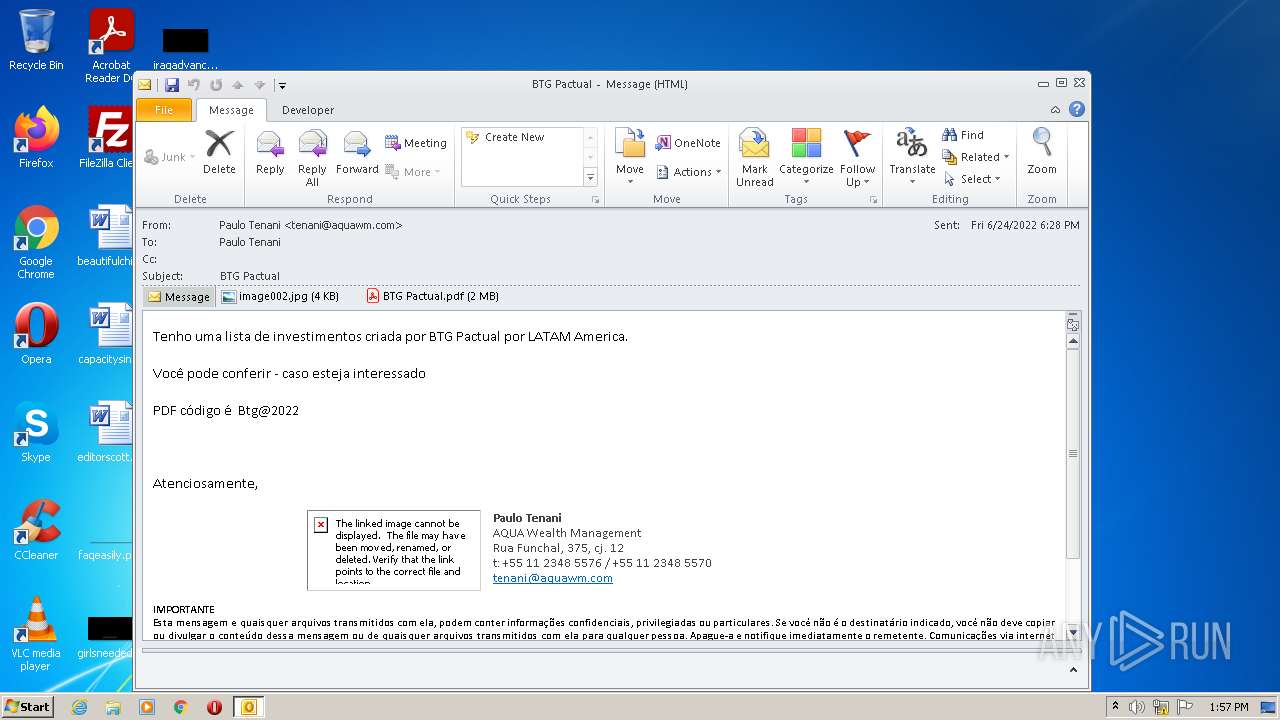
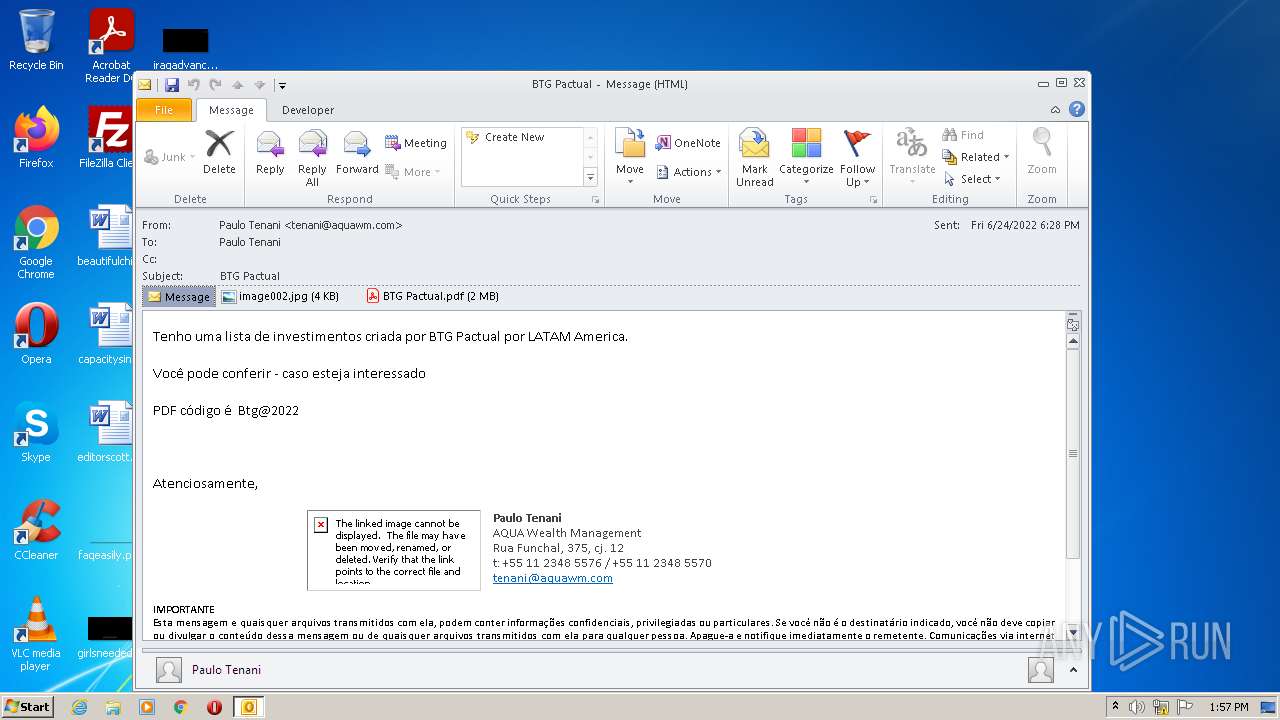
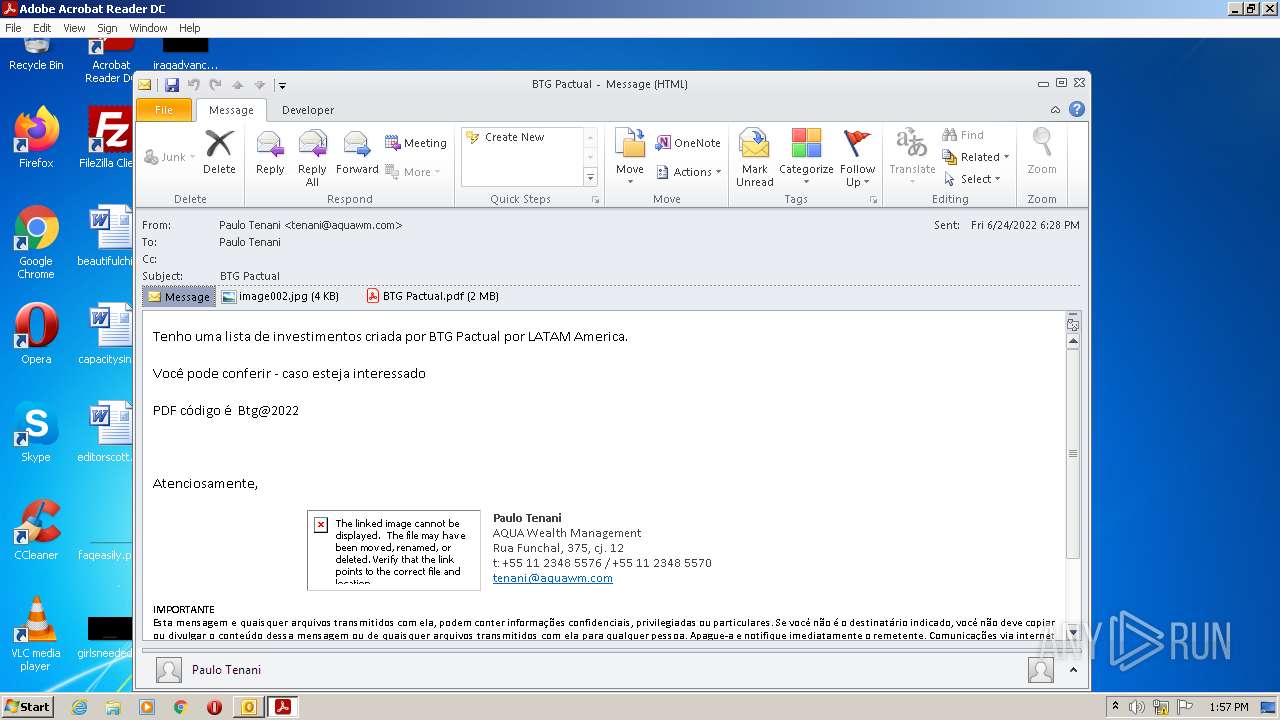
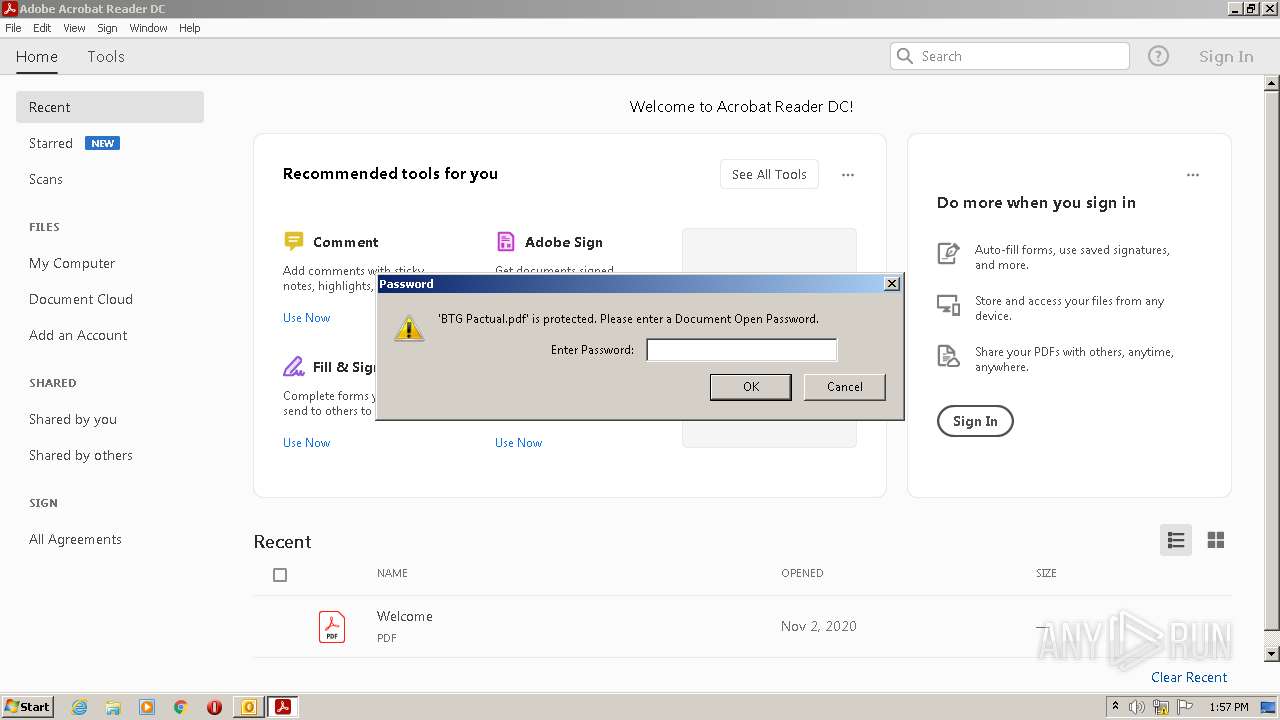
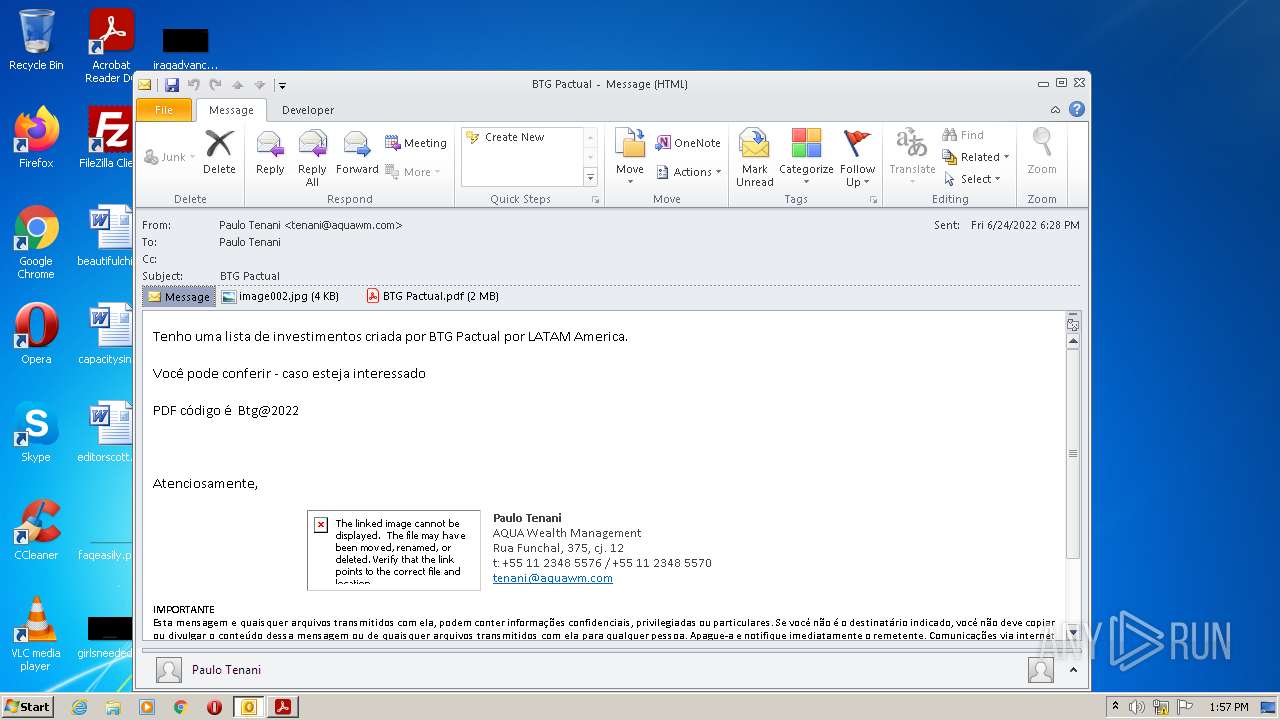
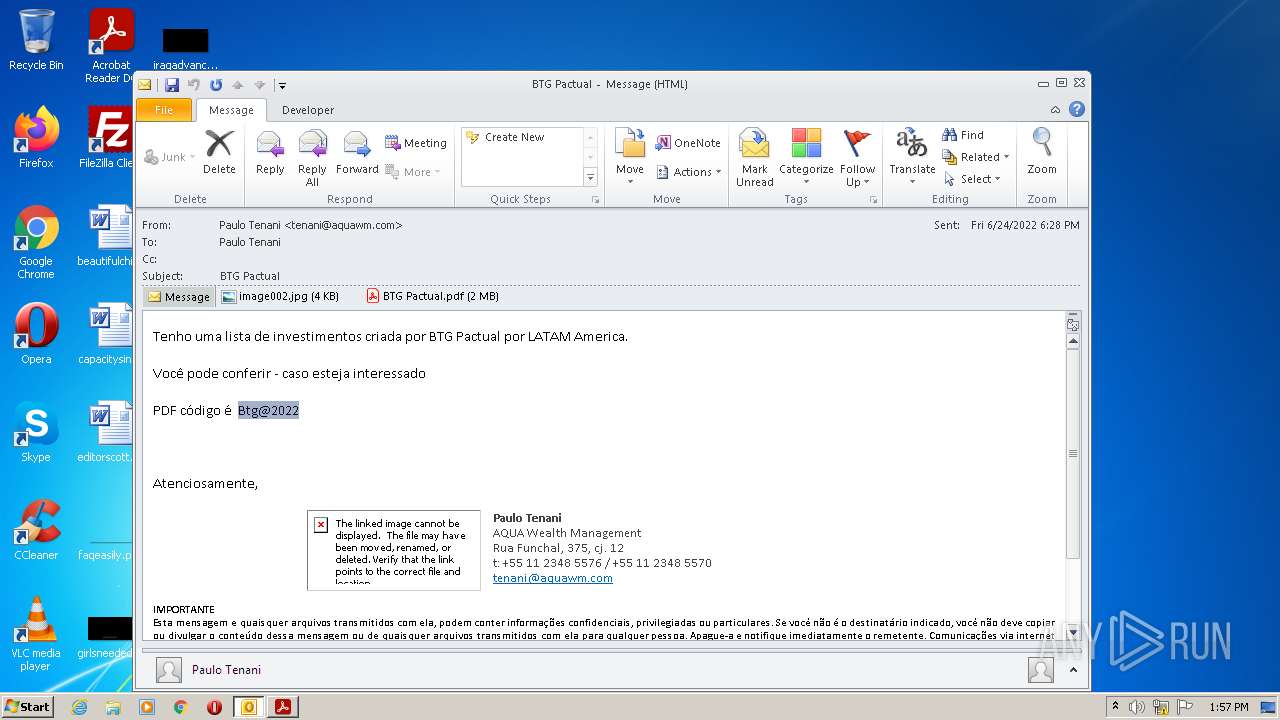
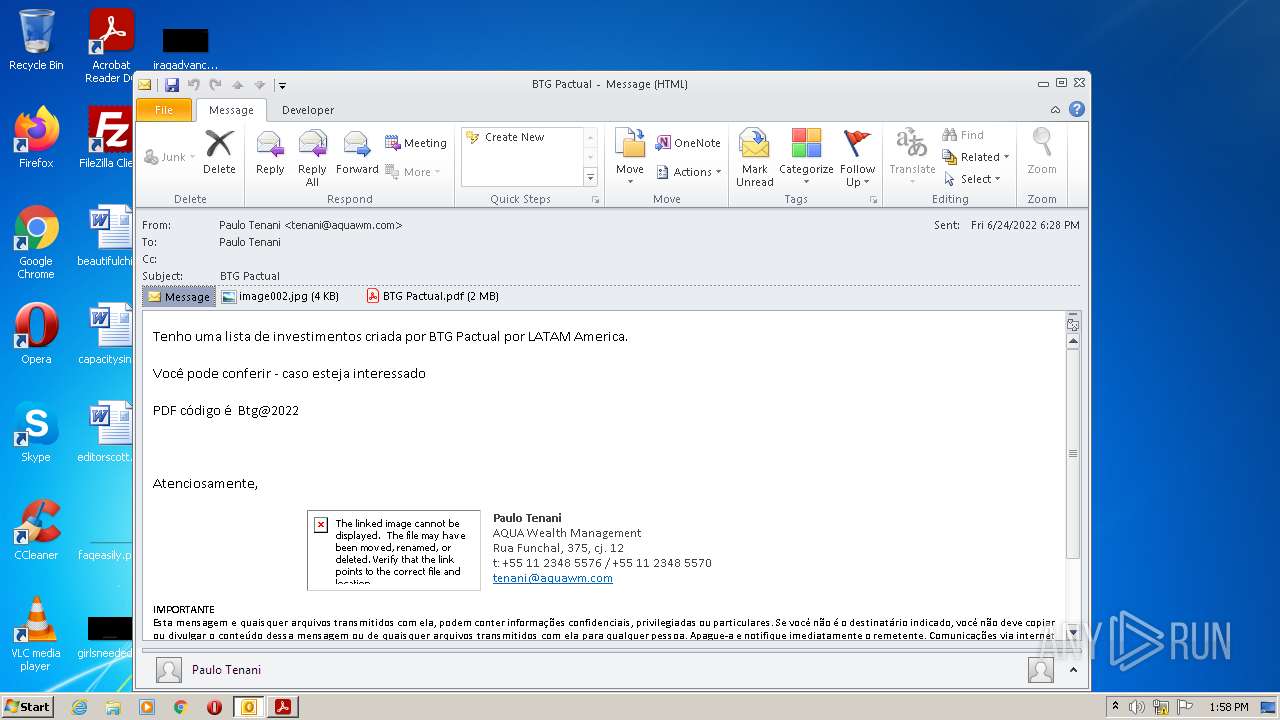
| File name: | Potential Phish (6).eml |
| Full analysis: | https://app.any.run/tasks/477d472e-9322-47a3-9177-115882a2c7ec |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 12:57:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | multipart/mixed; boundary="===============1170810377320412942==", ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 10ADF8A9DB4CCE0AC1F6FE420A0158A5 |
| SHA1: | 78C5BC0C27661CF20637280164EBDCCFE51CD4E4 |
| SHA256: | C02B571A53CD0D3F5E8D795BCF65DE2E516AEB4F26589FD7A55291D42F633163 |
| SSDEEP: | 49152:cdqNK2lPSbmDKTL8JkCkSLsSZAnb5ckoMpuRXR:n |
MALICIOUS
Drops executable file immediately after starts
- RdrCEF.exe (PID: 2124)
SUSPICIOUS
Reads the computer name
- OUTLOOK.EXE (PID: 2548)
- AdobeARM.exe (PID: 3012)
Checks supported languages
- OUTLOOK.EXE (PID: 2548)
- Reader_sl.exe (PID: 3036)
- AdobeARM.exe (PID: 3012)
Searches for installed software
- OUTLOOK.EXE (PID: 2548)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2548)
Starts Internet Explorer
- AcroRd32.exe (PID: 3572)
Drops a file with a compile date too recent
- RdrCEF.exe (PID: 2124)
INFO
Checks supported languages
- AcroRd32.exe (PID: 3572)
- AcroRd32.exe (PID: 1744)
- RdrCEF.exe (PID: 2124)
- RdrCEF.exe (PID: 1132)
- RdrCEF.exe (PID: 988)
- RdrCEF.exe (PID: 3308)
- RdrCEF.exe (PID: 3052)
- RdrCEF.exe (PID: 2120)
- RdrCEF.exe (PID: 4028)
- iexplore.exe (PID: 3284)
- AcroRd32.exe (PID: 1584)
- AcroRd32.exe (PID: 908)
- RdrCEF.exe (PID: 124)
Reads the computer name
- AcroRd32.exe (PID: 3572)
- AcroRd32.exe (PID: 1744)
- RdrCEF.exe (PID: 2124)
- AcroRd32.exe (PID: 1584)
- AcroRd32.exe (PID: 908)
- iexplore.exe (PID: 3284)
Application launched itself
- AcroRd32.exe (PID: 3572)
- RdrCEF.exe (PID: 2124)
- iexplore.exe (PID: 3284)
- AcroRd32.exe (PID: 908)
Searches for installed software
- AcroRd32.exe (PID: 3572)
- AcroRd32.exe (PID: 908)
- AcroRd32.exe (PID: 1744)
Reads CPU info
- AcroRd32.exe (PID: 1744)
- AcroRd32.exe (PID: 1584)
Reads the hosts file
- RdrCEF.exe (PID: 2124)
Reads settings of System Certificates
- AcroRd32.exe (PID: 3572)
- RdrCEF.exe (PID: 2124)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2548)
- AcroRd32.exe (PID: 1744)
Checks Windows Trust Settings
- AcroRd32.exe (PID: 3572)
Changes internet zones settings
- iexplore.exe (PID: 3284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 6) (100) |
|---|
Total processes
56
Monitored processes
17
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1180,3642734004160377188,16354372603882291562,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9820379326013958088 --renderer-client-id=7 --mojo-platform-channel-handle=1648 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
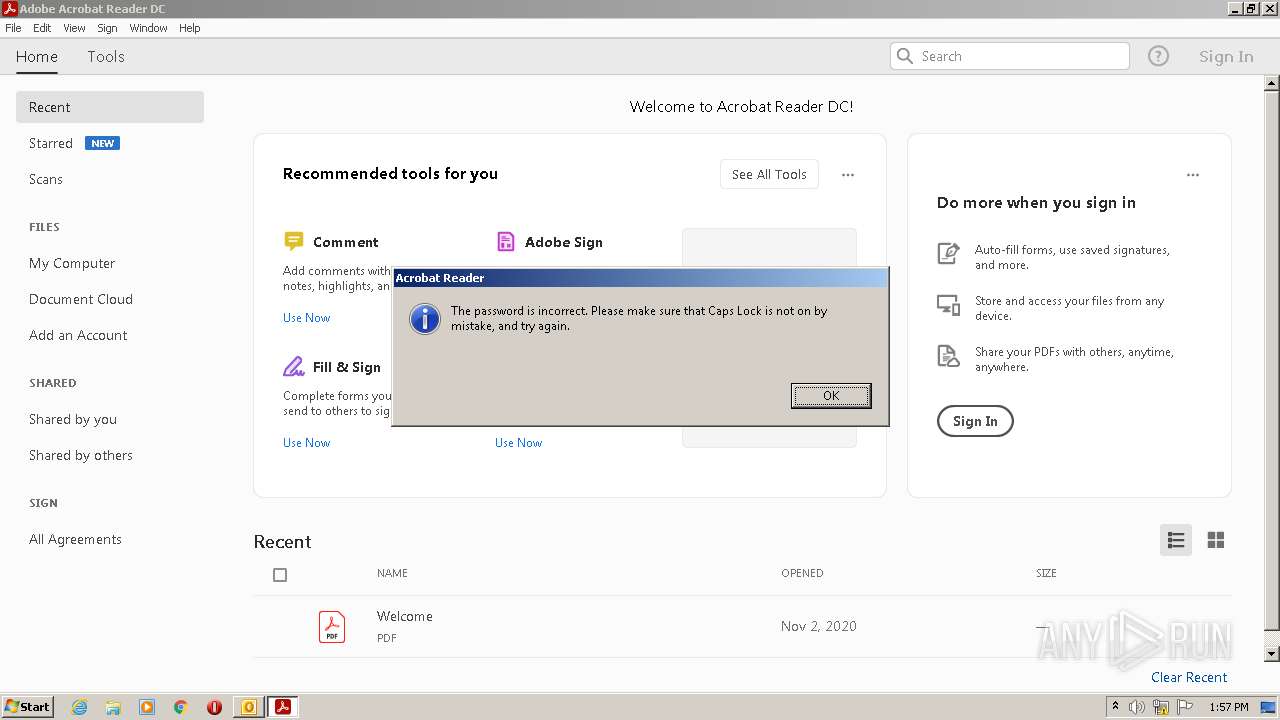
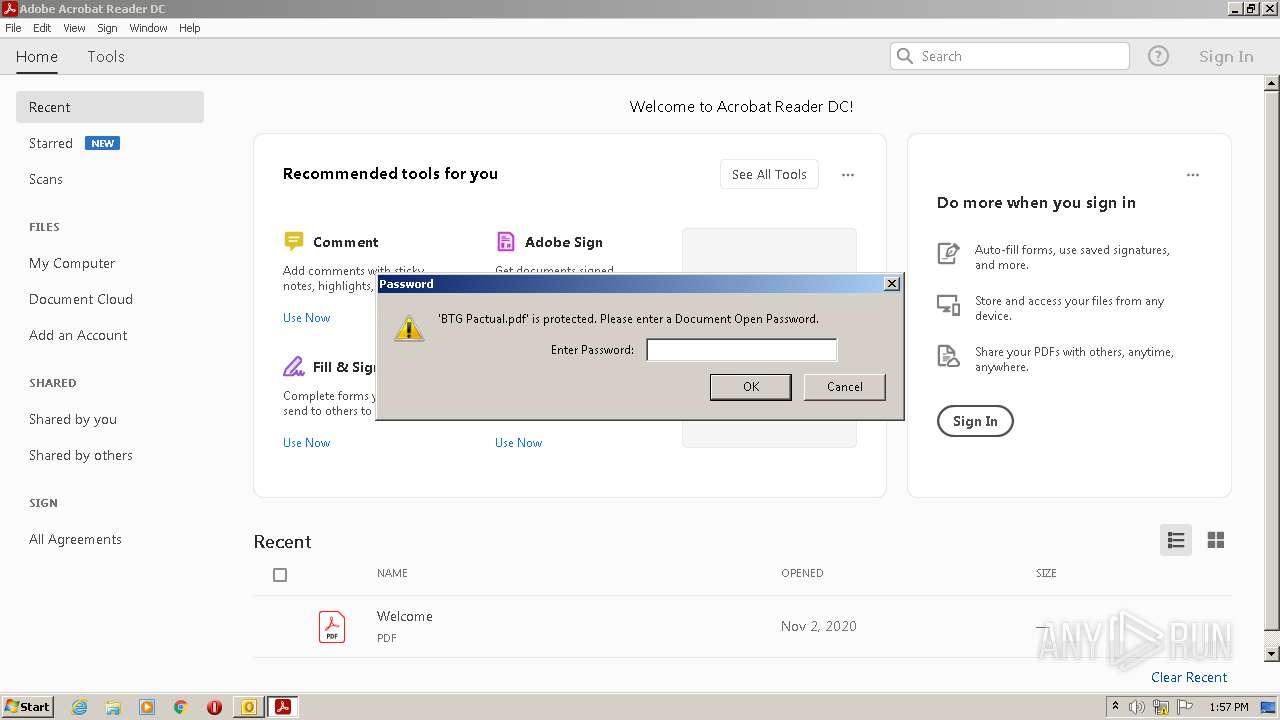
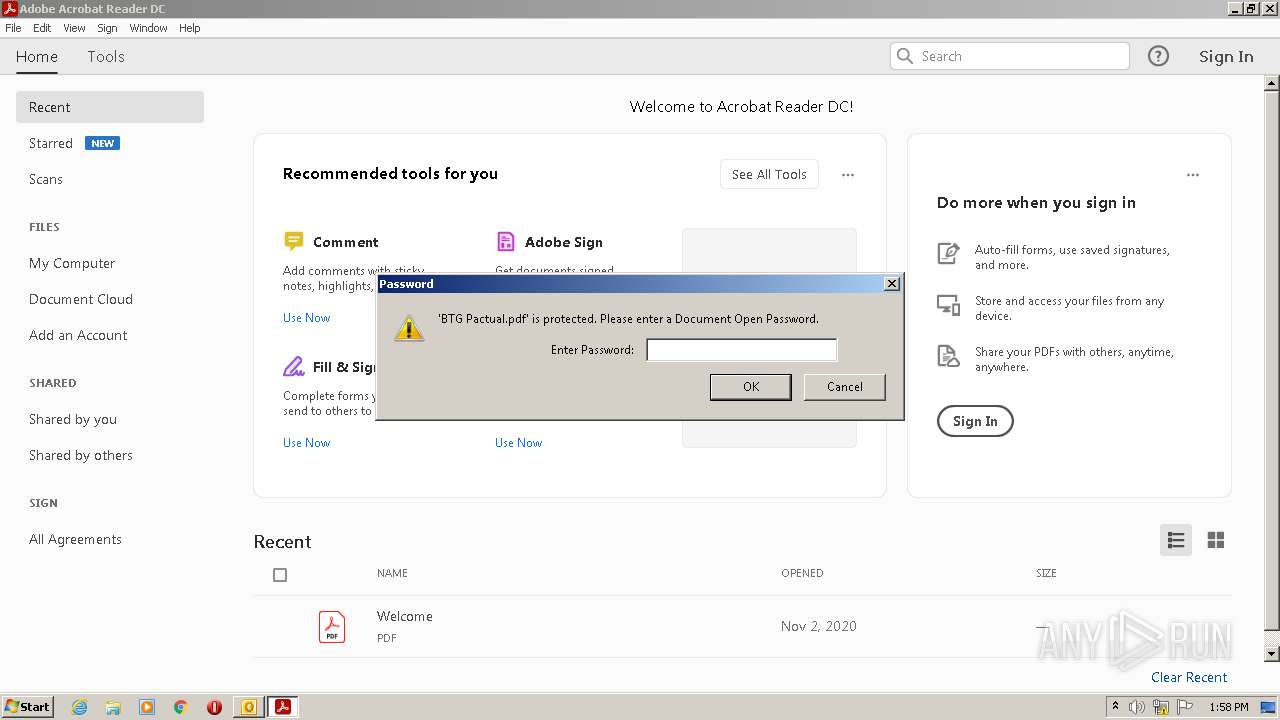
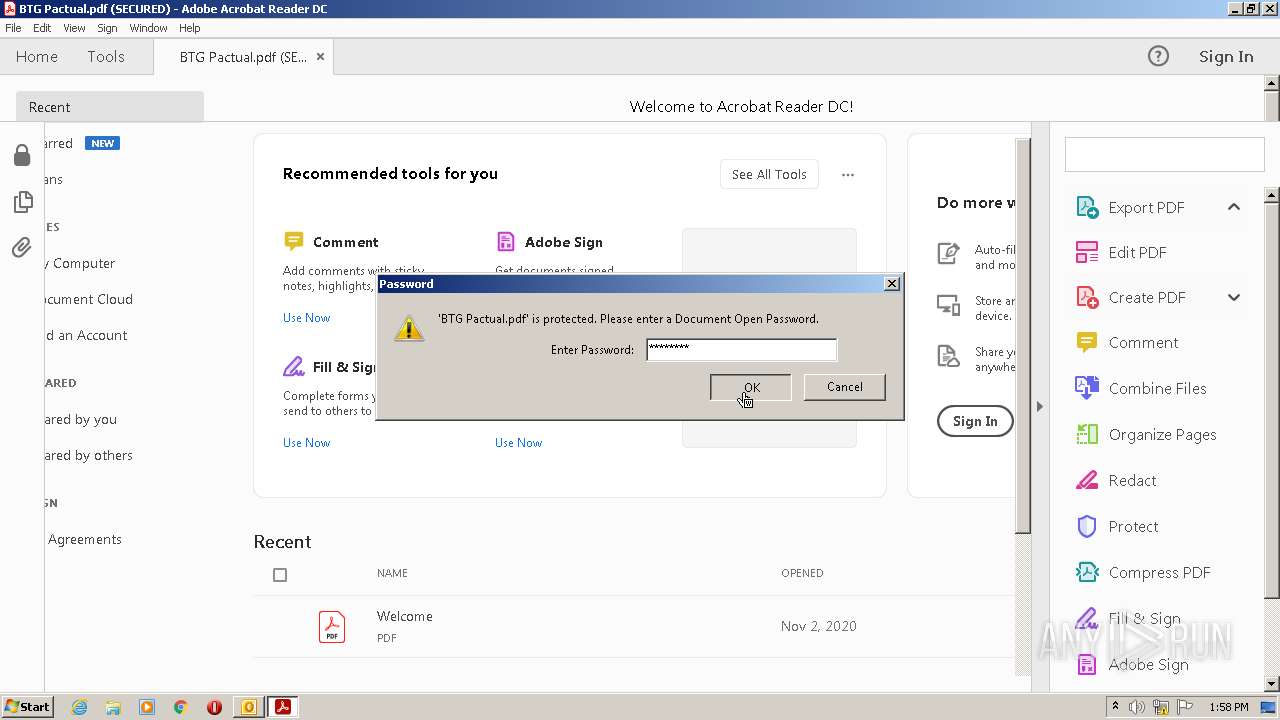
| 908 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\A7RO3479\BTG Pactual.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 988 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1180,3642734004160377188,16354372603882291562,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1324632808604041752 --renderer-client-id=2 --mojo-platform-channel-handle=1188 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1180,3642734004160377188,16354372603882291562,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=13362219631397461212 --mojo-platform-channel-handle=1216 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\A7RO3479\BTG Pactual.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\A7RO3479\BTG Pactual.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1180,3642734004160377188,16354372603882291562,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=4070697000390757668 --mojo-platform-channel-handle=1456 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3284 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2548 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Potential Phish (6).eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
20 379
Read events
19 665
Write events
692
Delete events
22
Modification events
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2548) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
162
Text files
16
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR642F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2548 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2548 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_7A0376D5E8E713409A8975AE18231867.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 2548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_43512E8072DE9D409EF36A8E242DBD6D.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 2548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp65A7.tmp | binary | |
MD5:— | SHA256:— | |||
| 2124 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:— | SHA256:— | |||
| 2124 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
| 2124 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2548 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3572 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3572 | AcroRd32.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?587b7615ea606136 | US | compressed | 4.70 Kb | whitelisted |
3572 | AcroRd32.exe | GET | 304 | 92.123.225.41:80 | http://acroipm2.adobe.com/20/rdr/ENU/win/nooem/none/consumer/279_20_13_20064.zip | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2548 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2124 | RdrCEF.exe | 104.102.28.179:443 | geo2.adobe.com | Akamai Technologies, Inc. | US | unknown |
— | — | 104.102.28.179:443 | geo2.adobe.com | Akamai Technologies, Inc. | US | unknown |
2124 | RdrCEF.exe | 23.22.254.206:443 | p13n.adobe.io | Amazon.com, Inc. | US | suspicious |
3572 | AcroRd32.exe | 92.123.225.41:443 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
2124 | RdrCEF.exe | 104.90.104.172:443 | armmf.adobe.com | Akamai Technologies, Inc. | NL | suspicious |
3572 | AcroRd32.exe | 8.248.149.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3572 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
3572 | AcroRd32.exe | 92.123.225.41:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
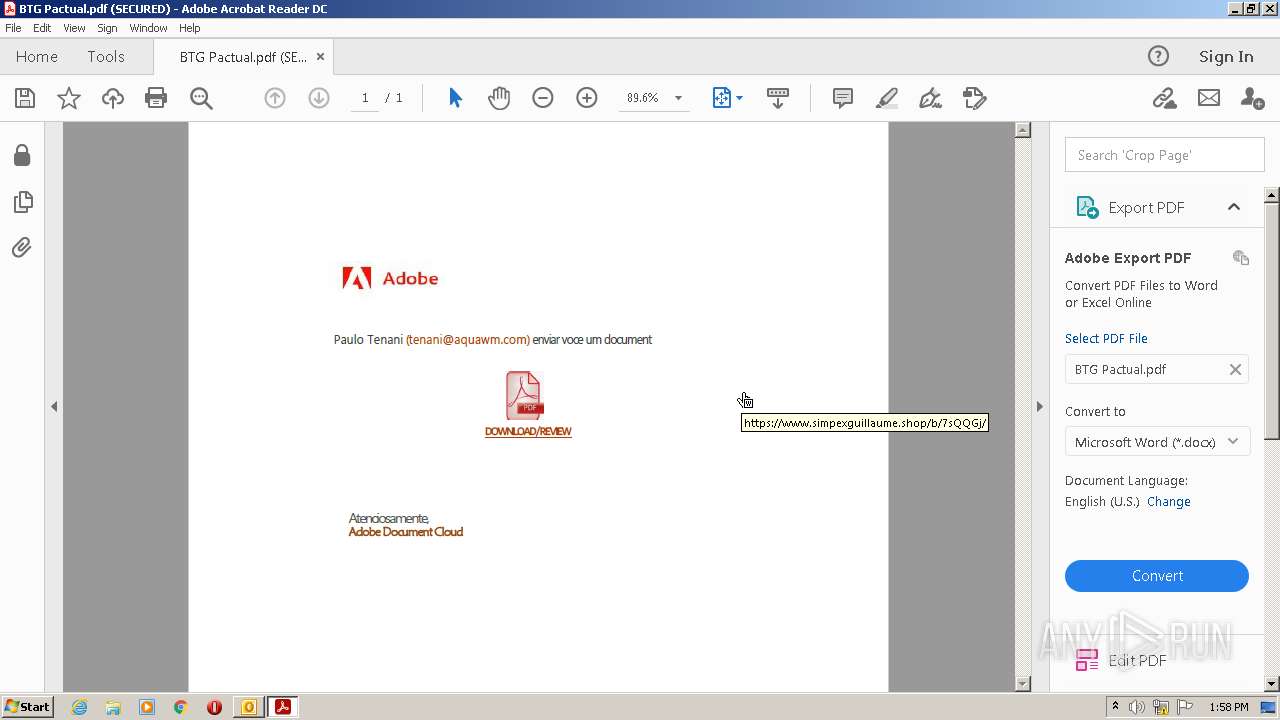
www.simpexguillaume.shop |
| suspicious |