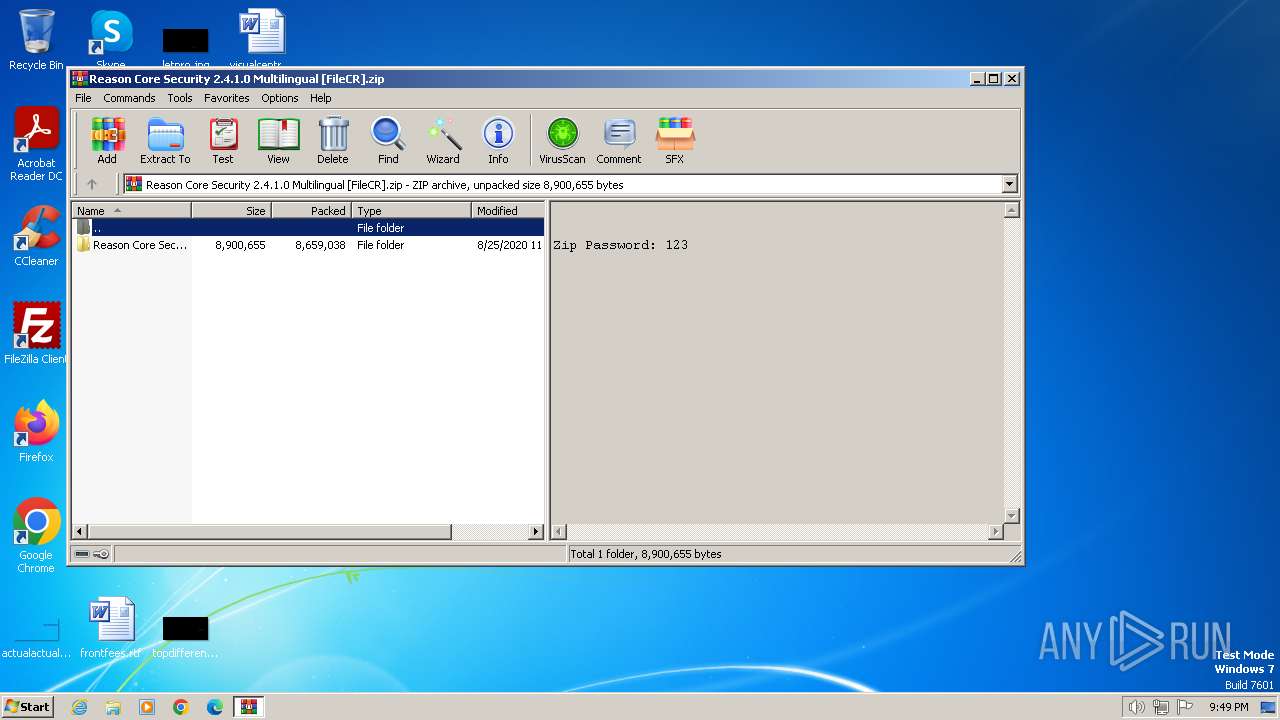
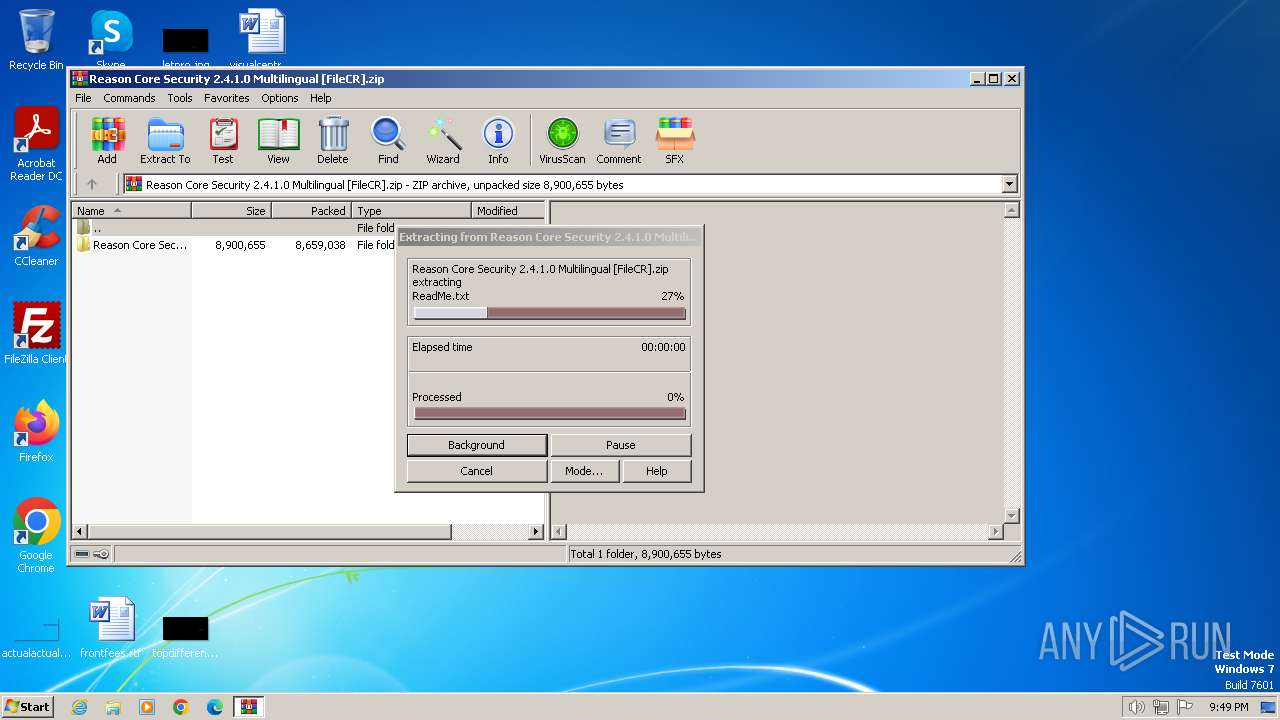
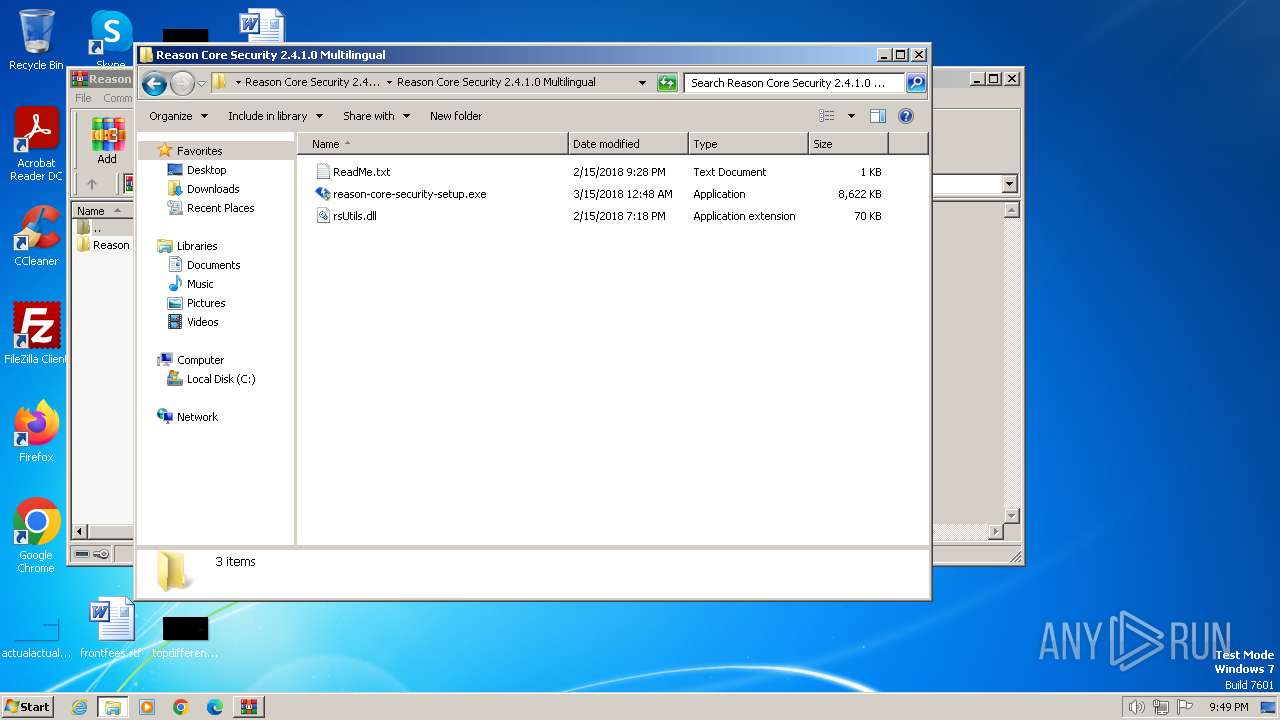
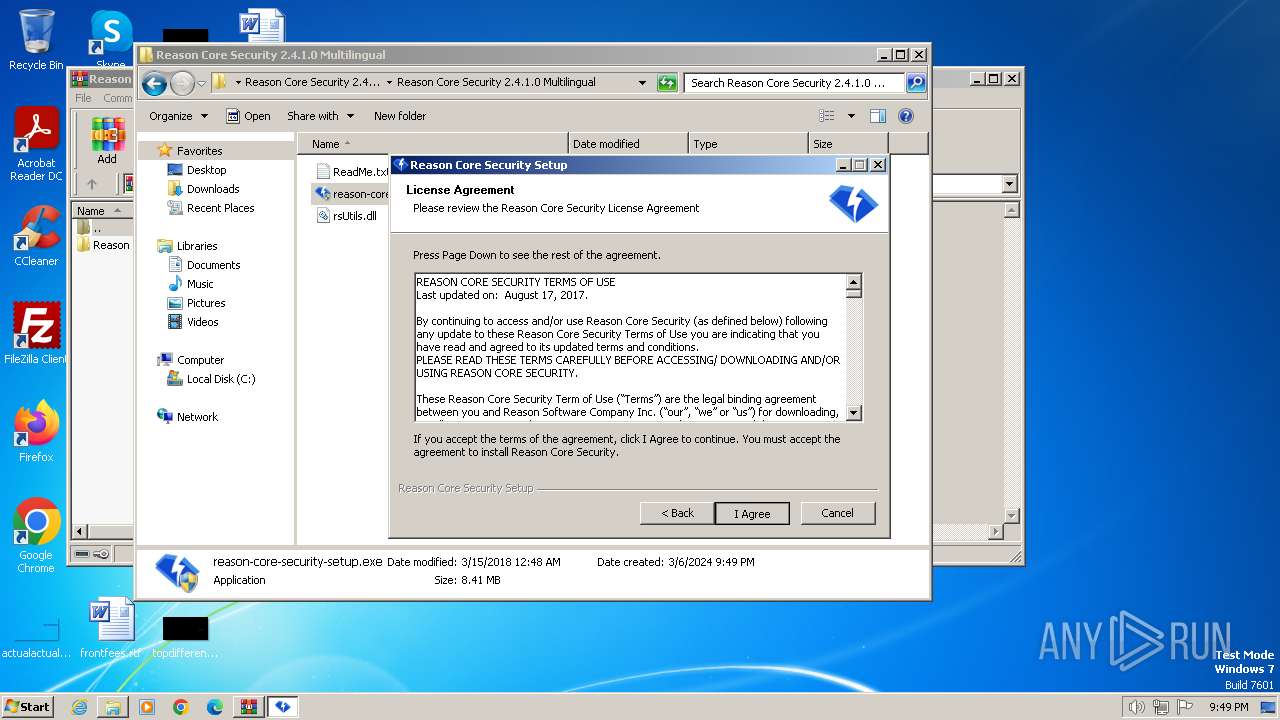
| File name: | Reason Core Security 2.4.1.0 Multilingual [FileCR].zip |
| Full analysis: | https://app.any.run/tasks/6ff64ce4-4ef9-4078-b815-8160cfe940ef |
| Verdict: | Malicious activity |
| Analysis date: | March 06, 2024, 21:49:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 557E9AC53B7059AE57E1B005010DAE42 |
| SHA1: | 1D7F5170C9880731BA8A3CB802D77B1E2273AA5B |
| SHA256: | BFCC061D8EE4DBB0BC576DD5833E8D0D9F398F496EA3A9C6E1AB037C1CEC7F46 |
| SSDEEP: | 98304:8xCFFitUUrs4fKtN8P4g6g3zCf0rD1viYvxr72AtaYL/h8F3DsQ4i9rHQk+YMClg:Q6S+Kepal |
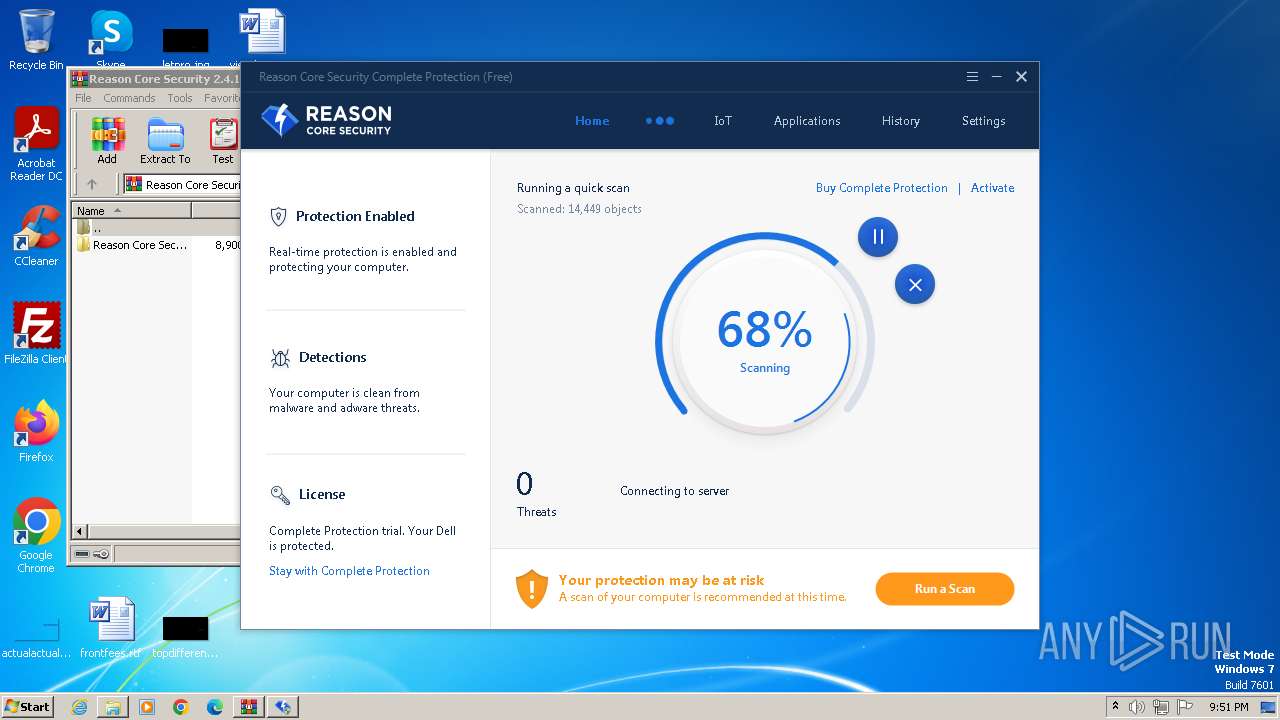
MALICIOUS
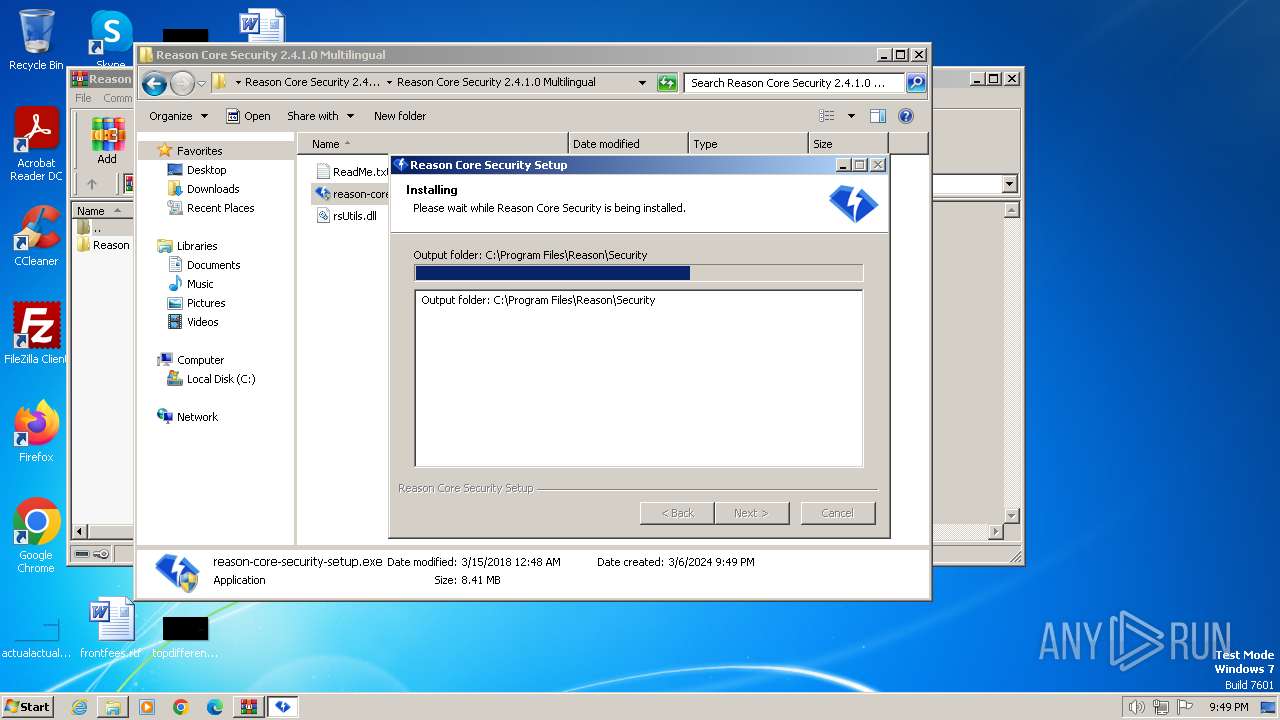
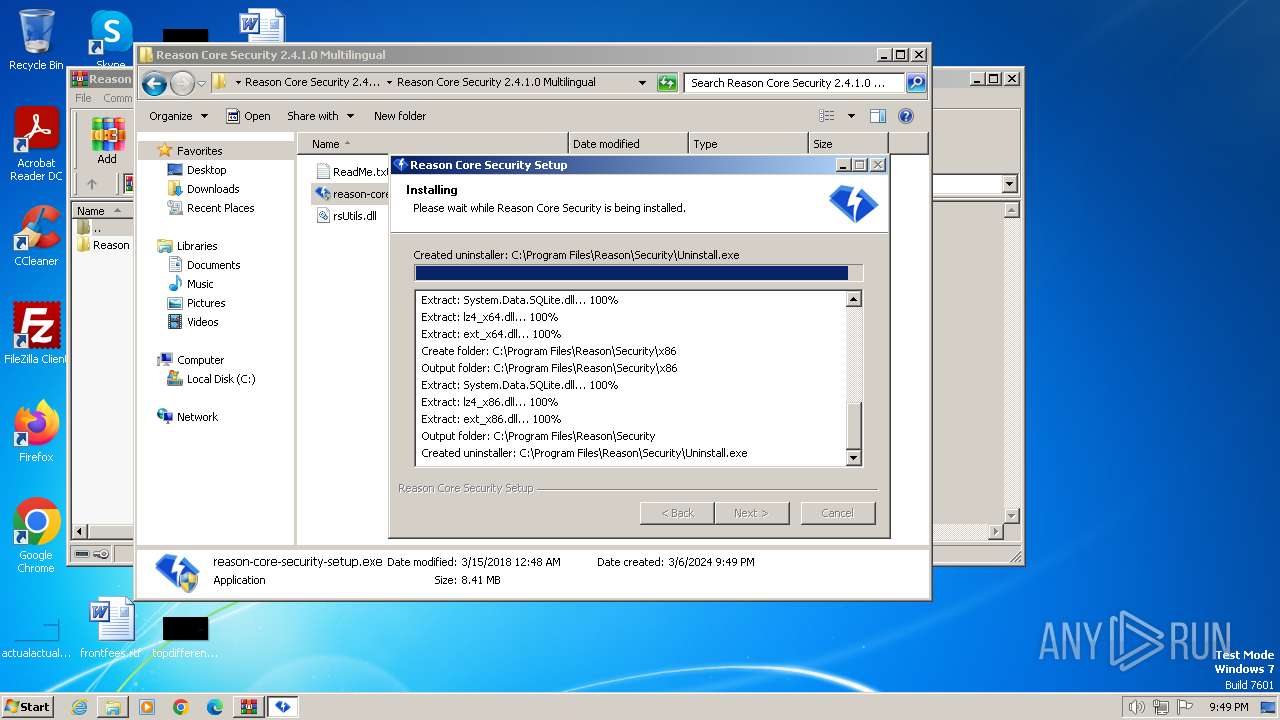
Drops the executable file immediately after the start
- reason-core-security-setup.exe (PID: 2860)
- reason-core-security-setup.exe (PID: 3940)
- rsUI.exe (PID: 968)
Actions looks like stealing of personal data
- rsUI.exe (PID: 968)
Steals credentials from Web Browsers
- rsUI.exe (PID: 968)
SUSPICIOUS
Executable content was dropped or overwritten
- reason-core-security-setup.exe (PID: 2860)
- reason-core-security-setup.exe (PID: 3940)
- rsUI.exe (PID: 968)
Malware-specific behavior (creating "System.dll" in Temp)
- reason-core-security-setup.exe (PID: 3940)
The process creates files with name similar to system file names
- reason-core-security-setup.exe (PID: 3940)
Uses TASKKILL.EXE to kill process
- ns414F.tmp (PID: 1236)
- ns41EC.tmp (PID: 1336)
- ns3F67.tmp (PID: 2208)
- ns4053.tmp (PID: 3684)
- ns40D1.tmp (PID: 2644)
- ns426A.tmp (PID: 1556)
Reads the Internet Settings
- reason-core-security-setup.exe (PID: 3940)
- rsUI.exe (PID: 968)
- rsEngineHelper.exe (PID: 3192)
- rsEngineHelper.exe (PID: 4072)
- rsEngineHelper.exe (PID: 4084)
- rsEngineHelper.exe (PID: 3492)
- rsEngineHelper.exe (PID: 1192)
- rsEngineHelper.exe (PID: 3388)
- rsEngineHelper.exe (PID: 3180)
- rsEngineHelper.exe (PID: 2152)
- rsEngineHelper.exe (PID: 2832)
- rsEngineHelper.exe (PID: 2788)
- rsEngineHelper.exe (PID: 568)
- rsEngineHelper.exe (PID: 2248)
- rsEngineHelper.exe (PID: 2860)
- rsEngineHelper.exe (PID: 3336)
- rsEngineHelper.exe (PID: 2736)
- rsEngineHelper.exe (PID: 2348)
- rsEngineHelper.exe (PID: 3564)
- rsEngineHelper.exe (PID: 3840)
- rsEngineHelper.exe (PID: 3688)
Starts application with an unusual extension
- reason-core-security-setup.exe (PID: 3940)
Creates a software uninstall entry
- reason-core-security-setup.exe (PID: 3940)
Reads the date of Windows installation
- rsUI.exe (PID: 968)
Reads the BIOS version
- rsUI.exe (PID: 968)
Reads security settings of Internet Explorer
- rsUI.exe (PID: 968)
Executes as Windows Service
- rsService.exe (PID: 124)
Reads settings of System Certificates
- rsLggr.exe (PID: 2324)
- rsUI.exe (PID: 968)
- rsEngineHelper.exe (PID: 3192)
- rsEngineHelper.exe (PID: 4084)
- rsEngineHelper.exe (PID: 4072)
- rsEngineHelper.exe (PID: 1192)
- rsEngineHelper.exe (PID: 3492)
- rsEngineHelper.exe (PID: 3388)
- rsEngineHelper.exe (PID: 3180)
- rsEngineHelper.exe (PID: 2832)
- rsEngineHelper.exe (PID: 568)
- rsEngineHelper.exe (PID: 2860)
- rsEngineHelper.exe (PID: 3336)
- rsEngineHelper.exe (PID: 3564)
- rsEngineHelper.exe (PID: 3840)
Searches for installed software
- rsUI.exe (PID: 968)
Suspicious use of NETSH.EXE
- rsUI.exe (PID: 968)
Checks Windows Trust Settings
- rsUI.exe (PID: 968)
Read startup parameters
- rsUI.exe (PID: 968)
Loads DLL from Mozilla Firefox
- rsUI.exe (PID: 968)
Adds/modifies Windows certificates
- rsUI.exe (PID: 968)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3652)
Manual execution by a user
- reason-core-security-setup.exe (PID: 2860)
- reason-core-security-setup.exe (PID: 3932)
Checks supported languages
- reason-core-security-setup.exe (PID: 2860)
- InstallTools.exe (PID: 4000)
- reason-core-security-setup.exe (PID: 3940)
- ns3F67.tmp (PID: 2208)
- ns4053.tmp (PID: 3684)
- ns40D1.tmp (PID: 2644)
- ns41EC.tmp (PID: 1336)
- ns414F.tmp (PID: 1236)
- ns426A.tmp (PID: 1556)
- rsUI.exe (PID: 968)
- rsLggr.exe (PID: 2324)
- rsLggr.exe (PID: 1780)
- rsLggr.exe (PID: 316)
- rsLggr.exe (PID: 296)
- rsService.exe (PID: 3520)
- rsLggr.exe (PID: 552)
- InstallTools.exe (PID: 712)
- rsService.exe (PID: 124)
- rsEngineHelper.exe (PID: 3192)
- rsEngineHelper.exe (PID: 4084)
- rsEngineHelper.exe (PID: 3492)
- rsEngineHelper.exe (PID: 4072)
- rsEngineHelper.exe (PID: 3388)
- rsEngineHelper.exe (PID: 1192)
- rscp_setup.exe (PID: 3056)
- rsLggr.exe (PID: 4056)
- rsEngineHelper.exe (PID: 3180)
- rsEngineHelper.exe (PID: 2832)
- rsEngineHelper.exe (PID: 2788)
- rsEngineHelper.exe (PID: 568)
- rsEngineHelper.exe (PID: 2152)
- rsEngineHelper.exe (PID: 2248)
- rsEngineHelper.exe (PID: 2860)
- rsEngineHelper.exe (PID: 3336)
- rsEngineHelper.exe (PID: 2736)
- rsEngineHelper.exe (PID: 3564)
- rsEngineHelper.exe (PID: 2348)
- rsEngineHelper.exe (PID: 3840)
- rsEngineHelper.exe (PID: 3688)
Reads the computer name
- InstallTools.exe (PID: 4000)
- reason-core-security-setup.exe (PID: 2860)
- reason-core-security-setup.exe (PID: 3940)
- rsUI.exe (PID: 968)
- rsService.exe (PID: 3520)
- InstallTools.exe (PID: 712)
- rsLggr.exe (PID: 2324)
- rsService.exe (PID: 124)
- rsEngineHelper.exe (PID: 3192)
- rsEngineHelper.exe (PID: 4072)
- rsEngineHelper.exe (PID: 4084)
- rsEngineHelper.exe (PID: 3492)
- rsEngineHelper.exe (PID: 1192)
- rscp_setup.exe (PID: 3056)
- rsEngineHelper.exe (PID: 3388)
- rsEngineHelper.exe (PID: 3180)
- rsEngineHelper.exe (PID: 2152)
- rsEngineHelper.exe (PID: 2832)
- rsEngineHelper.exe (PID: 2788)
- rsEngineHelper.exe (PID: 568)
- rsEngineHelper.exe (PID: 2248)
- rsEngineHelper.exe (PID: 2860)
- rsEngineHelper.exe (PID: 3336)
- rsEngineHelper.exe (PID: 3564)
- rsEngineHelper.exe (PID: 2736)
- rsEngineHelper.exe (PID: 2348)
- rsEngineHelper.exe (PID: 3840)
- rsEngineHelper.exe (PID: 3688)
Create files in a temporary directory
- reason-core-security-setup.exe (PID: 2860)
- reason-core-security-setup.exe (PID: 3940)
- rsUI.exe (PID: 968)
Reads Environment values
- InstallTools.exe (PID: 4000)
- reason-core-security-setup.exe (PID: 3940)
- InstallTools.exe (PID: 712)
- rsUI.exe (PID: 968)
- rsService.exe (PID: 124)
- rsEngineHelper.exe (PID: 3192)
- rsEngineHelper.exe (PID: 4072)
- rsEngineHelper.exe (PID: 4084)
- rsEngineHelper.exe (PID: 3492)
- rsEngineHelper.exe (PID: 1192)
- rsEngineHelper.exe (PID: 3388)
- rsEngineHelper.exe (PID: 3180)
- rsEngineHelper.exe (PID: 2152)
- rsEngineHelper.exe (PID: 2832)
- rsEngineHelper.exe (PID: 2788)
- rsEngineHelper.exe (PID: 2248)
- rsEngineHelper.exe (PID: 2860)
- rsEngineHelper.exe (PID: 568)
- rsEngineHelper.exe (PID: 2348)
- rsEngineHelper.exe (PID: 3336)
- rsEngineHelper.exe (PID: 2736)
- rsEngineHelper.exe (PID: 3564)
- rsEngineHelper.exe (PID: 3840)
- rsEngineHelper.exe (PID: 3688)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3652)
Creates files in the program directory
- reason-core-security-setup.exe (PID: 3940)
- rsUI.exe (PID: 968)
- rsLggr.exe (PID: 2324)
- rsService.exe (PID: 3520)
- rsEngineHelper.exe (PID: 3192)
Checks proxy server information
- reason-core-security-setup.exe (PID: 3940)
- rsUI.exe (PID: 968)
Reads the machine GUID from the registry
- rsUI.exe (PID: 968)
- rsService.exe (PID: 3520)
- rsService.exe (PID: 124)
- rsLggr.exe (PID: 2324)
- rsEngineHelper.exe (PID: 3192)
- rsEngineHelper.exe (PID: 4072)
- rsEngineHelper.exe (PID: 4084)
- rsEngineHelper.exe (PID: 3492)
- rsEngineHelper.exe (PID: 1192)
- rsEngineHelper.exe (PID: 3388)
- rsEngineHelper.exe (PID: 3180)
- rsEngineHelper.exe (PID: 2152)
- rsEngineHelper.exe (PID: 2832)
- rsEngineHelper.exe (PID: 2788)
- rsEngineHelper.exe (PID: 568)
- rsEngineHelper.exe (PID: 2248)
- rsEngineHelper.exe (PID: 2860)
- rsEngineHelper.exe (PID: 2348)
- rsEngineHelper.exe (PID: 3336)
- rsEngineHelper.exe (PID: 2736)
- rsEngineHelper.exe (PID: 3564)
- rsEngineHelper.exe (PID: 3840)
- rsEngineHelper.exe (PID: 3688)
Reads product name
- rsUI.exe (PID: 968)
- rsEngineHelper.exe (PID: 3192)
Reads the software policy settings
- rsLggr.exe (PID: 2324)
- rsUI.exe (PID: 968)
- rsEngineHelper.exe (PID: 3192)
- rsEngineHelper.exe (PID: 4084)
- rsEngineHelper.exe (PID: 4072)
- rsEngineHelper.exe (PID: 1192)
- rsEngineHelper.exe (PID: 3492)
- rsEngineHelper.exe (PID: 3388)
- rsEngineHelper.exe (PID: 3180)
- rsEngineHelper.exe (PID: 2832)
- rsEngineHelper.exe (PID: 568)
- rsEngineHelper.exe (PID: 2860)
- rsEngineHelper.exe (PID: 3336)
- rsEngineHelper.exe (PID: 3564)
- rsEngineHelper.exe (PID: 3840)
Reads Microsoft Office registry keys
- rsUI.exe (PID: 968)
Process checks whether UAC notifications are on
- rsEngineHelper.exe (PID: 3192)
Creates files or folders in the user directory
- rsUI.exe (PID: 968)
Reads mouse settings
- rsUI.exe (PID: 968)
Uses BITSADMIN.EXE
- rsUI.exe (PID: 968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:08:25 03:08:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Reason Core Security 2.4.1.0 Multilingual/ |
Total processes
121
Monitored processes
51
Malicious processes
17
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
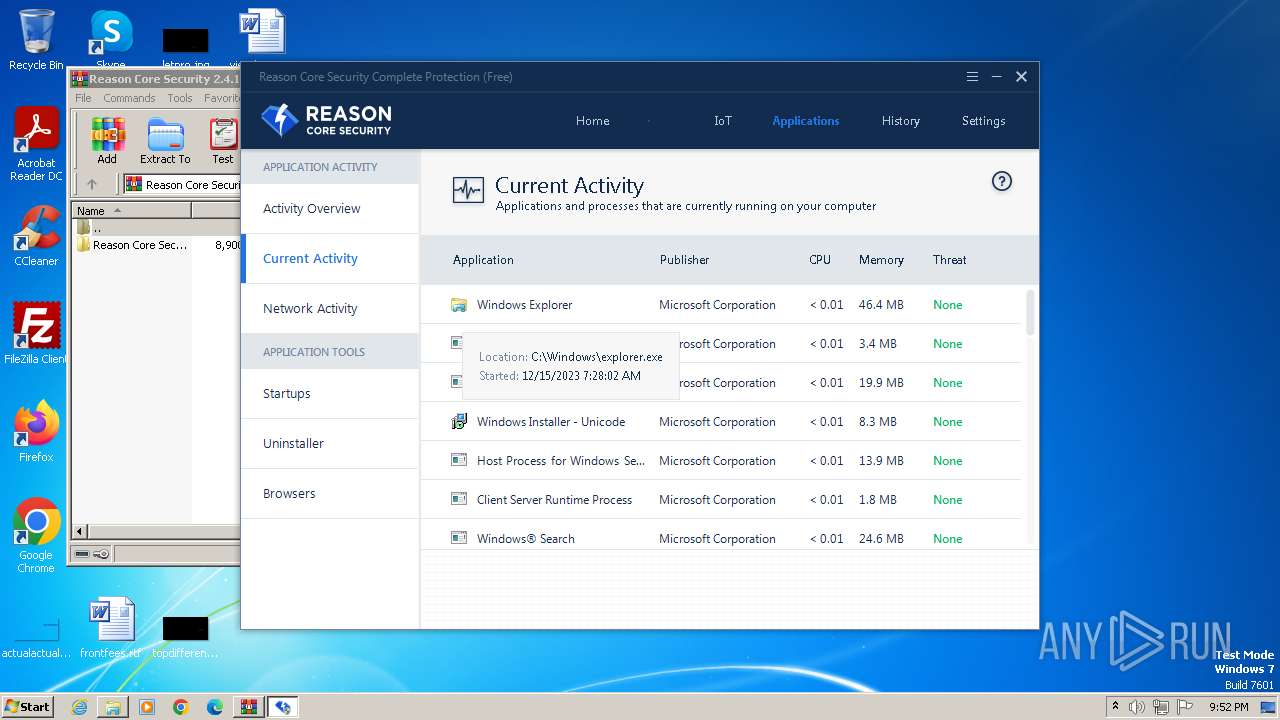
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Reason\Security\rsService.exe" | C:\Program Files\Reason\Security\rsService.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: Reason Core Security Service Exit code: 0 Version: 2.4.1.0 Modules
| |||||||||||||||
| 296 | "C:\Program Files\Reason\Security\rsLggr.exe" | C:\Program Files\Reason\Security\rsLggr.exe | — | rsUI.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Reason\Security\rsLggr.exe" | C:\Program Files\Reason\Security\rsLggr.exe | — | rsUI.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Reason\Security\rsLggr.exe" | C:\Program Files\Reason\Security\rsLggr.exe | — | rsUI.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Reason\Security\rsEngineHelper.exe" uploadString url:https://api1.reasonsecurity.com/api.ashx?RETRYATTEMPT=1&method=gSR token:592ce0bf-06e8-4330-89d3-09d2f868cef4 method:scanresults product:RS | C:\Program Files\Reason\Security\rsEngineHelper.exe | rsUI.exe | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: Reason Security Engine Helper Exit code: 0 Version: 2.0.3.1 Modules
| |||||||||||||||
| 712 | "C:\Users\admin\AppData\Local\Temp\InstallTools.exe" "C:\Users\admin\AppData\Local\Temp\Reason Core Security 2.4.1.0 Multilingual [FileCR]\Reason Core Security 2.4.1.0 Multilingual\reason-core-security-setup.exe" Software\Reason\Security INSNDE "C:\Users\admin\AppData\Local\Temp\Reason Core Security 2.4.1.0 Multilingual [FileCR]\Reason Core Security 2.4.1.0 Multilingual\reason-core-security-setup.exe" /mode=f /url=logs.reasonsecurity.com/event /product=RS | C:\Users\admin\AppData\Local\Temp\InstallTools.exe | — | reason-core-security-setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Reason\Security\rsUI.exe" | C:\Program Files\Reason\Security\rsUI.exe | reason-core-security-setup.exe | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: Reason Core Security Exit code: 0 Version: 2.4.1.0 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Reason\Security\rsEngineHelper.exe" uploadString url:https://api1.reasonsecurity.com/api.ashx?RETRYATTEMPT=1&method=iSA&signatures=927104&v=2.0.3.2&p=Security&sigver=1 token:9f4f21fa-81d0-42fd-aeaa-0ee46a941fe0 method:signaturesavail product:RS | C:\Program Files\Reason\Security\rsEngineHelper.exe | rsUI.exe | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: Reason Security Engine Helper Exit code: 0 Version: 2.0.3.1 Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\ns414F.tmp" taskkill /f /im rsEngineHelper.exe | C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\ns414F.tmp | — | reason-core-security-setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 128 Modules
| |||||||||||||||
| 1336 | "C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\ns41EC.tmp" taskkill /f /im rsLggr.exe | C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\ns41EC.tmp | — | reason-core-security-setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 128 Modules
| |||||||||||||||
Total events
224 337
Read events
223 848
Write events
475
Delete events
14
Modification events
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Reason Core Security 2.4.1.0 Multilingual [FileCR].zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
32
Suspicious files
33
Text files
531
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2860 | reason-core-security-setup.exe | C:\Users\admin\AppData\Local\Temp\reason-core-security-setup.exe | executable | |
MD5:0BB4D6CD294E33ECE7DAC8660AE80FC5 | SHA256:309E6F0B926D8E224DC2DBCF4BFAACDC53615EC40EB12B6B7C85A5CF47A5C056 | |||
| 3940 | reason-core-security-setup.exe | C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\modern-wizard.bmp | image | |
MD5:11960430353F5727CB95B7189CDD6187 | SHA256:B3250A80B201D9652DC06A86BAE1F02C23EE2F707AFDC5F08C6075DD4B18C6C1 | |||
| 3940 | reason-core-security-setup.exe | C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\System.dll | executable | |
MD5:17ED1C86BD67E78ADE4712BE48A7D2BD | SHA256:BD046E6497B304E4EA4AB102CAB2B1F94CE09BDE0EEBBA4C59942A732679E4EB | |||
| 3940 | reason-core-security-setup.exe | C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\modern-header.bmp | image | |
MD5:071D47FA9D9A8FBA12E820FED8CBD221 | SHA256:22FAA11A3606FF4D6A0F6F3ED07EF6D908C2A99FB1B58B6C95937DF3411C2BF3 | |||
| 3940 | reason-core-security-setup.exe | C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\nsDialogs.dll | executable | |
MD5:42B064366F780C1F298FA3CB3AEAE260 | SHA256:C13104552B8B553159F50F6E2CA45114493397A6FA4BF2CBB960C4A2BBD349AB | |||
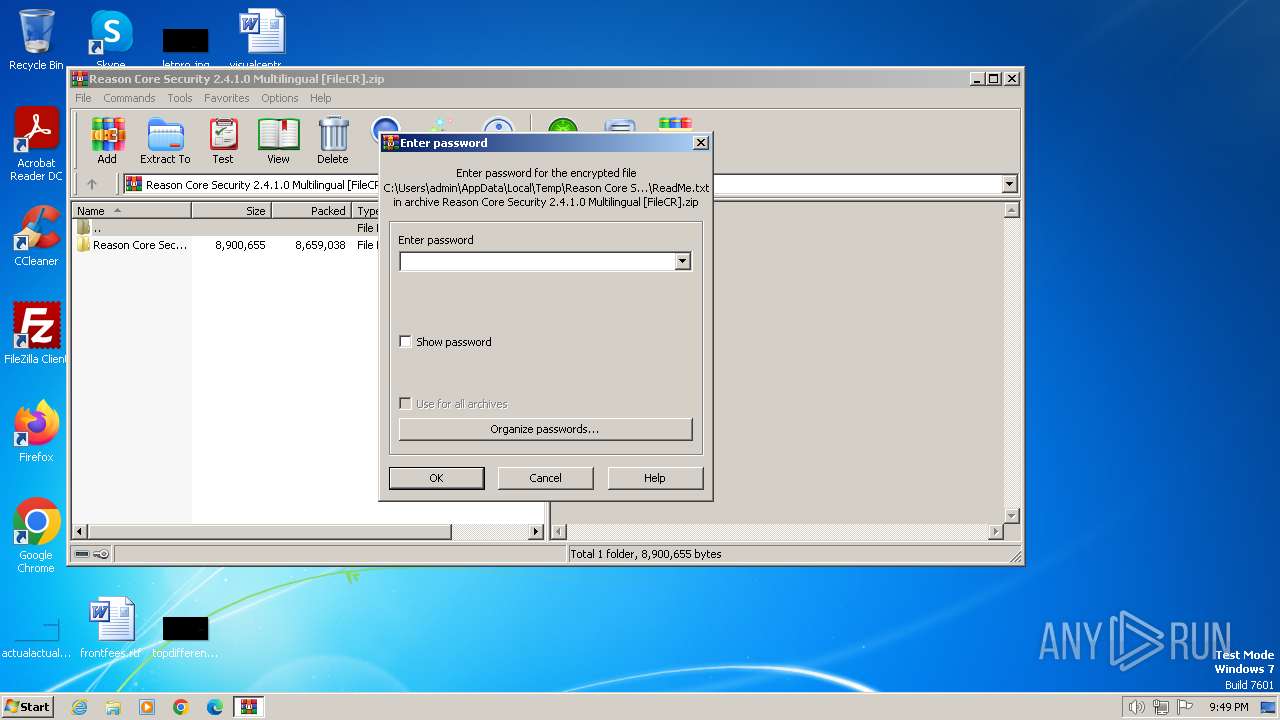
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Reason Core Security 2.4.1.0 Multilingual [FileCR]\Reason Core Security 2.4.1.0 Multilingual\ReadMe.txt | text | |
MD5:10AE60EBC7F25C6757D4340AC68CDCF9 | SHA256:4C70646A9F4633D1DEAAB6BA23B78A67C0108982D4125A96742EBA47EFEE6031 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Reason Core Security 2.4.1.0 Multilingual [FileCR]\Reason Core Security 2.4.1.0 Multilingual\rsUtils.dll | executable | |
MD5:DFAEA0C5E4F55098D6467657594CB96F | SHA256:F1D2023E074DA05D25F8B680D56B667FB769CDDE4955A5DBA45E3EE8A04C17C1 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Reason Core Security 2.4.1.0 Multilingual [FileCR]\Reason Core Security 2.4.1.0 Multilingual\reason-core-security-setup.exe | executable | |
MD5:B47664651FA758CE34979354F88CB014 | SHA256:1BBB97E1B44BCA5C37AB718092F30BD8DEA363126139F280CED23379E5C856C0 | |||
| 3940 | reason-core-security-setup.exe | C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\ns3F67.tmp | executable | |
MD5:B55F7F1B17C39018910C23108F929082 | SHA256:C4C6FE032F3CD8B31528D7B99661F85EE22CB78746AEE98EC568431D4F5043F7 | |||
| 3940 | reason-core-security-setup.exe | C:\Users\admin\AppData\Local\Temp\nsp3276.tmp\nsisdl.dll | executable | |
MD5:A9A134D9E9A8C5A30277282AF1F14A81 | SHA256:8C97868E7237B5E6973C72DA16CB534E80EA327E366CD15D45E16FAFECFC2C77 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
108
DNS requests
29
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3940 | reason-core-security-setup.exe | GET | 200 | 52.21.131.106:80 | http://logs.reasonsecurity.com/event?Eventname=Installer&status=Start&Product=Security&i_data=&ruserid=&tag=2.0.50727&OSVersion=6.1.0.0&version=2.4.1.0&hostapp_version=2.4.1.0 | unknown | — | — | unknown |
3940 | reason-core-security-setup.exe | GET | 200 | 52.21.131.106:80 | http://logs.reasonsecurity.com/event?Eventname=Installer&status=Finish&Product=Security&i_data=&ruserid=&OSVersion=6.1.0.0&version=2.4.1.0&hostapp_version=2.4.1.0 | unknown | — | — | unknown |
968 | rsUI.exe | GET | 301 | 52.222.214.2:80 | http://cdn.reasonsecurity.com/resources/installers/protection/rscp_setup.exe | unknown | html | 167 b | unknown |
968 | rsUI.exe | GET | 304 | 92.122.50.70:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cf99a4f054be1c61 | unknown | — | — | unknown |
3056 | rscp_setup.exe | POST | 403 | 13.248.169.48:80 | http://logs.isrtb.com/bulk_safe | unknown | — | — | unknown |
968 | rsUI.exe | GET | 304 | 92.122.50.70:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?19819c000474ec49 | unknown | — | — | unknown |
968 | rsUI.exe | GET | 200 | 184.86.251.206:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
968 | rsUI.exe | GET | 200 | 23.33.233.193:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | binary | 1.05 Kb | unknown |
968 | rsUI.exe | GET | 200 | 184.86.251.206:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | binary | 767 b | unknown |
968 | rsUI.exe | GET | 200 | 184.86.251.206:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | binary | 519 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3940 | reason-core-security-setup.exe | 52.21.131.106:80 | logs.reasonsecurity.com | AMAZON-AES | US | unknown |
2324 | rsLggr.exe | 52.21.131.106:443 | logs.reasonsecurity.com | AMAZON-AES | US | unknown |
968 | rsUI.exe | 104.22.0.235:443 | api.reasonsecurity.com | CLOUDFLARENET | — | unknown |
968 | rsUI.exe | 172.67.9.68:443 | api1.reasonsecurity.com | CLOUDFLARENET | US | unknown |
3192 | rsEngineHelper.exe | 172.67.9.68:443 | api1.reasonsecurity.com | CLOUDFLARENET | US | unknown |
4072 | rsEngineHelper.exe | 104.22.0.235:443 | api.reasonsecurity.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
logs.reasonsecurity.com |
| unknown |
api.reasonsecurity.com |
| unknown |
api1.reasonsecurity.com |
| unknown |
cdn.reasonsecurity.com |
| shared |
logs.isrtb.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
s2.symcb.com |
| whitelisted |
s1.symcb.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
968 | rsUI.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
4 ETPRO signatures available at the full report