| File name: | HW2.rar |
| Full analysis: | https://app.any.run/tasks/f290bf4a-7b41-4729-9b6a-d36a8fb3714c |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 21:35:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 829620C4DD5AB8E5738B13C729786260 |
| SHA1: | 42D44763F7A81A4B0F6C6206D39654457C3E7C38 |
| SHA256: | C05DE7B8712DBEC41C58DF0D6D949E0D942DFA4EEC3797EA87C67C245CD3BA63 |
| SSDEEP: | 98304:fr/LS5sHezOaI2li7CctSkLOsHIXHnnUENP1cZY+IwHJVcCCjMaLIz1V2d86Xs2s:6gEhaRaMOIH |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- WinRAR.exe (PID: 1452)
Process drops legitimate windows executable
- WinRAR.exe (PID: 1452)
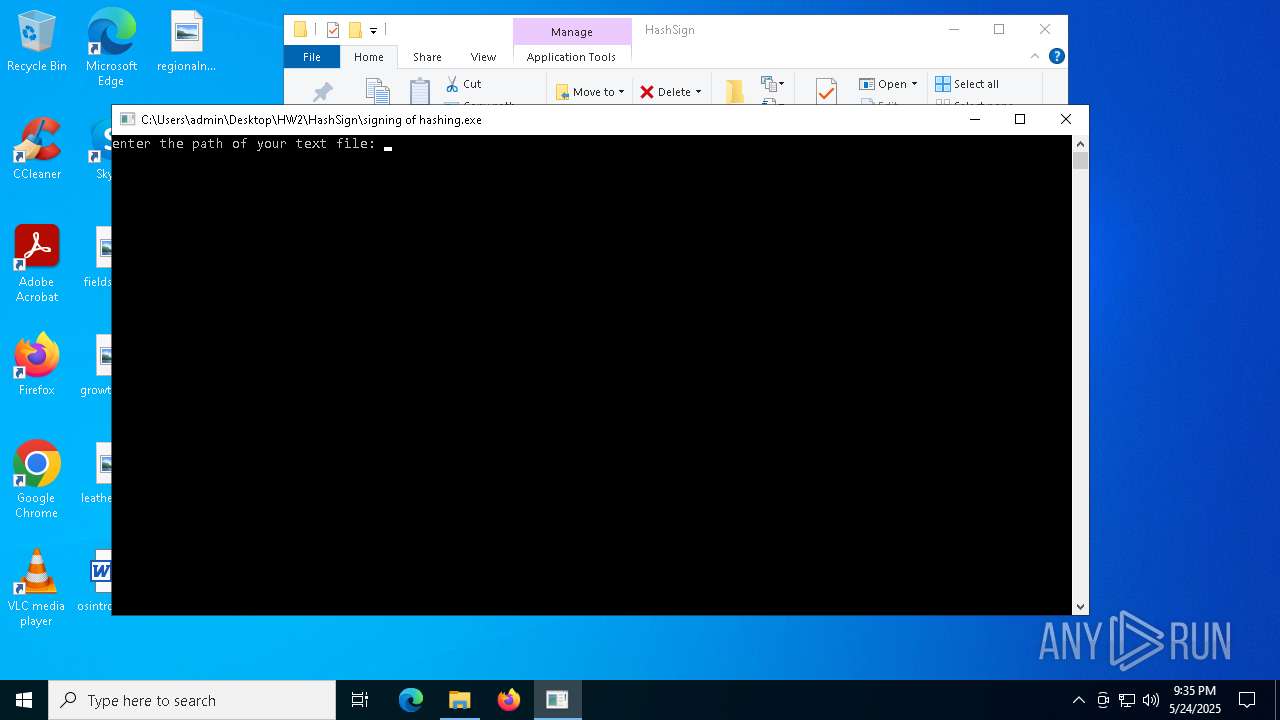
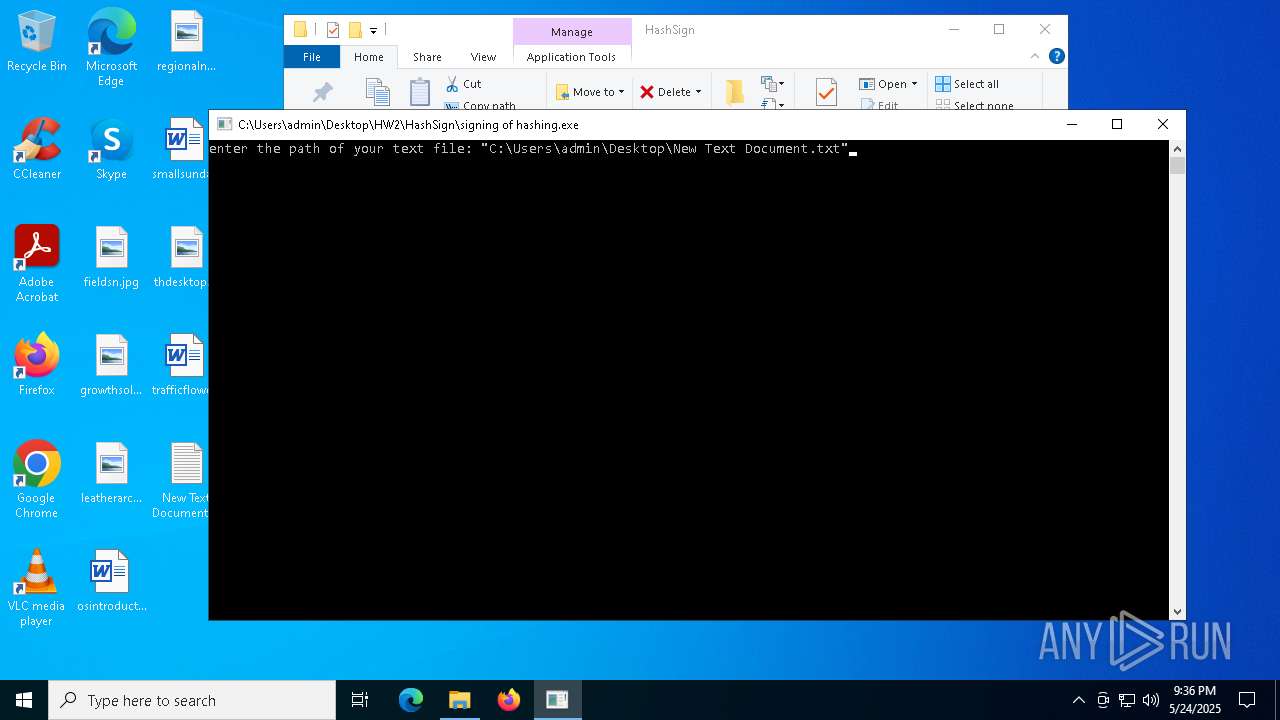
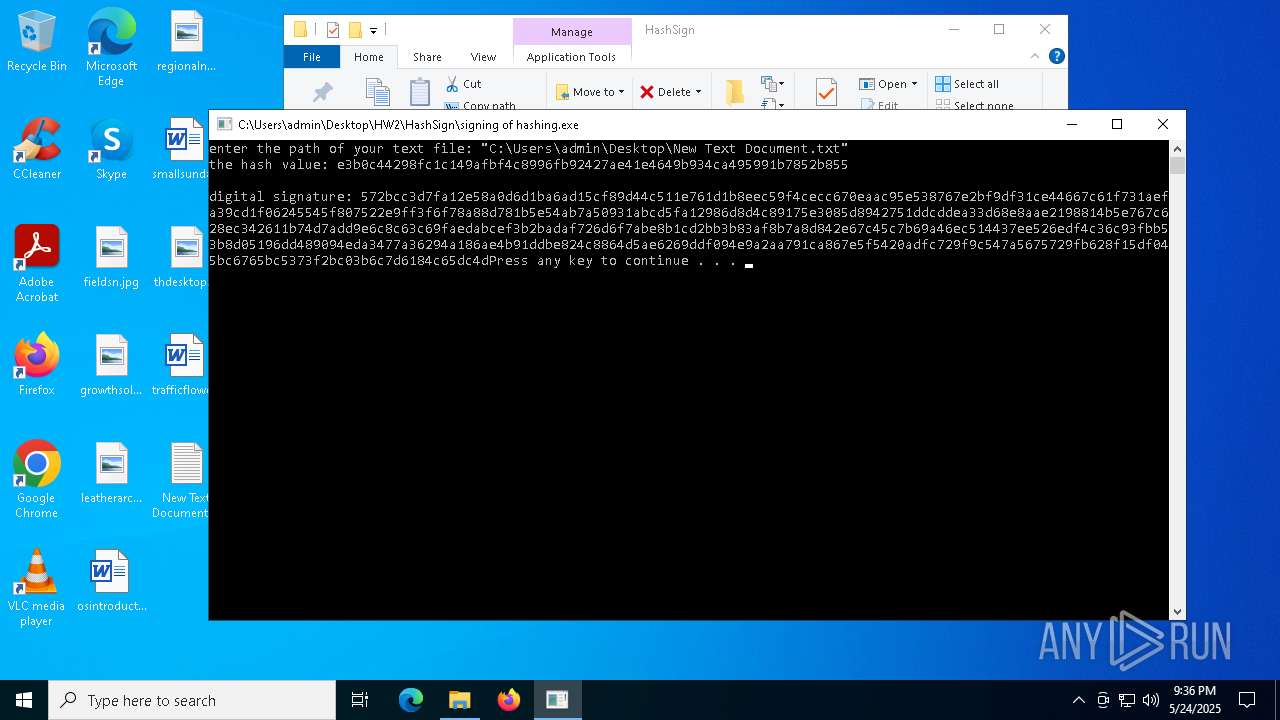
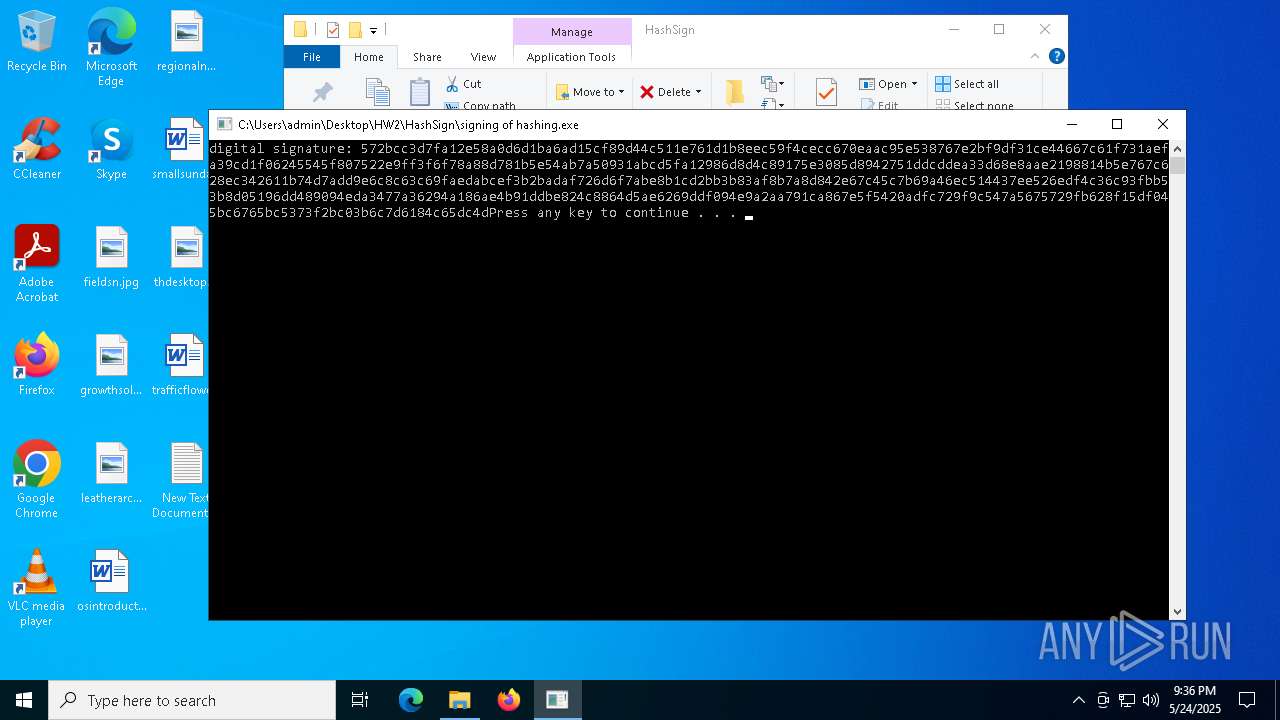
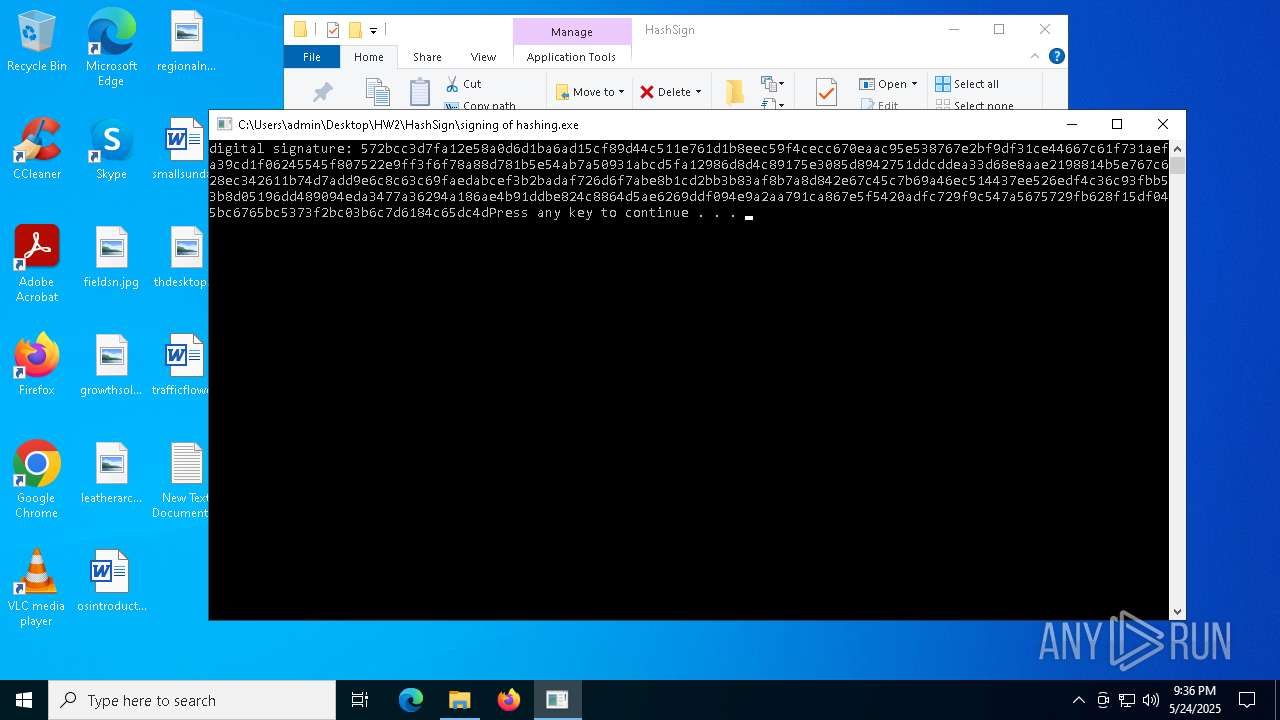
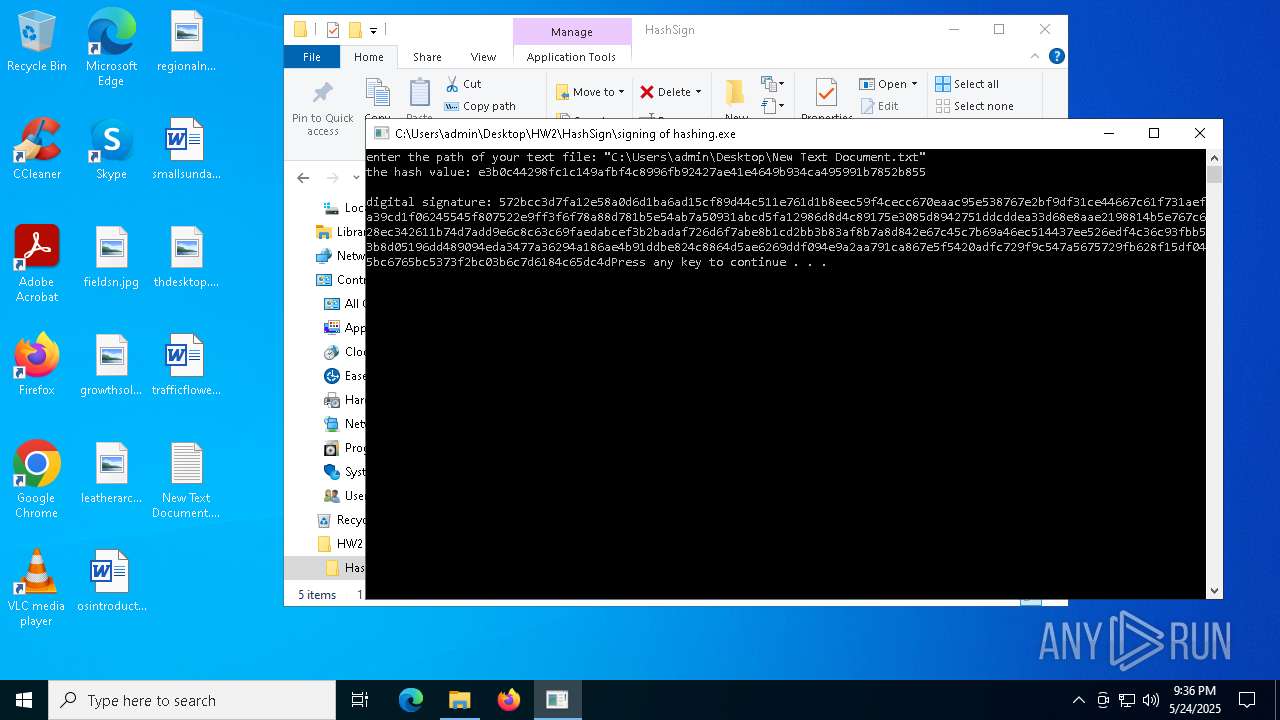
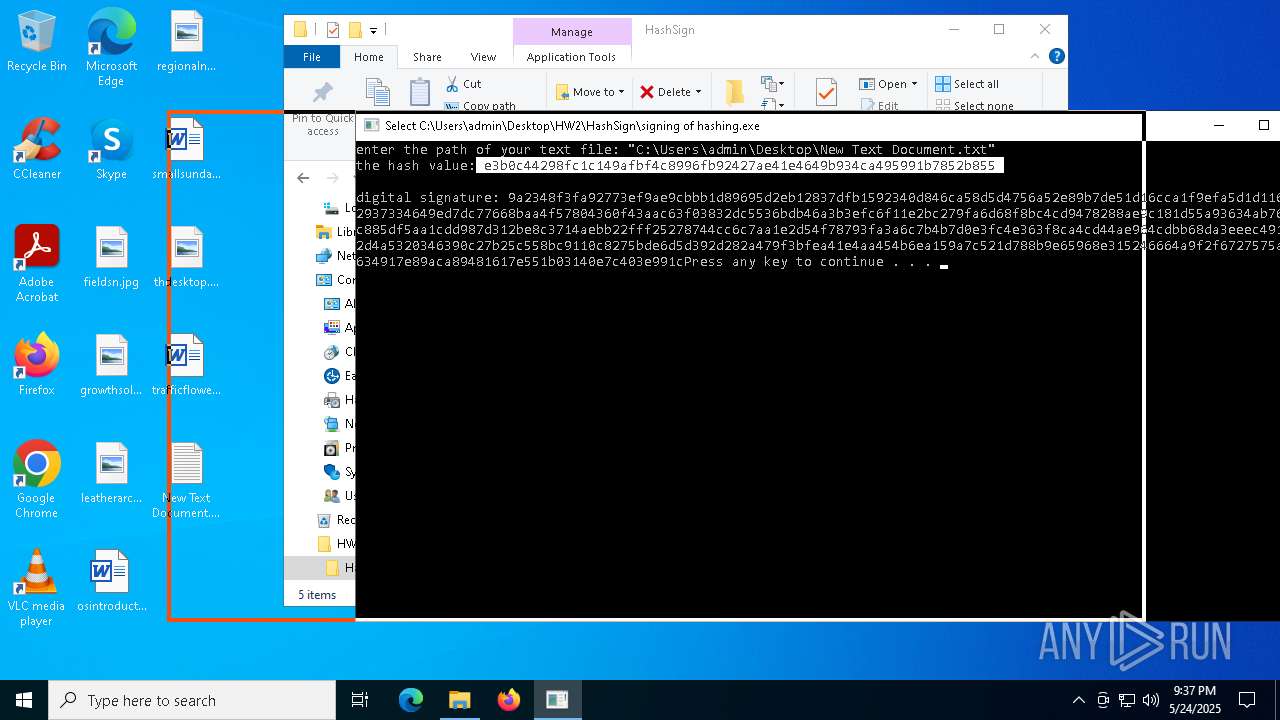
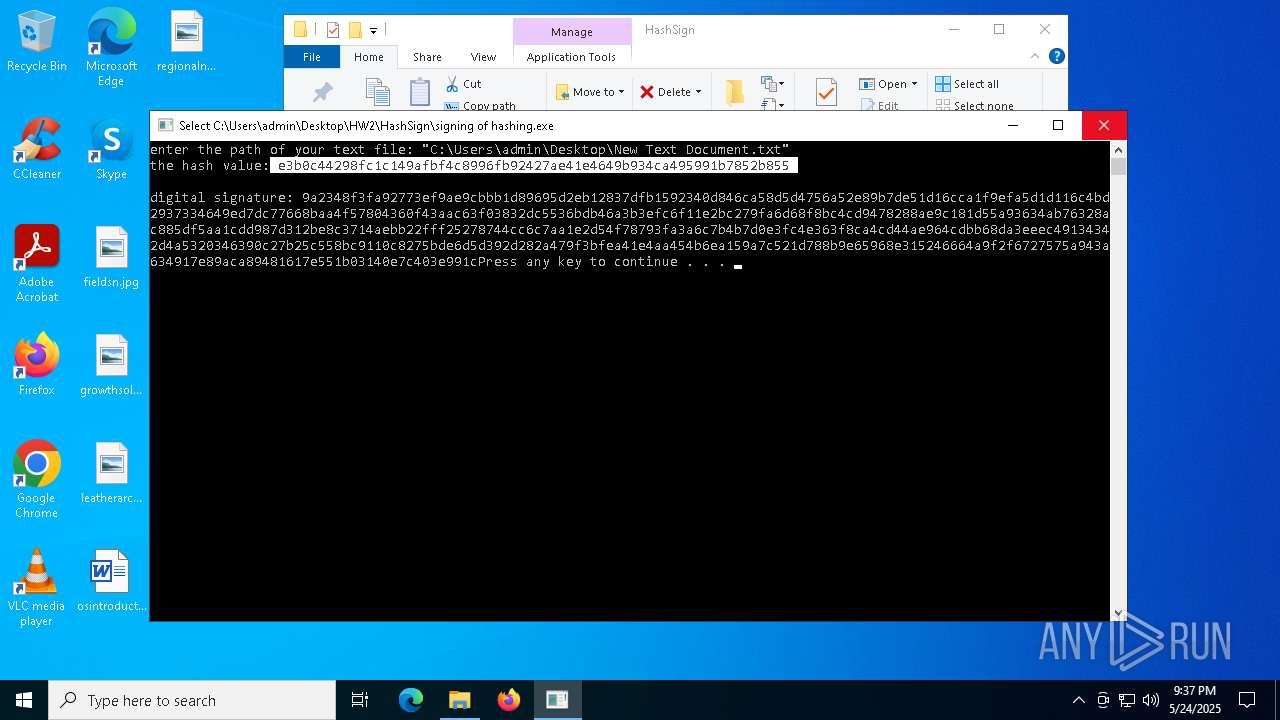
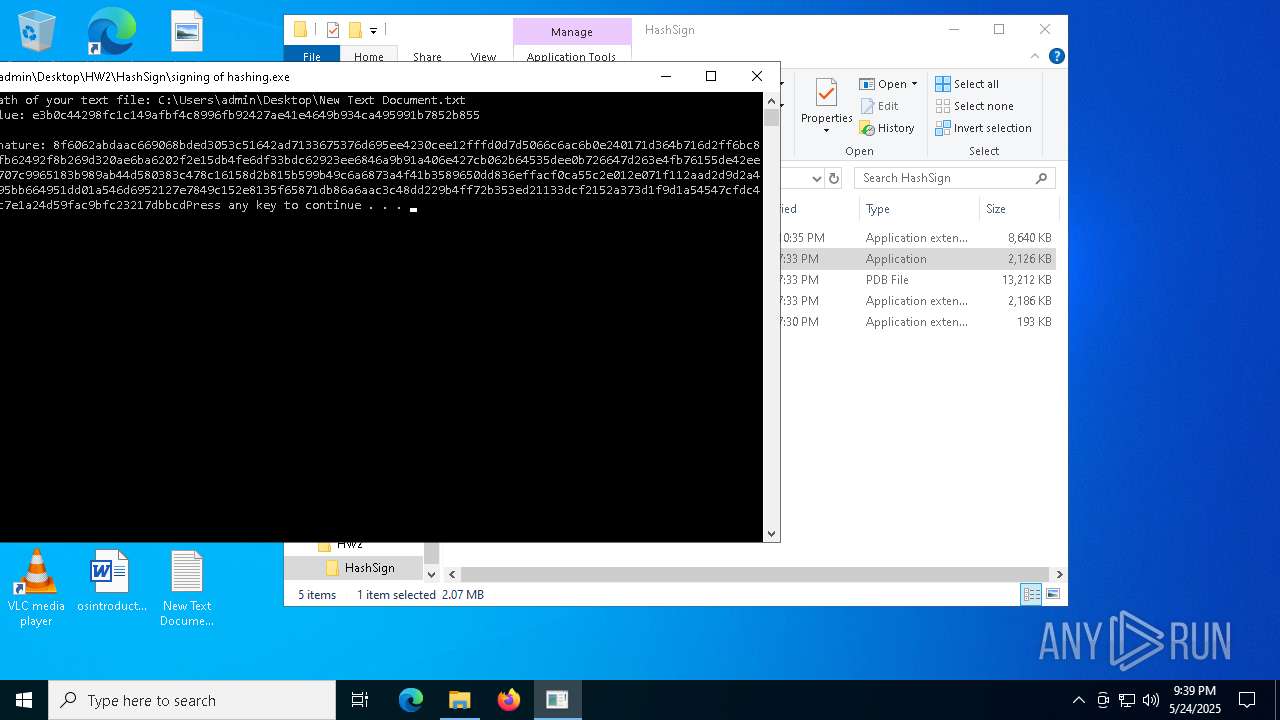
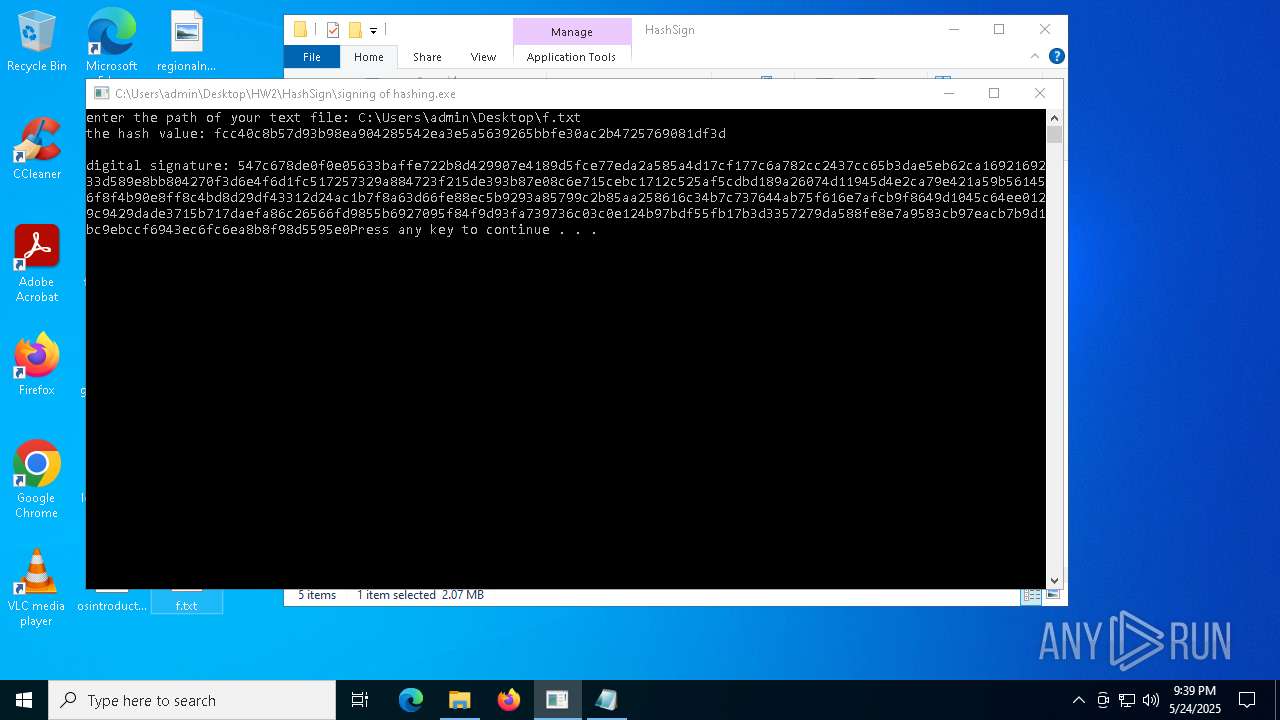
Detected use of alternative data streams (AltDS)
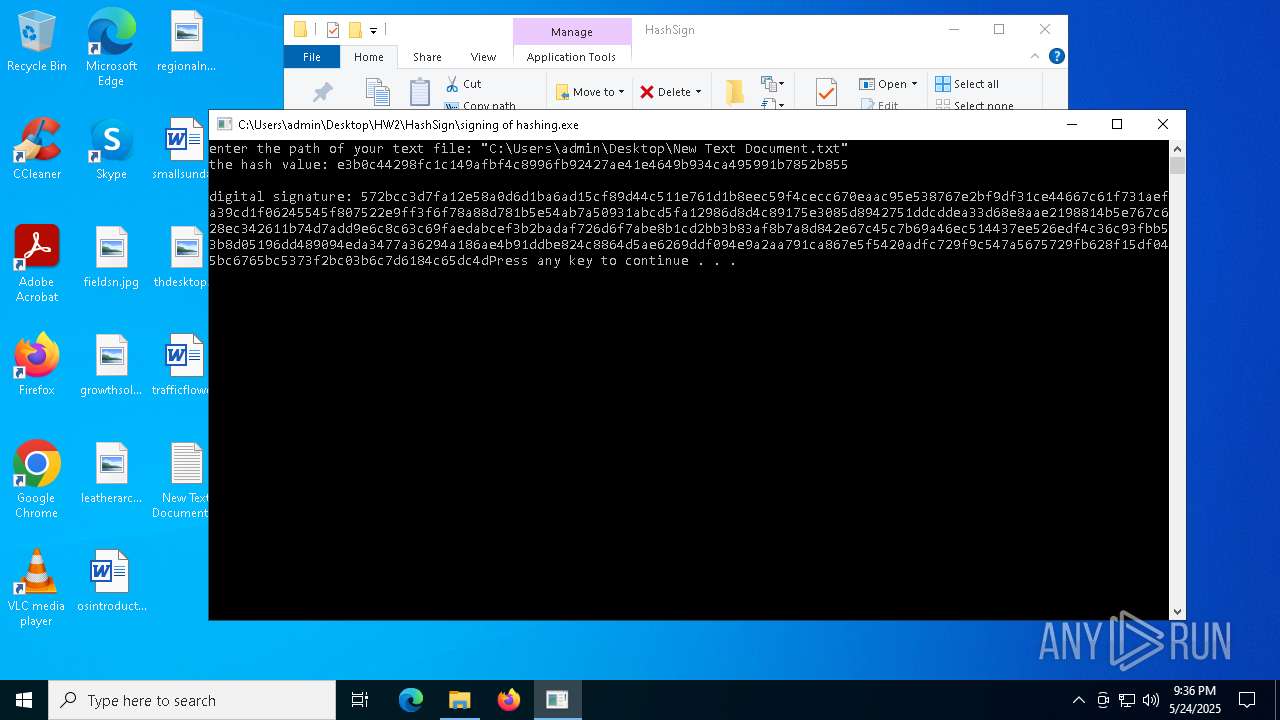
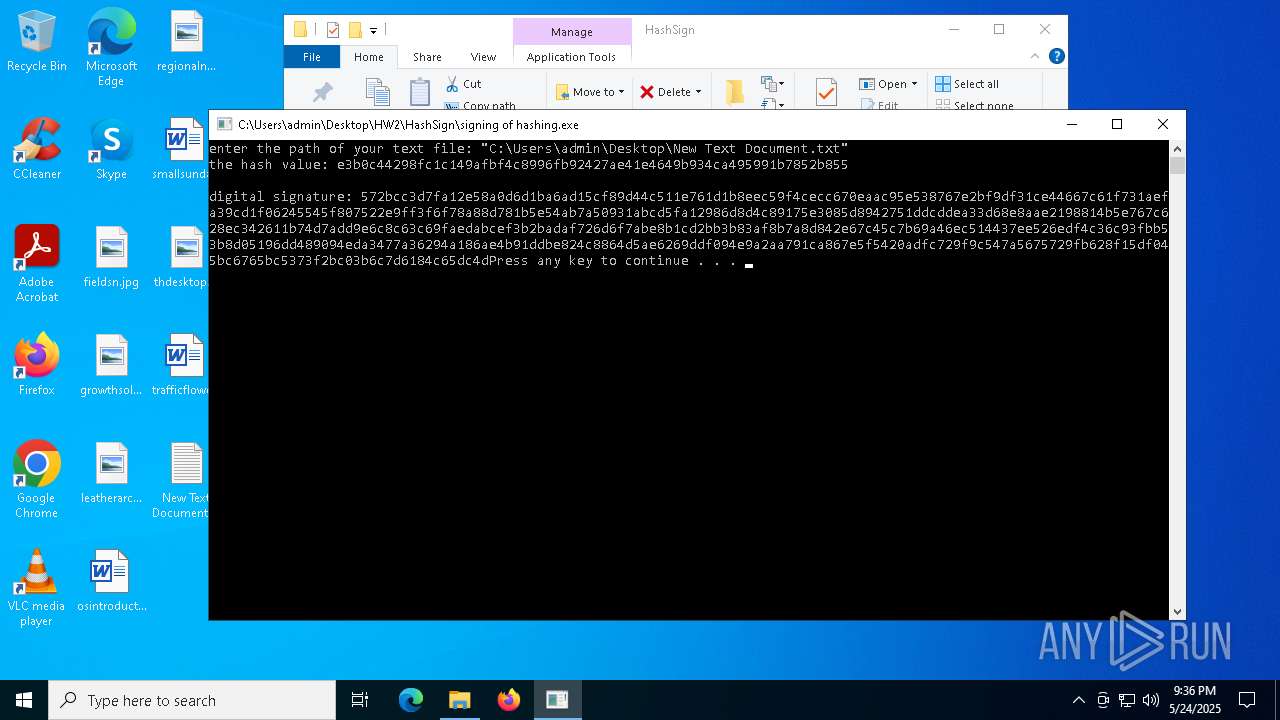
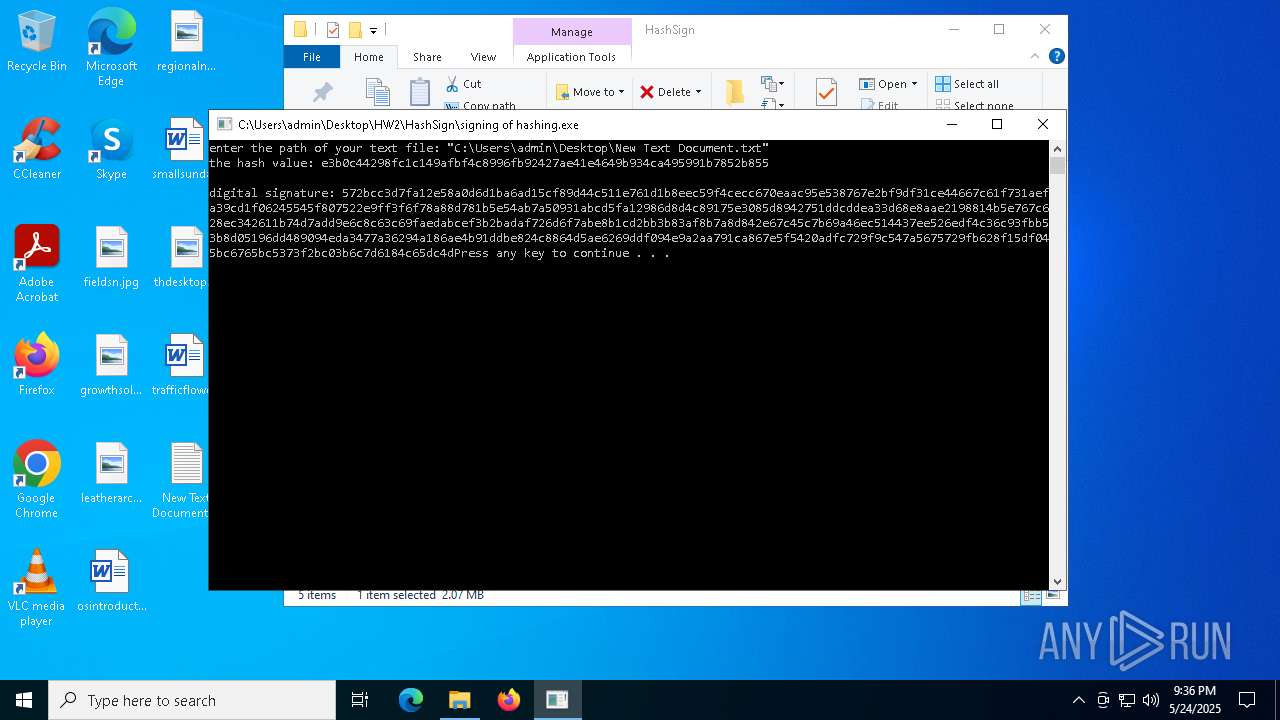
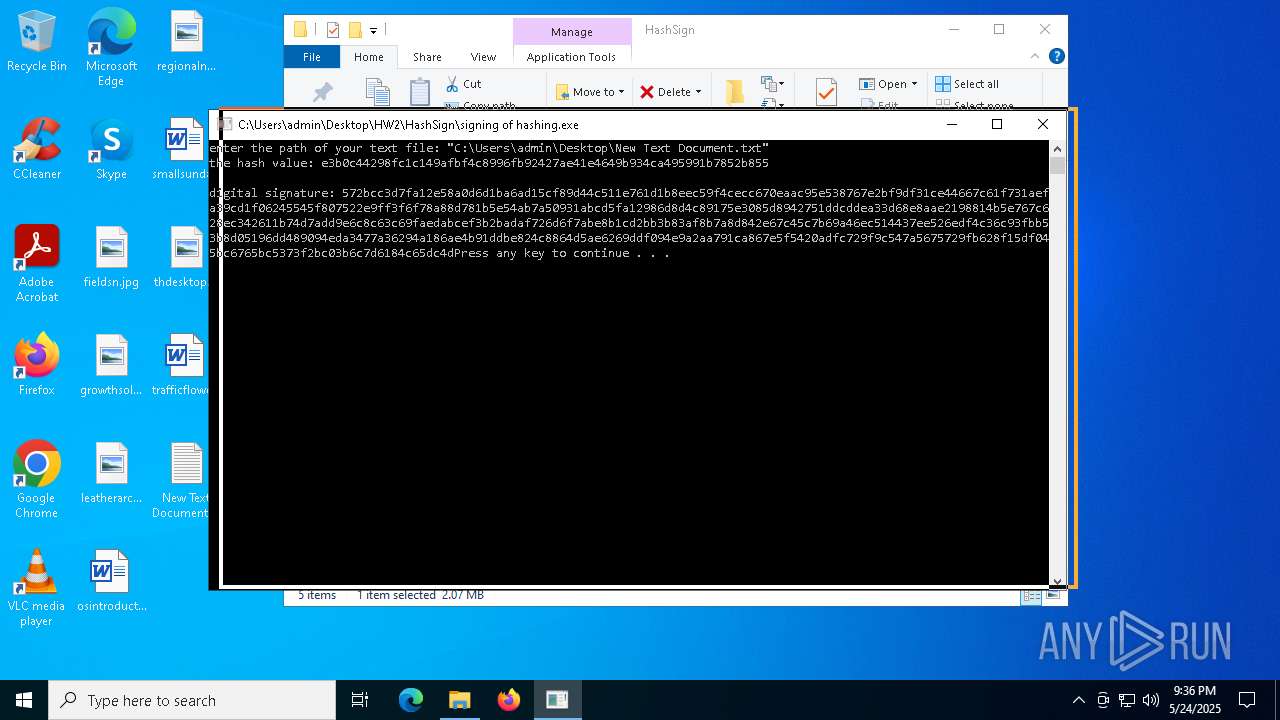
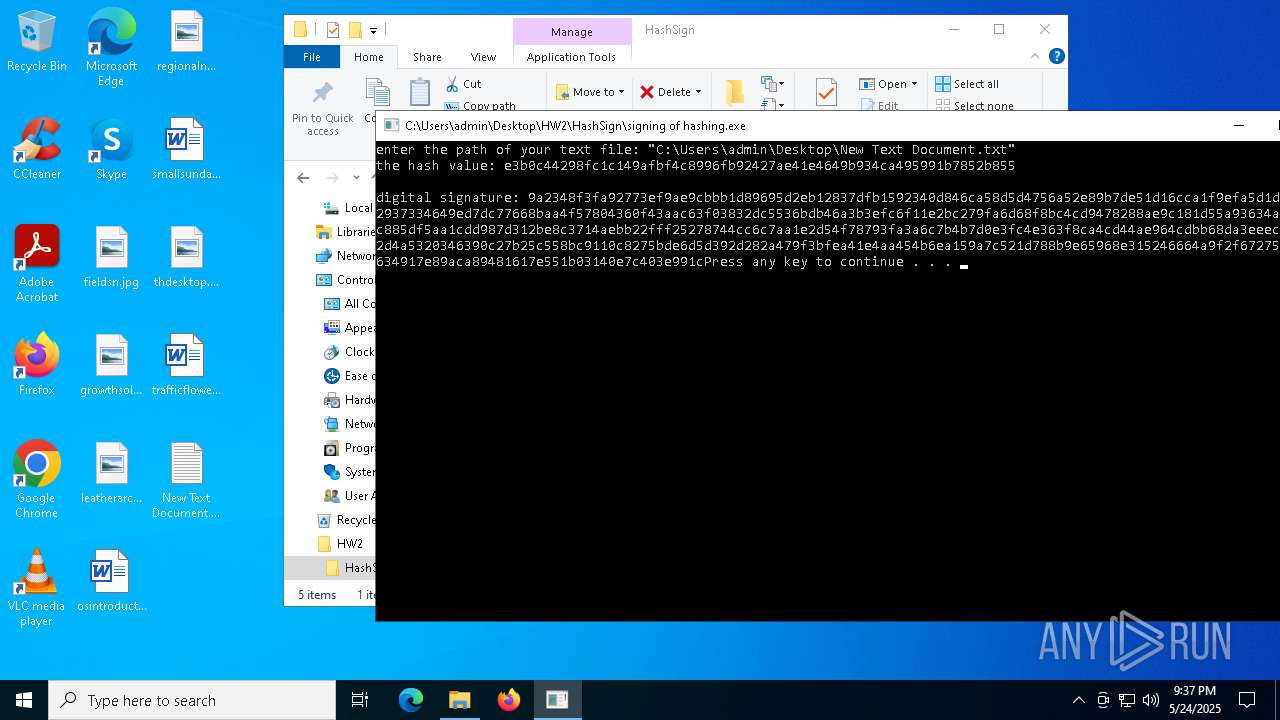
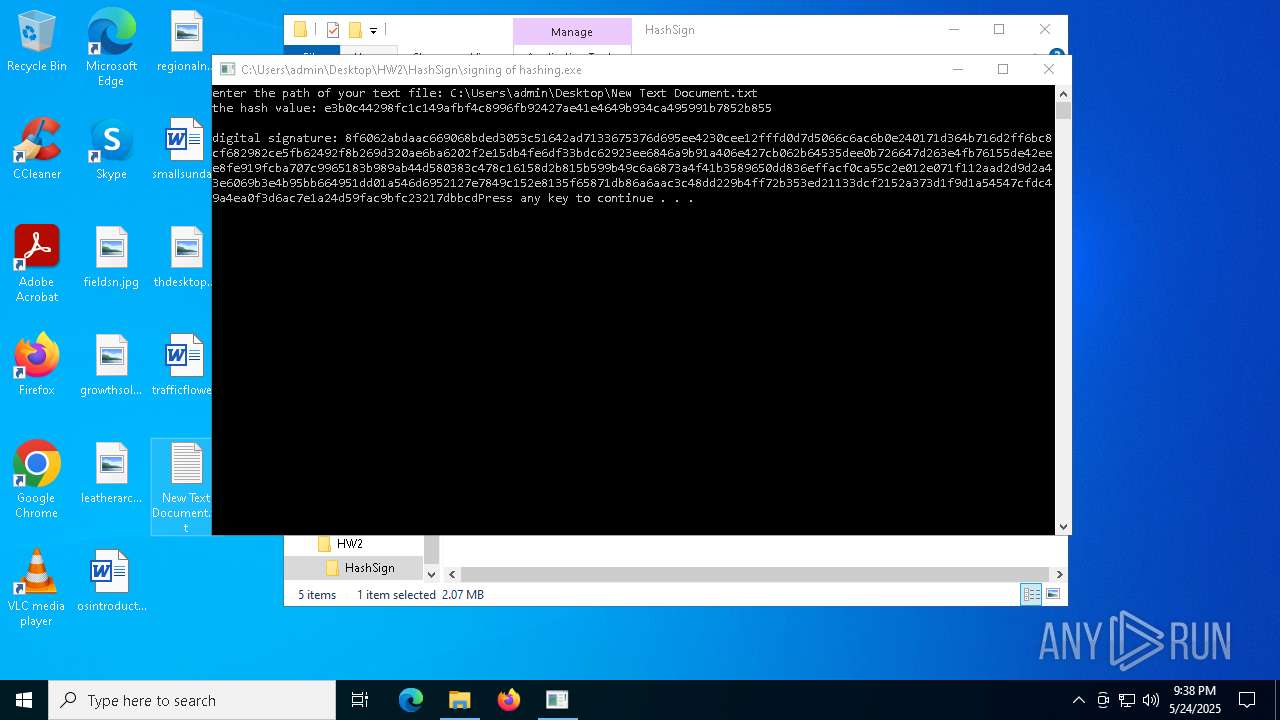
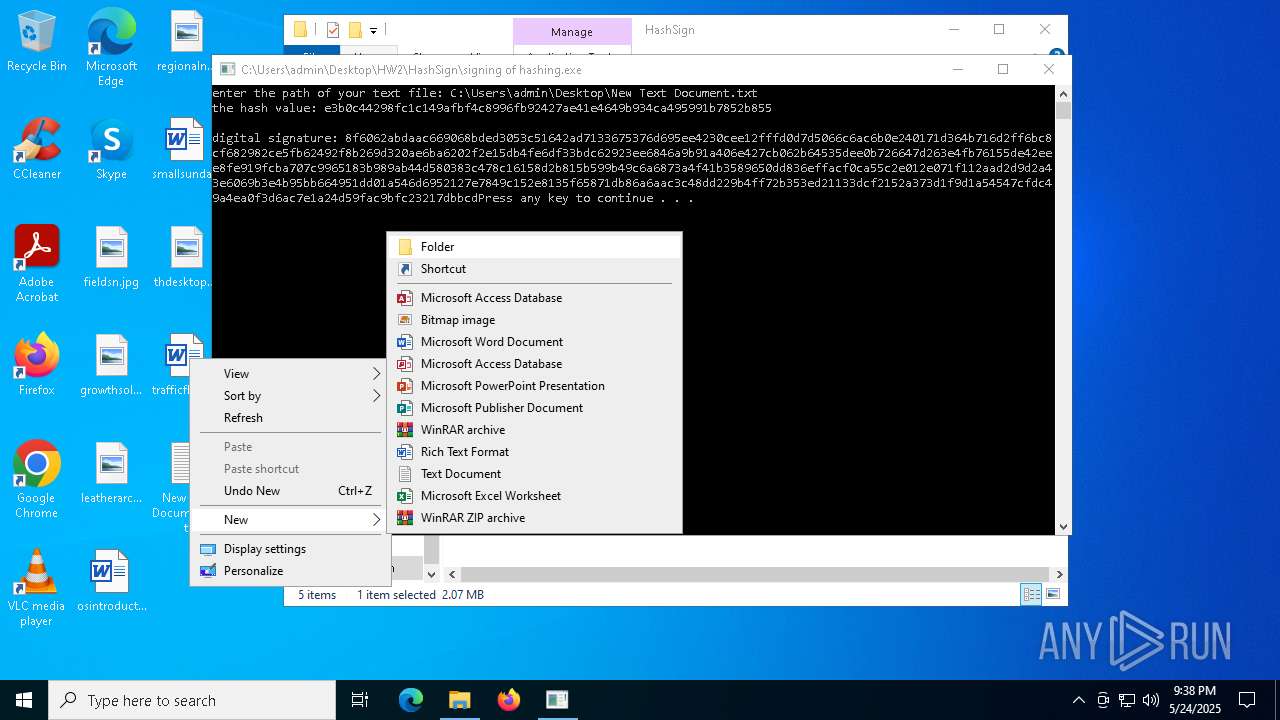
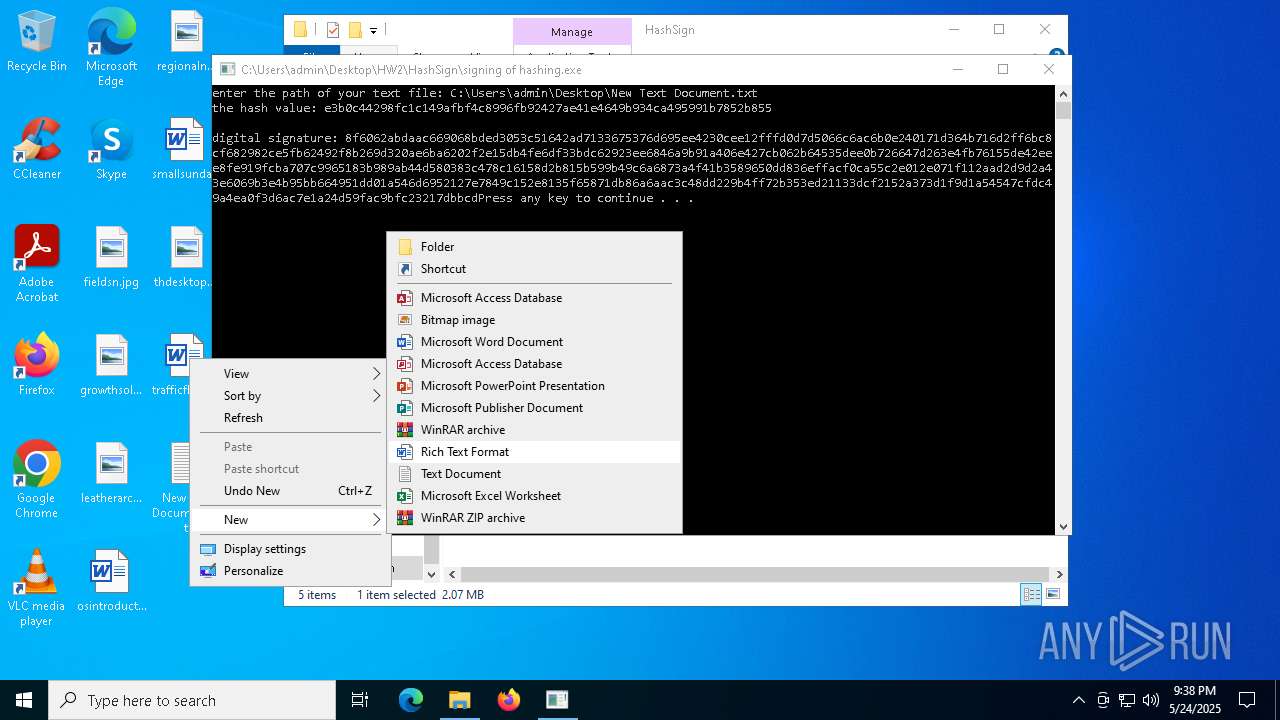
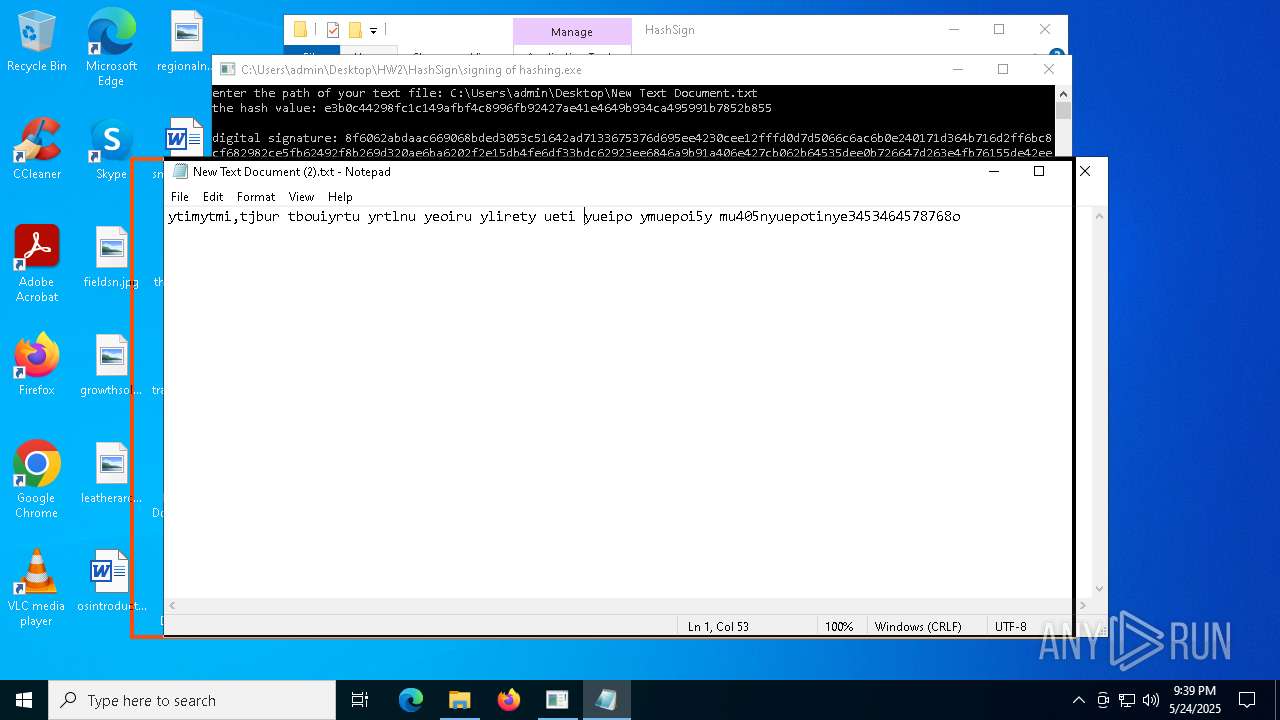
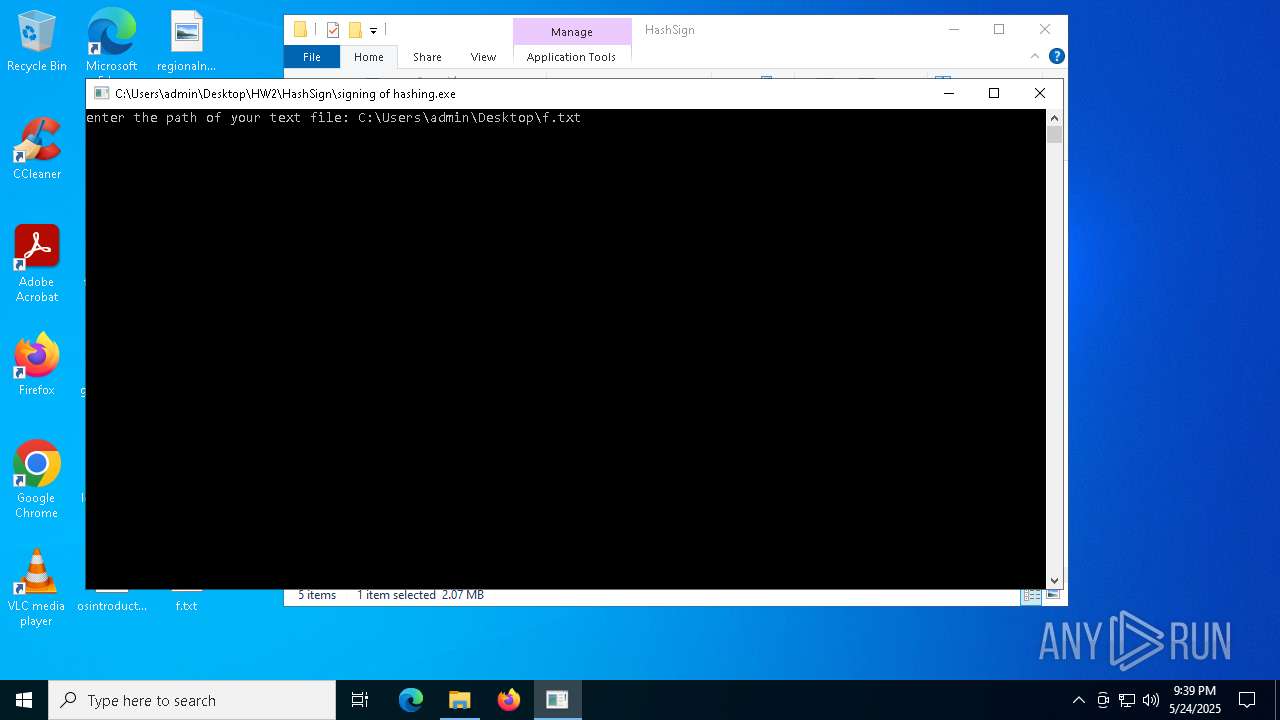
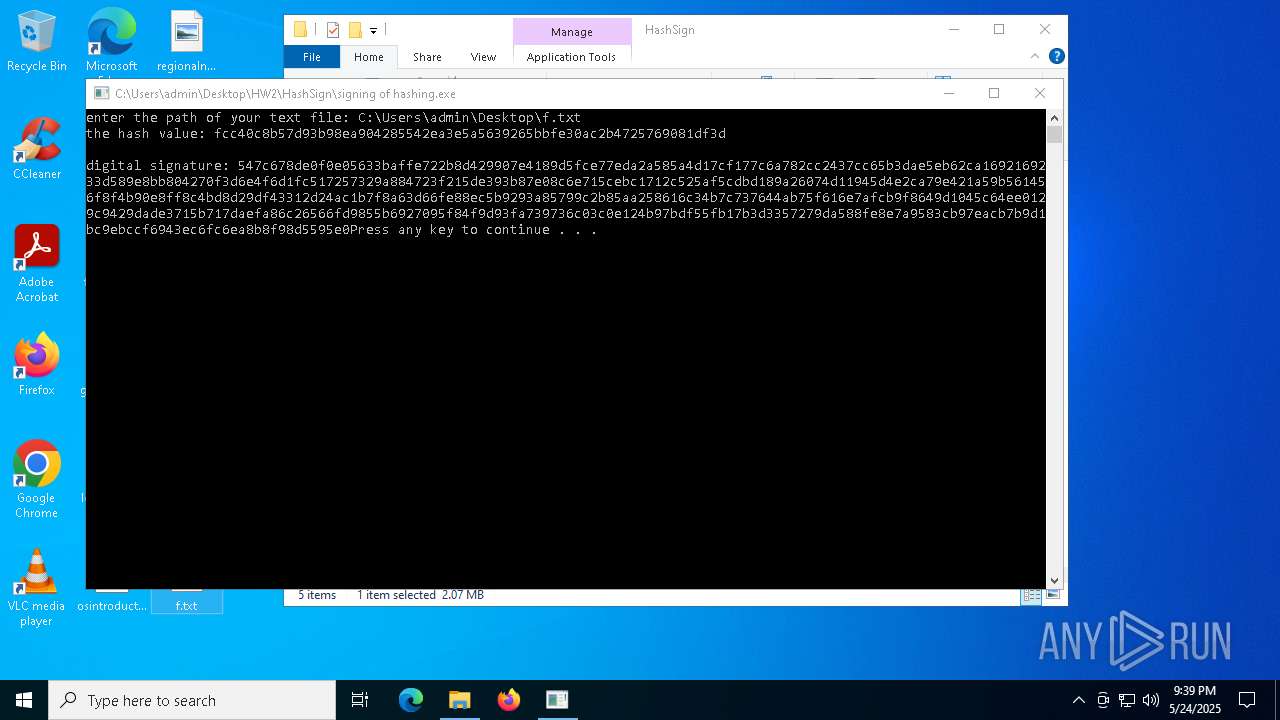
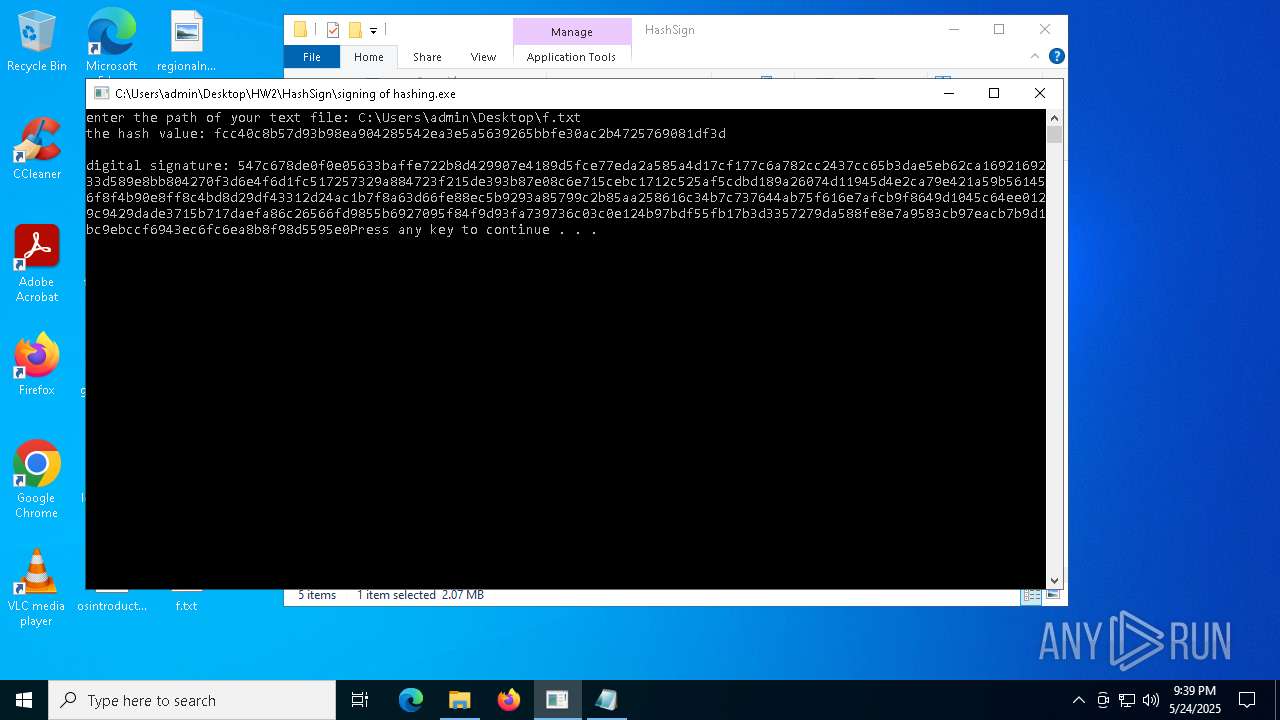
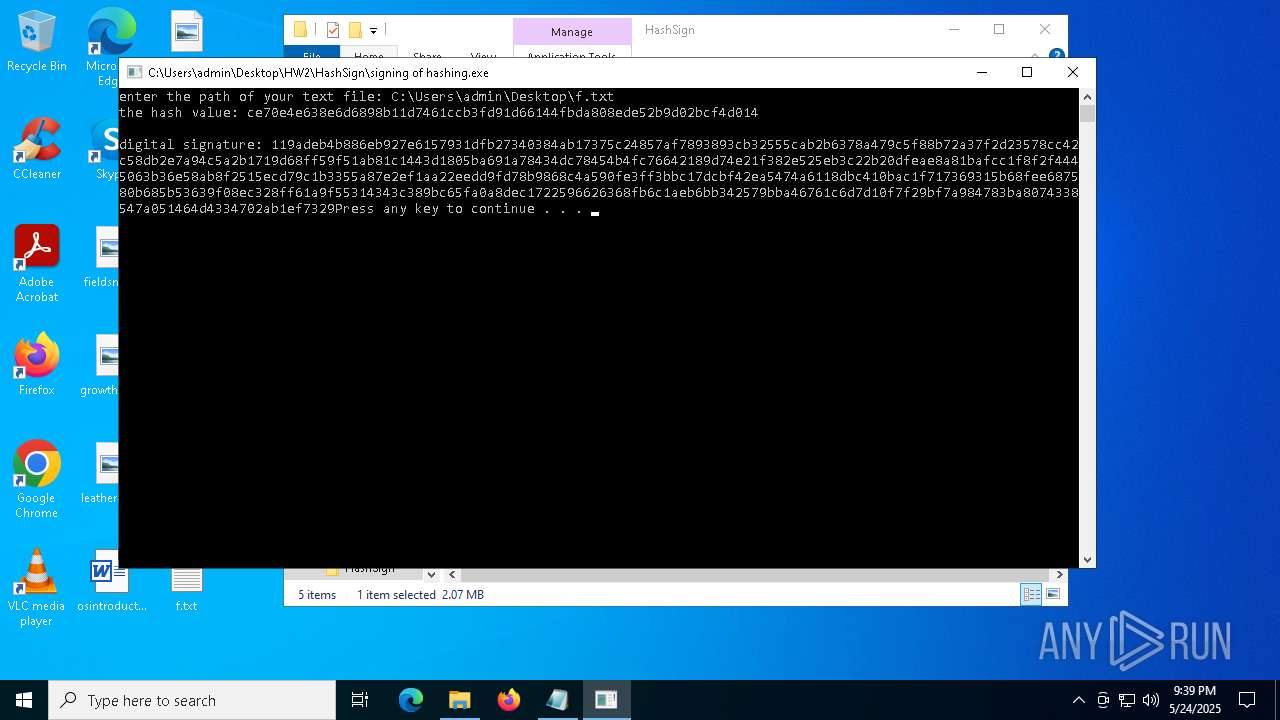
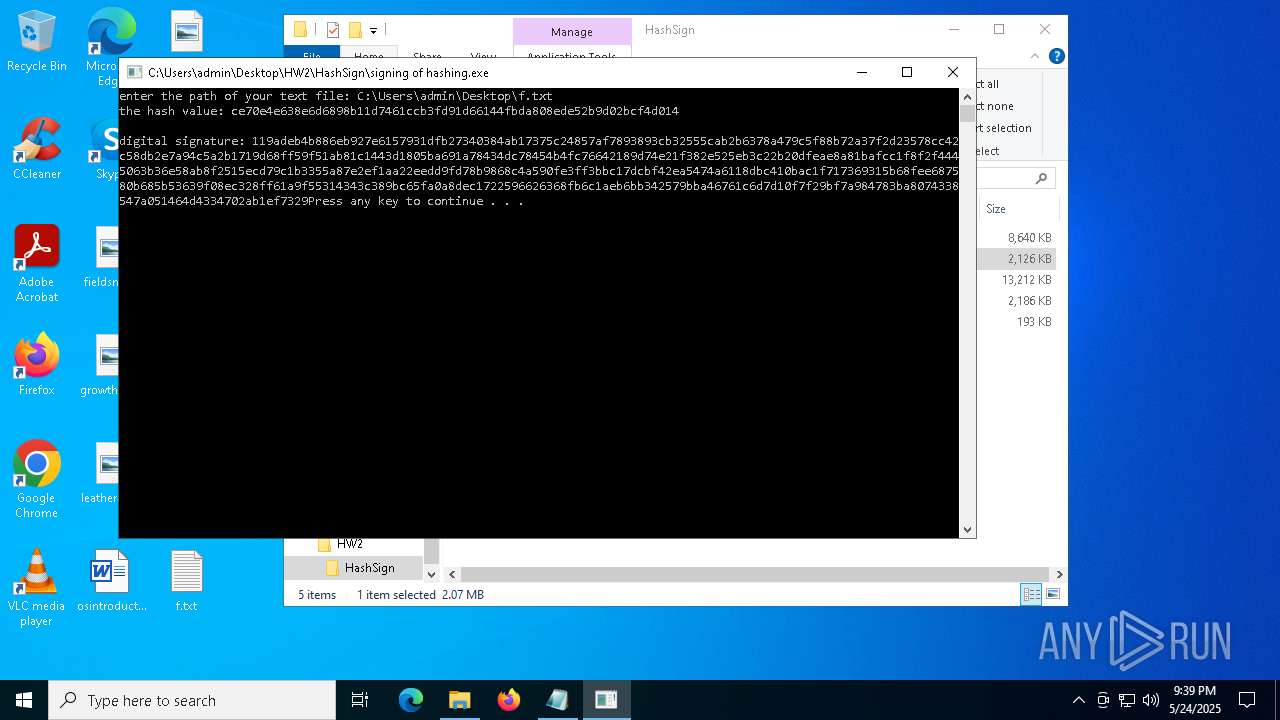
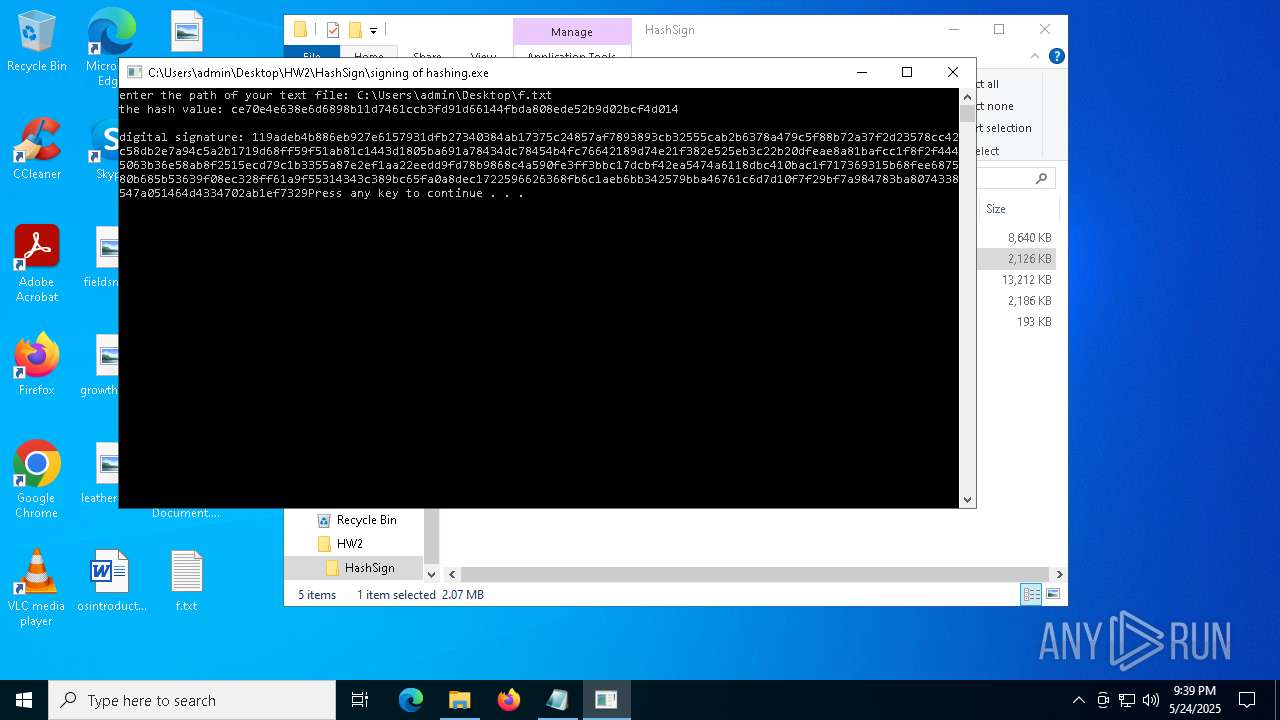
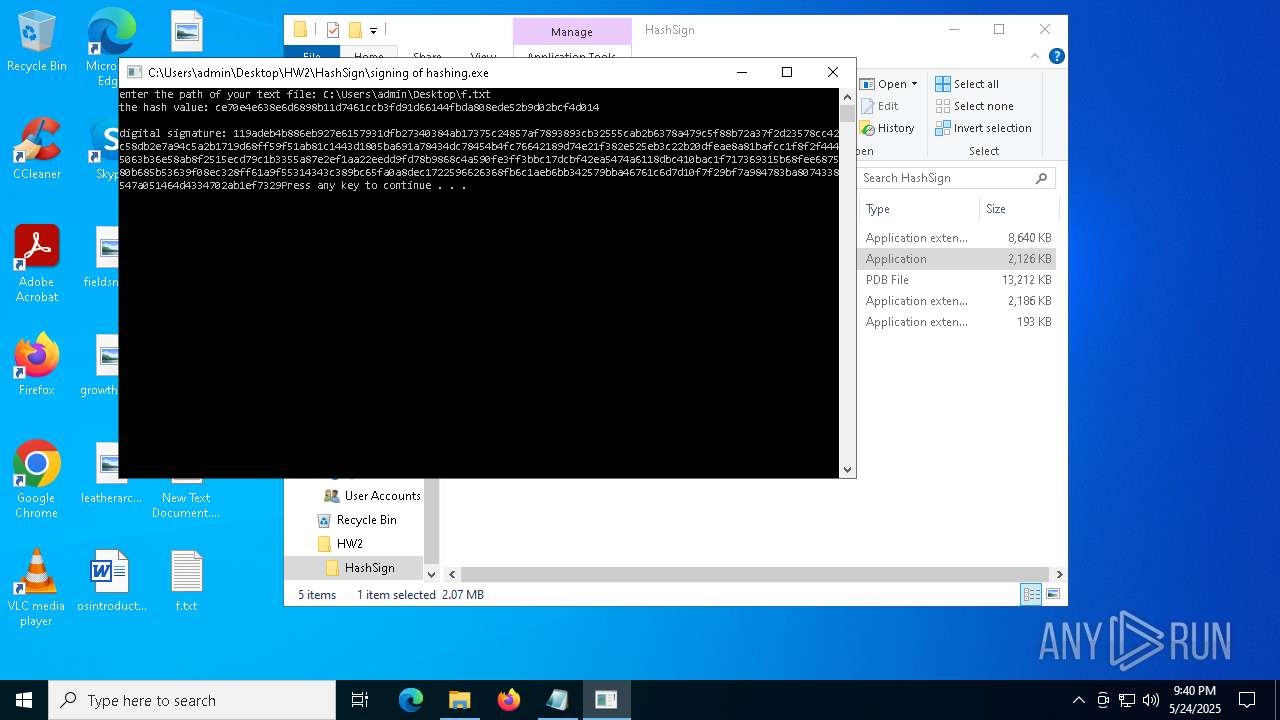
- signing of hashing.exe (PID: 1804)
- signing of hashing.exe (PID: 3896)
- signing of hashing.exe (PID: 4208)
Starts CMD.EXE for commands execution
- signing of hashing.exe (PID: 1804)
- signing of hashing.exe (PID: 3896)
- signing of hashing.exe (PID: 4208)
- signing of hashing.exe (PID: 6268)
- signing of hashing.exe (PID: 6480)
- signing of hashing.exe (PID: 2148)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1452)
The sample compiled with english language support
- WinRAR.exe (PID: 1452)
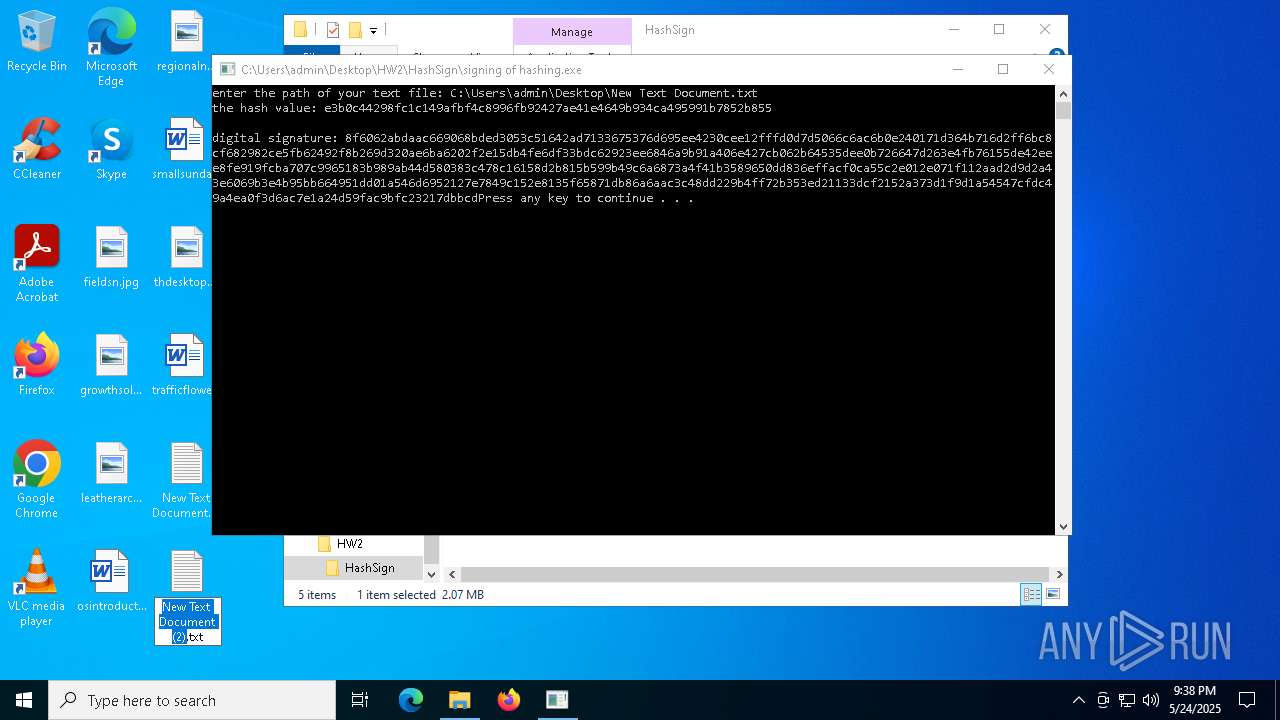
Manual execution by a user
- signing of hashing.exe (PID: 1804)
- notepad.exe (PID: 5720)
- notepad.exe (PID: 6324)
- signing of hashing.exe (PID: 3896)
- notepad.exe (PID: 6156)
- signing of hashing.exe (PID: 4208)
- signing of hashing.exe (PID: 6268)
- notepad.exe (PID: 5408)
- signing of hashing.exe (PID: 5244)
- notepad.exe (PID: 3016)
- signing of hashing.exe (PID: 6480)
- signing of hashing.exe (PID: 2148)
Checks supported languages
- signing of hashing.exe (PID: 1804)
- signing of hashing.exe (PID: 3896)
- signing of hashing.exe (PID: 4208)
- signing of hashing.exe (PID: 6268)
- signing of hashing.exe (PID: 5244)
- signing of hashing.exe (PID: 6480)
- signing of hashing.exe (PID: 2148)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5720)
- notepad.exe (PID: 6324)
- notepad.exe (PID: 5408)
- notepad.exe (PID: 6156)
- notepad.exe (PID: 3016)
Reads the machine GUID from the registry
- signing of hashing.exe (PID: 1804)
- signing of hashing.exe (PID: 3896)
- signing of hashing.exe (PID: 4208)
- signing of hashing.exe (PID: 6268)
- signing of hashing.exe (PID: 6480)
- signing of hashing.exe (PID: 2148)
Reads the software policy settings
- slui.exe (PID: 5008)
- slui.exe (PID: 6880)
Checks proxy server information
- slui.exe (PID: 6880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1635216 |
| UncompressedSize: | 8847360 |
| OperatingSystem: | Win32 |
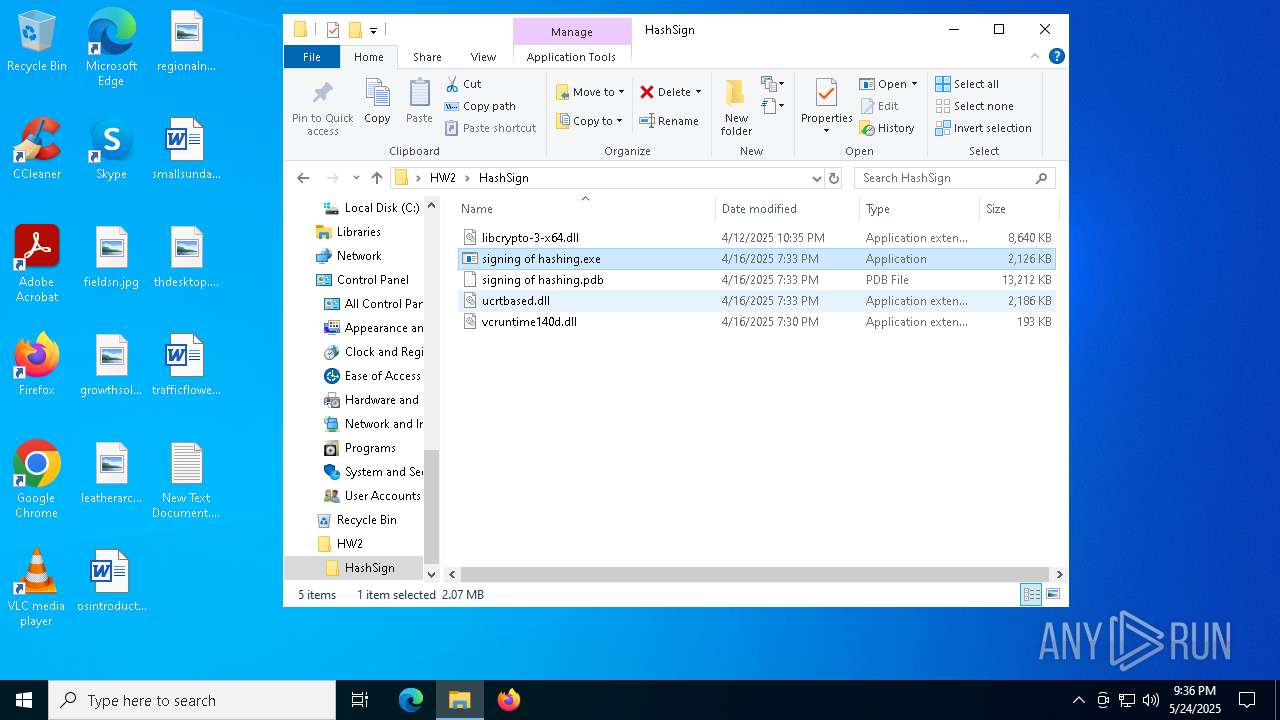
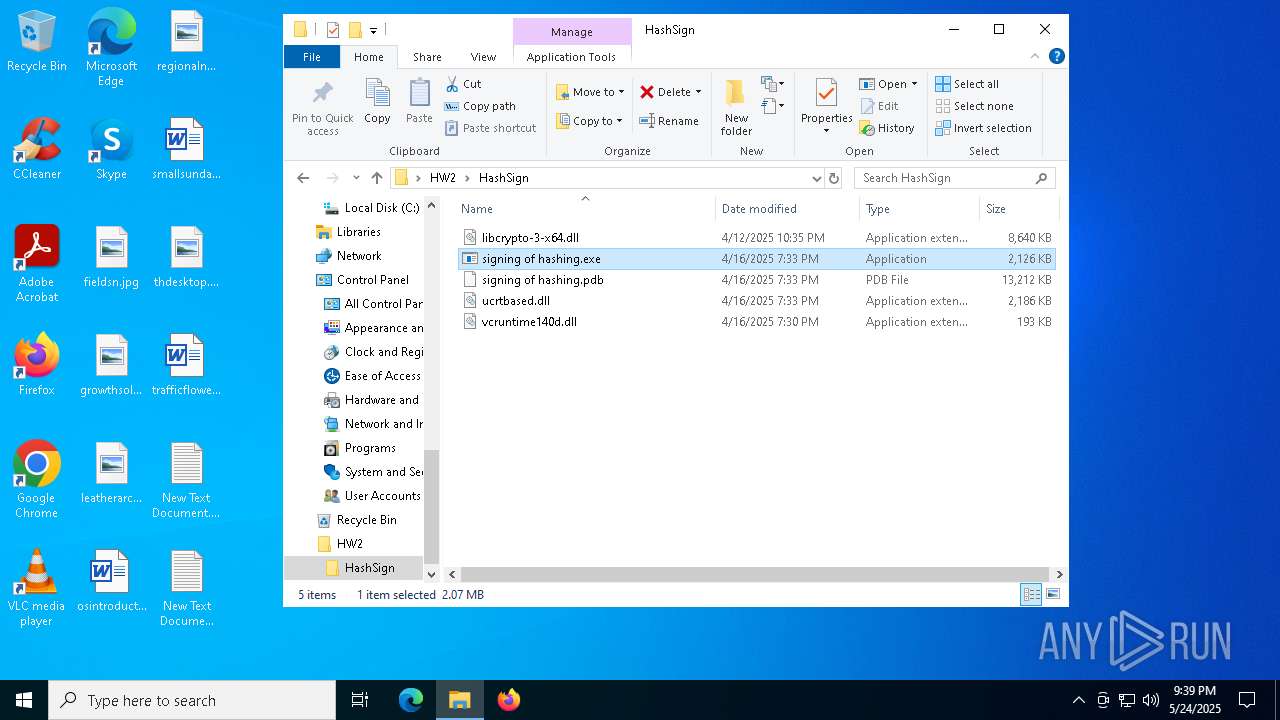
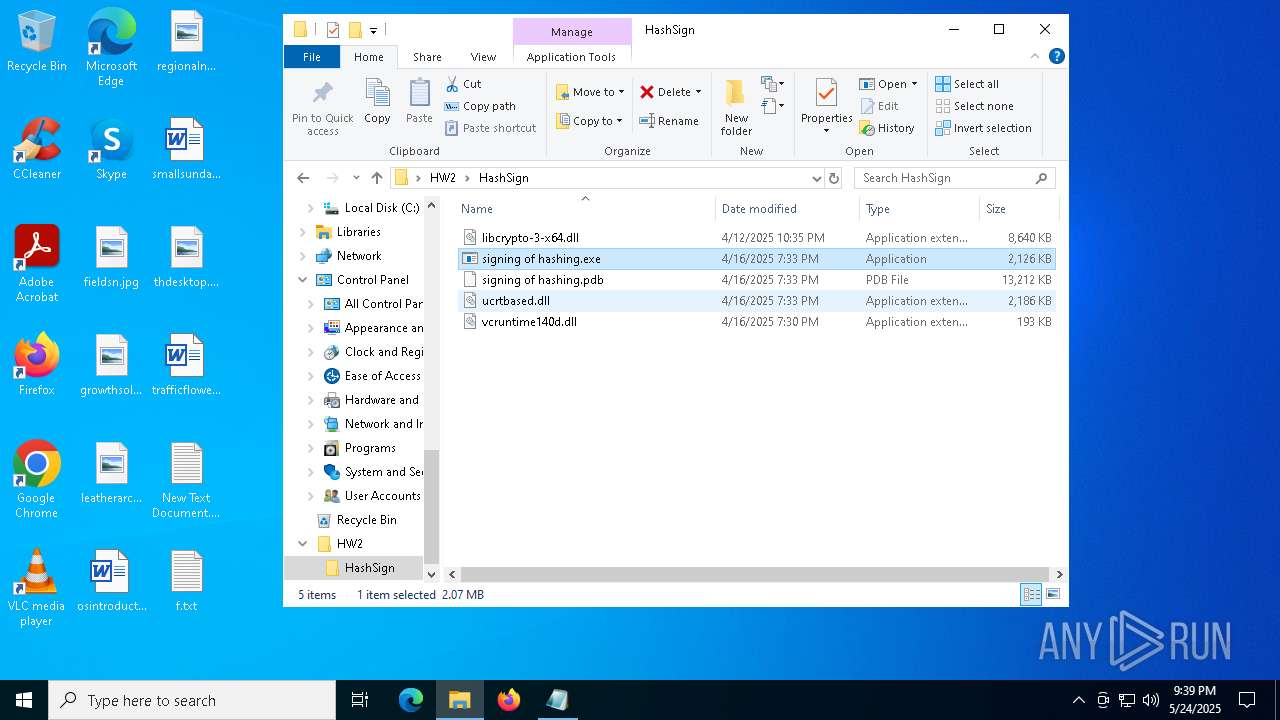
| ArchivedFileName: | HW2/HashSign/libcrypto-3-x64.dll |
Total processes
158
Monitored processes
30
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 300 | C:\WINDOWS\system32\cmd.exe /c PAUSE | C:\Windows\System32\cmd.exe | — | signing of hashing.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 496 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | signing of hashing.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1132 | C:\WINDOWS\system32\cmd.exe /c PAUSE | C:\Windows\System32\cmd.exe | — | signing of hashing.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1276 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | signing of hashing.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1324 | C:\WINDOWS\system32\cmd.exe /c PAUSE | C:\Windows\System32\cmd.exe | — | signing of hashing.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1452 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\HW2.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 | ||||
| 1804 | "C:\Users\admin\Desktop\HW2\HashSign\signing of hashing.exe" | C:\Users\admin\Desktop\HW2\HashSign\signing of hashing.exe | — | explorer.exe |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
| 1804 | C:\WINDOWS\system32\cmd.exe /c PAUSE | C:\Windows\System32\cmd.exe | — | signing of hashing.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 2108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | signing of hashing.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 2148 | "C:\Users\admin\Desktop\HW2\HashSign\signing of hashing.exe" | C:\Users\admin\Desktop\HW2\HashSign\signing of hashing.exe | — | explorer.exe |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
4
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1452.35343\HW2\HashSign\signing of hashing.pdb | — | |
MD5:— | SHA256:— | |||
| 1452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1452.35343\HW2\src.cpp | text | |
MD5:BC1EC7DE25AB6BD7576B1E9D008E17CF | SHA256:B0C936588AA7AFB580987D2458A4AB9C3CFC87014D133EF46DD84AC964872C4F | |||
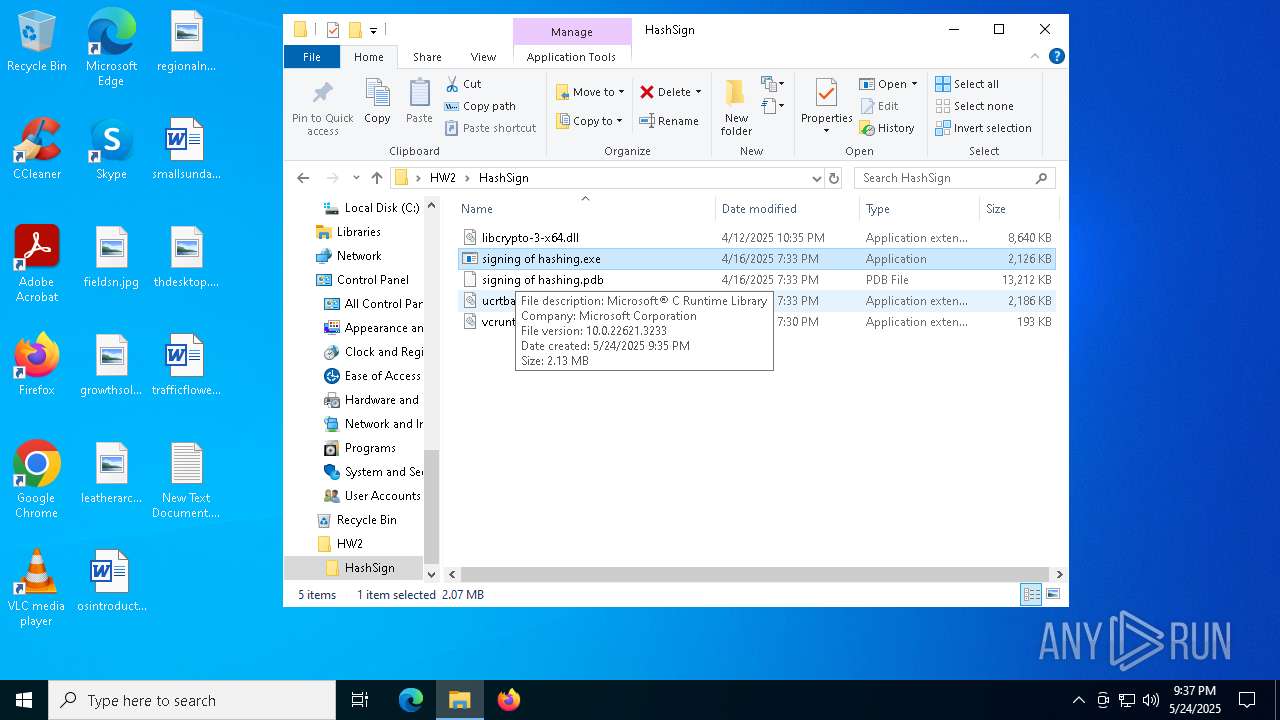
| 1452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1452.35343\HW2\HashSign\vcruntime140d.dll | executable | |
MD5:6DFEEAE14AB3AFB0535822B5E9B70E3E | SHA256:B77FA384C1BBFD7F97710F02EF224373B67E7B004F3F9BB27A35F5C6D0AD3C44 | |||
| 1452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1452.35343\HW2\HashSign\libcrypto-3-x64.dll | executable | |
MD5:1488096D9628676F12714D1376C53144 | SHA256:A641CF05B0CF5A9916F4196DB934E6C74C57C3AB3C373F2B143200F08AC69935 | |||
| 1452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1452.35343\HW2\HashSign\ucrtbased.dll | executable | |
MD5:3A8C1CF9A61F4B68DBD99B9DE1569746 | SHA256:10B6AA53516134EA514B6F9E1A40C2E32662BF5FCF1926C37CC31DA516104519 | |||
| 1452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1452.35343\HW2\HashSign\signing of hashing.exe | executable | |
MD5:093D92FAAA8A3BE16FCC576BC812EDF8 | SHA256:21444C8F4EA03401BF29CE4A9E6205F39C0C44AE77E720081425EE040D354AF2 | |||
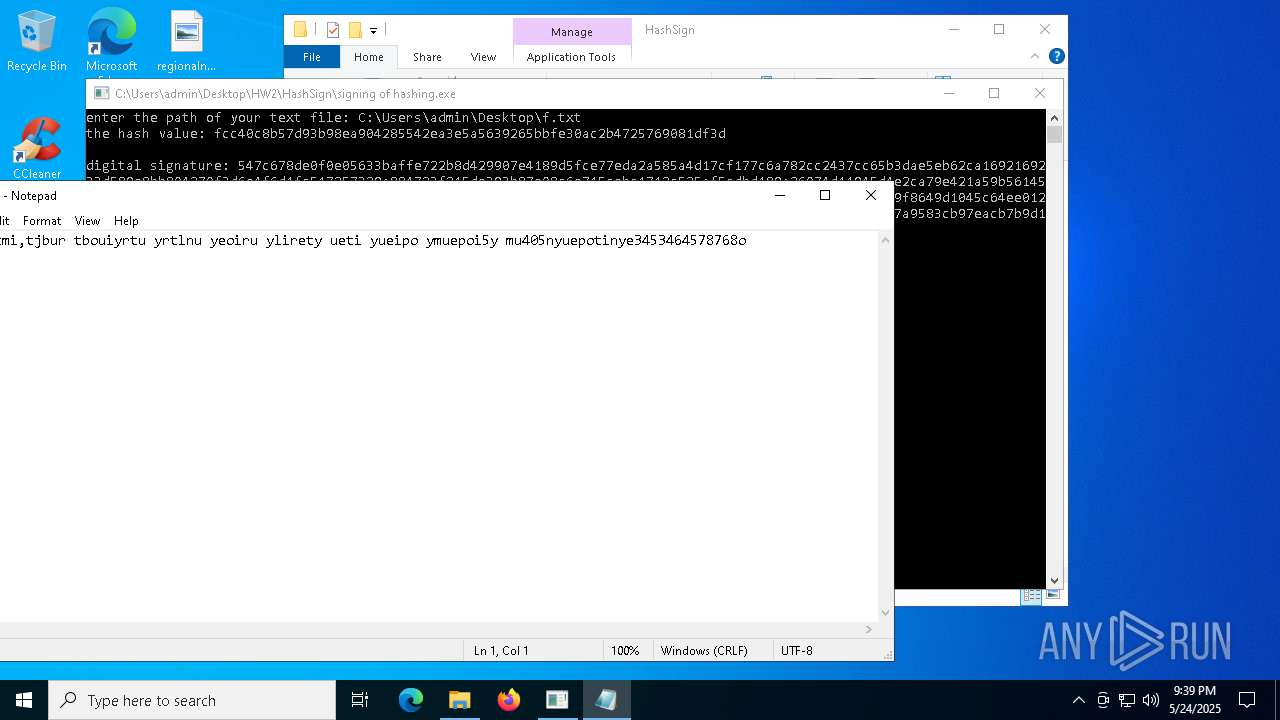
| 5720 | notepad.exe | C:\Users\admin\Desktop\New Text Document.txt | text | |
MD5:ACCEEFD4B53920E4E25E626ACCE6797D | SHA256:56DCB3BC3918B112921B5271021A42C767894674F266D302C8CA249B5D5F1FCD | |||
| 5408 | notepad.exe | C:\Users\admin\Desktop\New Text Document (2).txt | text | |
MD5:FBE03780B11FAD212A2B340D4FDB235D | SHA256:FCC40C8B57D93B98EA904285542EA3E5A5639265BBFE30AC2B4725769081DF3D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1196 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2140 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2140 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |