| File name: | EKANS snake ransomware.zip |
| Full analysis: | https://app.any.run/tasks/a2303b2d-f421-4da8-978d-037a20aa071e |
| Verdict: | Malicious activity |
| Analysis date: | June 09, 2020, 07:48:38 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FAF1FC2823E60247B0CB8B78F0A0B9A6 |
| SHA1: | C221C2ABB13E791D5328B3EB3208FC9737AB308B |
| SHA256: | C076D84DF7303FAA68C3F29DDF0D36D699817C48BD4475F54663664A29183FB1 |
| SSDEEP: | 24576:C8vw7sVrrcQki5KzhY5h7DBAWVUSVh0HPr9utbPXKdhVR/lX16gSgjO:ho7sVrrnK2P7NtUu0HPsp6XVJl8JgjO |
MALICIOUS
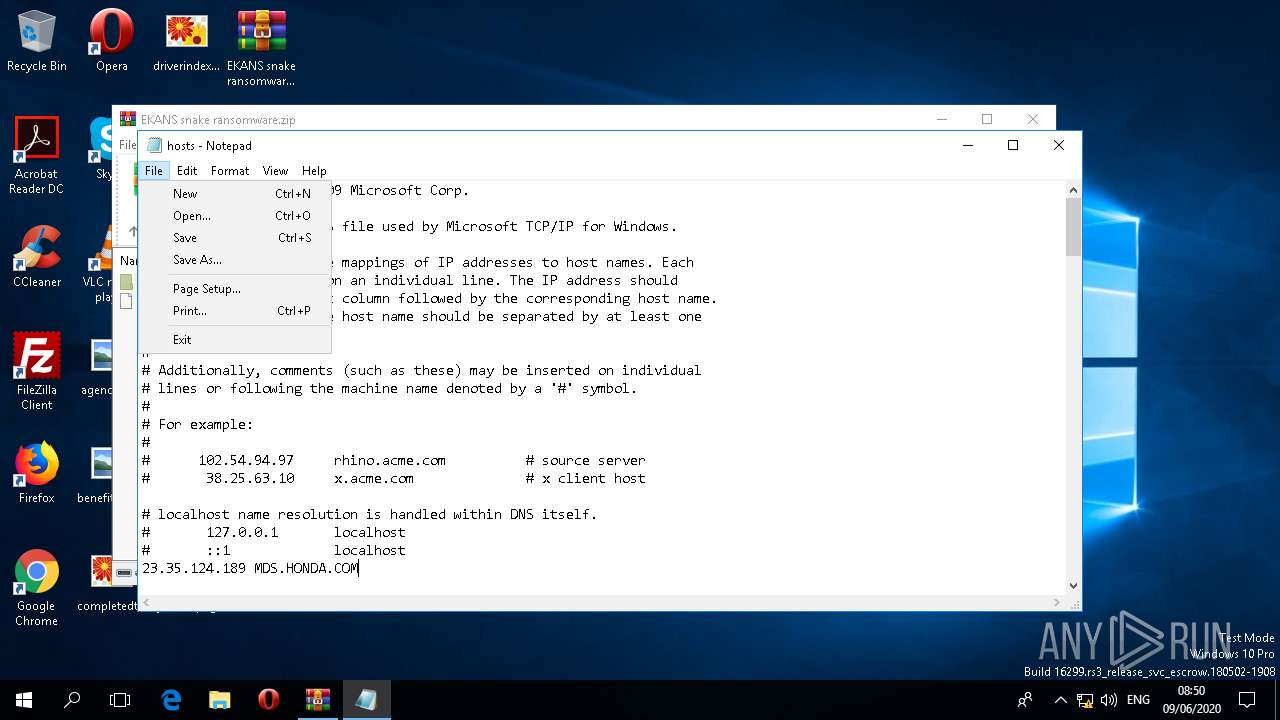
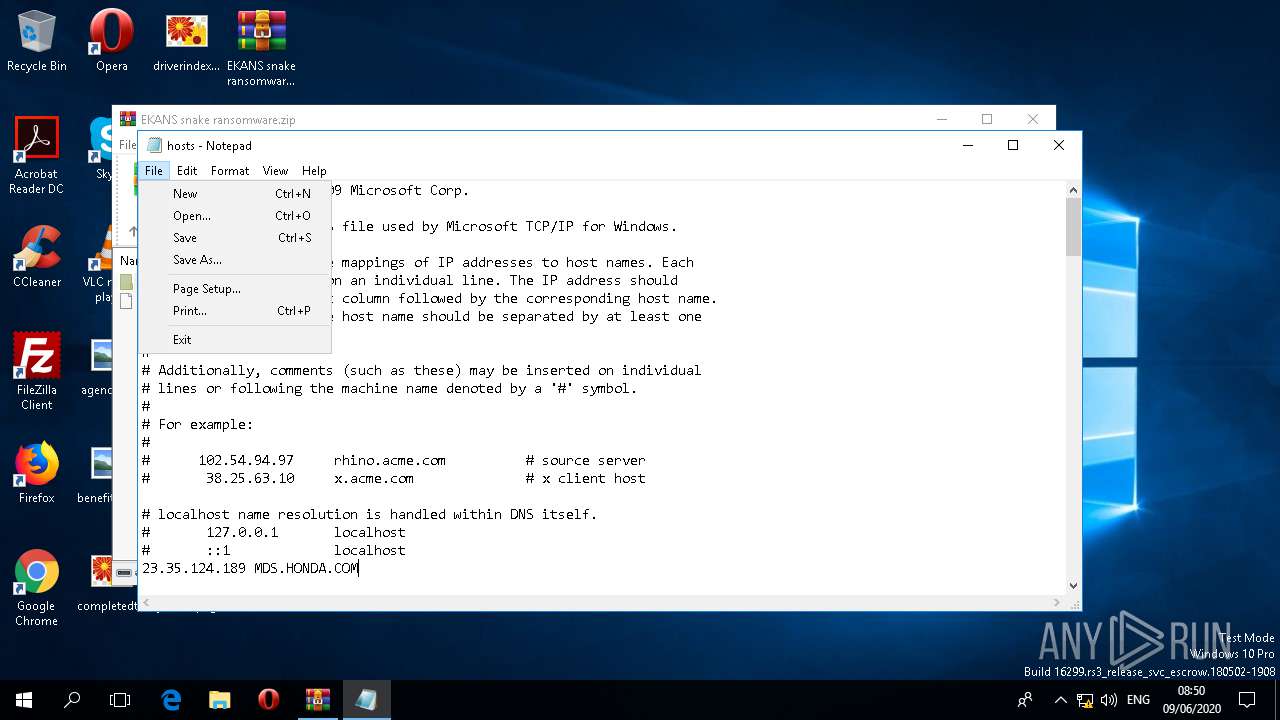
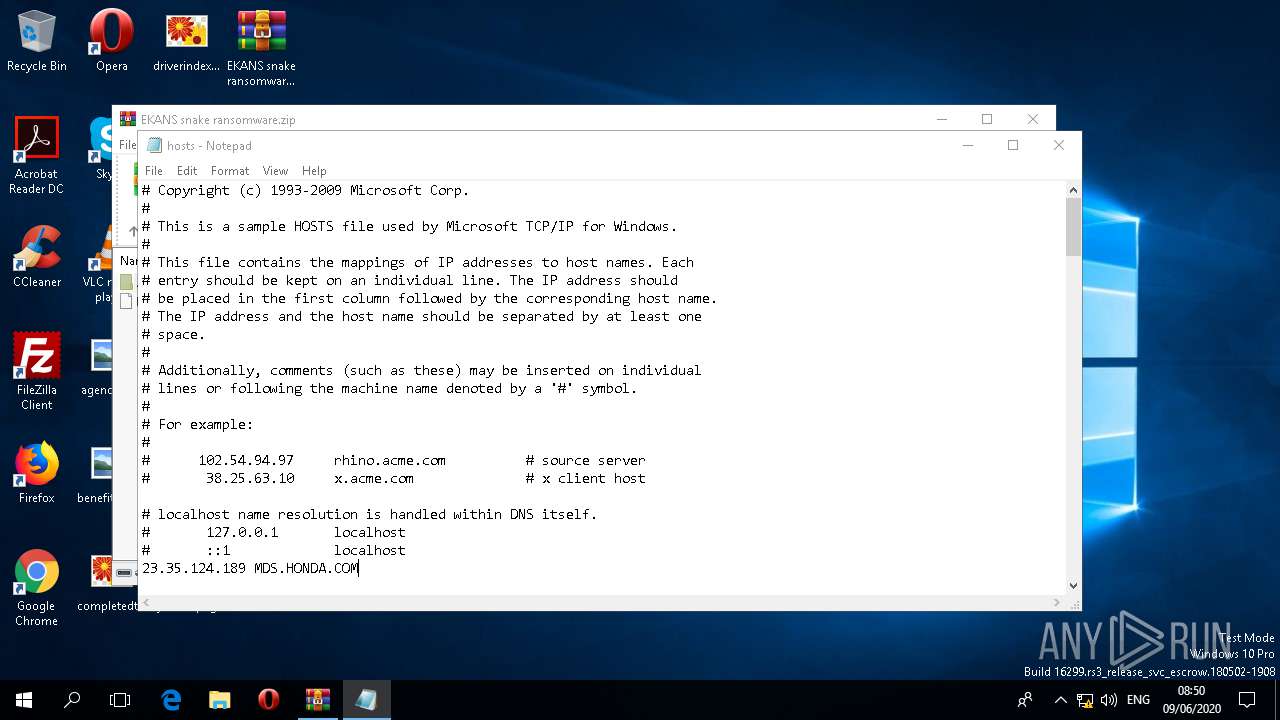
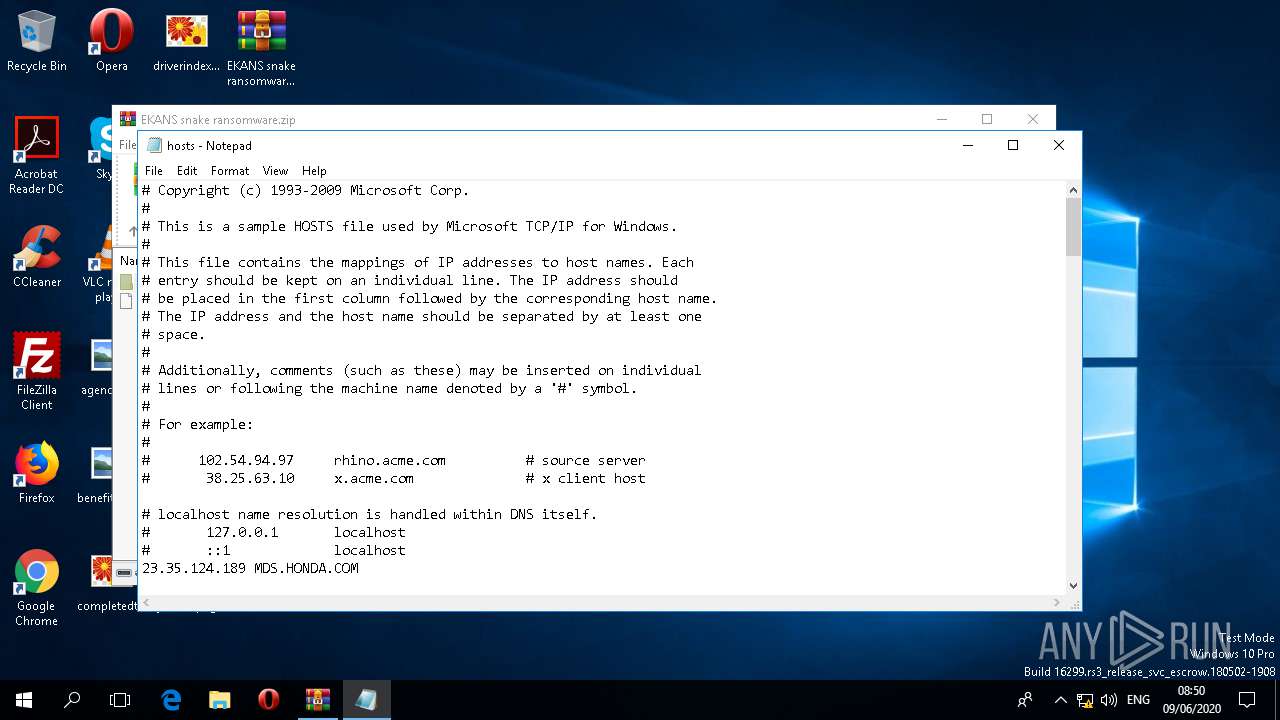
Writes to the hosts file
- notepad.exe (PID: 852)
Modifies hosts file to block updates
- notepad.exe (PID: 852)
Application was dropped or rewritten from another process
- EKANS snake ransomware.exe (PID: 5340)
- EKANS snake ransomware.exe (PID: 856)
- EKANS snake ransomware.exe (PID: 2236)
SUSPICIOUS
Executed via COM
- DllHost.exe (PID: 540)
- DllHost.exe (PID: 1088)
- backgroundTaskHost.exe (PID: 2344)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4840)
INFO
Manual execution by user
- notepad.exe (PID: 2716)
- notepad.exe (PID: 852)
- EKANS snake ransomware.exe (PID: 5340)
- EKANS snake ransomware.exe (PID: 2236)
- EKANS snake ransomware.exe (PID: 856)
Reads the hosts file
- notepad.exe (PID: 852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:06:08 19:42:07 |
| ZipCRC: | 0x5ff49c11 |
| ZipCompressedSize: | 1220080 |
| ZipUncompressedSize: | 3965952 |
| ZipFileName: | EKANS snake ransomware |
Total processes
199
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | C:\WINDOWS\system32\DllHost.exe /Processid:{973D20D7-562D-44B9-B70B-5A0F49CCDF3F} | C:\WINDOWS\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 1073807364 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 852 | "C:\WINDOWS\system32\notepad.exe" | C:\WINDOWS\system32\notepad.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Users\admin\Desktop\EKANS snake ransomware.exe" | C:\Users\admin\Desktop\EKANS snake ransomware.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1088 | C:\WINDOWS\system32\DllHost.exe /Processid:{7966B4D8-4FDC-4126-A10B-39A3209AD251} | C:\WINDOWS\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | EKANS snake ransomware.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\Desktop\EKANS snake ransomware.exe" | C:\Users\admin\Desktop\EKANS snake ransomware.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | EKANS snake ransomware.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2344 | "C:\WINDOWS\system32\backgroundTaskHost.exe" -ServerName:CortanaUI.AppXy7vb4pc2dr3kc93kfc509b1d0arkfb2x.mca | C:\WINDOWS\system32\backgroundTaskHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Background Task Host Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\WINDOWS\system32\conhost.exe | EKANS snake ransomware.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | "C:\WINDOWS\system32\notepad.exe" | C:\WINDOWS\system32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 758
Read events
2 587
Write events
167
Delete events
4
Modification events
| (PID) Process: | (4840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4840) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\194\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\EKANS snake ransomware.zip | |||
| (PID) Process: | (4840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2716) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 130 | |||
| (PID) Process: | (2716) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 130 | |||
Executable files
1
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 540 | DllHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Cortana_cw5n1h2txyewy\AppData\Indexed DB\IndexedDB.edb | — | |
MD5:— | SHA256:— | |||
| 540 | DllHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Cortana_cw5n1h2txyewy\AppData\Indexed DB\IndexedDB.jfm | — | |
MD5:— | SHA256:— | |||
| 540 | DllHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Cortana_cw5n1h2txyewy\AppData\Indexed DB\edb.log | — | |
MD5:— | SHA256:— | |||
| 540 | DllHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Cortana_cw5n1h2txyewy\AppData\Indexed DB\edb.chk | binary | |
MD5:— | SHA256:— | |||
| 4840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4840.34926\EKANS snake ransomware | executable | |
MD5:ED3C05BDE9F0EA0F1321355B03AC42D0 | SHA256:D4DA69E424241C291C173C8B3756639C654432706E7DEF5025A649730868C4A1 | |||
| 852 | notepad.exe | C:\Windows\System32\drivers\etc\hosts | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3524 | svchost.exe | GET | 200 | 13.78.184.186:443 | https://geo-prod.do.dsp.mp.microsoft.com/geo?doClientVersion=10.0.16299.431 | US | text | 266 b | whitelisted |
3524 | svchost.exe | GET | 200 | 104.121.117.211:443 | https://kv801.prod.do.dsp.mp.microsoft.com/all?doClientVersion=10.0.16299.431&countryCode=NL | NL | text | 2.06 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2228 | svchost.exe | 13.78.184.186:443 | geo-prod.do.dsp.mp.microsoft.com | Microsoft Corporation | US | whitelisted |
2228 | svchost.exe | 104.121.117.211:443 | kv801.prod.do.dsp.mp.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
self.events.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| malicious |
geo-prod.do.dsp.mp.microsoft.com |
| whitelisted |
kv801.prod.do.dsp.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |