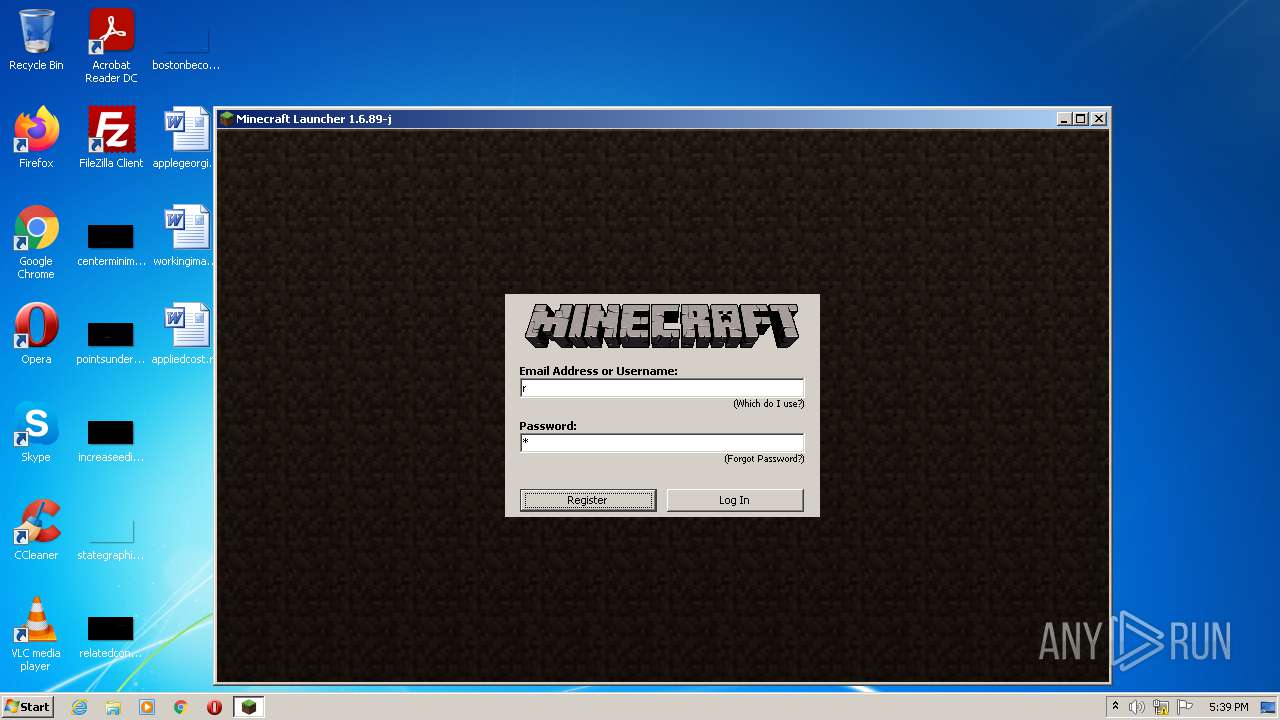
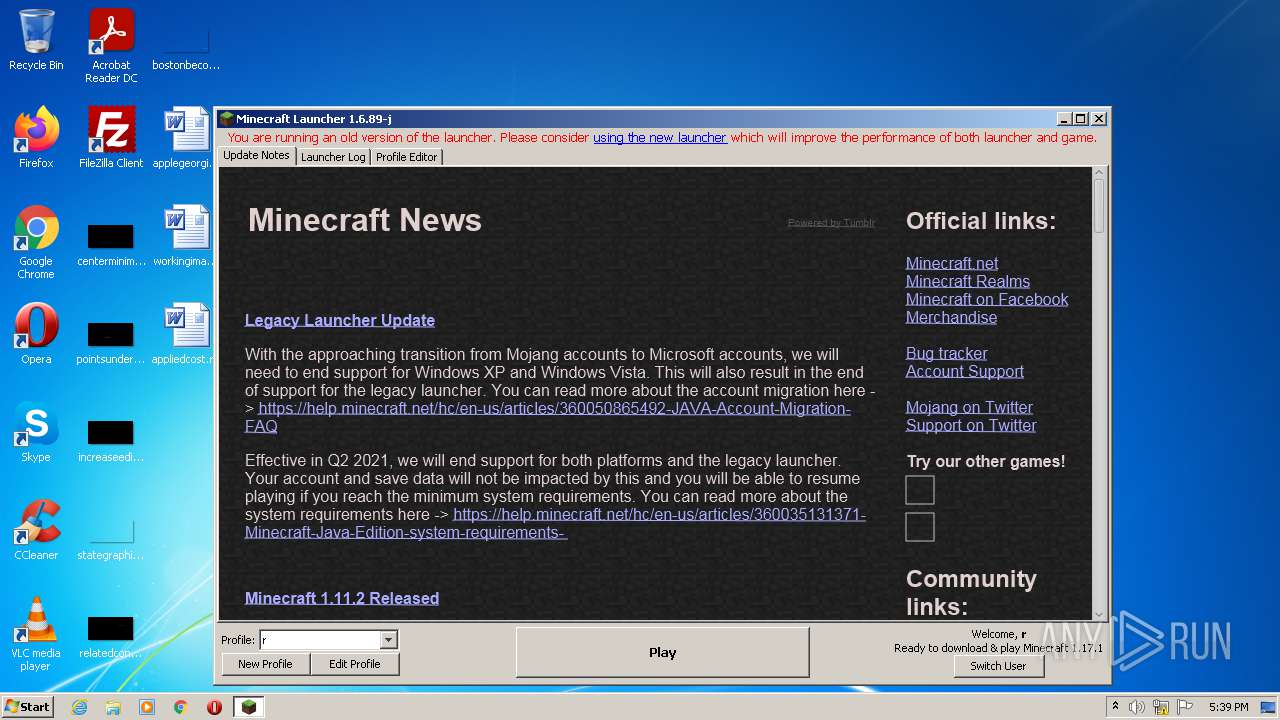
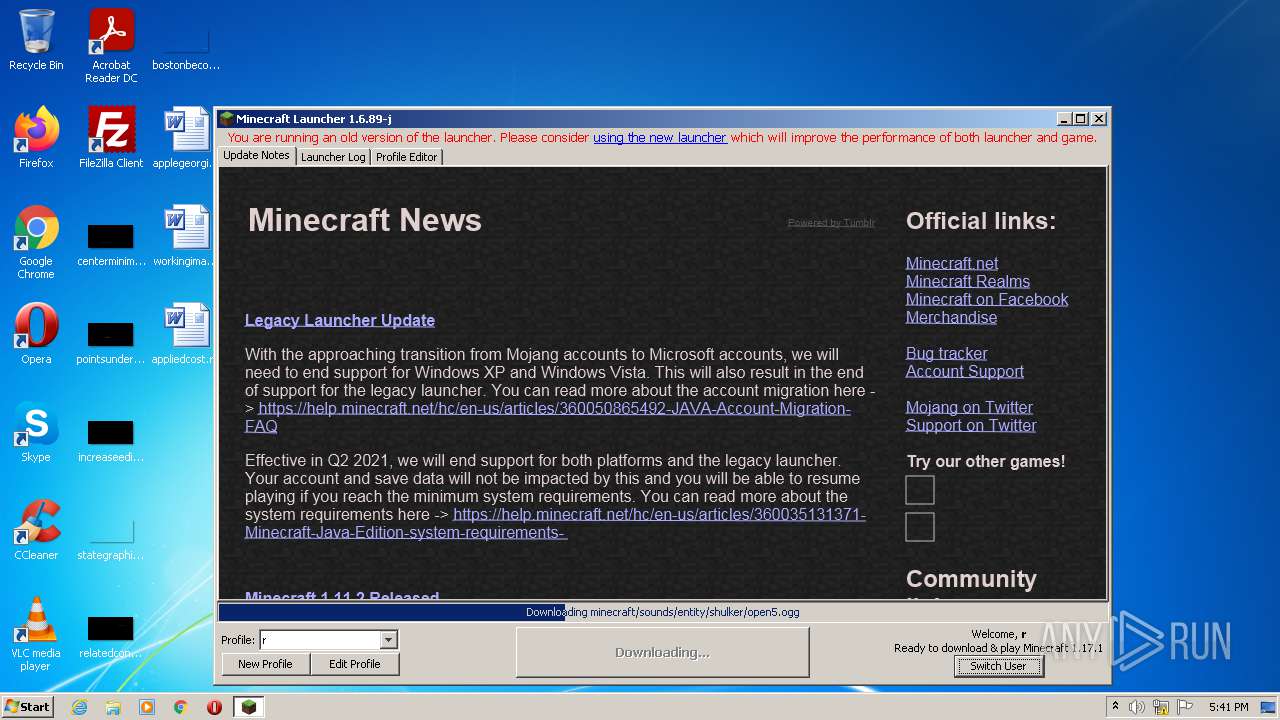
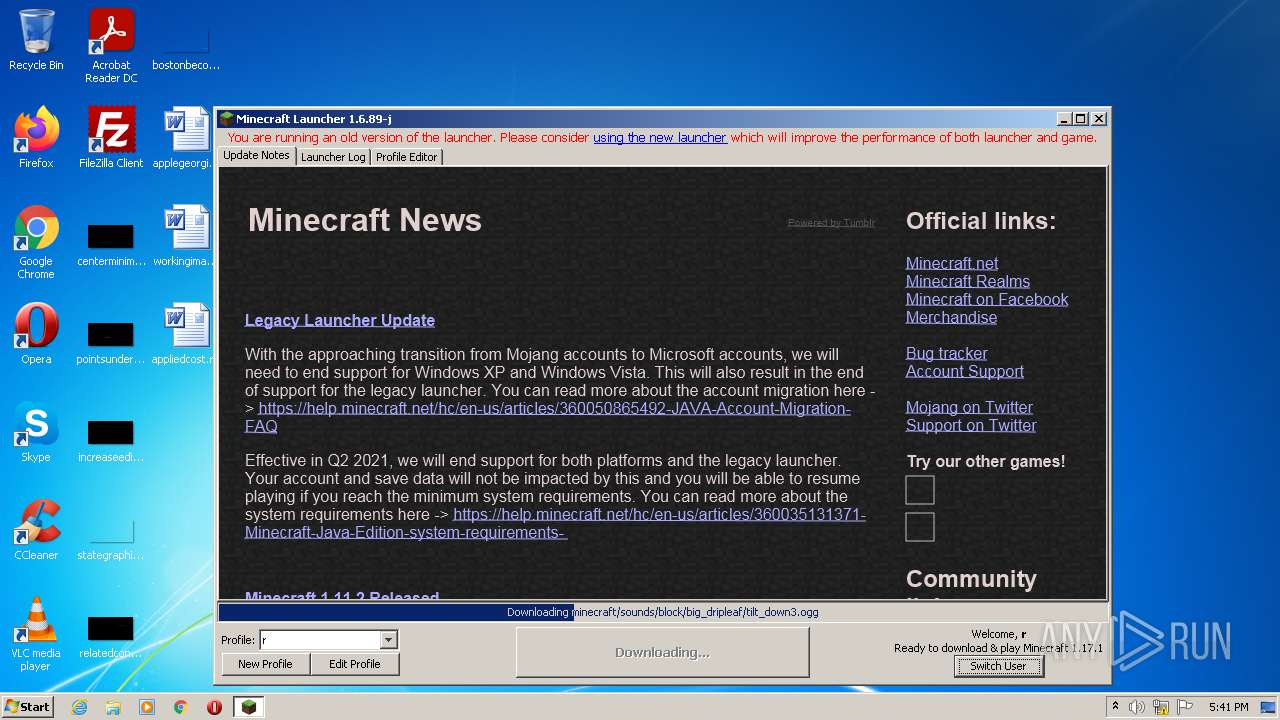
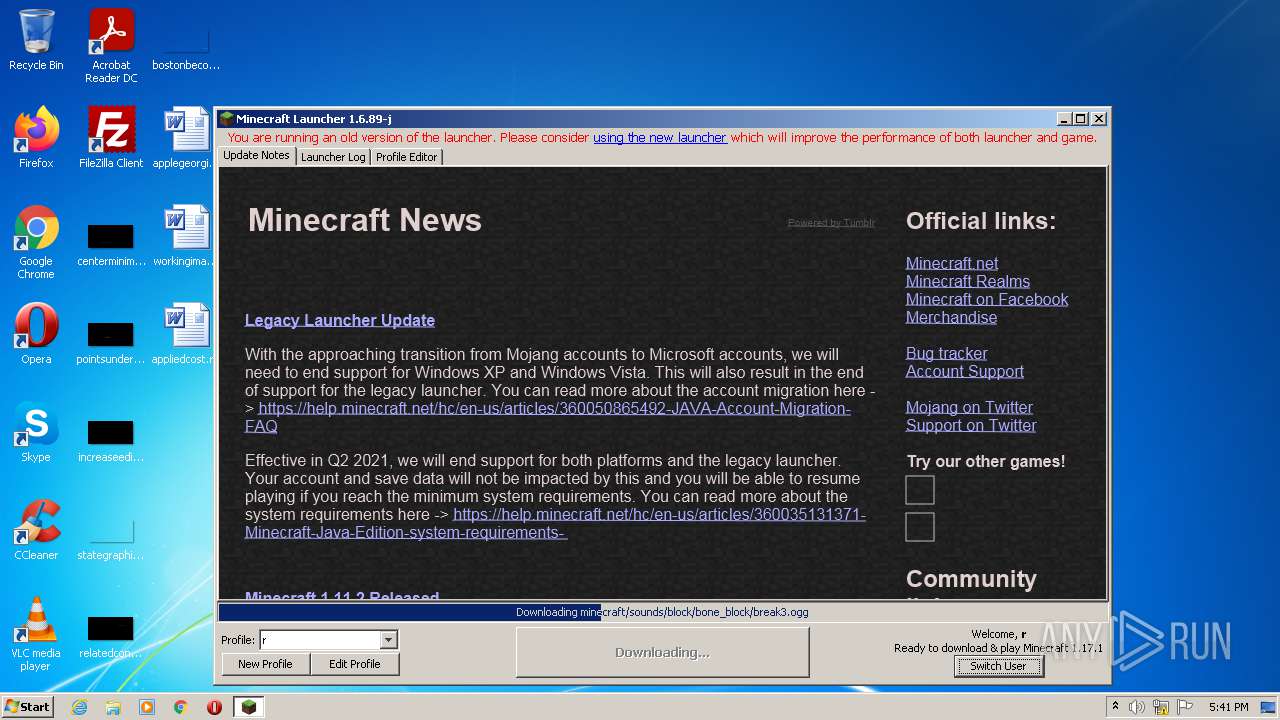
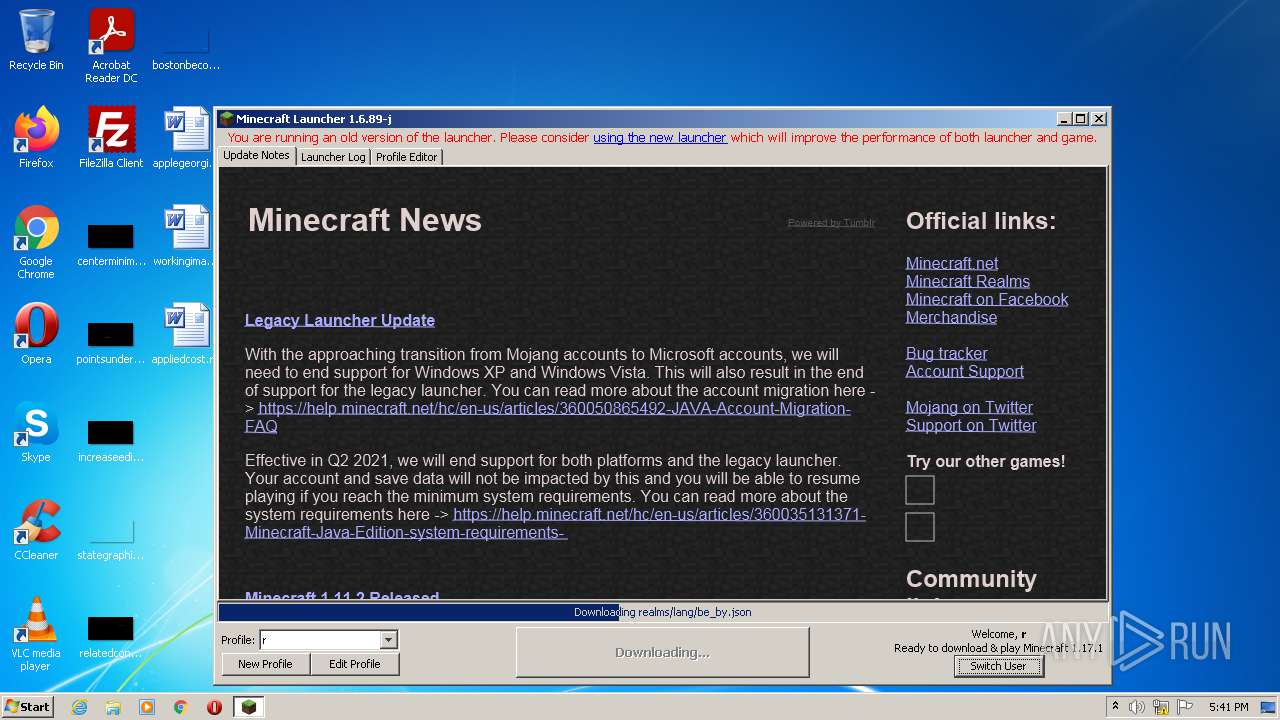
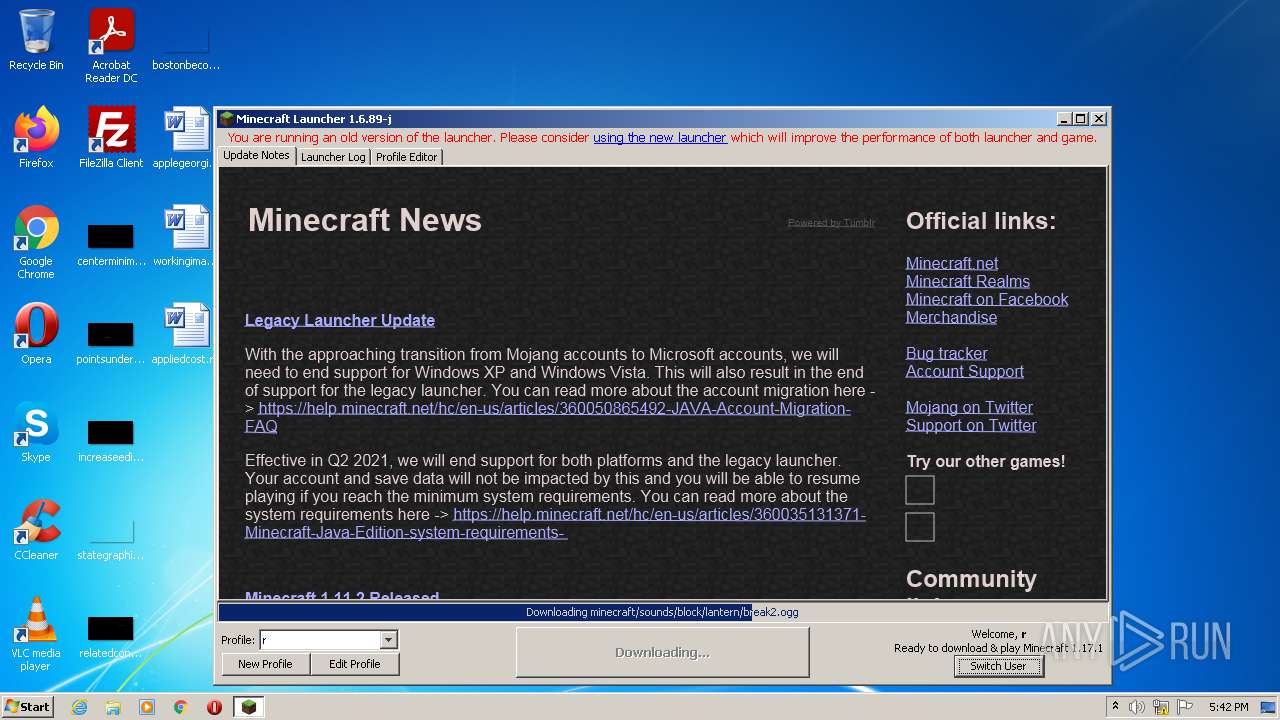
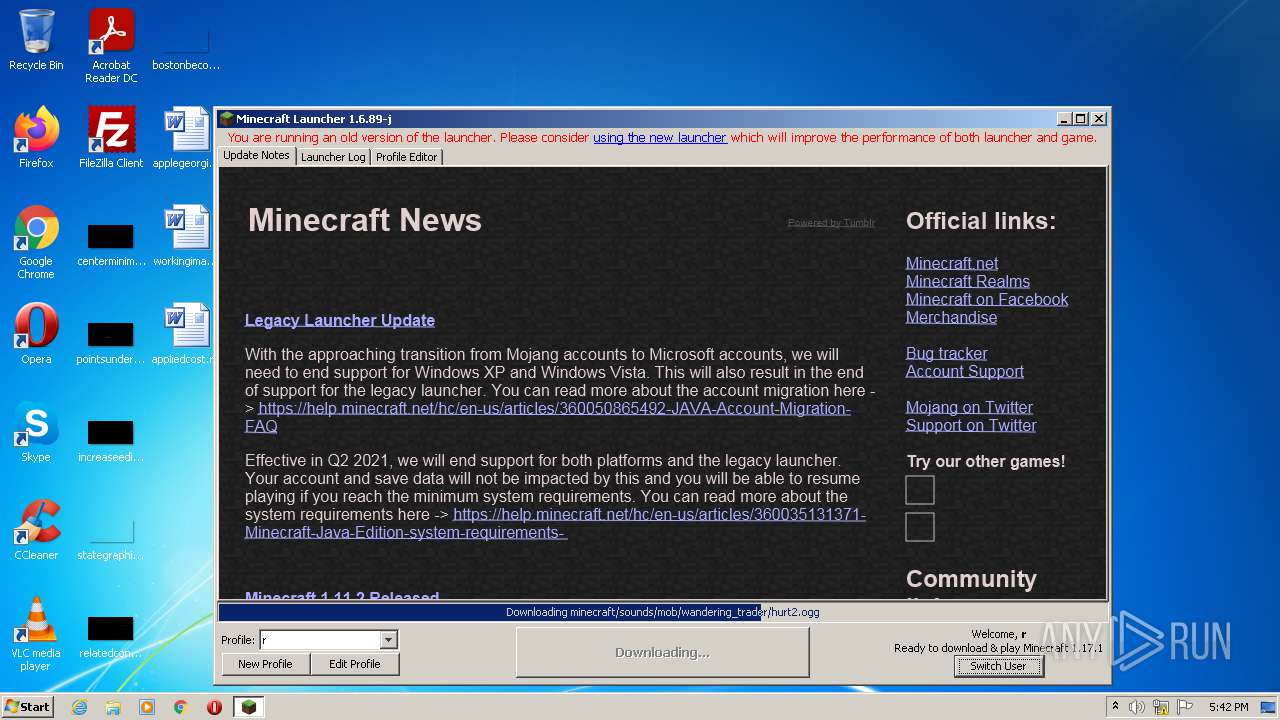
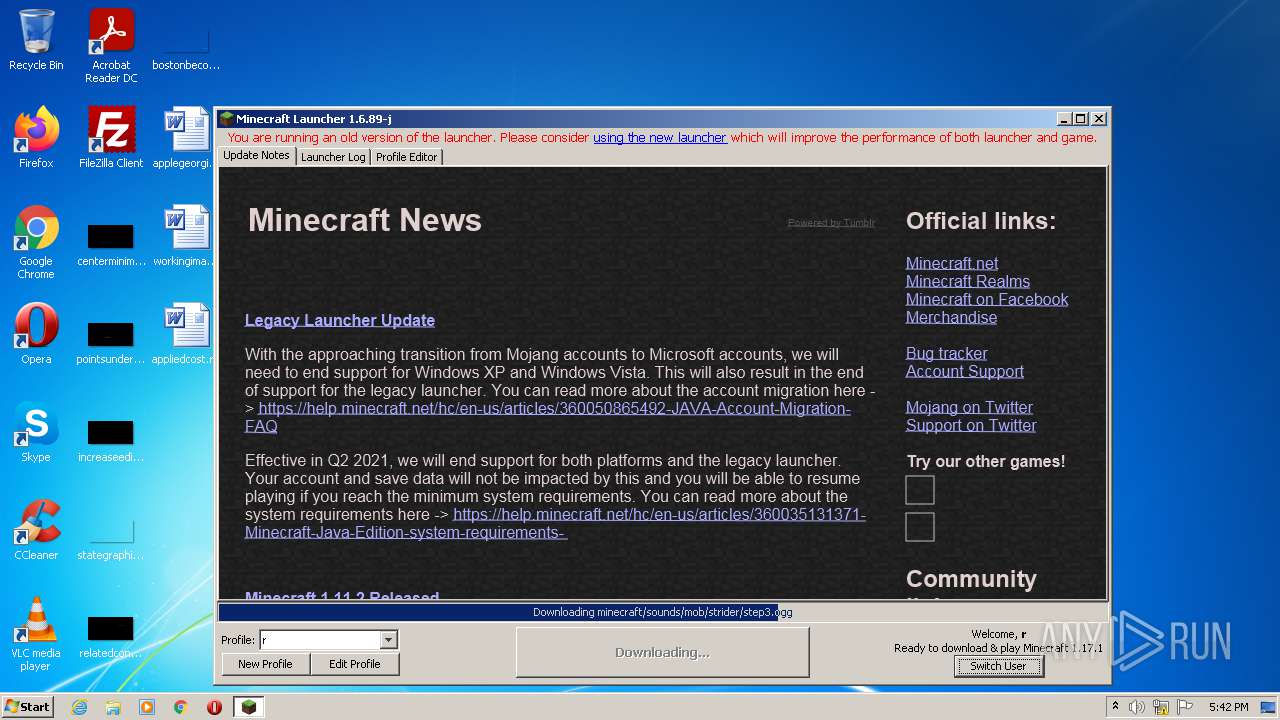
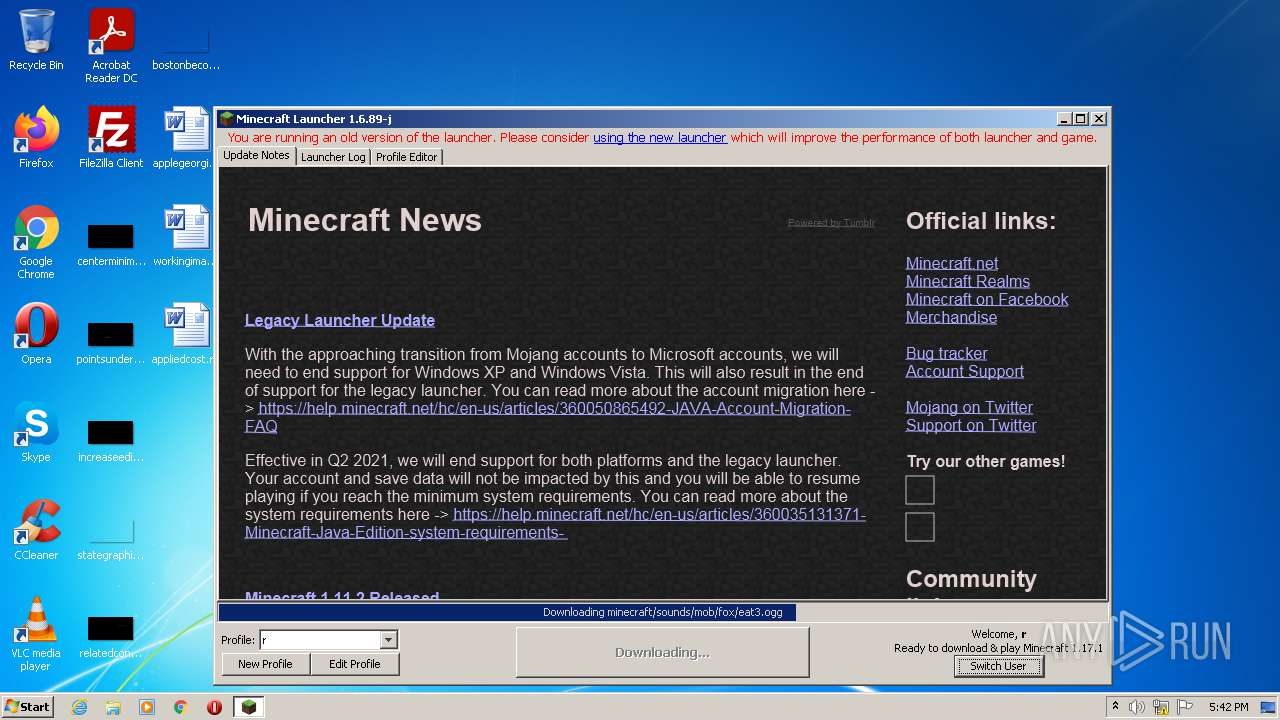
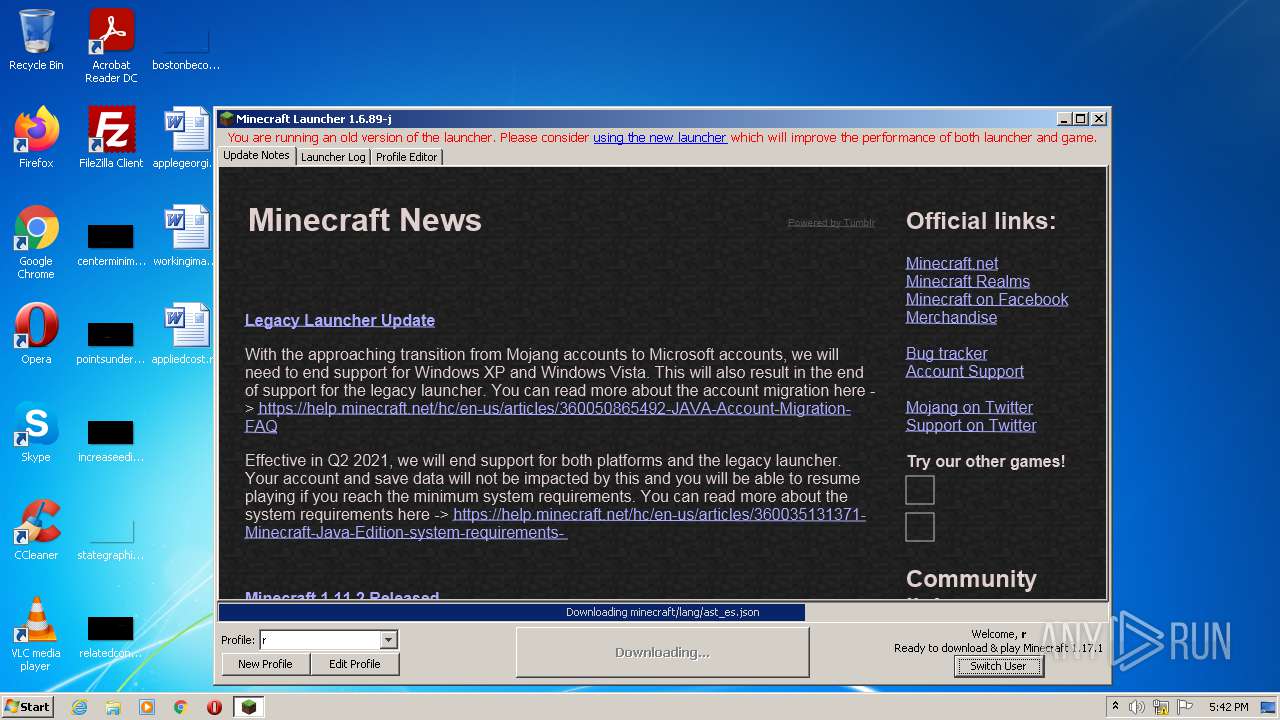
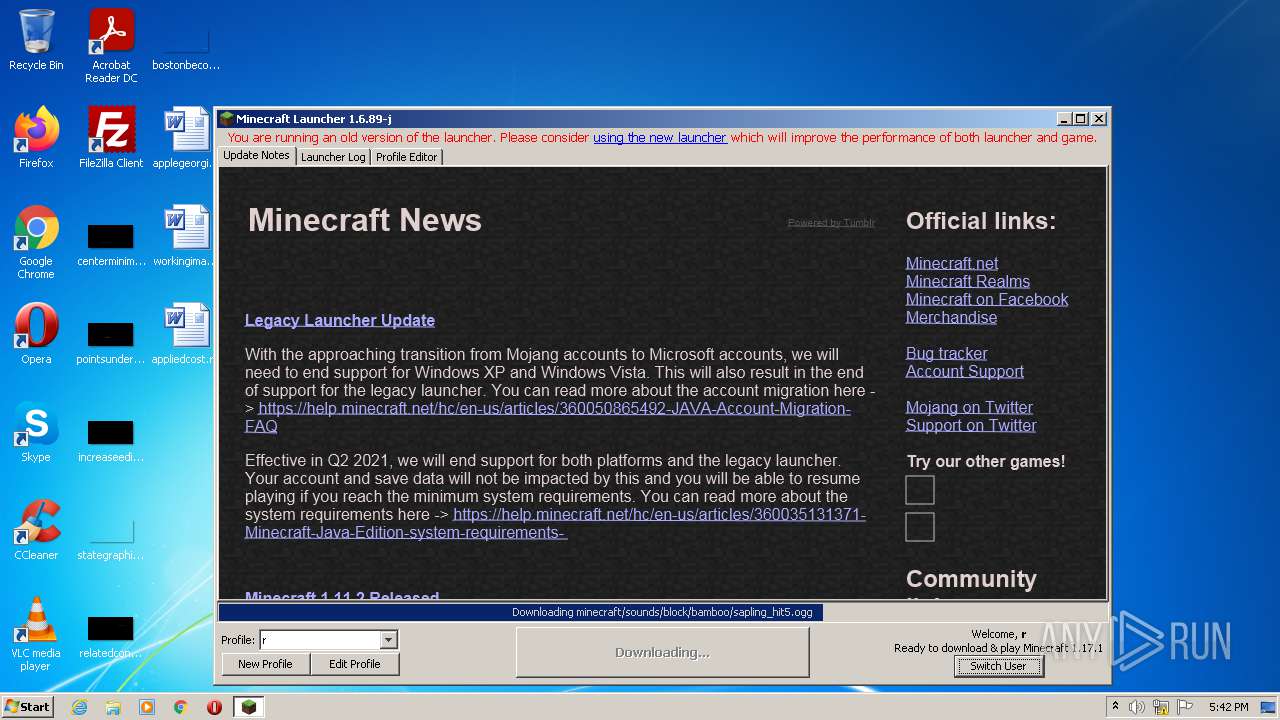
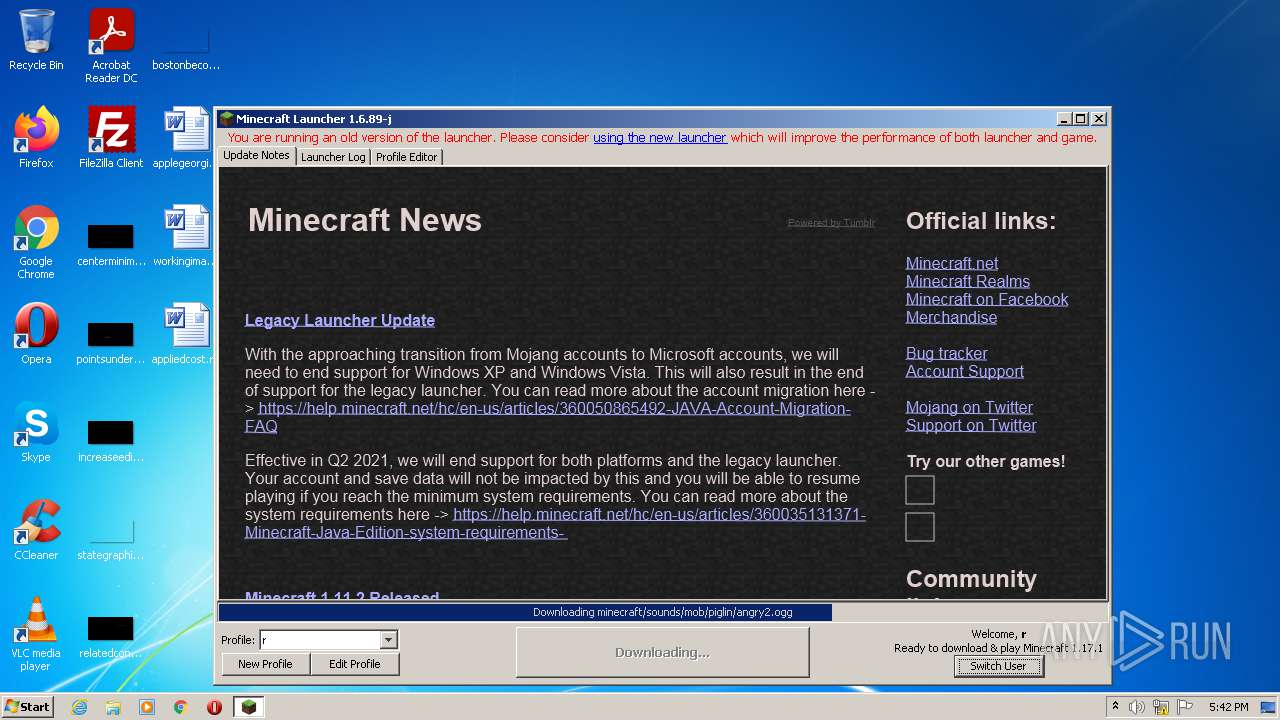
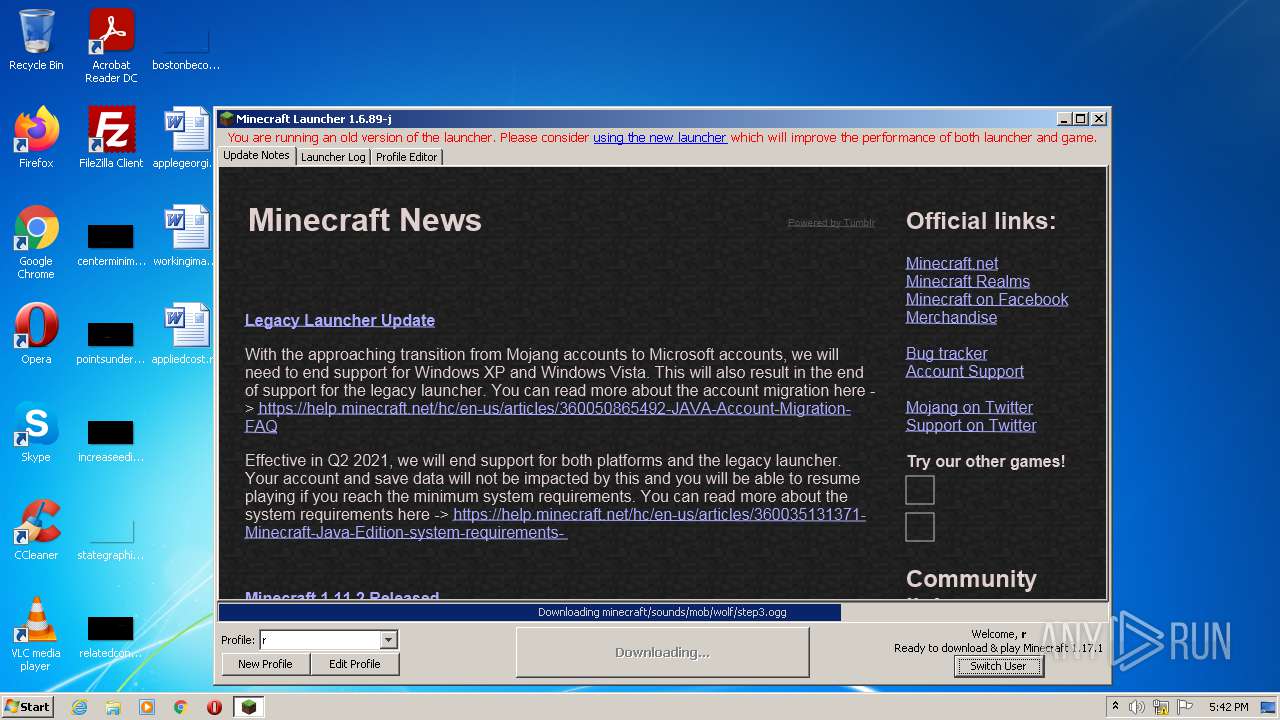
| File name: | Mineshafter-launcher.jar |
| Full analysis: | https://app.any.run/tasks/e01cc25b-1d78-49b3-af6d-86f2c360812f |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2021, 16:38:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | F6CD55DE2534393363E1A40E04D71156 |
| SHA1: | 7A8D89DD5548D6BDF8DE77E198AD518300C560CF |
| SHA256: | C03140A4216BD64EE1BF7D5E7416973F1E3F9E60B0513ADA448893DD6952EAD6 |
| SSDEEP: | 3072:hDDxhlswtTmiVBmqt7yANM/+0QGLF0BVHt:JNBtTmCBm07tMpQ4F0/t |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the program directory
- javaw.exe (PID: 3412)
Checks supported languages
- javaw.exe (PID: 3412)
- javaw.exe (PID: 1116)
Uses ICACLS.EXE to modify access control list
- javaw.exe (PID: 3412)
Reads the computer name
- javaw.exe (PID: 3412)
Starts Internet Explorer
- javaw.exe (PID: 3412)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2440)
Executable content was dropped or overwritten
- javaw.exe (PID: 3412)
Drops a file that was compiled in debug mode
- javaw.exe (PID: 3412)
Executes JAVA applets
- javaw.exe (PID: 3412)
Application launched itself
- javaw.exe (PID: 3412)
Creates files in the user directory
- javaw.exe (PID: 3412)
INFO
Reads the computer name
- iexplore.exe (PID: 2060)
- icacls.exe (PID: 3892)
- iexplore.exe (PID: 2440)
Application launched itself
- iexplore.exe (PID: 2060)
Checks supported languages
- iexplore.exe (PID: 2440)
- icacls.exe (PID: 3892)
- iexplore.exe (PID: 2060)
Reads settings of System Certificates
- iexplore.exe (PID: 2440)
Reads the date of Windows installation
- iexplore.exe (PID: 2060)
Dropped object may contain Bitcoin addresses
- javaw.exe (PID: 3412)
Changes internet zones settings
- iexplore.exe (PID: 2060)
Checks Windows Trust Settings
- iexplore.exe (PID: 2440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | META-INF/MANIFEST.MF |
|---|---|
| ZipUncompressedSize: | 65 |
| ZipCompressedSize: | 67 |
| ZipCRC: | 0xe40dfb26 |
| ZipModifyDate: | 2019:09:05 23:31:15 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0808 |
| ZipRequiredVersion: | 20 |
Total processes
40
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
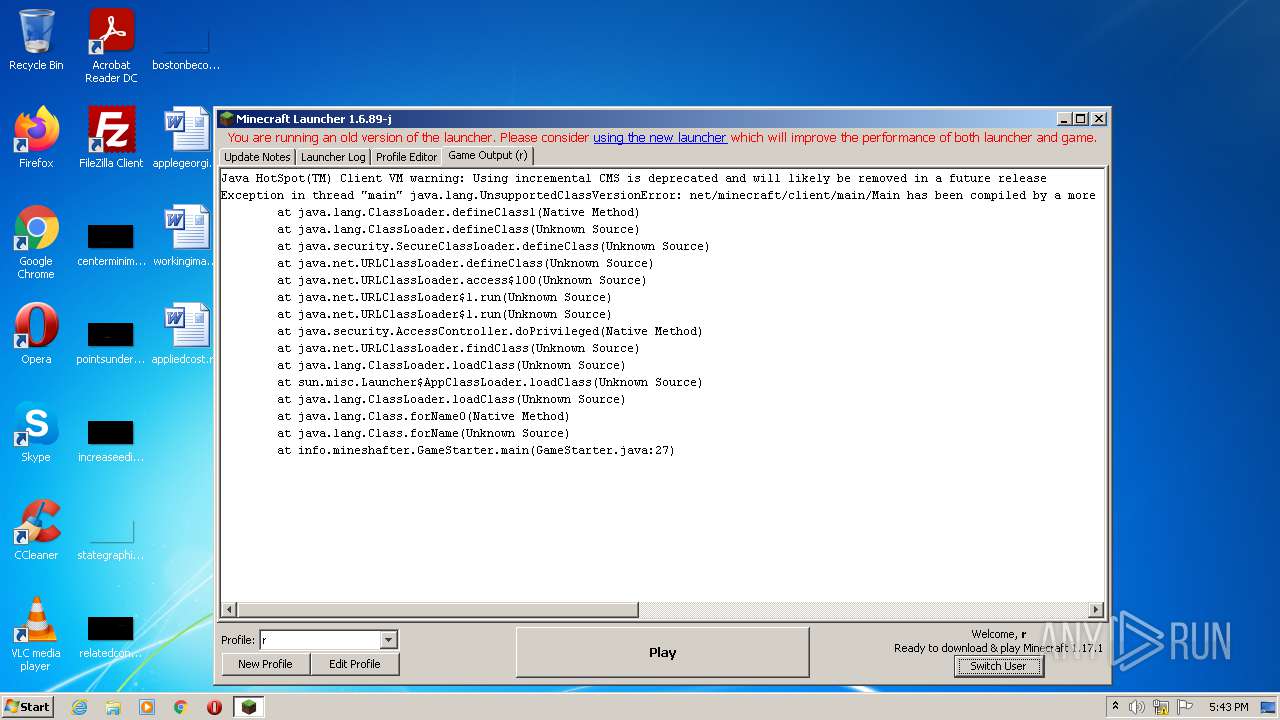
| 1116 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -Xmx512M -XX:+UseConcMarkSweepGC -XX:+CMSIncrementalMode -XX:-UseAdaptiveSizePolicy -Xmn128M -XX:HeapDumpPath=MojangTricksIntelDriversForPerformance_javaw.exe_minecraft.exe.heapdump -Xss1M -Djava.library.path=C:\Users\admin\AppData\Roaming\.minecraft\versions\1.17.1\1.17.1-natives-961872907031 -Dminecraft.launcher.brand=java-minecraft-launcher -Dminecraft.launcher.version=1.6.89-j -cp C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\blocklist\1.0.5\blocklist-1.0.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\patchy\2.1.6\patchy-2.1.6.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\github\oshi\oshi-core\5.7.5\oshi-core-5.7.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\dev\jna\jna\5.8.0\jna-5.8.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\dev\jna\jna-platform\5.8.0\jna-platform-5.8.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\slf4j\slf4j-api\1.8.0-beta4\slf4j-api-1.8.0-beta4.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\logging\log4j\log4j-slf4j18-impl\2.14.1\log4j-slf4j18-impl-2.14.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\ibm\icu\icu4j\66.1\icu4j-66.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\javabridge\1.1.23\javabridge-1.1.23.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\sf\jopt-simple\jopt-simple\5.0.3\jopt-simple-5.0.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\io\netty\netty-all\4.1.25.Final\netty-all-4.1.25.Final.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\guava\guava\21.0\guava-21.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\commons\commons-lang3\3.5\commons-lang3-3.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-io\commons-io\2.5\commons-io-2.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-codec\commons-codec\1.10\commons-codec-1.10.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\jinput\jinput\2.0.5\jinput-2.0.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\jutils\jutils\1.0.0\jutils-1.0.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\brigadier\1.0.18\brigadier-1.0.18.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\datafixerupper\4.0.26\datafixerupper-4.0.26.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\code\gson\gson\2.8.0\gson-2.8.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\authlib\2.3.31\authlib-2.3.31.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\commons\commons-compress\1.8.1\commons-compress-1.8.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\httpcomponents\httpclient\4.3.3\httpclient-4.3.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-logging\commons-logging\1.1.3\commons-logging-1.1.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\httpcomponents\httpcore\4.3.2\httpcore-4.3.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\it\unimi\dsi\fastutil\8.2.1\fastutil-8.2.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\logging\log4j\log4j-api\2.14.1\log4j-api-2.14.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\logging\log4j\log4j-core\2.14.1\log4j-core-2.14.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl\3.2.2\lwjgl-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-jemalloc\3.2.2\lwjgl-jemalloc-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-openal\3.2.2\lwjgl-openal-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-opengl\3.2.2\lwjgl-opengl-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-glfw\3.2.2\lwjgl-glfw-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-stb\3.2.2\lwjgl-stb-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl-tinyfd\3.2.2\lwjgl-tinyfd-3.2.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\text2speech\1.11.3\text2speech-1.11.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\versions\1.17.1\1.17.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\ms-starter.jar info.mineshafter.GameStarter net.minecraft.client.main.Main --username r --version 1.17.1 --gameDir C:\Users\admin\AppData\Roaming\.minecraft --assetsDir C:\Users\admin\AppData\Roaming\.minecraft\assets --assetIndex 1.17 --uuid 4b43b0aee35624cd95b910189b3dc231 --accessToken 472888c9-b688-edc1-ab01-ea321c4a7029 --userType mojang --versionType release | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
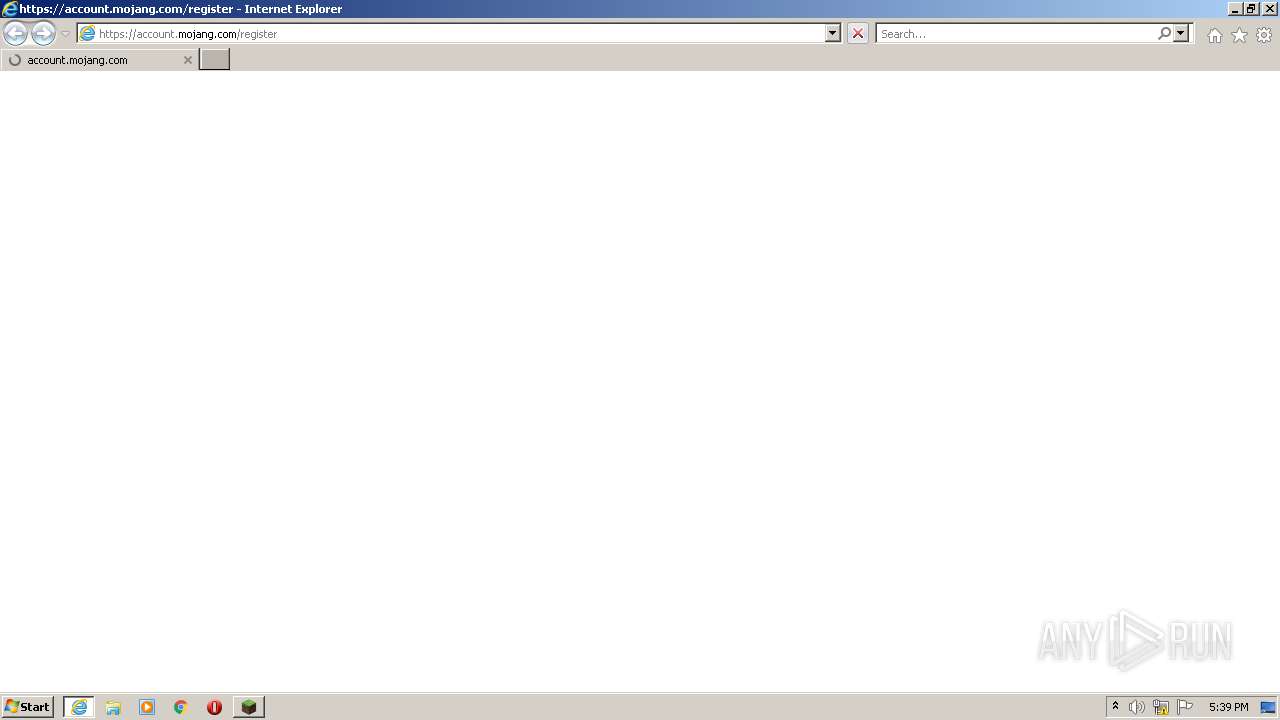
| 2060 | "C:\Program Files\Internet Explorer\iexplore.exe" https://account.mojang.com/register | C:\Program Files\Internet Explorer\iexplore.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2440 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2060 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3412 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\Mineshafter-launcher.jar.zip" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | Explorer.EXE | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3892 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\system32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 631
Read events
6 568
Write events
62
Delete events
1
Modification events
| (PID) Process: | (3412) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 673378368 | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30899992 | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 973504696 | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30899992 | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2060) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
39
Suspicious files
37
Text files
295
Unknown types
2 759
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3412 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:— | SHA256:— | |||
| 3412 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher.pack.lzma.new | lzma | |
MD5:— | SHA256:— | |||
| 3412 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher_mcpatched.jar | compressed | |
MD5:— | SHA256:— | |||
| 3412 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher_profiles.json | text | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_93E4B2BA79A897B3100CCB27F2D3BF4F | der | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 3412 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher.pack.lzma | lzma | |
MD5:— | SHA256:— | |||
| 3412 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher.pack | binary | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3 030
TCP/UDP connections
67
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3412 | javaw.exe | GET | 302 | 74.114.154.18:80 | http://mcupdate.tumblr.com/ | CA | — | — | suspicious |
3412 | javaw.exe | GET | 200 | 143.204.98.69:80 | http://resources.download.minecraft.net/7d/7ddf113383574a42b1570d5878c1c17b40b5cc3a | US | text | 321 Kb | shared |
2440 | iexplore.exe | GET | 200 | 13.32.23.69:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
2440 | iexplore.exe | GET | 200 | 13.32.23.215:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2440 | iexplore.exe | GET | 200 | 143.204.214.141:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAgt6Wb%2F1rMtYV4NvNJ9088%3D | US | der | 471 b | whitelisted |
3412 | javaw.exe | GET | 200 | 143.204.98.69:80 | http://resources.download.minecraft.net/93/93d7176f92d6525bb62bd75280047cf0eba04e24 | US | ogg | 32.2 Kb | shared |
3412 | javaw.exe | GET | 200 | 143.204.98.69:80 | http://resources.download.minecraft.net/58/580a2de441d8caa949758dfb193ba3e6ab4ee61d | US | ogg | 11.6 Kb | shared |
3412 | javaw.exe | GET | 200 | 143.204.98.69:80 | http://resources.download.minecraft.net/8d/8d56863e83e0e114937522d3a4a7e124528c65b4 | US | ogg | 4.16 Kb | shared |
3412 | javaw.exe | GET | 200 | 143.204.98.69:80 | http://resources.download.minecraft.net/b8/b88ded63fb4428d72b0b7ef07dd870b6e1fad52f | US | ogg | 34.6 Kb | shared |
3412 | javaw.exe | GET | 200 | 143.204.98.69:80 | http://resources.download.minecraft.net/3a/3a395719dac4db21f2092558c28afcf35b833d99 | US | ogg | 52.0 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3412 | javaw.exe | 185.142.236.247:443 | mineshafter.info | Cogent Communications | NL | unknown |
3412 | javaw.exe | 74.114.154.18:80 | mcupdate.tumblr.com | Automattic, Inc | CA | malicious |
3412 | javaw.exe | 143.204.93.135:443 | launchermeta.mojang.com | — | US | unknown |
3412 | javaw.exe | 74.114.154.18:443 | mcupdate.tumblr.com | Automattic, Inc | CA | malicious |
3412 | javaw.exe | 192.0.77.40:443 | assets.tumblr.com | Automattic, Inc | US | suspicious |
3412 | javaw.exe | 192.0.77.3:443 | 64.media.tumblr.com | Automattic, Inc | US | suspicious |
2440 | iexplore.exe | 205.185.216.42:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2440 | iexplore.exe | 13.32.23.204:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
2440 | iexplore.exe | 143.204.214.141:80 | ocsp.sca1b.amazontrust.com | — | US | whitelisted |
2440 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mineshafter.info |
| whitelisted |
s3.amazonaws.com |
| shared |
launchermeta.mojang.com |
| whitelisted |
mcupdate.tumblr.com |
| suspicious |
assets.tumblr.com |
| whitelisted |
64.media.tumblr.com |
| suspicious |
assets.mojang.com |
| shared |
px.srvcs.tumblr.com |
| whitelisted |
static.tumblr.com |
| whitelisted |
account.mojang.com |
| whitelisted |