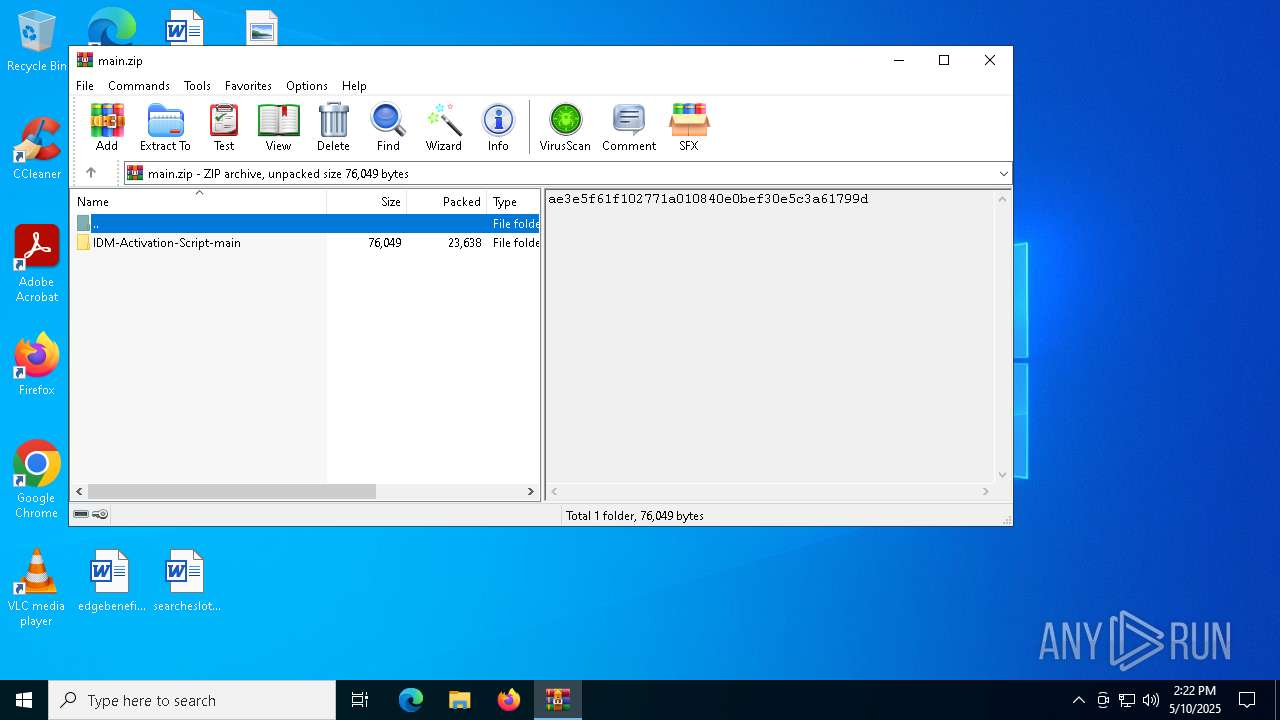
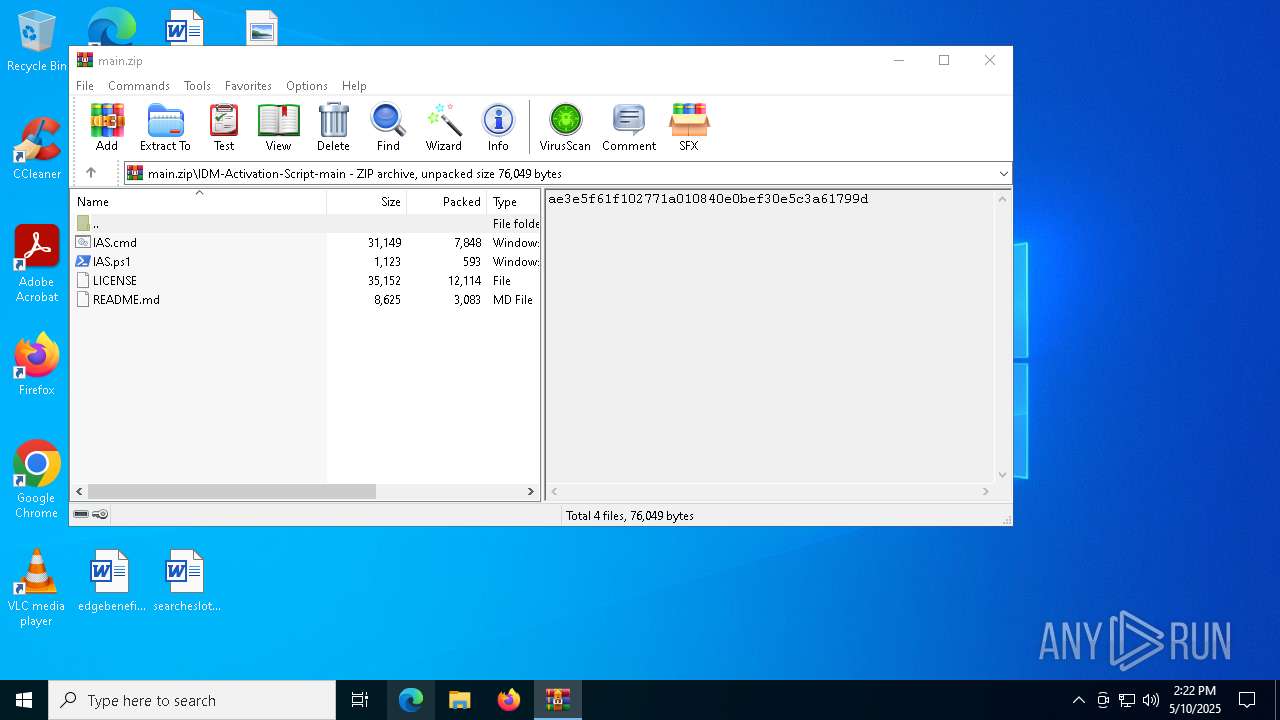
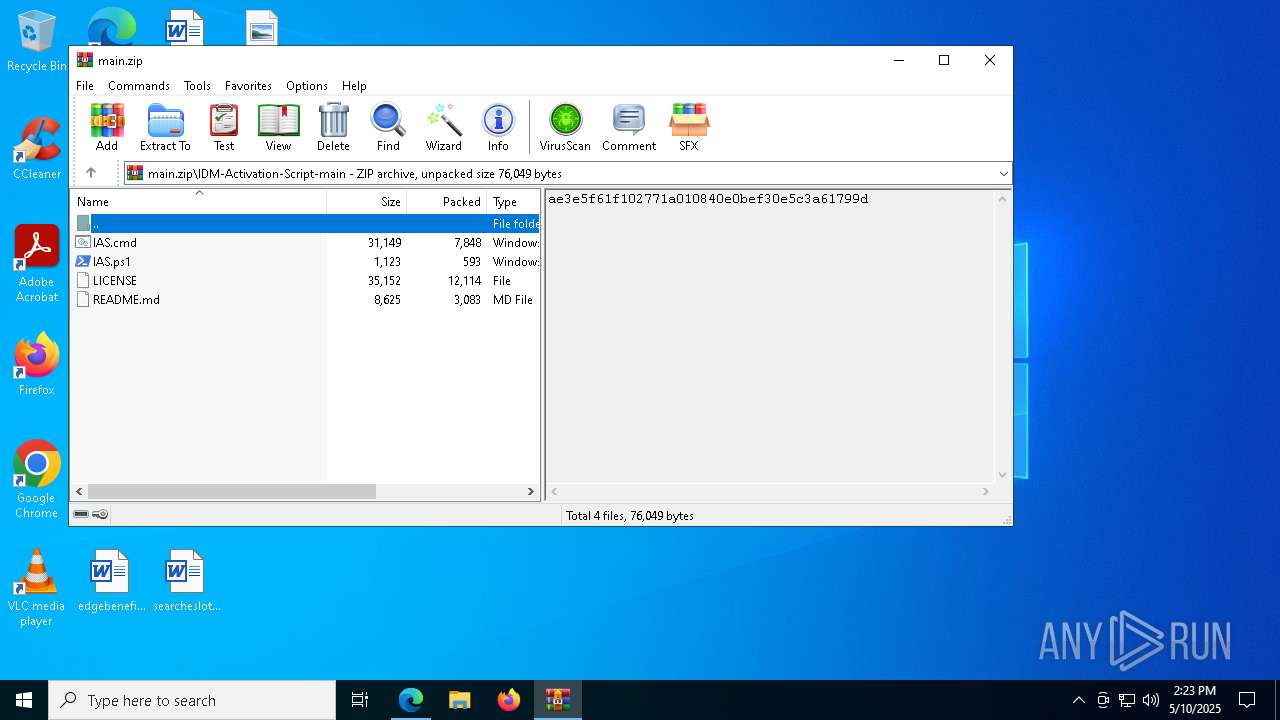
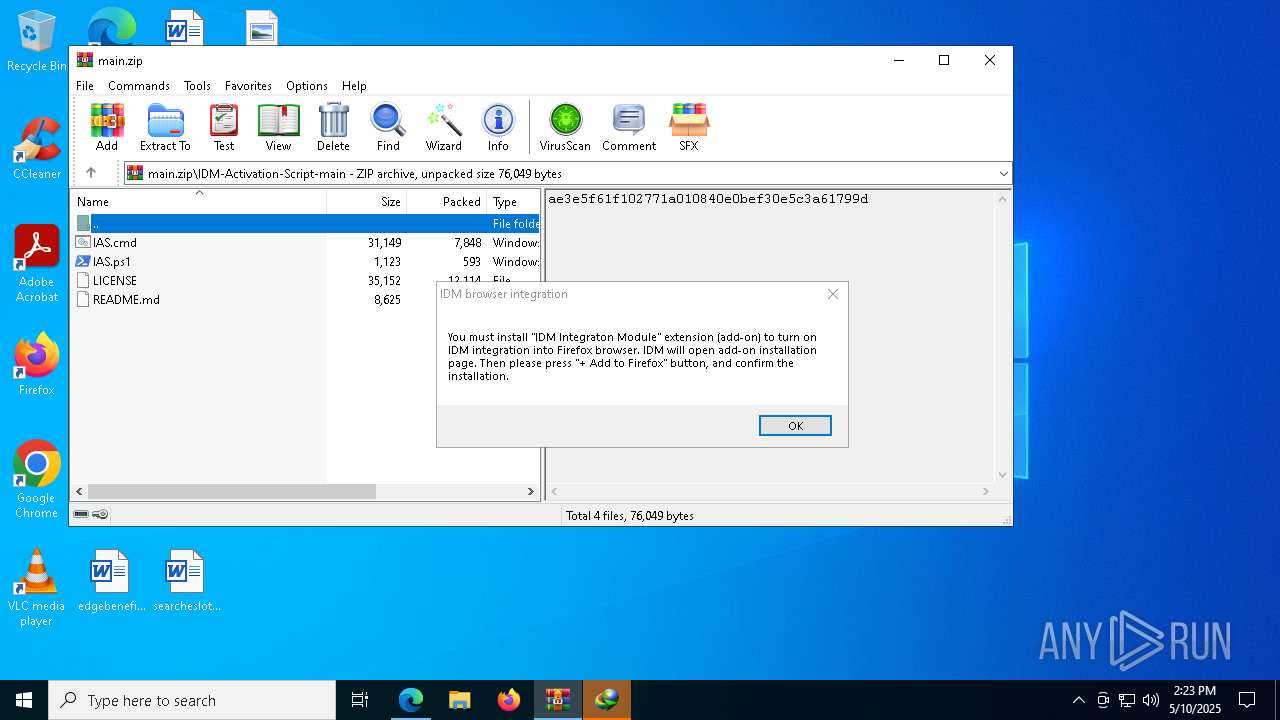
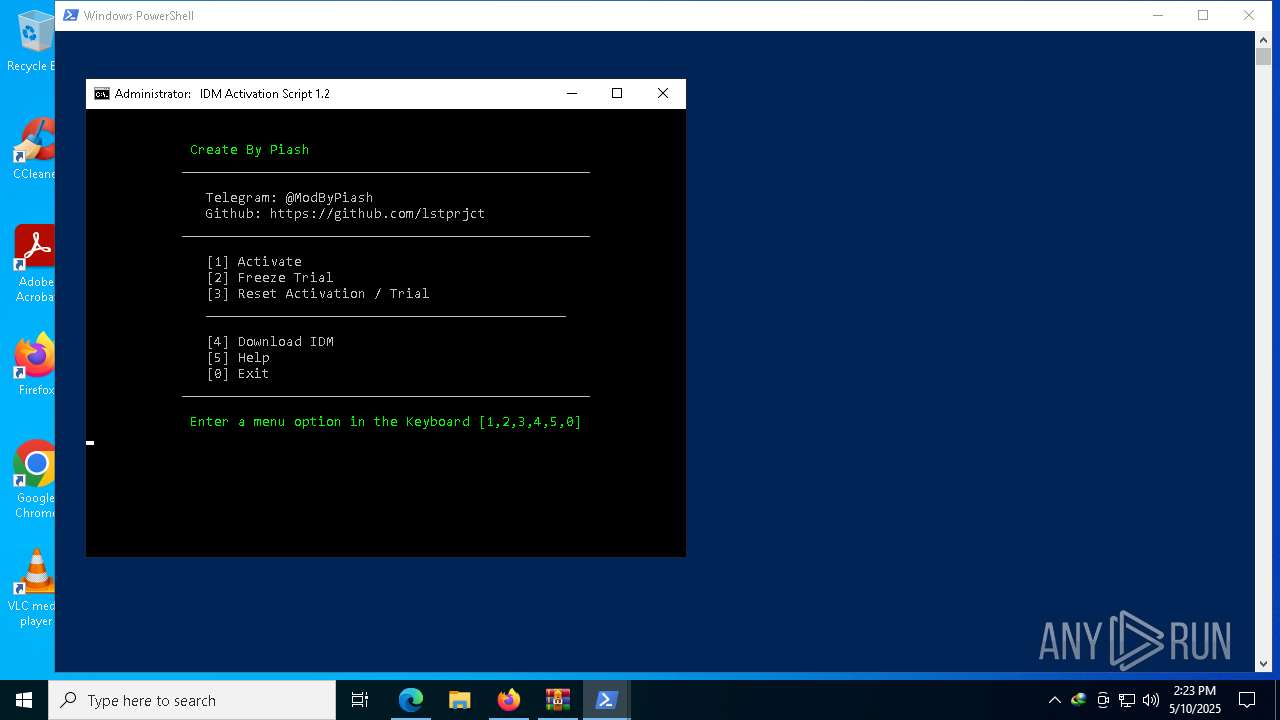
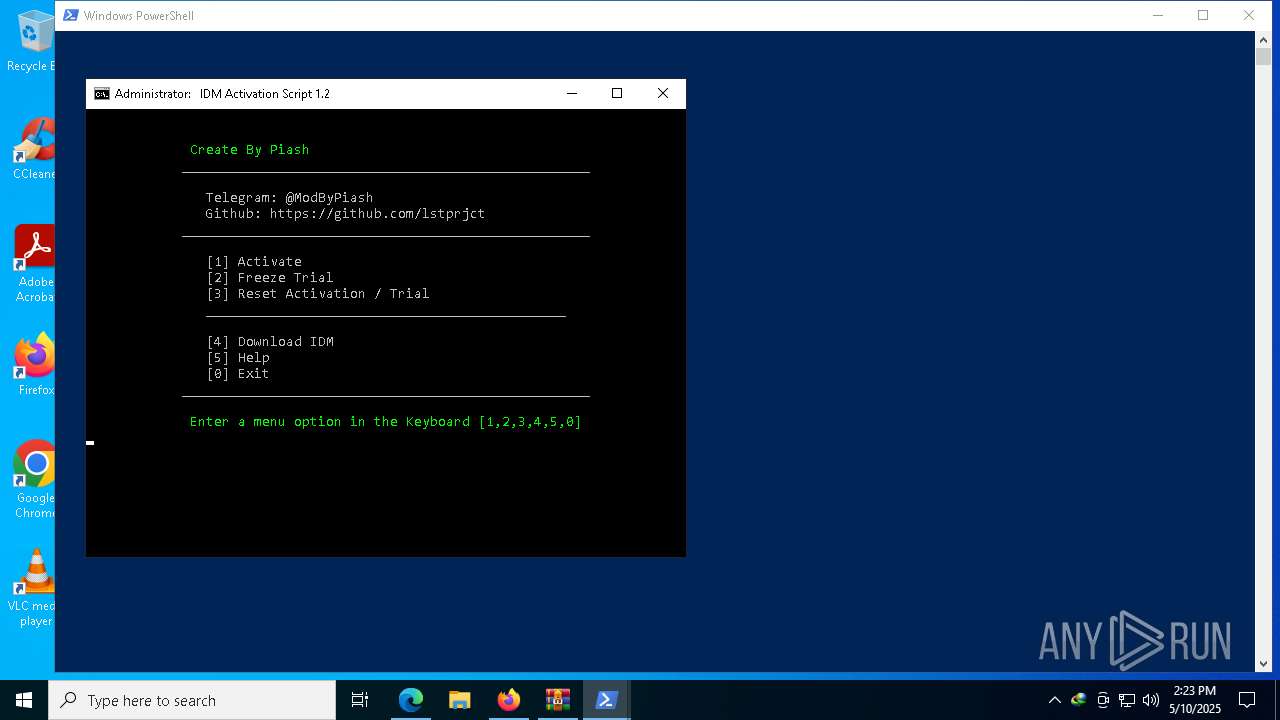
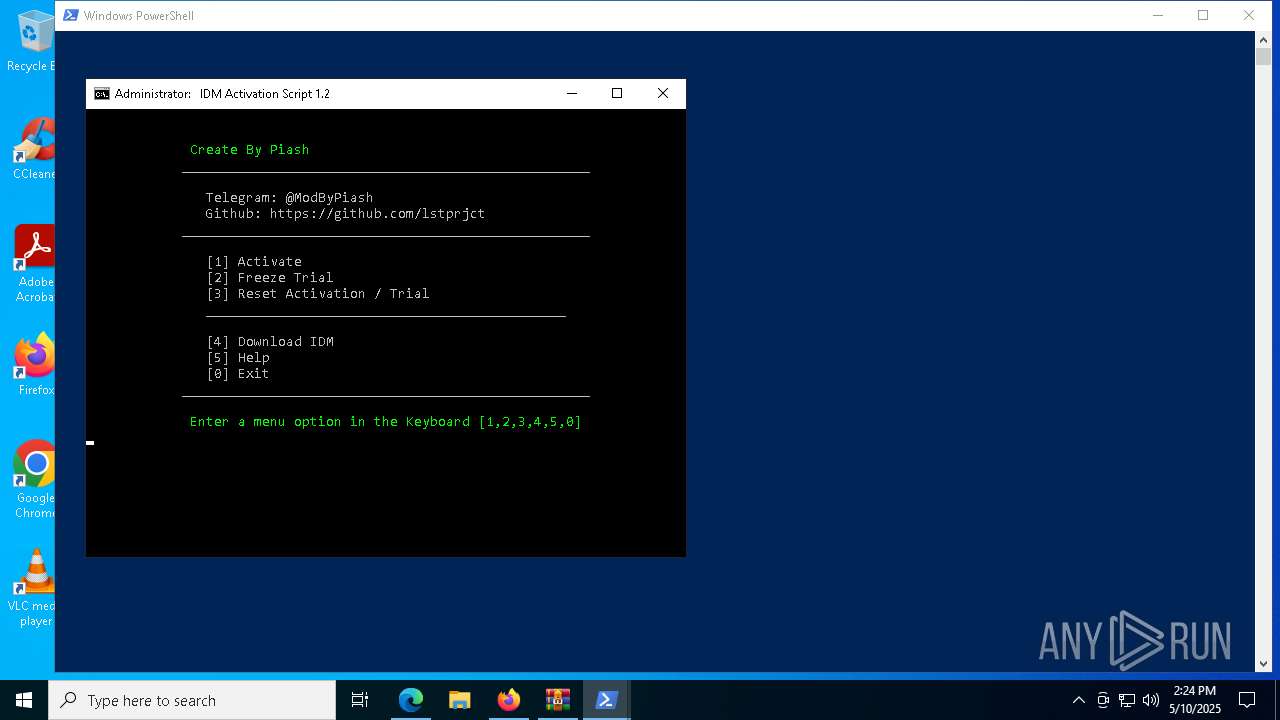
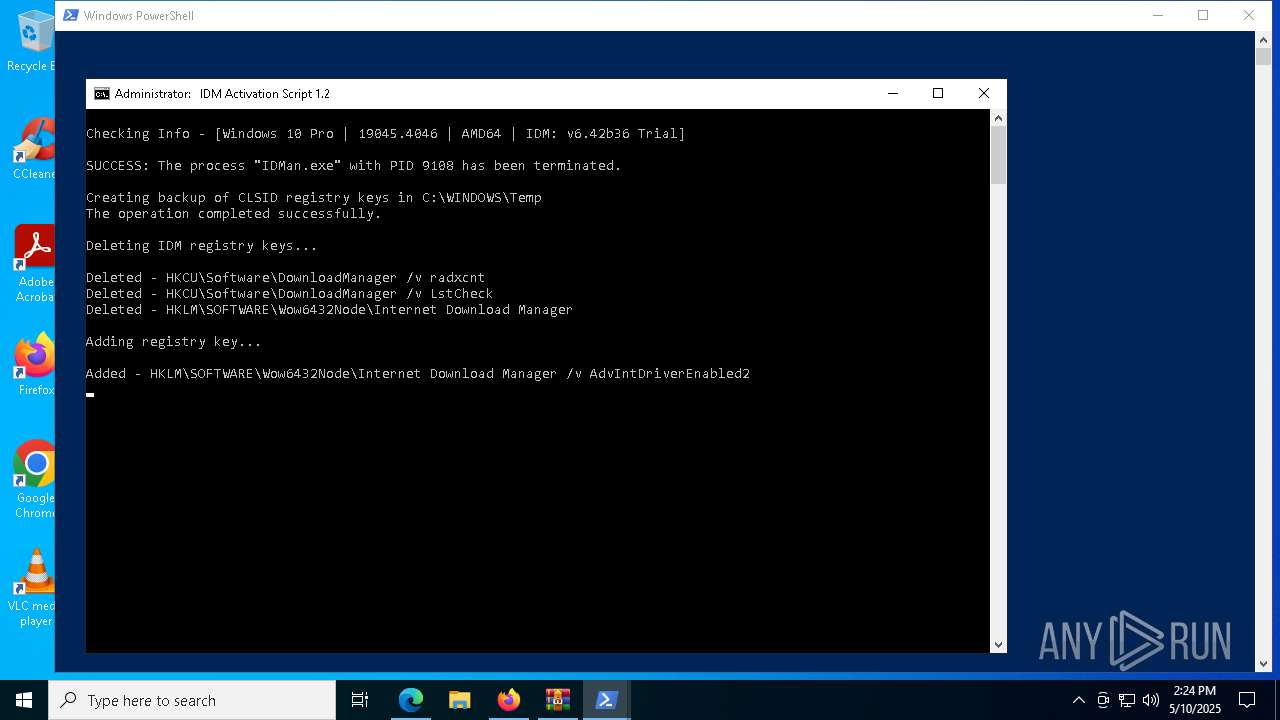
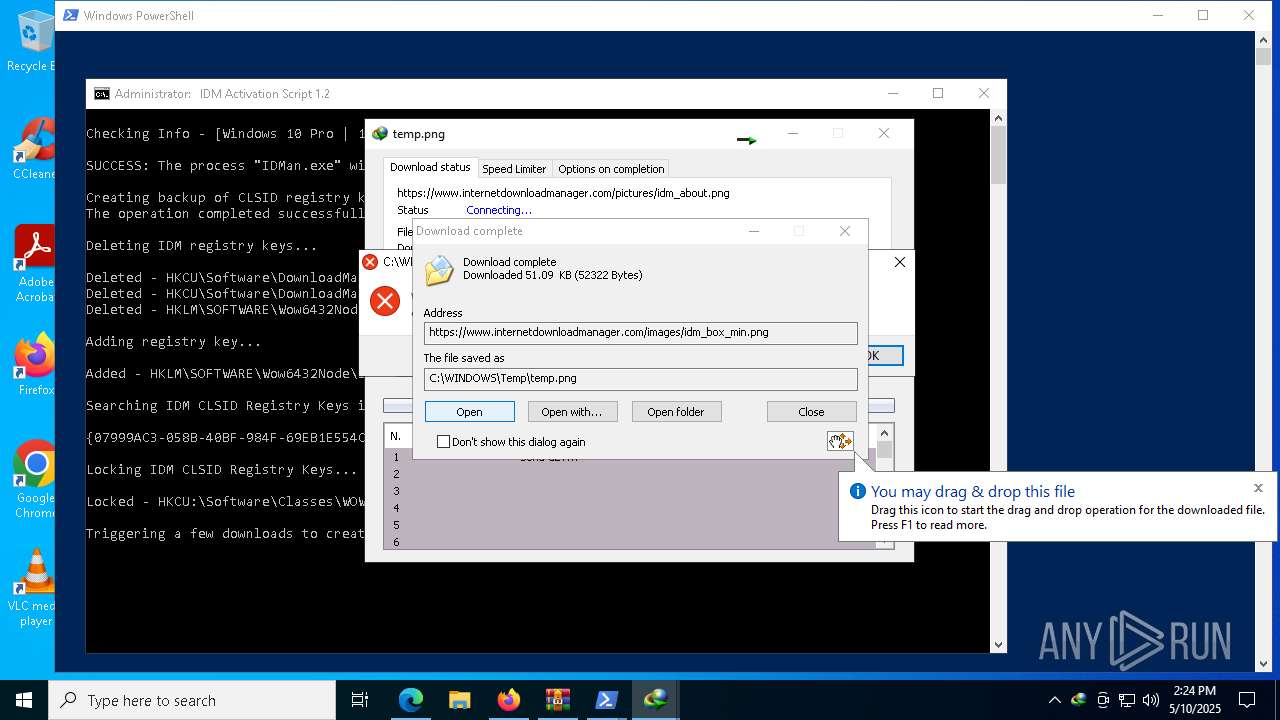
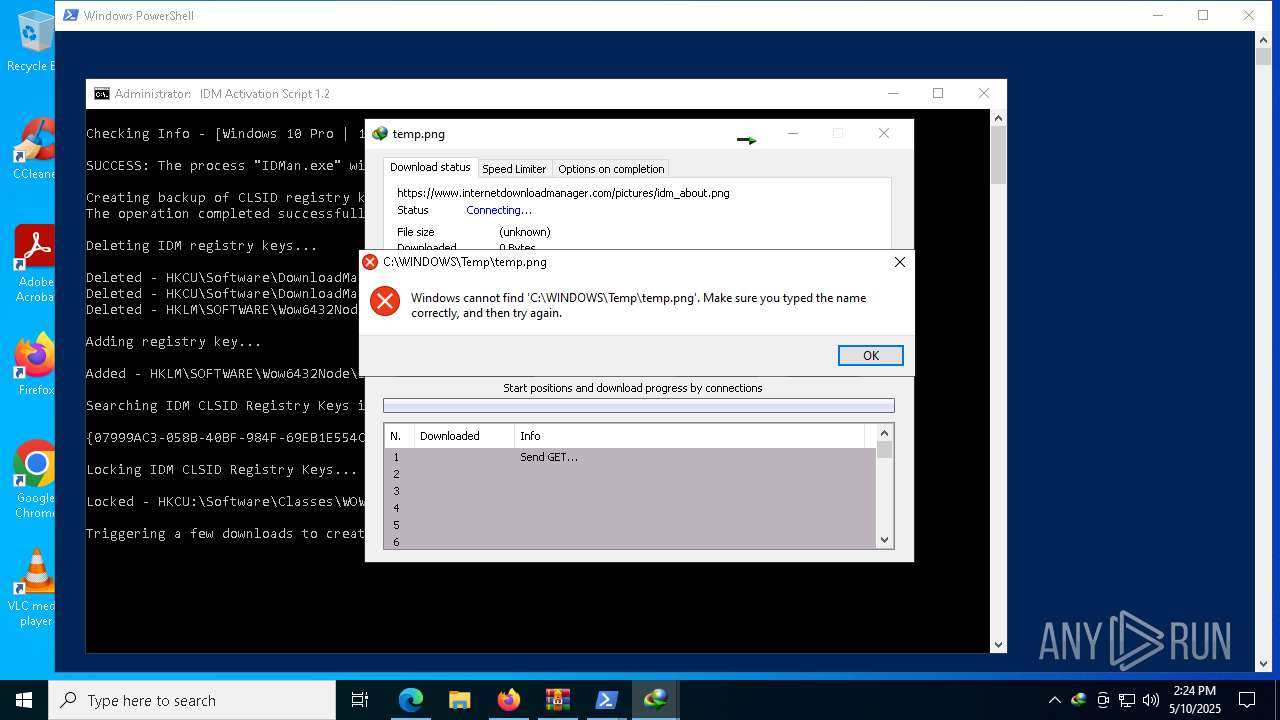
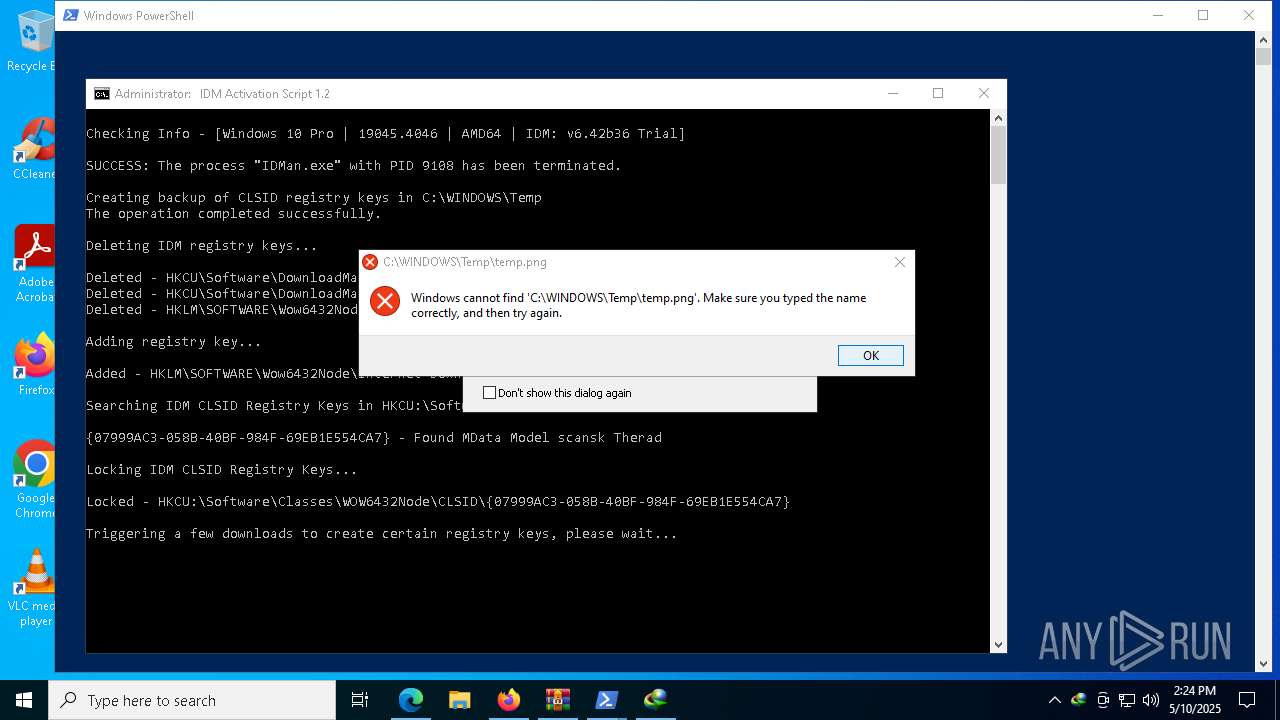
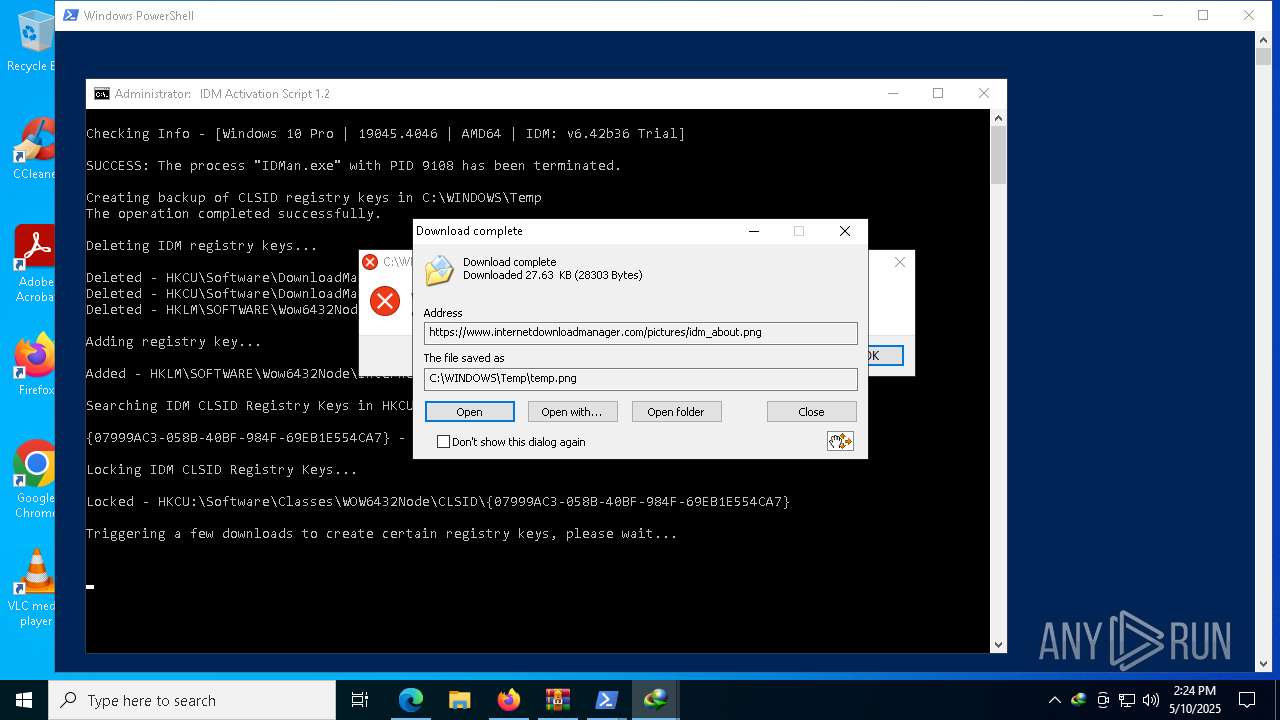
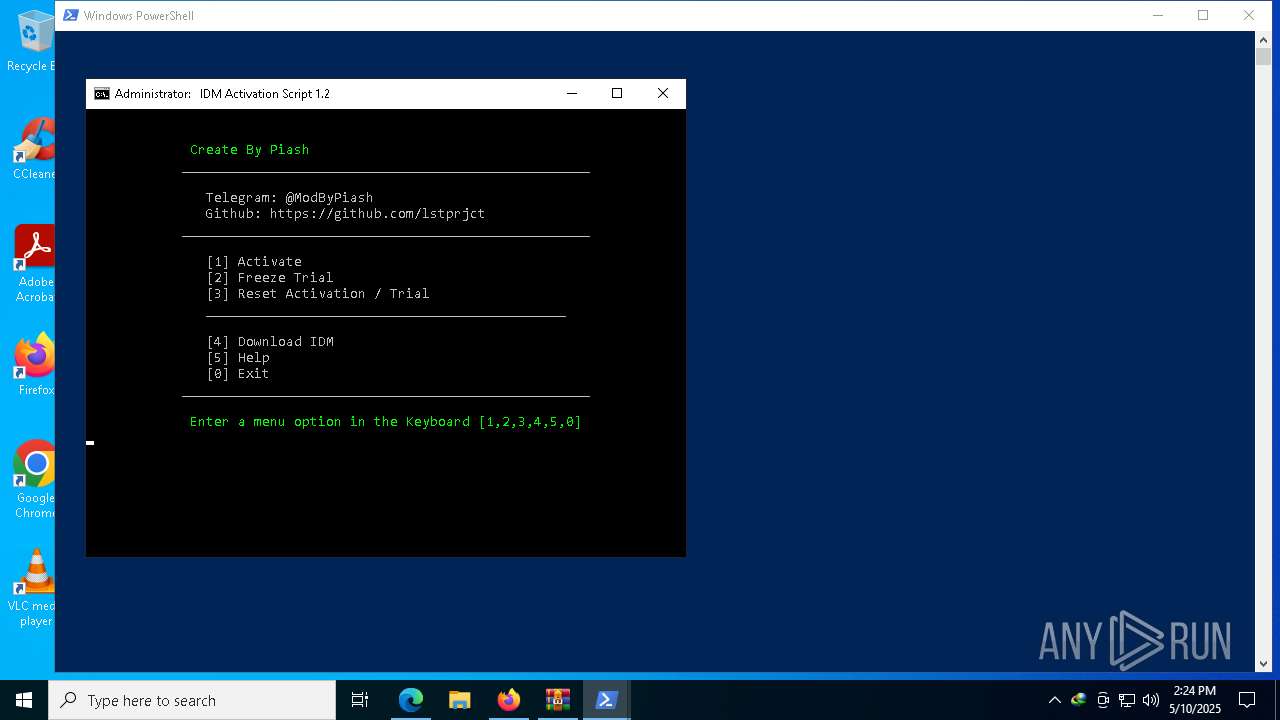
| download: | /lstprjct/IDM-Activation-Script/archive/refs/heads/main.zip |
| Full analysis: | https://app.any.run/tasks/36f0ebd4-e9ab-40fd-b8c6-bc215fee42c1 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 14:22:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 59E89B051AF47ACC25F7380555C48B42 |
| SHA1: | 8885A18EC5F36C26F387713B9BFC71CA870E94A0 |
| SHA256: | C03A9E6621006DC69B38D6DADF4E0BB89042FB7A0A542F4F785B16AD76C45092 |
| SSDEEP: | 768:ZNXNa3iCCwTjifjHqTT+ISEGM/zEZIWUZtbFXbezaUt0:ZNXNGiVdjHqH+IaM6NU3Rb/40 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4892)
Registers / Runs the DLL via REGSVR32.EXE
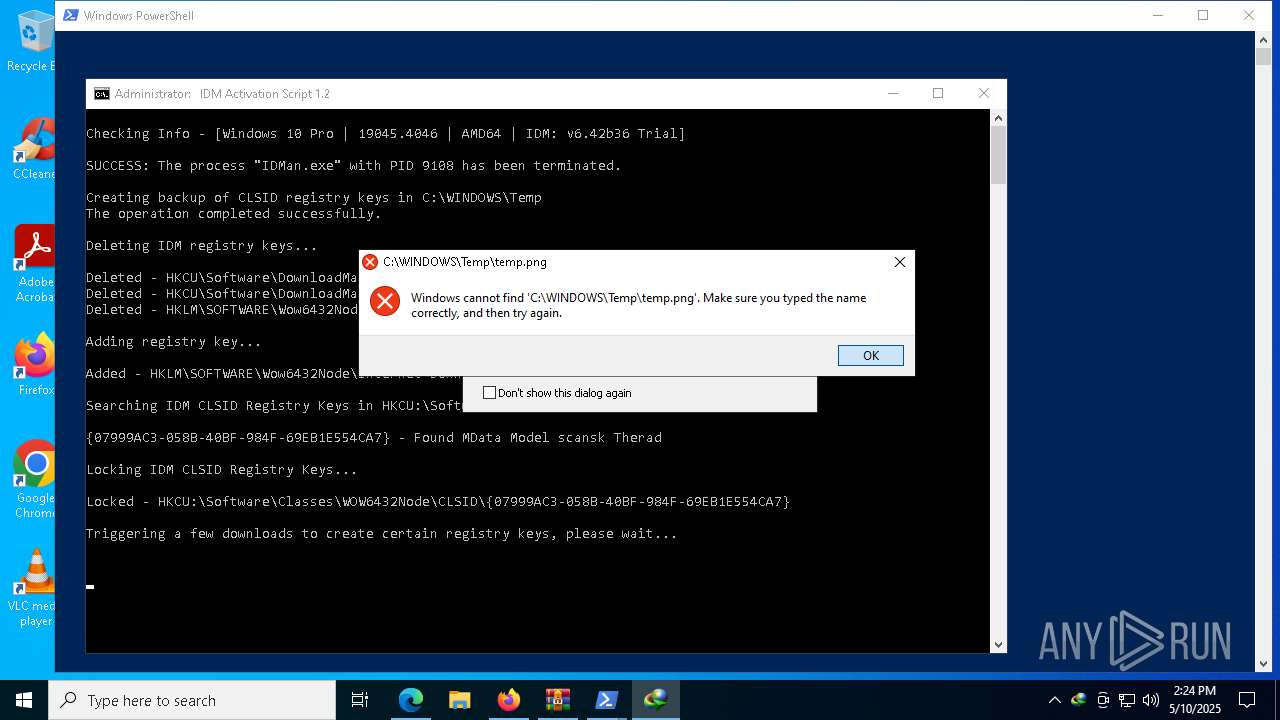
- IDM1.tmp (PID: 8460)
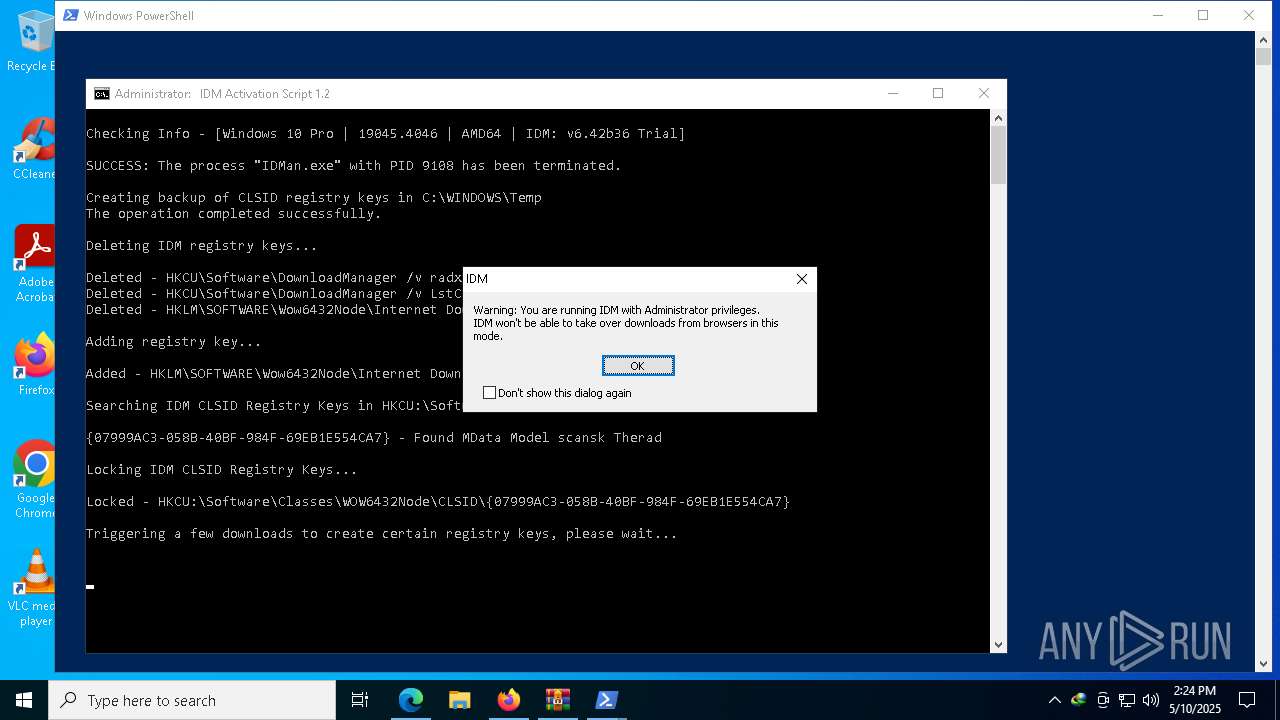
- IDMan.exe (PID: 8896)
- Uninstall.exe (PID: 8308)
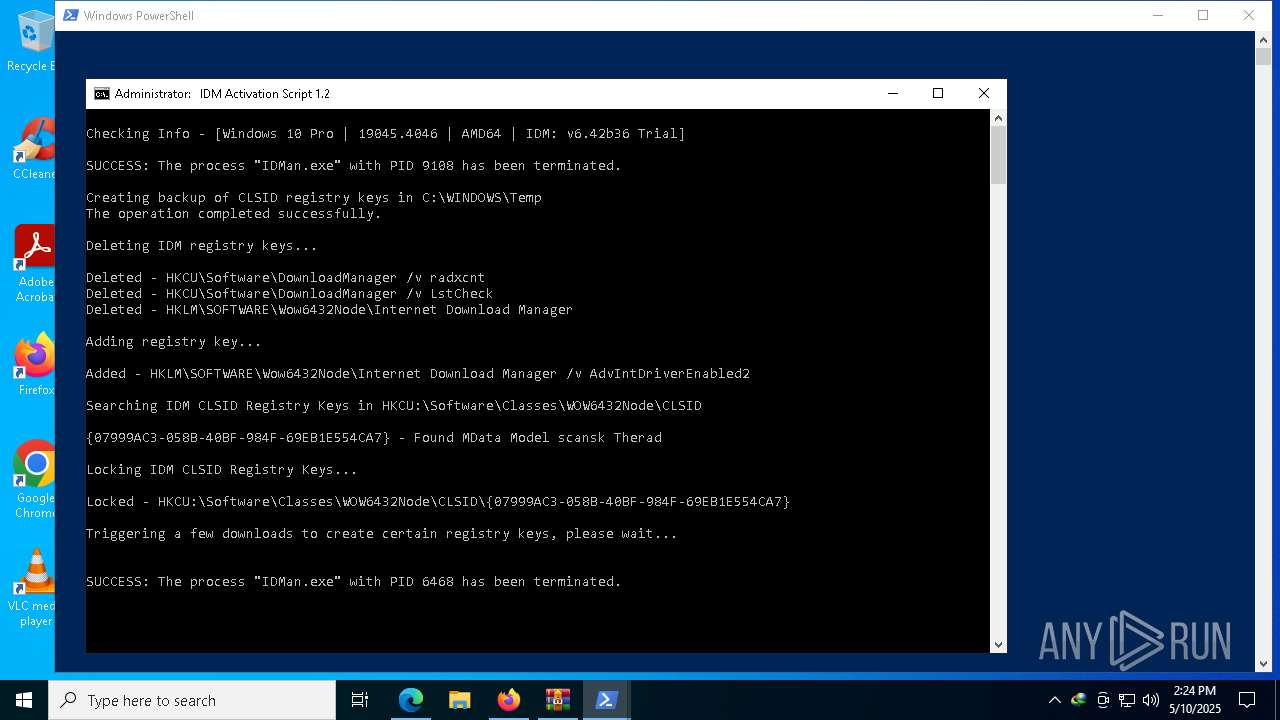
- IDMan.exe (PID: 9108)
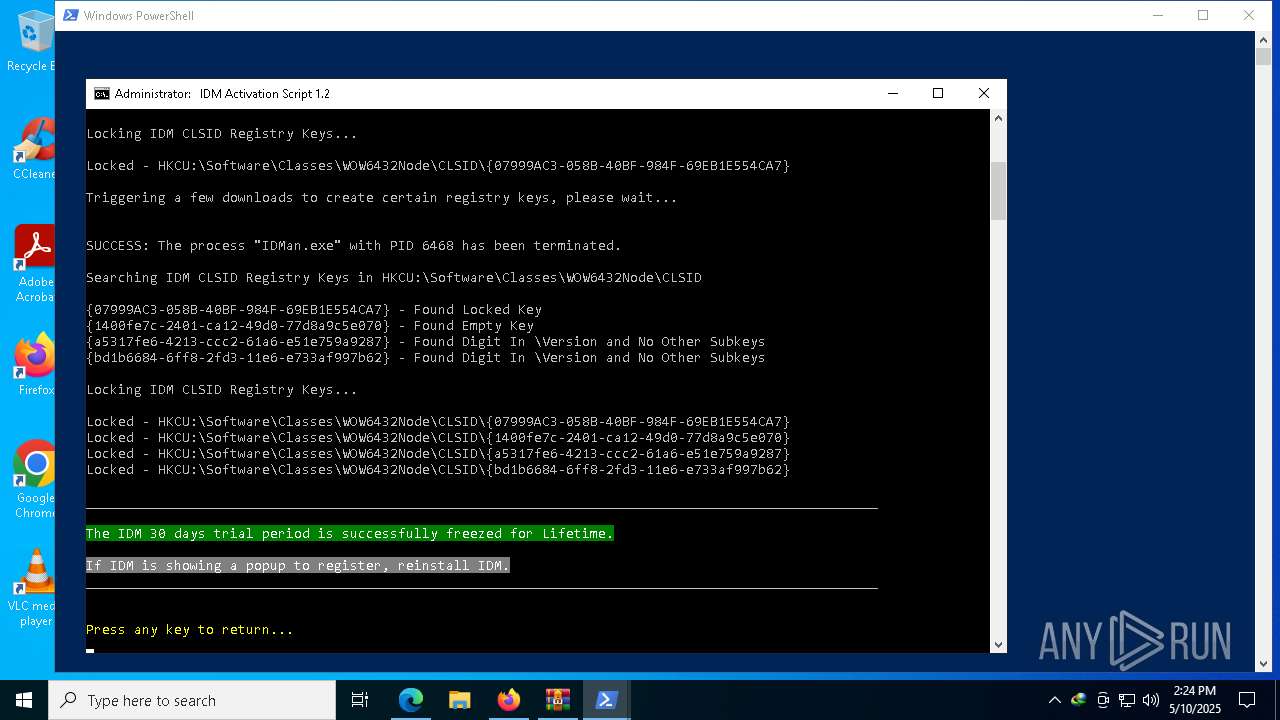
- IDMan.exe (PID: 6468)
Starts NET.EXE for service management
- Uninstall.exe (PID: 8308)
- net.exe (PID: 9184)
Bypass execution policy to execute commands
- powershell.exe (PID: 7360)
Changes powershell execution policy (Bypass)
- WinRAR.exe (PID: 4892)
Execute application with conhost.exe as parent process
- powershell.exe (PID: 4528)
SUSPICIOUS
Starts application with an unusual extension
- idman642build36.exe (PID: 8428)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 8460)
Creates a software uninstall entry
- IDM1.tmp (PID: 8460)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 8460)
- regsvr32.exe (PID: 8844)
- regsvr32.exe (PID: 8828)
- regsvr32.exe (PID: 8864)
- regsvr32.exe (PID: 9116)
- IDMan.exe (PID: 8896)
- regsvr32.exe (PID: 9020)
- regsvr32.exe (PID: 9084)
- regsvr32.exe (PID: 9060)
Reads security settings of Internet Explorer
- IDM1.tmp (PID: 8460)
- IDMan.exe (PID: 8896)
- Uninstall.exe (PID: 8308)
Executable content was dropped or overwritten
- IDMan.exe (PID: 8896)
- drvinst.exe (PID: 8892)
- rundll32.exe (PID: 8420)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 8308)
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 8892)
- rundll32.exe (PID: 8420)
Starts POWERSHELL.EXE for commands execution
- WinRAR.exe (PID: 4892)
- cmd.exe (PID: 8268)
- conhost.exe (PID: 4108)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 7932)
- cmd.exe (PID: 8636)
- cmd.exe (PID: 7368)
The process executes Powershell scripts
- WinRAR.exe (PID: 4892)
Executing commands from ".cmd" file
- powershell.exe (PID: 7360)
- cmd.exe (PID: 8268)
- powershell.exe (PID: 5796)
- cmd.exe (PID: 9200)
- powershell.exe (PID: 4528)
- cmd.exe (PID: 7932)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 7360)
- cmd.exe (PID: 8268)
- cmd.exe (PID: 3240)
- powershell.exe (PID: 5796)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 5548)
- powershell.exe (PID: 4528)
- cmd.exe (PID: 7932)
- cmd.exe (PID: 9200)
Windows service management via SC.EXE
- sc.exe (PID: 7932)
- sc.exe (PID: 8000)
- sc.exe (PID: 8636)
Application launched itself
- cmd.exe (PID: 8268)
- cmd.exe (PID: 3240)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 5548)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 7932)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 8268)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 7932)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 8268)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 7932)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 9200)
- cmd.exe (PID: 8268)
- cmd.exe (PID: 7932)
Starts SC.EXE for service management
- cmd.exe (PID: 8268)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 7932)
Hides command output
- cmd.exe (PID: 8636)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 6192)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2800)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 7932)
Get information on the list of running processes
- cmd.exe (PID: 7932)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7932)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7932)
INFO
Application launched itself
- msedge.exe (PID: 1184)
- firefox.exe (PID: 5556)
- firefox.exe (PID: 8360)
Manual execution by a user
- msedge.exe (PID: 1184)
- firefox.exe (PID: 5556)
Reads the computer name
- identity_helper.exe (PID: 8004)
- idman642build36.exe (PID: 8428)
- idmBroker.exe (PID: 8852)
- IDMan.exe (PID: 8896)
- Uninstall.exe (PID: 8308)
- IDM1.tmp (PID: 8460)
Checks supported languages
- identity_helper.exe (PID: 8004)
- idman642build36.exe (PID: 8428)
- IDM1.tmp (PID: 8460)
- IDMan.exe (PID: 8896)
- idmBroker.exe (PID: 8852)
- Uninstall.exe (PID: 8308)
- drvinst.exe (PID: 8892)
Executable content was dropped or overwritten
- msedge.exe (PID: 1184)
- msedge.exe (PID: 6872)
Reads Environment values
- identity_helper.exe (PID: 8004)
The sample compiled with english language support
- msedge.exe (PID: 6872)
- IDMan.exe (PID: 8896)
- rundll32.exe (PID: 8420)
- drvinst.exe (PID: 8892)
INTERNETDOWNLOADMANAGER mutex has been found
- idman642build36.exe (PID: 8428)
- IDM1.tmp (PID: 8460)
- IDMan.exe (PID: 8896)
Create files in a temporary directory
- idman642build36.exe (PID: 8428)
- IDM1.tmp (PID: 8460)
- IDMan.exe (PID: 8896)
- rundll32.exe (PID: 8420)
Creates files or folders in the user directory
- IDM1.tmp (PID: 8460)
- IDMan.exe (PID: 8896)
Reads the software policy settings
- IDMan.exe (PID: 8896)
Process checks computer location settings
- IDM1.tmp (PID: 8460)
- IDMan.exe (PID: 8896)
- Uninstall.exe (PID: 8308)
Reads the machine GUID from the registry
- IDMan.exe (PID: 8896)
Disables trace logs
- IDMan.exe (PID: 8896)
Creates files in the program directory
- IDMan.exe (PID: 8896)
- IDM1.tmp (PID: 8460)
Checks proxy server information
- IDMan.exe (PID: 8896)
Checks operating system version
- cmd.exe (PID: 8268)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 7932)
Starts MODE.COM to configure console settings
- mode.com (PID: 2596)
- mode.com (PID: 9208)
- mode.com (PID: 6752)
- mode.com (PID: 5756)
- mode.com (PID: 6240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:17 05:38:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | IDM-Activation-Script-main/ |
Total processes
388
Monitored processes
250
Malicious processes
13
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | reg query "HKCU\Software\DownloadManager" "/v" "Email" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | findstr /i "idman.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | C:\WINDOWS\system32\net1 start IDMWFP | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | reg query "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Environment" /v PROCESSOR_ARCHITECTURE | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "C:\Users\admin\AppData\Local\Temp\IAS_50948030.cmd" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2180 -parentBuildID 20240213221259 -prefsHandle 2172 -prefMapHandle 2160 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1d7a2610-3568-43b3-92fb-5051ec5b6ac5} 8360 "\\.\pipe\gecko-crash-server-pipe.8360" 2dd2f582110 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1196 | ping -n 1 internetdownloadmanager.com | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2104 | C:\WINDOWS\system32\cmd.exe /c reg query "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Environment" /v PROCESSOR_ARCHITECTURE | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
116 717
Read events
115 625
Write events
771
Delete events
321
Modification events
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\main.zip | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1184) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1184) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2CA922195F932F00 | |||
Executable files
56
Suspicious files
977
Text files
229
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10d5ff.TMP | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10d60f.TMP | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10d60f.TMP | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10d60f.TMP | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10d61e.TMP | — | |
MD5:— | SHA256:— | |||
| 1184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
178
DNS requests
223
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7596 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7596 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8360 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
8360 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
8360 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
8360 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
8360 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
8360 | firefox.exe | POST | 200 | 18.173.205.57:80 | http://ocsps.ssl.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.139:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1184 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |