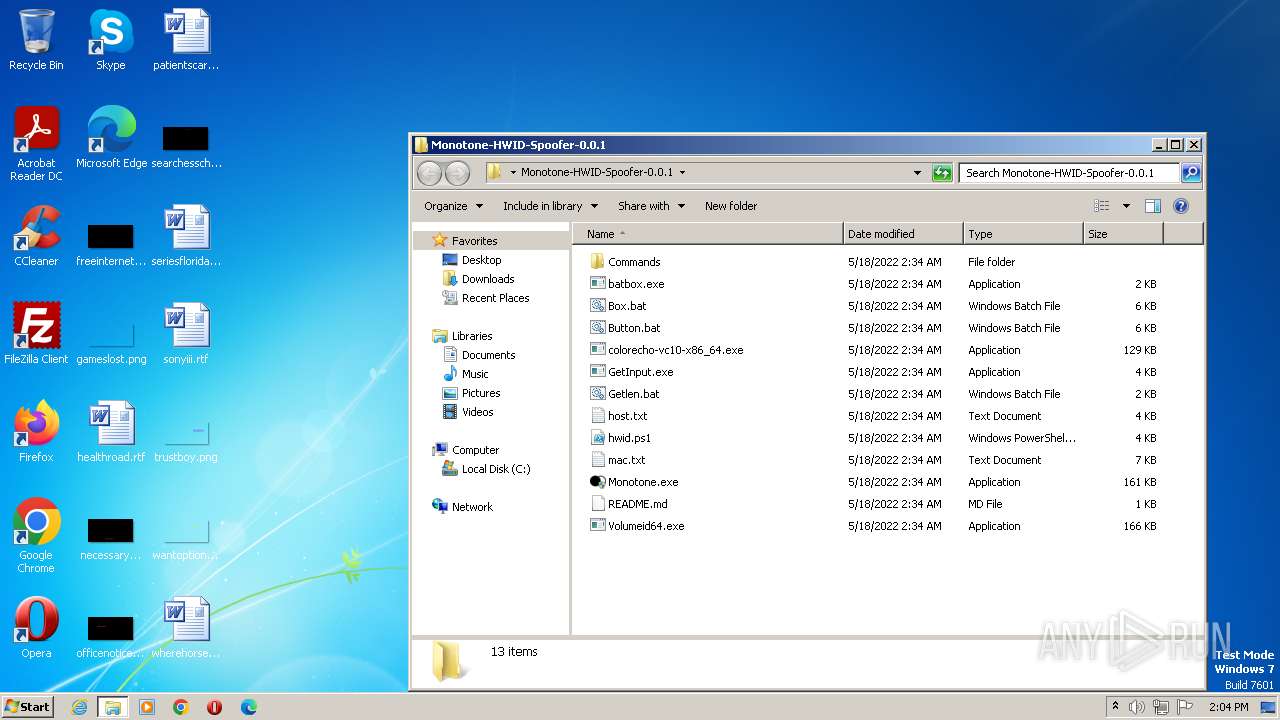
| File name: | Monotone-HWID-Spoofer-0.0.1.7z |
| Full analysis: | https://app.any.run/tasks/d9e8bd72-c180-4d04-b510-d7de569ad5df |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2023, 13:04:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | AF1D2B3725C153BD093D2A0929D8DA6B |
| SHA1: | 97445399186405C5B41F72B1E23E3C8DA97EAB33 |
| SHA256: | BF8206D858EFFDD6F2DE6DA41A9DCDF53DB710DBFEF5EEB98944CD21D61EFE94 |
| SSDEEP: | 12288:CpTQTtDfboQpDmUO4xS9f5a4XYjPT8QQk6RuYWC5G9Y:ATSbbo+mCxSa38mYWkGW |
MALICIOUS
Application was dropped or rewritten from another process
- GetInput.exe (PID: 3876)
- batbox.exe (PID: 2504)
- GetInput.exe (PID: 2952)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 1276)
Get information on the list of running processes
- cmd.exe (PID: 3724)
INFO
Checks supported languages
- batbox.exe (PID: 2504)
The process checks LSA protection
- tasklist.exe (PID: 1916)
Manual execution by a user
- GetInput.exe (PID: 3876)
- cmd.exe (PID: 2600)
- GetInput.exe (PID: 2952)
- cmd.exe (PID: 1900)
- notepad.exe (PID: 3576)
- batbox.exe (PID: 2504)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 3724)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
59
Monitored processes
12
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1276 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Monotone-HWID-Spoofer-0.0.1.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1900 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\Box.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1916 | tasklist /NH /FI "imagename eq Monotone.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2344 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\Getlen.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2504 | "C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\batbox.exe" | C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\batbox.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2580 | find /i "Monotone.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2600 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\Button.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\GetInput.exe" | C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\GetInput.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3576 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\process.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3676 | ping localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 217
Read events
1 198
Write events
19
Delete events
0
Modification events
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
10
Suspicious files
0
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\Box.bat | text | |
MD5:A95505942D3EBCF724F080B49D4E981F | SHA256:64556D24498BCD280CD7CC248A98ED22C4DB921495D825F141AF1547C8FDD275 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\AlternateStreamView.cfg | text | |
MD5:D298348206017D0CB04217887A677334 | SHA256:2E44DAD813EFA86DDBD849A53962C5BDCACC9BCC2039DC09BCB2C25C770F3D8B | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\Button.bat | text | |
MD5:96FEFE69F2FACF74197A8AF3004A6167 | SHA256:38AA0C1AD69D96732C776CBD73275F5CCB881D42158158B32815DAD869EF9876 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\UnbanComplete.vbs | text | |
MD5:4EDF8ECAF575C93E307BDCE09AA46E8C | SHA256:537F70F7B018610DFEDD4BCECF041D845EAB0C673E129185C2345EB68A95FE77 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\mac.txt | text | |
MD5:58726BCB98B77AFE581A7833C8F35F9A | SHA256:E53A19F0F36D7E7BE98522239E8AC2AF3248F4FE4B046D9FE270E3907CE11401 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\batbox.exe | executable | |
MD5:CB4A44BAA20AD26BF74615A7FC515A84 | SHA256:9553BC17FA0FD08E026C1865812B3388E3D5495A5394BBF671E5A8F21C79989A | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\hwid.ps1 | text | |
MD5:05673D49CC5F31E3D4812B7CB7419641 | SHA256:C7C54526B07F457E58D423AB22D61A0EFD78AD112BE2EF0A1EFE6C25013DF185 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\README.md | text | |
MD5:699D03E1E8ED798AEB721E8FD561682B | SHA256:4ABFD24B7422EE66D5849FDA386DFD1318DB4615F9126899A27FDB5A4FFA3D0D | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\host.txt | text | |
MD5:CDDA0101630962EAEE1EF0305C2028C0 | SHA256:ECF34C7BC93D5B7F1EA5D8D17E488946EED415128658DA3BA2D02633C543234B | |||
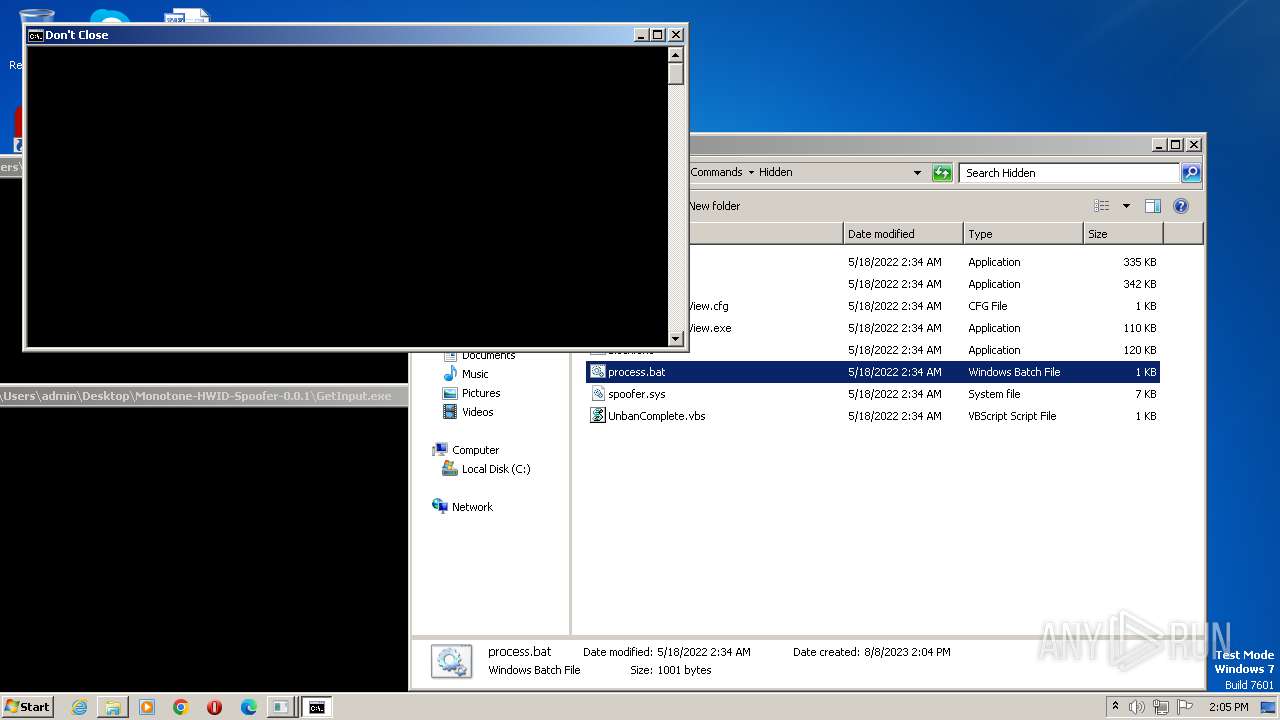
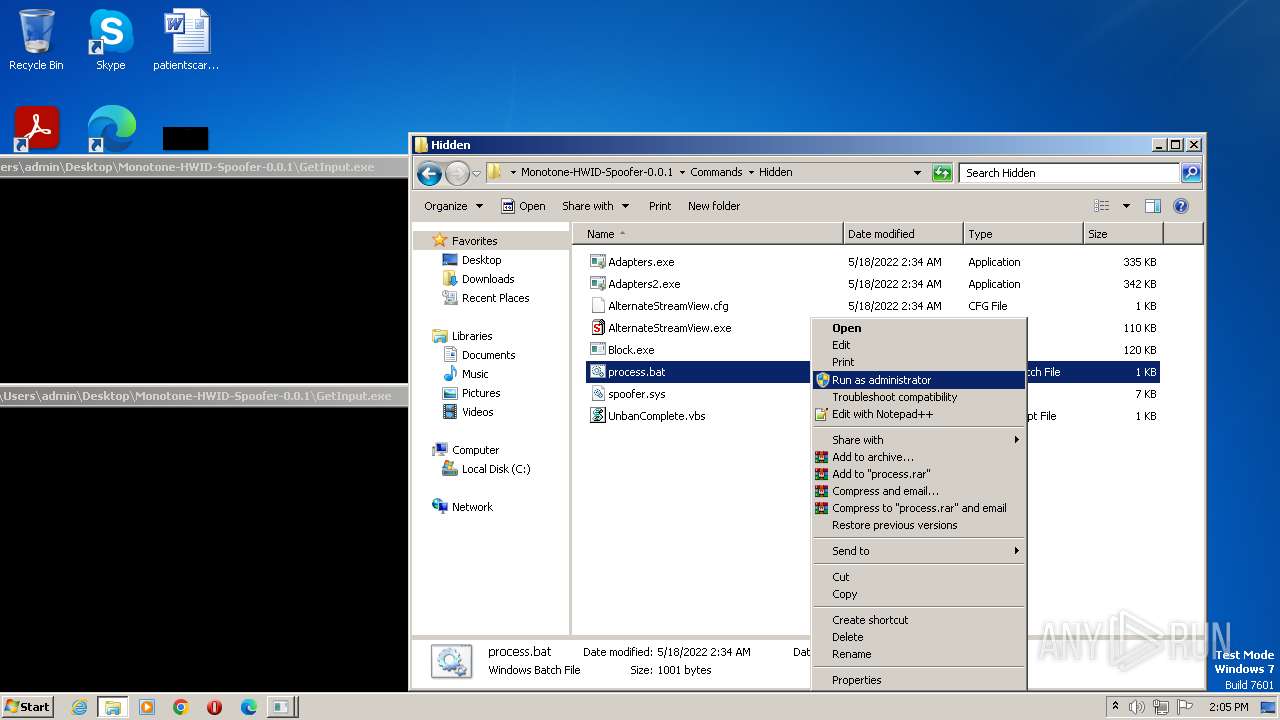
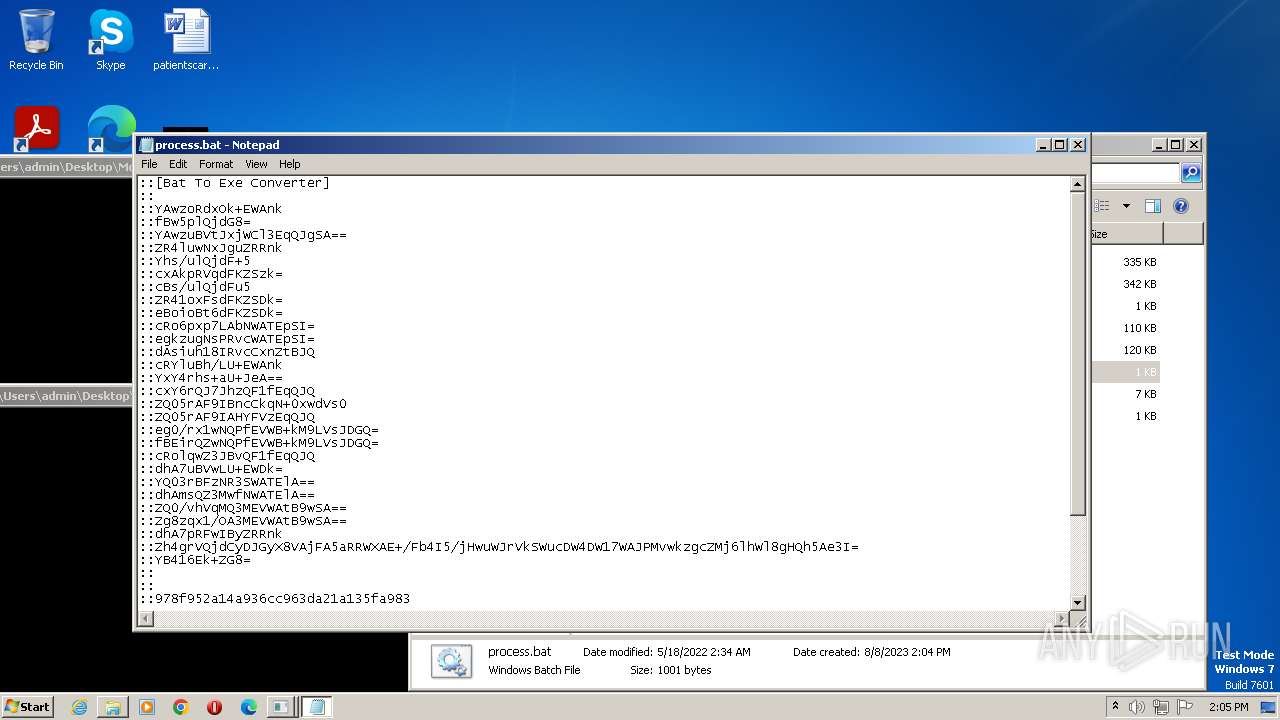
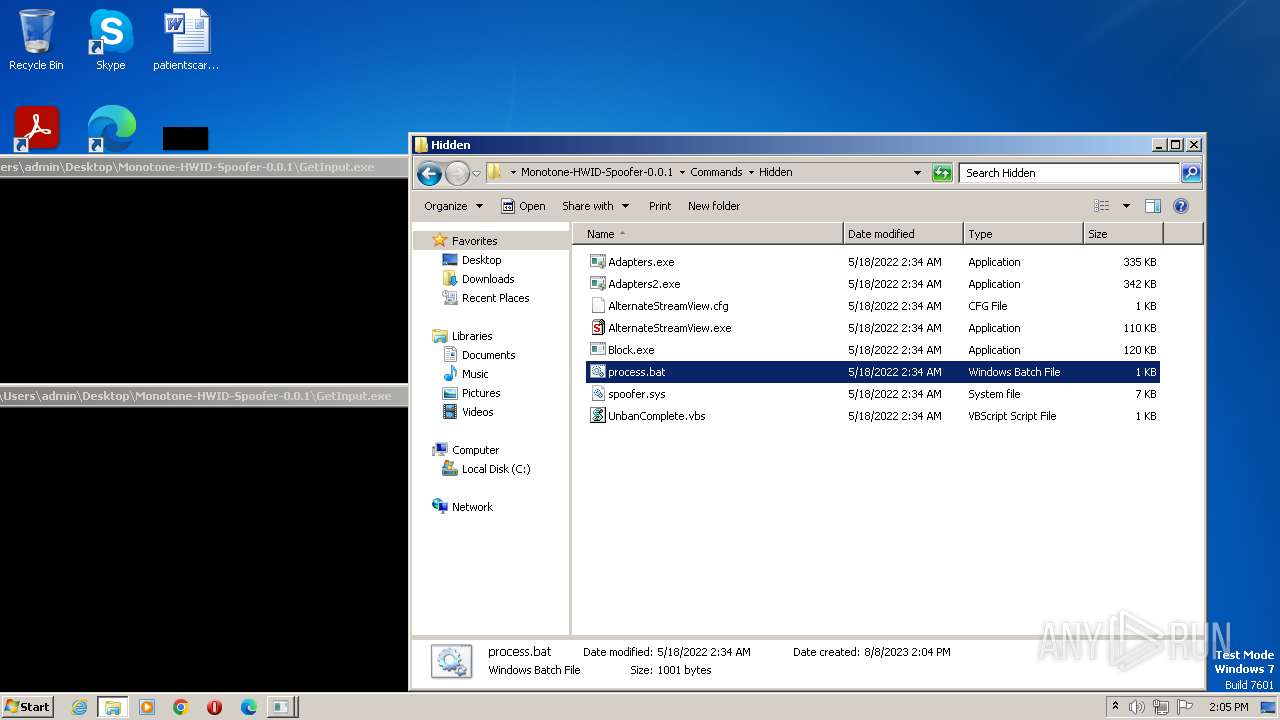
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.37214\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\process.bat | text | |
MD5:2D3F9B2D001ABD6E58AC6F0E7337C619 | SHA256:EF702CE2F8FB1BC71FB60E8B95CB83CEF4FA66AA96AFD7CA4FD67C96530B6E53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |