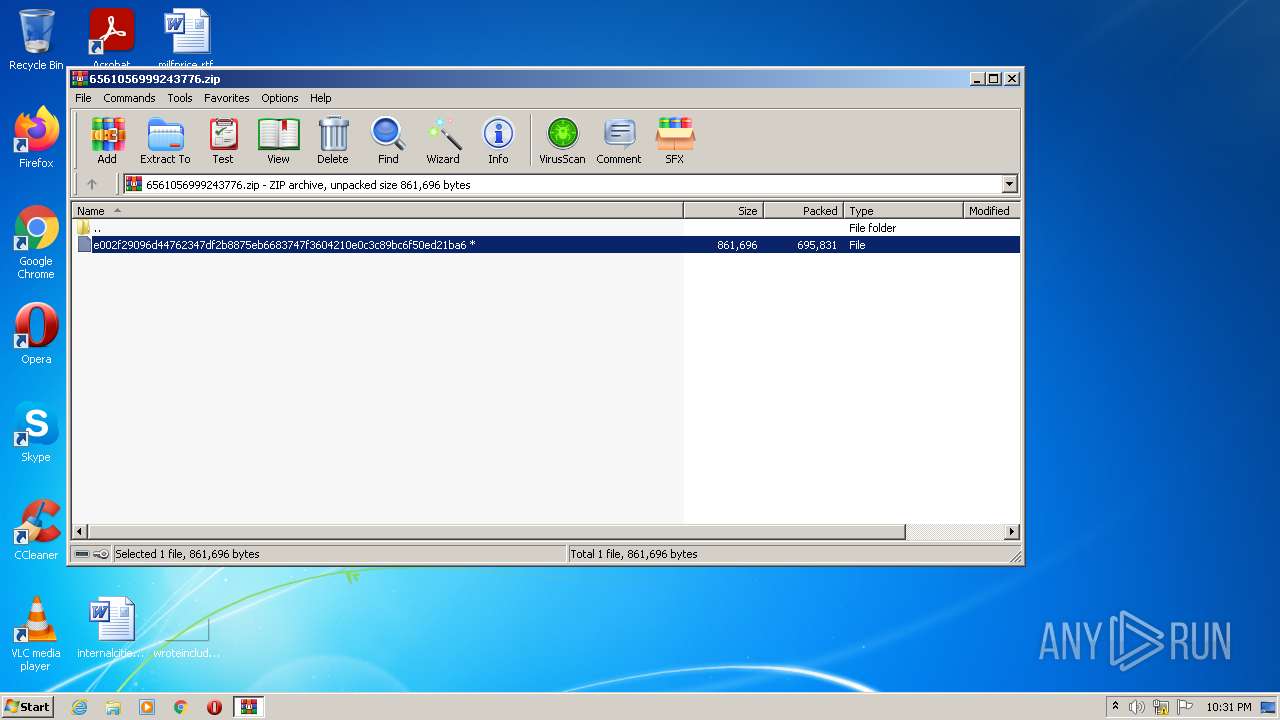
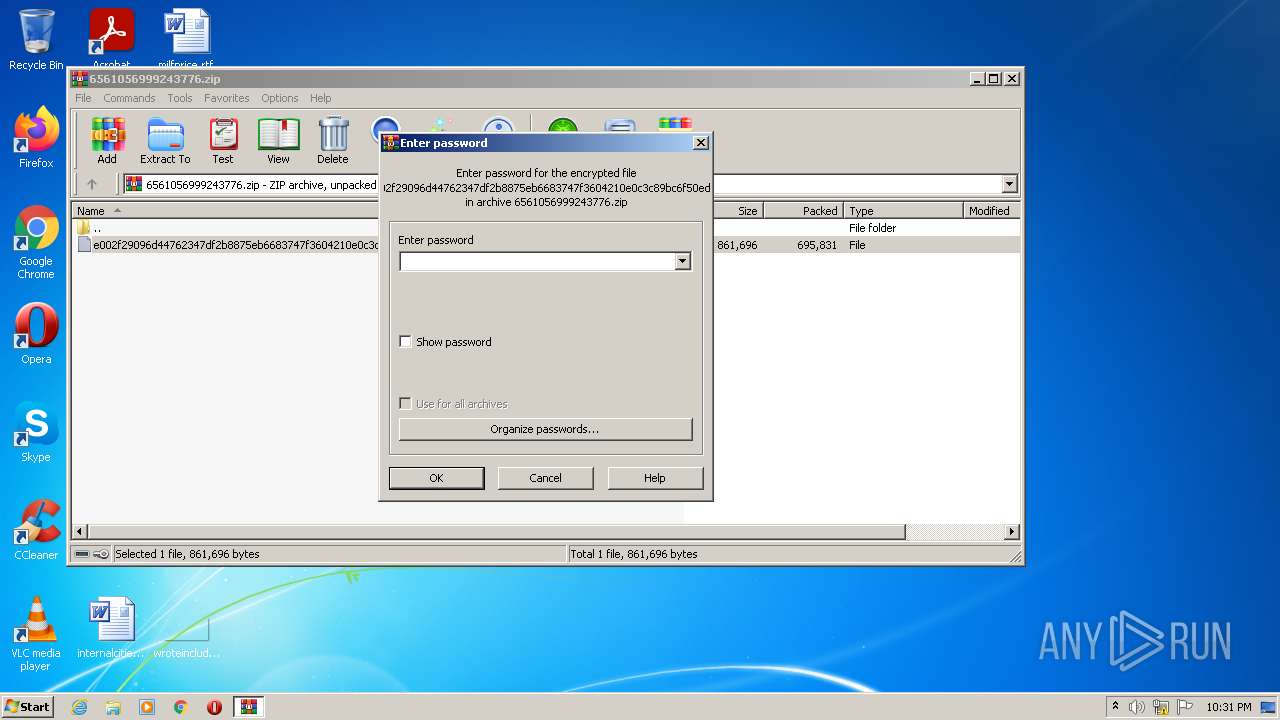
| File name: | 6561056999243776.zip |
| Full analysis: | https://app.any.run/tasks/ac086976-7dff-48bc-8d73-0588474e2fb0 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 22:30:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B6EEEDB52C8B64799C50CDBD39C79C2F |
| SHA1: | C21F6A1A65375D27B74415B286D2F88F63411FC2 |
| SHA256: | C0217DB96F90E98F6A9522FB5CE578C3B6EBD0EB6B2C80A3B89CFD3AC2B37051 |
| SSDEEP: | 12288:tGg6VhQO0sag3UIKEsZbwBomYoVbgM/sDc5TZmlxC+bsKX4RobFbkX3UQImngVv:8Thx0sag3knKO+zU6TUG8XJJ0kbmgVv |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3980)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3980)
Reads the computer name
- WinRAR.exe (PID: 3980)
- WORDPAD.EXE (PID: 1660)
Checks supported languages
- WinRAR.exe (PID: 3980)
- WORDPAD.EXE (PID: 1660)
Reads the date of Windows installation
- rundll32.exe (PID: 2544)
- rundll32.exe (PID: 3624)
Starts Internet Explorer
- rundll32.exe (PID: 3624)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3980)
- iexplore.exe (PID: 2132)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1800)
INFO
Checks supported languages
- rundll32.exe (PID: 2544)
- iexplore.exe (PID: 2132)
- rundll32.exe (PID: 3624)
- iexplore.exe (PID: 1800)
- rundll32.exe (PID: 1852)
Reads the computer name
- rundll32.exe (PID: 3624)
- rundll32.exe (PID: 2544)
- iexplore.exe (PID: 2132)
- iexplore.exe (PID: 1800)
- rundll32.exe (PID: 1852)
Changes internet zones settings
- iexplore.exe (PID: 2132)
Application launched itself
- iexplore.exe (PID: 2132)
Reads the date of Windows installation
- iexplore.exe (PID: 2132)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2132)
Checks Windows Trust Settings
- iexplore.exe (PID: 2132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | e002f29096d44762347df2b8875eb6683747f3604210e0c3c89bc6f50ed21ba6 |
|---|---|
| ZipUncompressedSize: | 861696 |
| ZipCompressedSize: | 695831 |
| ZipCRC: | 0x20bdac55 |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
40
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
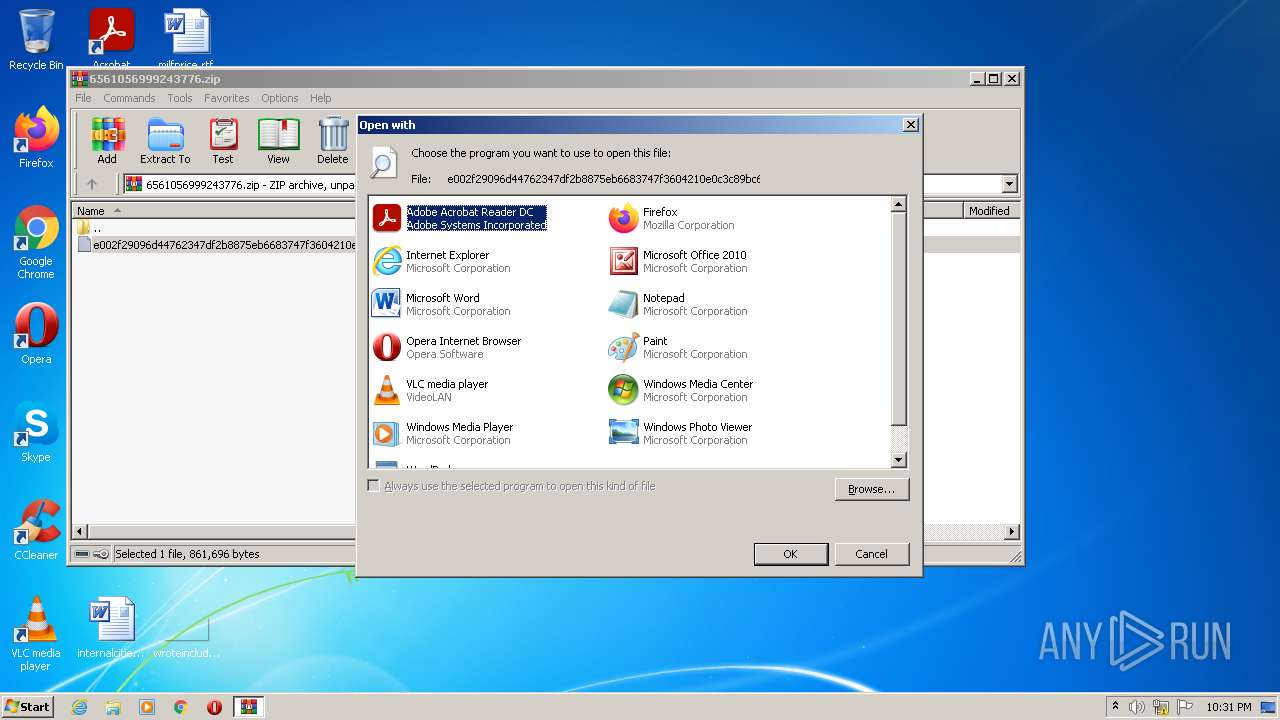
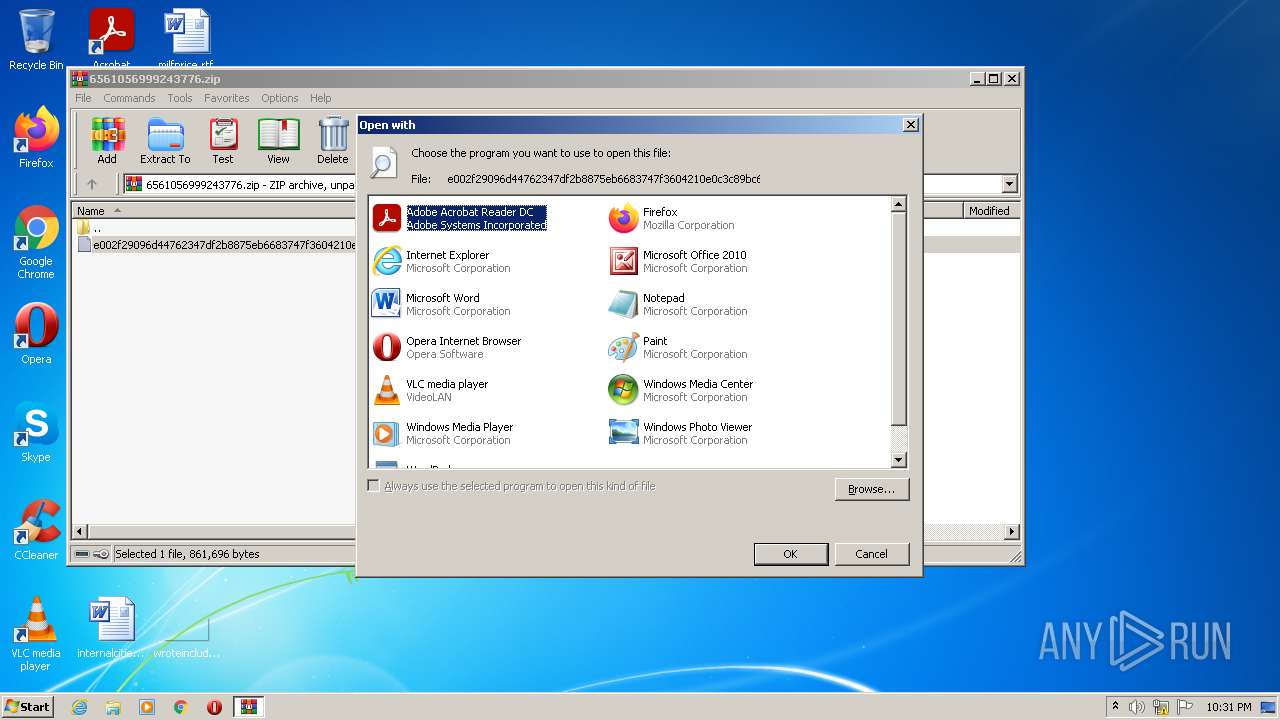
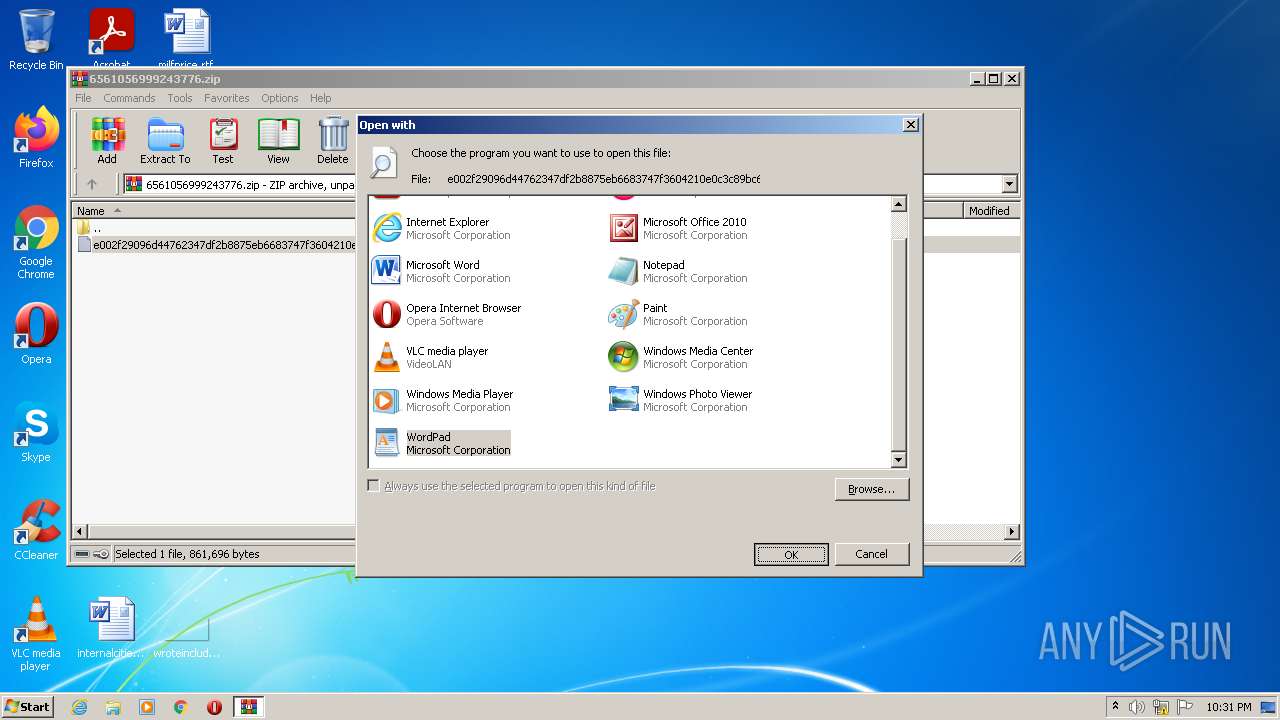
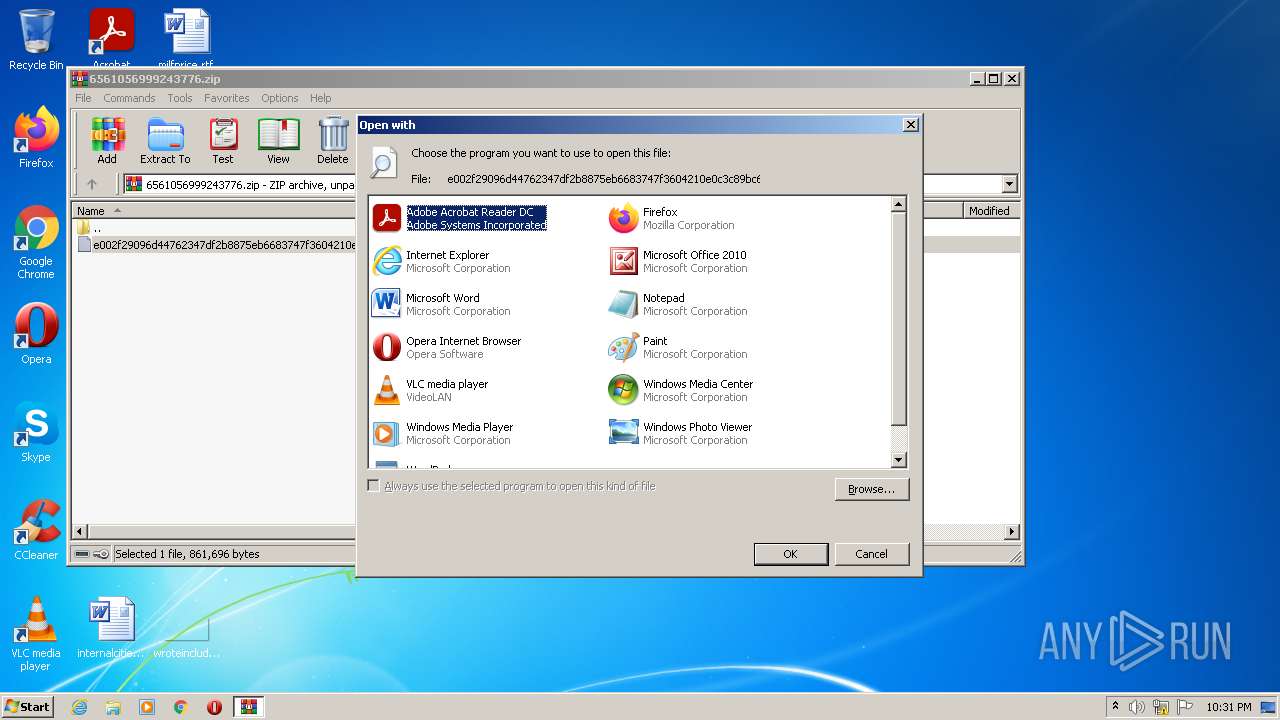
| 1660 | "C:\Program Files\Windows NT\Accessories\WORDPAD.EXE" "C:\Users\admin\AppData\Local\Temp\Rar$DIb3980.12388\e002f29096d44762347df2b8875eb6683747f3604210e0c3c89bc6f50ed21ba6" | C:\Program Files\Windows NT\Accessories\WORDPAD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Wordpad Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
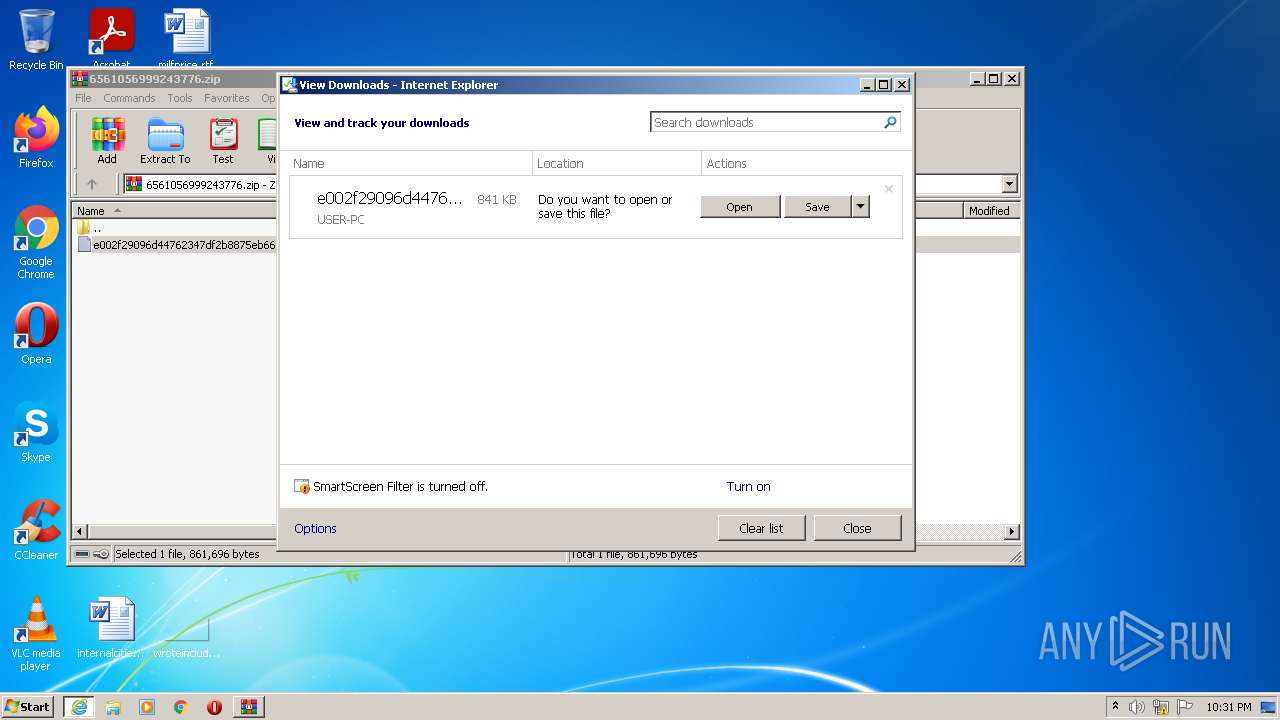
| 1800 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2132 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1852 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb3980.14724\e002f29096d44762347df2b8875eb6683747f3604210e0c3c89bc6f50ed21ba6 | C:\Windows\system32\rundll32.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb3980.14724\e002f29096d44762347df2b8875eb6683747f3604210e0c3c89bc6f50ed21ba6 | C:\Program Files\Internet Explorer\iexplore.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2544 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb3980.12388\e002f29096d44762347df2b8875eb6683747f3604210e0c3c89bc6f50ed21ba6 | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3624 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb3980.14724\e002f29096d44762347df2b8875eb6683747f3604210e0c3c89bc6f50ed21ba6 | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\6561056999243776.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 267
Read events
6 029
Write events
237
Delete events
1
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\6561056999243776.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
1
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2132 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{686FD093-7D65-11EC-A20C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2132 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA07755356248BFD0.TMP | gmc | |
MD5:— | SHA256:— | |||
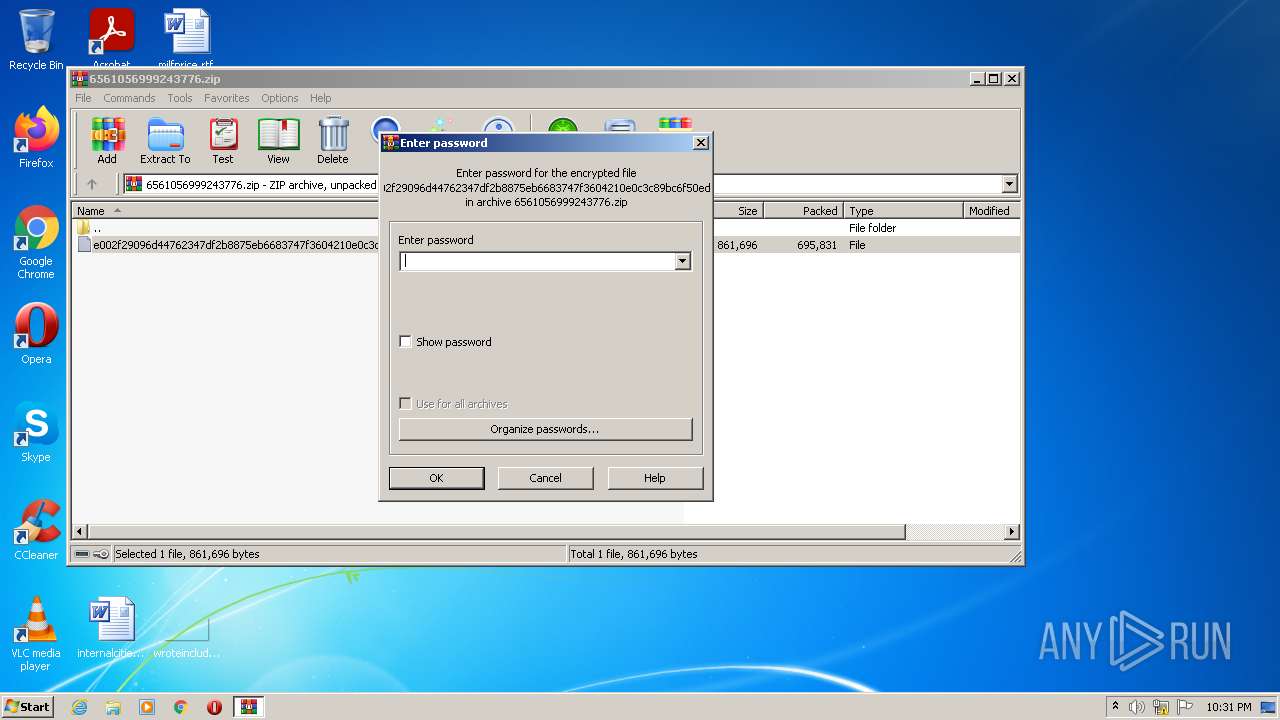
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3980.14724\e002f29096d44762347df2b8875eb6683747f3604210e0c3c89bc6f50ed21ba6 | executable | |
MD5:— | SHA256:— | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3980.12388\e002f29096d44762347df2b8875eb6683747f3604210e0c3c89bc6f50ed21ba6 | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report