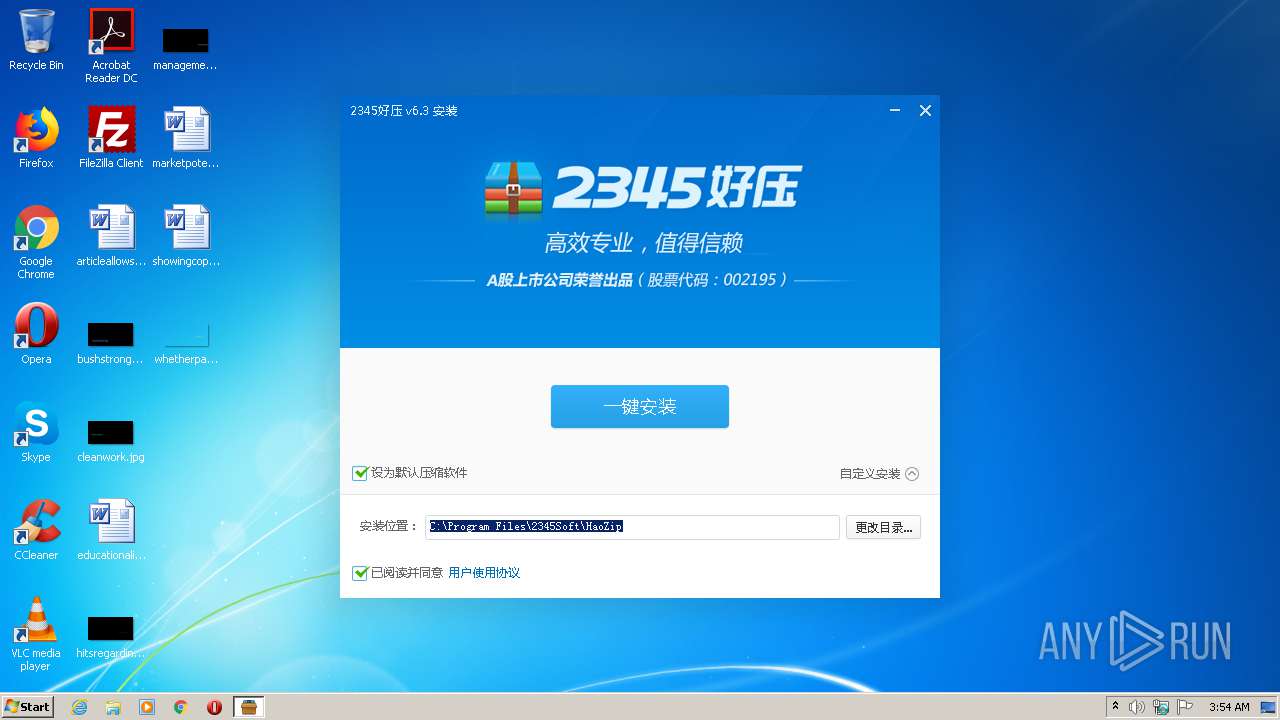
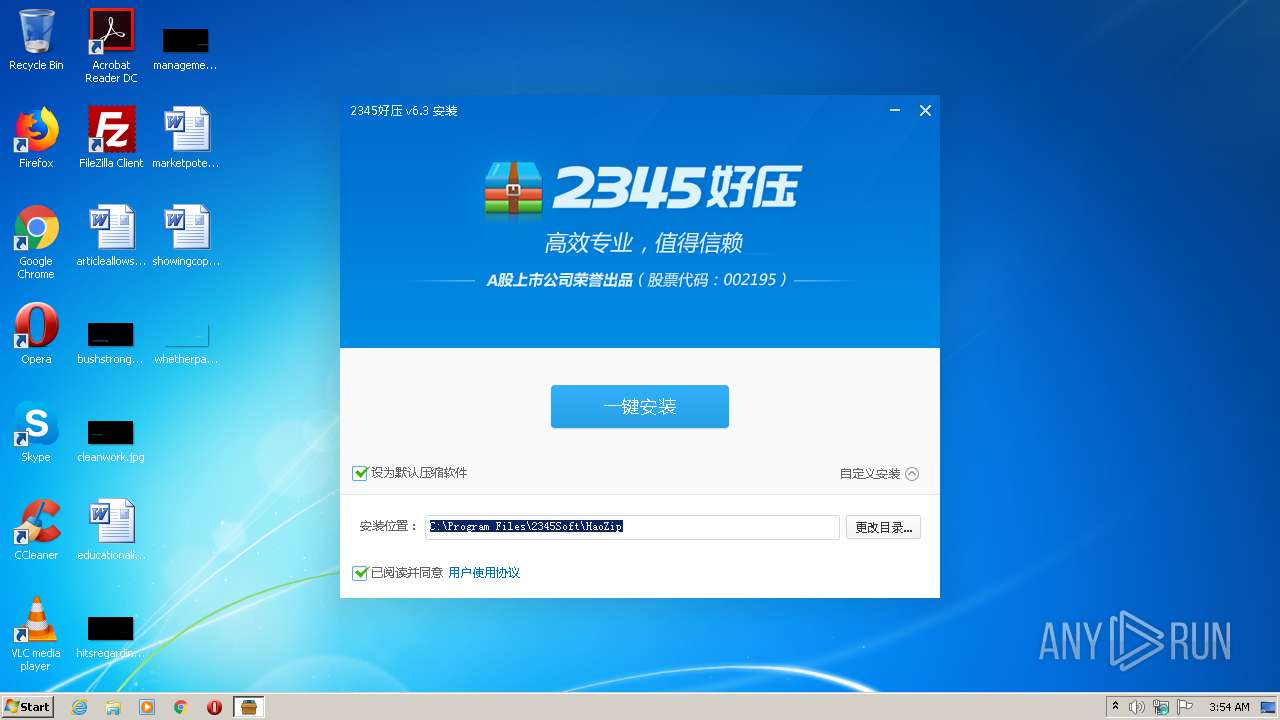
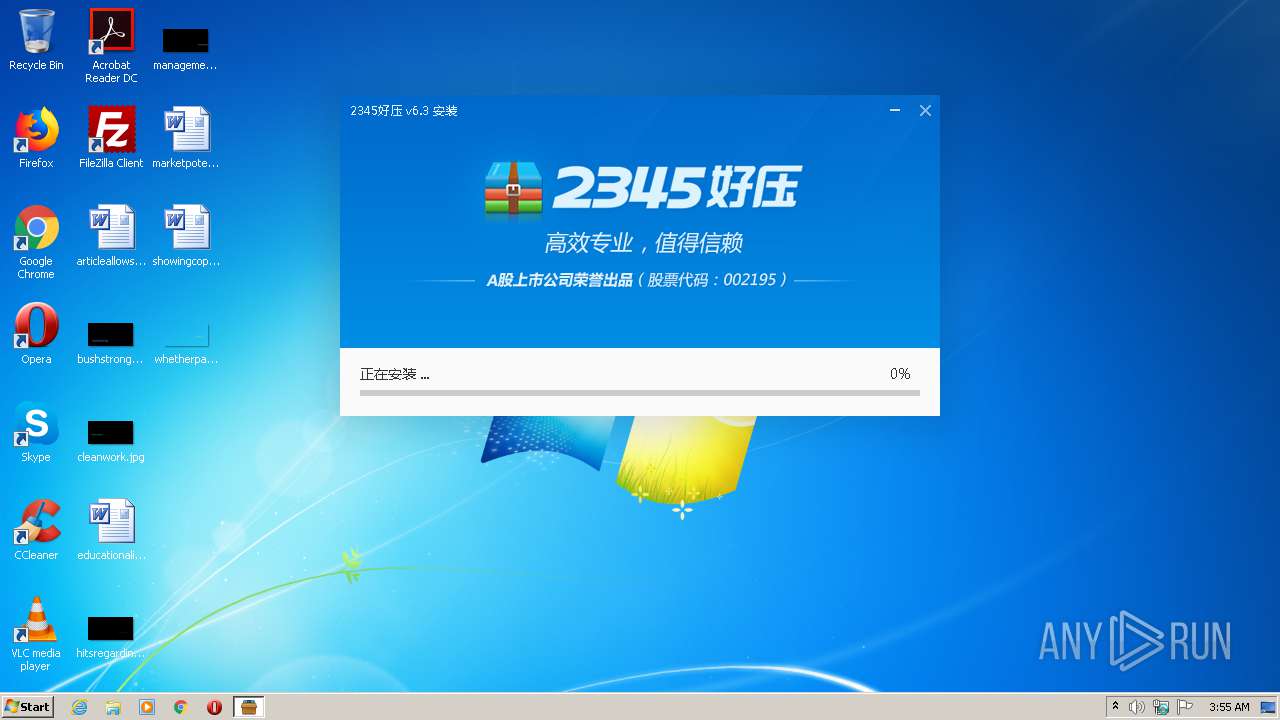
| download: | 2345haozip_000000_6.3.1.11082.exe |
| Full analysis: | https://app.any.run/tasks/5423ecfd-941b-4e53-82b0-a5b2fba56ffe |
| Verdict: | Malicious activity |
| Analysis date: | April 09, 2021, 02:53:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 41DA44DB6AA757E99103286703E296A8 |
| SHA1: | 7FEE53258D9BC74556E2AA08FD2EB49DEDE141E0 |
| SHA256: | C03EA023BC122FA642D1F47683FE1E24791BFA336BF2FCA484A1632B25D09EC7 |
| SSDEEP: | 393216:xFhu6Uj6QV1/6diA9ExyQBxjJO7FnGl2Bwqwx5oIUN7BRlNG5/0k:xDu6VQywAqsQBgQ2B57BdG5 |
MALICIOUS
Loads dropped or rewritten executable
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
- HaoZipLoader.exe (PID: 2104)
- HaoZipLoader.exe (PID: 2392)
- HaoZipLoader.exe (PID: 2980)
Changes settings of System certificates
- HaoZipLoader.exe (PID: 2392)
Application was dropped or rewritten from another process
- HaoZipLoader.exe (PID: 2104)
- HaoZipLoader.exe (PID: 2980)
- HaoZipUpdate.exe (PID: 3432)
- HaoZipLoader.exe (PID: 3932)
- HaoZipLoader.exe (PID: 2392)
Loads the Task Scheduler COM API
- HaoZipLoader.exe (PID: 2104)
SUSPICIOUS
Executable content was dropped or overwritten
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
Creates/Modifies COM task schedule object
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
- HaoZipLoader.exe (PID: 2104)
Drops a file that was compiled in debug mode
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
Creates files in the program directory
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
Drops a file with too old compile date
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
Creates a directory in Program Files
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
Drops a file with a compile date too recent
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
Creates files in the user directory
- HaoZipLoader.exe (PID: 2392)
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
- HaoZipLoader.exe (PID: 2104)
Adds / modifies Windows certificates
- HaoZipLoader.exe (PID: 2392)
Creates a software uninstall entry
- 2345haozip_000000_6.3.1.11082.exe (PID: 604)
Application launched itself
- HaoZipLoader.exe (PID: 2104)
Changes default file association
- HaoZipLoader.exe (PID: 2104)
INFO
Reads settings of System Certificates
- HaoZipLoader.exe (PID: 2392)
- HaoZipLoader.exe (PID: 2104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| SpecialBuild: | 000000 |
|---|---|
| ProductVersion: | 6.3.1.11082 |
| ProductName: | 2345好压 |
| LegalCopyright: | 版权所有 (C) 2018, 2345移动科技 |
| FileVersion: | 6.3.1.11082 |
| FileDescription: | 2345好压 v6.3 安装程序 |
| CompanyName: | 2345移动科技 |
| Comments: | 2345好压 v6.3 |
| CharacterSet: | Windows, Chinese (Simplified) |
| LanguageCode: | Chinese (Simplified) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 6.3.1.11082 |
| FileVersionNumber: | 6.3.1.11082 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5.1 |
| ImageVersion: | 6 |
| OSVersion: | 5.1 |
| EntryPoint: | 0x4f90 |
| UninitializedDataSize: | 4096 |
| InitializedDataSize: | 190976 |
| CodeSize: | 44544 |
| LinkerVersion: | 12 |
| PEType: | PE32 |
| TimeStamp: | 2020:04:29 03:59:53+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 29-Apr-2020 01:59:53 |
| Detected languages: |
|
| Comments: | 2345好压 v6.3 |
| CompanyName: | 2345移动科技 |
| FileDescription: | 2345好压 v6.3 安装程序 |
| FileVersion: | 6.3.1.11082 |
| LegalCopyright: | 版权所有 (C) 2018, 2345移动科技 |
| ProductName: | 2345好压 |
| ProductVersion: | 6.3.1.11082 |
| SpecialBuild: | 000000 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 29-Apr-2020 01:59:53 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000AD22 | 0x0000AE00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.39916 |
.rdata | 0x0000C000 | 0x00001D30 | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.96621 |
.data | 0x0000E000 | 0x0002B660 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.92141 |
.CRT | 0x0003A000 | 0x00000004 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.0611629 |
.ndata | 0x0003B000 | 0x00050000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0008B000 | 0x00004528 | 0x00004600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.15016 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.29299 | 1081 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.4592 | 4264 | UNKNOWN | English - United States | RT_ICON |
3 | 5.30901 | 1128 | UNKNOWN | English - United States | RT_ICON |
103 | 2.45849 | 48 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.55952 | 236 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.36476 | 76 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
46
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | "C:\Users\admin\AppData\Local\Temp\2345haozip_000000_6.3.1.11082.exe" | C:\Users\admin\AppData\Local\Temp\2345haozip_000000_6.3.1.11082.exe | explorer.exe | ||||||||||||
User: admin Company: 2345移动科技 Integrity Level: HIGH Description: 2345好压 v6.3 安装程序 Exit code: 0 Version: 6.3.1.11082 Modules
| |||||||||||||||
| 2104 | "C:\Program Files\2345Soft\HaoZip\HaoZipLoader.exe" -install02 0 7 | C:\Program Files\2345Soft\HaoZip\HaoZipLoader.exe | — | 2345haozip_000000_6.3.1.11082.exe | |||||||||||
User: admin Company: 2345移动科技 Integrity Level: HIGH Description: 2345好压-Windows扩展加载程序 Exit code: 0 Version: 6.3.1.11082 Modules
| |||||||||||||||
| 2392 | "C:\Program Files\2345Soft\HaoZip\HaoZipLoader.exe" --fixdir | C:\Program Files\2345Soft\HaoZip\HaoZipLoader.exe | — | 2345haozip_000000_6.3.1.11082.exe | |||||||||||
User: admin Company: 2345移动科技 Integrity Level: HIGH Description: 2345好压-Windows扩展加载程序 Exit code: 0 Version: 6.3.1.11082 Modules
| |||||||||||||||
| 2540 | "C:\Users\admin\AppData\Local\Temp\2345haozip_000000_6.3.1.11082.exe" | C:\Users\admin\AppData\Local\Temp\2345haozip_000000_6.3.1.11082.exe | — | explorer.exe | |||||||||||
User: admin Company: 2345移动科技 Integrity Level: MEDIUM Description: 2345好压 v6.3 安装程序 Exit code: 3221226540 Version: 6.3.1.11082 Modules
| |||||||||||||||
| 2980 | "C:\Program Files\2345Soft\HaoZip\HaoZipLoader.exe" --rescue --invoke-point=1 | C:\Program Files\2345Soft\HaoZip\HaoZipLoader.exe | — | HaoZipLoader.exe | |||||||||||
User: admin Company: 2345移动科技 Integrity Level: HIGH Description: 2345好压-Windows扩展加载程序 Exit code: 0 Version: 6.3.1.11082 Modules
| |||||||||||||||
| 3432 | "C:\Program Files\2345Soft\HaoZip\HaoZipUpdate.exe" -update-force-config | C:\Program Files\2345Soft\HaoZip\HaoZipUpdate.exe | — | HaoZipLoader.exe | |||||||||||
User: admin Company: 2345移动科技 Integrity Level: HIGH Description: 2345好压-在线升级程序 Exit code: 0 Version: 6.3.1.11082 Modules
| |||||||||||||||
| 3932 | "C:\Program Files\2345Soft\HaoZip\HaoZipLoader.exe" -statistics aq_01#0 | C:\Program Files\2345Soft\HaoZip\HaoZipLoader.exe | — | 2345haozip_000000_6.3.1.11082.exe | |||||||||||
User: admin Company: 2345移动科技 Integrity Level: HIGH Description: 2345好压-Windows扩展加载程序 Exit code: 0 Version: 6.3.1.11082 Modules
| |||||||||||||||
Total events
2 255
Read events
1 106
Write events
1 106
Delete events
43
Modification events
| (PID) Process: | (604) 2345haozip_000000_6.3.1.11082.exe | Key: | HKEY_CURRENT_USER\Software\2345.com\HaoZip |
| Operation: | write | Name: | InstallBy |
Value: explorer.exe 18259 | |||
| (PID) Process: | (604) 2345haozip_000000_6.3.1.11082.exe | Key: | HKEY_CURRENT_USER\Software\2345.com\HaoZip |
| Operation: | write | Name: | UpgradeBy |
Value: | |||
| (PID) Process: | (604) 2345haozip_000000_6.3.1.11082.exe | Key: | HKEY_CURRENT_USER\Software\2345.com\HaoZip |
| Operation: | write | Name: | UninstallBy |
Value: | |||
| (PID) Process: | (2392) HaoZipLoader.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2392) HaoZipLoader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\5FB7EE0633E259DBAD0C4C9AE6D38F1A61C7DC25 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000D474DE575C39B2D39C8583C5C065498A0F0000000100000014000000E35EF08D884F0A0ADE2F75E96301CE6230F213A80300000001000000140000005FB7EE0633E259DBAD0C4C9AE6D38F1A61C7DC251D00000001000000100000008F76B981D528AD4770088245E2031B630B0000000100000012000000440069006700690043006500720074000000140000000100000014000000B13EC36903F8BF4701D498261A0802EF63642BC36200000001000000200000007431E5F4C3C1CE4690774F0B61E05440883BA9A01ED00BA6ABD7806ED3B118CF5300000001000000230000003021301F06096086480186FD6C020130123010060A2B0601040182373C0101030200C0090000000100000034000000303206082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030306082B06010505070308190000000100000010000000BA4F3972E7AED9DCCDC210DB59DA13C92000000001000000C9030000308203C5308202ADA003020102021002AC5C266A0B409B8F0B79F2AE462577300D06092A864886F70D0101050500306C310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D312B30290603550403132244696769436572742048696768204173737572616E636520455620526F6F74204341301E170D3036313131303030303030305A170D3331313131303030303030305A306C310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D312B30290603550403132244696769436572742048696768204173737572616E636520455620526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100C6CCE573E6FBD4BBE52D2D32A6DFE5813FC9CD2549B6712AC3D5943467A20A1CB05F69A640B1C4B7B28FD098A4A941593AD3DC94D63CDB7438A44ACC4D2582F74AA5531238EEF3496D71917E63B6ABA65FC3A484F84F6251BEF8C5ECDB3892E306E508910CC4284155FBCB5A89157E71E835BF4D72093DBE3A38505B77311B8DB3C724459AA7AC6D00145A04B7BA13EB510A984141224E656187814150A6795C89DE194A57D52EE65D1C532C7E98CD1A0616A46873D03404135CA171D35A7C55DB5E64E13787305604E511B4298012F1793988A202117C2766B788B778F2CA0AA838AB0A64C2BF665D9584C1A1251E875D1A500B2012CC41BB6E0B5138B84BCB0203010001A3633061300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF301D0603551D0E04160414B13EC36903F8BF4701D498261A0802EF63642BC3301F0603551D23041830168014B13EC36903F8BF4701D498261A0802EF63642BC3300D06092A864886F70D010105050003820101001C1A0697DCD79C9F3C886606085721DB2147F82A67AABF183276401057C18AF37AD911658E35FA9EFC45B59ED94C314BB891E8432C8EB378CEDBE3537971D6E5219401DA55879A2464F68A66CCDE9C37CDA834B1699B23C89E78222B7043E35547316119EF58C5852F4E30F6A0311623C8E7E2651633CBBF1A1BA03DF8CA5E8B318B6008892D0C065C52B7C4F90A98D1155F9F12BE7C366338BD44A47FE4262B0AC497690DE98CE2C01057B8C876129155F24869D8BC2A025B0F44D42031DBF4BA70265D90609EBC4B17092FB4CB1E4368C90727C1D25CF7EA21B968129C3C9CBF9EFC805C9B63CDEC47AA252767A037F300827D54D7A9F8E92E13A377E81F4A | |||
| (PID) Process: | (2392) HaoZipLoader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\0563B8630D62D75ABBC8AB1E4BDFB5A899B24D43 |
| Operation: | write | Name: | Blob |
Value: 04000000010000001000000087CE0B7B2A0E4900E158719B37A893720F00000001000000140000006DCA5BD00DCF1C0F327059D374B29CA6E3C50AA60300000001000000140000000563B8630D62D75ABBC8AB1E4BDFB5A899B24D431D00000001000000100000004F5F106930398D09107B40C3C7CA8F1C0B000000010000001200000044006900670069004300650072007400000014000000010000001400000045EBA2AFF492CB82312D518BA7A7219DF36DC80F6200000001000000200000003E9099B5015E8F486C00BCEA9D111EE721FABA355A89BCF1DF69561E3DC6325C5300000001000000230000003021301F06096086480186FD6C020130123010060A2B0601040182373C0101030200C0090000000100000034000000303206082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030306082B06010505070308190000000100000010000000749966CECC95C1874194CA7203F9B6202000000001000000BB030000308203B73082029FA00302010202100CE7E0E517D846FE8FE560FC1BF03039300D06092A864886F70D01010505003065310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D312430220603550403131B4469676943657274204173737572656420494420526F6F74204341301E170D3036313131303030303030305A170D3331313131303030303030305A3065310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D312430220603550403131B4469676943657274204173737572656420494420526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100AD0E15CEE443805CB187F3B760F97112A5AEDC269488AAF4CEF520392858600CF880DAA9159532613CB5B128848A8ADC9F0A0C83177A8F90AC8AE779535C31842AF60F98323676CCDEDD3CA8A2EF6AFB21F25261DF9F20D71FE2B1D9FE1864D2125B5FF9581835BC47CDA136F96B7FD4B0383EC11BC38C33D9D82F18FE280FB3A783D6C36E44C061359616FE599C8B766DD7F1A24B0D2BFF0B72DA9E60D08E9035C678558720A1CFE56D0AC8497C3198336C22E987D0325AA2BA138211ED39179D993A72A1E6FAA4D9D5173175AE857D22AE3F014686F62879C8B1DAE45717C47E1C0EB0B492A656B3BDB297EDAAA7F0B7C5A83F9516D0FFA196EB085F18774F0203010001A3633061300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF301D0603551D0E0416041445EBA2AFF492CB82312D518BA7A7219DF36DC80F301F0603551D2304183016801445EBA2AFF492CB82312D518BA7A7219DF36DC80F300D06092A864886F70D01010505000382010100A20EBCDFE2EDF0E372737A6494BFF77266D832E4427562AE87EBF2D5D9DE56B39FCCCE1428B90D97605C124C58E4D33D834945589735691AA847EA56C679AB12D8678184DF7F093C94E6B8262C20BD3DB32889F75FFF22E297841FE965EF87E0DFC16749B35DEBB2092AEB26ED78BE7D3F2BF3B726356D5F8901B6495B9F01059BAB3D25C1CCB67FC2F16F86C6FA6468EB812D94EB42B7FA8C1EDD62F1BE5067B76CBDF3F11F6B0C3607167F377CA95B6D7AF112466083D72704BE4BCE97BEC3672A6811DF80E70C3366BF130D146EF37F1F63101EFA8D1B256D6C8FA5B76101B1D2A326A110719DADE2C3F9C39951B72B0708CE2EE650B2A7FA0A452FA2F0F2 | |||
| (PID) Process: | (604) 2345haozip_000000_6.3.1.11082.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {5FED836A-C96C-4d88-A91E-F63F07726585} |
Value: HaoZip Shell Extension | |||
| (PID) Process: | (604) 2345haozip_000000_6.3.1.11082.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{5FED836A-C96C-4d88-A91E-F63F07726585} |
| Operation: | write | Name: | (default) |
Value: HaoZip Shell Extension | |||
| (PID) Process: | (604) 2345haozip_000000_6.3.1.11082.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{5FED836A-C96C-4d88-A91E-F63F07726585}\InprocServer32 |
| Operation: | write | Name: | (default) |
Value: C:\Program Files\2345Soft\HaoZip\HaoZipExt.dll | |||
| (PID) Process: | (604) 2345haozip_000000_6.3.1.11082.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{5FED836A-C96C-4d88-A91E-F63F07726585}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
Executable files
98
Suspicious files
11
Text files
7
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Users\admin\AppData\Local\Temp\nskAF3E.tmp\RCWidgetPlugin.dll | executable | |
MD5:— | SHA256:— | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Users\admin\AppData\Local\Temp\nskAF3E.tmp\System.dll | executable | |
MD5:736012EAAD895766D1A73AD1AB4CE105 | SHA256:1EDB0CF663CE51F11AA17DC2D8F7B7329910E7801A21E686F95BB1B8354EBA78 | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Program Files\2345Soft\HaoZip\api-ms-win-core-heap-l1-1-0.dll | executable | |
MD5:FF8026DAB5D3DABCA8F72B6FA7D258FA | SHA256:535E9D20F00A2F1A62F843A4A26CFB763138D5DFE358B0126D33996FBA9CA4D1 | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Program Files\2345Soft\HaoZip\api-ms-win-core-libraryloader-l1-1-0.dll | executable | |
MD5:0C48220A4485F36FEED84EF5DD0A5E9C | SHA256:2DD4EBAA12CBBA142B5D61A0EBF84A14D0D1BB8826BA42B63E303FE6721408DF | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Program Files\2345Soft\HaoZip\api-ms-win-core-interlocked-l1-1-0.dll | executable | |
MD5:CFE87D58F973DAEDA4EE7D2CF4AE521D | SHA256:4997FDA5D0E90B8A0AB7DA314CB56F25D1450B366701C45C294D8DD3254DE483 | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Program Files\2345Soft\HaoZip\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:AABBB38C4110CC0BF7203A567734A7E7 | SHA256:24B07028C1E38B9CA2F197750654A0DFB7D33C2E52C9DD67100609499E8028DB | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Program Files\2345Soft\HaoZip\api-ms-win-core-memory-l1-1-0.dll | executable | |
MD5:3940167FFB4383992E73F9A10E4B8B1E | SHA256:EC573431338371504B7B9E57B2D91382B856AABF25D2B4AD96486EFB794C198E | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Program Files\2345Soft\HaoZip\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:3F224766FE9B090333FDB43D5A22F9EA | SHA256:AE5E73416EB64BC18249ACE99F6847024ECEEA7CE9C343696C84196460F3A357 | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Program Files\2345Soft\HaoZip\api-ms-win-core-localization-l1-2-0.dll | executable | |
MD5:23BD405A6CFD1E38C74C5150EEC28D0A | SHA256:A7FA48DE6C06666B80184AFEE7E544C258E0FB11399AB3FE47D4E74667779F41 | |||
| 604 | 2345haozip_000000_6.3.1.11082.exe | C:\Program Files\2345Soft\HaoZip\api-ms-win-core-namedpipe-l1-1-0.dll | executable | |
MD5:990AC84AE2D83EEB532A28FE29602827 | SHA256:DBD788B1C5694D65FA6F6E2202BFABB30ADF77EB1973CEB9A737EFB16E9EDAE2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
604 | 2345haozip_000000_6.3.1.11082.exe | 180.163.196.56:443 | update-haozip.2345.cc | China Telecom (Group) | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
update-haozip.2345.cc |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |