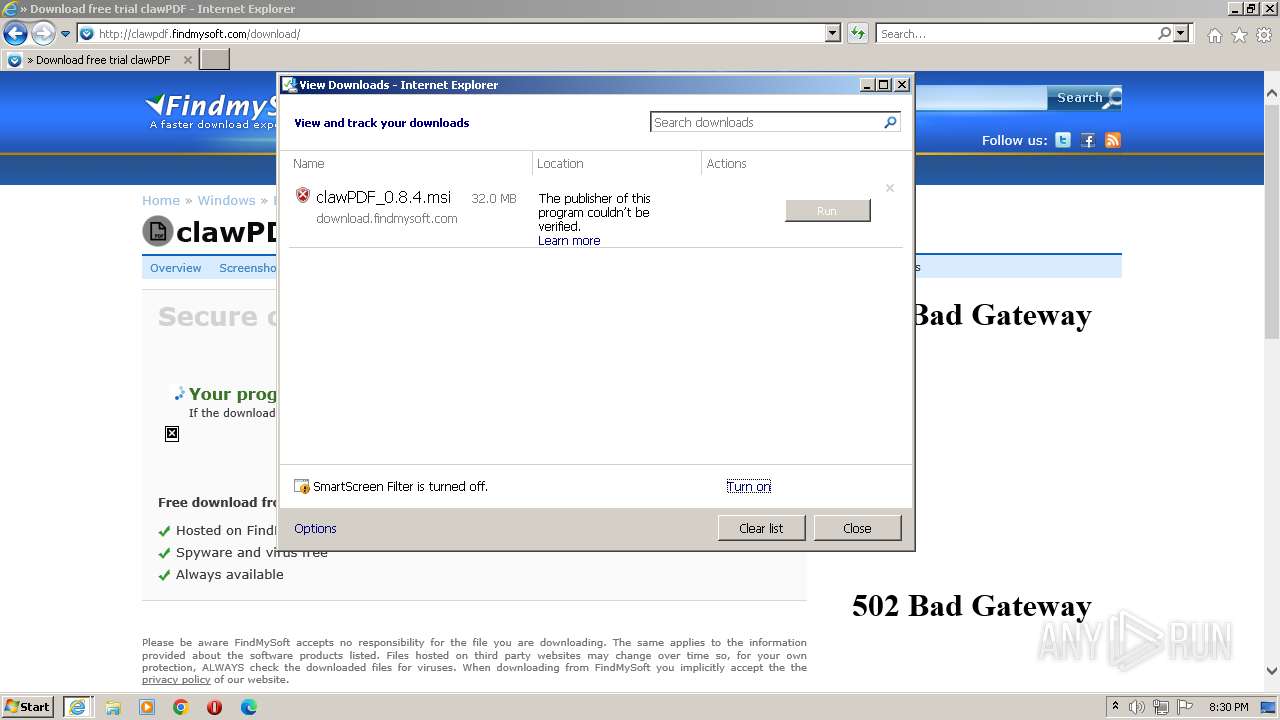
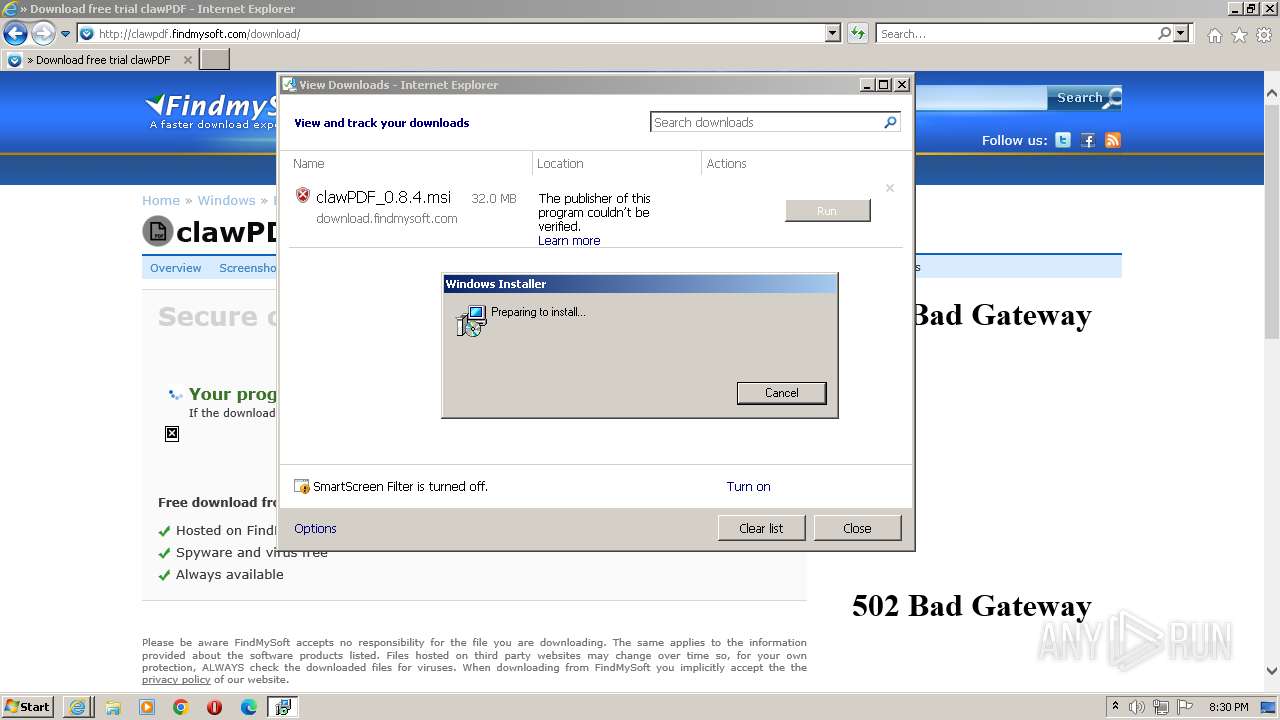
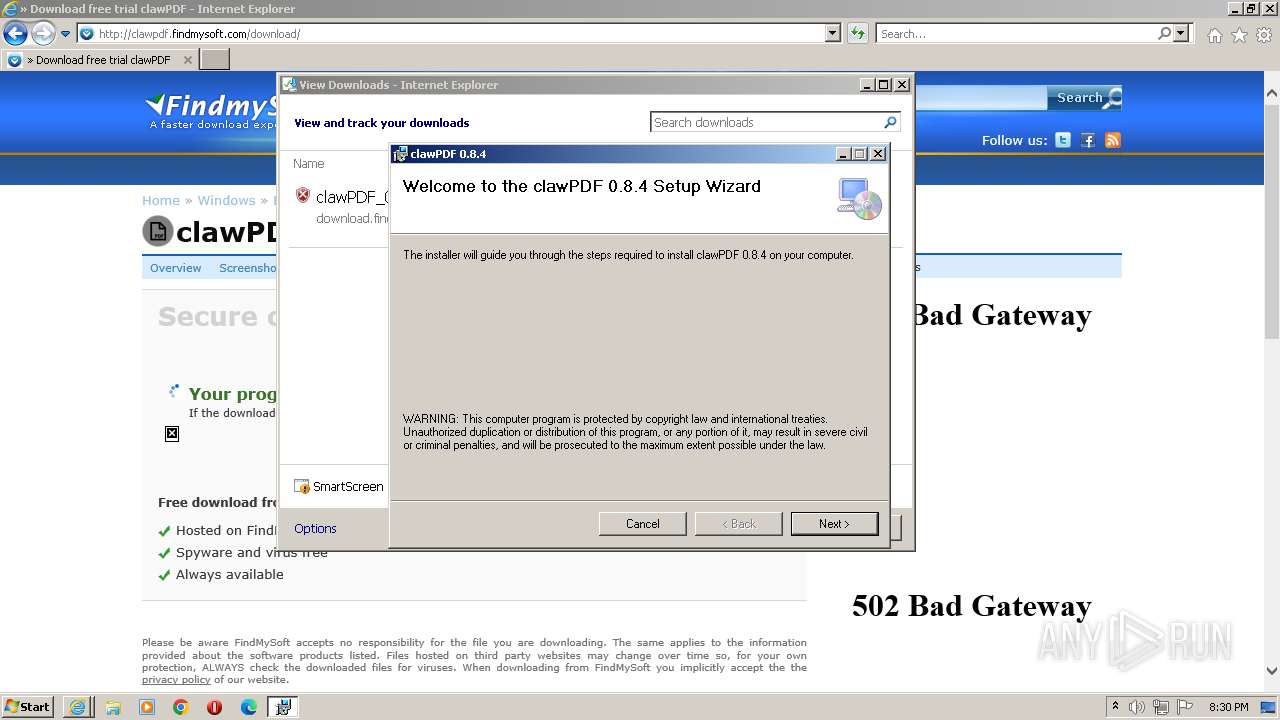
| URL: | http://clawpdf.findmysoft.com |
| Full analysis: | https://app.any.run/tasks/b0eb4754-029e-4f45-b9c1-a2f637fd031e |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2023, 19:27:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4556CE7136700CCDA038A13590D32F42 |
| SHA1: | 5701981EB36CC939FA492DA2FB29BB7D4D89D0A0 |
| SHA256: | C0C269A6EA8AF1D8B808C7F218F387A5E4E64C70DE1F59A3682365D2D2BB5E8D |
| SSDEEP: | 3:N1KdJEm+WKDR2:CzKo |
MALICIOUS
Loads dropped or rewritten executable
- msiexec.exe (PID: 280)
- msiexec.exe (PID: 3512)
- msiexec.exe (PID: 2372)
- SetupHelper.exe (PID: 2488)
- SetupHelper.exe (PID: 2204)
- spoolsv.exe (PID: 1064)
- clawPDF.exe (PID: 1796)
Starts NET.EXE for service management
- SetupHelper.exe (PID: 2488)
- net.exe (PID: 1508)
- net.exe (PID: 4040)
- SetupHelper.exe (PID: 2204)
- net.exe (PID: 1992)
- net.exe (PID: 2892)
Application was dropped or rewritten from another process
- SetupHelper.exe (PID: 2488)
- SetupHelper.exe (PID: 2204)
- clawPDF.exe (PID: 1796)
Creates a writable file the system directory
- SetupHelper.exe (PID: 2204)
- spoolsv.exe (PID: 1064)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3708)
- spoolsv.exe (PID: 2412)
- spoolsv.exe (PID: 1064)
The process creates files with name similar to system file names
- msiexec.exe (PID: 2372)
Executable content was dropped or overwritten
- SetupHelper.exe (PID: 2204)
- spoolsv.exe (PID: 1064)
Reads the Internet Settings
- clawPDF.exe (PID: 1796)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 3316)
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 2972)
Application launched itself
- iexplore.exe (PID: 3316)
- msiexec.exe (PID: 2372)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2372)
- msiexec.exe (PID: 280)
- msiexec.exe (PID: 3512)
- clawPDF.exe (PID: 1796)
Reads the computer name
- msiexec.exe (PID: 2372)
- msiexec.exe (PID: 280)
- msiexec.exe (PID: 3512)
- SetupHelper.exe (PID: 2488)
- SetupHelper.exe (PID: 2204)
- clawPDF.exe (PID: 1796)
The process checks LSA protection
- msiexec.exe (PID: 3280)
- msiexec.exe (PID: 2372)
- msiexec.exe (PID: 280)
- VSSVC.exe (PID: 3708)
- spoolsv.exe (PID: 2412)
- msiexec.exe (PID: 3512)
- spoolsv.exe (PID: 1064)
- wisptis.exe (PID: 1924)
- clawPDF.exe (PID: 1796)
Checks supported languages
- msiexec.exe (PID: 280)
- msiexec.exe (PID: 2372)
- msiexec.exe (PID: 3512)
- SetupHelper.exe (PID: 2204)
- SetupHelper.exe (PID: 2488)
- clawPDF.exe (PID: 1796)
Create files in a temporary directory
- msiexec.exe (PID: 280)
- msiexec.exe (PID: 3512)
- msiexec.exe (PID: 2372)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3280)
- msiexec.exe (PID: 2372)
Manual execution by a user
- clawPDF.exe (PID: 1796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
25
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | C:\Windows\system32\MsiExec.exe -Embedding 81C0A3C16353F4B2178E27DDCEAACF1C C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | — | clawPDF.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Pen and Touch Input Component Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1056 | C:\Windows\system32\net1 start spooler | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1064 | C:\Windows\System32\spoolsv.exe | C:\Windows\System32\spoolsv.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Spooler SubSystem App Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1508 | "net.exe" start spooler | C:\Windows\System32\net.exe | SetupHelper.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1700 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
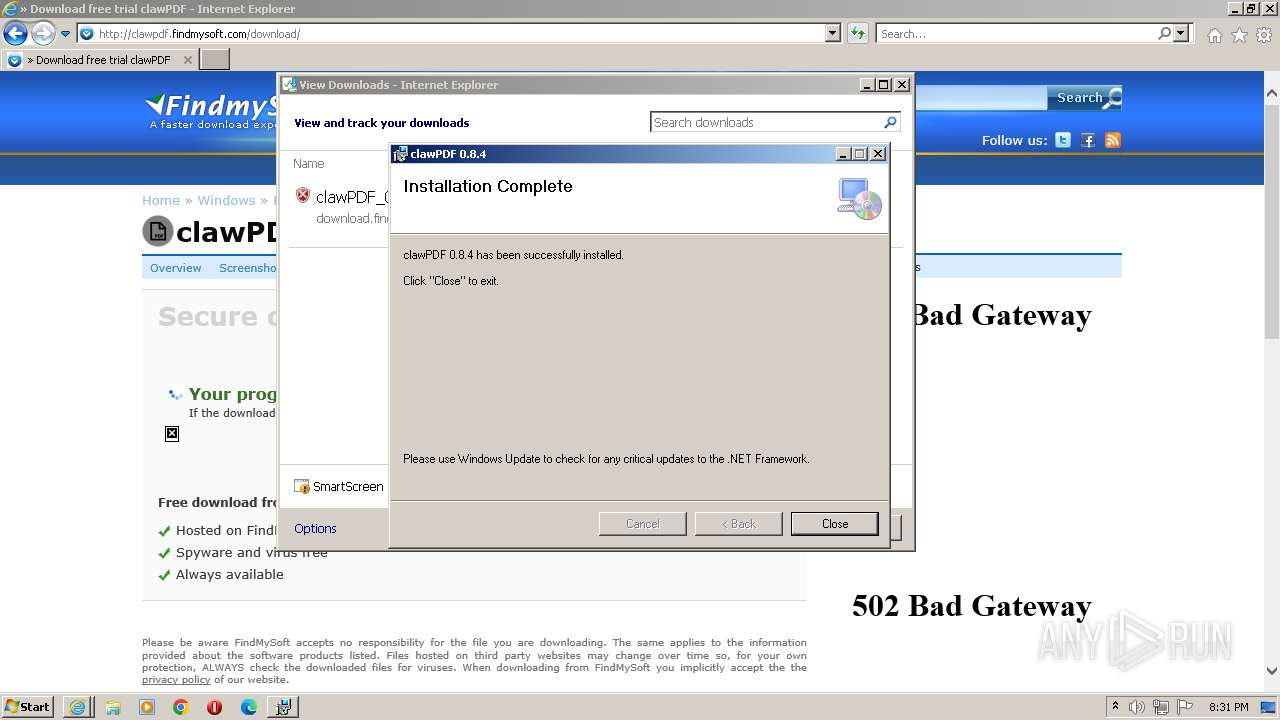
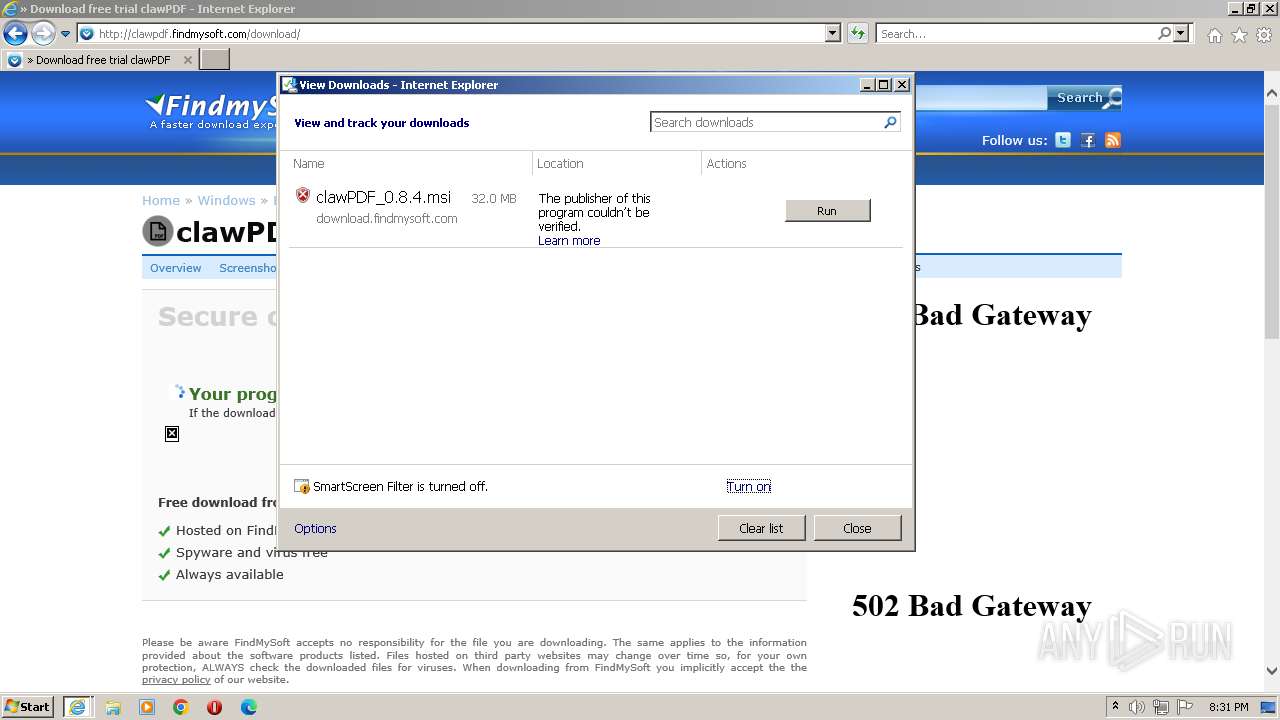
| 1796 | "C:\Program Files\clawpdf\clawPDF.exe" | C:\Program Files\clawpdf\clawPDF.exe | — | explorer.exe | |||||||||||
User: admin Company: Andrew Hess // clawSoft Integrity Level: MEDIUM Description: clawPDF Exit code: 0 Version: 0.8.4.0 Modules
| |||||||||||||||
| 1924 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | clawPDF.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1992 | "net.exe" stop spooler | C:\Windows\System32\net.exe | SetupHelper.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2204 | "C:\Program Files\clawpdf\SetupHelper.exe" /Driver=Add | C:\Program Files\clawpdf\SetupHelper.exe | msiexec.exe | ||||||||||||
User: admin Company: Andrew Hess // clawSoft Integrity Level: MEDIUM Description: clawPDF.SetupHelper Exit code: 0 Version: 0.8.4.0 Modules
| |||||||||||||||
Total events
29 315
Read events
28 835
Write events
467
Delete events
13
Modification events
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
41
Suspicious files
98
Text files
139
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\blank[1].gif | image | |
MD5:76084E29CB2CF72B320E888EDC583DFB | SHA256:02D2855C8A5417CD637DF1E81F781E42FF2B12AD6DFFB923A3822F16B5BFA82A | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\135386[1].jpg | image | |
MD5:37A3E4FE5A556486F465D1F68DB27FD3 | SHA256:DEFAF134DF203BE697BD7F0270CB339359D446F304D7E405E09DDD8F1135AC9D | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\tav_v1_300x250[1].png | image | |
MD5:0004540C3AFB7E74C3CC42FA8EA8124B | SHA256:1C49C354C6E38714224C046944D887BF2A0BE88A6460588F10E9941FCEF7C821 | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\behavior[1].js | text | |
MD5:6287C9B096CF43BB5790893BCC78FC3B | SHA256:DC23BC46254C776C75D2CBAC30B1A97A1D37FC832EE2A98B269D6EA0EB07D800 | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\review2_5_clawPDF_award[1].png | image | |
MD5:141E0726CEE752D635996540668F6AA7 | SHA256:80786C81D76EFCF7B65FA434E5F25EBEA6E8491547BEA403DF3F3BA7BEFB06FF | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\s4[1].css | text | |
MD5:86FB317C372F7FA581D5A0593A5FAA07 | SHA256:3A8FF59A7DDD1BFF1862756337A59A3EF2660EEB346CE85F0A016CF4F0AE00DF | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\Frederick-Barton_th[1].jpg | image | |
MD5:A87D037501139DE4BEB25B26ED82DD0B | SHA256:A24F2DBA227E606E5CCC25DE71CB47592CAA95E31CC12890949EC34CDD5A1F3F | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\YDX12G1L.htm | html | |
MD5:667CA2E61B995C1E304B2B4D2E68E2A0 | SHA256:1FC779832891B21061725887DF58B72A41872DC3455F2DACFB689BBF7199C62A | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\sprite_ico[1].png | image | |
MD5:5AA49E50F2AA18D23A558D2D0B2115F5 | SHA256:9FF9843B07FC44904CCD9F097F84EF04B2002D9ECBB19CA93E5CDF1F5A73A98C | |||
| 2732 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:7EDE04ED5BB17FF60C9D62912031D5C3 | SHA256:C5217DAB060B3AD187908811C202203A707267F2A4E9F60F5A0905C233306229 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
72
TCP/UDP connections
111
DNS requests
51
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2732 | iexplore.exe | GET | — | 52.73.84.74:80 | http://www.findmysoft.com/i3/sprite.png | US | — | — | unknown |
2732 | iexplore.exe | GET | — | 52.73.84.74:80 | http://www.findmysoft.com/i3/header.jpg | US | — | — | unknown |
2732 | iexplore.exe | GET | — | 172.217.18.8:80 | http://www.googletagmanager.com/gtm.js?id=GTM-MJ4SPG | US | — | — | whitelisted |
2732 | iexplore.exe | GET | — | 52.73.84.74:80 | http://www.findmysoft.com/i3/verticalbg.gif | US | — | — | unknown |
2732 | iexplore.exe | GET | 200 | 52.73.84.74:80 | http://www.findmysoft.com/s4.css | US | image | 15.7 Kb | unknown |
2732 | iexplore.exe | GET | — | 52.73.84.74:80 | http://www.findmysoft.com/i3/dl.gif | US | — | — | unknown |
2732 | iexplore.exe | GET | 200 | 52.73.84.74:80 | http://www.findmysoft.com/thumb/135386.jpg | US | image | 6.60 Kb | unknown |
2732 | iexplore.exe | GET | 200 | 108.138.17.3:80 | http://img.findmysoft.com/js3/ga_social_tracking.js | US | text | 4.70 Kb | shared |
2732 | iexplore.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?120f34a79f4bffbd | US | compressed | 4.70 Kb | whitelisted |
2732 | iexplore.exe | GET | 200 | 52.73.84.74:80 | http://clawpdf.findmysoft.com/ | US | html | 7.05 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2732 | iexplore.exe | 52.73.84.74:80 | clawpdf.findmysoft.com | AMAZON-AES | US | unknown |
2732 | iexplore.exe | 108.138.17.3:80 | img.findmysoft.com | AMAZON-02 | US | suspicious |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2732 | iexplore.exe | 157.240.252.13:443 | connect.facebook.net | FACEBOOK | DE | whitelisted |
2732 | iexplore.exe | 142.250.186.46:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
2732 | iexplore.exe | 23.35.236.137:443 | geo2.adobe.com | AKAMAI-AS | DE | suspicious |
2732 | iexplore.exe | 35.186.251.103:80 | static.totalav.com | GOOGLE | US | unknown |
2732 | iexplore.exe | 172.217.18.8:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
2732 | iexplore.exe | 67.27.159.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clawpdf.findmysoft.com |
| unknown |
www.findmysoft.com |
| unknown |
img.findmysoft.com |
| shared |
static.totalav.com |
| unknown |
connect.facebook.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
apis.google.com |
| whitelisted |
api.bing.com |
| whitelisted |