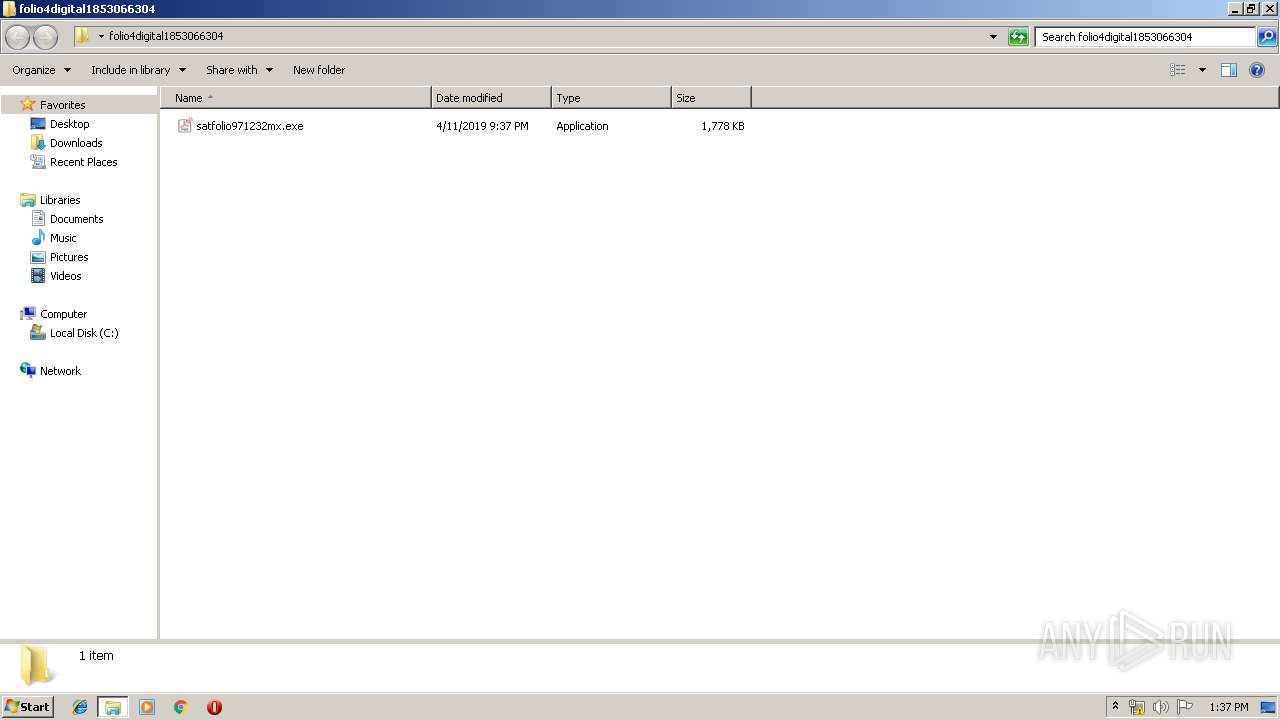
| File name: | folio4digital1853066304.zip |
| Full analysis: | https://app.any.run/tasks/31454ed7-12dc-48ad-ac3b-ca8e79d51334 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | April 15, 2019, 12:37:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 5E9FADB147C76CDF4D47222A3BCC99E7 |
| SHA1: | 5AB3A0F44D306707F10AB1521EB9BBBAAD27E6B0 |
| SHA256: | C1145C022E49492E2EC736A7391EB44E95D9EED6D582FBE6D87FB659C1776A88 |
| SSDEEP: | 12288:ru0zOSY9oS1DTAK6+O890gfSt8AgFsfSfee+ZTUDrPEDPXGLYIN+:ru39oSdTAWO806SiAIjIXhD |
MALICIOUS
Application was dropped or rewritten from another process
- satfolio971232mx.exe (PID: 1820)
Changes settings of System certificates
- satfolio971232mx.exe (PID: 1820)
Writes to a start menu file
- hardMN5sumer.exe (PID: 2460)
Stealing of credential data
- hardMN5sumer.exe (PID: 2460)
Loads dropped or rewritten executable
- hardMN5sumer.exe (PID: 2460)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1432)
- hardMN5sumer.exe (PID: 2460)
Adds / modifies Windows certificates
- satfolio971232mx.exe (PID: 1820)
Starts Internet Explorer
- satfolio971232mx.exe (PID: 1820)
Creates files in the user directory
- satfolio971232mx.exe (PID: 1820)
- hardMN5sumer.exe (PID: 2460)
Reads internet explorer settings
- satfolio971232mx.exe (PID: 1820)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 1704)
Reads Internet Cache Settings
- iexplore.exe (PID: 1704)
Changes internet zones settings
- iexplore.exe (PID: 3652)
Creates files in the user directory
- iexplore.exe (PID: 1704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
Total processes
38
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1432 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\folio4digital1853066304.zip" C:\Users\admin\Desktop\folio4digital1853066304\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3652 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\Desktop\folio4digital1853066304\satfolio971232mx.exe" | C:\Users\admin\Desktop\folio4digital1853066304\satfolio971232mx.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2088 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\folio4digital1853066304.zip.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2460 | "C:\Users\admin\AppData\Roaming\TadminII\hardMN5sumer.exe" | C:\Users\admin\AppData\Roaming\TadminII\hardMN5sumer.exe | satfolio971232mx.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3652 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | satfolio971232mx.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 263
Read events
1 150
Write events
109
Delete events
4
Modification events
| (PID) Process: | (2088) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 132 | |||
| (PID) Process: | (2088) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 132 | |||
| (PID) Process: | (2088) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (2088) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
4
Text files
19
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1704 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\W1489E6G\ErrorPageTemplate[1] | text | |
MD5:F4FE1CB77E758E1BA56B8A8EC20417C5 | SHA256:8D018639281B33DA8EB3CE0B21D11E1D414E59024C3689F92BE8904EB5779B5F | |||
| 1704 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\UAI16QC6\dnserror[1] | html | |
MD5:68E03ED57EC741A4AFBBCD11FAB1BDBE | SHA256:1FF3334C3EB27033F8F37029FD72F648EDD4551FCE85FC1F5159FEAEA1439630 | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Feeds Cache\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA202A602B9825E2C.TMP | — | |
MD5:— | SHA256:— | |||
| 1704 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\41DR7T87\errorPageStrings[1] | text | |
MD5:1A0563F7FB85A678771450B131ED66FD | SHA256:EB5678DE9D8F29CA6893D4E6CA79BD5AB4F312813820FE4997B009A2B1A1654C | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFAD155E7FC388658C.TMP | — | |
MD5:— | SHA256:— | |||
| 1704 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\4SBHNZX4\httpErrorPagesScripts[1] | text | |
MD5:E7CA76A3C9EE0564471671D500E3F0F3 | SHA256:58268CA71A28973B756A48BBD7C9DC2F6B87B62AE343E582CE067C725275B63C | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF4236828ADF2D0B5.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
8
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1820 | satfolio971232mx.exe | GET | 200 | 23.229.232.7:80 | http://shcpsatgobmxfoliofiscal.com/contador/index.php | US | — | — | malicious |
3652 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
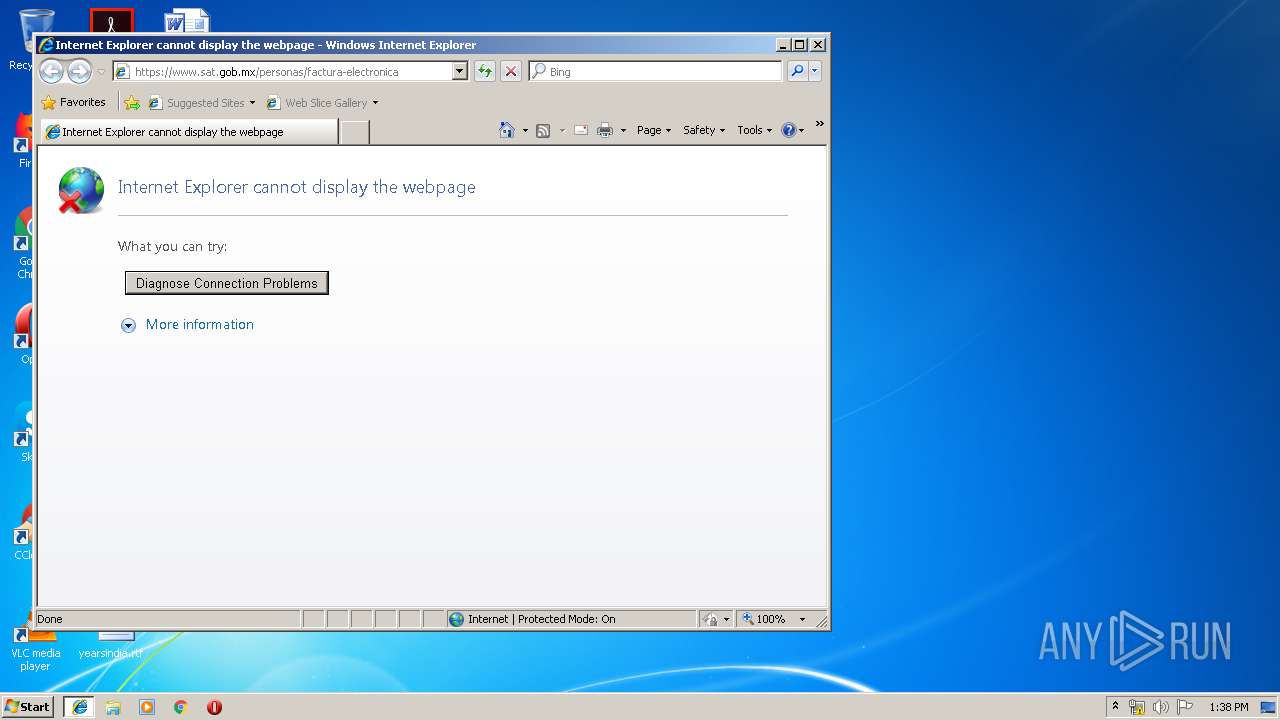
1704 | iexplore.exe | 13.32.219.100:443 | www.sat.gob.mx | Amazon.com, Inc. | US | unknown |
2460 | hardMN5sumer.exe | 18.231.115.111:8890 | chbu4889a03kashtoas.hopto.org | Amazon.com, Inc. | BR | unknown |
3652 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1820 | satfolio971232mx.exe | 52.95.165.50:443 | s3-sa-east-1.amazonaws.com | — | US | shared |
1820 | satfolio971232mx.exe | 23.229.232.7:80 | shcpsatgobmxfoliofiscal.com | GoDaddy.com, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.sat.gob.mx |
| whitelisted |
www.bing.com |
| whitelisted |
s3-sa-east-1.amazonaws.com |
| shared |
shcpsatgobmxfoliofiscal.com |
| malicious |
noismxnc8xns8ymde5.serveminecraft.net |
| unknown |
chbu4889a03kashtoas.hopto.org |
| malicious |