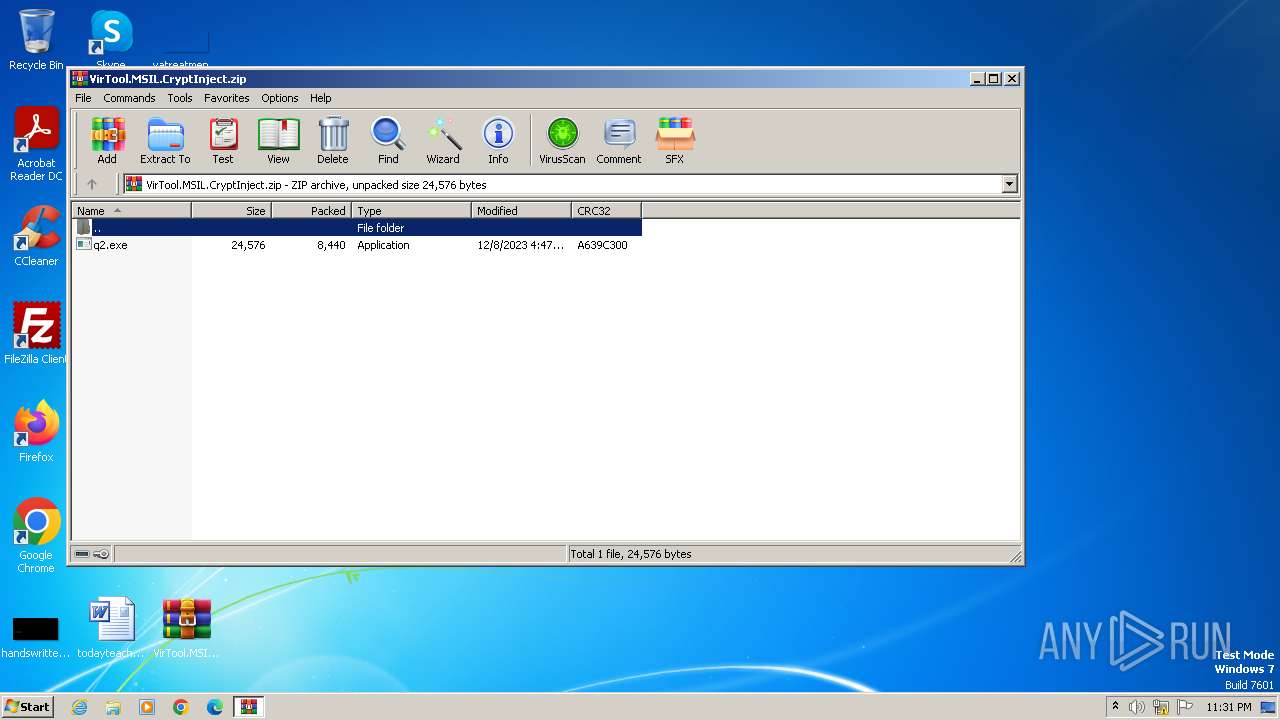
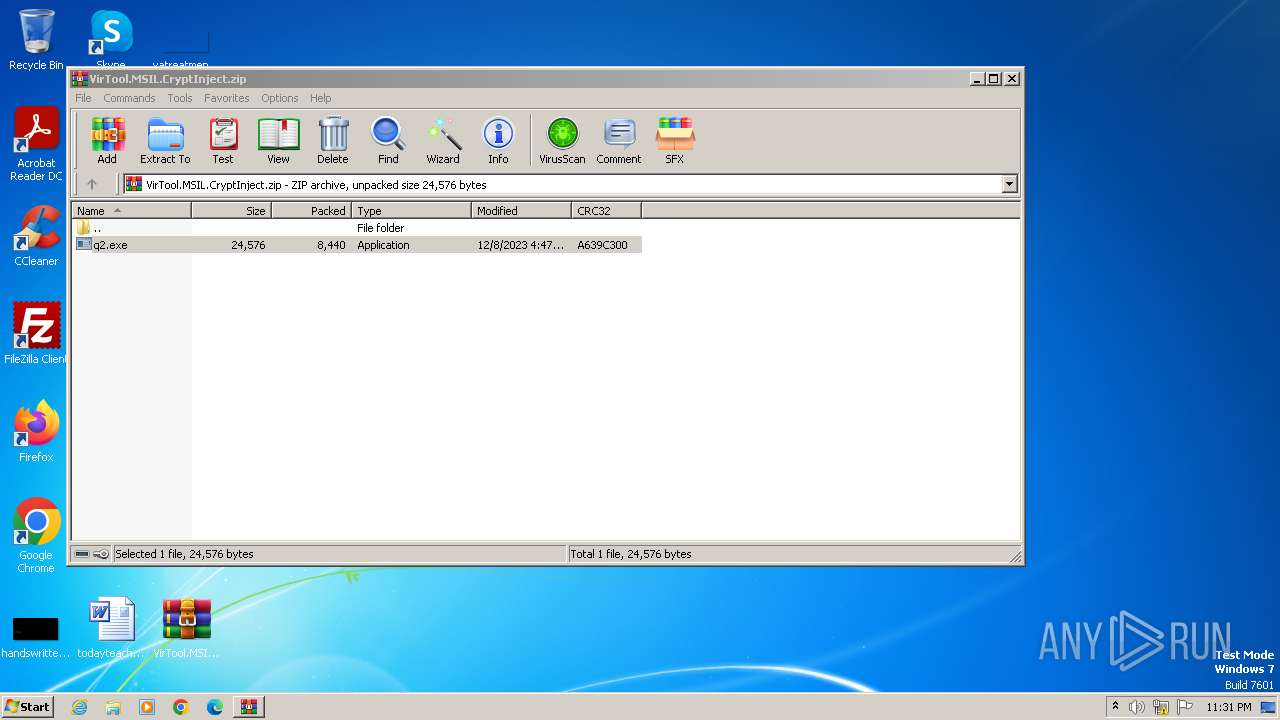
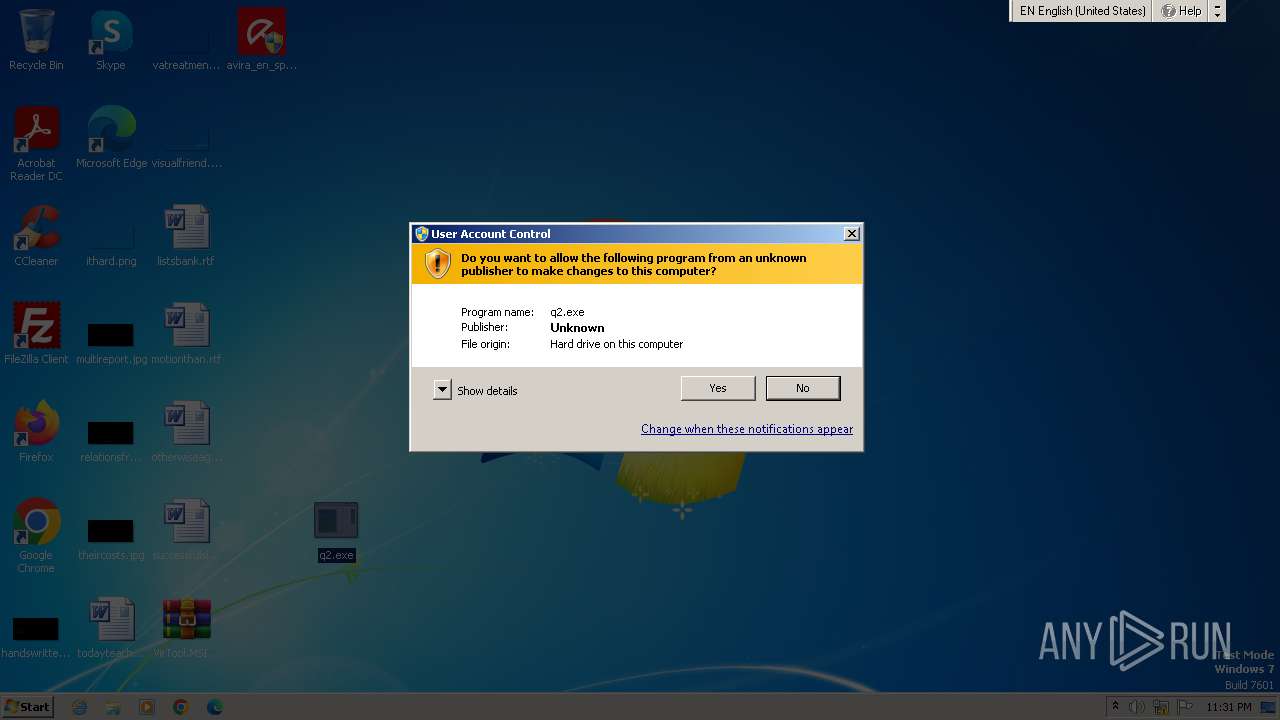
| File name: | VirTool.MSIL.CryptInject.zip |
| Full analysis: | https://app.any.run/tasks/af494b7c-c879-4a18-b4c5-506351891fff |
| Verdict: | Malicious activity |
| Analysis date: | December 08, 2023, 23:30:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F54A6C775A61AEF84419BA7221876B1B |
| SHA1: | 4D0DBB333CAA433D16670169D8278DE511025CF0 |
| SHA256: | BF7779098DA0EE1CD1E086C1F43DDCFE909878465B836E32D139C178B9B2815F |
| SSDEEP: | 192:KnKKduvzbRwoloJTK/0NZQCx3paXoA4BrFcgF5ak9KaCUzm1zi:KAv/RxlvGaYjB9N9VCOwi |
MALICIOUS
Uses Task Scheduler to run other applications
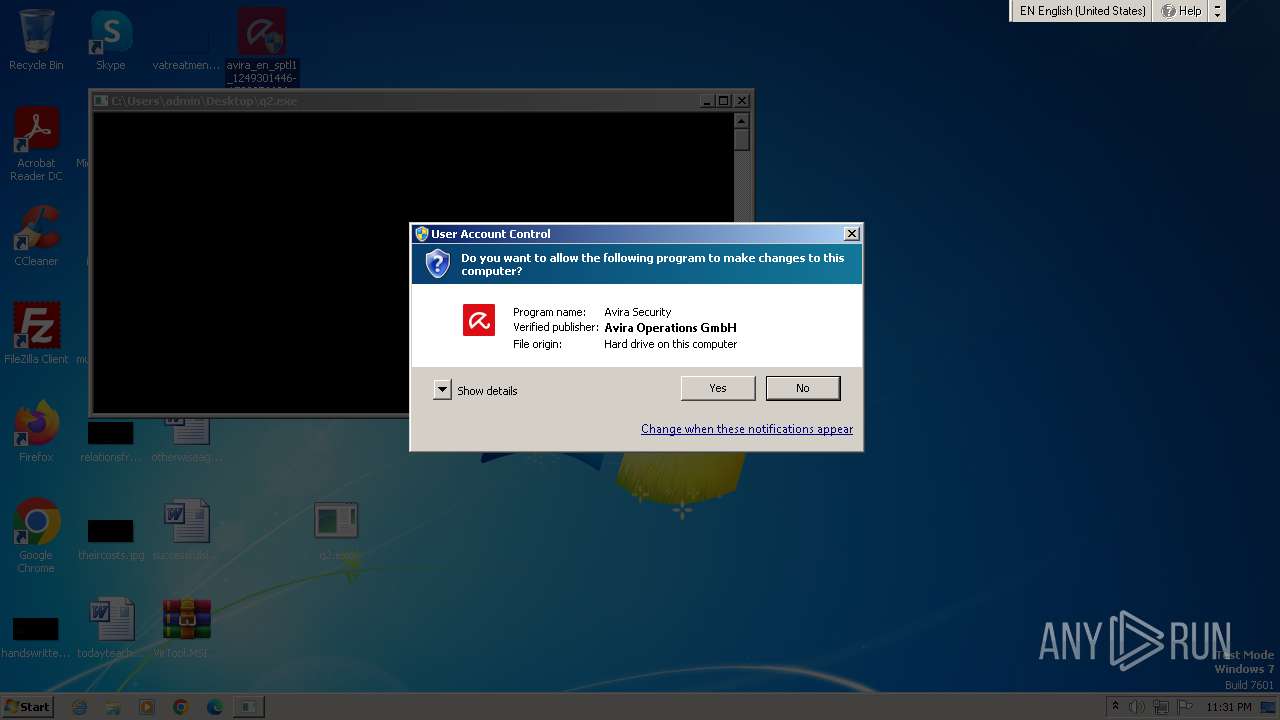
- avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe (PID: 3224)
Drops the executable file immediately after the start
- avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe (PID: 3224)
SUSPICIOUS
Reads settings of System Certificates
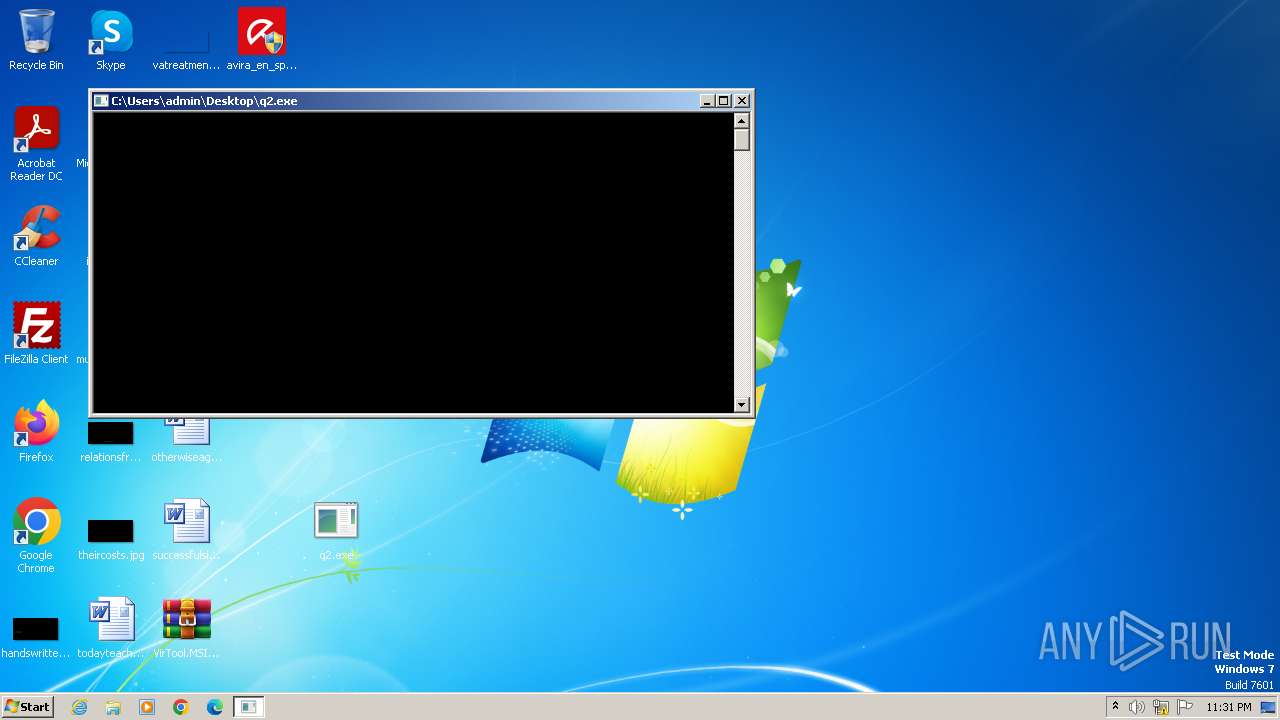
- q2.exe (PID: 3200)
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
Checks Windows Trust Settings
- q2.exe (PID: 3200)
Reads the Internet Settings
- q2.exe (PID: 3200)
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
Reads security settings of Internet Explorer
- q2.exe (PID: 3200)
The process creates files with name similar to system file names
- avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe (PID: 3224)
Searches for installed software
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
INFO
Checks supported languages
- q2.exe (PID: 3200)
- wmpnscfg.exe (PID: 4080)
- avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe (PID: 3224)
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
Checks proxy server information
- q2.exe (PID: 3200)
Reads the computer name
- q2.exe (PID: 3200)
- wmpnscfg.exe (PID: 4080)
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3048)
Creates files or folders in the user directory
- q2.exe (PID: 3200)
Manual execution by a user
- wmpnscfg.exe (PID: 4080)
- q2.exe (PID: 3200)
- avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe (PID: 3224)
Reads the machine GUID from the registry
- q2.exe (PID: 3200)
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
Create files in a temporary directory
- avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe (PID: 3224)
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
Reads Environment values
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
Creates files in the program directory
- Avira.Spotlight.Bootstrapper.exe (PID: 3380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:08 16:47:32 |
| ZipCRC: | 0xa639c300 |
| ZipCompressedSize: | 8440 |
| ZipUncompressedSize: | 24576 |
| ZipFileName: | q2.exe |
Total processes
52
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3048 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\VirTool.MSIL.CryptInject.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3200 | "C:\Users\admin\Desktop\q2.exe" | C:\Users\admin\Desktop\q2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3224 | "C:\Users\admin\Desktop\avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe" | C:\Users\admin\Desktop\avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe | explorer.exe | ||||||||||||
User: admin Company: Avira Operations GmbH Integrity Level: HIGH Description: Avira Security Exit code: 0 Version: 1.0.45.1 Modules
| |||||||||||||||
| 3380 | "C:\Users\admin\AppData\Local\Temp\.CR.27401\Avira.Spotlight.Bootstrapper.exe" "C:\Users\admin\AppData\Local\Temp\.CR.27401\Avira.Spotlight.Bootstrapper.exe" OriginalFileName=avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe | C:\Users\admin\AppData\Local\Temp\.CR.27401\Avira.Spotlight.Bootstrapper.exe | avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe | ||||||||||||
User: admin Company: Avira Operations GmbH Integrity Level: HIGH Description: Avira Security Exit code: 0 Version: 1.0.45.1 Modules
| |||||||||||||||
| 3776 | "C:\Windows\system32\schtasks.exe" /Create /Xml "C:\Users\admin\AppData\Local\Temp\.CR.4225\Avira_Security_Installation.xml" /F /TN "Avira_Security_Installation" | C:\Windows\System32\schtasks.exe | — | avira_en_sptl1_1249301446-1702076626__pavwws-spotlight-release.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4080 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
30 552
Read events
30 392
Write events
160
Delete events
0
Modification events
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
3
Suspicious files
7
Text files
2 418
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\1OIA0KV8.htm | html | |
MD5:5308620F06B1B61F0AE32E12A2DA954E | SHA256:F0BF2A2AB411B245AABE88214B65DCBAF37A55D9EBDAFA43DEB15FDDE6CBFE87 | |||
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\WX731MYG.htm | html | |
MD5:5308620F06B1B61F0AE32E12A2DA954E | SHA256:F0BF2A2AB411B245AABE88214B65DCBAF37A55D9EBDAFA43DEB15FDDE6CBFE87 | |||
| 3048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3048.25895\q2.exe | executable | |
MD5:C04FD8D9198095192E7D55345966DA2E | SHA256:0C98769E42B364711C478226EF199BFBBA90DB80175EB1B8CD565AA694C09852 | |||
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\0M55NSGJ.htm | html | |
MD5:5308620F06B1B61F0AE32E12A2DA954E | SHA256:F0BF2A2AB411B245AABE88214B65DCBAF37A55D9EBDAFA43DEB15FDDE6CBFE87 | |||
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\HFMBKB47.htm | html | |
MD5:5308620F06B1B61F0AE32E12A2DA954E | SHA256:F0BF2A2AB411B245AABE88214B65DCBAF37A55D9EBDAFA43DEB15FDDE6CBFE87 | |||
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\B40MXLLM.htm | html | |
MD5:5308620F06B1B61F0AE32E12A2DA954E | SHA256:F0BF2A2AB411B245AABE88214B65DCBAF37A55D9EBDAFA43DEB15FDDE6CBFE87 | |||
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\J944RMBQ.htm | html | |
MD5:B3B7B65619C07EE6E6C7058B33FD780A | SHA256:71E7FD08F132E6E0AE6CA65C1703BA29C36B319CA8F1949009ED2EDC13CB8C70 | |||
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\JBOYJY3G.htm | html | |
MD5:B3B7B65619C07EE6E6C7058B33FD780A | SHA256:71E7FD08F132E6E0AE6CA65C1703BA29C36B319CA8F1949009ED2EDC13CB8C70 | |||
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\R7H3HNY1.htm | html | |
MD5:5308620F06B1B61F0AE32E12A2DA954E | SHA256:F0BF2A2AB411B245AABE88214B65DCBAF37A55D9EBDAFA43DEB15FDDE6CBFE87 | |||
| 3200 | q2.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\XIZLTA0U.htm | html | |
MD5:5308620F06B1B61F0AE32E12A2DA954E | SHA256:F0BF2A2AB411B245AABE88214B65DCBAF37A55D9EBDAFA43DEB15FDDE6CBFE87 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2 402
TCP/UDP connections
18
DNS requests
10
Threats
2 417
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.malwareanalysisbook.com/ | unknown | html | 74 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.malwareanalysisbook.com/ | unknown | html | 74 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.malwareanalysisbook.com/ | unknown | html | 74 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.malwareanalysisbook.com/ | unknown | html | 74 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.malwareanalysisbook.com/ | unknown | html | 74 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.practicalmalwareanalysis.com/ | unknown | html | 63 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.malwareanalysisbook.com/ | unknown | html | 74 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.practicalmalwareanalysis.com/ | unknown | html | 63 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.malwareanalysisbook.com/ | unknown | html | 74 b | unknown |
3200 | q2.exe | GET | 301 | 15.197.142.173:80 | http://www.malwareanalysisbook.com/ | unknown | html | 74 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3200 | q2.exe | 15.197.142.173:80 | www.malwareanalysisbook.com | AMAZON-02 | US | unknown |
3200 | q2.exe | 104.20.120.46:443 | nostarch.com | CLOUDFLARENET | — | unknown |
3200 | q2.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
3200 | q2.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3380 | Avira.Spotlight.Bootstrapper.exe | 35.158.225.56:443 | dispatch.avira-update.com | AMAZON-02 | DE | unknown |
3380 | Avira.Spotlight.Bootstrapper.exe | 35.186.241.51:443 | api.mixpanel.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.malwareanalysisbook.com |
| whitelisted |
www.practicalmalwareanalysis.com |
| whitelisted |
nostarch.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dispatch.avira-update.com |
| unknown |
api.mixpanel.com |
| whitelisted |
api.my.avira.com |
| unknown |
package.avira.com |
| unknown |
Threats
2417 ETPRO signatures available at the full report