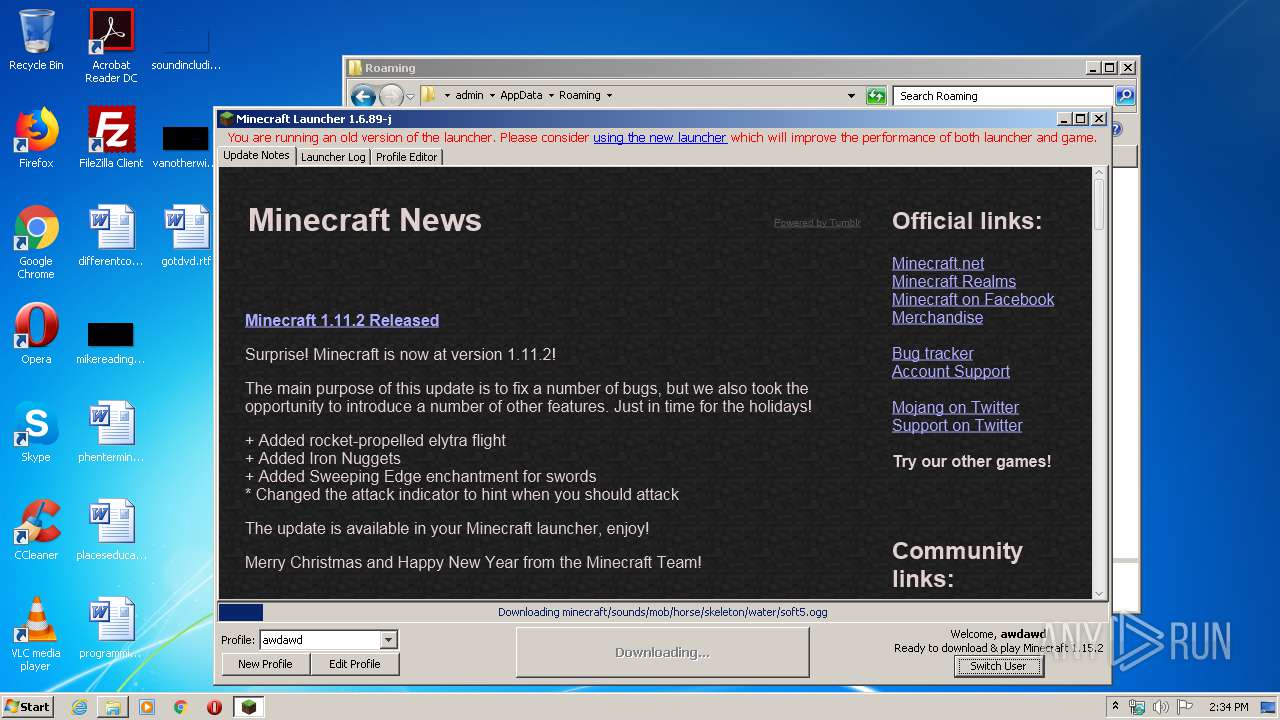
| File name: | Mineshafter-launcher.jar |
| Full analysis: | https://app.any.run/tasks/e12dfab1-2f99-4f42-889f-2e14ab39c978 |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2020, 13:33:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | F6CD55DE2534393363E1A40E04D71156 |
| SHA1: | 7A8D89DD5548D6BDF8DE77E198AD518300C560CF |
| SHA256: | C03140A4216BD64EE1BF7D5E7416973F1E3F9E60B0513ADA448893DD6952EAD6 |
| SSDEEP: | 3072:hDDxhlswtTmiVBmqt7yANM/+0QGLF0BVHt:JNBtTmCBm07tMpQ4F0/t |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- javaw.exe (PID: 3600)
INFO
Dropped object may contain Bitcoin addresses
- javaw.exe (PID: 3600)
Manual execution by user
- explorer.exe (PID: 3272)
- chrome.exe (PID: 2616)
Reads the hosts file
- chrome.exe (PID: 2948)
- chrome.exe (PID: 2616)
Application launched itself
- chrome.exe (PID: 2616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:09:05 23:31:15 |
| ZipCRC: | 0xe40dfb26 |
| ZipCompressedSize: | 67 |
| ZipUncompressedSize: | 65 |
| ZipFileName: | META-INF/MANIFEST.MF |
Total processes
56
Monitored processes
18
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,12647565795071468451,10274676897873765912,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2891840046358215325 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2524 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,12647565795071468451,10274676897873765912,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6923010560460510929 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2256 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,12647565795071468451,10274676897873765912,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10264706231246535474 --mojo-platform-channel-handle=3904 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | |||||||||||||||
| 2616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,12647565795071468451,10274676897873765912,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1521376958339555661 --mojo-platform-channel-handle=3376 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,12647565795071468451,10274676897873765912,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=13052032473917072102 --mojo-platform-channel-handle=1652 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,12647565795071468451,10274676897873765912,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9427255034929561804 --mojo-platform-channel-handle=3320 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,12647565795071468451,10274676897873765912,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4974848257027306747 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2280 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3272 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,12647565795071468451,10274676897873765912,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2010985574384765197 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3764 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | |||||||||||||||
Total events
224
Read events
188
Write events
33
Delete events
3
Modification events
| (PID) Process: | (3600) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
| (PID) Process: | (3956) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2616-13231085700537476 |
Value: 259 | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
Executable files
21
Suspicious files
37
Text files
92
Unknown types
295
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
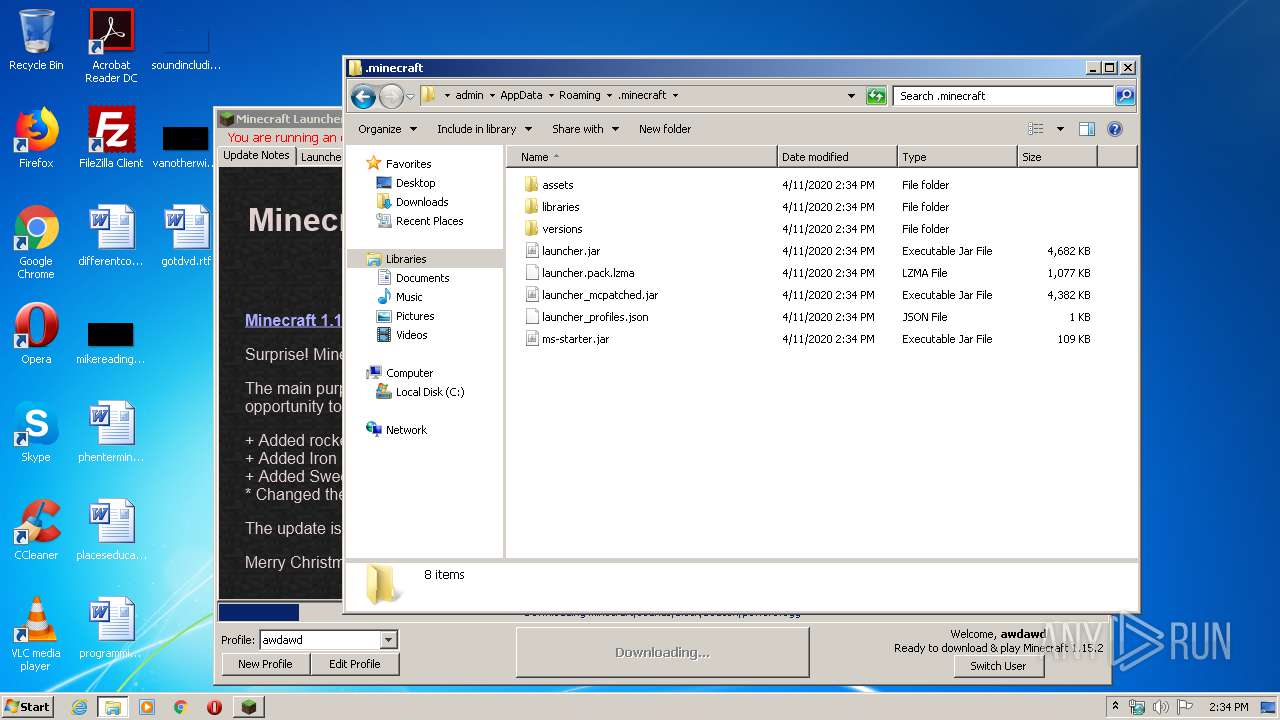
| 3600 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher.pack.lzma.new | — | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio1220883593293715128.tmp | — | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio45875556922554393.tmp | — | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio5202116602735298569.tmp | — | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio9208775910808649104.tmp | — | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher.pack | binary | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher_mcpatched.jar | compressed | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher_profiles.json | text | |
MD5:— | SHA256:— | |||
| 3600 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\versions\1.15.2\1.15.2.json | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
365
TCP/UDP connections
65
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3600 | javaw.exe | GET | 302 | 74.114.154.18:80 | http://mcupdate.tumblr.com/ | CA | — | — | suspicious |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/86/8686687fd6079185de0e872f8dbf434c0a49e5ca | US | text | 308 Kb | shared |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/72/72a006be3bd693aa23cc2f8e9c9d13ea6f829aa1 | US | ogg | 16.3 Kb | shared |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/1d/1d355313b9da07fc2e5c5fb9f3869e9390ec739a | US | ogg | 23.6 Kb | shared |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/5e/5ed98b8375fd787baf19d7d434f0333a189ccb51 | US | ogg | 8.53 Kb | shared |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/a9/a92ba2b8f6abc41aa8d679ad808a81d0aafa04b2 | US | ogg | 28.5 Kb | shared |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/cb/cb95637a9d5e9b0cb36a2516f0dfac30fed9d720 | US | ogg | 6.39 Kb | shared |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/ea/eac71e547a1b5fc95f6d3580abfb4d31d3c8403d | US | ogg | 13.2 Kb | shared |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/2d/2d52b67698da28316cd9cdb50eb8d6eb93a2abf4 | US | ogg | 21.4 Kb | shared |
3600 | javaw.exe | GET | 200 | 13.224.194.57:80 | http://resources.download.minecraft.net/a6/a69ab2376207659ed24a427d15997bb7fbcd5286 | US | ogg | 8.23 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3600 | javaw.exe | 185.142.236.247:443 | mineshafter.info | Cogent Communications | NL | unknown |
3600 | javaw.exe | 13.225.74.128:443 | launchermeta.mojang.com | — | US | unknown |
3600 | javaw.exe | 74.114.154.18:80 | mcupdate.tumblr.com | Automattic, Inc | CA | malicious |
3600 | javaw.exe | 74.114.154.18:443 | mcupdate.tumblr.com | Automattic, Inc | CA | malicious |
3600 | javaw.exe | 152.199.19.43:443 | 66.media.tumblr.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3600 | javaw.exe | 13.225.86.78:443 | libraries.minecraft.net | — | US | unknown |
3600 | javaw.exe | 13.224.194.57:80 | resources.download.minecraft.net | — | US | suspicious |
3600 | javaw.exe | 13.224.189.128:443 | launcher.mojang.com | — | US | unknown |
3600 | javaw.exe | 152.199.21.147:443 | assets.tumblr.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | suspicious |
2948 | chrome.exe | 172.217.22.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mineshafter.info |
| whitelisted |
s3.amazonaws.com |
| shared |
launchermeta.mojang.com |
| whitelisted |
mcupdate.tumblr.com |
| suspicious |
assets.tumblr.com |
| whitelisted |
66.media.tumblr.com |
| suspicious |
px.srvcs.tumblr.com |
| whitelisted |
static.tumblr.com |
| whitelisted |
libraries.minecraft.net |
| shared |
launcher.mojang.com |
| whitelisted |