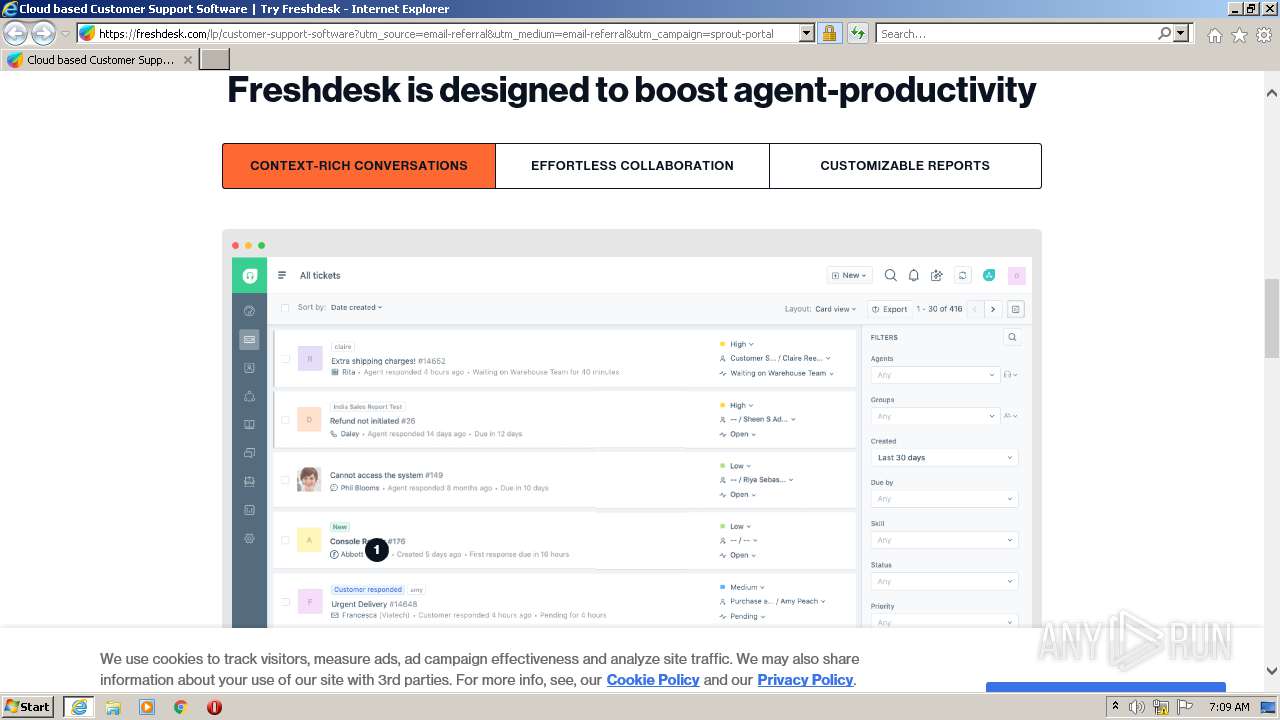
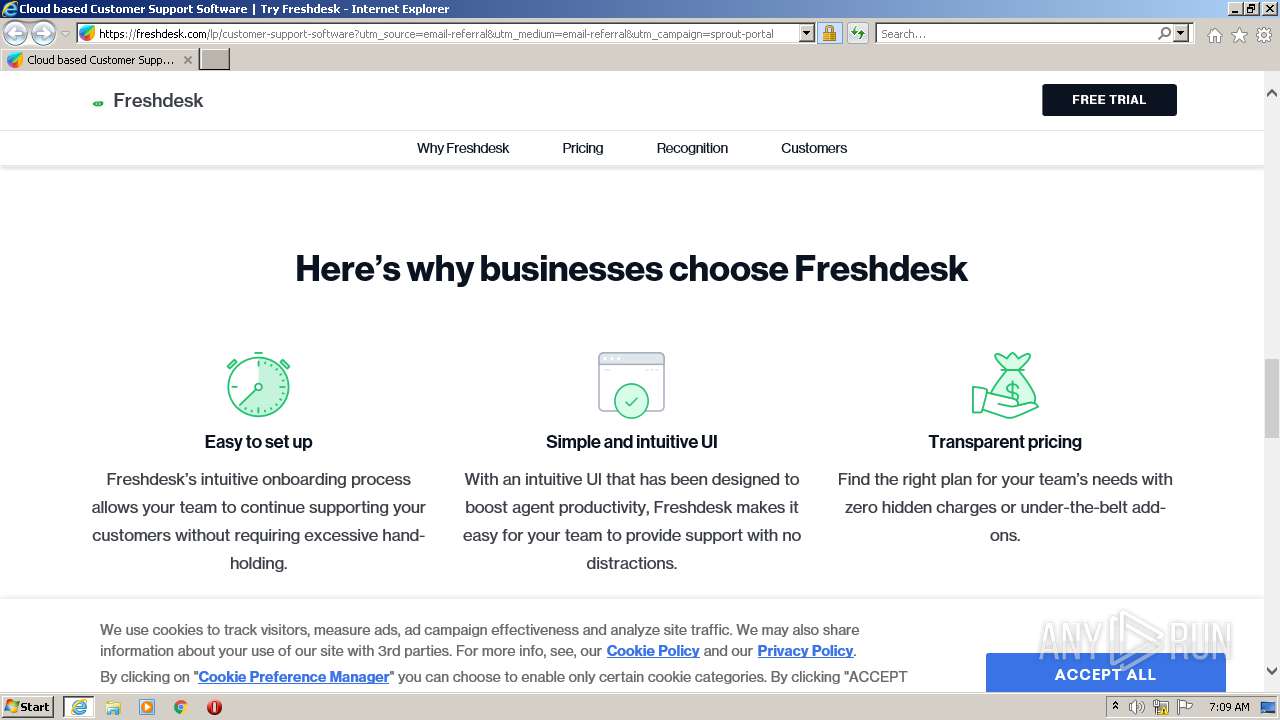
| URL: | https://emea01.safelinks.protection.outlook.com/?url=https%3A%2F%2Ffreshdesk.com%2Flp%2Fcustomer-support-software%3Futm_source%3Demail-referral%26utm_medium%3Demail-referral%26utm_campaign%3Dsprout-portal&data=04%7C01%7C%7Caa6ebe93ad68415b9d4808d97c451f7d%7C84df9e7fe9f640afb435aaaaaaaaaaaa%7C1%7C0%7C637677458587786362%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C1000&sdata=rhFtHecdvUIdE8DkUDVGy9YVuvo7X9%2B43BtslAaxLxI%3D&reserved=0 |
| Full analysis: | https://app.any.run/tasks/22dc8a6e-b9c3-4141-a71b-e0d7d6dcae7d |
| Verdict: | Malicious activity |
| Analysis date: | September 21, 2021, 06:08:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3248E7E8AFD5CD5DAE2623D5AC68663F |
| SHA1: | 5B385E11A20D849053BC6BA867652334C3BE618B |
| SHA256: | C0C29DA3F58FE40D580225424C755F1CCD6759C2D8C0AB864197C47912A5D75D |
| SSDEEP: | 12:2WhqxprGMjEXW1SN21XW18mez3TyFtEyTNKP7RltNCd:2Whq3VAX1KXRTyFthTEP7vtNCd |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2888)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 120)
Checks supported languages
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2888)
Reads the computer name
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2888)
Creates files in the user directory
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2888)
INFO
Reads the computer name
- iexplore.exe (PID: 3600)
- iexplore.exe (PID: 120)
Application launched itself
- iexplore.exe (PID: 3600)
Reads internet explorer settings
- iexplore.exe (PID: 120)
Checks supported languages
- iexplore.exe (PID: 3600)
- iexplore.exe (PID: 120)
Checks Windows Trust Settings
- iexplore.exe (PID: 3600)
- iexplore.exe (PID: 120)
Reads CPU info
- iexplore.exe (PID: 120)
Creates files in the user directory
- iexplore.exe (PID: 120)
Changes internet zones settings
- iexplore.exe (PID: 3600)
Reads settings of System Certificates
- iexplore.exe (PID: 120)
- iexplore.exe (PID: 3600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3600 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2888 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe� Flash� Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
| 3600 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://emea01.safelinks.protection.outlook.com/?url=https%3A%2F%2Ffreshdesk.com%2Flp%2Fcustomer-support-software%3Futm_source%3Demail-referral%26utm_medium%3Demail-referral%26utm_campaign%3Dsprout-portal&data=04%7C01%7C%7Caa6ebe93ad68415b9d4808d97c451f7d%7C84df9e7fe9f640afb435aaaaaaaaaaaa%7C1%7C0%7C637677458587786362%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C1000&sdata=rhFtHecdvUIdE8DkUDVGy9YVuvo7X9%2B43BtslAaxLxI%3D&reserved=0" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
19 901
Read events
19 706
Write events
195
Delete events
0
Modification events
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 457851200 | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30912175 | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 758009560 | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30912175 | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3600) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
54
Text files
195
Unknown types
75
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\620BEF1064BD8E252C599957B3C91896 | der | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | binary | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | der | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 3600 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 3600 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
202
DNS requests
83
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3600 | iexplore.exe | GET | 304 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b072fe614b297e8f | US | — | — | whitelisted |
3600 | iexplore.exe | GET | 304 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0909b505f8f582c7 | US | — | — | whitelisted |
120 | iexplore.exe | GET | 200 | 143.204.214.74:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEA5hWxGl7iUZQhOwoI7GQGk%3D | US | der | 471 b | whitelisted |
120 | iexplore.exe | GET | 200 | 143.204.101.118:80 | http://crl.rootca1.amazontrust.com/rootca1.crl | US | der | 493 b | whitelisted |
120 | iexplore.exe | GET | 200 | 143.204.101.74:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
120 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
120 | iexplore.exe | GET | 200 | 143.204.214.74:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAtu34GCoHPn%2F24dtshZTxs%3D | US | der | 471 b | whitelisted |
120 | iexplore.exe | GET | 200 | 143.204.214.74:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAs2b5qCrFdsZdoGMqFy7WE%3D | US | der | 471 b | whitelisted |
3600 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
120 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAGewca9P1l7sgwzOOVR2Hc%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
120 | iexplore.exe | 104.47.6.28:443 | emea01.safelinks.protection.outlook.com | Microsoft Corporation | US | whitelisted |
— | — | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
120 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
120 | iexplore.exe | 143.204.98.101:443 | freshdesk.com | — | US | suspicious |
120 | iexplore.exe | 13.225.84.68:80 | o.ss2.us | — | US | unknown |
120 | iexplore.exe | 143.204.101.74:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
120 | iexplore.exe | 13.32.11.60:80 | ocsp.rootca1.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
3600 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3600 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3600 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
emea01.safelinks.protection.outlook.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
freshdesk.com |
| shared |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
crl.rootca1.amazontrust.com |
| whitelisted |