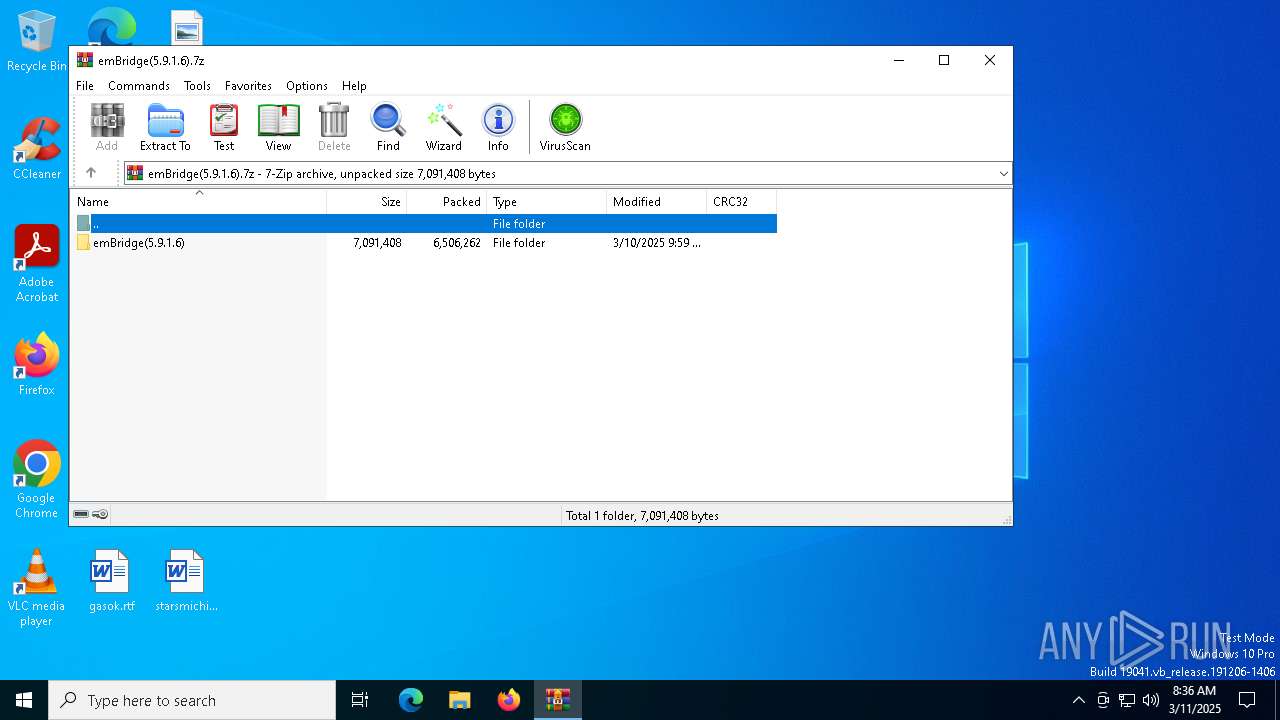
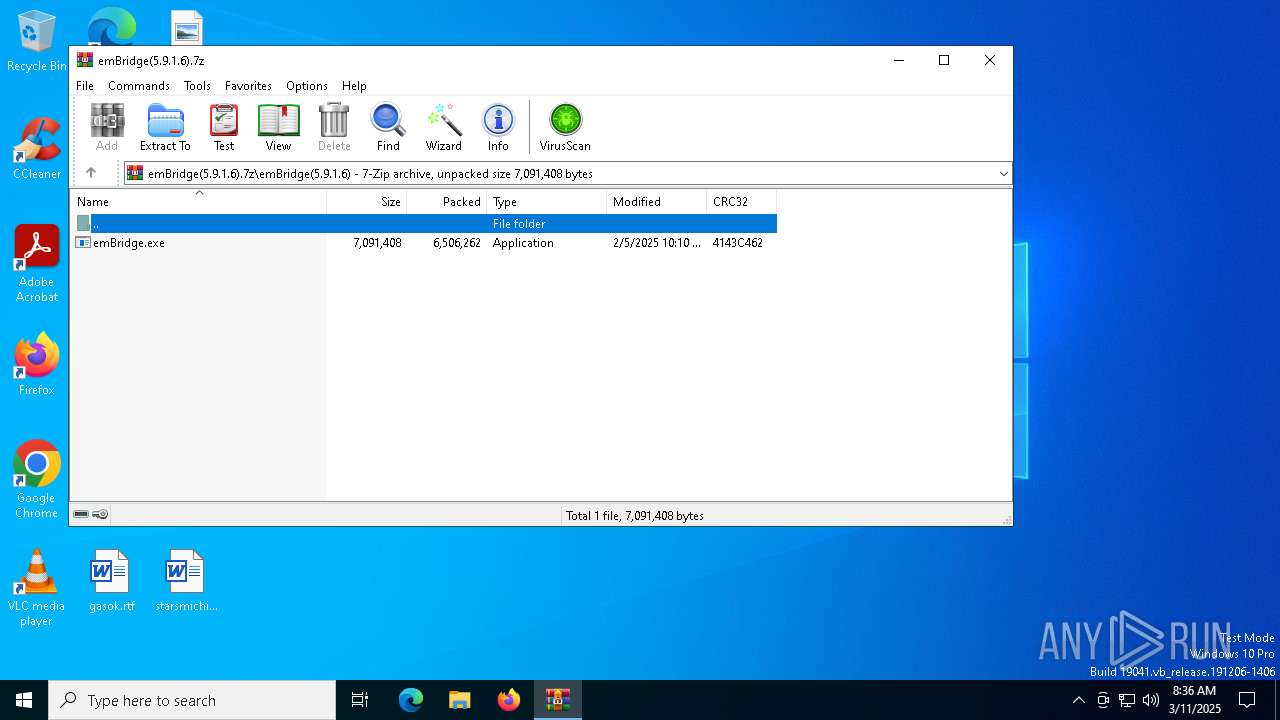
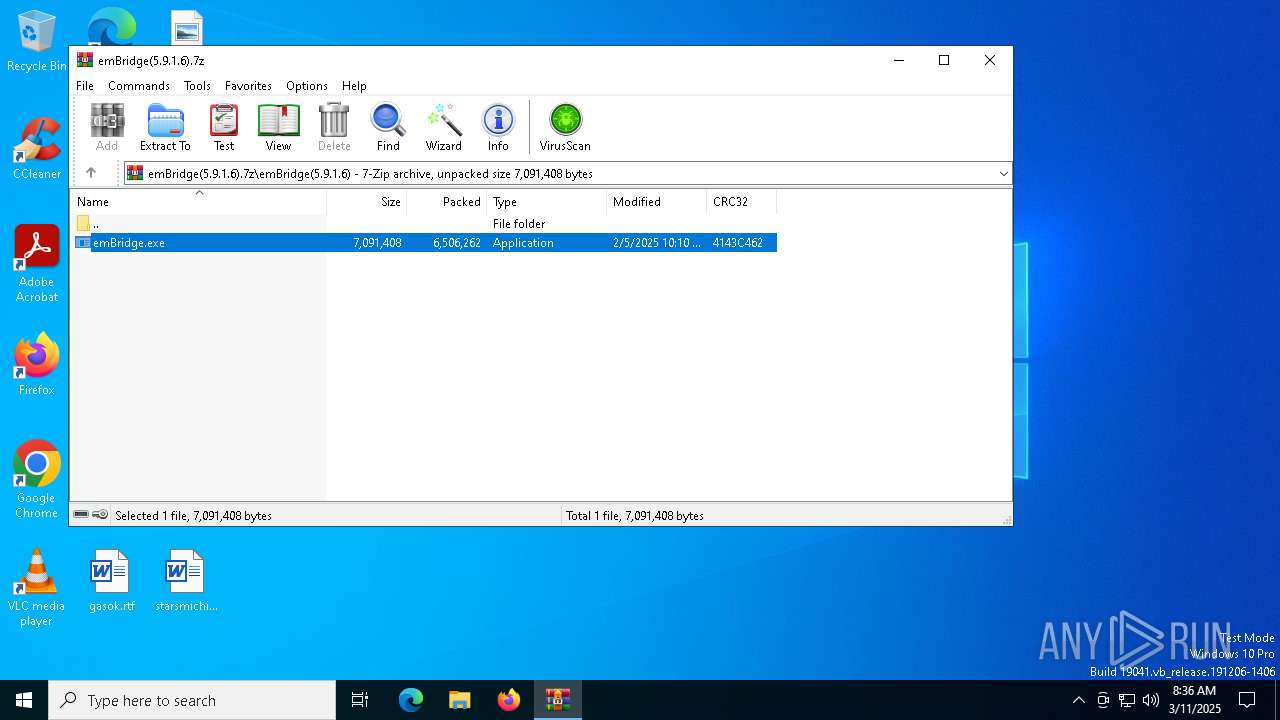
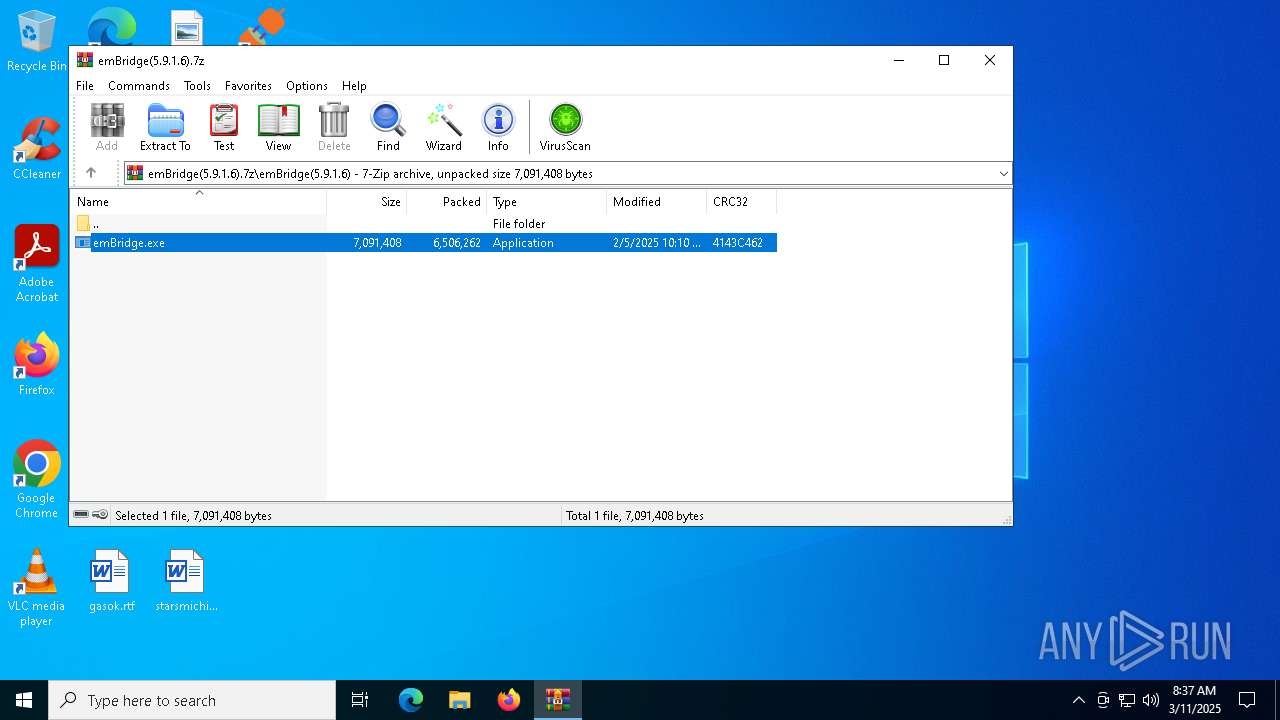
| File name: | emBridge(5.9.1.6).7z |
| Full analysis: | https://app.any.run/tasks/b830f69f-5695-45d4-83f6-a784ed78894a |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2025, 08:36:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 1BEEED04BF4BE7CD2A9FE5873A979C48 |
| SHA1: | 6C1A738314F30878099D44693B1F3F63A85BF1AA |
| SHA256: | BF98BD95AA2D934EA57EF80C08AAE3EE816B08648DCBF0ABCD6D8ACD36816249 |
| SSDEEP: | 98304:ZeAmUt56LVxfhk2kSL6fJ54pN72ci3Wzzve/HySFkPnXT85nV6TdIMq+/KA+qP6h:rAjT4sGvsVK |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7400)
Create files in the Startup directory
- emBridge.tmp (PID: 7368)
- emBridge.tmp (PID: 7244)
SUSPICIOUS
Executable content was dropped or overwritten
- emBridge.exe (PID: 7232)
- emBridge.exe (PID: 2140)
- emBridge.tmp (PID: 7368)
- emBridge.exe (PID: 2040)
- emBridge.tmp (PID: 7244)
- _unins.tmp (PID: 4784)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7400)
- emBridge.tmp (PID: 7148)
- emBridge.tmp (PID: 6080)
- emBridge.exe (PID: 7516)
Reads the Windows owner or organization settings
- emBridge.tmp (PID: 7368)
- emBridge.tmp (PID: 7244)
- _unins.tmp (PID: 4784)
Process drops legitimate windows executable
- emBridge.tmp (PID: 7368)
- emBridge.tmp (PID: 7244)
Executing commands from a ".bat" file
- emBridge.tmp (PID: 7368)
- emBridge.tmp (PID: 7244)
Starts CMD.EXE for commands execution
- emBridge.tmp (PID: 7368)
- emBridge.tmp (PID: 7244)
- emBridge.exe (PID: 7516)
Creates or modifies Windows services
- emBridge.exe (PID: 5204)
Executes as Windows Service
- emBridge.exe (PID: 7020)
- emBridge.exe (PID: 7516)
Adds/modifies Windows certificates
- emBridge.exe (PID: 7020)
Executes application which crashes
- emBridge.exe (PID: 7020)
Searches for installed software
- emBridge.tmp (PID: 7244)
Starts itself from another location
- unins000.exe (PID: 1272)
Starts application with an unusual extension
- unins000.exe (PID: 1272)
Uses TASKKILL.EXE to kill process
- _unins.tmp (PID: 4784)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 7692)
- cmd.exe (PID: 7364)
- cmd.exe (PID: 7660)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 6960)
- cmd.exe (PID: 7852)
INFO
Create files in a temporary directory
- emBridge.exe (PID: 7232)
- emBridge.exe (PID: 2140)
- emBridge.tmp (PID: 7368)
- emBridge.exe (PID: 7264)
- emBridge.exe (PID: 2040)
- emBridge.tmp (PID: 7244)
- _unins.tmp (PID: 4784)
- unins000.exe (PID: 1272)
Checks supported languages
- emBridge.exe (PID: 7232)
- emBridge.tmp (PID: 7148)
- emBridge.exe (PID: 2140)
- emBridge.tmp (PID: 7368)
- emBridge.exe (PID: 5204)
- emBridge.exe (PID: 7172)
- emBridge.exe (PID: 7020)
- emBridge.exe (PID: 7264)
- emBridge.exe (PID: 2040)
- emBridge.tmp (PID: 6080)
- emBridge.tmp (PID: 7244)
- unins000.exe (PID: 1272)
- emBridge.exe (PID: 1348)
- _unins.tmp (PID: 4784)
- emBridge.exe (PID: 6808)
- emBridge.exe (PID: 4200)
- emBridge.exe (PID: 7516)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7400)
Reads the computer name
- emBridge.tmp (PID: 7148)
- emBridge.tmp (PID: 7368)
- emBridge.exe (PID: 5204)
- emBridge.exe (PID: 7172)
- emBridge.exe (PID: 7020)
- emBridge.tmp (PID: 6080)
- emBridge.tmp (PID: 7244)
- unins000.exe (PID: 1272)
- _unins.tmp (PID: 4784)
- emBridge.exe (PID: 1348)
- emBridge.exe (PID: 6808)
- emBridge.exe (PID: 4200)
Process checks computer location settings
- emBridge.tmp (PID: 7148)
- emBridge.tmp (PID: 6080)
- _unins.tmp (PID: 4784)
Compiled with Borland Delphi (YARA)
- emBridge.exe (PID: 7232)
- emBridge.tmp (PID: 7148)
- emBridge.exe (PID: 2140)
- emBridge.tmp (PID: 7368)
- emBridge.exe (PID: 7264)
- emBridge.tmp (PID: 6080)
- emBridge.tmp (PID: 7244)
Detects InnoSetup installer (YARA)
- emBridge.exe (PID: 7232)
- emBridge.tmp (PID: 7148)
- emBridge.exe (PID: 2140)
- emBridge.tmp (PID: 7368)
- emBridge.exe (PID: 7264)
- emBridge.tmp (PID: 6080)
- emBridge.tmp (PID: 7244)
Creates files in the program directory
- emBridge.tmp (PID: 7368)
- emBridge.exe (PID: 5204)
- emBridge.exe (PID: 7020)
- emBridge.tmp (PID: 7244)
- emBridge.exe (PID: 7516)
Checks proxy server information
- emBridge.tmp (PID: 7368)
The sample compiled with english language support
- emBridge.tmp (PID: 7368)
- emBridge.tmp (PID: 7244)
Creates a software uninstall entry
- emBridge.tmp (PID: 7368)
- emBridge.tmp (PID: 7244)
Reads the machine GUID from the registry
- emBridge.exe (PID: 5204)
- emBridge.exe (PID: 7172)
- emBridge.exe (PID: 7020)
- emBridge.exe (PID: 1348)
- emBridge.exe (PID: 7516)
- emBridge.exe (PID: 4200)
Disables trace logs
- emBridge.exe (PID: 7020)
Reads the software policy settings
- slui.exe (PID: 7584)
- slui.exe (PID: 7816)
Confuser has been detected (YARA)
- emBridge.exe (PID: 7516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:03:10 09:59:48+00:00 |
| ArchivedFileName: | emBridge(5.9.1.6) |
Total processes
194
Monitored processes
52
Malicious processes
3
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\WINDOWS\system32\taskkill.exe" /f /im emBridge.exe | C:\Windows\SysWOW64\taskkill.exe | — | _unins.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | CheckNetIsolation LoopbackExempt -a -n=Microsoft.MicrosoftEdge_8wekyb3d8bbwe | C:\Windows\SysWOW64\CheckNetIsolation.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: AppContainer Network Isolation Diagnostic Tool Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\eMudhra\emBridge\unins000.exe" /SILENT /NORESTART /SUPPRESSMSGBOXES | C:\Program Files (x86)\eMudhra\emBridge\unins000.exe | — | emBridge.tmp | |||||||||||
User: admin Company: eMudhra Limited Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\Program Files (x86)\eMudhra\emBridge\emBridge.exe" uninstall | C:\Program Files (x86)\eMudhra\emBridge\emBridge.exe | — | _unins.tmp | |||||||||||
User: admin Company: eMudhra Limited Integrity Level: HIGH Description: emBridge Exit code: 0 Version: 5.9.1.6 Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7400.6904\emBridge(5.9.1.6)\emBridge.exe" /SPAWNWND=$802D2 /NOTIFYWND=$40256 | C:\Users\admin\AppData\Local\Temp\Rar$EXa7400.6904\emBridge(5.9.1.6)\emBridge.exe | emBridge.tmp | ||||||||||||
User: admin Company: eMudhra Limited Integrity Level: HIGH Description: emBridge Setup Exit code: 1 Version: 5.9.1.6 Modules
| |||||||||||||||
| 2140 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7400.2678\emBridge(5.9.1.6)\emBridge.exe" /SPAWNWND=$1702DC /NOTIFYWND=$6025C | C:\Users\admin\AppData\Local\Temp\Rar$EXa7400.2678\emBridge(5.9.1.6)\emBridge.exe | emBridge.tmp | ||||||||||||
User: admin Company: eMudhra Limited Integrity Level: HIGH Description: emBridge Setup Exit code: 0 Version: 5.9.1.6 Modules
| |||||||||||||||
| 2316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 795
Read events
23 694
Write events
90
Delete events
11
Modification events
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\emBridge(5.9.1.6).7z | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7368) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (7368) emBridge.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{a38aa4bd-f42d-44fa-a9c9-da61f74ca666}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\eMudhra\emBridge | |||
Executable files
62
Suspicious files
21
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7368 | emBridge.tmp | C:\Windows\System32\drivers\etc\hosts | text | |
MD5:F79F7E6578AB981C42623758399B885A | SHA256:56FFA8A9A7562DF1620C7A37BDB07A16841DAB627984D8ECE0A2BDEF985E53AD | |||
| 7368 | emBridge.tmp | C:\Users\admin\AppData\Local\Temp\is-P88DG.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 2140 | emBridge.exe | C:\Users\admin\AppData\Local\Temp\is-A314G.tmp\emBridge.tmp | executable | |
MD5:231A054793512A64C9E972FFA1AB683C | SHA256:B1A3FD598E9A7D312B9B546A41EF9D9F2E3D27AA59B3DADE43669048CAF8055B | |||
| 7400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7400.2678\emBridge(5.9.1.6)\emBridge.exe | executable | |
MD5:BD4F0C6901227527B3D616CE5F3231EA | SHA256:B3BA81BD993CA038C0F11328A6D98181DCFF01E93B7863260EC5FD87C2A18CAB | |||
| 7232 | emBridge.exe | C:\Users\admin\AppData\Local\Temp\is-BTNN3.tmp\emBridge.tmp | executable | |
MD5:231A054793512A64C9E972FFA1AB683C | SHA256:B1A3FD598E9A7D312B9B546A41EF9D9F2E3D27AA59B3DADE43669048CAF8055B | |||
| 7368 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-LRBTT.tmp | executable | |
MD5:EEAB8804E228437A0E58993D7A066944 | SHA256:E1BADD6860328384FB16178487CC293D79EB6618750A8A28EC652BC7AAB0F7BA | |||
| 7368 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\System.Web.Http.dll | executable | |
MD5:BDC52F53AE7BBD99D60CDC2156F27BD3 | SHA256:EA4C2C88771AD1FAB8C1772B75FC9B16162AFD94596FF92905D9741047F75C9B | |||
| 7368 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-8DP28.tmp | executable | |
MD5:743FDB1D35A0A0D28F31DC16B03940B6 | SHA256:FD1D581C1E7BA97A4137B7907B95EEBABE55206A43FC0138B64892E793B0F74B | |||
| 7368 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-57C93.tmp | executable | |
MD5:A16A0AE73197C99125266C81599DA511 | SHA256:152EF62B614CA2B746283BC7FD008655408B3BAB763CA20B77AC83A316670519 | |||
| 7368 | emBridge.tmp | C:\Program Files (x86)\eMudhra\emBridge\is-92CJ5.tmp | executable | |
MD5:C724ACF1B7F9D029C35F80315D3E340A | SHA256:EC2C36C86514579E8E960724C9D5FDE2793F4FD68BED503B62F2C580B96D863C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
27
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7732 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5588 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5588 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7020 | emBridge.exe | GET | 200 | 13.234.51.255:80 | http://resources.emudhra.com/hs/updates.xml | unknown | — | — | whitelisted |
7516 | emBridge.exe | GET | 200 | 13.234.51.255:80 | http://resources.emudhra.com/hs/updates.xml | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7732 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7732 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
resources.emudhra.com |
| whitelisted |
Threats
Process | Message |
|---|---|
emBridge.exe | Configuration Result:
[Success] Name emBridge
[Success] DisplayName emBridge Service
[Success] Description emBridge Service.
[Success] ServiceName emBridge
|
emBridge.exe | Topshelf v3.3.154.0, .NET Framework v4.0.30319.42000
|
emBridge.exe | Topshelf.HostConfigurators.HostConfiguratorImpl Information: 0 : |
emBridge.exe | Topshelf.HostFactory Information: 0 : |
emBridge.exe | Starting as a Windows service
|
emBridge.exe | Topshelf.Runtime.Windows.WindowsServiceHost Information: 0 : |
emBridge.exe | Topshelf.Runtime.Windows.WindowsServiceHost Information: 0 : |
emBridge.exe | [Topshelf] Starting
|
emBridge.exe | Topshelf.Runtime.Windows.WindowsServiceHost Information: 0 : |
emBridge.exe | [Topshelf] Started
|