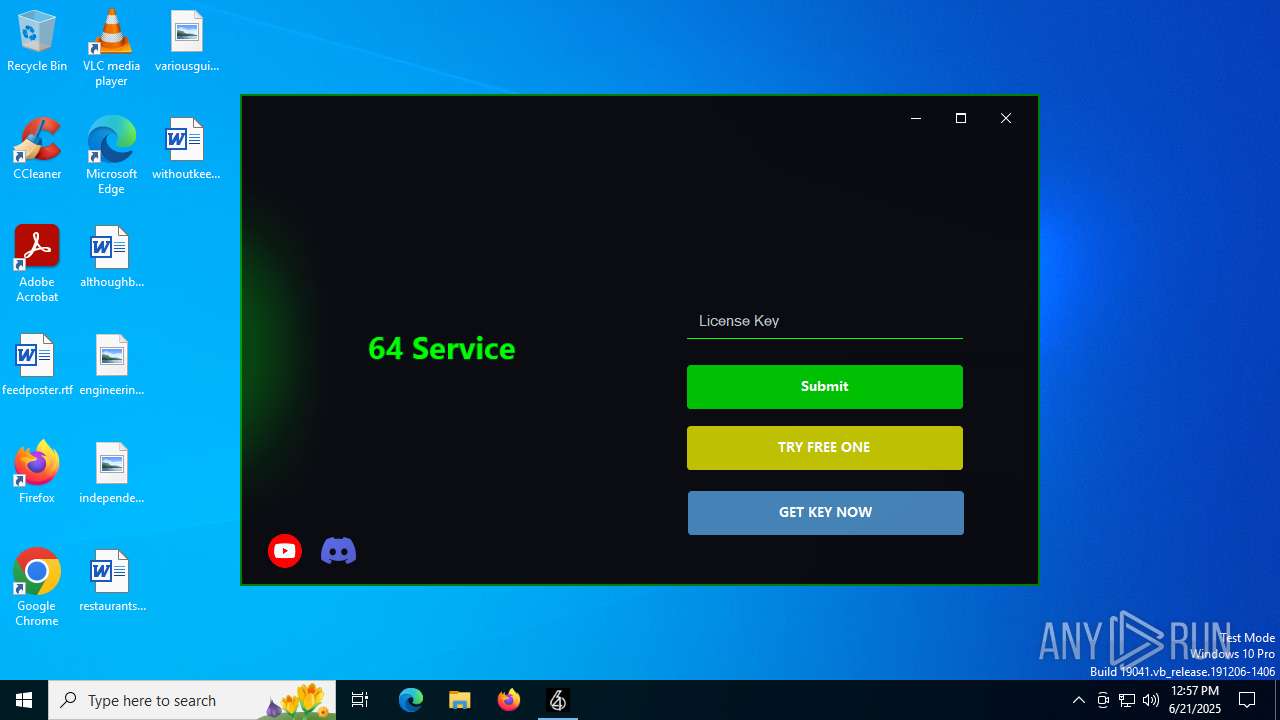
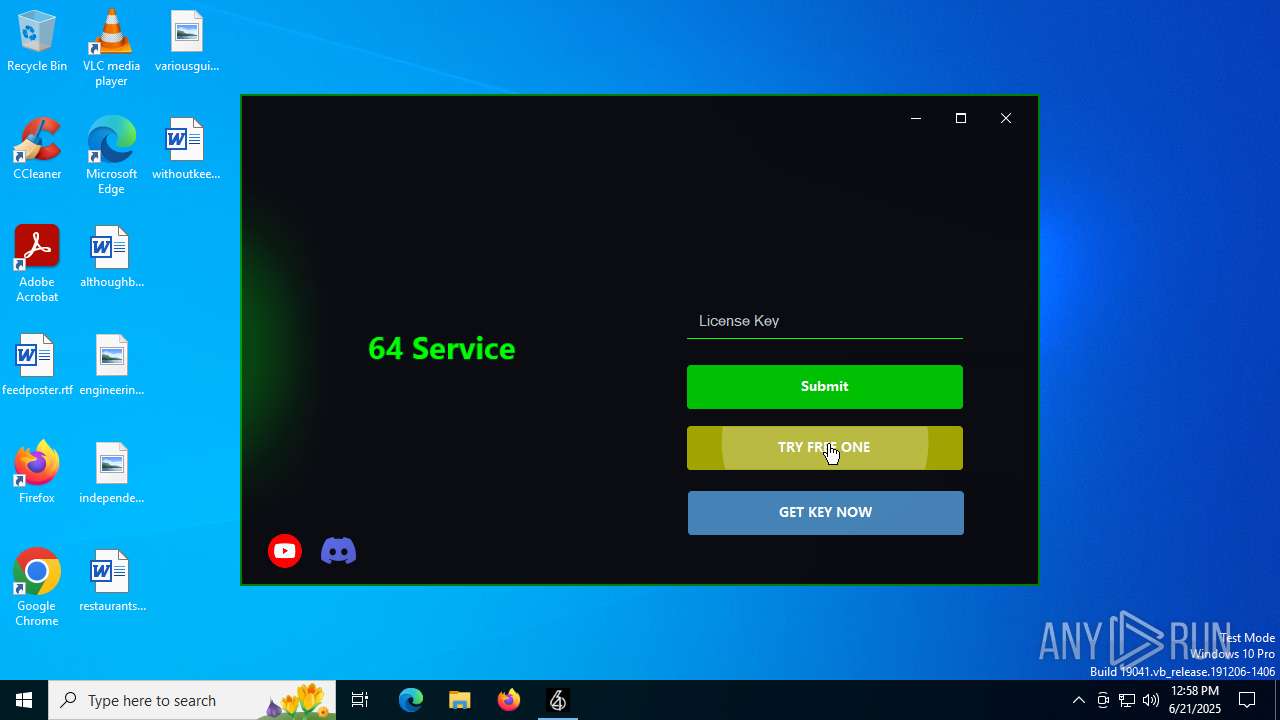
| File name: | 64_Service.exe |
| Full analysis: | https://app.any.run/tasks/a9567e1b-3522-4301-ba31-afe519223fe6 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 12:57:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 13DD953D30085824457696DB3DC7CDE3 |
| SHA1: | 3B4EC8CDEB0662BBAC587278264583F09D9B10E9 |
| SHA256: | C032A110EA3A36BEB548A3BD5D1D9957AF4644E974AED610BBA36A3A6A3EF2E1 |
| SSDEEP: | 3072:RN1vgxeyHPlK3rRRb8PlZngmhY6zHffpg:NgxeB3DglV9Zffp |
MALICIOUS
Downloads the requested resource (POWERSHELL)
- 64_Service.exe (PID: 5288)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 6492)
SUSPICIOUS
Reads security settings of Internet Explorer
- 64_Service.exe (PID: 5288)
- Runtime Broker.exe (PID: 2076)
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2728)
Executable content was dropped or overwritten
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2728)
- Runtime Broker.exe (PID: 2076)
Writes data into a file (POWERSHELL)
- 64_Service.exe (PID: 5288)
Reads the date of Windows installation
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2076)
- Runtime Broker.exe (PID: 2728)
Process drops legitimate windows executable
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2076)
- Runtime Broker.exe (PID: 2728)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2976)
- cmd.exe (PID: 856)
The executable file from the user directory is run by the CMD process
- Runtime Broker.exe (PID: 2716)
- Runtime Broker.exe (PID: 4984)
Starts CMD.EXE for commands execution
- Runtime Broker.exe (PID: 2728)
- Runtime Broker.exe (PID: 2076)
Executing commands from a ".bat" file
- Runtime Broker.exe (PID: 2076)
- Runtime Broker.exe (PID: 2728)
Executes application which crashes
- 64th%20Services_Free.exe (PID: 6400)
INFO
Reads the machine GUID from the registry
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2076)
- Runtime Broker.exe (PID: 2728)
- Runtime Broker.exe (PID: 4984)
- 64th%20Services_Free.exe (PID: 6400)
Reads the computer name
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2076)
- Runtime Broker.exe (PID: 2728)
- Runtime Broker.exe (PID: 2716)
- 64th%20Services_Free.exe (PID: 6400)
- Runtime Broker.exe (PID: 4984)
Checks supported languages
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2076)
- Runtime Broker.exe (PID: 2728)
- Runtime Broker.exe (PID: 2716)
- Runtime Broker.exe (PID: 4984)
- 64th%20Services_Free.exe (PID: 6400)
Create files in a temporary directory
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2076)
- 64th%20Services_Free.exe (PID: 6400)
- Runtime Broker.exe (PID: 2728)
Reads Environment values
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
Checks if a key exists in the options dictionary (POWERSHELL)
- 64_Service.exe (PID: 5288)
Reads the software policy settings
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- WerFault.exe (PID: 7132)
Disables trace logs
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
Checks proxy server information
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- WerFault.exe (PID: 7132)
Process checks computer location settings
- 64_Service.exe (PID: 5288)
- tmp7E57.exe (PID: 6368)
- Runtime Broker.exe (PID: 2076)
- Runtime Broker.exe (PID: 2728)
Creates files in the program directory
- tmp7E57.exe (PID: 6368)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- cmd.exe (PID: 592)
Creates files or folders in the user directory
- Runtime Broker.exe (PID: 2076)
- WerFault.exe (PID: 7132)
- Runtime Broker.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:23 20:32:00+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 25600 |
| InitializedDataSize: | 190464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x827e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.1.1.1 |
| ProductVersionNumber: | 1.1.1.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 1.1.1.1 |
| InternalName: | 769F - Copy.exe |
| LegalCopyright: | |
| OriginalFileName: | 769F - Copy.exe |
| ProductName: | 64 Service |
| ProductVersion: | 1.1.1.1 |
| AssemblyVersion: | 1.1.1.1 |
Total processes
163
Monitored processes
24
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 592 | "C:\Windows\System32\cmd.exe" /c schtasks /create /f /sc onlogon /rl highest /tn "Runtime Broker" /tr '"C:\Users\admin\AppData\Roaming\Runtime Broker.exe"' & exit | C:\Windows\System32\cmd.exe | Runtime Broker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmp9B55.tmp.bat"" | C:\Windows\System32\cmd.exe | — | Runtime Broker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | "C:\ProgramData\SystemCache64\Runtime Broker.exe" | C:\ProgramData\SystemCache64\Runtime Broker.exe | tmp7E57.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Runtime Broker Exit code: 0 Version: 6.2.19041.3636 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2524 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2648 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | "C:\Users\admin\AppData\Roaming\Runtime Broker.exe" | C:\Users\admin\AppData\Roaming\Runtime Broker.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Runtime Broker Exit code: 4294967295 Version: 6.2.19041.3636 Modules
| |||||||||||||||
| 2728 | "C:\ProgramData\SystemCache64\Runtime Broker.exe" | C:\ProgramData\SystemCache64\Runtime Broker.exe | tmp7E57.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Runtime Broker Exit code: 0 Version: 6.2.19041.3636 Modules
| |||||||||||||||
Total events
14 160
Read events
14 107
Write events
50
Delete events
3
Modification events
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5288) 64_Service.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\64_Service_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
5
Suspicious files
5
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7132 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_64th_20Services__6b817dfef6c07477d6fc1bdfcfe3b2ae466224c9_bc30dbcc_e6c2bd10-116a-4f7a-96b2-8353e67d90ce\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7132 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\64th_20Services_Free.exe.6400.dmp | — | |
MD5:— | SHA256:— | |||
| 2728 | Runtime Broker.exe | C:\Users\admin\AppData\Roaming\Runtime Broker.exe | executable | |
MD5:03D6F540DABC52C2B6764C7F9E37E6F4 | SHA256:3536D24588D5363B1C6BAACC2EC62054004860F950425EA26CDAAEEB8CE8EA1E | |||
| 6368 | tmp7E57.exe | C:\ProgramData\KeyAuth\debug\tmp7E57\Jun_21_2025_logs.txt | text | |
MD5:4988A8ACAB79D74AB88CE29C86328F0F | SHA256:EC26B74AC547A0D369E421D84DE2B633164ACA4B1C2DFACEEA931EC1A22D5066 | |||
| 6368 | tmp7E57.exe | C:\ProgramData\SystemCache64\Runtime Broker.exe | executable | |
MD5:03D6F540DABC52C2B6764C7F9E37E6F4 | SHA256:3536D24588D5363B1C6BAACC2EC62054004860F950425EA26CDAAEEB8CE8EA1E | |||
| 2076 | Runtime Broker.exe | C:\Users\admin\AppData\Roaming\Runtime Broker.exe | executable | |
MD5:03D6F540DABC52C2B6764C7F9E37E6F4 | SHA256:3536D24588D5363B1C6BAACC2EC62054004860F950425EA26CDAAEEB8CE8EA1E | |||
| 2728 | Runtime Broker.exe | C:\Users\admin\AppData\Local\Temp\tmp9B55.tmp.bat | text | |
MD5:FB841C055106B6A7AA9C5FD83541E0BE | SHA256:C59524B01755DA57A7673754D106A285771397EA36556059386B82B0F01BE184 | |||
| 7132 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERB43C.tmp.dmp | binary | |
MD5:2754EF3FF99BEFAF9763F4021451A6AE | SHA256:6FB28F75C8125AA486CE41EF024EC54B9348742DDFD14928F6526769E800276C | |||
| 6368 | tmp7E57.exe | C:\ProgramData\cloudware\64th%20Services_Free.exe | executable | |
MD5:808ED39F4403E6357F716935CDD18229 | SHA256:4D1F25B7B111BA0BEA32CBC398995E91B822EB012E4B0598018942791D6DAA7C | |||
| 5288 | 64_Service.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xhc3yygu.had.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1336 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7132 | WerFault.exe | GET | 200 | 184.24.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7132 | WerFault.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1028 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1028 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3100 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5288 | 64_Service.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
5288 | 64_Service.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1336 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1336 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
prod.keyauth.com |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |