| File name: | kkk |
| Full analysis: | https://app.any.run/tasks/e3038d72-0a76-4ec6-a9aa-e03f804c826c |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 15:01:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 8EFE63FBEC56DA047389523C77654EF6 |
| SHA1: | B73FC2CECEB2B76CF1F8E5AE5987A5ED52E512C4 |
| SHA256: | BFC97F484B27A23CE32D54A542422938B66B537F956BA0A9CD69B7AB64190EFA |
| SSDEEP: | 196608:ZBqsN8Fwc75pl5sDSOmRSdE+K5Uy2TVMP3HxRYAsxMdyEW:/N87PsS9Sm+3VMPHfYDxdf |
MALICIOUS
Loads dropped or rewritten executable
- kkk.exe (PID: 3864)
Application was dropped or rewritten from another process
- Tomcat7.exe (PID: 3556)
- Tomcat7.exe (PID: 2652)
- Tomcat7.exe (PID: 3688)
- Tomcat7.exe (PID: 2760)
- Tomcat7.exe (PID: 3772)
- nsC01D.tmp (PID: 3040)
- nsC4E0.tmp (PID: 1868)
- nsC5CC.tmp (PID: 3200)
- nsC6A8.tmp (PID: 2172)
- Tomcat7w.exe (PID: 4060)
- nsC793.tmp (PID: 3276)
- Tomcat7.exe (PID: 3516)
Changes the autorun value in the registry
- kkk.exe (PID: 3864)
SUSPICIOUS
Executable content was dropped or overwritten
- kkk.exe (PID: 3864)
Starts application with an unusual extension
- kkk.exe (PID: 3864)
Creates files in the program directory
- Tomcat7.exe (PID: 3556)
- Tomcat7.exe (PID: 3772)
- kkk.exe (PID: 3864)
- Tomcat7.exe (PID: 3516)
Creates files in the user directory
- kkk.exe (PID: 3864)
Creates a software uninstall entry
- kkk.exe (PID: 3864)
Creates files in the Windows directory
- Tomcat7.exe (PID: 3516)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:30 04:57:38+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3328 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.0.90.0 |
| ProductVersionNumber: | 7.0.90.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | tomcat.apache.org |
| CompanyName: | Apache Software Foundation |
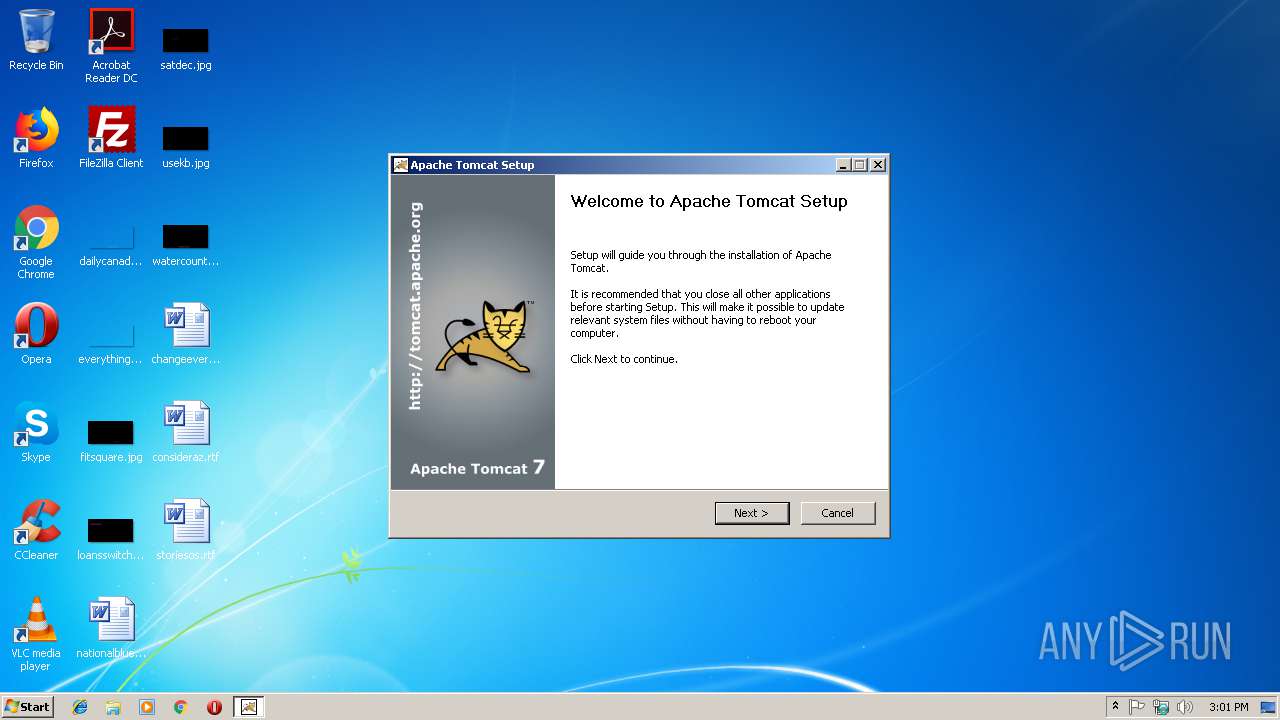
| FileDescription: | Apache Tomcat Installer |
| FileVersion: | 2 |
| InternalName: | apache-tomcat-7.0.90.exe |
| LegalCopyright: | Copyright (c) 1999-2018 The Apache Software Foundation |
| ProductName: | Apache Tomcat |
| ProductVersion: | 7.0.90 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-Jan-2018 03:57:38 |
| Detected languages: |
|
| Comments: | tomcat.apache.org |
| CompanyName: | Apache Software Foundation |
| FileDescription: | Apache Tomcat Installer |
| FileVersion: | 2.0 |
| InternalName: | apache-tomcat-7.0.90.exe |
| LegalCopyright: | Copyright (c) 1999-2018 The Apache Software Foundation |
| ProductName: | Apache Tomcat |
| ProductVersion: | 7.0.90 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 30-Jan-2018 03:57:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006077 | 0x00006200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.40397 |
.rdata | 0x00008000 | 0x00001248 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.04426 |
.data | 0x0000A000 | 0x0001A838 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.22445 |
.ndata | 0x00025000 | 0x0001E000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00043000 | 0x00006E68 | 0x00007000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.3461 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28813 | 1070 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.58585 | 3752 | UNKNOWN | English - United States | RT_ICON |
3 | 4.1463 | 3240 | UNKNOWN | English - United States | RT_ICON |
4 | 3.71606 | 2216 | UNKNOWN | English - United States | RT_ICON |
5 | 2.64646 | 1640 | UNKNOWN | English - United States | RT_ICON |
6 | 2.71436 | 1384 | UNKNOWN | English - United States | RT_ICON |
7 | 4.23914 | 872 | UNKNOWN | English - United States | RT_ICON |
8 | 2.95894 | 744 | UNKNOWN | English - United States | RT_ICON |
9 | 2.78721 | 296 | UNKNOWN | English - United States | RT_ICON |
102 | 2.71813 | 180 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
53
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1576 | "C:\Windows\system32\NOTEPAD.EXE" C:\Program Files\Apache Software Foundation\Tomcat 7.0\webapps\ROOT\RELEASE-NOTES.txt | C:\Windows\system32\NOTEPAD.EXE | — | kkk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1868 | "C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC4E0.tmp" "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" //US//Tomcat7 --Classpath "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\bootstrap.jar;C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\tomcat-juli.jar" --StartClass org.apache.catalina.startup.Bootstrap --StopClass org.apache.catalina.startup.Bootstrap --StartParams start --StopParams stop --StartMode jvm --StopMode jvm | C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC4E0.tmp | — | kkk.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2172 | "C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC6A8.tmp" "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" //US//Tomcat7 --JvmOptions9 "--add-opens=java.base/java.lang=ALL-UNNAMED#--add-opens=java.base/java.io=ALL-UNNAMED#--add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMED" | C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC6A8.tmp | — | kkk.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2652 | "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" //US//Tomcat7 --Classpath "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\bootstrap.jar;C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\tomcat-juli.jar" --StartClass org.apache.catalina.startup.Bootstrap --StopClass org.apache.catalina.startup.Bootstrap --StartParams start --StopParams stop --StartMode jvm --StopMode jvm | C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe | — | nsC4E0.tmp | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: Commons Daemon Service Runner Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 2760 | "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" //US//Tomcat7 --JvmOptions9 "--add-opens=java.base/java.lang=ALL-UNNAMED#--add-opens=java.base/java.io=ALL-UNNAMED#--add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMED" | C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe | — | nsC6A8.tmp | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: Commons Daemon Service Runner Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
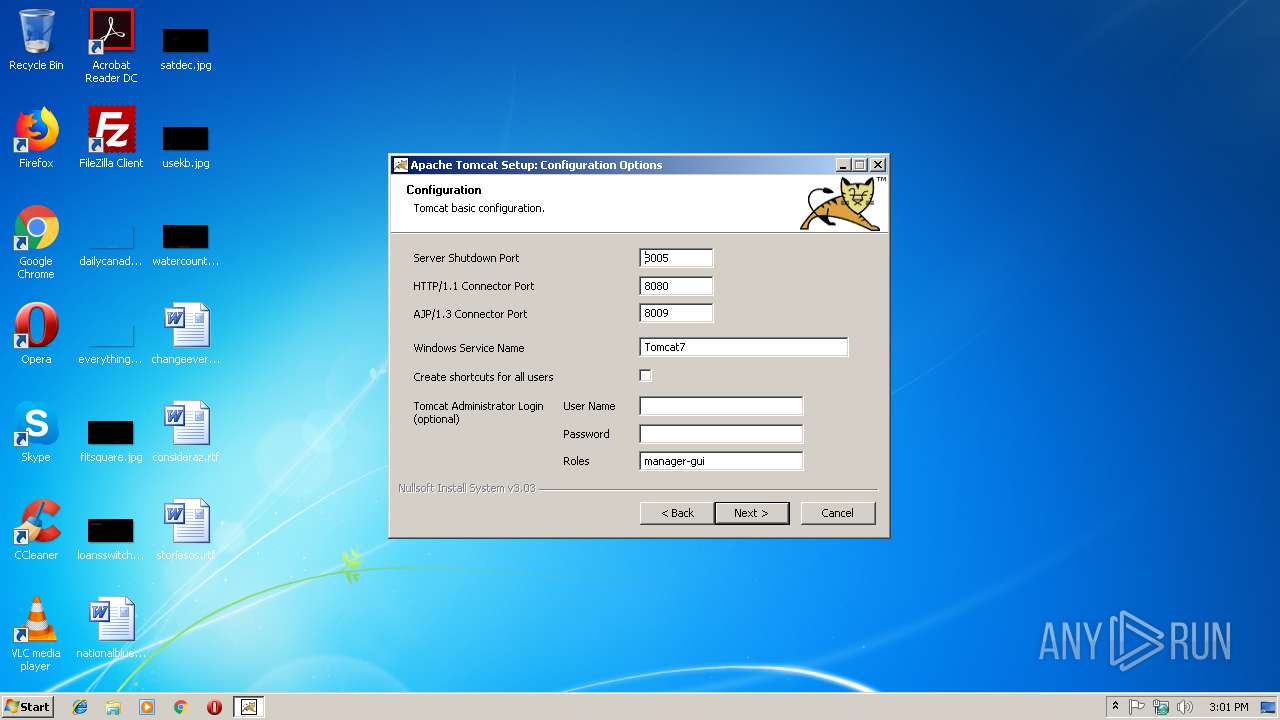
| 3040 | "C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC01D.tmp" "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" //IS//Tomcat7 --DisplayName "Apache Tomcat 7.0 Tomcat7" --Description "Apache Tomcat 7.0.90 Server - https://tomcat.apache.org/" --LogPath "C:\Program Files\Apache Software Foundation\Tomcat 7.0\logs" --Install "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" --Jvm "C:\Program Files\Java\jre1.8.0_92\bin\client\jvm.dll" --StartPath "C:\Program Files\Apache Software Foundation\Tomcat 7.0" --StopPath "C:\Program Files\Apache Software Foundation\Tomcat 7.0" | C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC01D.tmp | — | kkk.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3200 | "C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC5CC.tmp" "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" //US//Tomcat7 --JvmOptions "-Dcatalina.home=C:\Program Files\Apache Software Foundation\Tomcat 7.0#-Dcatalina.base=C:\Program Files\Apache Software Foundation\Tomcat 7.0#-Djava.io.tmpdir=C:\Program Files\Apache Software Foundation\Tomcat 7.0\temp#-Djava.util.logging.manager=org.apache.juli.ClassLoaderLogManager#-Djava.util.logging.config.file=C:\Program Files\Apache Software Foundation\Tomcat 7.0\conf\logging.properties" | C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC5CC.tmp | — | kkk.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3276 | "C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC793.tmp" "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" //US//Tomcat7 --StdOutput auto --StdError auto --JvmMs 128 --JvmMx 256 | C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsC793.tmp | — | kkk.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3364 | "C:\Users\admin\AppData\Local\Temp\kkk.exe" | C:\Users\admin\AppData\Local\Temp\kkk.exe | — | explorer.exe | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: MEDIUM Description: Apache Tomcat Installer Exit code: 3221226540 Version: 2.0 Modules
| |||||||||||||||
| 3516 | "C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe" //RS//Tomcat7 | C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\Tomcat7.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Apache Software Foundation Integrity Level: SYSTEM Description: Commons Daemon Service Runner Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
Total events
407
Read events
374
Write events
33
Delete events
0
Modification events
| (PID) Process: | (3556) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Java |
| Operation: | write | Name: | Jvm |
Value: C:\Program Files\Java\jre1.8.0_92\bin\client\jvm.dll | |||
| (PID) Process: | (3556) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Stop |
| Operation: | write | Name: | WorkingPath |
Value: C:\Program Files\Apache Software Foundation\Tomcat 7.0 | |||
| (PID) Process: | (3556) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Start |
| Operation: | write | Name: | WorkingPath |
Value: C:\Program Files\Apache Software Foundation\Tomcat 7.0 | |||
| (PID) Process: | (3556) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Log |
| Operation: | write | Name: | Path |
Value: C:\Program Files\Apache Software Foundation\Tomcat 7.0\logs | |||
| (PID) Process: | (2652) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Java |
| Operation: | write | Name: | Classpath |
Value: C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\bootstrap.jar;C:\Program Files\Apache Software Foundation\Tomcat 7.0\bin\tomcat-juli.jar | |||
| (PID) Process: | (2652) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Stop |
| Operation: | write | Name: | Class |
Value: org.apache.catalina.startup.Bootstrap | |||
| (PID) Process: | (2652) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Stop |
| Operation: | write | Name: | Params |
Value: stop | |||
| (PID) Process: | (2652) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Stop |
| Operation: | write | Name: | Mode |
Value: jvm | |||
| (PID) Process: | (2652) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Start |
| Operation: | write | Name: | Class |
Value: org.apache.catalina.startup.Bootstrap | |||
| (PID) Process: | (2652) Tomcat7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Apache Software Foundation\Procrun 2.0\Tomcat7\Parameters\Start |
| Operation: | write | Name: | Params |
Value: start | |||
Executable files
10
Suspicious files
23
Text files
190
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | kkk.exe | C:\Program Files\Apache Software Foundation\Tomcat 7.0\NOTICE | text | |
MD5:— | SHA256:— | |||
| 3864 | kkk.exe | C:\Program Files\Apache Software Foundation\Tomcat 7.0\RELEASE-NOTES | text | |
MD5:— | SHA256:— | |||
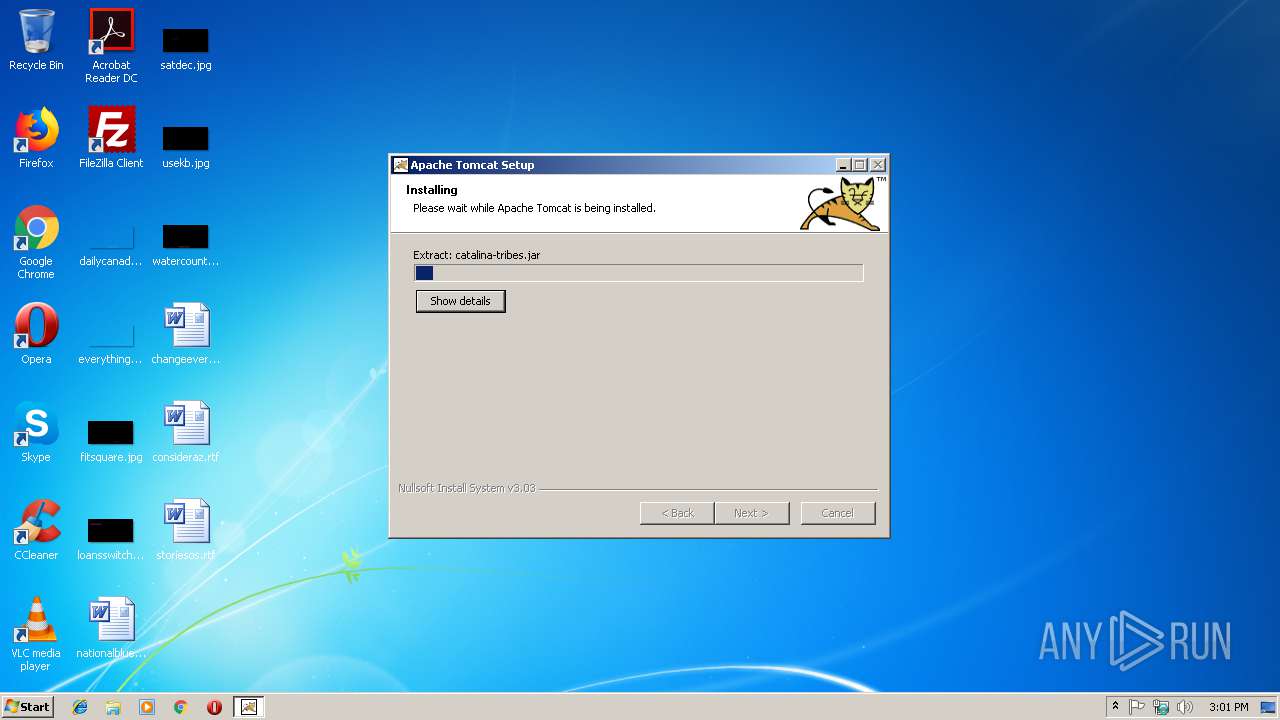
| 3864 | kkk.exe | C:\Program Files\Apache Software Foundation\Tomcat 7.0\lib\catalina-ant.jar | compressed | |
MD5:— | SHA256:— | |||
| 3864 | kkk.exe | C:\Program Files\Apache Software Foundation\Tomcat 7.0\lib\annotations-api.jar | compressed | |
MD5:— | SHA256:— | |||
| 3864 | kkk.exe | C:\Program Files\Apache Software Foundation\Tomcat 7.0\lib\catalina-tribes.jar | compressed | |
MD5:— | SHA256:— | |||
| 3864 | kkk.exe | C:\Program Files\Apache Software Foundation\Tomcat 7.0\lib\catalina-ha.jar | compressed | |
MD5:— | SHA256:— | |||
| 3864 | kkk.exe | C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\modern-wizard.bmp | image | |
MD5:4F7C3FD818EA30571D84FD9D217A60C5 | SHA256:DD41483287B5A50DEB16FC587FC5654D25F6B5E1680CF400B21CABE86D925F67 | |||
| 3864 | kkk.exe | C:\Users\admin\AppData\Local\Temp\nsc9BAC.tmp\nsDialogs.dll | executable | |
MD5:EAC1C3707970FE7C71B2D760C34763FA | SHA256:062C75AD650548750564FFD7AEF8CD553773B5C26CAE7F25A5749B13165194E3 | |||
| 3864 | kkk.exe | C:\Program Files\Apache Software Foundation\Tomcat 7.0\LICENSE | text | |
MD5:77CDEAA98DEF0E01E61A53D09BFDE75D | SHA256:235D08270681F90E9151773D197D7EBAF52E99D95D1F4630328EF1D70EF8C3A4 | |||
| 3864 | kkk.exe | C:\Program Files\Apache Software Foundation\Tomcat 7.0\lib\jasper-el.jar | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report