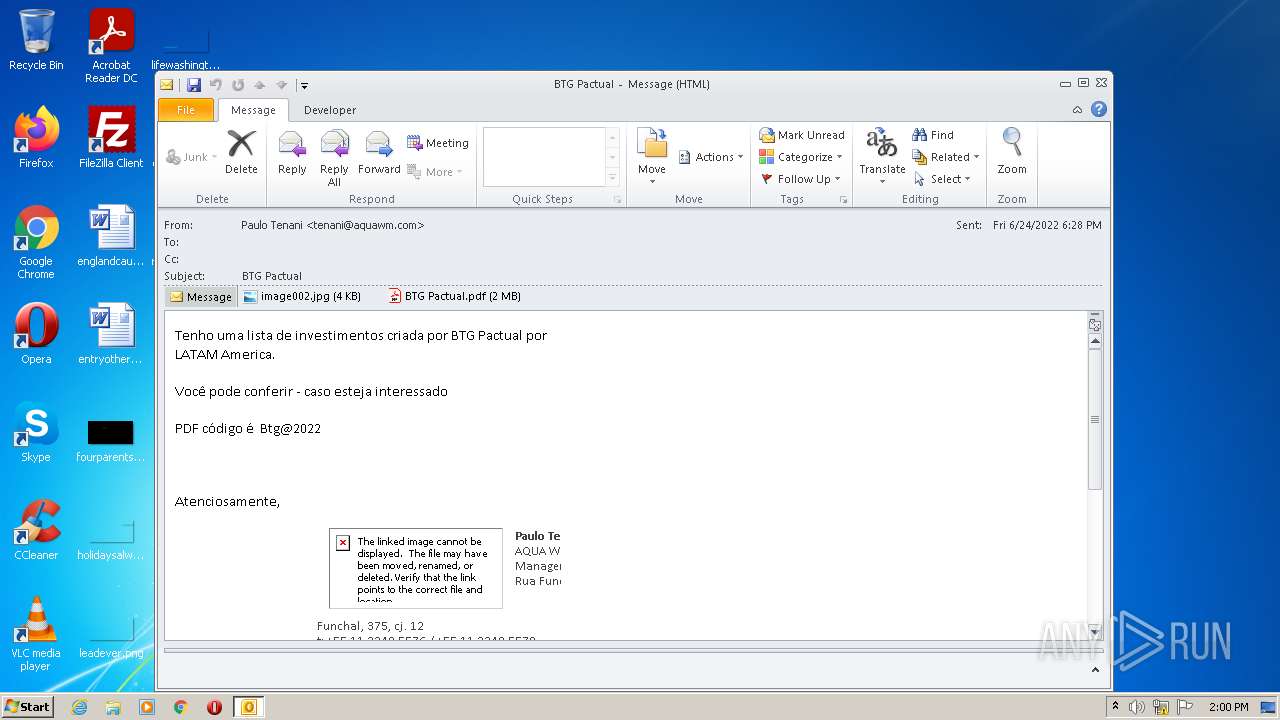
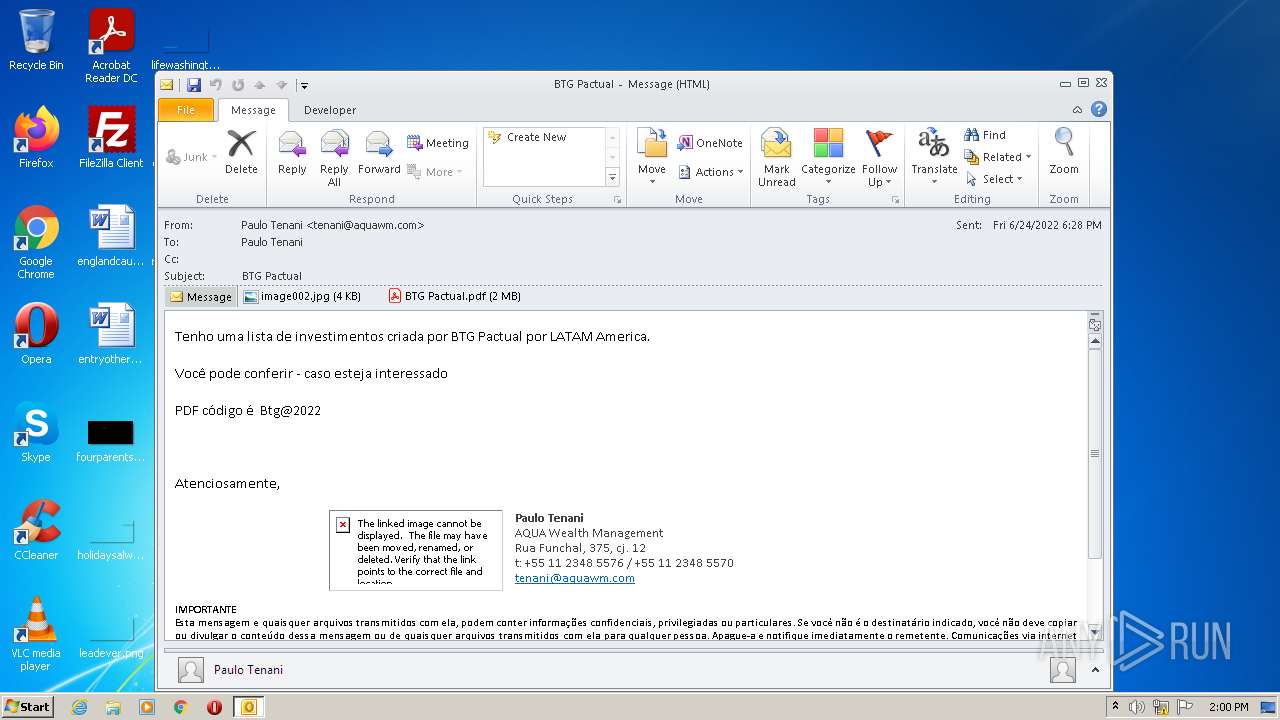
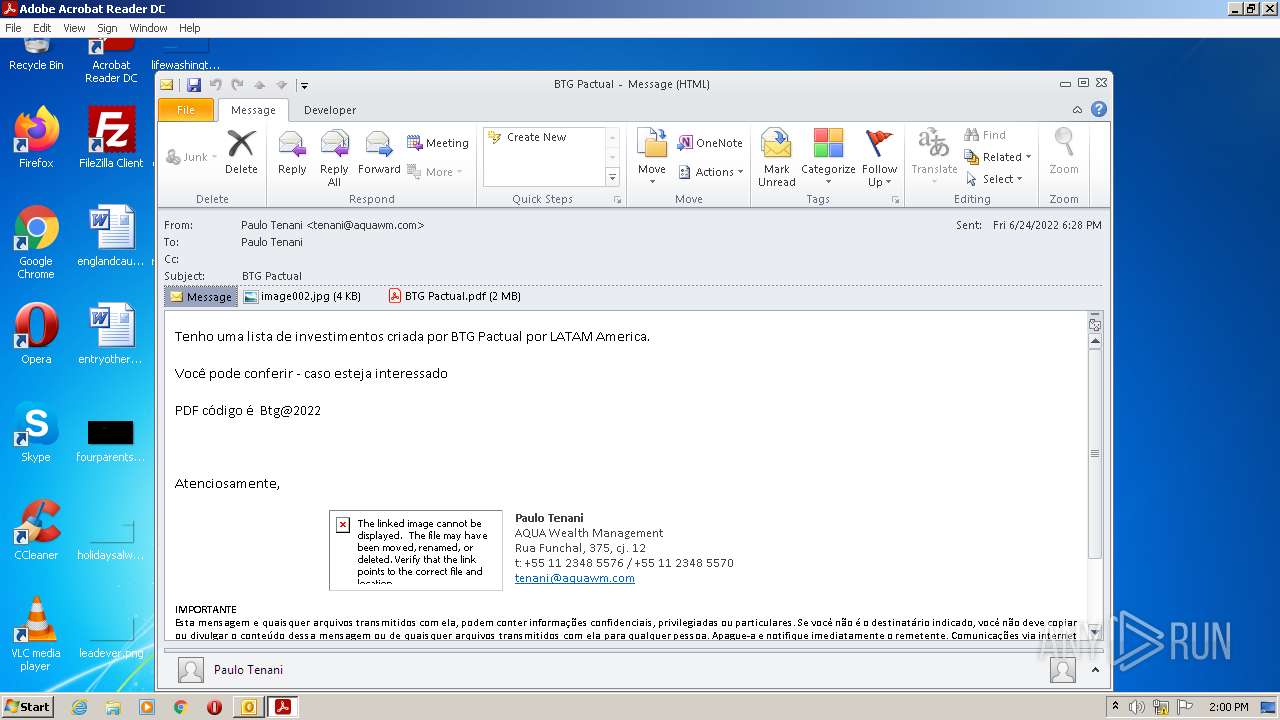
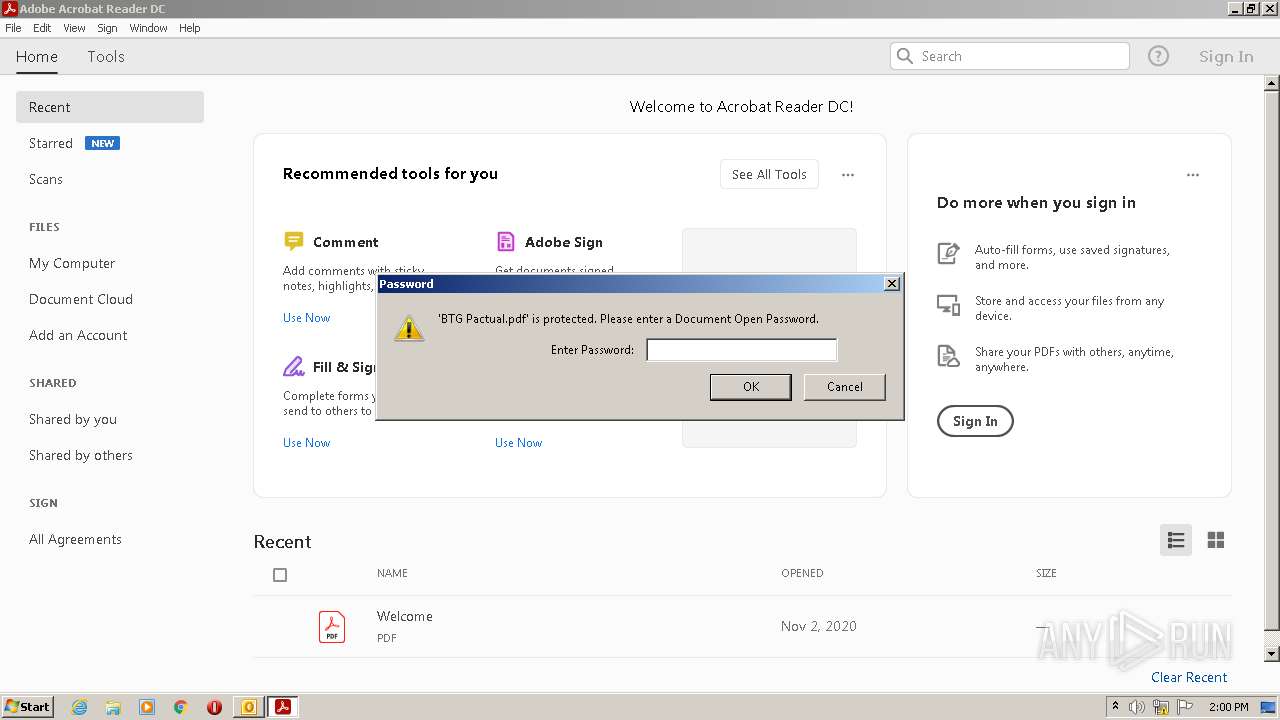
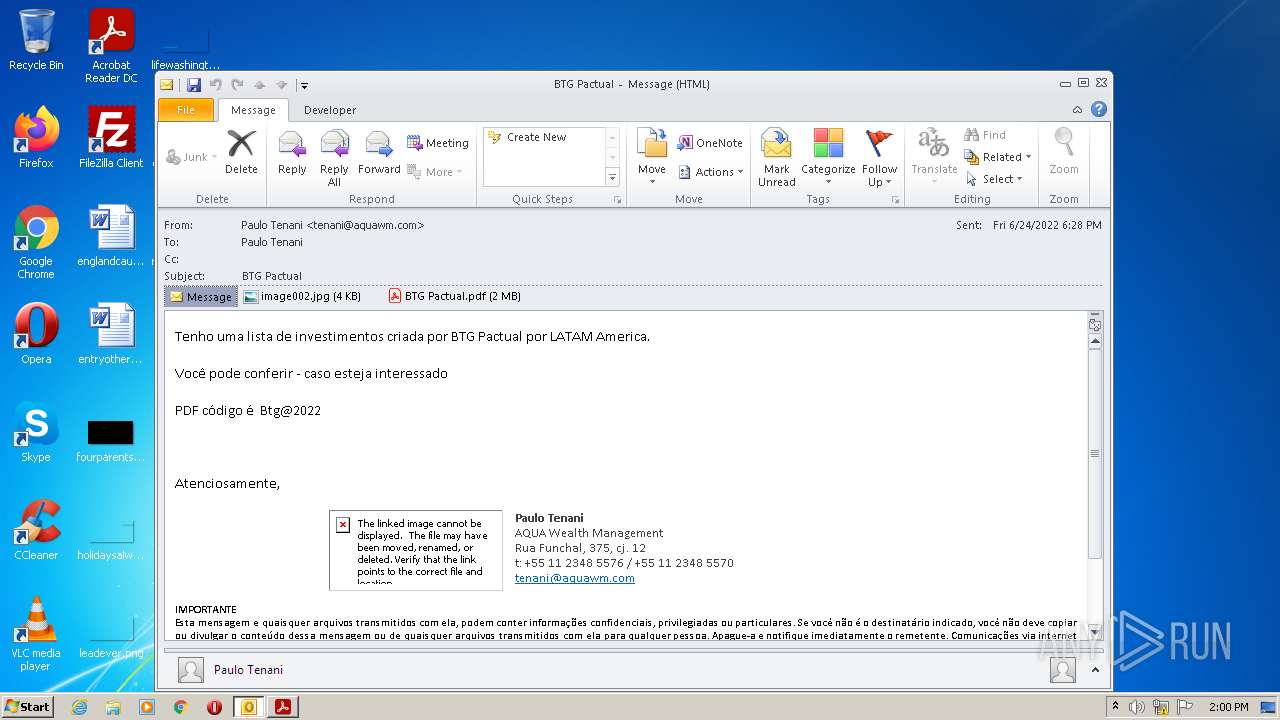
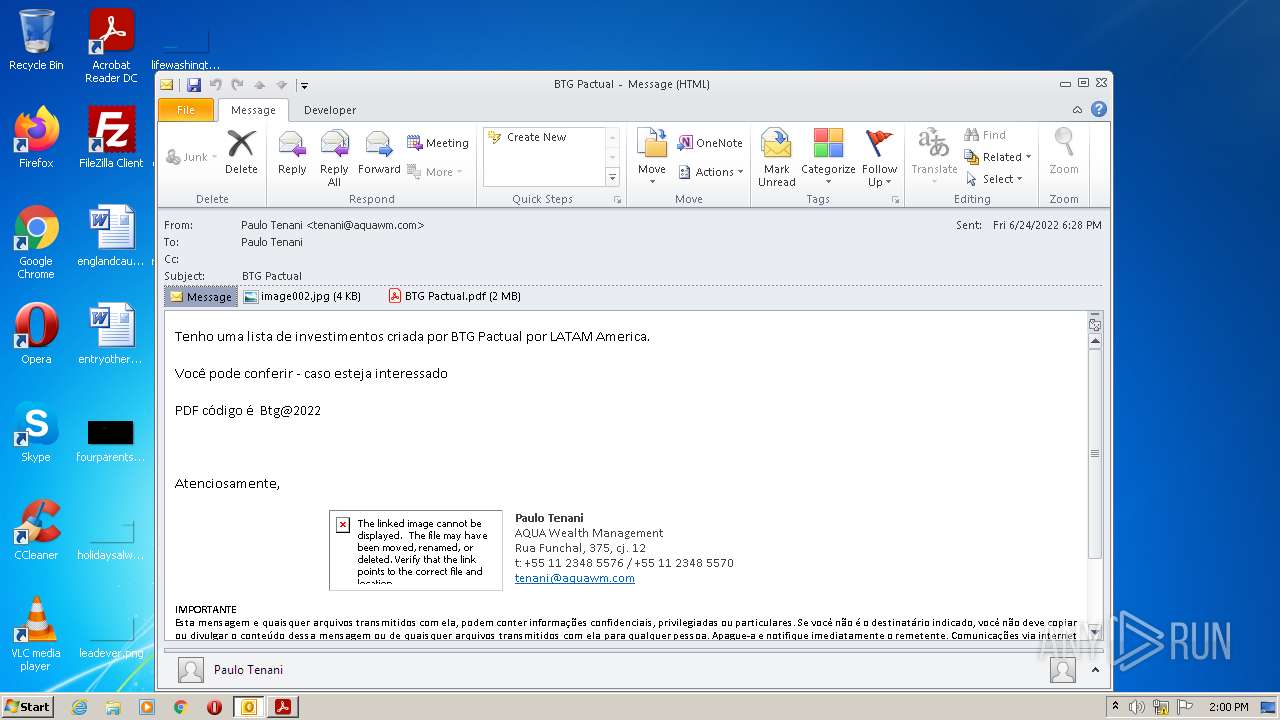
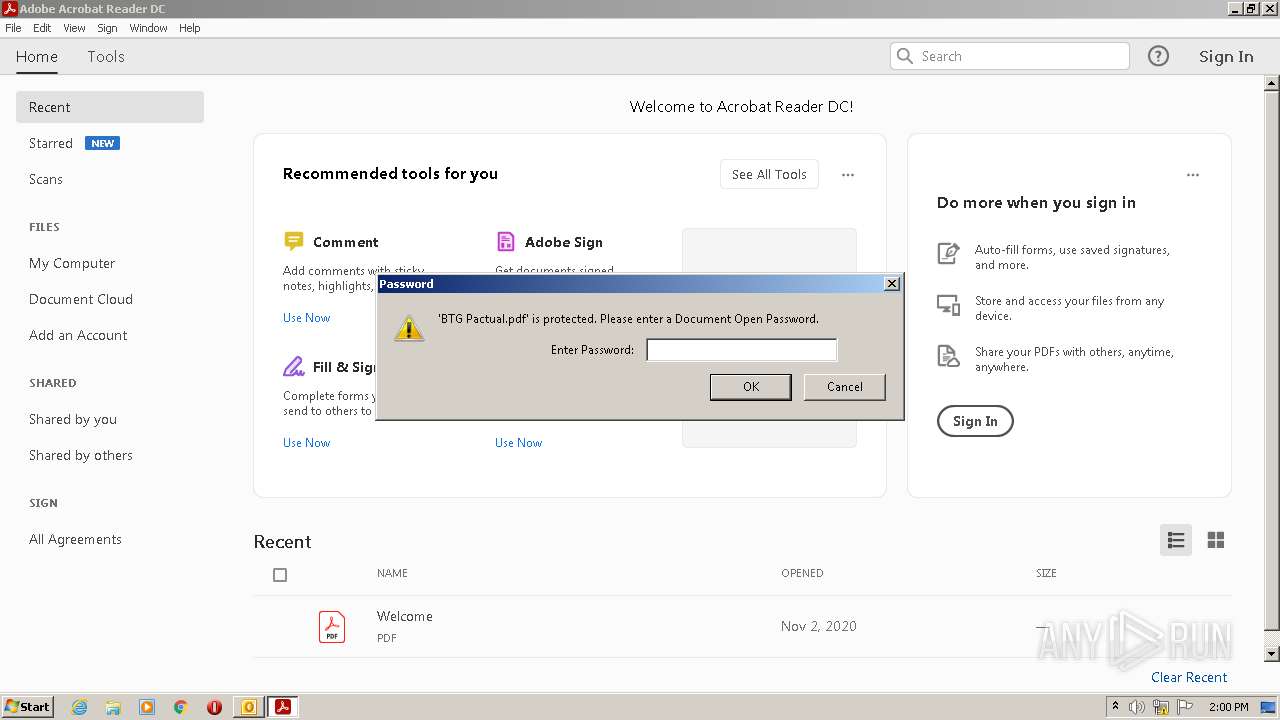
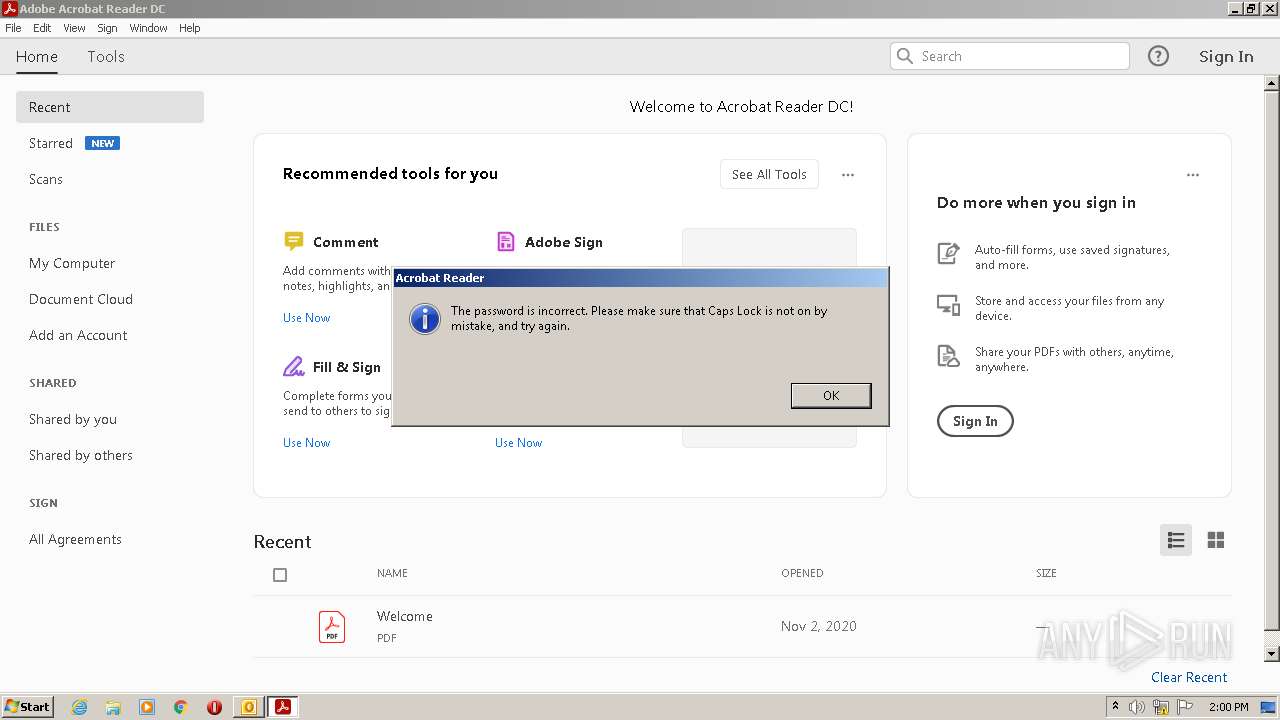
| File name: | Potential Phish (6).eml |
| Full analysis: | https://app.any.run/tasks/4f8feecf-a191-49be-be26-f11108f95a1d |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 13:00:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | multipart/mixed; boundary="===============1170810377320412942==", ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 10ADF8A9DB4CCE0AC1F6FE420A0158A5 |
| SHA1: | 78C5BC0C27661CF20637280164EBDCCFE51CD4E4 |
| SHA256: | C02B571A53CD0D3F5E8D795BCF65DE2E516AEB4F26589FD7A55291D42F633163 |
| SSDEEP: | 49152:cdqNK2lPSbmDKTL8JkCkSLsSZAnb5ckoMpuRXR:n |
MALICIOUS
Drops executable file immediately after starts
- RdrCEF.exe (PID: 2776)
SUSPICIOUS
Checks supported languages
- OUTLOOK.EXE (PID: 2088)
- AdobeARM.exe (PID: 1000)
- Reader_sl.exe (PID: 2312)
Reads the computer name
- OUTLOOK.EXE (PID: 2088)
- AdobeARM.exe (PID: 1000)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2088)
Searches for installed software
- OUTLOOK.EXE (PID: 2088)
Drops a file with a compile date too recent
- RdrCEF.exe (PID: 2776)
Starts Internet Explorer
- AcroRd32.exe (PID: 2100)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2020)
INFO
Reads the computer name
- AcroRd32.exe (PID: 2100)
- AcroRd32.exe (PID: 120)
- RdrCEF.exe (PID: 2776)
- AcroRd32.exe (PID: 3800)
- AcroRd32.exe (PID: 2912)
- iexplore.exe (PID: 1120)
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2020)
Checks supported languages
- AcroRd32.exe (PID: 2100)
- AcroRd32.exe (PID: 120)
- RdrCEF.exe (PID: 2776)
- RdrCEF.exe (PID: 3948)
- RdrCEF.exe (PID: 3072)
- RdrCEF.exe (PID: 2568)
- RdrCEF.exe (PID: 2188)
- RdrCEF.exe (PID: 3924)
- RdrCEF.exe (PID: 2480)
- AcroRd32.exe (PID: 3800)
- AcroRd32.exe (PID: 2912)
- RdrCEF.exe (PID: 3728)
- iexplore.exe (PID: 2020)
- iexplore.exe (PID: 1120)
- iexplore.exe (PID: 2644)
Application launched itself
- AcroRd32.exe (PID: 2100)
- RdrCEF.exe (PID: 2776)
- AcroRd32.exe (PID: 3800)
- iexplore.exe (PID: 1120)
Searches for installed software
- AcroRd32.exe (PID: 2100)
- AcroRd32.exe (PID: 120)
- AcroRd32.exe (PID: 3800)
Reads CPU info
- AcroRd32.exe (PID: 120)
- AcroRd32.exe (PID: 2912)
Reads the hosts file
- RdrCEF.exe (PID: 2776)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2088)
- AcroRd32.exe (PID: 120)
Reads settings of System Certificates
- AcroRd32.exe (PID: 2100)
- RdrCEF.exe (PID: 2776)
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 1120)
- iexplore.exe (PID: 2020)
Checks Windows Trust Settings
- AcroRd32.exe (PID: 2100)
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 1120)
- iexplore.exe (PID: 2020)
Changes internet zones settings
- iexplore.exe (PID: 1120)
Reads internet explorer settings
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2020)
Changes settings of System certificates
- iexplore.exe (PID: 1120)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1120)
Creates files in the user directory
- iexplore.exe (PID: 1120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 6) (100) |
|---|
Total processes
61
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
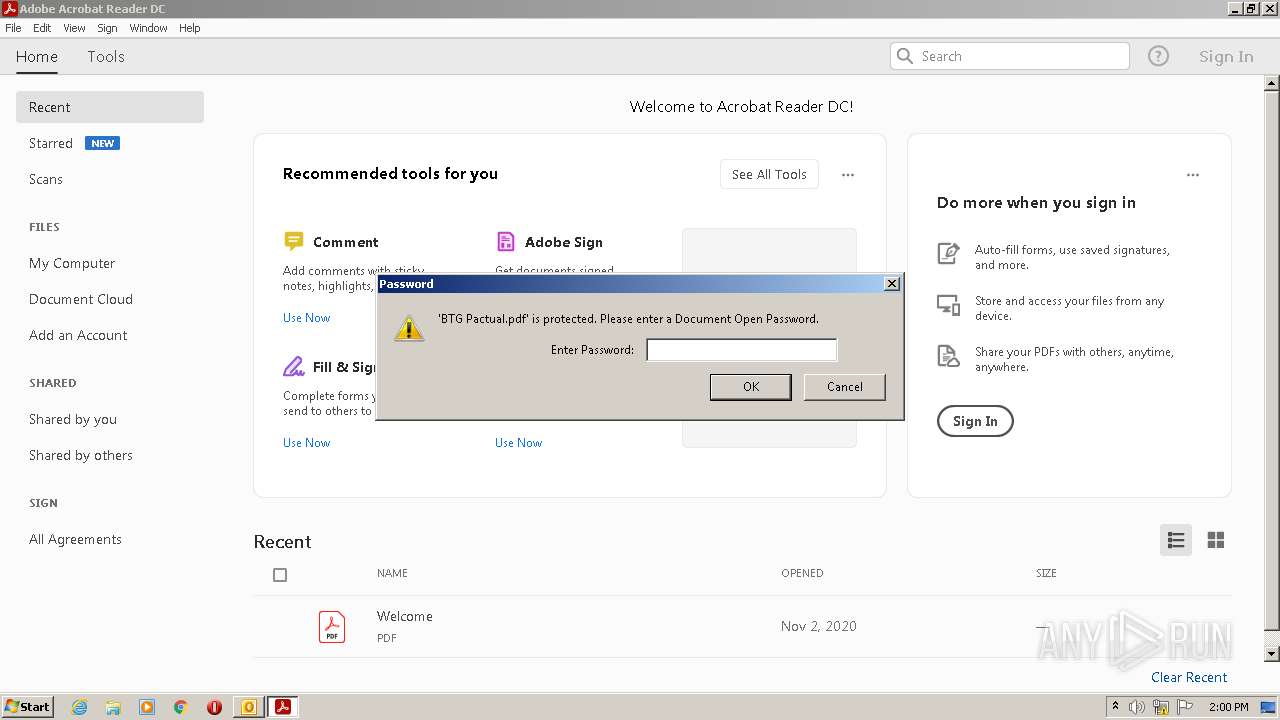
| 120 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\A12CKF3Q\BTG Pactual.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:20.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.39.9311 Modules
| |||||||||||||||
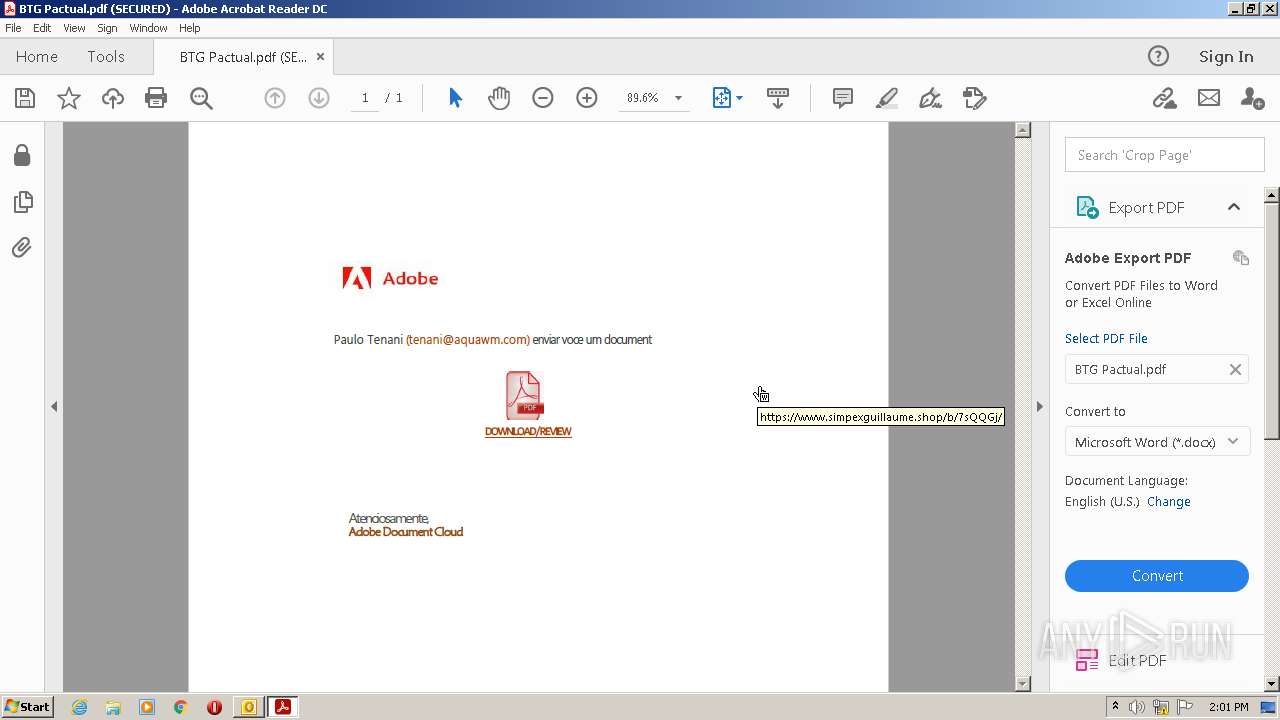
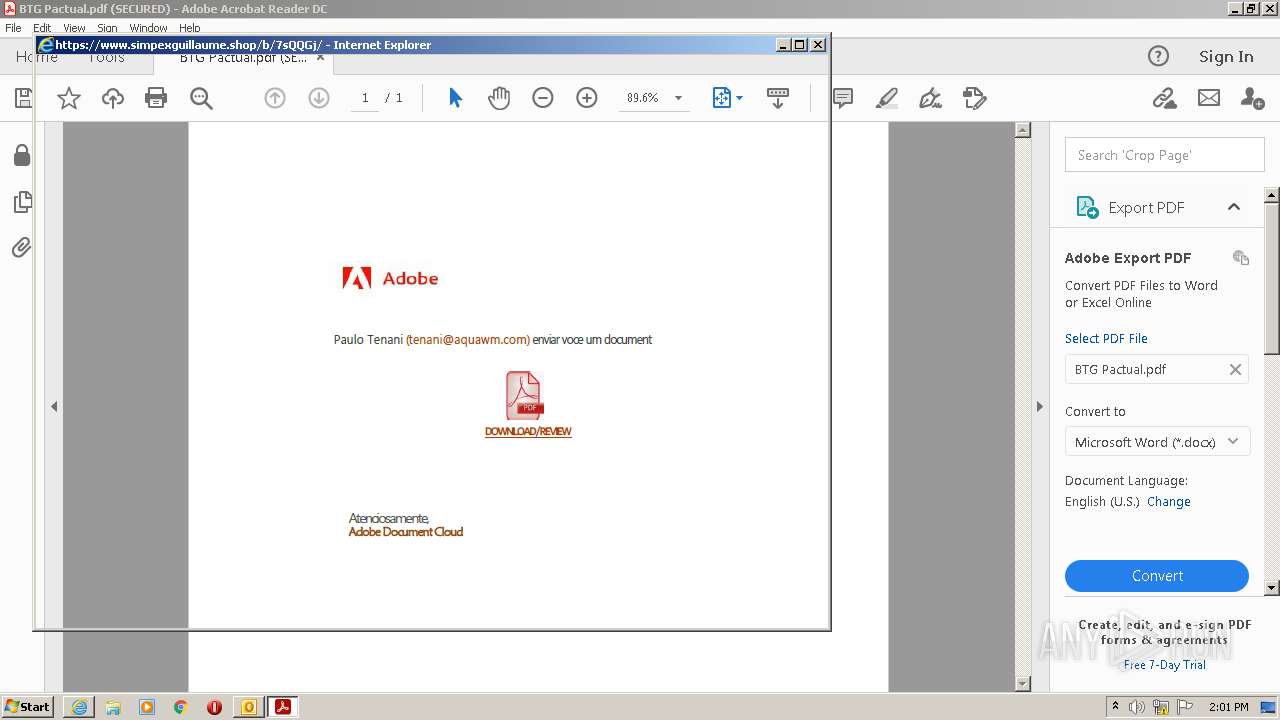
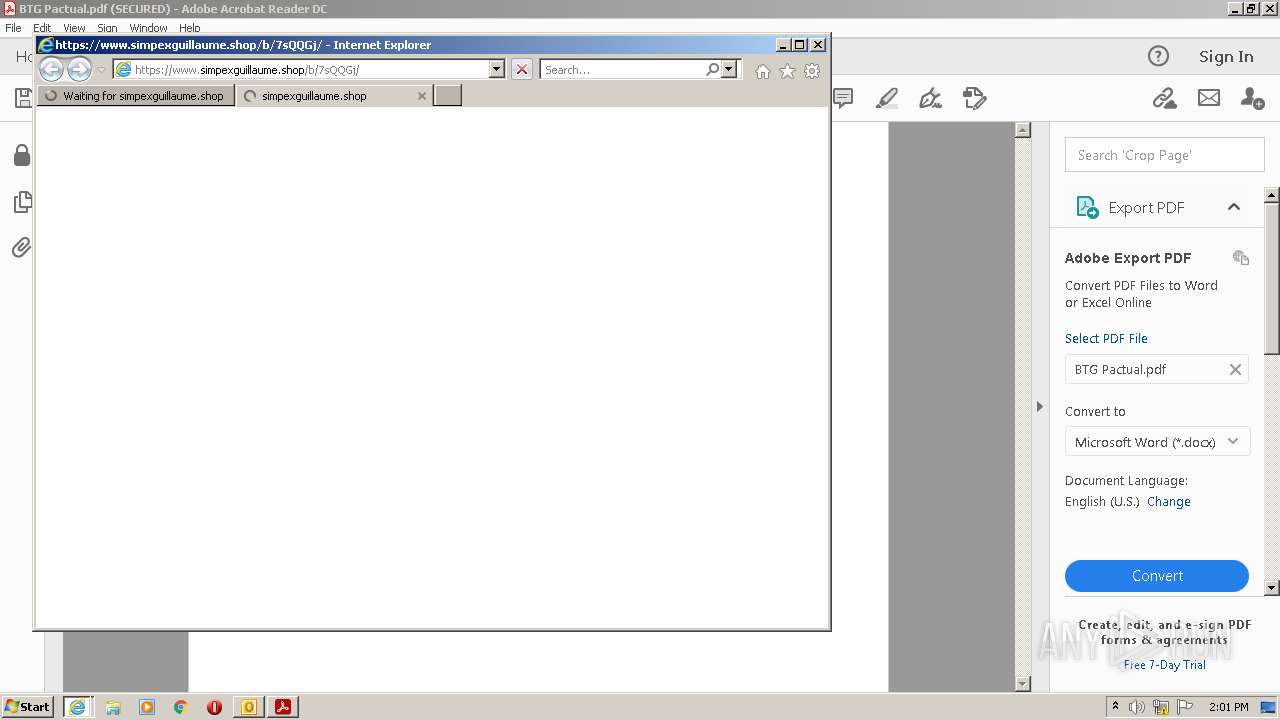
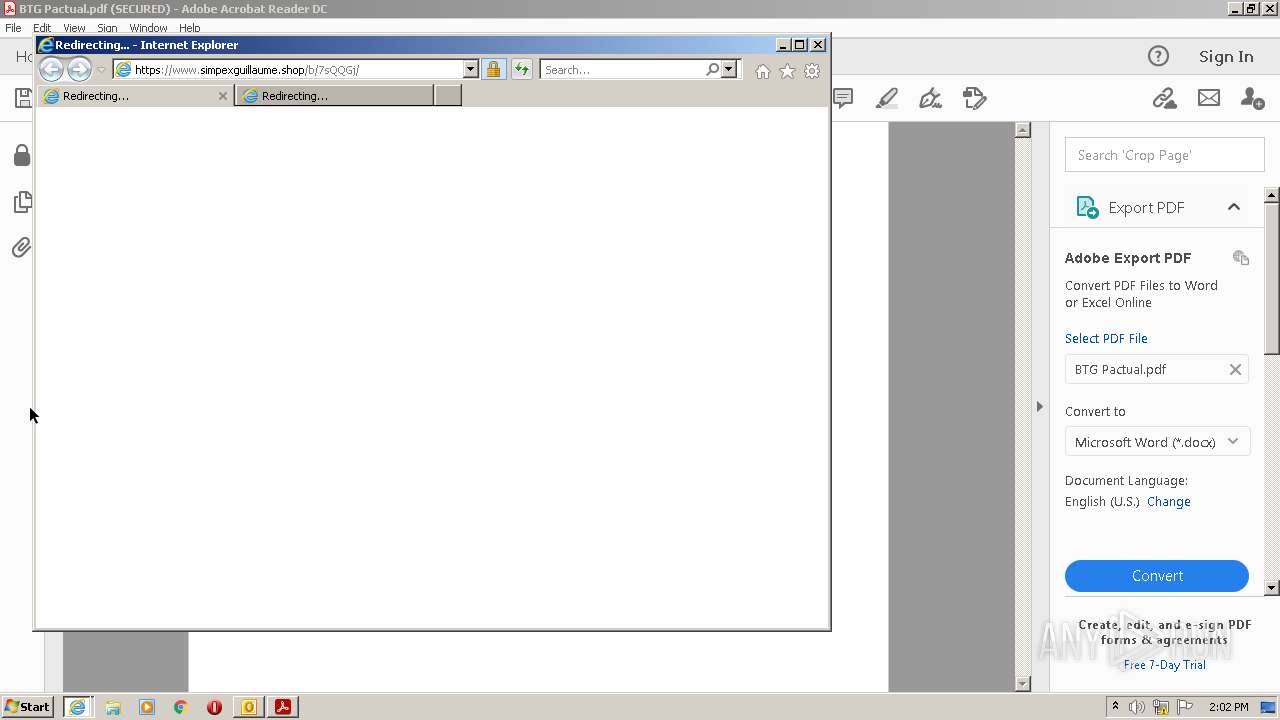
| 1120 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.simpexguillaume.shop/b/7sQQGj/ | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2020 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1120 CREDAT:202000 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2088 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Potential Phish (6).eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
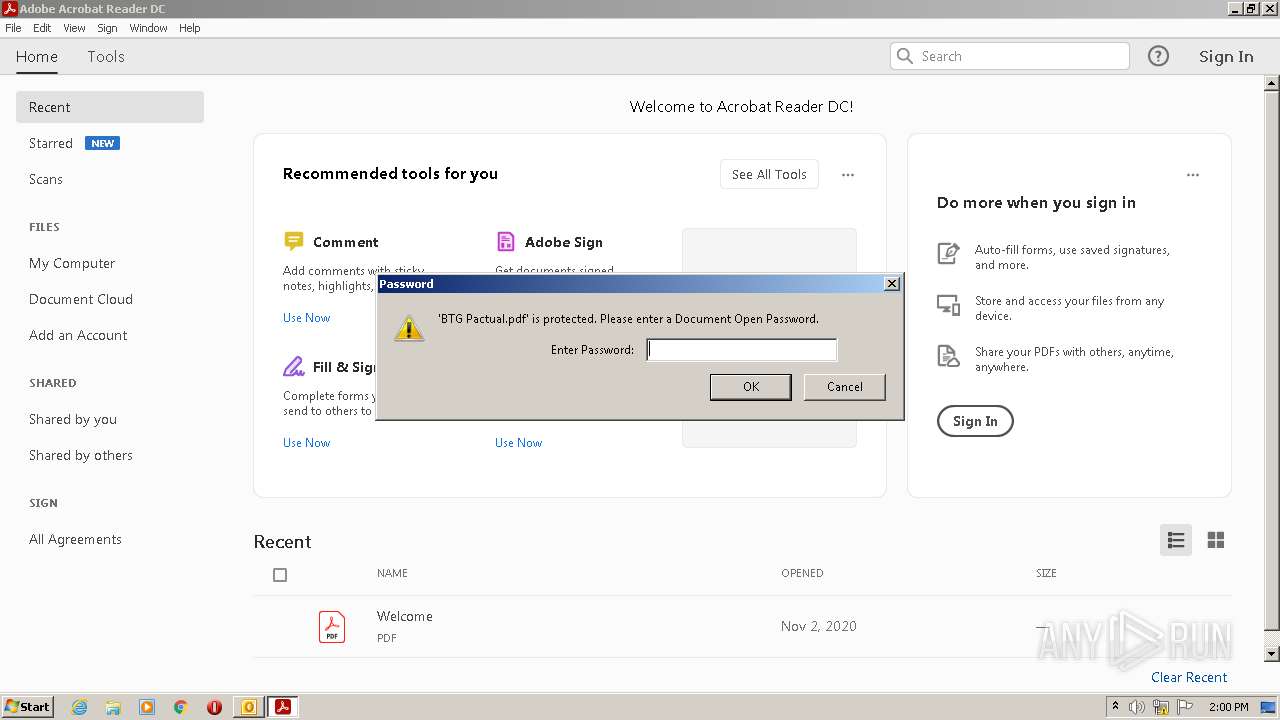
| 2100 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\A12CKF3Q\BTG Pactual.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1180,3266505897302262462,10252756254526176846,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=14455304448374236998 --mojo-platform-channel-handle=1444 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 20.12.20041.394260 Modules
| |||||||||||||||
| 2480 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1180,3266505897302262462,10252756254526176846,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5866178380471257374 --renderer-client-id=7 --mojo-platform-channel-handle=1676 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2568 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1180,3266505897302262462,10252756254526176846,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=1865109785757179203 --mojo-platform-channel-handle=1380 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
39 988
Read events
39 166
Write events
797
Delete events
25
Modification events
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2088) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
175
Text files
32
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9A91.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2088 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2088 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2088 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp9C09.tmp | binary | |
MD5:— | SHA256:— | |||
| 2088 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2088 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2088 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\A12CKF3Q\BTG Pactual (2).pdf | ||
MD5:— | SHA256:— | |||
| 2776 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
| 2088 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\A12CKF3Q\BTG Pactual.pdf | ||
MD5:— | SHA256:— | |||
| 2776 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
44
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1120 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2100 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
1120 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2644 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?95152217c76b6483 | US | compressed | 60.0 Kb | whitelisted |
2644 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6ba467927d98f4cb | US | compressed | 60.0 Kb | whitelisted |
2100 | AcroRd32.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1f1a8b7571c14ebb | US | compressed | 4.70 Kb | whitelisted |
2644 | iexplore.exe | GET | 200 | 104.89.32.83:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
2020 | iexplore.exe | GET | 200 | 23.55.163.58:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNyuL9CGnNi%2FwTkONpcOKdkfQ%3D%3D | US | der | 503 b | shared |
2644 | iexplore.exe | GET | 200 | 23.55.163.58:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNyuL9CGnNi%2FwTkONpcOKdkfQ%3D%3D | US | der | 503 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2776 | RdrCEF.exe | 104.90.104.172:443 | armmf.adobe.com | Akamai Technologies, Inc. | NL | suspicious |
2776 | RdrCEF.exe | 104.102.28.179:443 | geo2.adobe.com | Akamai Technologies, Inc. | US | unknown |
2100 | AcroRd32.exe | 92.123.194.153:443 | acroipm2.adobe.com | Akamai International B.V. | — | suspicious |
2100 | AcroRd32.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
— | — | 104.90.104.172:443 | armmf.adobe.com | Akamai Technologies, Inc. | NL | suspicious |
2644 | iexplore.exe | 190.123.44.137:443 | www.simpexguillaume.shop | Panamaserver.com | PA | malicious |
2644 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
1120 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2020 | iexplore.exe | 190.123.44.137:443 | www.simpexguillaume.shop | Panamaserver.com | PA | malicious |
2088 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
config.messenger.msn.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.simpexguillaume.shop |
| suspicious |
api.bing.com |
| whitelisted |