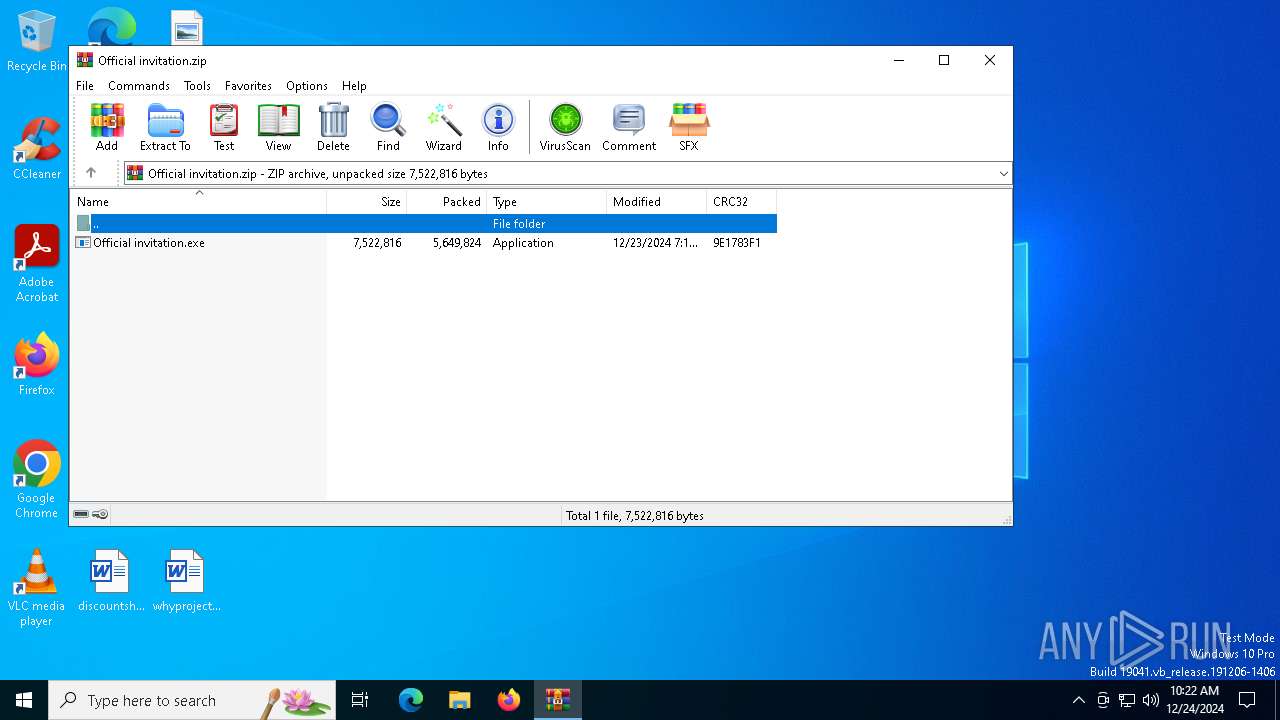
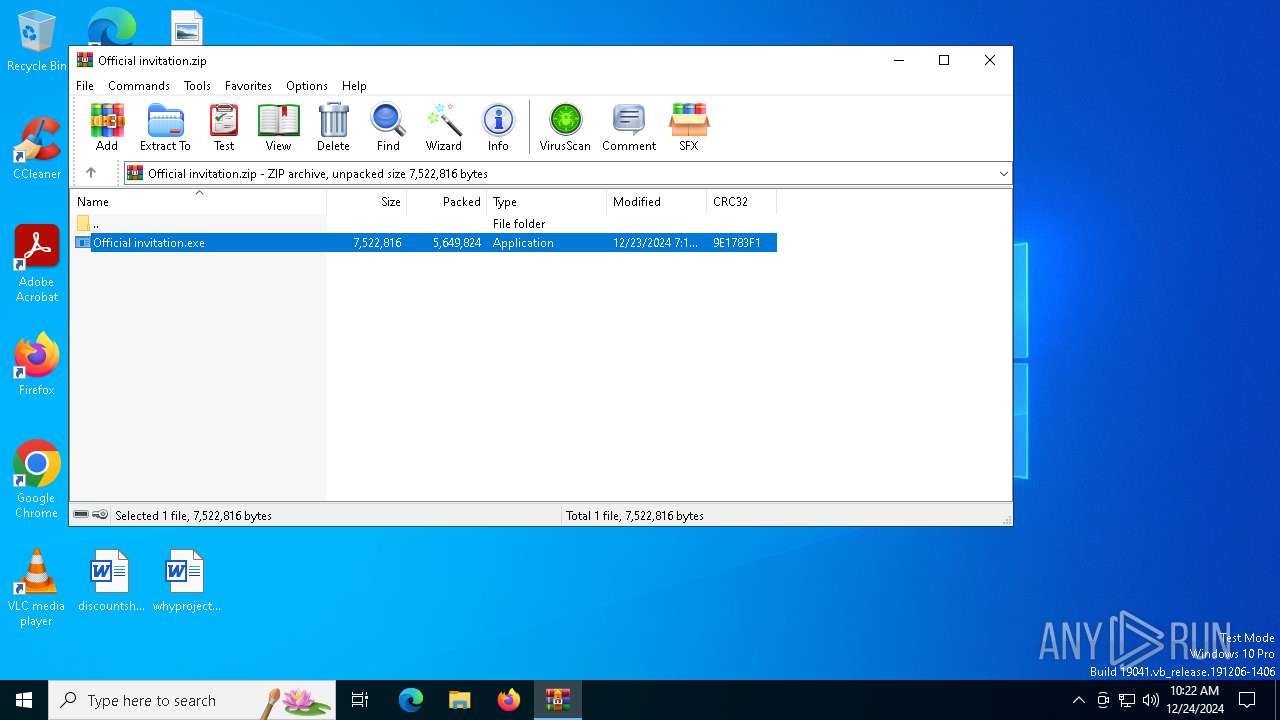
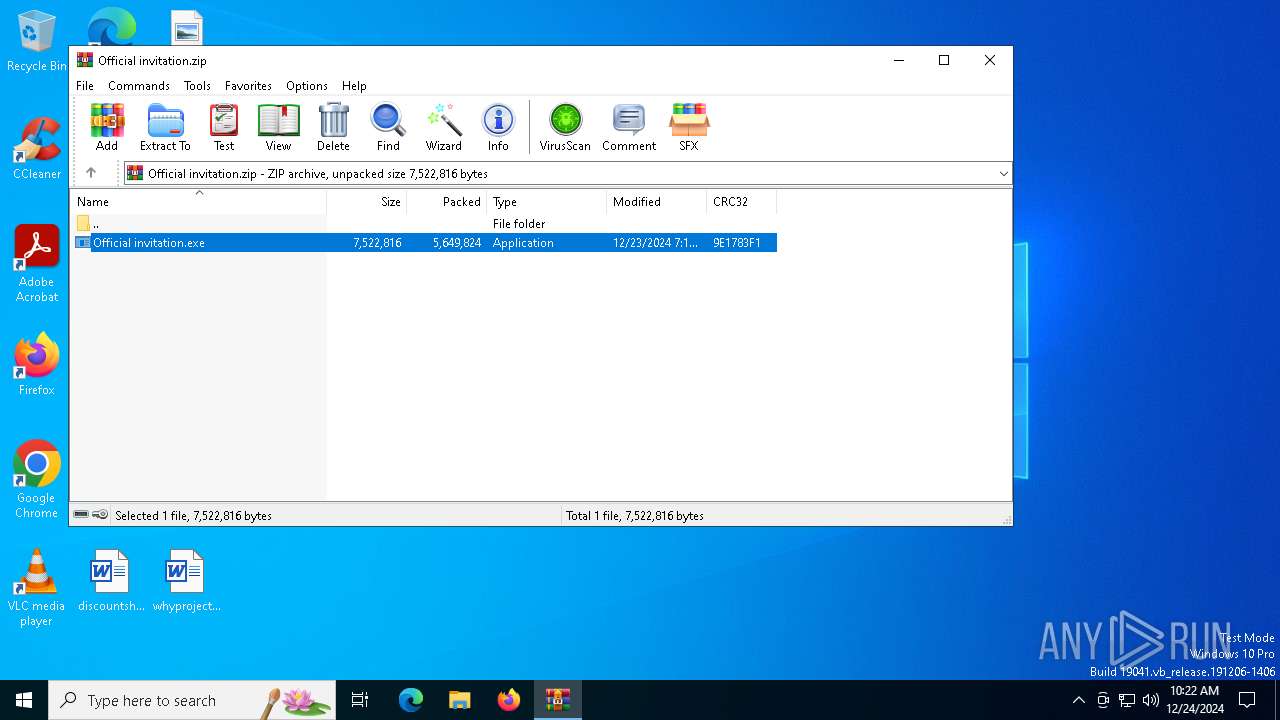
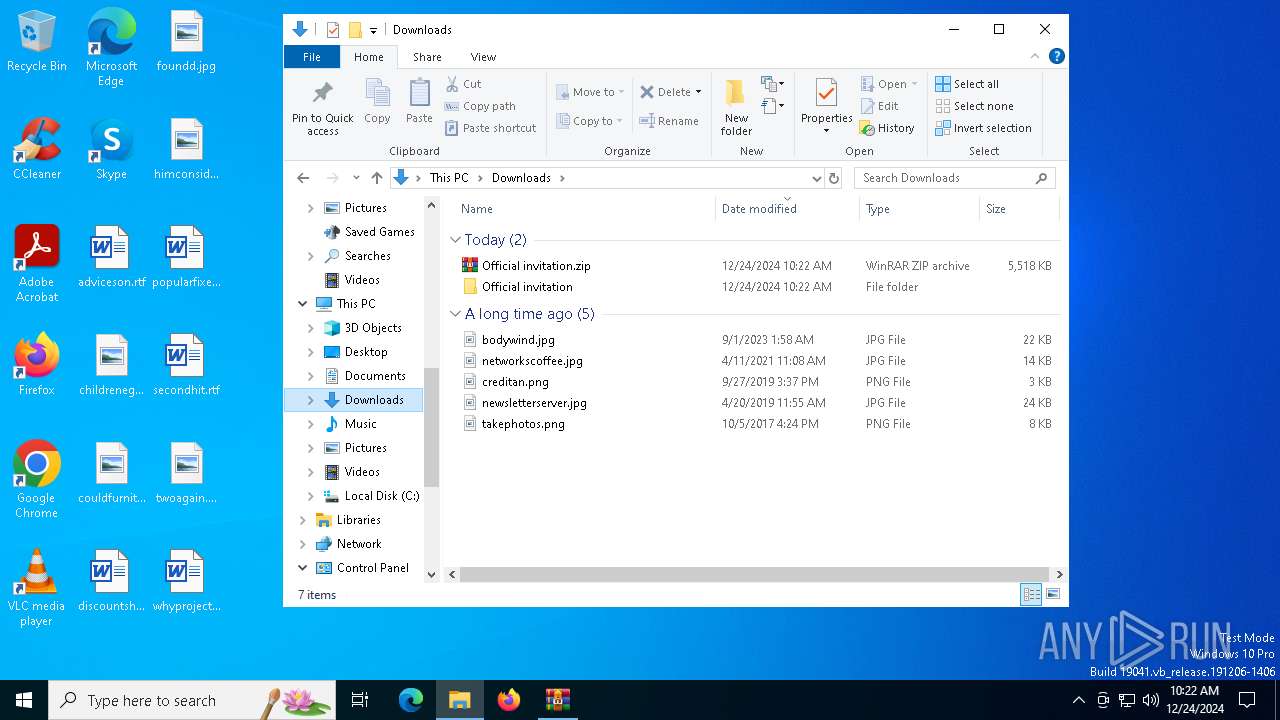
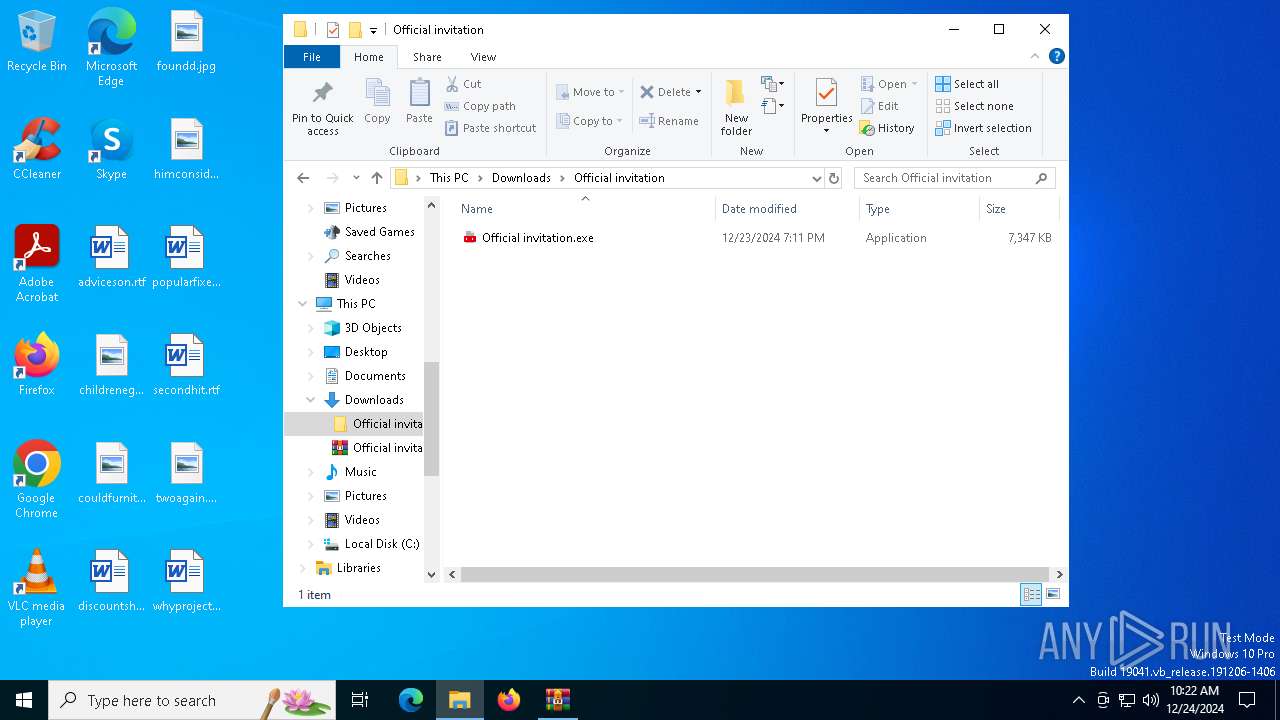
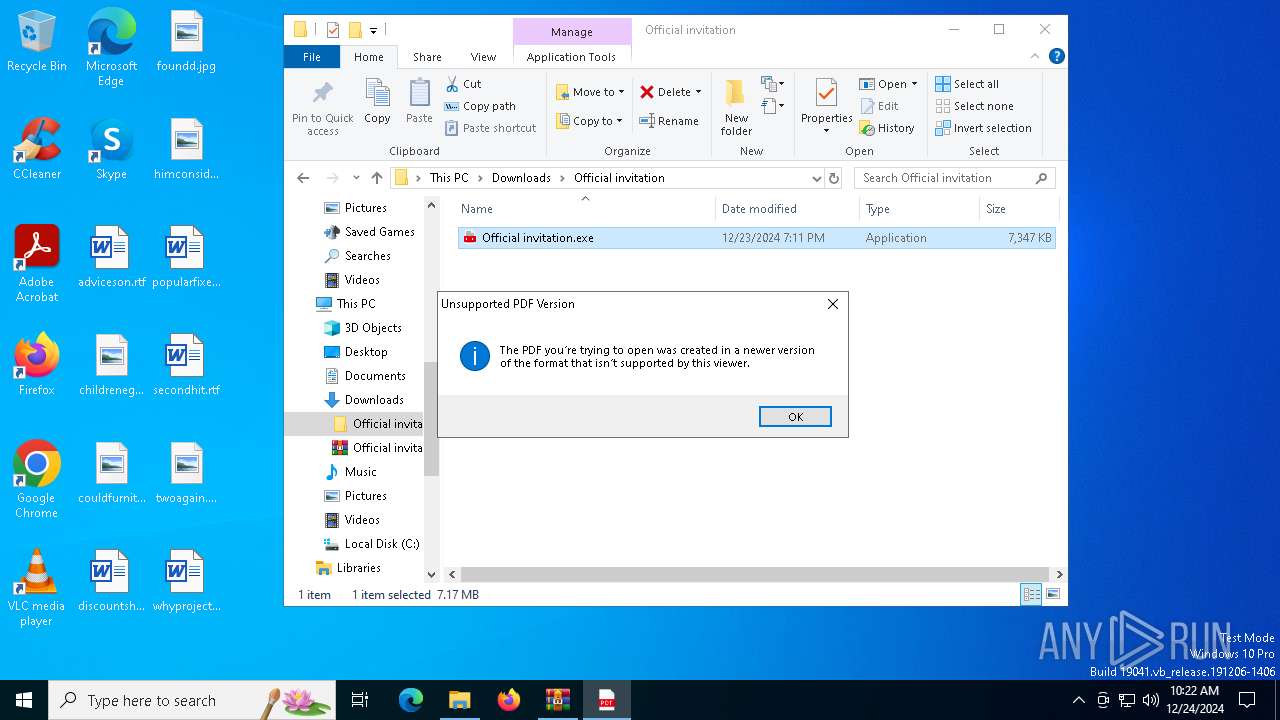
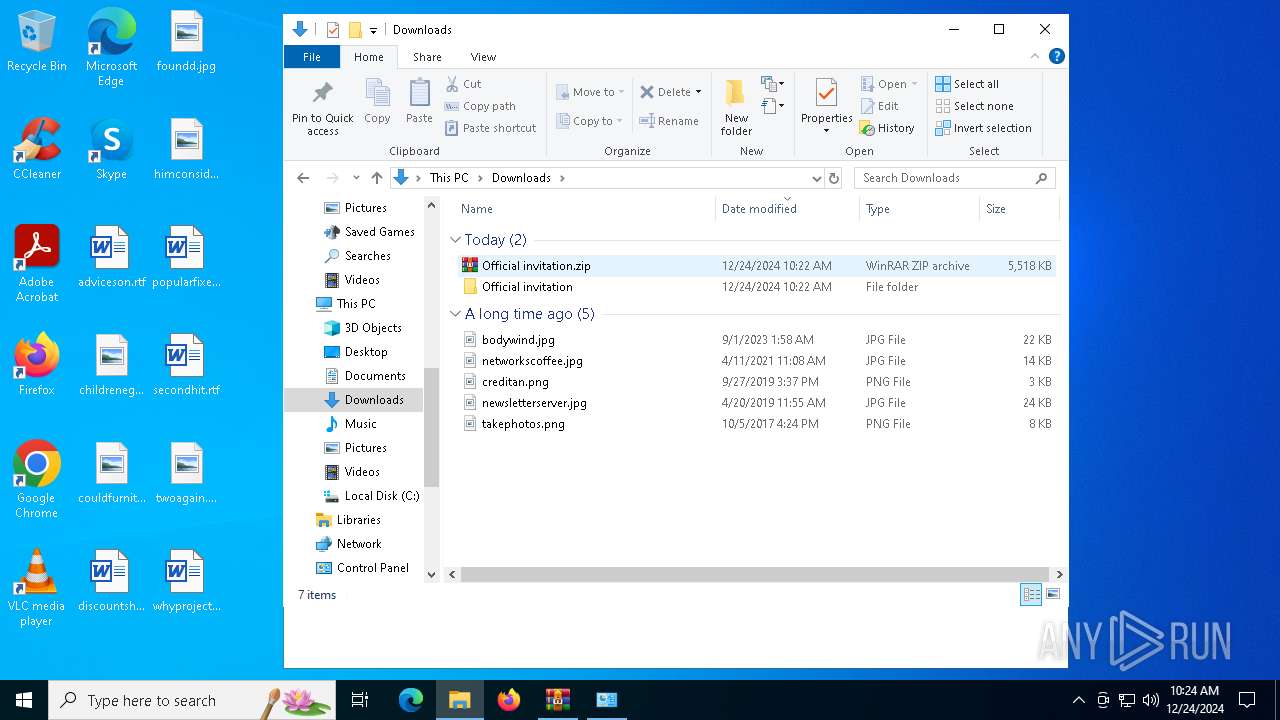
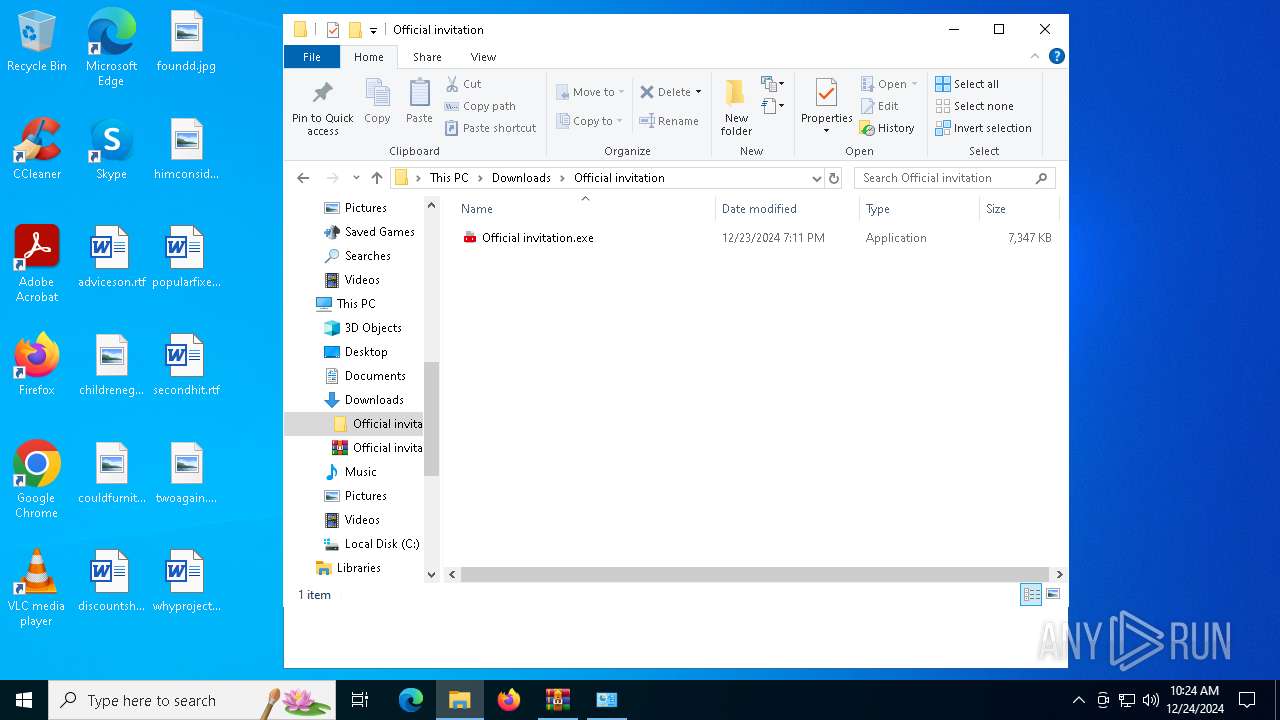
| File name: | Official invitation.zip |
| Full analysis: | https://app.any.run/tasks/a3546157-2160-4d96-aec6-25224fa14128 |
| Verdict: | Malicious activity |
| Analysis date: | December 24, 2024, 10:22:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 17F8B90BC723FC70A1874FBAB149C84D |
| SHA1: | 19739E0D21FB6BE235ECC3252370AE6CC39E4BB5 |
| SHA256: | C0C1E0F4736A95893ECD6DA8B093B07CD1413A6735E3C6B379D161C9F2ADB45C |
| SSDEEP: | 98304:nulftCshNKEzUOLqVRaeKtqW6QjrDZyMl5e1kDNzHNzm1Bwmw+c2SJBWLLeI9xPD:U9BFHbhJ6 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3144)
SUSPICIOUS
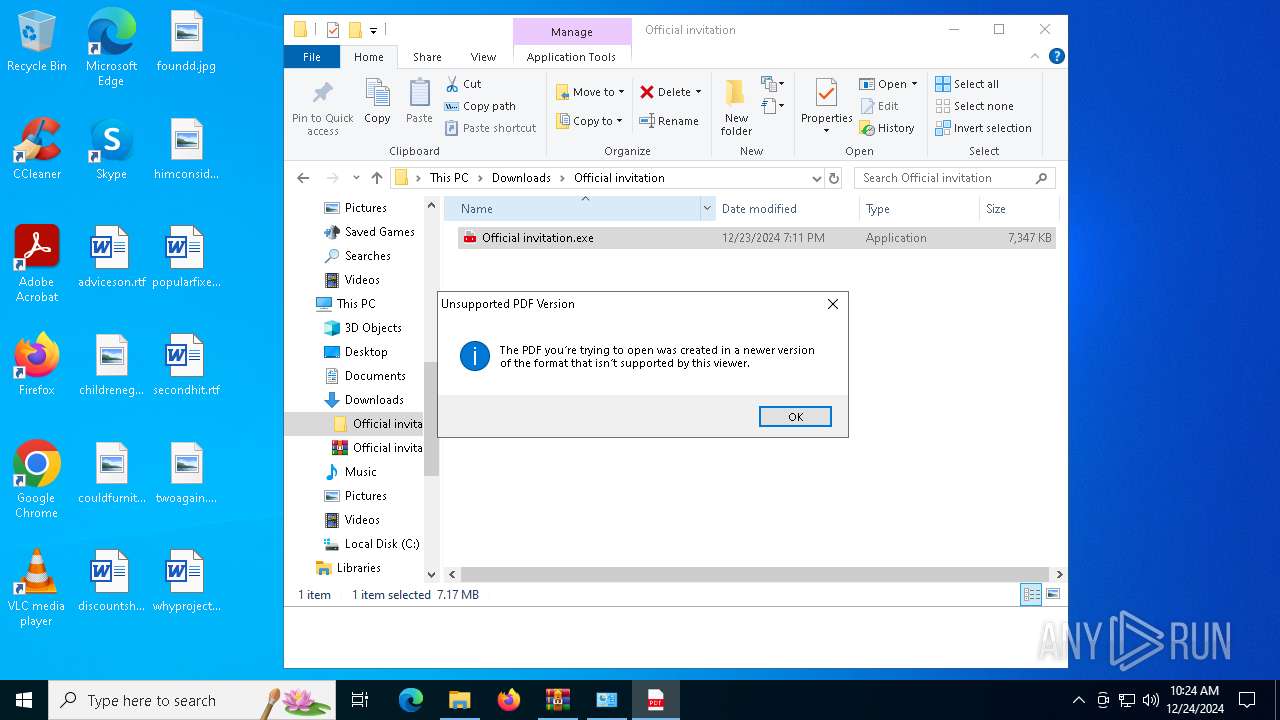
Executable content was dropped or overwritten
- Official invitation.exe (PID: 6680)
The process executes via Task Scheduler
- emailService.exe (PID: 4876)
Checks Windows Trust Settings
- emailService.exe (PID: 4876)
Reads security settings of Internet Explorer
- emailService.exe (PID: 4876)
Connects to unusual port
- emailService.exe (PID: 4876)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 3144)
- emailService.exe (PID: 4876)
Reads the computer name
- Official invitation.exe (PID: 6680)
- Official invitation.exe (PID: 4244)
- emailService.exe (PID: 4876)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3144)
Reads the machine GUID from the registry
- Official invitation.exe (PID: 6680)
- emailService.exe (PID: 4876)
Creates files or folders in the user directory
- Official invitation.exe (PID: 6680)
Manual execution by a user
- Official invitation.exe (PID: 6680)
- Official invitation.exe (PID: 4244)
Checks supported languages
- Official invitation.exe (PID: 6680)
- emailService.exe (PID: 4876)
- Official invitation.exe (PID: 4244)
Create files in a temporary directory
- emailService.exe (PID: 4876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:23 22:11:16 |
| ZipCRC: | 0x9e1783f1 |
| ZipCompressedSize: | 5649824 |
| ZipUncompressedSize: | 7522816 |
| ZipFileName: | Official invitation.exe |
Total processes
133
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3144 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Official invitation.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4244 | "C:\Users\admin\Downloads\Official invitation\Official invitation.exe" | C:\Users\admin\Downloads\Official invitation\Official invitation.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: TatoPm Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4876 | "C:\users\admin\AppData\Local\Microsoft\Windows\serviceTools\emailService.exe" -all 12.10.2022 | C:\Users\admin\AppData\Local\Microsoft\Windows\serviceTools\emailService.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: EmailManagement Version: 1.0.0.0 Modules
| |||||||||||||||
| 6620 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6680 | "C:\Users\admin\Downloads\Official invitation\Official invitation.exe" | C:\Users\admin\Downloads\Official invitation\Official invitation.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TatoPm Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7060 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7124 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 076
Read events
12 043
Write events
20
Delete events
13
Modification events
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Official invitation.zip | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
2
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4876 | emailService.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f3ljelqo.qpa.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4876 | emailService.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0f1hues2.xvq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4876 | emailService.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cbfsyj00.bwl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4876 | emailService.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:5F62DFB53E47D6CD6715ABE772A855F8 | SHA256:C327736DF96A1BC7AC8A64CFC9935A7665EE601ACCC469BAB24E3822FA7AEFC0 | |||
| 6680 | Official invitation.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\serviceTools\emailService.exe | executable | |
MD5:D4F77F6188C428DB6A1E17A73E71A99D | SHA256:BCE30DF20DD93249B57A871F0E5D5791E8C9209ED79BBC967AE054BA3C54315D | |||
| 6680 | Official invitation.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\serviceTools\emailService.exe.config | xml | |
MD5:8CD05ED3D741BE3F20CA182BE6F429A7 | SHA256:D7BE84B65B10076A7658C35124CE114C7E2B451B6EDBA4D1A41B5473E58D0EC0 | |||
| 4876 | emailService.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iczwx5ea.r0r.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3144 | WinRAR.exe | C:\Users\admin\Downloads\Official invitation\Official invitation.exe | executable | |
MD5:1A650573EB02A9FAF93E9C1853A42F08 | SHA256:F8F1D1C5076B045E3FCB0CFEFE99118696916775EBF2A1385211752443080F1D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
50
DNS requests
17
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3996 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3976 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.152:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4876 | emailService.exe | 37.98.226.123:993 | eco.pmo.gov.iq | ScopeSky for communications, internet and technology services LLC | IQ | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
eco.pmo.gov.iq |
| unknown |
dns.msftncsi.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
18.31.95.13.in-addr.arpa |
| unknown |