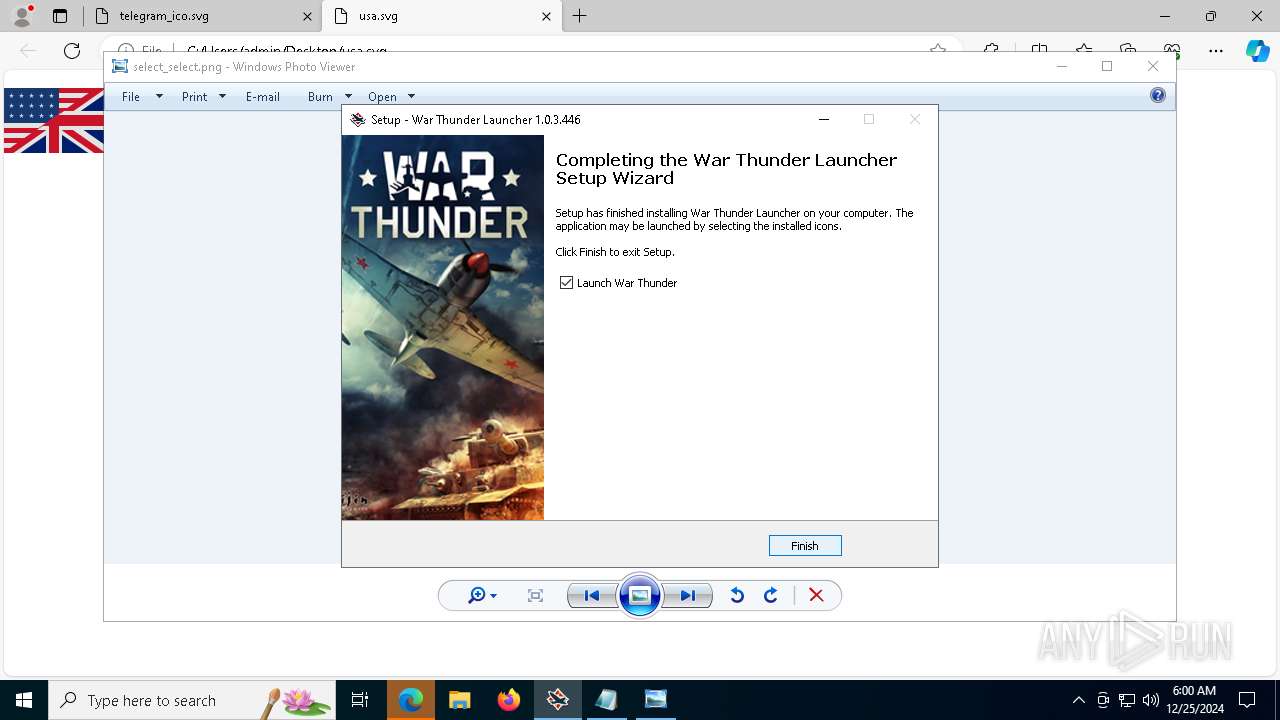
| File name: | wt_launcher_1.0.3.446-q4gnzmgpg.exe |
| Full analysis: | https://app.any.run/tasks/8d6020d8-a539-4c23-a707-c97b6c31932e |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2024, 06:00:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 2739A976BA1714A6F45A916891C5A78A |
| SHA1: | AF3EC1C860D3A80EC9E22637CD440A0D03ED18B1 |
| SHA256: | C08D97F8F9A1AE7166AC92C83F420C953AA866F3D3723B3A13DDF5D7B2A557FB |
| SSDEEP: | 98304:C+cD4dnveSD4bRBNq9W06o3B4nQMNXR8D+VTrAwidbwGm/gCpDR/r3bidx/C+kxg:y2b0254bvBaBMdkt6aiajuX2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
- wt_launcher_1.0.3.446-q4gnzmgpg.exe (PID: 6056)
Reads the Windows owner or organization settings
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
Uses NETSH.EXE to add a firewall rule or allowed programs
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
INFO
Checks supported languages
- wt_launcher_1.0.3.446-q4gnzmgpg.exe (PID: 6056)
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
- identity_helper.exe (PID: 7284)
Reads the computer name
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
- identity_helper.exe (PID: 7284)
Create files in a temporary directory
- wt_launcher_1.0.3.446-q4gnzmgpg.exe (PID: 6056)
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
Creates files or folders in the user directory
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
Creates a software uninstall entry
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
Reads the software policy settings
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
Reads the machine GUID from the registry
- wt_launcher_1.0.3.446-q4gnzmgpg.tmp (PID: 5432)
Manual execution by a user
- notepad.exe (PID: 4976)
- msedge.exe (PID: 1200)
- rundll32.exe (PID: 6784)
- msedge.exe (PID: 7120)
- msedge.exe (PID: 2736)
- msedge.exe (PID: 6688)
- msedge.exe (PID: 6888)
- rundll32.exe (PID: 6472)
- msedge.exe (PID: 7052)
- msedge.exe (PID: 7720)
- msedge.exe (PID: 7384)
- msedge.exe (PID: 7544)
- msedge.exe (PID: 7844)
- msedge.exe (PID: 7860)
- msedge.exe (PID: 7856)
- msedge.exe (PID: 7968)
- msedge.exe (PID: 8088)
- rundll32.exe (PID: 7364)
- rundll32.exe (PID: 7428)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4976)
- rundll32.exe (PID: 6784)
Application launched itself
- msedge.exe (PID: 1200)
Reads Environment values
- identity_helper.exe (PID: 7284)
Reads Microsoft Office registry keys
- rundll32.exe (PID: 6784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 182272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Gaijin Network |
| FileDescription: | War Thunder Launcher Setup |
| FileVersion: | |
| LegalCopyright: | 2014-2023 Gaijin Games KFT |
| OriginalFileName: | |
| ProductName: | War Thunder Launcher |
| ProductVersion: |
Total processes
235
Monitored processes
113
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\WarThunder\win64\bpreport.exe" "War Thunder Crash Reporter" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\WINDOWS\system32\netsh" firewall add portopening protocol = UDP port = 3478-3480 name = "War Thunder" | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\WINDOWS\system32\netsh" firewall add portopening protocol = TCP port = 27022-27042 name = "War Thunder" | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\WarThunder\ForceSingleGPU.exe" "War Thunder Game Client for disabled CrossFire\SLI" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" C:\Users\admin\Desktop\telegram_ico.svg | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1296 | "C:\WINDOWS\system32\netsh" firewall add portopening protocol = TCP port = 6881 name = "War Thunder" | C:\Windows\SysWOW64\netsh.exe | — | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1416 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=5200 --field-trial-handle=2328,i,16416300999299810353,6371864999109344402,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
22 400
Read events
22 305
Write events
95
Delete events
0
Modification events
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | StartupWithWindows |
Value: Yes | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | InstallDir |
Value: C:\Users\admin\AppData\Local\WarThunder | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | InstallPath |
Value: C:\Users\admin\AppData\Local\WarThunder | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | Dir |
Value: C:\Users\admin\AppData\Local\WarThunder | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\AppData\Local\WarThunder\launcher.exe | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\WarThunder |
| Operation: | write | Name: | language |
Value: English | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ed8deea4-29fa-3932-9612-e2122d8a62d9}}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ed8deea4-29fa-3932-9612-e2122d8a62d9}}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Local\WarThunder | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ed8deea4-29fa-3932-9612-e2122d8a62d9}}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\WarThunder\ | |||
| (PID) Process: | (5432) wt_launcher_1.0.3.446-q4gnzmgpg.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ed8deea4-29fa-3932-9612-e2122d8a62d9}}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: WarThunder | |||
Executable files
16
Suspicious files
340
Text files
52
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6056 | wt_launcher_1.0.3.446-q4gnzmgpg.exe | C:\Users\admin\AppData\Local\Temp\is-AD7RK.tmp\wt_launcher_1.0.3.446-q4gnzmgpg.tmp | executable | |
MD5:1EE2BA9595F06D6287EFEA41FAFE9589 | SHA256:03875721400F5FE8AB2B28B058EA89B0175D5B36360882953FFF63B239B56D31 | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\WarThunder\is-4B2TI.tmp | executable | |
MD5:B5A4FA79412BA8FBC06ADB6F0EABB206 | SHA256:329107A505E084804BFA4FE7C15440255AC1EDA1EAB5D9D87570575B233D9705 | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\WarThunder\unins000.exe | executable | |
MD5:1EE2BA9595F06D6287EFEA41FAFE9589 | SHA256:03875721400F5FE8AB2B28B058EA89B0175D5B36360882953FFF63B239B56D31 | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\WarThunder\launcher.exe | executable | |
MD5:B5A4FA79412BA8FBC06ADB6F0EABB206 | SHA256:329107A505E084804BFA4FE7C15440255AC1EDA1EAB5D9D87570575B233D9705 | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\WarThunder\bpreport.exe | executable | |
MD5:31911C6EA459F516D1DA0A12EC677BEA | SHA256:44C1DB6B7BF4103B2C4D3A1F014A1EA8FAFBBEBA19CD028525D494E3E390A896 | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\WarThunder\is-CQ2S9.tmp | executable | |
MD5:1EE2BA9595F06D6287EFEA41FAFE9589 | SHA256:03875721400F5FE8AB2B28B058EA89B0175D5B36360882953FFF63B239B56D31 | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\Temp\is-GUPGS.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\WarThunder\gaijin_downloader.exe | executable | |
MD5:ADC796431F36632ED86663E8BCAFDDB8 | SHA256:699783D9218C730A4334532DD0ADC6FA9D6E22395E96274B20CDB32EFEA6EDBA | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\WarThunder\is-PNHG7.tmp | image | |
MD5:945B144169D97344B11E182F773DBB67 | SHA256:FAC97A96962BE6B9347FE414AACD99B02A0DE63D79BA6E49D8690506A3C96EE4 | |||
| 5432 | wt_launcher_1.0.3.446-q4gnzmgpg.tmp | C:\Users\admin\AppData\Local\WarThunder\gjagent.exe | executable | |
MD5:65F9CBA4FB02014A13685D8358CB0E67 | SHA256:2ED5BFDA0B759B4CD795514C0F1FFBDBD0DF40A82EA4FD50044BDFD8AD25CE37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
54
DNS requests
47
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | — | — | unknown |
— | — | GET | 304 | 13.107.21.239:443 | https://edge.microsoft.com/abusiveadblocking/api/v1/blocklist | unknown | — | — | unknown |
— | — | GET | — | 2.21.110.139:443 | https://edgeservices.bing.com/edgesvc/userstatus | unknown | — | — | unknown |
488 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
488 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/122.0.2365.59?clientId=4489578223053569932&agents=Edge%2CEdgeConfig%2CEdgeServices%2CEdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=44&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245&fg=1 | unknown | binary | 10.2 Kb | whitelisted |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/work/api/v2/tenant/my/settingswithflights?&clienttype=edge-omnibox | unknown | binary | 581 b | whitelisted |
— | — | GET | 200 | 2.21.110.139:443 | https://www.bing.com/bloomfilterfiles/ExpandedDomainsFilterGlobal.json | unknown | binary | 620 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
488 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
488 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
488 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
488 | svchost.exe | 13.71.55.58:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IN | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
launcher-bq.gaijin.net |
| whitelisted |
www.bing.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |