| File name: | .crdownload |
| Full analysis: | https://app.any.run/tasks/b8f97b54-724a-412c-ad9d-0a0b04d2c7fd |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2024, 14:30:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
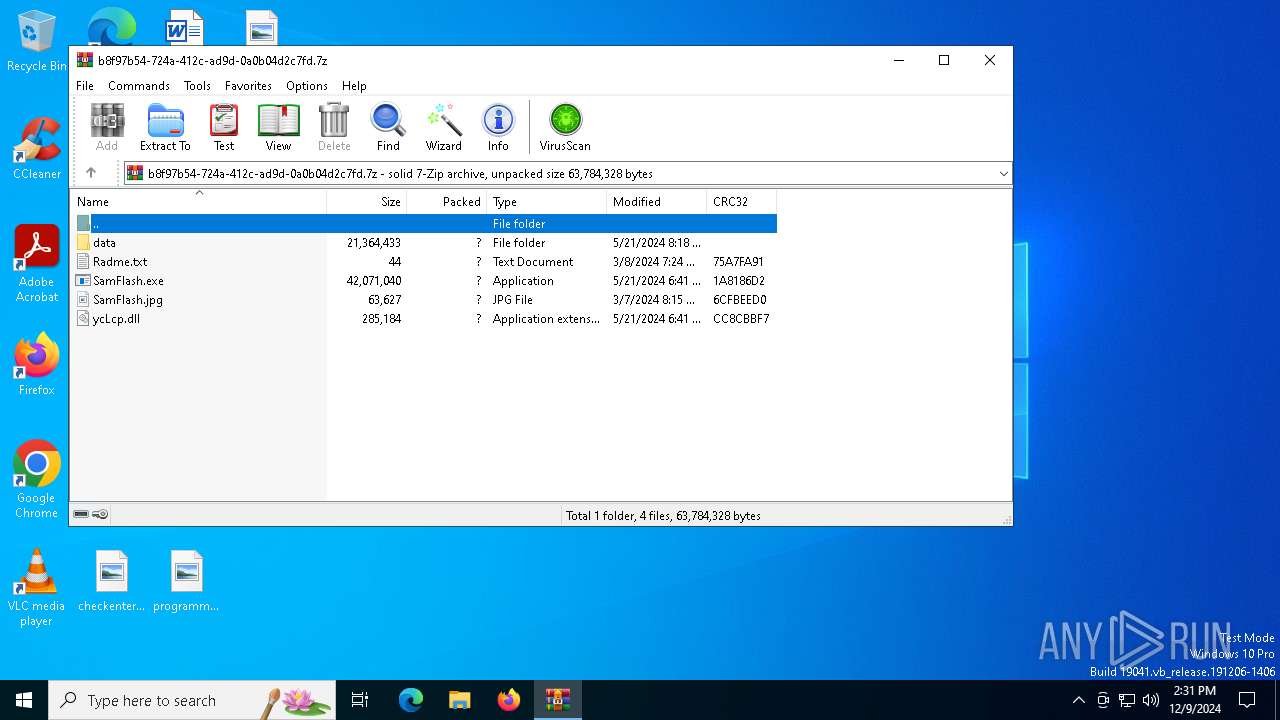
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | B77B39C881C3D159A5041DB48702E262 |
| SHA1: | E68446FF24594389894725F78948CC9168F25C75 |
| SHA256: | BF791A2F43CE7856AD76C87F06CB323735A92ACB1A4F17F4C5A6EA93A973AB19 |
| SSDEEP: | 393216:DftZbByPqUuTwsmaIQCGW11pbESZaO2Dh1uswrCGj9I4A1TdD:pp4lds3IQCGi1mSZa1Dh1uswZWp1V |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5096)
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 3820)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 5096)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5096)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5096)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5096)
INFO
Manual execution by a user
- install-filter.exe (PID: 4400)
- rundll32.exe (PID: 3744)
- OpenWith.exe (PID: 204)
- notepad.exe (PID: 3612)
Checks supported languages
- install-filter.exe (PID: 4400)
- MpCmdRun.exe (PID: 3820)
Reads the computer name
- MpCmdRun.exe (PID: 3820)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 204)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5096)
The process uses the downloaded file
- WinRAR.exe (PID: 5096)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:05:21 20:18:48+00:00 |
| ArchivedFileName: | data |
Total processes
117
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\8ae23cbdd3b5f3ee9037c7377ffa2dad8bf7c036.bin | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | install-filter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Radme.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3744 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\SamFlash.jpg | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3820 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | "C:\Users\admin\Desktop\install-filter.exe" | C:\Users\admin\Desktop\install-filter.exe | — | explorer.exe | |||||||||||
User: admin Company: http://libusb-win32.sourceforge.net Integrity Level: MEDIUM Description: libusb-win32 - Install-Filter Exit code: 4294967295 Version: 1.2.6.0 Modules
| |||||||||||||||
| 5096 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5888 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\Rar$Scan14626.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 928
Read events
2 919
Write events
9
Delete events
0
Modification events
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z | |||
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
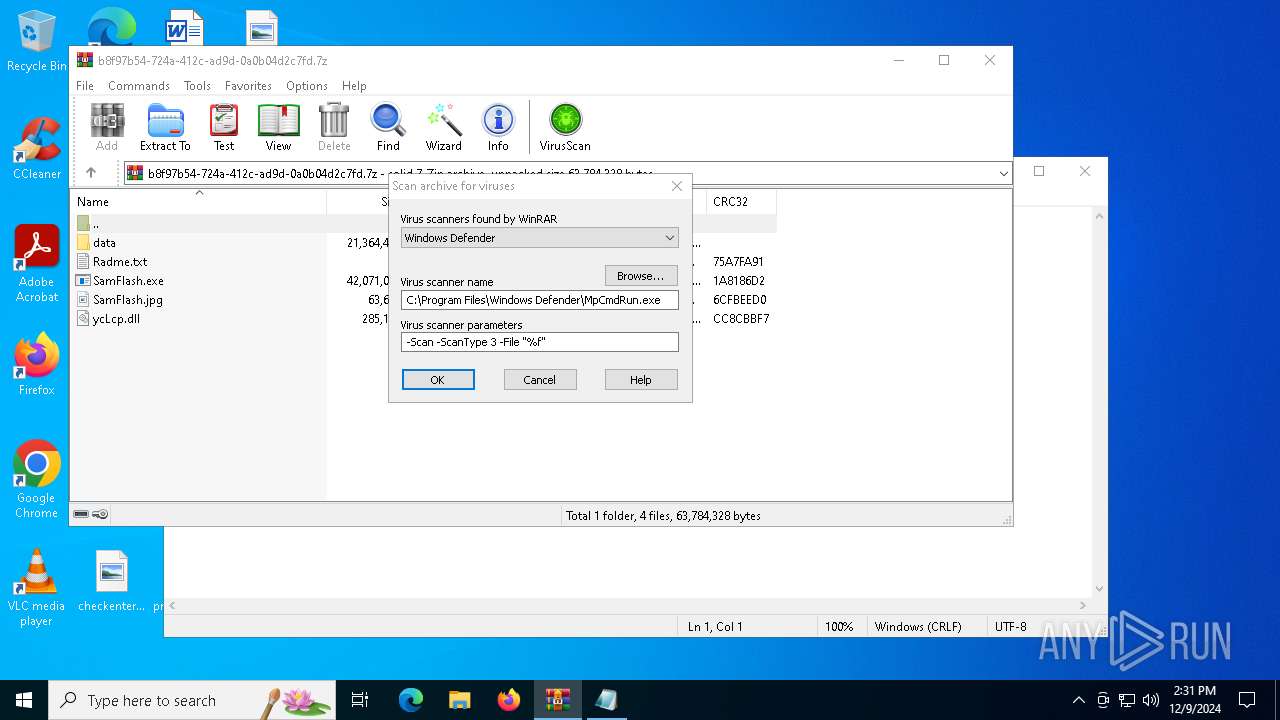
| (PID) Process: | (5096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
12
Suspicious files
12
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\data\loader\079fc51e57460e4ea9ccc9c98d08ee4728a1109c.bin | o | |
MD5:406421ADD08D335160DE789BB1A5D100 | SHA256:05AC3FCE76DBD7617D85B47CF322B75D6362EF1FFEB896639ED8B23FC0C11CE5 | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\data\loader\66ff4d4b730cebb967383a650b7cefbd8d681c57.bin | o | |
MD5:E3597190D113411E1CBDE6B29D59DA94 | SHA256:2107A6F06C1F19FF561B325F81F7D6B9A210C73BC3A77BA664EC841407E22D03 | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\SamFlash.jpg | image | |
MD5:9077B10CBB8C95FCC2359FD1491A9FDF | SHA256:3F5EF13FDA8ABBBBCA31558070C4C949DC4D311B0C564C25D3D96E3F4EDA63C4 | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\data\loader\674ac4a88d37e0cc585f310e53df597d8ad88c43.bin | o | |
MD5:4FB68A5169EB4034271D18437F0CFD84 | SHA256:EEFB3E649F71237C1E8C370D3C0F0A3D5EC29E9A6D9388522944422702CB6086 | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\data\loader\8ae23cbdd3b5f3ee9037c7377ffa2dad8bf7c036.bin | binary | |
MD5:1591976AF66042714D647058DA66769D | SHA256:DBB80135B4017282A181D2B0C13CEBE8F1239B114756EDE99083424F8426E424 | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\data\loader\27f620d71722f964eb2ccc1c0fb7fcbd48d4e79e.bin | o | |
MD5:26120C829CBD2C34FDD9A6CC3E5780CA | SHA256:9AEC3E68331A3CD230DDF878A5A322E4C85812A6F4982B8EC86DF5207C2C6EB6 | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\SamFlash.exe | — | |
MD5:— | SHA256:— | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\data\loader\58e8fc27a8543e11fd2ccaf98fbe261448bc8aca.bin | o | |
MD5:94B32EC7ED7C0A4F57EE91A62694DCA0 | SHA256:877B0017F1A17EEEB32C805FA2BD543078946B0F266EBD8CFE0A6C23889DE2CC | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\data\loader\88e16eb57235e6a900dac581d6c2bc463f7061cf.bin | binary | |
MD5:05EF0CE7A7BDFDB2720B673E63E6ABA3 | SHA256:DEFBC9219B85E4BED1BB925CC88943C132C0DF4D76FD66B520BC39D0FCE2C3EF | |||
| 5096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5096.982\b8f97b54-724a-412c-ad9d-0a0b04d2c7fd.7z\data\loader\d1a8e970429c5e6795db98bd3cadbdeb879a392c.bin | o | |
MD5:2C2745CB2DE08C2E0DF77093D2D5DA98 | SHA256:C7C1BCE40EFB53BF5688126FBEE96B6AE7997B288B742DB15FD96D4143A7F5B7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1684 | svchost.exe | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1684 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1684 | svchost.exe | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1684 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |