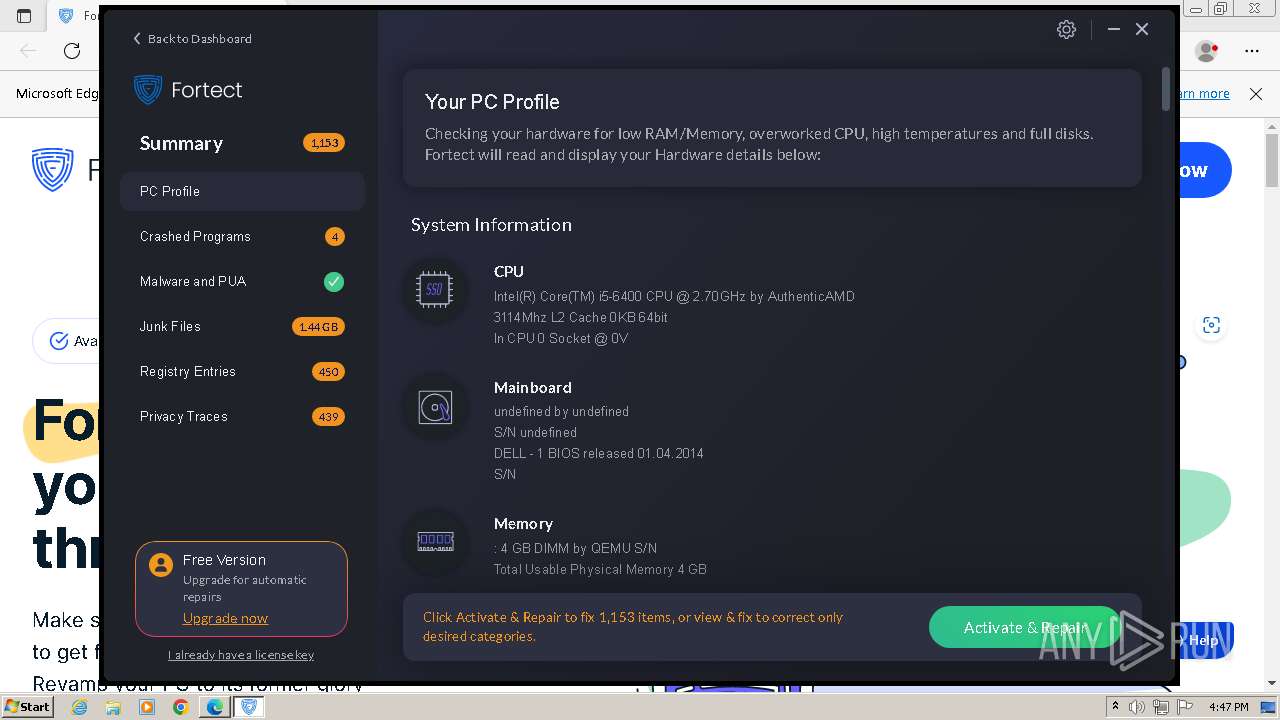
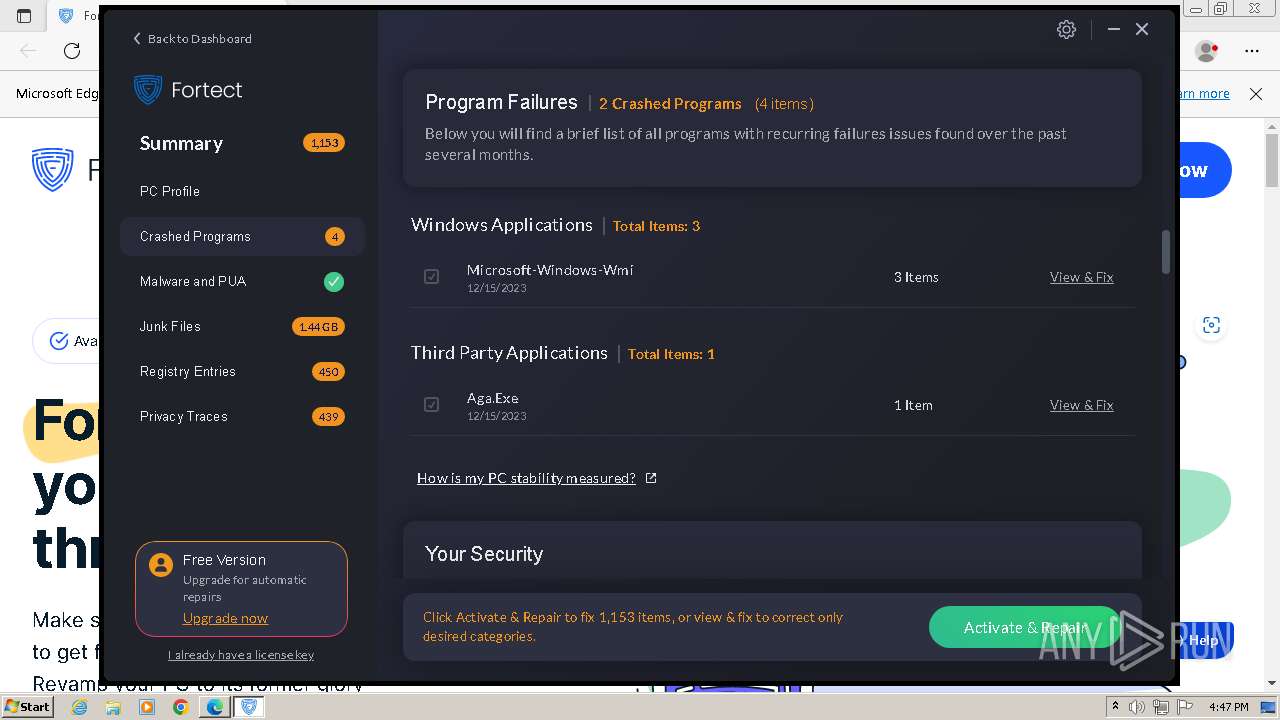
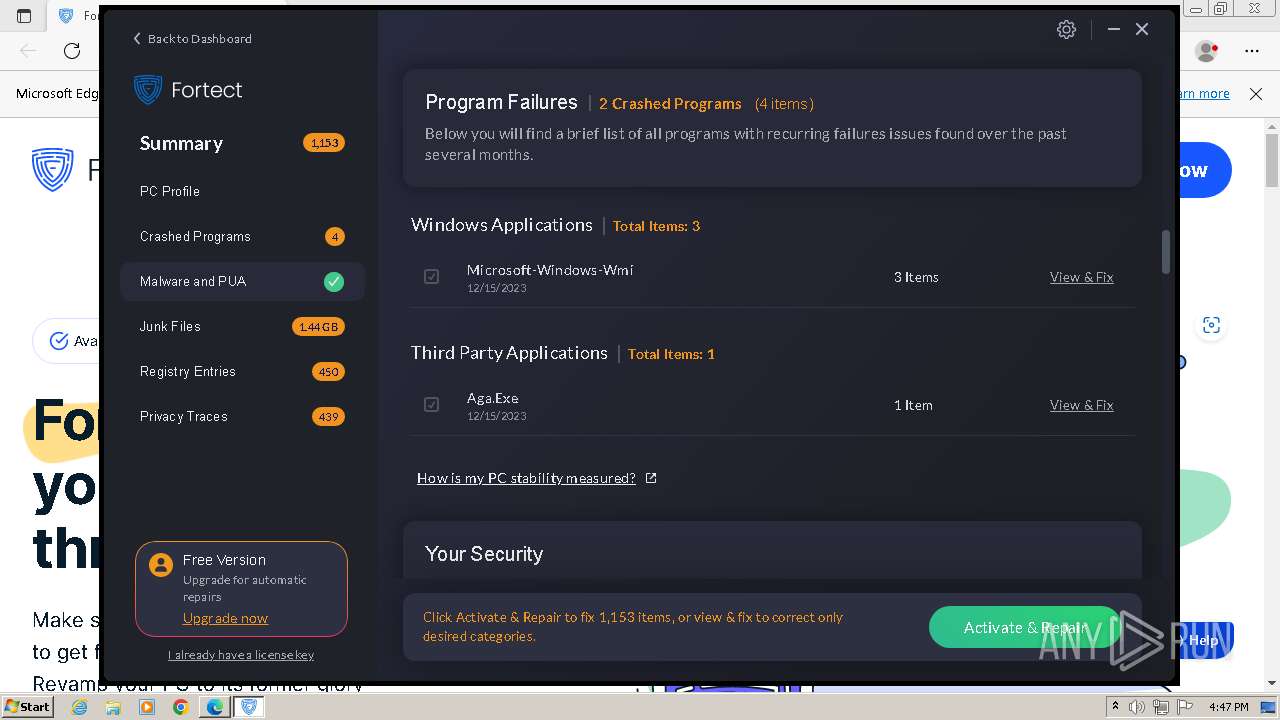
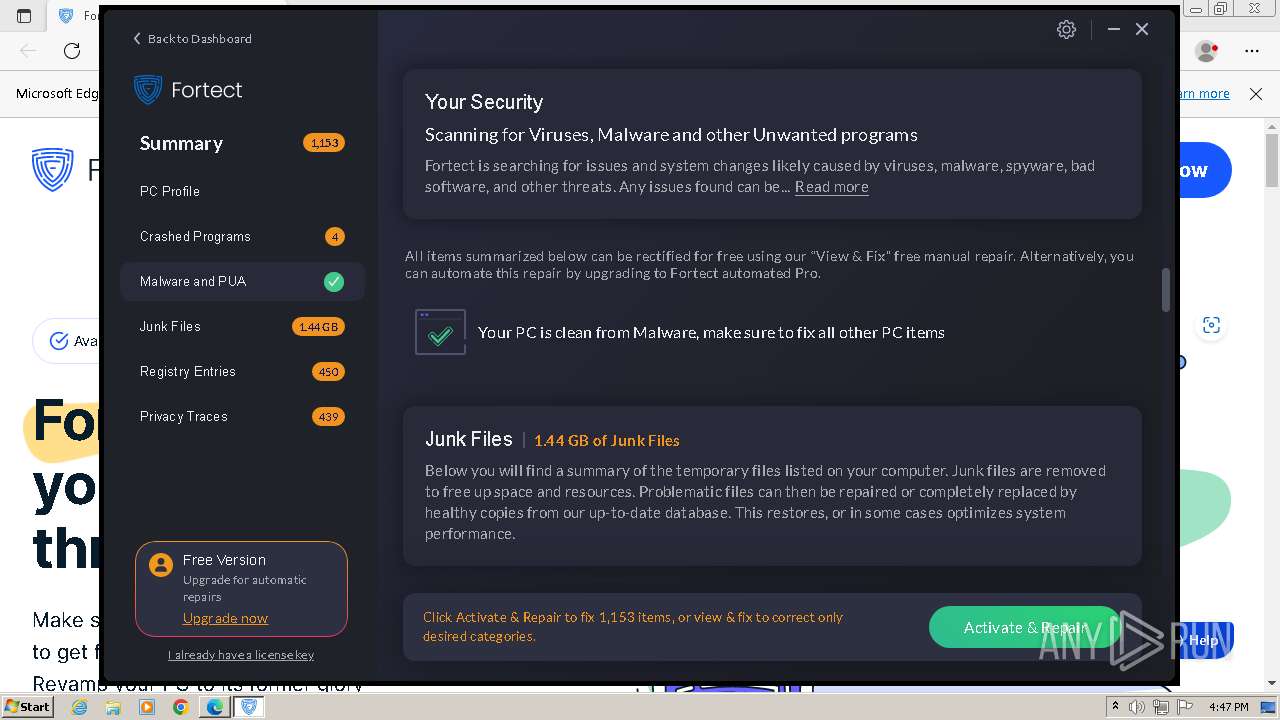
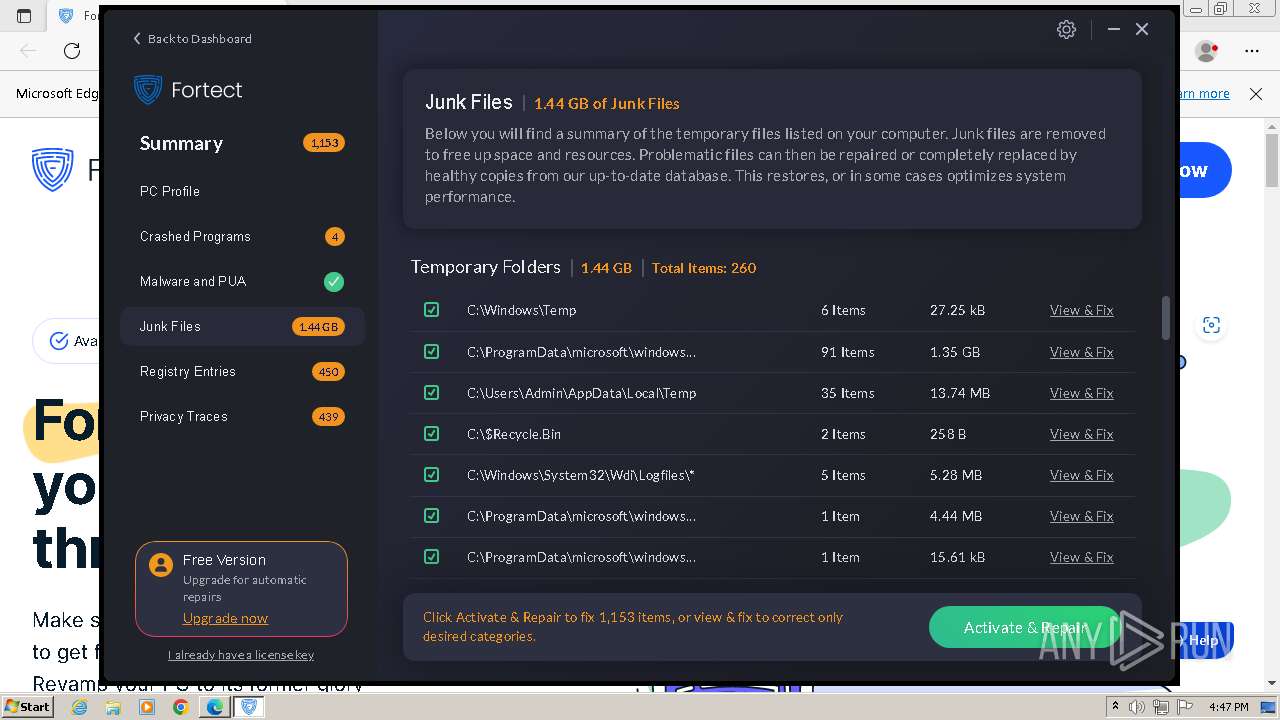
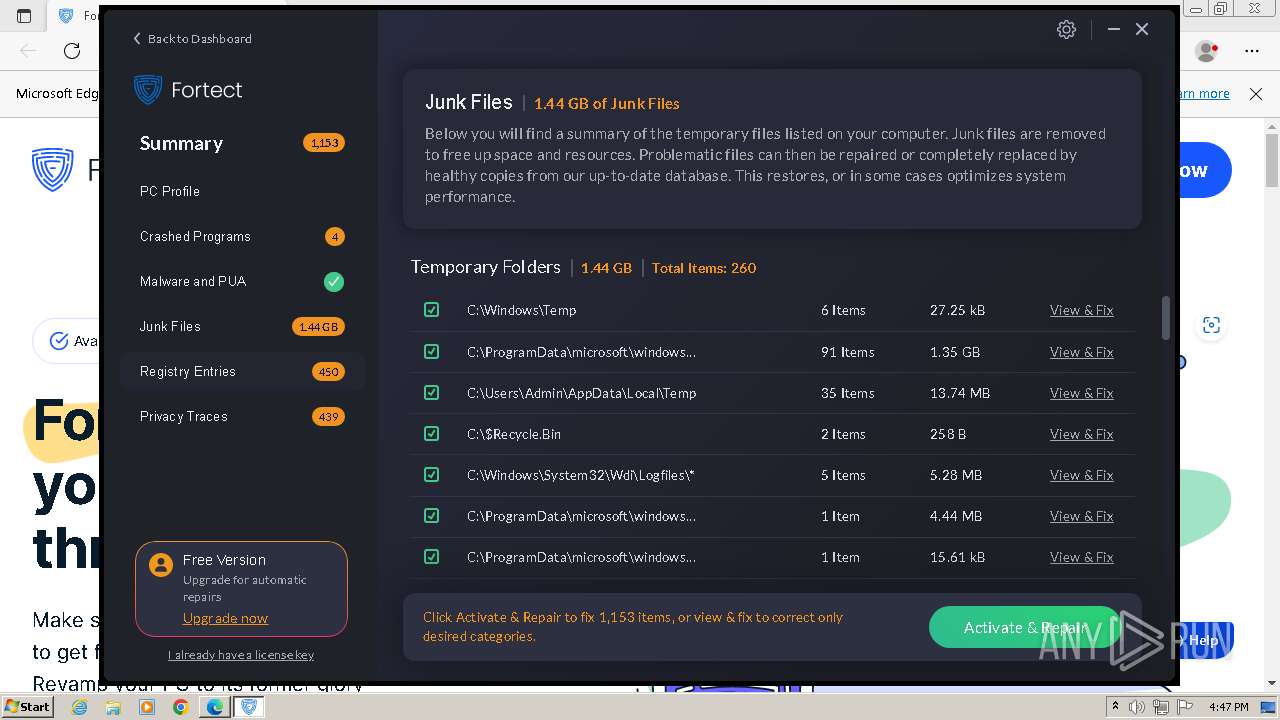
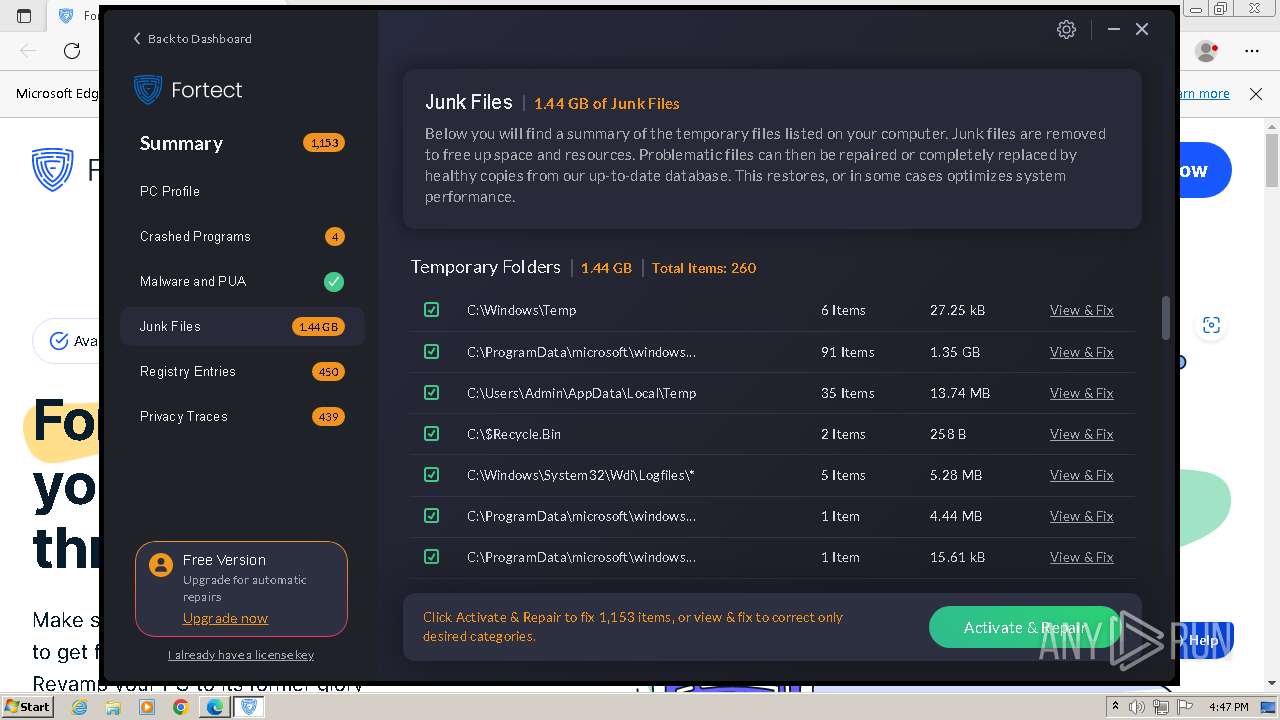
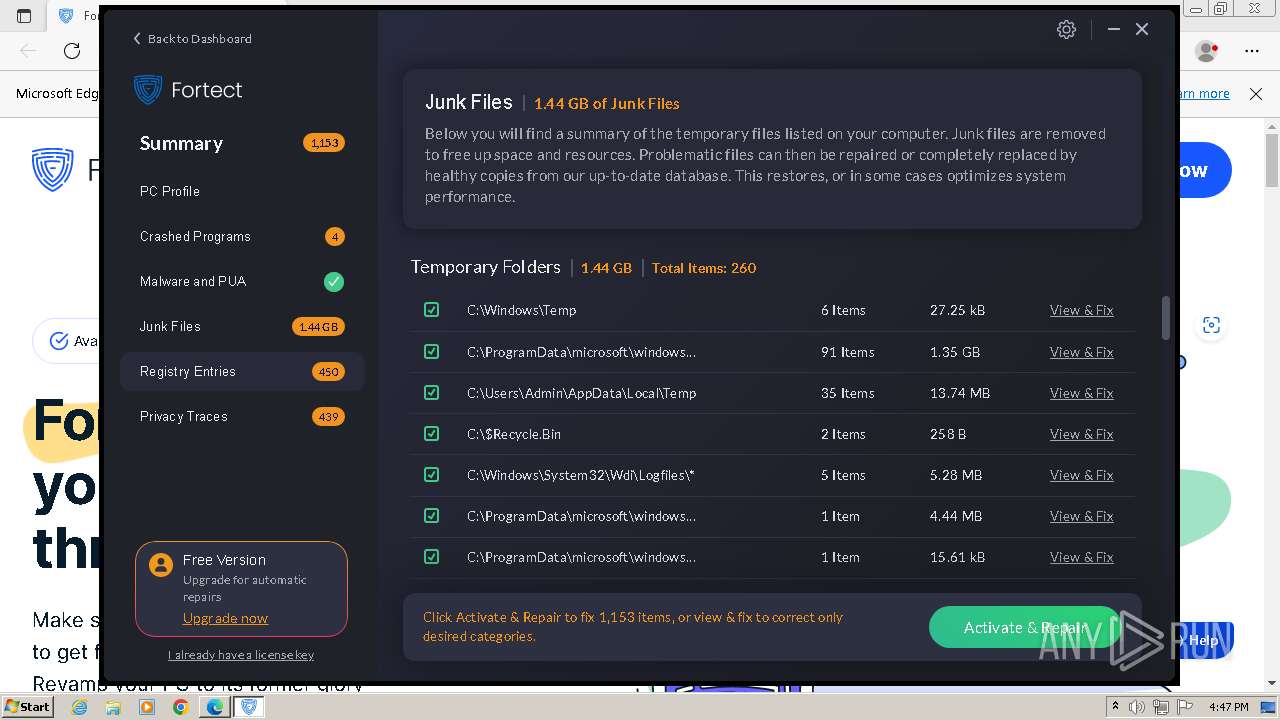
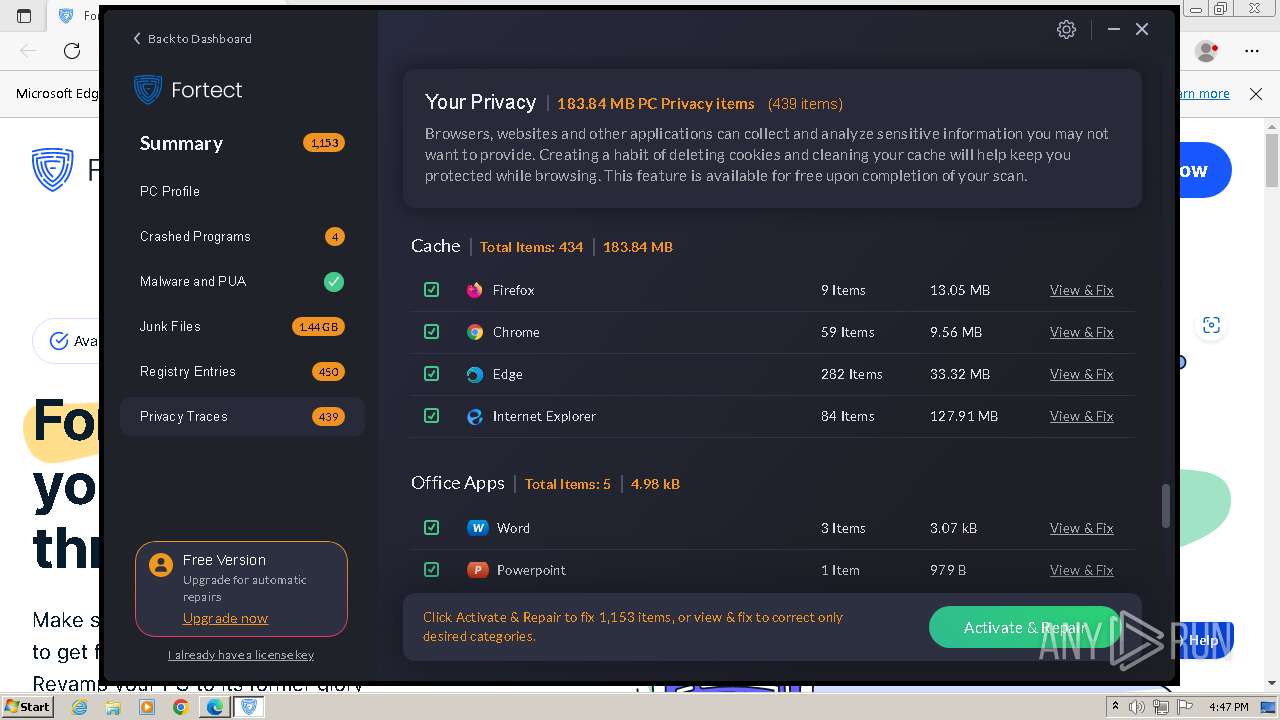
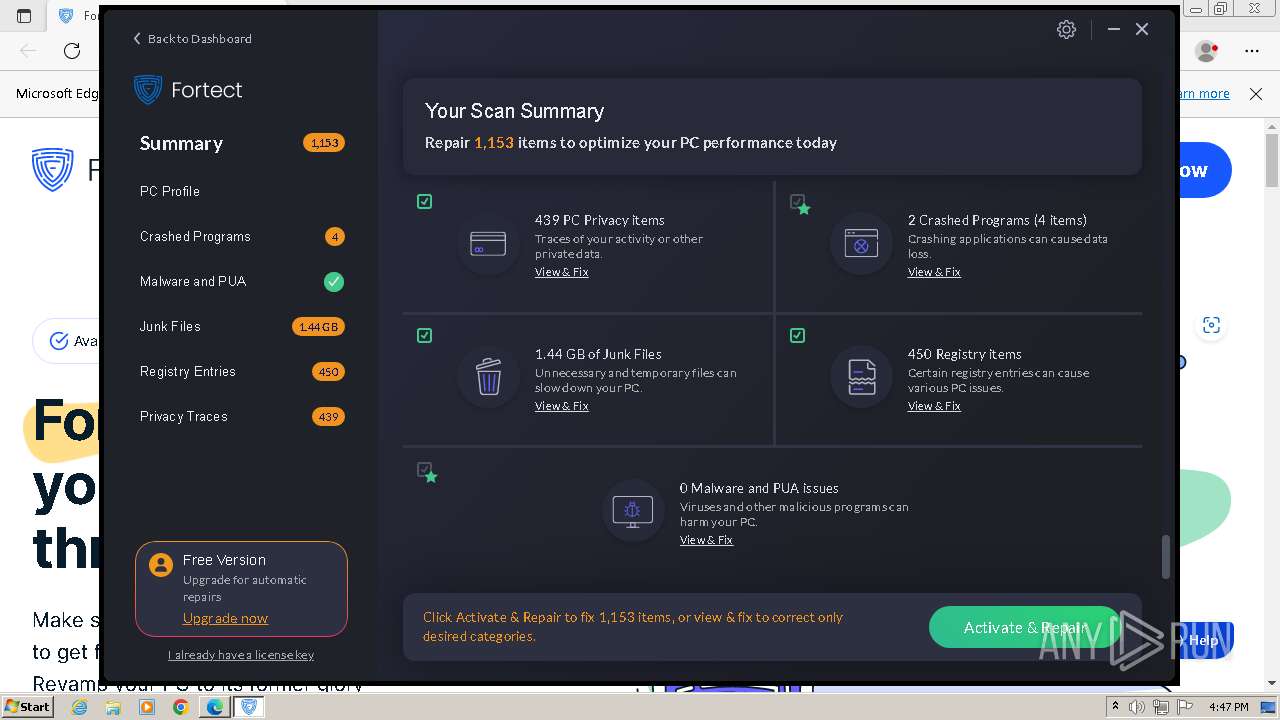
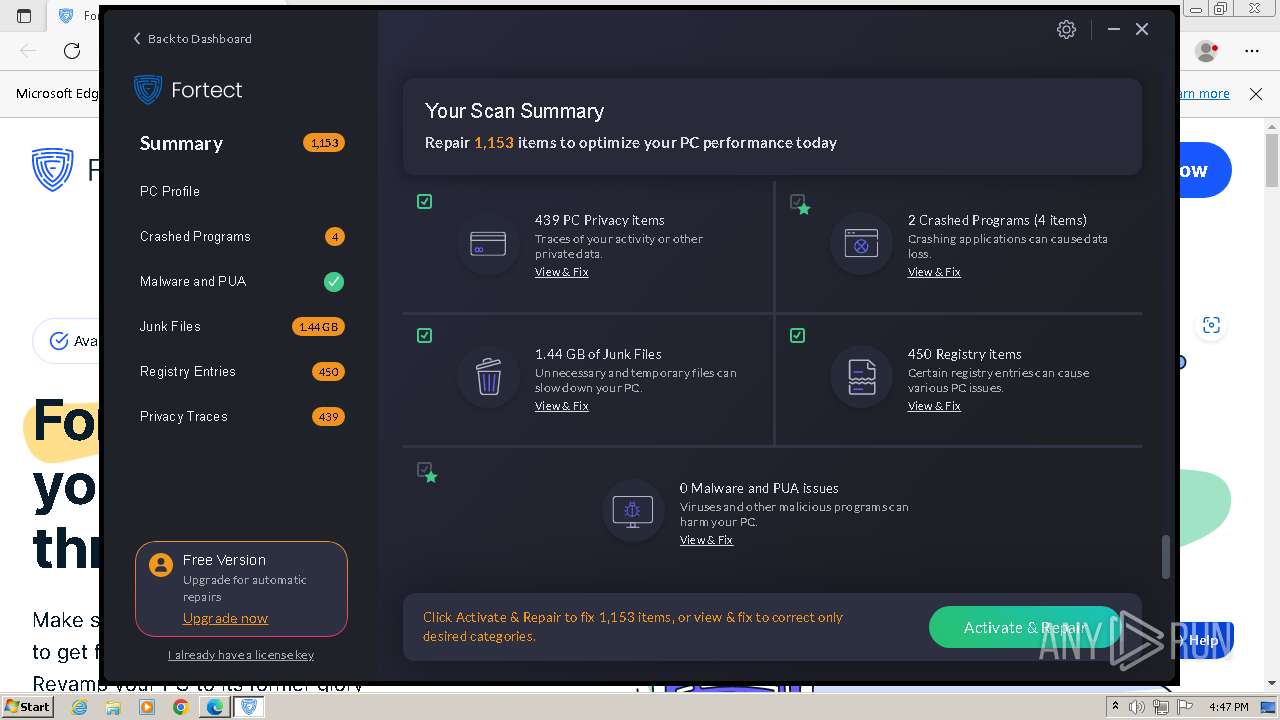
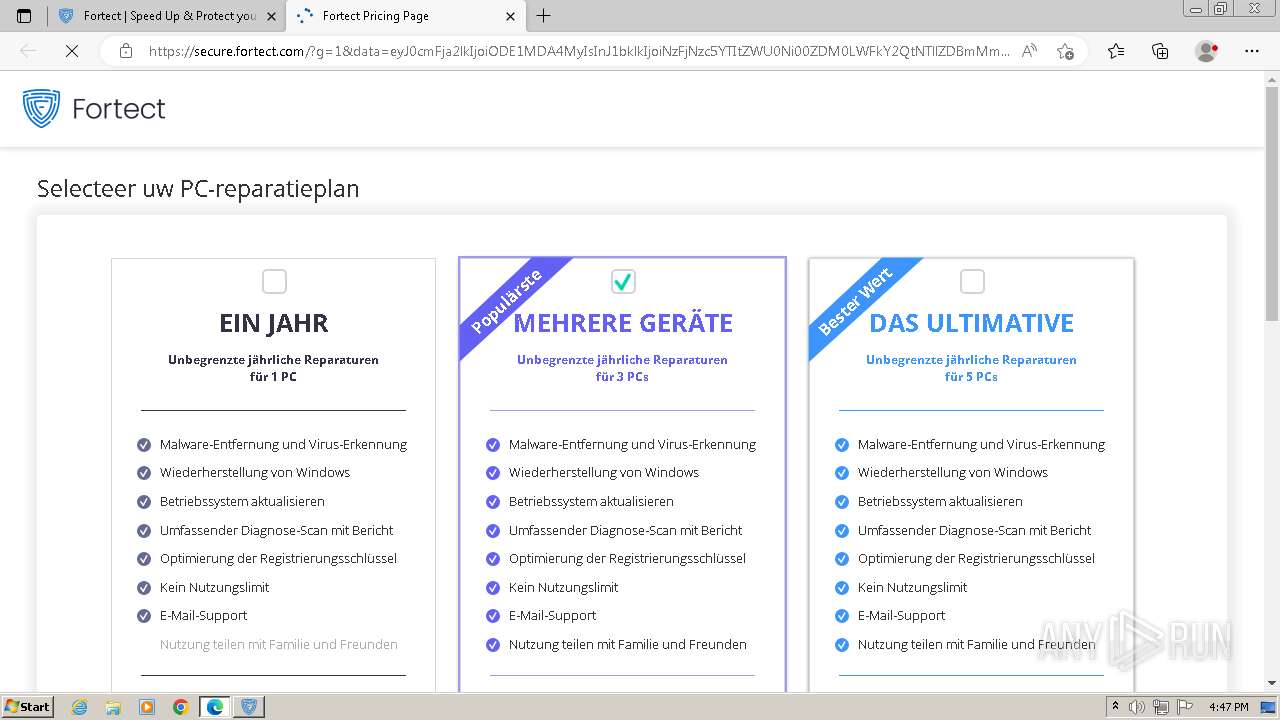
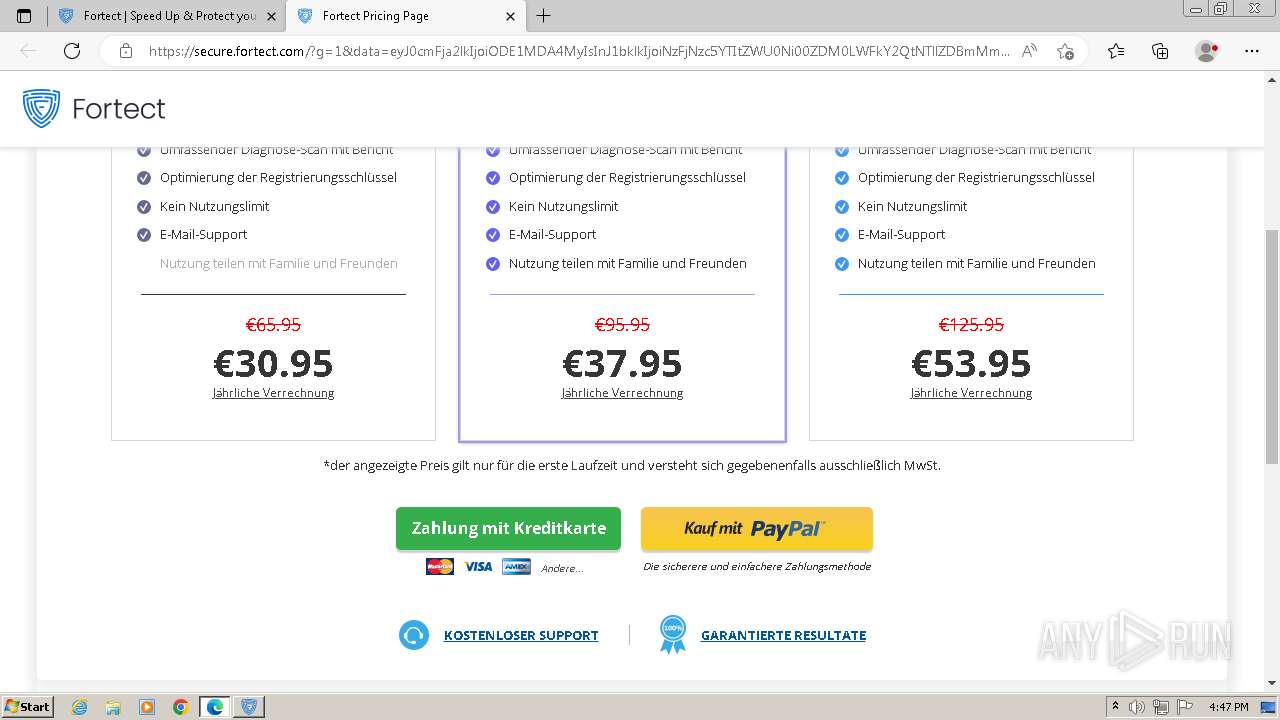
| URL: | fortect.com |
| Full analysis: | https://app.any.run/tasks/3a257da6-77e2-4ef6-a45f-9a5690fe79ad |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 16:42:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | ACB5C79CE7AFF3E9CAF20C407F29CFEF |
| SHA1: | 54CE00064F108EF9240E05EBE16EB26016591357 |
| SHA256: | BFD64CED9F20BF6DA1FF4BFF46EF202AC3417743CE6D7562EBEBD505CC179D31 |
| SSDEEP: | 3:QRt2:Qm |
MALICIOUS
Drops the executable file immediately after the start
- Fortect.exe (PID: 1380)
- FortectMain.exe (PID: 392)
Changes the autorun value in the registry
- Fortect.exe (PID: 1380)
Actions looks like stealing of personal data
- MainService.exe (PID: 3128)
SUSPICIOUS
The process creates files with name similar to system file names
- Fortect.exe (PID: 1380)
Executable content was dropped or overwritten
- Fortect.exe (PID: 1380)
- FortectMain.exe (PID: 392)
Starts CMD.EXE for commands execution
- Fortect.exe (PID: 1380)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 2736)
Reads the Internet Settings
- WMIC.exe (PID: 3564)
- WMIC.exe (PID: 3248)
- WMIC.exe (PID: 3376)
- Fortect.exe (PID: 1380)
- WMIC.exe (PID: 3636)
- FortectMain.exe (PID: 392)
- FortectMain.exe (PID: 2836)
Uses WMIC.EXE to obtain data on the partitioned areas of a physical disk
- Fortect.exe (PID: 1380)
Accesses computer name via WMI (SCRIPT)
- WMIC.exe (PID: 3248)
Uses WMIC.EXE to obtain physical disk drive information
- Fortect.exe (PID: 1380)
Reads security settings of Internet Explorer
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
Reads settings of System Certificates
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
- FortectMain.exe (PID: 392)
Checks Windows Trust Settings
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
- MainService.exe (PID: 3128)
Drops 7-zip archiver for unpacking
- Fortect.exe (PID: 1380)
Process drops legitimate windows executable
- Fortect.exe (PID: 1380)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 1192)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 3636)
Executes as Windows Service
- MainDaemon.exe (PID: 948)
- MainService.exe (PID: 3128)
Creates a software uninstall entry
- Fortect.exe (PID: 1380)
Searches for installed software
- MainDaemon.exe (PID: 948)
- MainService.exe (PID: 3128)
Application launched itself
- FortectMain.exe (PID: 392)
Reads the date of Windows installation
- MainService.exe (PID: 3128)
Reads Internet Explorer settings
- MainService.exe (PID: 3128)
Read startup parameters
- MainService.exe (PID: 3128)
Reads Microsoft Outlook installation path
- MainService.exe (PID: 3128)
Adds/modifies Windows certificates
- MainService.exe (PID: 3128)
INFO
Application launched itself
- msedge.exe (PID: 3700)
- msedge.exe (PID: 3388)
Checks supported languages
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
- MainDaemon.exe (PID: 948)
- MainService.exe (PID: 3312)
- MainService.exe (PID: 3128)
- FortectTray.exe (PID: 1264)
- FortectMain.exe (PID: 392)
- FortectMain.exe (PID: 1196)
- FortectMain.exe (PID: 3548)
- FortectMain.exe (PID: 2836)
- FortectMain.exe (PID: 1236)
- wmpnscfg.exe (PID: 992)
The process uses the downloaded file
- msedge.exe (PID: 2404)
- msedge.exe (PID: 3700)
- Fortect.exe (PID: 1380)
Executable content was dropped or overwritten
- msedge.exe (PID: 1040)
- msedge.exe (PID: 3700)
Drops the executable file immediately after the start
- msedge.exe (PID: 1040)
- msedge.exe (PID: 3700)
Reads the computer name
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
- MainDaemon.exe (PID: 948)
- MainService.exe (PID: 3312)
- MainService.exe (PID: 3128)
- FortectMain.exe (PID: 392)
- FortectMain.exe (PID: 1196)
- FortectMain.exe (PID: 3548)
- FortectMain.exe (PID: 1236)
- wmpnscfg.exe (PID: 992)
- FortectMain.exe (PID: 2836)
Create files in a temporary directory
- Fortect.exe (PID: 1380)
- FortectMain.exe (PID: 392)
Reads Environment values
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
- MainDaemon.exe (PID: 948)
- MainService.exe (PID: 3312)
- MainService.exe (PID: 3128)
- FortectMain.exe (PID: 392)
Checks proxy server information
- Fortect.exe (PID: 1380)
Creates files or folders in the user directory
- Fortect.exe (PID: 1380)
- FortectMain.exe (PID: 392)
- FortectMain.exe (PID: 3548)
Reads the machine GUID from the registry
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
- MainDaemon.exe (PID: 948)
- MainService.exe (PID: 3128)
- FortectMain.exe (PID: 392)
Reads the software policy settings
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
- MainService.exe (PID: 3128)
- FortectMain.exe (PID: 392)
Dropped object may contain TOR URL's
- Fortect.exe (PID: 1380)
Creates files in the program directory
- Fortect.exe (PID: 1380)
- MainDaemon.exe (PID: 3616)
- MainDaemon.exe (PID: 948)
- MainService.exe (PID: 3312)
- MainService.exe (PID: 3128)
Reads product name
- FortectMain.exe (PID: 392)
Manual execution by a user
- FortectMain.exe (PID: 392)
- wmpnscfg.exe (PID: 992)
Process checks computer location settings
- FortectMain.exe (PID: 392)
- FortectMain.exe (PID: 2836)
- MainService.exe (PID: 3128)
Process checks the number of cached credentials
- MainService.exe (PID: 3128)
Reads mouse settings
- MainService.exe (PID: 3128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
93
Monitored processes
44
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2200 --field-trial-handle=1356,i,728643502309601401,8897656117155358800,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Fortect\FortectMain.exe" --lang=en --runId=71c779a2-ee46-4d34-adcd-59ed0f2f44a3 | C:\Program Files\Fortect\FortectMain.exe | explorer.exe | ||||||||||||
User: admin Company: Fortect LTD® Integrity Level: MEDIUM Description: Fortect Main Exit code: 0 Version: 6.1.0.0 Modules
| |||||||||||||||
| 448 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=1564 --field-trial-handle=1356,i,728643502309601401,8897656117155358800,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 680 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3952 --field-trial-handle=1356,i,728643502309601401,8897656117155358800,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Fortect\bin\MainDaemon.exe" | C:\Program Files\Fortect\bin\MainDaemon.exe | services.exe | ||||||||||||
User: SYSTEM Company: Fortect Ltd. Integrity Level: SYSTEM Description: Fortect Daemon Exit code: 0 Version: 6.1.0.0 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1464 --field-trial-handle=1356,i,728643502309601401,8897656117155358800,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1192 | C:\Windows\system32\cmd.exe /Q /C "%SYSTEMROOT%\System32\wbem\wmic.exe" path Win32_ComputerSystemProduct get UUID | C:\Windows\System32\cmd.exe | — | Fortect.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Fortect\FortectMain.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\Fortect" --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1096 --field-trial-handle=1132,i,2173179920320366868,12698756958868249665,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:2 | C:\Program Files\Fortect\FortectMain.exe | — | FortectMain.exe | |||||||||||
User: admin Company: Fortect LTD® Integrity Level: LOW Description: Fortect Main Exit code: 0 Version: 6.1.0.0 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Fortect\FortectMain.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\Fortect" --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1384 --field-trial-handle=1132,i,2173179920320366868,12698756958868249665,131072 --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:2 | C:\Program Files\Fortect\FortectMain.exe | — | FortectMain.exe | |||||||||||
User: admin Company: Fortect LTD® Integrity Level: LOW Description: Fortect Main Exit code: 0 Version: 6.1.0.0 Modules
| |||||||||||||||
Total events
119 005
Read events
118 763
Write events
212
Delete events
30
Modification events
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: 449AA289A5702F00 | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (3700) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
59
Suspicious files
228
Text files
139
Unknown types
89
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF17f4c0.TMP | — | |
MD5:— | SHA256:— | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF17f4ef.TMP | — | |
MD5:— | SHA256:— | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF17f4fe.TMP | — | |
MD5:— | SHA256:— | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:DF0BCCD68449F07F531D76F53C718178 | SHA256:12025F4DA9E53A8B91892D4F6E6A9B89513F3488BFE9F1EEEC3C05F7EF96BDD8 | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:72265FBF816F9AAE473C0CEB421DE724 | SHA256:C549BD4A176A3744A5D91391D311E28F0503BB69213E38835A1CB213038D938C | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:0FFCDE9AA0F7BF34DC35C8AEADCA5BA5 | SHA256:5A9F6E7DDB2557B2C5921117AE4D6A407BB2504F6728DD1352FF88492E0ECC3D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
152
DNS requests
81
Threats
57
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3128 | MainService.exe | GET | 301 | 34.225.4.114:80 | http://cloud.toppcprotection.com/lib/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0A5nmpJtuaxEvON+yt46QhY7E9f4bb0JBYKHQwwOUBxCecv7B/6rROXsyRmhj6rFy5XgoAt0rBV1mCAP3s/Mf8oqSVyCeJoSqeZMPWKVM8WJeZo4wYxmjCk+9QByObtv4gtYvQ1aqF3UCcvmZ3qzqvzw2RzUsZ+7u/VbgDxMETXghK1SLu6M7TqNt3gg1QkLqDHO/nEFXWs4cdgkLzwbSTsUbQbeCLaqrQIRQUH3wHi5Md2PwKf6AlS/p611JprheyQ== | unknown | html | 641 b | unknown |
3128 | MainService.exe | POST | 200 | 34.225.4.114:80 | http://cloud.toppcprotection.com/events/scandblatest.php | unknown | xml | 32.0 Kb | unknown |
3128 | MainService.exe | GET | 200 | 34.225.4.114:80 | http://cloud.toppcprotection.com/events/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0A5nmpJtuaxEvON+yt46QhY7E9f4bb0JBYKHQwwOUBxCecv7B/6rROXsyRmhj6rFy5XgoAt0rBV1mCAP3s/Mf8oqSVyCeJoSqeZMPWKVM8WJeZo4wYxmjCk+9QByObtv4gtYvQ1aqF3UCcvmZ3qzqvzw2RzUsZ+7u/VbgDxMETXghK1SLu6M7TqNt3gg1QkLqDHO/nEFXWs4cdgkLzwbSTsUbQbeCLaqrQIRQUH3wHi5Md2PwKf6AlS/p611JprheyQ== | unknown | text | 44 b | unknown |
3128 | MainService.exe | GET | 301 | 34.225.4.114:80 | http://cloud.toppcprotection.com/lib/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0A4ghJsXlfgtehOvqt/6FVDuuThAVDz0qn45uaOtV9mNs0f2rm5lXRo2LODte56JHFqGnaMJEDFmeCgGY/jKep0hWyy0FqWzgcV+zwm2cVCmgOeUKL3s0mthCotQIwSL2/iaR2AT+iAPLqsCh29nAAxVjMp8zTKx4inALxluujKVEZhnXbFNS+kWNKWWYX3+UKXm5Cp2ZaJy8b5Vv5i6R9dCfk8M/5CcQw6cEy4/SDGum6CuOMK1Td3EkyLw+2gXxow== | unknown | html | 641 b | unknown |
3128 | MainService.exe | GET | 301 | 34.225.4.114:80 | http://cloud.toppcprotection.com/lib/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0AxEeUI+GuH3ovZfbr/OOjXPwYiN+NtM1Ml0/lATkqnYslGZ7jqZMDEo42gH9C/rY+cwWR13mTDb4Y0PeGNPUyz0Vh0NZhmd84+y6uKyXFroAip53VkmRjjNEMnu7baZrBVoHTVP9oh3llOUfXY1YLTupuBZkx38nixJt4FlCGXpVEH/0o1DeMZXWOgHCNPX/f01AKKUzk3BvmhXkcIqT4CZ4JE7rqiqvv7Af93JtAmyTSowEuw76qoR5hc2FrNjmOw== | unknown | html | 641 b | unknown |
3128 | MainService.exe | GET | 200 | 34.225.4.114:80 | http://cloud.toppcprotection.com/events/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0AxEeUI+GuH3ovZfbr/OOjXPwYiN+NtM1Ml0/lATkqnYslGZ7jqZMDEo42gH9C/rY+cwWR13mTDb4Y0PeGNPUyz0Vh0NZhmd84+y6uKyXFroAip53VkmRjjNEMnu7baZrBVoHTVP9oh3llOUfXY1YLTupuBZkx38nixJt4FlCGXpVEH/0o1DeMZXWOgHCNPX/f01AKKUzk3BvmhXkcIqT4CZ4JE7rqiqvv7Af93JtAmyTSowEuw76qoR5hc2FrNjmOw== | unknown | text | 44 b | unknown |
3128 | MainService.exe | GET | 200 | 34.225.4.114:80 | http://cloud.toppcprotection.com/events/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0A4ghJsXlfgtehOvqt/6FVDuuThAVDz0qn45uaOtV9mNs0f2rm5lXRo2LODte56JHFqGnaMJEDFmeCgGY/jKep0hWyy0FqWzgcV+zwm2cVCmgOeUKL3s0mthCotQIwSL2/iaR2AT+iAPLqsCh29nAAxVjMp8zTKx4inALxluujKVEZhnXbFNS+kWNKWWYX3+UKXm5Cp2ZaJy8b5Vv5i6R9dCfk8M/5CcQw6cEy4/SDGum6CuOMK1Td3EkyLw+2gXxow== | unknown | text | 44 b | unknown |
3128 | MainService.exe | GET | 200 | 34.225.4.114:80 | http://cloud.toppcprotection.com/events/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0A0SV0tsBrfmgH/S1HQspQ05/Anqrtg/FjVSOJglETmSGph6j9PfoGg010AifTITt45t5juX8wpsaSM4j7gKeCc0e5vq9/4byX0JqhNO7Uoo2X65DFoGShRt3wVupeMu1jU/MKX//mCc81tA6bIP3aqbo3garTz4czjplFz3RtD7ZCnYiSZF1tqVWztUcbMtnoC62X2farCGP0CMyCMCctY1ENtsZ3XqOm2G7Xeg4KDQCYMDkL6WqIkc7tzxxxBd5Xq9b3f/2QP11U3zyvrXrcc+QZCErapiLrAwua0LHy3uI | unknown | text | 44 b | unknown |
3128 | MainService.exe | GET | 301 | 34.225.4.114:80 | http://cloud.toppcprotection.com/lib/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0A0SV0tsBrfmgH/S1HQspQ05/Anqrtg/FjVSOJglETmSGph6j9PfoGg010AifTITt45t5juX8wpsaSM4j7gKeCc0e5vq9/4byX0JqhNO7Uoo2X65DFoGShRt3wVupeMu1jU/MKX//mCc81tA6bIP3aqbo3garTz4czjplFz3RtD7ZCnYiSZF1tqVWztUcbMtnoC62X2farCGP0CMyCMCctY1ENtsZ3XqOm2G7Xeg4KDQCYMDkL6WqIkc7tzxxxBd5Xq9b3f/2QP11U3zyvrXrcc+QZCErapiLrAwua0LHy3uI | unknown | html | 681 b | unknown |
3128 | MainService.exe | GET | 301 | 34.225.4.114:80 | http://cloud.toppcprotection.com/lib/cloud-scan.php?param1=wx2Z/yprmlGv8NAb93i0Awc85i9XCMbCSaN+2ldx12ExMm5iXi/IHFBoHtRINUqmQIsTGAy6+JiGIxRArcl3v1VPWQRYEBUouXa7gUQDVtQxEcNKRsPGHTZyXTROb4FHQN4rsWtKi6vk57N19EnPqJO/yRtJF04mj3RnFpi9MNQyETeZn+b+S6AhmA4RxeH4np6rk/5hG1WOr84N/MhKaCMj+wSZVWyiq9FYKLk6H76ExnbVDpLEL+eL9iNu2se+3e7uFRPvckSIur50bnFO0CVG2CyHbM3rFYY0ZgMFL3o= | unknown | html | 661 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3700 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
1040 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1040 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1040 | msedge.exe | 172.67.75.40:443 | fortect.com | CLOUDFLARENET | US | unknown |
1040 | msedge.exe | 142.250.186.104:443 | www.googletagmanager.com | — | — | unknown |
1040 | msedge.exe | 18.173.205.71:443 | widget.freshworks.com | — | US | unknown |
1040 | msedge.exe | 216.58.212.138:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
fortect.com |
| unknown |
edge.microsoft.com |
| whitelisted |
www.fortect.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
widget.freshworks.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
region1.analytics.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
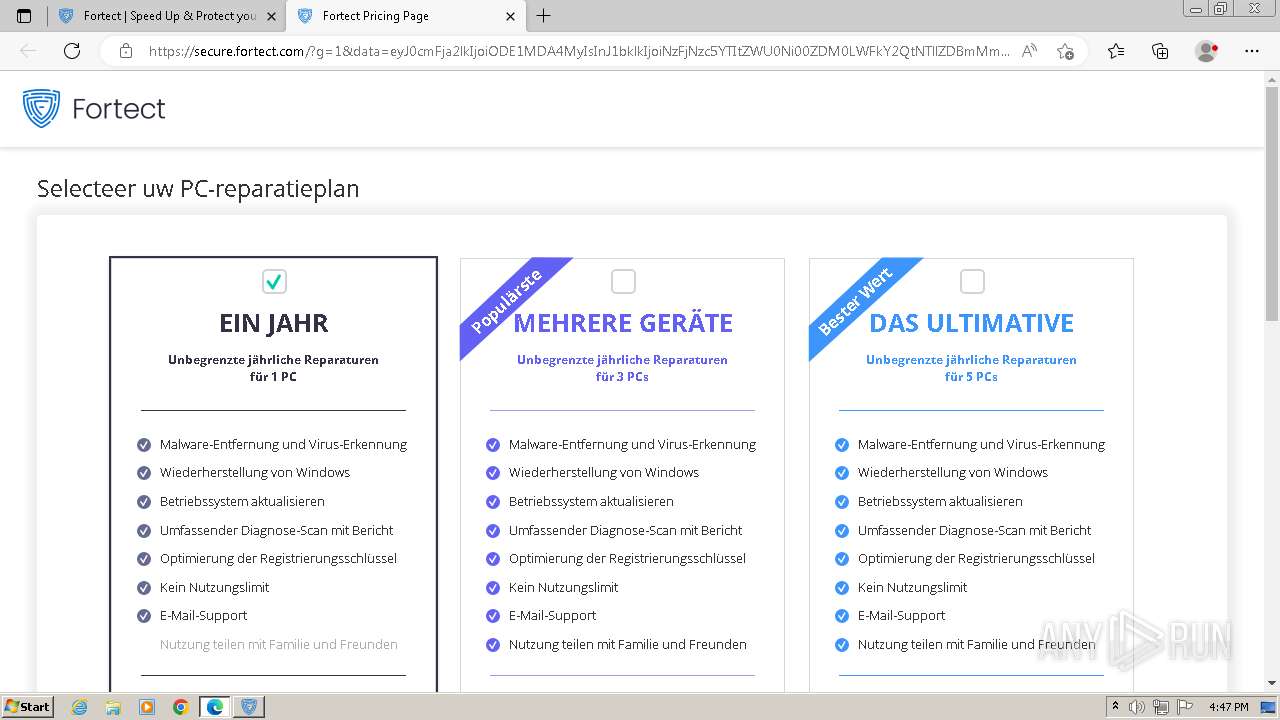
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed PC Optimizer Software Domain (fortect .com in TLS SNI) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
1040 | msedge.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to PC Optimizer Software Domain (fortect .com) |
Process | Message |
|---|---|
Fortect.exe | ExecShellAsUser: got desktop |
Fortect.exe | ExecShellAsUser: elevated process detected |
Fortect.exe | ExecShellAsUser: thread finished |
Fortect.exe | ExecShellAsUser: DLL_PROCESS_DETACH |
msedge.exe | [0223/164724.438:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|