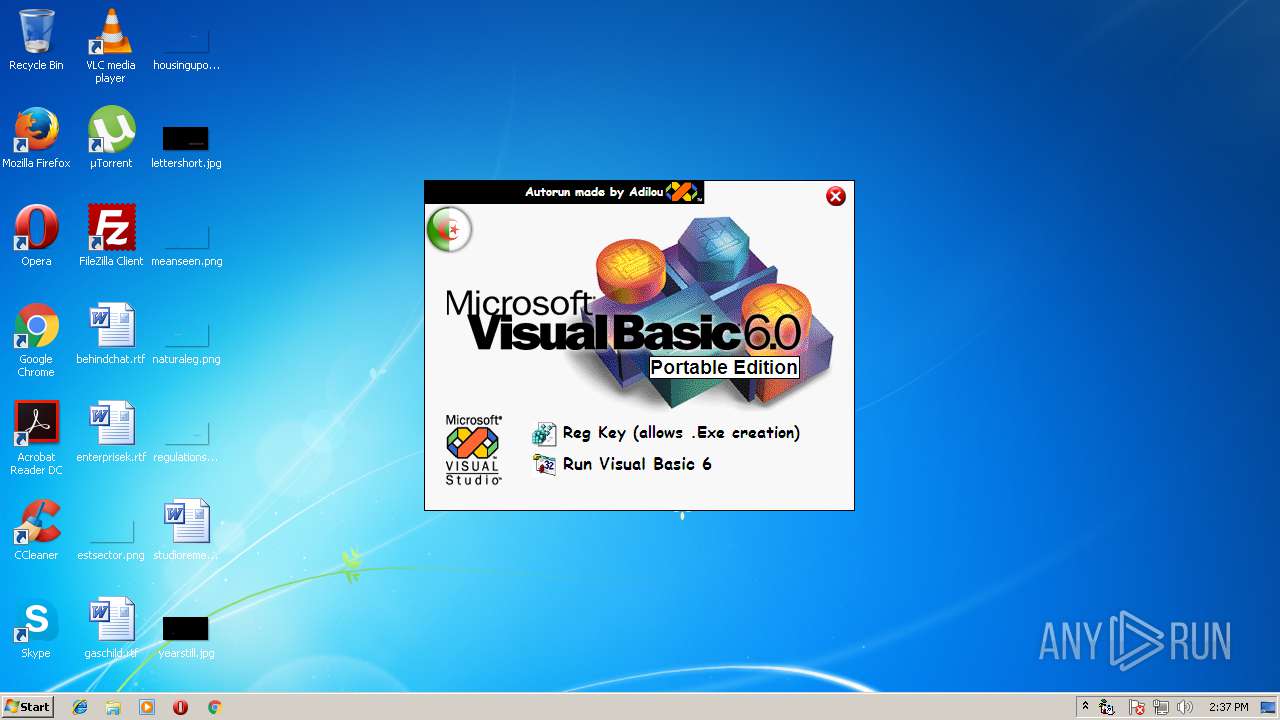
| File name: | Visual Basic 6 Portable.exe |
| Full analysis: | https://app.any.run/tasks/d4cd63c6-9bc6-4e53-a176-f1bf257040d9 |
| Verdict: | No threats detected |
| Analysis date: | April 12, 2018, 13:37:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FA7F4C0C8DB7351B7D2A43ED96F01E42 |
| SHA1: | CF7C0DC9ECA9FF322072D7A8753E6672D65F7CA1 |
| SHA256: | BFD56403A87D93C96F5DD7F175DE276A272C6C78AE2AA8A379C56175A29C3BAE |
| SSDEEP: | 98304:m85pJdgrGxVnbcyVzD2GMMrUirHlbj8QKsMkVd4vTIVPnuIqhgGeHUkYEfg3ROqK:v+EkMPrHlbo/k37VPnuXhgT0kYEfDACN |
MALICIOUS
Application was dropped or rewritten from another process
- autorun.exe (PID: 2340)
SUSPICIOUS
No suspicious indicators.INFO
Dropped object may contain URL's
- Visual Basic 6 Portable.exe (PID: 1516)
Loads rich edit control libraries
- Visual Basic 6 Portable.exe (PID: 1516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.8) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2006:08:04 20:28:08+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 77824 |
| InitializedDataSize: | 99840 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 04-Aug-2006 18:28:08 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000200 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 04-Aug-2006 18:28:08 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00013000 | 0x00012E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.46788 |
.data | 0x00014000 | 0x00007000 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.75622 |
.idata | 0x0001B000 | 0x00001000 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.05399 |
.rsrc | 0x0001C000 | 0x00016ACC | 0x00016C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.58002 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.10885 | 531 | Latin 1 / Western European | Russian - Russia | RT_MANIFEST |
2 | 2.30303 | 296 | Latin 1 / Western European | Process Default Language | RT_ICON |
7 | 3.24143 | 556 | Latin 1 / Western European | Russian - Russia | RT_STRING |
8 | 3.28574 | 946 | Latin 1 / Western European | Russian - Russia | RT_STRING |
9 | 3.04375 | 530 | Latin 1 / Western European | Russian - Russia | RT_STRING |
10 | 3.15563 | 638 | Latin 1 / Western European | Russian - Russia | RT_STRING |
100 | 2.37086 | 34 | Latin 1 / Western European | Process Default Language | RT_GROUP_ICON |
101 | 6.50685 | 84602 | Latin 1 / Western European | Process Default Language | RT_BITMAP |
ASKNEXTVOL | 3.42532 | 642 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
GETPASSWORD1 | 3.29928 | 314 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
COMDLG32.DLL |
GDI32.DLL |
KERNEL32.DLL |
OLE32.DLL |
SHELL32.DLL |
USER32.DLL |
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1516 | "C:\Users\admin\AppData\Local\Temp\Visual Basic 6 Portable.exe" | C:\Users\admin\AppData\Local\Temp\Visual Basic 6 Portable.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2164 | "C:\Users\admin\AppData\Local\Temp\Visual Basic 6 Portable.exe" | C:\Users\admin\AppData\Local\Temp\Visual Basic 6 Portable.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2340 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\autorun.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\autorun.exe | — | Visual Basic 6 Portable.exe | |||||||||||
User: admin Integrity Level: HIGH Description: AutoPlay Application Exit code: 0 Version: 6.0.0.0 Modules
| |||||||||||||||
Total events
405
Read events
399
Write events
6
Delete events
0
Modification events
| (PID) Process: | (1516) Visual Basic 6 Portable.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1516) Visual Basic 6 Portable.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2340) autorun.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
Executable files
15
Suspicious files
1
Text files
8
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Audio\Click1.ogg | ogg | |
MD5:93270C4FA492E4E4EDEE872A2B961DDE | SHA256:25D49CBBD65D48AD462455F1143F73EE997DF8F747E7D2213DAAB18E321C028B | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Docs\Portable.VB6\Mrt7enu.dll | executable | |
MD5:09808BFC59FAFC966E69FDDCDD7A3092 | SHA256:20D86C0E7D081E368458DEF67BDF69472EF3E1BBADEECC65F5D019DFE6249F57 | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Docs\Portable.VB6\Vb6debug.dll | executable | |
MD5:D74F88570F8365918C95E2D764D10EE4 | SHA256:E4A00FEE7B7584553B2A3350C7FCF9383E59AD4592D6F31EADB50AD372D08C7E | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Docs\Portable.VB6\Link.exe | executable | |
MD5:97161E066763A3C5877285BF03FEB3C8 | SHA256:08D3A4C9701C8F6C871B2C48BD74D07422AA1F86E5D9A4DDB2C9BD6A88B857E7 | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Docs\Portable.VB6\Vb6.olb | tlb | |
MD5:376F14DCD409160260FDF98B20FB12DC | SHA256:4109EE488C9E930F8884280526B4C36FFC7CEE03329CAC6A9B8F5864B15C8453 | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Docs\Portable.VB6\Vb6ext.olb | executable | |
MD5:DA80AC130EB2D179BD444160DC4A707C | SHA256:F639D64368206803D695F96714A9F01FE8EC09981F3285C364BBF879DAAB74F3 | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Docs\Portable.VB6\Mspdb60.dll | executable | |
MD5:81F220E337B1696323D8EB7FB321F50D | SHA256:7C90B80D42914562332E28C253415E72A80C6651003D08A9FFDC4BA6E27FC37C | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Docs\Portable.VB6\Dao350.dll | executable | |
MD5:8888BDBD4E118D915D40A11748282BCA | SHA256:A4B20735BE317A924D2E36707BAAF911FBAE890CA53C5044FB506F15D33BCB6D | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Docs\Portable.VB6\Vb6ide.dll | executable | |
MD5:F38A2F55850CEB80250BA657C06F8F5F | SHA256:6670180ABCA14045B4362C683C59F9F2E903CE976746E49599CACD0C8FFD05D2 | |||
| 1516 | Visual Basic 6 Portable.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\AutoPlay\Audio\High1.ogg | ogg | |
MD5:FC2A595F574B1EAD82A6DCF06492C985 | SHA256:EE9A4903A8DF90EFF4C5B65A8073E564A3581CF73772A72EB82396E69932E769 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
teredo.ipv6.microsoft.com |
| whitelisted |