| URL: | cancelar-comprar-ya1.iceiy.com |
| Full analysis: | https://app.any.run/tasks/d0c4d122-856c-4d69-8a77-3e452d5b847a |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2024, 13:39:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5EF34A2DA15DC089CB5755A60E36A93F |
| SHA1: | 6ABFCE46D2C997A1DA9545CD4DEBF14A4EAA82A3 |
| SHA256: | BF8592DEF93C62039D1F153721D00706BA745F3A2480860B2B4E09D3C7106536 |
| SSDEEP: | 3:HZ2snLA4:HM4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" "cancelar-comprar-ya1.iceiy.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:116 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
31 643
Read events
31 558
Write events
81
Delete events
4
Modification events
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
24
Text files
65
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\aes[1].js | text | |
MD5:FC66E046447092C606F2587837F96874 | SHA256:5069425B121346B36F730910D05402D50920FC2178B01E0C878B71AF4EF1EB96 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\BSUQWGDI.htm | html | |
MD5:E30C2EBE043F7E386C2661324AD1A13A | SHA256:0BD2A58A15A426C7A98AADEA602326A7493A59175139F9AC6C4A08B0E4EDE343 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\n[1].htm | html | |
MD5:D75C637B56FAD3A8A77FBD2D4BC43A2A | SHA256:5F78B83FA6428F9B668DFD34EBB1F9655063C94B6827A6BA8DFB0569129C90CF | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\visa_debit[1].gif | image | |
MD5:39EB00A359B1E7889E8FC1492E6E8B54 | SHA256:06A0DA77E15940E1F2FCA30D2A86F811CD374210110291D192C9889F9BCB6658 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\L29VSDD5.htm | html | |
MD5:A31EE573B02743B54DAB2543CA1E70E7 | SHA256:02918CE6150E0CAF2FF5BBAE9DF0C46923641C183202A164719E0D64DE0A15D2 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\diners[1].gif | image | |
MD5:D2EB8E8405A9C28B53585F22C4F081C0 | SHA256:06595C098D5353960932C86E86DC03F77AF77D6D5CFCA543A9E9B95CC2DCC3A5 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\3XG1DOXF.txt | text | |
MD5:DB083EAADB9658E36F44DEA56E184D54 | SHA256:9E05FADE66D5241B4E82191B086FD2FDD528580AC7E09D572CC9E0EE7E0D8263 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\mastercard[1].gif | image | |
MD5:1E720B07845702AFE9FDAE261F35CA86 | SHA256:070360778F733CF27020BAA93D0DE59C24F76A4D62BE31271C336A48902DB589 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\JCB[1].gif | image | |
MD5:5172D28E70898AFE10A55BAF9E971F75 | SHA256:FF060C6EE3BF890B183488F70DCD8E23751D13BD8855A7BF0737E0509D51D361 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\AMEX[1].gif | image | |
MD5:04180B3EE4B5C82C61BA1A91EE19A730 | SHA256:0C00B435DC46DA8C2DE0FEAB8D8DE208E5E996920FCC2EBBB5E68678D09D504F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
47
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | iexplore.exe | GET | 200 | 185.27.134.215:80 | http://cancelar-comprar-ya1.iceiy.com/ | unknown | html | 841 b | unknown |
2032 | iexplore.exe | GET | 200 | 185.27.134.215:80 | http://cancelar-comprar-ya1.iceiy.com/aes.js | unknown | text | 13.4 Kb | unknown |
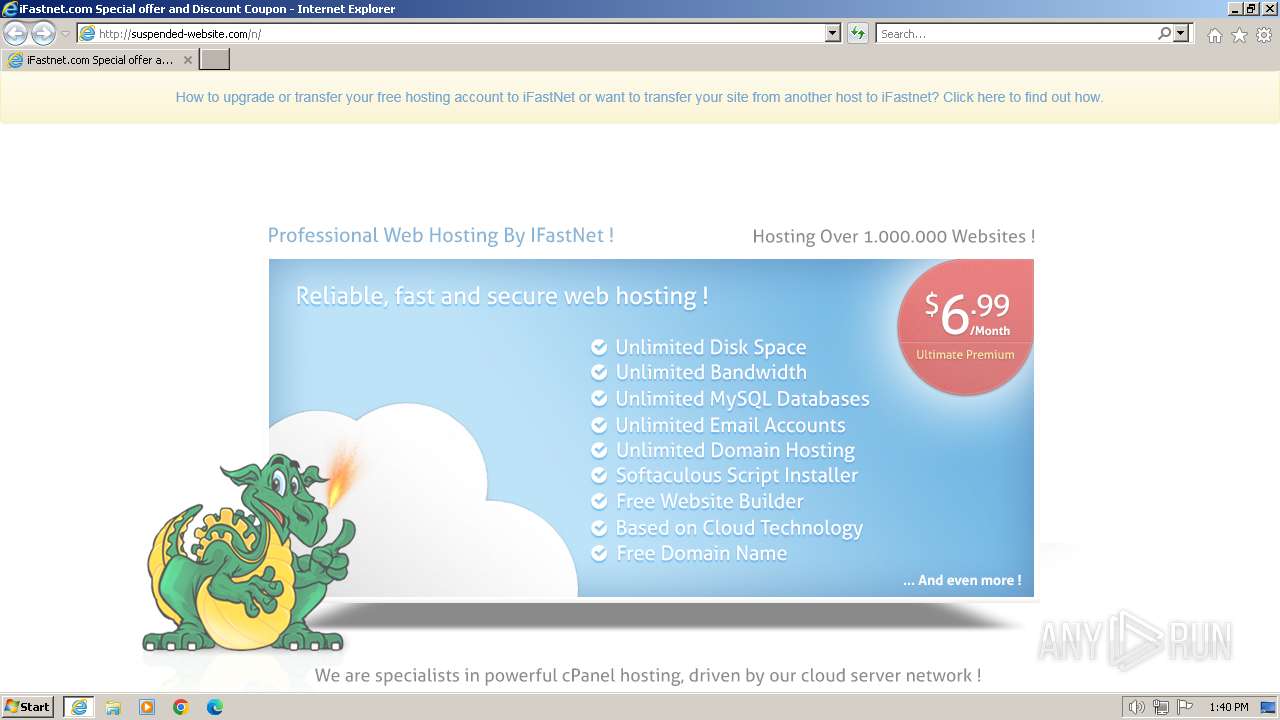
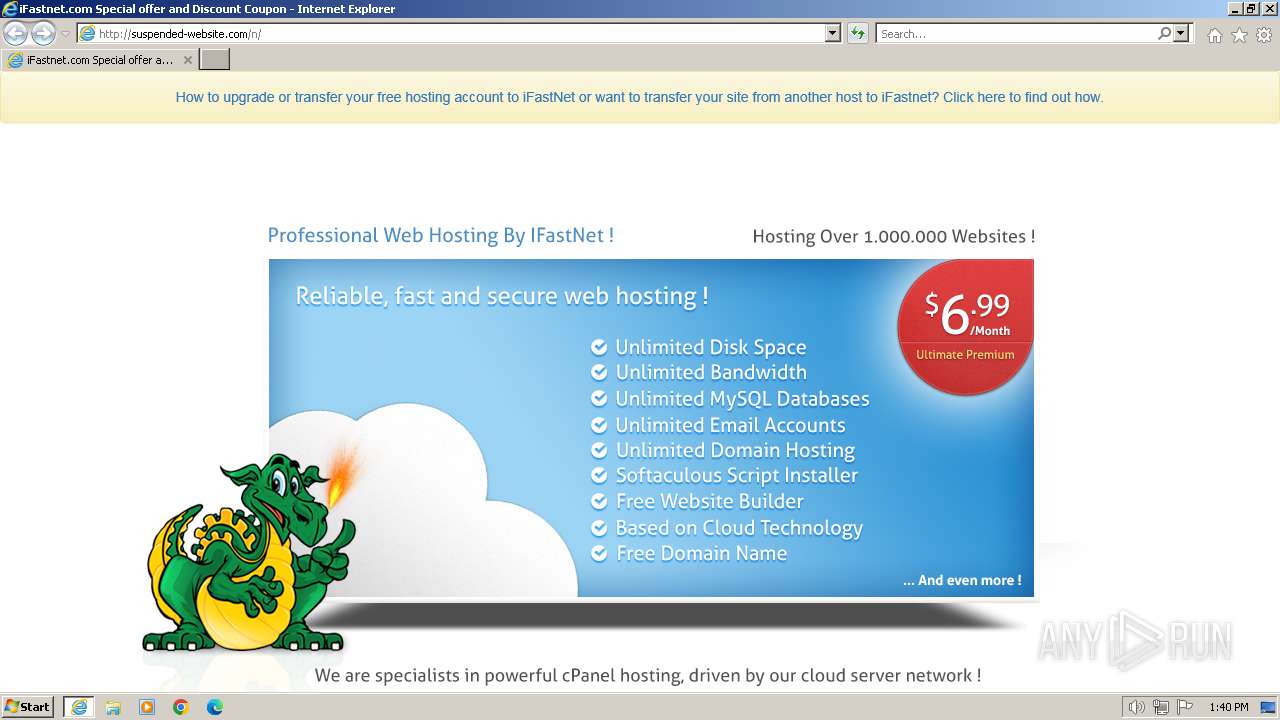
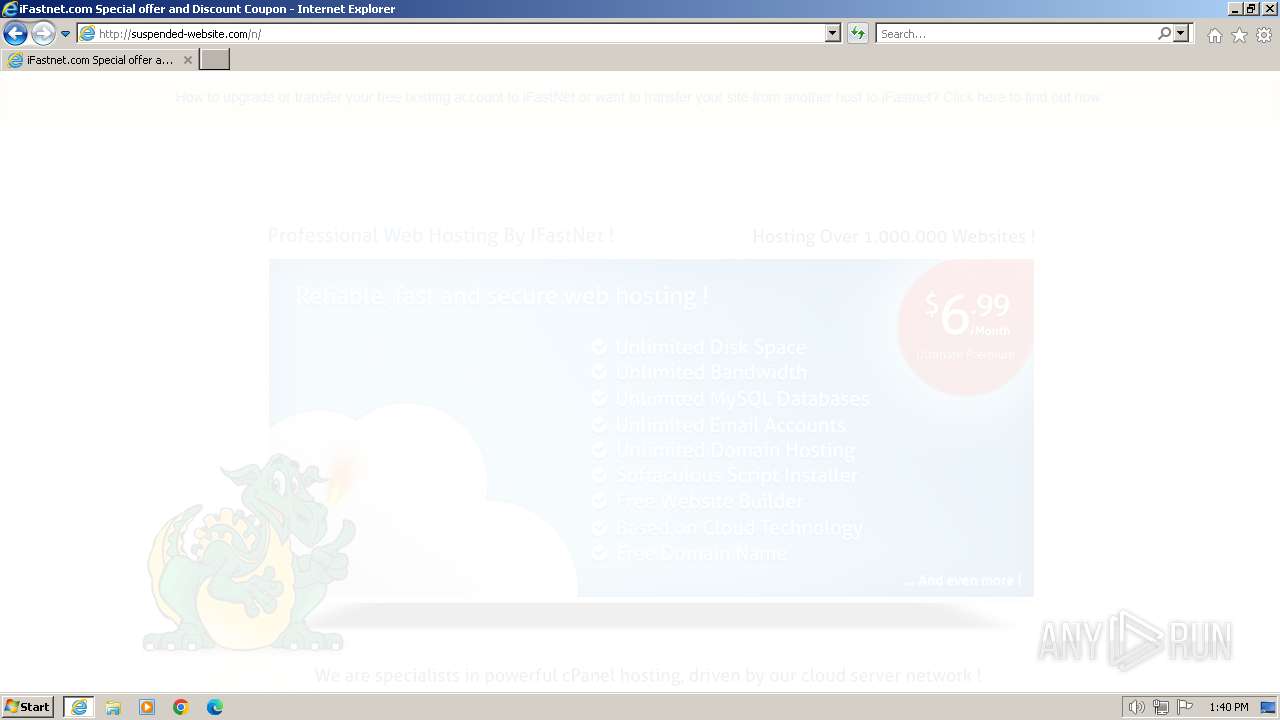
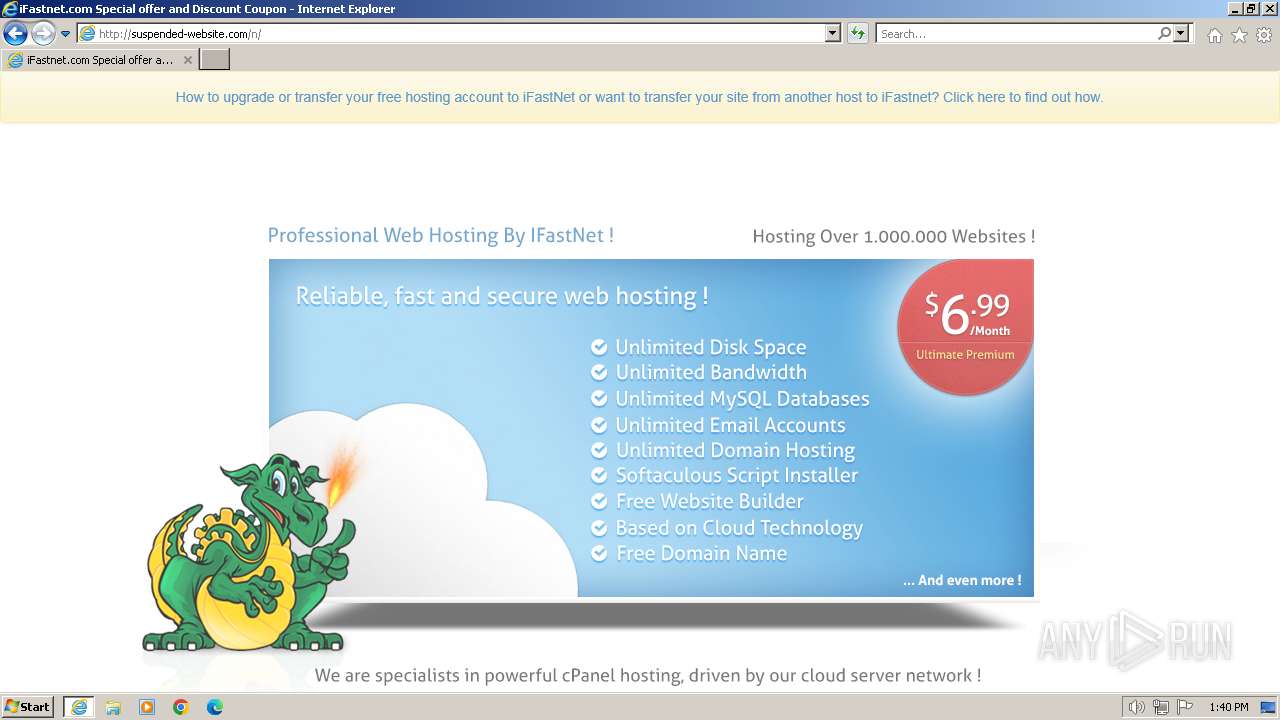
2032 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://suspended-website.com/n/ | unknown | html | 2.03 Kb | unknown |
2032 | iexplore.exe | GET | 302 | 185.27.134.215:80 | http://cancelar-comprar-ya1.iceiy.com/?i=1 | unknown | html | 258 b | unknown |
2032 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://suspended-website.com/visa_electron.gif | unknown | image | 2.96 Kb | unknown |
2032 | iexplore.exe | GET | 302 | 188.114.97.3:80 | http://suspended-website.com/index.php?host=cancelar-comprar-ya1.iceiy.com | unknown | html | 685 b | unknown |
2032 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://suspended-website.com/visa_debit.gif | unknown | image | 2.38 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://suspended-website.com/AMEX.gif | unknown | image | 558 b | unknown |
2032 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://suspended-website.com/mastercard.gif | unknown | image | 709 b | unknown |
2032 | iexplore.exe | GET | 200 | 188.114.97.3:80 | http://suspended-website.com/maestro.gif | unknown | image | 1.23 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2032 | iexplore.exe | 185.27.134.215:80 | cancelar-comprar-ya1.iceiy.com | Wildcard UK Limited | GB | malicious |
2032 | iexplore.exe | 188.114.97.3:80 | suspended-website.com | CLOUDFLARENET | NL | unknown |
2032 | iexplore.exe | 188.114.97.3:443 | suspended-website.com | CLOUDFLARENET | NL | unknown |
2032 | iexplore.exe | 104.18.10.207:443 | maxcdn.bootstrapcdn.com | CLOUDFLARENET | — | unknown |
2032 | iexplore.exe | 172.217.18.10:443 | ajax.googleapis.com | GOOGLE | US | whitelisted |
2032 | iexplore.exe | 104.20.95.138:80 | www.statcounter.com | CLOUDFLARENET | — | unknown |
2032 | iexplore.exe | 142.250.184.200:443 | www.googletagmanager.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cancelar-comprar-ya1.iceiy.com |
| unknown |
suspended-website.com |
| unknown |
maxcdn.bootstrapcdn.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
www.statcounter.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
c.statcounter.com |
| whitelisted |