| File name: | 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7 |
| Full analysis: | https://app.any.run/tasks/d609343b-5bdc-478b-9dff-4a5aa6cc2fdb |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2024, 18:54:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 11 sections |
| MD5: | 730F5713420FD708FB3DDFE631ACFC4F |
| SHA1: | 9CCB4B66EAB6E2ACF43C8C091D292967E7ACAAA7 |
| SHA256: | C02DEAC6989B918DE381B7FC8C05D93988A2FC85499BA6E884A1EBAB712E1240 |
| SSDEEP: | 196608:yETNxVVmgS/kYYAmZMruJqHGa+jb+89Lnw+7dfUm/2Ou9hPIQEqGEZDHDi+WQO0a:yETim48LpEcLHx |
MALICIOUS
XORed URL has been found (YARA)
- 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe (PID: 6092)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(6092) 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe
Decrypted-URLs (6)http://cacerts.digicert.com/DigiCertSHA2AssuredIDCodeSigningCA.crt0
http://crl3.digicert.com/sha2-assured-cs-g1.crl05
http://crl4.digicert.com/sha2-assured-cs-g1.crl0L
http://ocsp.digicert.com0N
http://www.appeon.com
https://www.digicert.com/CPS0
Decrypted-URLs (6)http://cacerts.digicert.com/DigiCertAssuredIDRootCA.crt0
http://crl.microsoft.com/pki/crl/products/MicrosoftCodeVerifRoot.crl0
http://crl3.digicert.com/DigiCertAssuredIDRootCA.crl0O
http://crl4.digicert.com/DigiCertAssuredIDRootCA.crl0:
http://ocsp.digicert.com0C
https://www.digicert.com/CPS0
Decrypted-URLs (11)http://cacerts.digicert.com/DigiCertAssuredIDRootCA.crt0
http://cacerts.digicert.com/DigiCertSHA2AssuredIDCodeSigningCA.crt0
http://crl.microsoft.com/pki/crl/products/MicrosoftCodeVerifRoot.crl0
http://crl3.digicert.com/DigiCertAssuredIDRootCA.crl0O
http://crl3.digicert.com/sha2-assured-cs-g1.crl05
http://crl4.digicert.com/DigiCertAssuredIDRootCA.crl0:
http://crl4.digicert.com/sha2-assured-cs-g1.crl0L
http://ocsp.digicert.com0C
http://ocsp.digicert.com0N
http://www.appeon.com
https://www.digicert.com/CPS0
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:11:14 02:01:51+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 553472 |
| InitializedDataSize: | 2950656 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xeca933 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
125
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3988 | "C:\Users\admin\Desktop\9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe" | C:\Users\admin\Desktop\9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5092 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6092 | "C:\Users\admin\Desktop\9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe" | C:\Users\admin\Desktop\9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
xor-url(PID) Process(6092) 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe Decrypted-URLs (6)http://cacerts.digicert.com/DigiCertSHA2AssuredIDCodeSigningCA.crt0 http://crl3.digicert.com/sha2-assured-cs-g1.crl05 http://crl4.digicert.com/sha2-assured-cs-g1.crl0L http://ocsp.digicert.com0N http://www.appeon.com https://www.digicert.com/CPS0 (PID) Process(6092) 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe Decrypted-URLs (6)http://cacerts.digicert.com/DigiCertAssuredIDRootCA.crt0 http://crl.microsoft.com/pki/crl/products/MicrosoftCodeVerifRoot.crl0 http://crl3.digicert.com/DigiCertAssuredIDRootCA.crl0O http://crl4.digicert.com/DigiCertAssuredIDRootCA.crl0: http://ocsp.digicert.com0C https://www.digicert.com/CPS0 (PID) Process(6092) 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe Decrypted-URLs (11)http://cacerts.digicert.com/DigiCertAssuredIDRootCA.crt0 http://cacerts.digicert.com/DigiCertSHA2AssuredIDCodeSigningCA.crt0 http://crl.microsoft.com/pki/crl/products/MicrosoftCodeVerifRoot.crl0 http://crl3.digicert.com/DigiCertAssuredIDRootCA.crl0O http://crl3.digicert.com/sha2-assured-cs-g1.crl05 http://crl4.digicert.com/DigiCertAssuredIDRootCA.crl0: http://crl4.digicert.com/sha2-assured-cs-g1.crl0L http://ocsp.digicert.com0C http://ocsp.digicert.com0N http://www.appeon.com https://www.digicert.com/CPS0 | |||||||||||||||
Total events
453
Read events
453
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
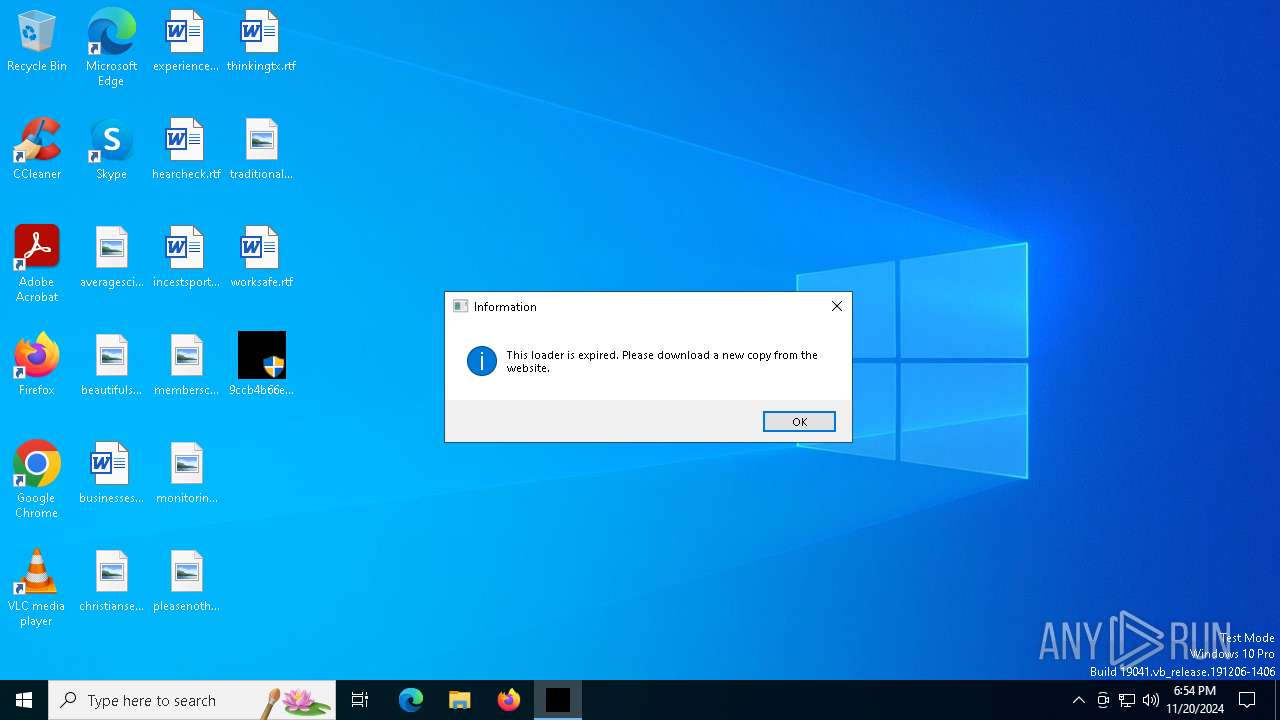
6092 | 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe | POST | 200 | 188.114.97.3:80 | http://www.atlasmods.net/api/external/service.php?serial=rnBUwtFJ3lDAYiIem4YtL5FzrRg9X8lpwXk3qZMulq1021846b&l=expired&c=YWRtaW5AREVTS1RPUC1KR0xMSkxE&q=0 | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3852 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3852 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2800 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2508 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6092 | 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe | 188.114.97.3:80 | www.atlasmods.net | CLOUDFLARENET | NL | unknown |
6092 | 9ccb4b66eab6e2acf43c8c091d292967e7acaaa7.exe | 206.108.0.131:123 | — | — | — | unknown |
4932 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
3852 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.atlasmods.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |