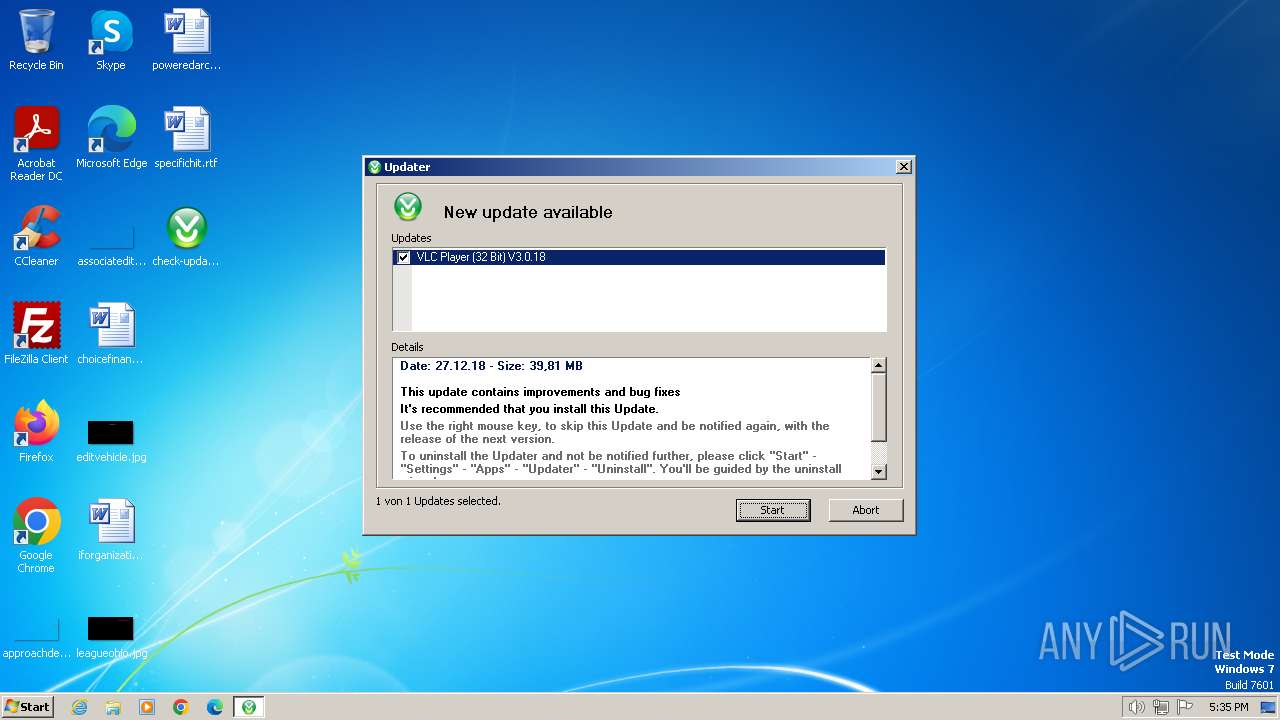
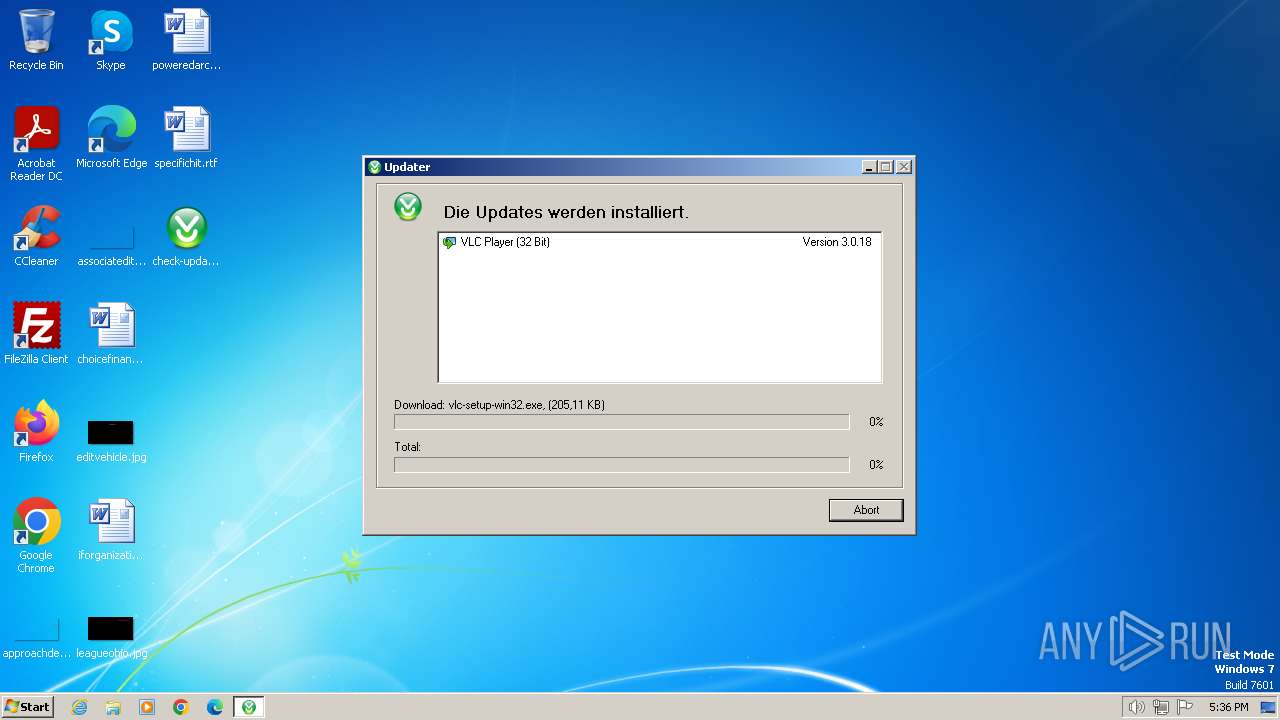
| File name: | check-update.exe |
| Full analysis: | https://app.any.run/tasks/ea6d3ebe-7b28-42a5-821d-9799f2ea15e7 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2024, 17:35:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6DAE4EBB66DC2A5B1F9D14B4AA8787BA |
| SHA1: | 3F6457A81C8FC2EE47456C03AB28B55B7ADA13D7 |
| SHA256: | BFC9F2E5D39F869702F7A080BE369699264CB82A65FF6C39C1F6951D294A8687 |
| SSDEEP: | 12288:cNnTT3AsoS22wwl/lLiItZUj4neHB5em3ske71M:cNnTTQsVxw+/lLiQjnenqM |
MALICIOUS
No malicious indicators.SUSPICIOUS
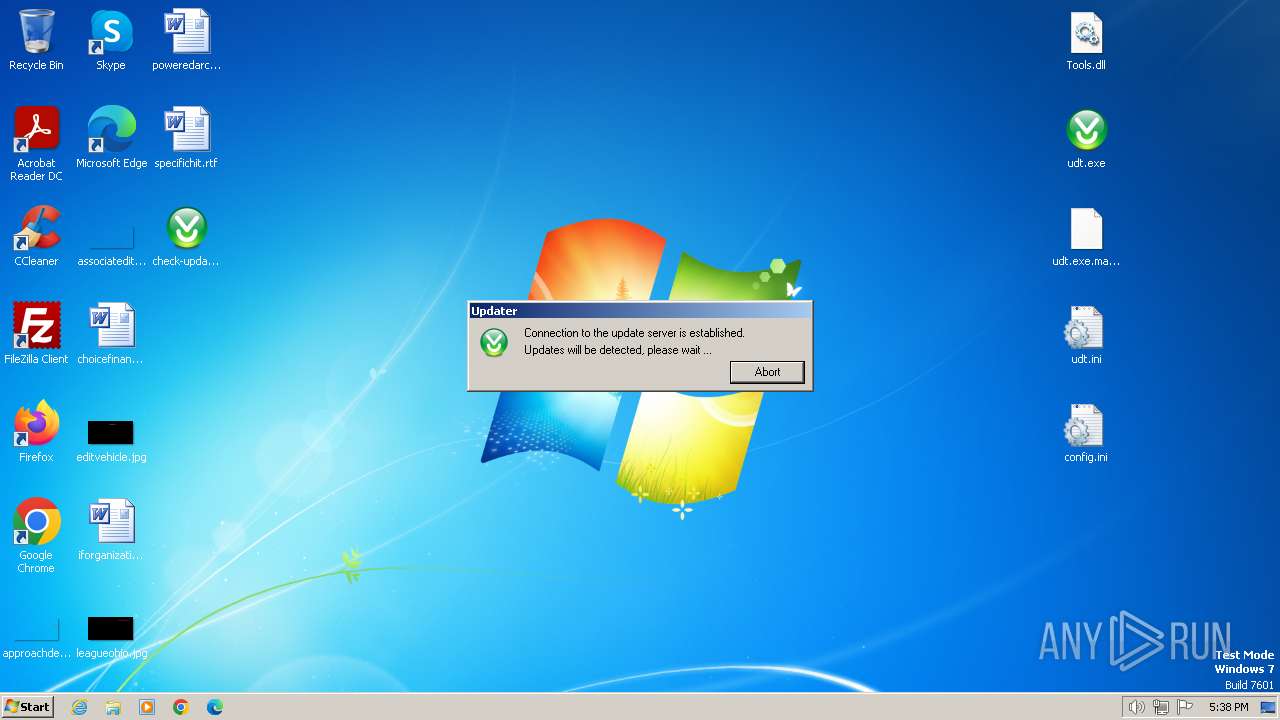
Reads the Internet Settings
- check-update.exe (PID: 120)
- udt.exe (PID: 2036)
- udt.exe (PID: 2832)
- check-update.exe (PID: 2840)
- udt.exe (PID: 4088)
Executing commands from a ".bat" file
- udt.exe (PID: 2036)
- udt.exe (PID: 2832)
- udt.exe (PID: 4088)
Starts CMD.EXE for commands execution
- udt.exe (PID: 2036)
- udt.exe (PID: 2832)
- udt.exe (PID: 4088)
INFO
Checks supported languages
- check-update.exe (PID: 120)
- udt.exe (PID: 2036)
- check-update.exe (PID: 2840)
- udt.exe (PID: 2832)
- udt.exe (PID: 4088)
Drops the executable file immediately after the start
- check-update.exe (PID: 120)
- udt.exe (PID: 2036)
- check-update.exe (PID: 2840)
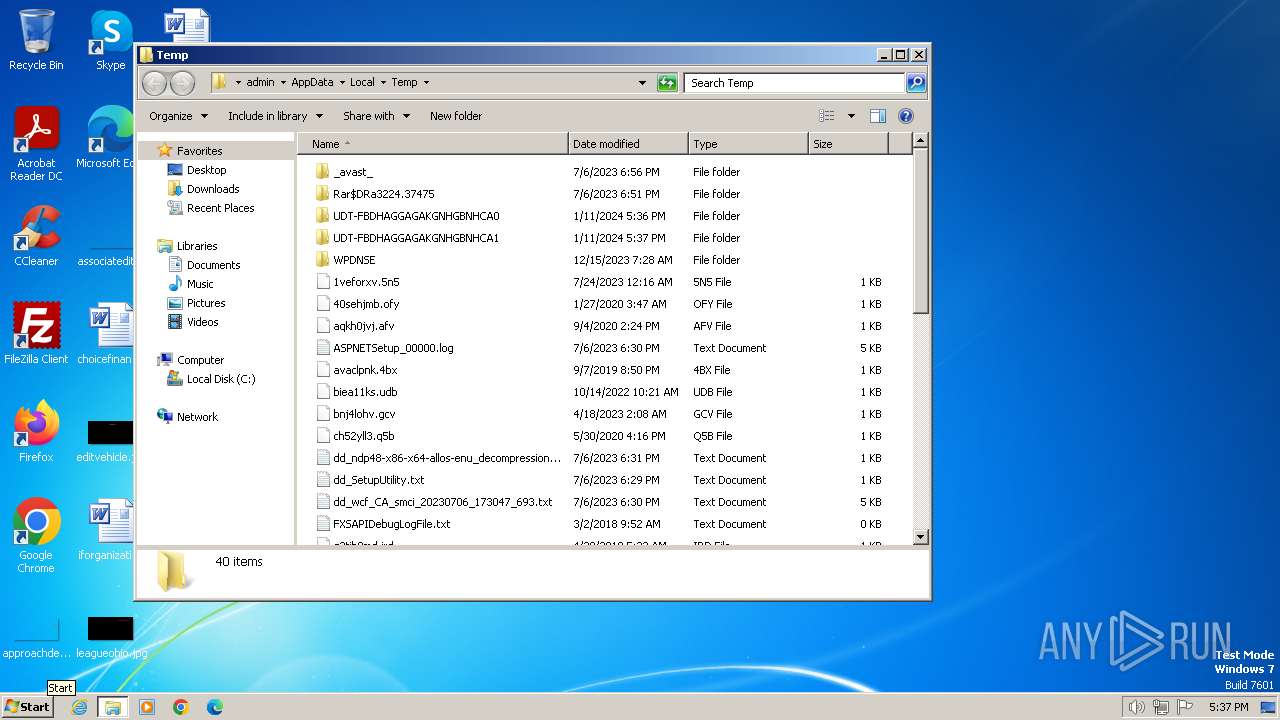
Create files in a temporary directory
- check-update.exe (PID: 120)
- udt.exe (PID: 2036)
- check-update.exe (PID: 2840)
- udt.exe (PID: 2832)
- udt.exe (PID: 4088)
Reads the computer name
- check-update.exe (PID: 120)
- udt.exe (PID: 2036)
- check-update.exe (PID: 2840)
- udt.exe (PID: 2832)
- udt.exe (PID: 4088)
Checks proxy server information
- udt.exe (PID: 2036)
- udt.exe (PID: 2832)
Reads the machine GUID from the registry
- udt.exe (PID: 2036)
- udt.exe (PID: 2832)
Creates files or folders in the user directory
- udt.exe (PID: 2036)
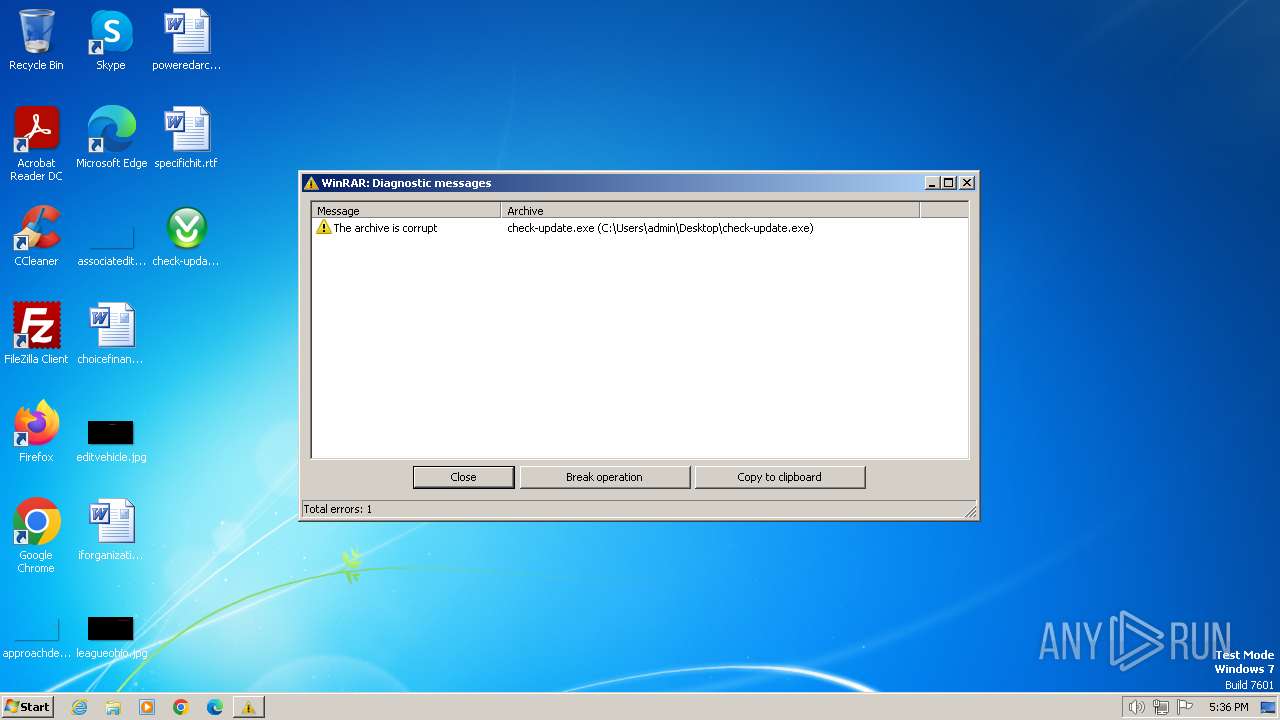
Manual execution by a user
- WinRAR.exe (PID: 1316)
- verclsid.exe (PID: 2340)
- notepad.exe (PID: 2636)
- check-update.exe (PID: 2840)
- udt.exe (PID: 4088)
- notepad.exe (PID: 3664)
- notepad.exe (PID: 3656)
Process requests binary or script from the Internet
- udt.exe (PID: 2036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:08:21 16:30:02+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 32768 |
| InitializedDataSize: | 225280 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x80b6 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.4.500.0 |
| ProductVersionNumber: | 2.7.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | German |
| CharacterSet: | Unicode |
| FileDescription: | Updater |
| FileVersion: | 2. 4. 500. 0 |
| LegalCopyright: | Aller Media e.K. |
| OriginalFileName: | Setup.EXE |
| ProductVersion: | 1,0 |
| CompanyName: | Aller Media e.K. |
| ProductName: | Updater |
| Comments: | Updater |
Total processes
59
Monitored processes
13
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\Desktop\check-update.exe" | C:\Users\admin\Desktop\check-update.exe | — | explorer.exe | |||||||||||
User: admin Company: Aller Media e.K. Integrity Level: MEDIUM Description: Updater Exit code: 0 Version: 2. 4. 500. 0 Modules
| |||||||||||||||
| 584 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\AKIDelST.bat" " | C:\Windows\System32\cmd.exe | — | udt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1316 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\check-update.exe" C:\Users\admin\Desktop\check-update\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 3 Version: 5.91.0 Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA0\udt.exe" | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA0\udt.exe | check-update.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: UDT Exit code: 0 Version: 2.4.500 Modules
| |||||||||||||||
| 2340 | "C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\System32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
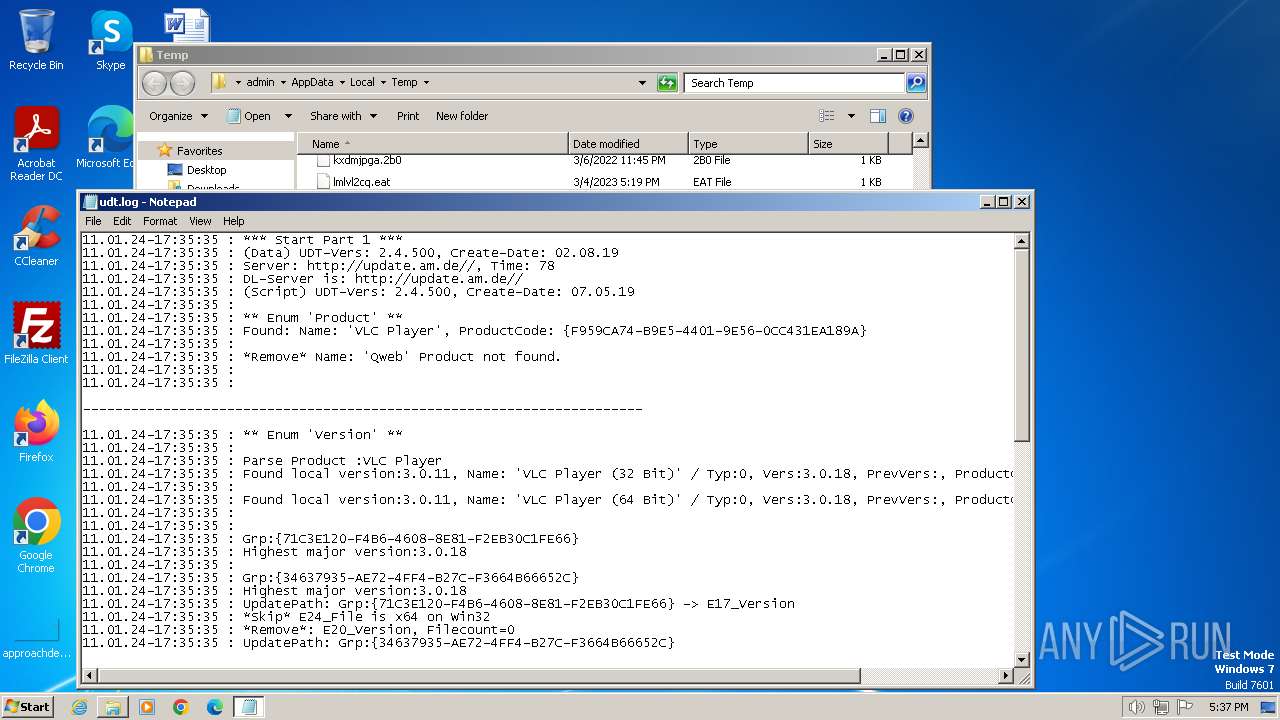
| 2636 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\udt.log | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2832 | "C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA1\udt.exe" | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA1\udt.exe | check-update.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: UDT Exit code: 0 Version: 2.4.500 Modules
| |||||||||||||||
| 2840 | "C:\Users\admin\Desktop\check-update.exe" | C:\Users\admin\Desktop\check-update.exe | — | explorer.exe | |||||||||||
User: admin Company: Aller Media e.K. Integrity Level: MEDIUM Description: Updater Exit code: 0 Version: 2. 4. 500. 0 Modules
| |||||||||||||||
| 3540 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\AKIDelST.bat" " | C:\Windows\System32\cmd.exe | — | udt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3656 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\config.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 592
Read events
4 505
Write events
87
Delete events
0
Modification events
| (PID) Process: | (120) check-update.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (120) check-update.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (120) check-update.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (120) check-update.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2036) udt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2036) udt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2036) udt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2036) udt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2036) udt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2036) udt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
10
Suspicious files
0
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 120 | check-update.exe | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA0\A2 | xml | |
MD5:AE6A394FCD53586B0875F4B40CC511BC | SHA256:2264ACAC265E8EEF34A7D37E18292A1550AB346FDFCC9F5A262E6A2C59AC4CD6 | |||
| 120 | check-update.exe | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA0\A0 | executable | |
MD5:5B1E449FBBA833D603725B82F49E26A8 | SHA256:7FB83AEDD630DE1E0C4A766837B85ACD65A1B61C6A6F66ED2583CAAB318ECCCC | |||
| 120 | check-update.exe | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA0\Tools.dll | executable | |
MD5:C0B8010D872F15C1FF0CA8063600BC9D | SHA256:2F5296C5FCC67F78CEE6EADB1D87201772602F94216D19F857140E51E2F691FF | |||
| 120 | check-update.exe | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA0\udt.ini | xml | |
MD5:C1688359F3C3CC7331417943CCD02517 | SHA256:7AD88EA8F937D54224FF31A06D11AF90F03338302E31BA7BFC1142023AD3F43F | |||
| 120 | check-update.exe | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA0\A1 | xml | |
MD5:C1688359F3C3CC7331417943CCD02517 | SHA256:7AD88EA8F937D54224FF31A06D11AF90F03338302E31BA7BFC1142023AD3F43F | |||
| 120 | check-update.exe | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA0\udt.exe.manifest | xml | |
MD5:AE6A394FCD53586B0875F4B40CC511BC | SHA256:2264ACAC265E8EEF34A7D37E18292A1550AB346FDFCC9F5A262E6A2C59AC4CD6 | |||
| 2036 | udt.exe | C:\Users\admin\AppData\Local\Temp\AKIDelST.bat | text | |
MD5:90E82ED987E1A130D2A022D22A54C9D2 | SHA256:309C1B7946663FEEDD04F7934114DFE55EF1D987A97265B16DC2FA6F9BCA4CBE | |||
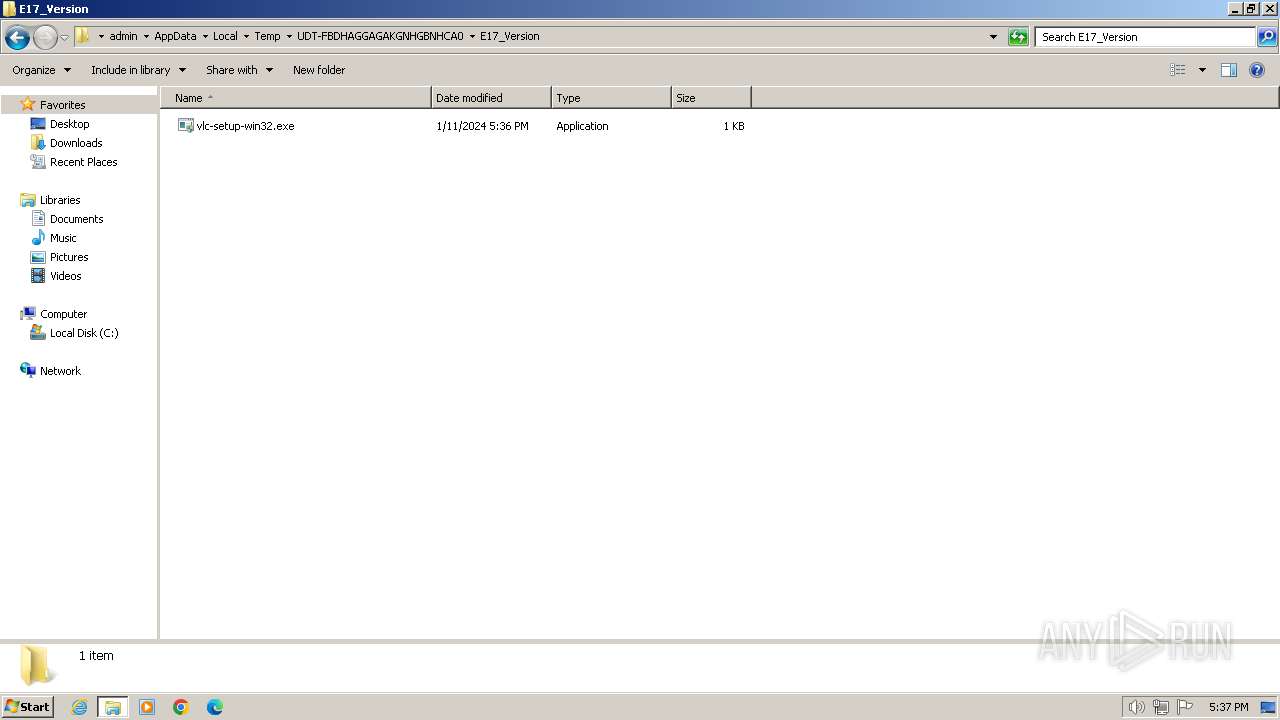
| 2036 | udt.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\vlc-setup-win32[1].exe | executable | |
MD5:6EB090129BDF8C2CBEE18CB81A37CF33 | SHA256:64B08BCC70A0CBA5CF4B753DBC621E0CDBBDC4FD32E80135AF47D9F16DBA5F46 | |||
| 2840 | check-update.exe | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA1\udt.exe.manifest | xml | |
MD5:AE6A394FCD53586B0875F4B40CC511BC | SHA256:2264ACAC265E8EEF34A7D37E18292A1550AB346FDFCC9F5A262E6A2C59AC4CD6 | |||
| 2840 | check-update.exe | C:\Users\admin\AppData\Local\Temp\UDT-FBDHAGGAGAKGNHGBNHCA1\A1 | xml | |
MD5:C1688359F3C3CC7331417943CCD02517 | SHA256:7AD88EA8F937D54224FF31A06D11AF90F03338302E31BA7BFC1142023AD3F43F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
9
DNS requests
5
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2036 | udt.exe | GET | 200 | 87.230.43.108:80 | http://update.am.de//version.xml | unknown | xml | 4.63 Kb | unknown |
2036 | udt.exe | GET | 200 | 87.230.43.108:80 | http://update.am.de//version.xml | unknown | xml | 4.63 Kb | unknown |
2036 | udt.exe | GET | — | 87.230.43.108:80 | http://update.am.de/vlc-setup-win32.exe | unknown | — | — | unknown |
2036 | udt.exe | GET | — | 87.230.43.108:80 | http://update.am.de/vlc-setup-win32.exe | unknown | — | — | unknown |
2832 | udt.exe | GET | — | 87.230.43.108:80 | http://update.am.de//version.xml | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2036 | udt.exe | 87.230.43.108:80 | update.am.de | Host Europe GmbH | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2832 | udt.exe | 87.230.43.108:80 | update.am.de | Host Europe GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
update.am.de |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2036 | udt.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |