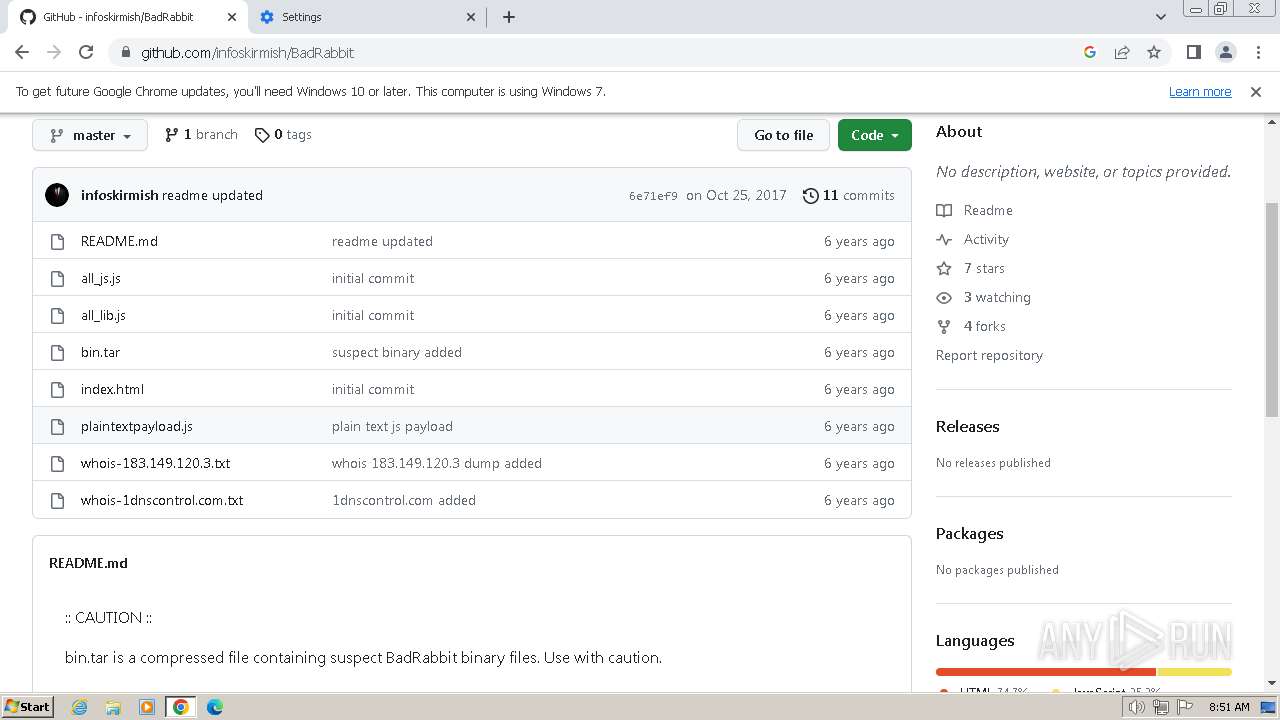
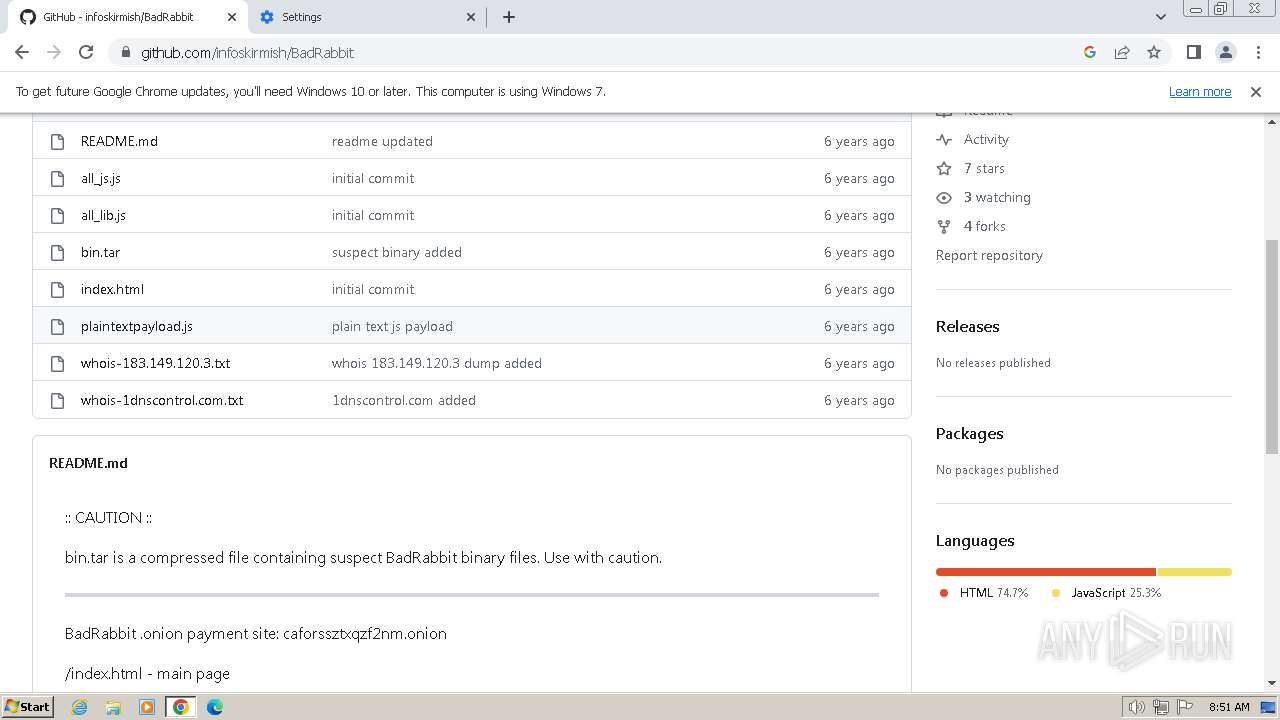
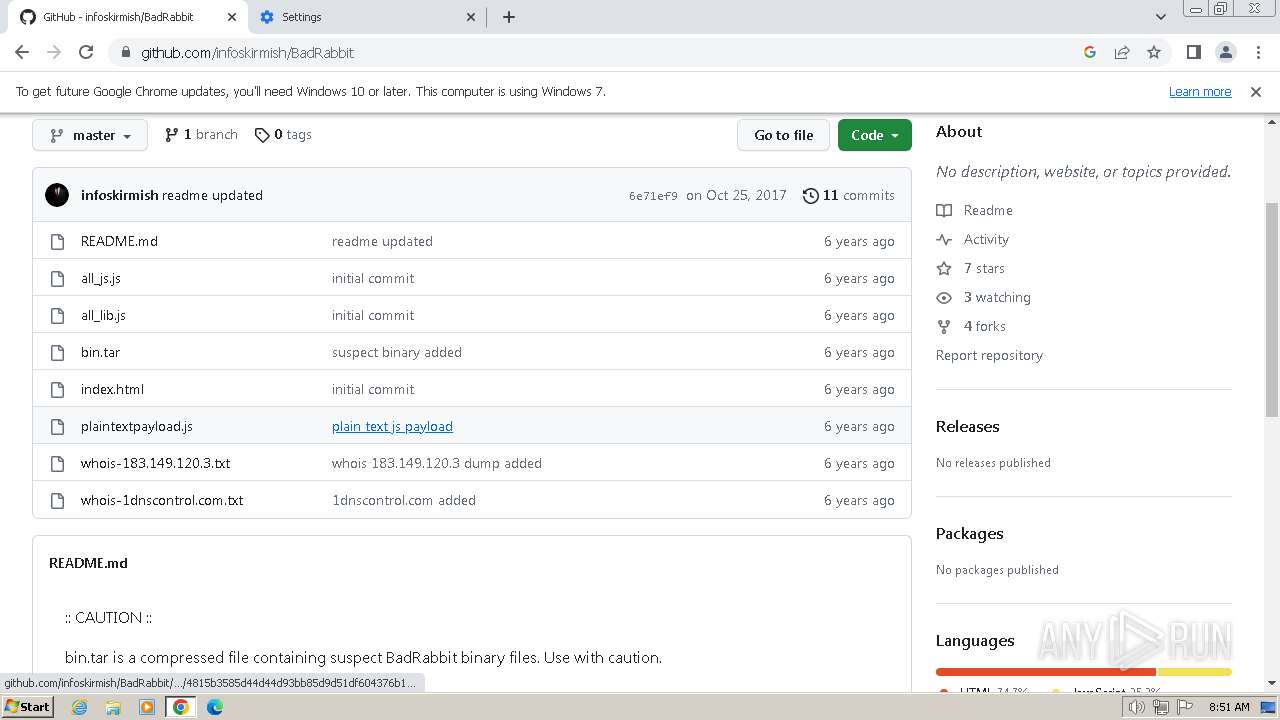
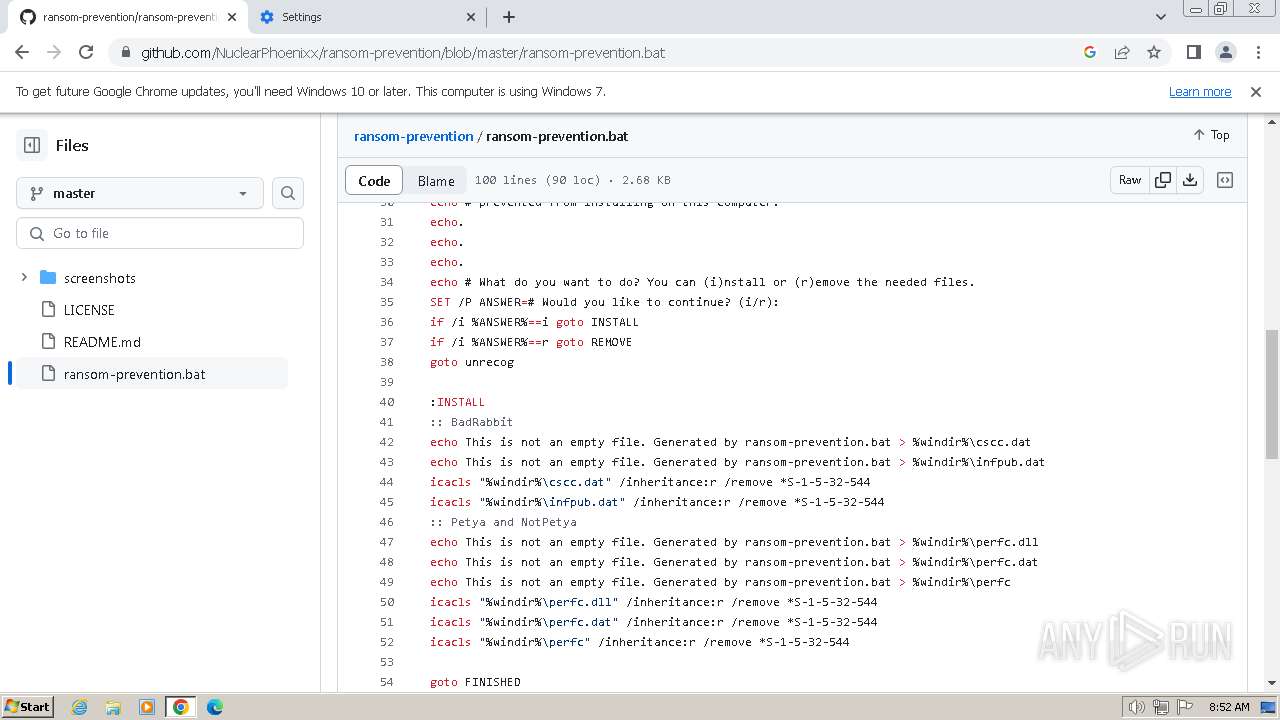
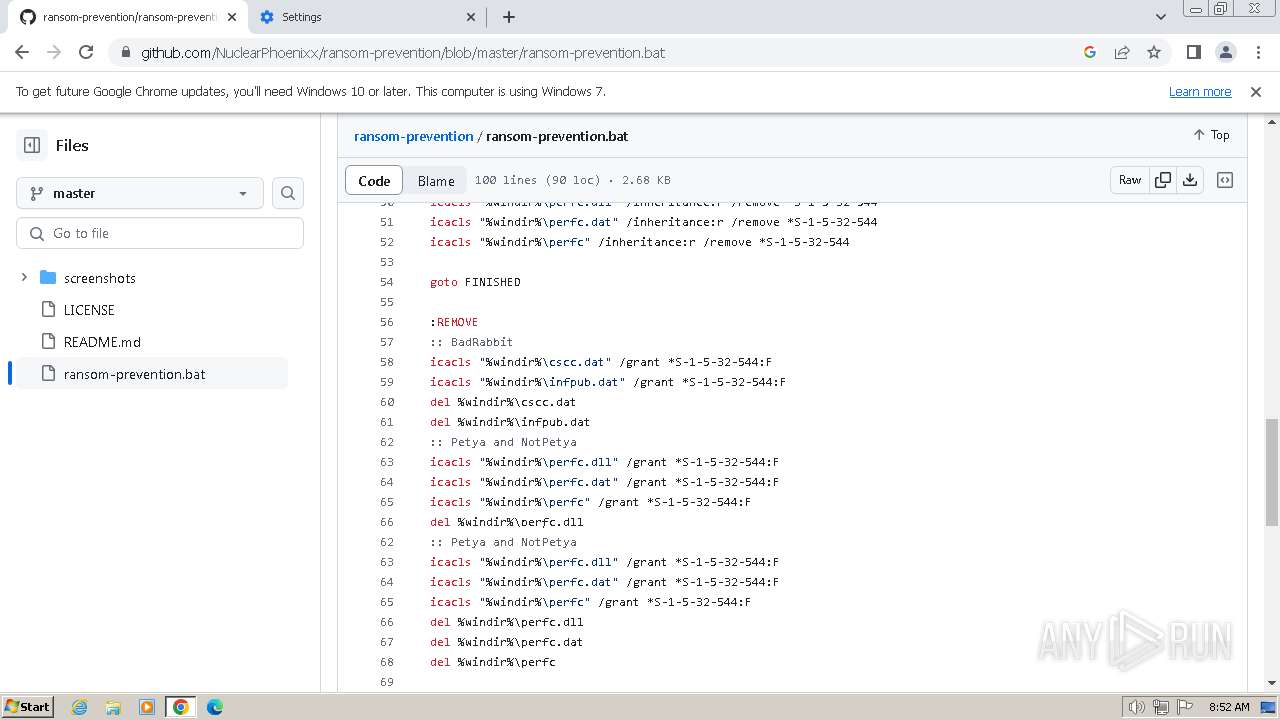
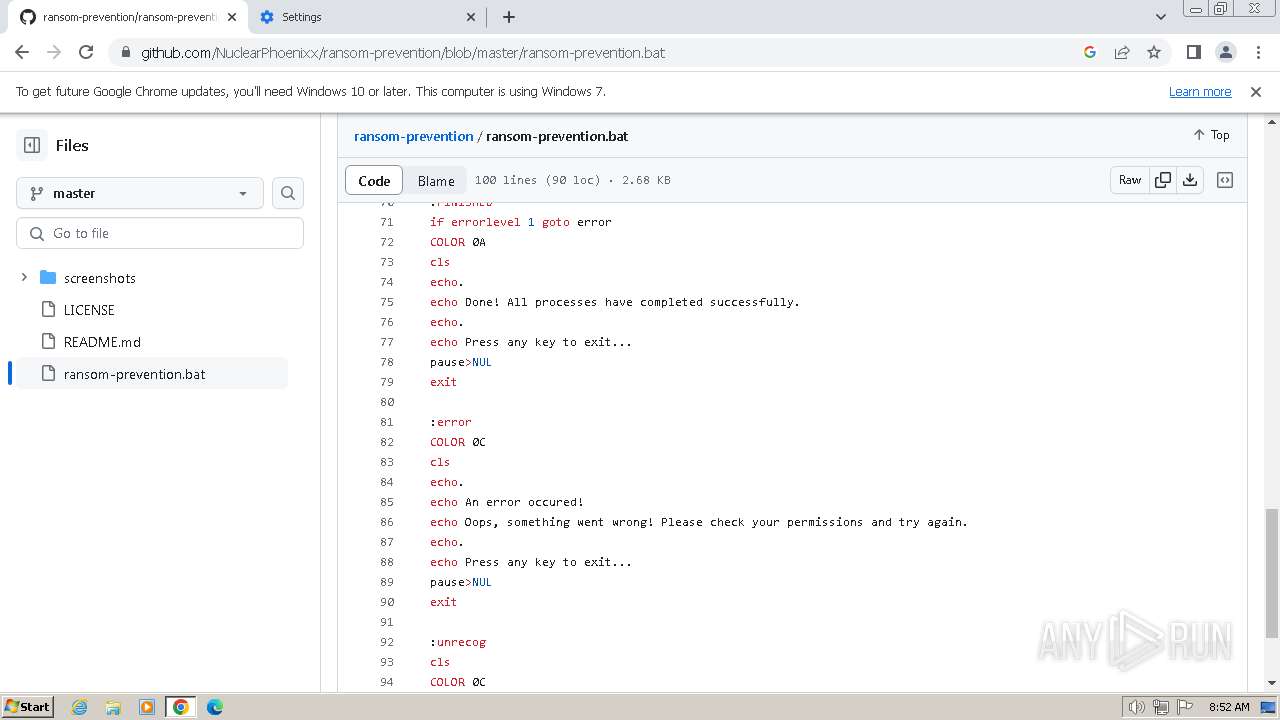
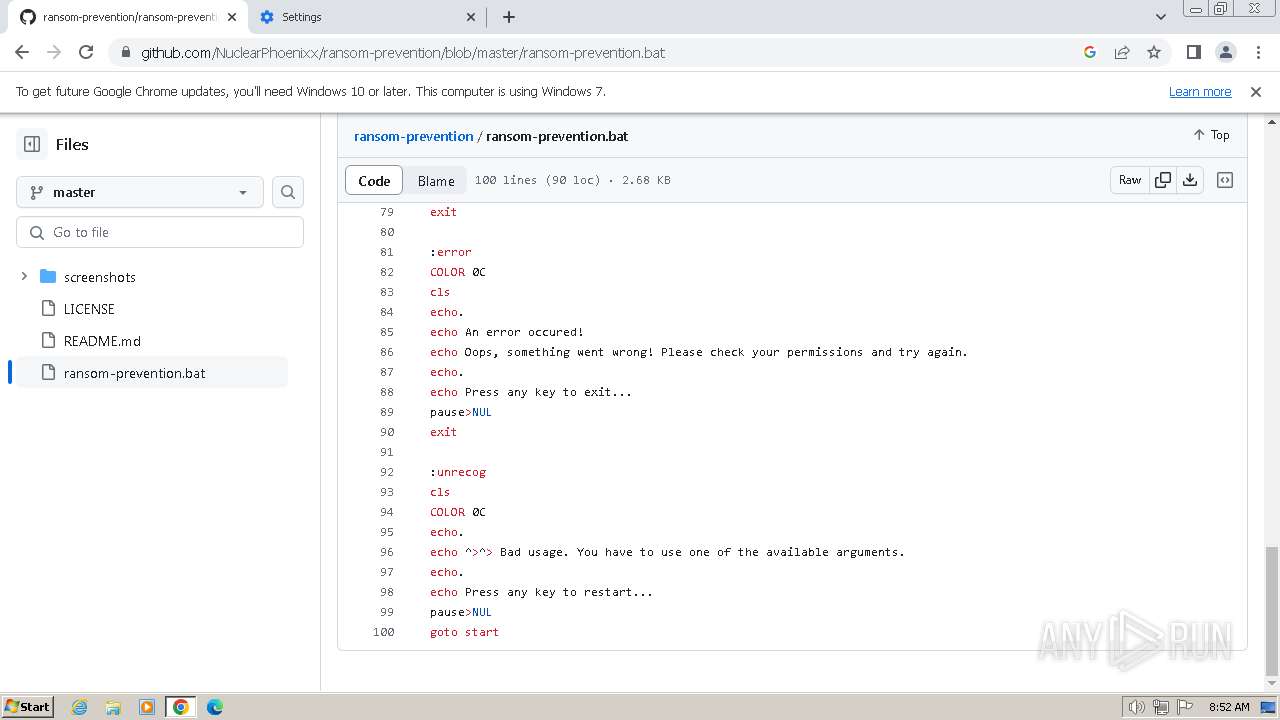
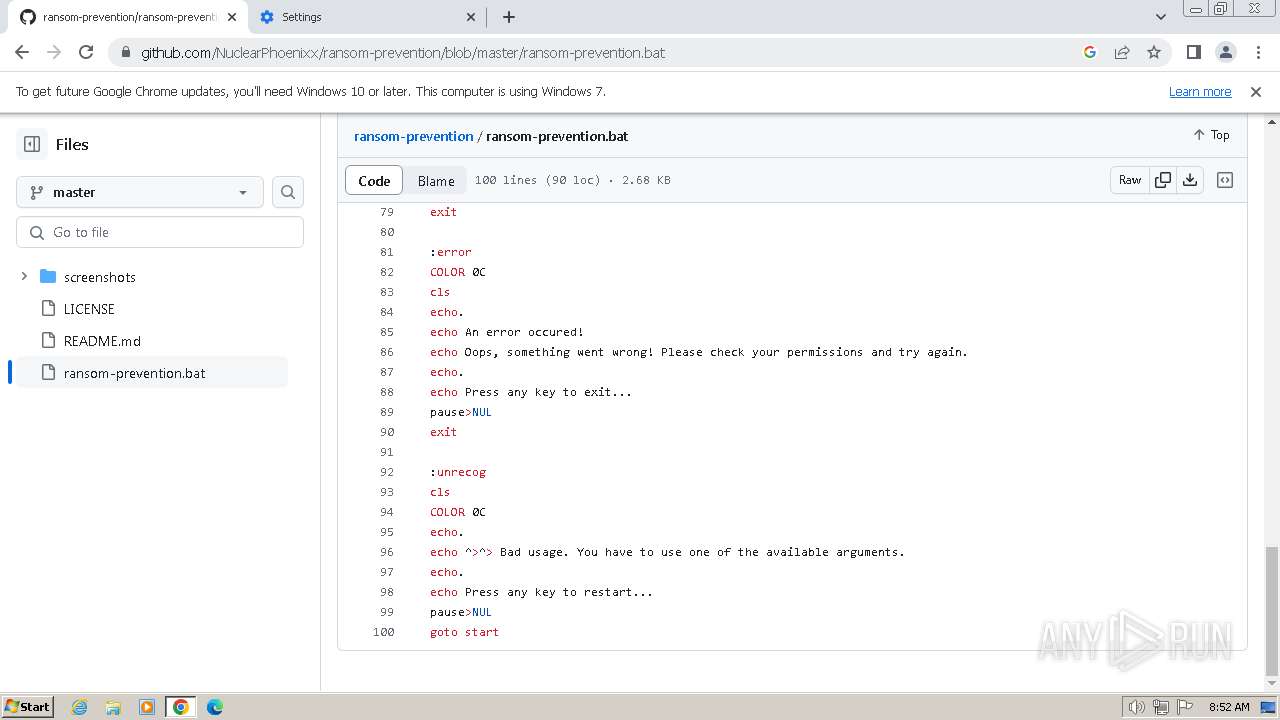
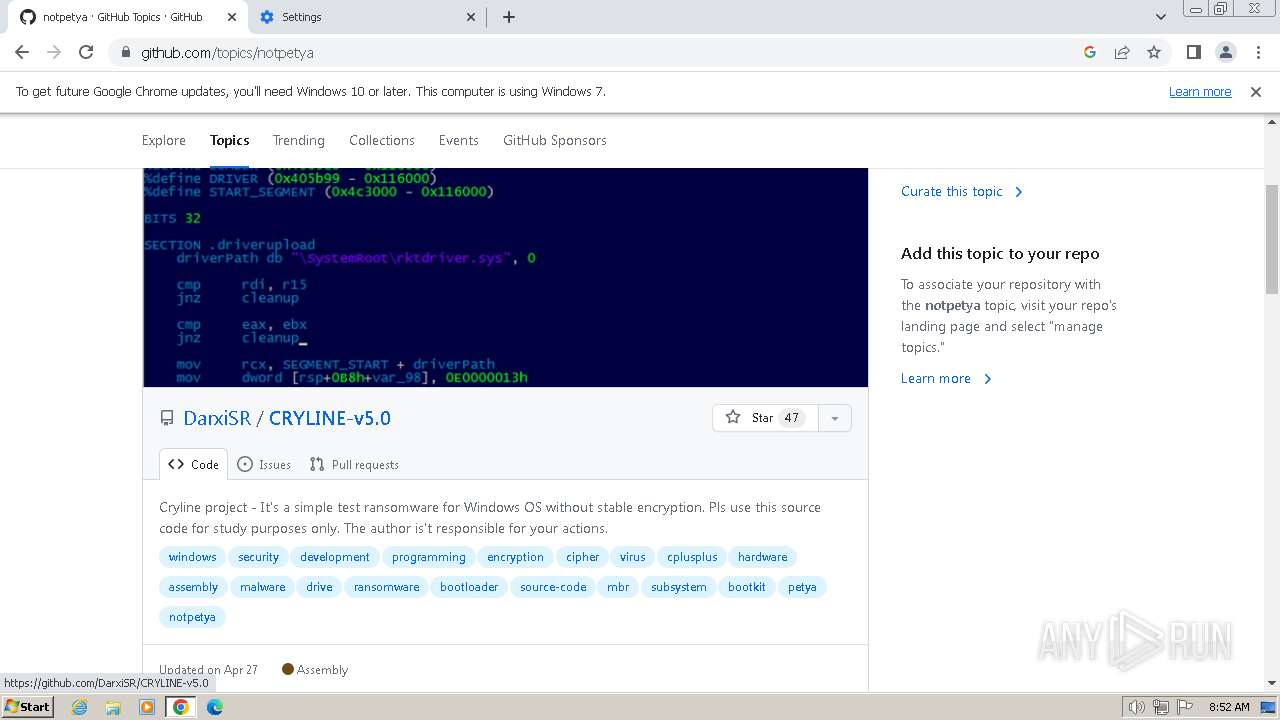
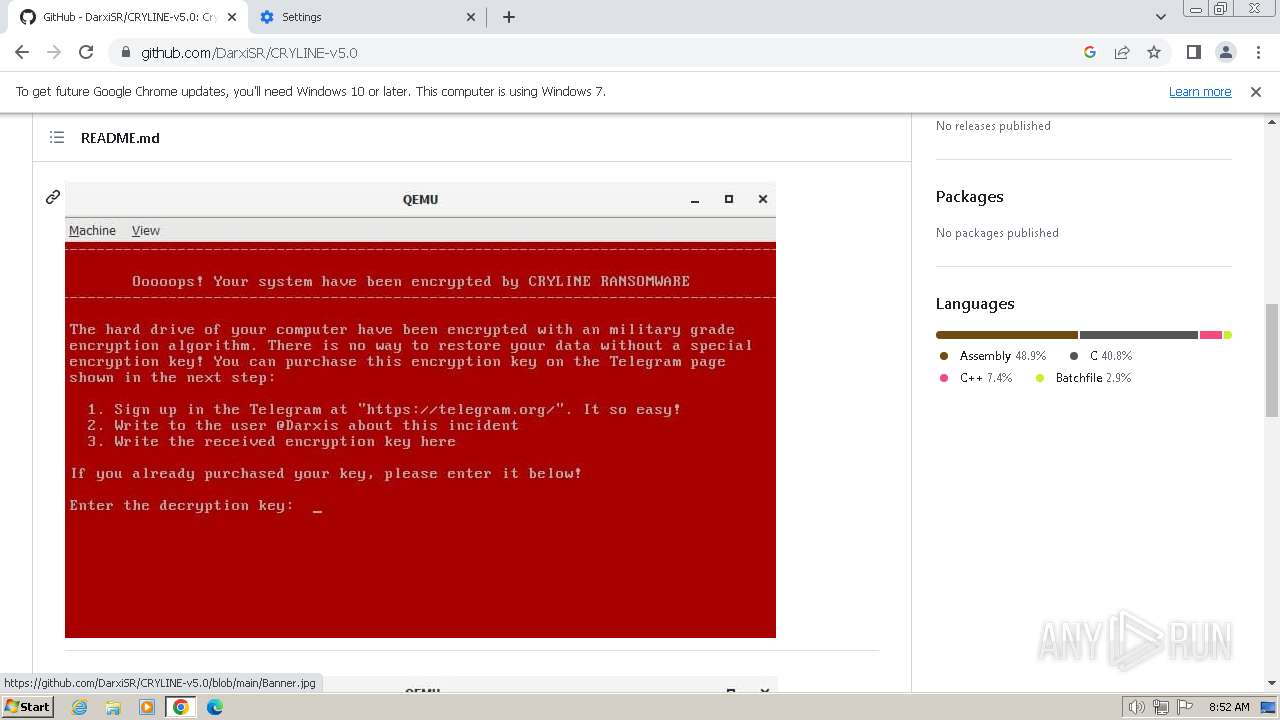
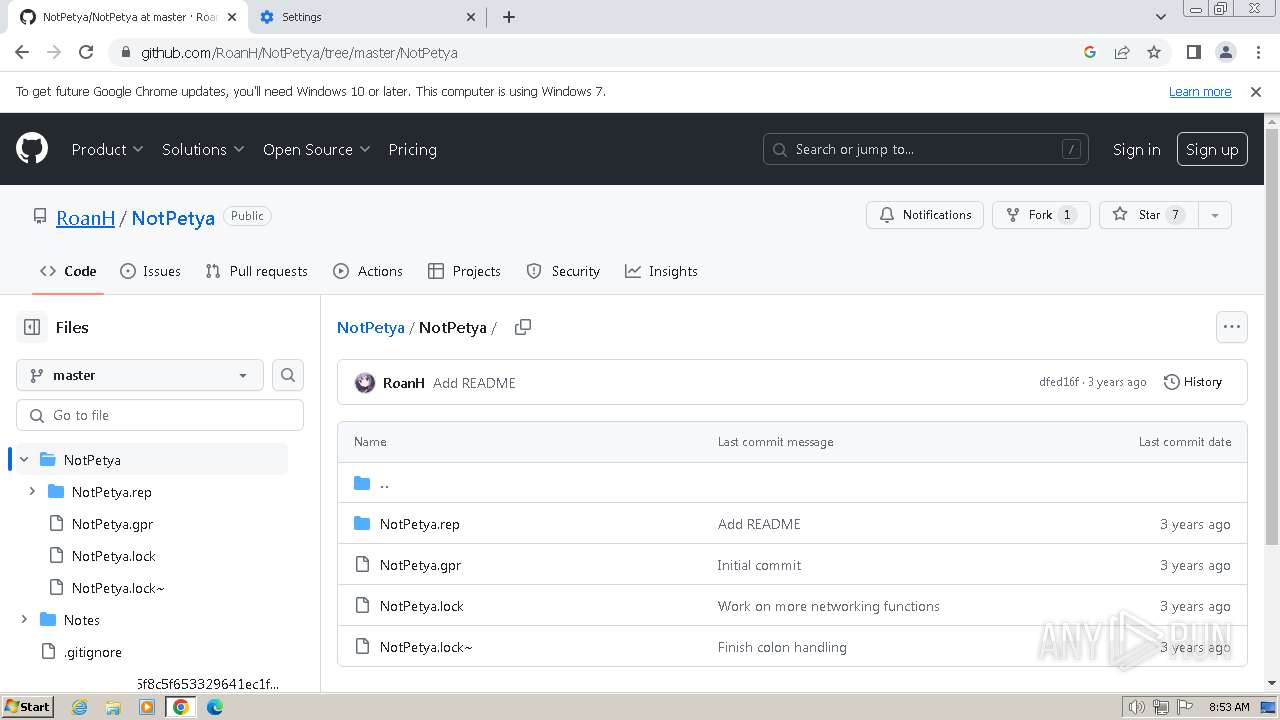
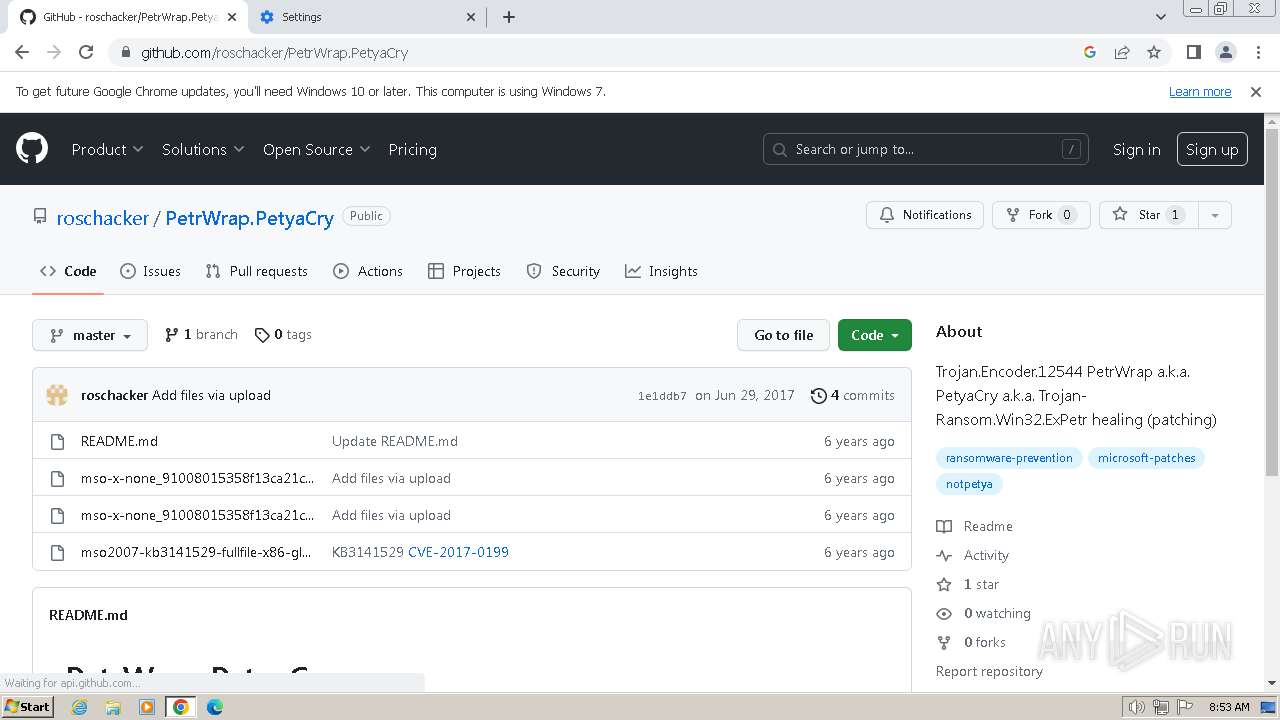
| download: | /Zusyaku/Malware-Collection-Part-2/blob/main/Ransomware/BadRabbit.exe |
| Full analysis: | https://app.any.run/tasks/4bd78a90-2fc1-4ead-9a5d-8d2b4704ef75 |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2023, 08:50:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/json |
| File info: | JSON data |
| MD5: | B8D35FCFAA6F27805C22B7BC443D09E4 |
| SHA1: | 7DCFDCCDB0F5A4B89AAC85485670962EF6C27CAE |
| SHA256: | BFDC338F9F4F7F90D00612E02A0EDEC759F89D14999D4A71E403B74D89168685 |
| SSDEEP: | 1536:Otz9DZxjDFBd9R9fBpNPAKptDx1r5VBtbfNbFfhNNl9FlddTNx99pB9NVV5Vlxvx:dF30 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- chrome.exe (PID: 2076)
Drops the executable file immediately after the start
- chrome.exe (PID: 332)
Application launched itself
- chrome.exe (PID: 2076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
JSON
| PayloadAllShortcutsEnabled: | - |
|---|---|
| PayloadBlobCsv: | null |
| PayloadBlobCsvError: | null |
| PayloadBlobDependabotInfoConfigFilePath: | null |
| PayloadBlobDependabotInfoConfigurationNoticeDismissed: | null |
| PayloadBlobDependabotInfoCurrentUserCanAdminRepo: | - |
| PayloadBlobDependabotInfoDismissConfigurationNoticePath: | /settings/dismiss-notice/dependabot_configuration_notice |
| PayloadBlobDependabotInfoNetworkDependabotPath: | /Zusyaku/Malware-Collection-Part-2/network/updates |
| PayloadBlobDependabotInfoRepoAlertsPath: | /Zusyaku/Malware-Collection-Part-2/security/dependabot |
| PayloadBlobDependabotInfoRepoOwnerIsOrg: | - |
| PayloadBlobDependabotInfoRepoSecurityAndAnalysisPath: | /Zusyaku/Malware-Collection-Part-2/settings/security_analysis |
| PayloadBlobDependabotInfoShowConfigurationBanner: | - |
| PayloadBlobDiscussionTemplate: | null |
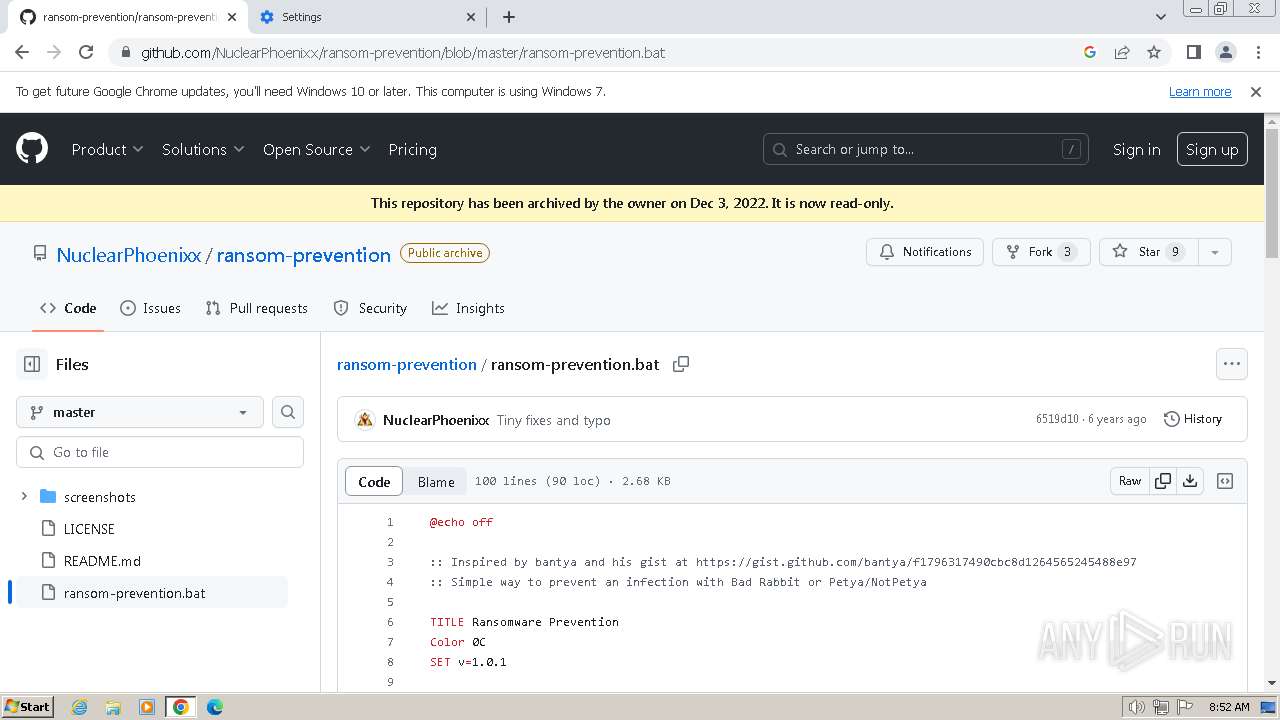
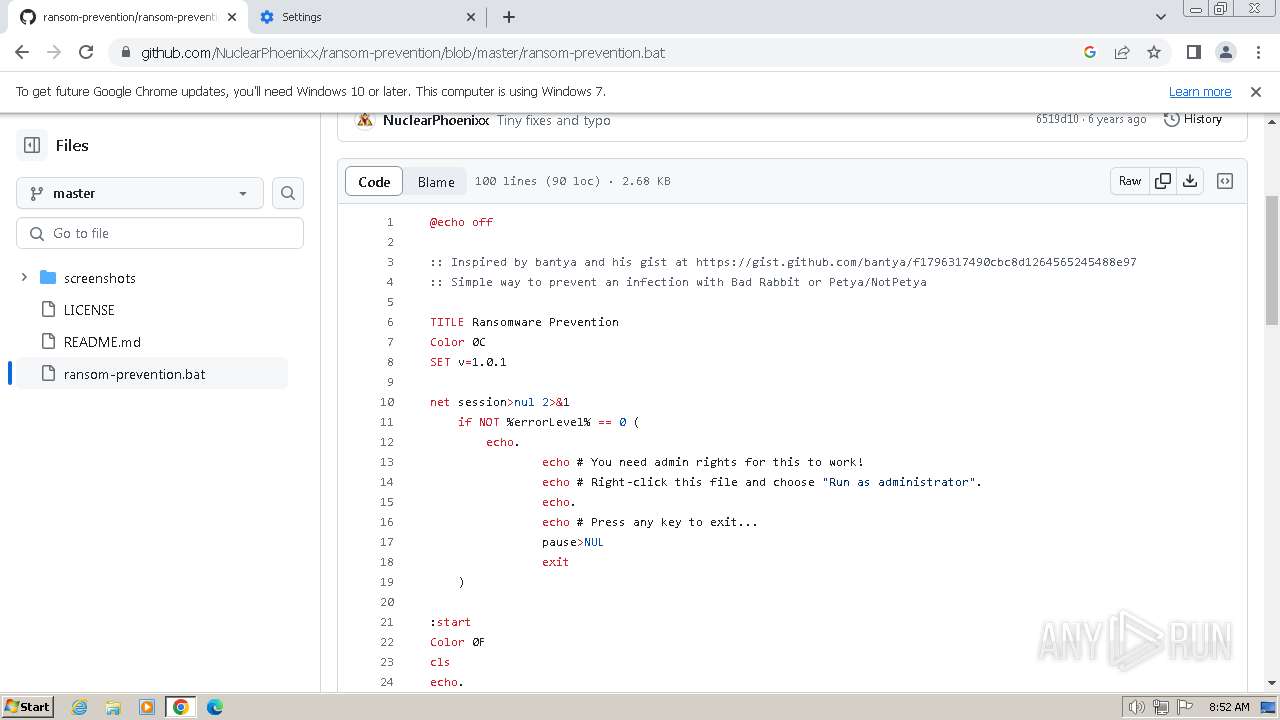
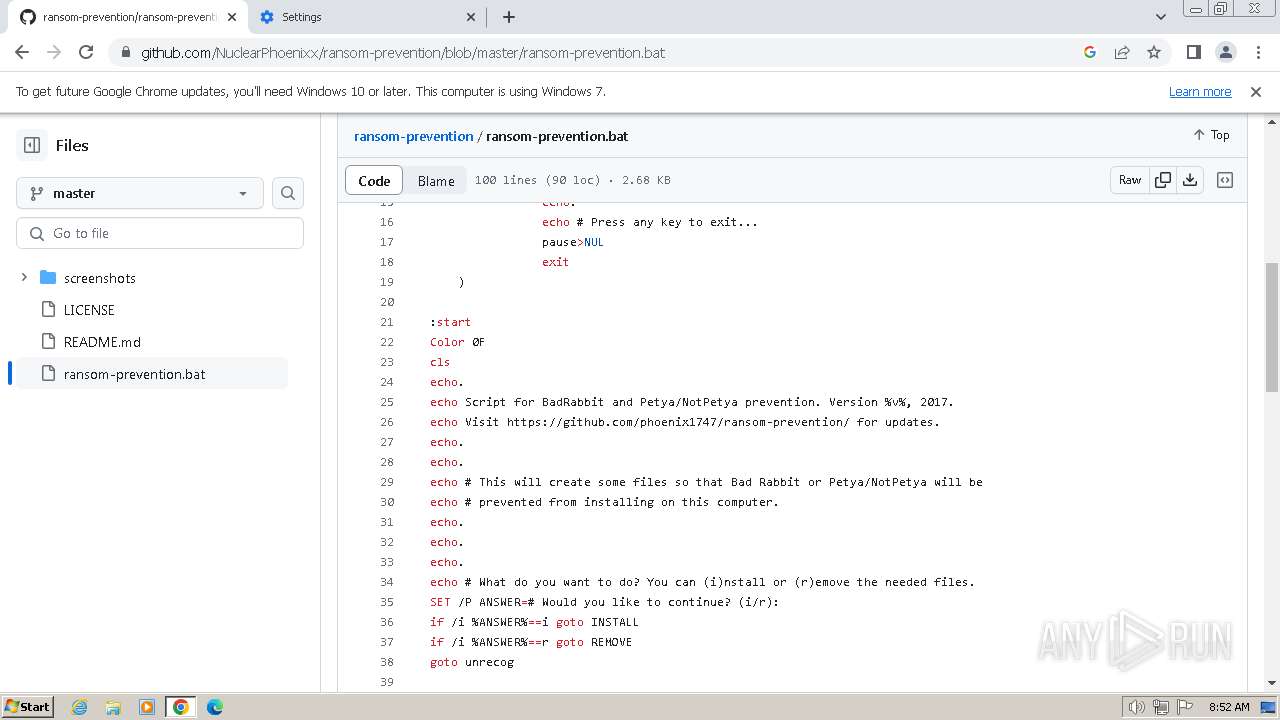
| PayloadBlobDisplayName: | BadRabbit.exe |
| PayloadBlobDisplayUrl: | https://github.com/Zusyaku/Malware-Collection-Part-2/blob/main/Ransomware/BadRabbit.exe?raw=true |
| PayloadBlobHeaderInfoBlobSize: | 432 KB |
| PayloadBlobHeaderInfoDeleteInfoDeleteTooltip: | You must be signed in to make or propose changes |
| PayloadBlobHeaderInfoEditInfoEditTooltip: | You must be signed in to make or propose changes |
| PayloadBlobHeaderInfoGhDesktopPath: | https://desktop.github.com |
| PayloadBlobHeaderInfoGitLfsPath: | null |
| PayloadBlobHeaderInfoIsCSV: | - |
| PayloadBlobHeaderInfoIsRichtext: | - |
| PayloadBlobHeaderInfoLineInfoTruncatedLoc: | null |
| PayloadBlobHeaderInfoLineInfoTruncatedSloc: | null |
| PayloadBlobHeaderInfoMode: | file |
| PayloadBlobHeaderInfoOnBranch: | |
| PayloadBlobHeaderInfoShortPath: | 99b9e66 |
| PayloadBlobHeaderInfoSiteNavLoginPath: | /login?return_to=https%3A%2F%2Fgithub.com%2FZusyaku%2FMalware-Collection-Part-2%2Fblob%2Fmain%2FRansomware%2FBadRabbit.exe |
| PayloadBlobHeaderInfoToc: | null |
| PayloadBlobImage: | - |
| PayloadBlobIsCodeownersFile: | null |
| PayloadBlobIsPlain: | - |
| PayloadBlobIsValidLegacyIssueTemplate: | - |
| PayloadBlobIssueTemplate: | null |
| PayloadBlobIssueTemplateHelpUrl: | https://docs.github.com/articles/about-issue-and-pull-request-templates |
| PayloadBlobLanguage: | null |
| PayloadBlobLanguageID: | null |
| PayloadBlobLarge: | - |
| PayloadBlobLoggedIn: | - |
| PayloadBlobNewDiscussionPath: | /Zusyaku/Malware-Collection-Part-2/discussions/new |
| PayloadBlobNewIssuePath: | /Zusyaku/Malware-Collection-Part-2/issues/new |
| PayloadBlobPlanSupportInfoRepoIsFork: | null |
| PayloadBlobPlanSupportInfoRepoOwnedByCurrentUser: | null |
| PayloadBlobPlanSupportInfoRequestFullPath: | /Zusyaku/Malware-Collection-Part-2/blob/main/Ransomware/BadRabbit.exe |
| PayloadBlobPlanSupportInfoShowFreeOrgGatedFeatureMessage: | null |
| PayloadBlobPlanSupportInfoShowPlanSupportBanner: | null |
| PayloadBlobPlanSupportInfoUpgradeDataAttributes: | null |
| PayloadBlobPlanSupportInfoUpgradePath: | null |
| PayloadBlobPublishBannersInfoDismissActionNoticePath: | /settings/dismiss-notice/publish_action_from_dockerfile |
| PayloadBlobPublishBannersInfoDismissStackNoticePath: | /settings/dismiss-notice/publish_stack_from_file |
| PayloadBlobPublishBannersInfoReleasePath: | /Zusyaku/Malware-Collection-Part-2/releases/new?marketplace=true |
| PayloadBlobPublishBannersInfoShowPublishActionBanner: | - |
| PayloadBlobPublishBannersInfoShowPublishStackBanner: | - |
| PayloadBlobRawBlobUrl: | https://github.com/Zusyaku/Malware-Collection-Part-2/raw/main/Ransomware/BadRabbit.exe |
| PayloadBlobRawLines: | null |
| PayloadBlobRenderImageOrRaw: | |
| PayloadBlobRenderedFileInfo: | null |
| PayloadBlobRichText: | null |
| PayloadBlobShortPath: | null |
| PayloadBlobStylingDirectives: | null |
| PayloadBlobSymbols: | null |
| PayloadBlobTabSize: | 8 |
| PayloadBlobTopBannersInfoActionsOnboardingTip: | null |
| PayloadBlobTopBannersInfoCitationHelpUrl: | https://docs.github.com/en/github/creating-cloning-and-archiving-repositories/creating-a-repository-on-github/about-citation-files |
| PayloadBlobTopBannersInfoGlobalPreferredFundingPath: | null |
| PayloadBlobTopBannersInfoOverridingGlobalFundingFile: | - |
| PayloadBlobTopBannersInfoRepoName: | Malware-Collection-Part-2 |
| PayloadBlobTopBannersInfoRepoOwner: | Zusyaku |
| PayloadBlobTopBannersInfoShowDependabotConfigurationBanner: | - |
| PayloadBlobTopBannersInfoShowInvalidCitationWarning: | - |
| PayloadBlobTruncated: | - |
| PayloadBlobViewable: | - |
| PayloadBlobWorkflowRedirectUrl: | null |
| PayloadCopilotAccessAllowed: | - |
| PayloadCopilotInfo: | null |
| PayloadCsrf_tokensZusyakuMalware-Collection-Part-2branchesPost: | gVbkHnha7fDjYhy271LhdP9WTWcZTtnOVB2BRbqPzI21R3KGilVAZCuNVyxs-n1EDRNn0St573cKdkwJGEQWiQ |
| PayloadCsrf_tokensrepospreferencesPost: | ajjW98dJH96d_tZb5dDucRJ2r11n50raQvAzguIZvmaeE4ak56jvCIOvDMl93ZC9C1ZFZIissq31doeM_PztPg |
| PayloadCurrentUser: | null |
| PayloadFileTreeItemsContentType: |
|
| PayloadFileTreeItemsName: |
|
| PayloadFileTreeItemsPath: |
|
| PayloadFileTreeTotalCount: | 815 |
| PayloadFileTreeRansomwareItemsContentType: |
|
| PayloadFileTreeRansomwareItemsName: |
|
| PayloadFileTreeRansomwareItemsPath: |
|
| PayloadFileTreeRansomwareTotalCount: | 27 |
| PayloadFileTreeProcessingTime: | 249.45605 |
| PayloadPath: | Ransomware/BadRabbit.exe |
| PayloadReducedMotionEnabled: | null |
| PayloadRefInfoCanEdit: | - |
| PayloadRefInfoCurrentOid: | ab33000abe1b26fcbdaa4fc6f535de5afc8f7e25 |
| PayloadRefInfoListCacheKey: | v0:1659434254.1775382 |
| PayloadRefInfoName: | main |
| PayloadRefInfoRefType: | branch |
| PayloadRepoCreatedAt: | 2021-10-02T11:22:52.000Z |
| PayloadRepoCurrentUserCanPush: | - |
| PayloadRepoDefaultBranch: | main |
| PayloadRepoId: | 412775311 |
| PayloadRepoIsEmpty: | - |
| PayloadRepoIsFork: | - |
| PayloadRepoIsOrgOwned: | - |
| PayloadRepoName: | Malware-Collection-Part-2 |
| PayloadRepoOwnerAvatar: | https://avatars.githubusercontent.com/u/71582475?v=4 |
| PayloadRepoOwnerLogin: | Zusyaku |
| PayloadRepoPrivate: | - |
| PayloadRepoPublic: | |
| PayloadSymbolsExpanded: | - |
| PayloadTreeExpanded: | |
| Title: | Malware-Collection-Part-2/Ransomware/BadRabbit.exe at main · Zusyaku/Malware-Collection-Part-2 |
Total processes
67
Monitored processes
33
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=4272 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2432 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3512 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1620 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2060 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2144 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3624 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1348 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1156 --field-trial-handle=1184,i,10883338599166317368,12998740964255942869,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
2 805
Read events
2 735
Write events
69
Delete events
1
Modification events
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (2076) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
10
Suspicious files
695
Text files
51
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe686a.TMP | — | |
MD5:— | SHA256:— | |||
| 2076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 120 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF4E0.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 2076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:ECD3386BCC950E73B86EB128A5F57622 | SHA256:C9A068EAFBC587EDFC89392F64DDD350EEB96C5CF195CDB030BAB8F6DD33833B | |||
| 120 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF4F0.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:358570F689377CE6838812643E03734B | SHA256:5B41FCC2E1A843AEAB9437B06E27B798870FF10D86A51B163BF48862BCD32590 | |||
| 2076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 2076 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFe6889.TMP | text | |
MD5:ADB669AB4CD1C63883C64FB0DBA2C7DA | SHA256:18BFF89047EC5B122573D089B3DC7A7DD14A5A7A515B2D8141584B41E723253F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
135
DNS requests
195
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 950 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 353 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 1.48 Mb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 1.39 Mb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 1.57 Mb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 6.12 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 9.82 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 9.78 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 9.68 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1596 | chrome.exe | 64.233.166.84:443 | accounts.google.com | GOOGLE | US | unknown |
2076 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1596 | chrome.exe | 216.58.212.163:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
1596 | chrome.exe | 142.250.186.68:443 | www.google.com | GOOGLE | US | whitelisted |
1596 | chrome.exe | 142.250.186.67:443 | www.gstatic.com | GOOGLE | US | whitelisted |
1596 | chrome.exe | 142.250.186.174:443 | apis.google.com | GOOGLE | US | whitelisted |
1596 | chrome.exe | 142.250.185.110:443 | encrypted-tbn0.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |
lh3.googleusercontent.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |