| File name: | Tftpd32_Installer_v4.71.exe |
| Full analysis: | https://app.any.run/tasks/50fa806c-6f5b-47fd-8e58-97bd5ed3a6a7 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2025, 18:41:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | A97D39DF28EE1F5388BC47B0A572A9D4 |
| SHA1: | 7393728112AE61D17F77A8C2FA48E64108670CA3 |
| SHA256: | BF47A3A494FA30E64C1FE32A9FFB1EC73BA60A0C01719036512E6CDEA5B4A4CF |
| SSDEEP: | 24576:h/JYpobkTT7bSUAxi9a1FZilgWiMgLXvYyYUsLd9bmZImxmpJT:h/JSobkTT7bSUAxi9a13i2WLgLXvYyY/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Tftpd32_Installer_v4.71.exe (PID: 6656)
- dllhost.exe (PID: 1160)
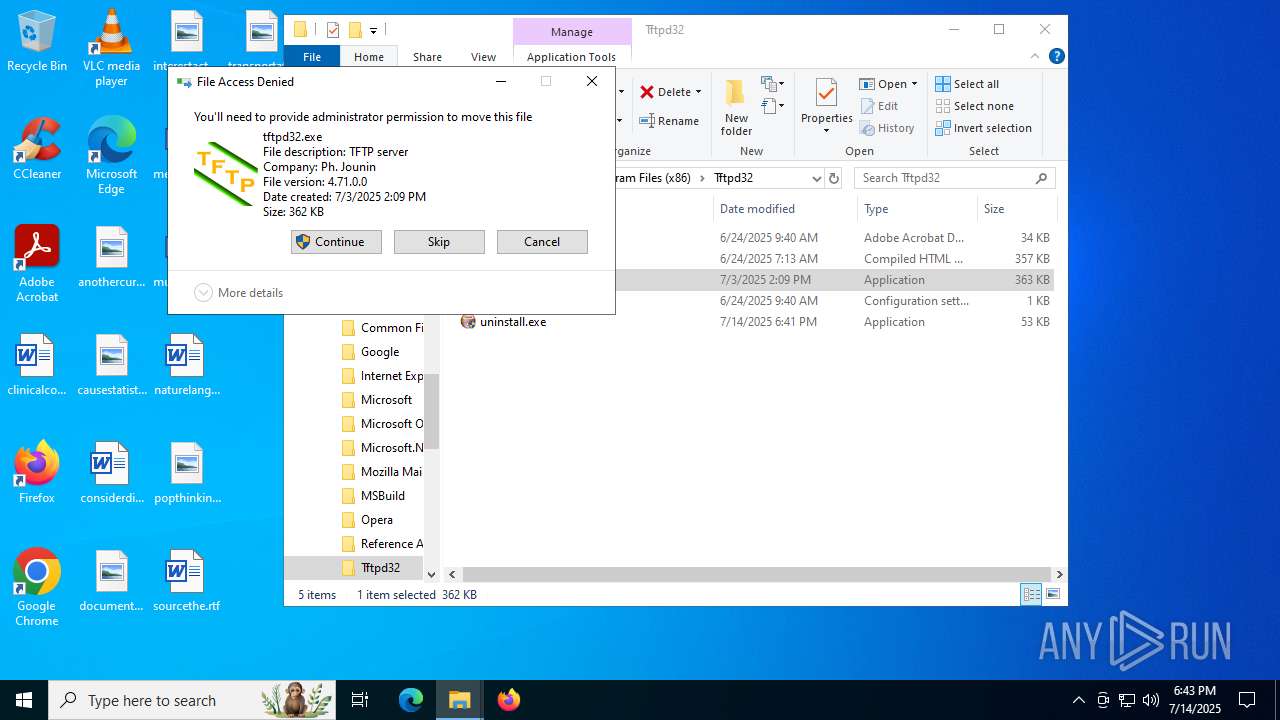
The process creates files with name similar to system file names
- Tftpd32_Installer_v4.71.exe (PID: 6656)
Malware-specific behavior (creating "System.dll" in Temp)
- Tftpd32_Installer_v4.71.exe (PID: 6656)
There is functionality for taking screenshot (YARA)
- Tftpd32_Installer_v4.71.exe (PID: 6656)
- tftpd32.exe (PID: 2732)
Creates a software uninstall entry
- Tftpd32_Installer_v4.71.exe (PID: 6656)
Reads security settings of Internet Explorer
- tftpd32.exe (PID: 2732)
Reads Microsoft Outlook installation path
- hh.exe (PID: 6140)
Reads Internet Explorer settings
- hh.exe (PID: 6140)
INFO
Create files in a temporary directory
- Tftpd32_Installer_v4.71.exe (PID: 6656)
- hh.exe (PID: 6140)
Checks supported languages
- Tftpd32_Installer_v4.71.exe (PID: 6656)
- tftpd32.exe (PID: 2732)
- tftpd32.exe (PID: 5172)
Reads the computer name
- Tftpd32_Installer_v4.71.exe (PID: 6656)
- tftpd32.exe (PID: 2732)
- tftpd32.exe (PID: 5172)
Creates files in the program directory
- Tftpd32_Installer_v4.71.exe (PID: 6656)
Creates files or folders in the user directory
- Tftpd32_Installer_v4.71.exe (PID: 6656)
- hh.exe (PID: 6140)
The sample compiled with french language support
- Tftpd32_Installer_v4.71.exe (PID: 6656)
- dllhost.exe (PID: 1160)
Process checks computer location settings
- tftpd32.exe (PID: 2732)
Manual execution by a user
- tftpd32.exe (PID: 2732)
- tftpd32.exe (PID: 5172)
Reads security settings of Internet Explorer
- hh.exe (PID: 6140)
- dllhost.exe (PID: 1160)
Checks proxy server information
- hh.exe (PID: 6140)
- slui.exe (PID: 7120)
The sample compiled with english language support
- hh.exe (PID: 6140)
Reads the software policy settings
- slui.exe (PID: 7120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:08 23:05:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x358d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
151
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1160 | C:\WINDOWS\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2732 | "C:\Program Files (x86)\Tftpd32\tftpd32.exe" | C:\Program Files (x86)\Tftpd32\tftpd32.exe | explorer.exe | ||||||||||||
User: admin Company: Ph. Jounin Integrity Level: MEDIUM Description: TFTP server Exit code: 0 Modules
| |||||||||||||||
| 4984 | "C:\Users\admin\Downloads\Tftpd32_Installer_v4.71.exe" | C:\Users\admin\Downloads\Tftpd32_Installer_v4.71.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5172 | "C:\Users\admin\Desktop\tftpd32.exe" | C:\Users\admin\Desktop\tftpd32.exe | explorer.exe | ||||||||||||
User: admin Company: Ph. Jounin Integrity Level: MEDIUM Description: TFTP server Exit code: 0 Modules
| |||||||||||||||
| 6140 | "C:\WINDOWS\hh.exe" C:\Program Files (x86)\Tftpd32\Tftpd32.chm | C:\Windows\hh.exe | — | tftpd32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6656 | "C:\Users\admin\Downloads\Tftpd32_Installer_v4.71.exe" | C:\Users\admin\Downloads\Tftpd32_Installer_v4.71.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7120 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 830
Read events
2 817
Write events
11
Delete events
2
Modification events
| (PID) Process: | (6656) Tftpd32_Installer_v4.71.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Tftpd32 |
| Operation: | write | Name: | DisplayName |
Value: Tftpd32 | |||
| (PID) Process: | (6656) Tftpd32_Installer_v4.71.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Tftpd32 |
| Operation: | write | Name: | DisplayVersion |
Value: 4.71 | |||
| (PID) Process: | (6656) Tftpd32_Installer_v4.71.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Tftpd32 |
| Operation: | write | Name: | Publisher |
Value: Ph. Jounin | |||
| (PID) Process: | (6656) Tftpd32_Installer_v4.71.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Tftpd32 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Tftpd32 | |||
| (PID) Process: | (6656) Tftpd32_Installer_v4.71.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Tftpd32 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Tftpd32\tftpd32.exe | |||
| (PID) Process: | (6656) Tftpd32_Installer_v4.71.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Tftpd32 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Tftpd32\uninstall.exe | |||
| (PID) Process: | (6656) Tftpd32_Installer_v4.71.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Tftpd32 |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files (x86)\Tftpd32 | |||
| (PID) Process: | (2732) tftpd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.chm\OpenWithProgids |
| Operation: | write | Name: | chm.file |
Value: | |||
| (PID) Process: | (6140) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6140) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
5
Suspicious files
4
Text files
4
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6656 | Tftpd32_Installer_v4.71.exe | C:\Users\admin\AppData\Local\Temp\nsi4A77.tmp\nsDialogs.dll | executable | |
MD5:8F0E7415F33843431DF308BB8E06AF81 | SHA256:BB49F15FA83452370047A7801E39FC7F64E70C7545B8999BB85AA4749EAA048B | |||
| 6656 | Tftpd32_Installer_v4.71.exe | C:\Users\admin\AppData\Local\Temp\nsi4A77.tmp\System.dll | executable | |
MD5:9B38A1B07A0EBC5C7E59E63346ECC2DB | SHA256:C881253DAFCF1322A771139B1A429EC1E78C507CA81A218A20DC1A4B25ABBFE7 | |||
| 6656 | Tftpd32_Installer_v4.71.exe | C:\Program Files (x86)\Tftpd32\uninstall.exe | executable | |
MD5:E788AE095D406FDBEA0B904B298FB379 | SHA256:E2BAF7BCFE4DEAF09534CB90FDCEEDC46E9375678F023F474BC350C93C83600E | |||
| 6140 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\style[1].css | text | |
MD5:299697A50846097E56D45A7B018E31E8 | SHA256:86E2B6DEB97EC52E9C718C1AE59C1BE804A5F80E94EFCD044E4529E9927246D6 | |||
| 6656 | Tftpd32_Installer_v4.71.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Tftpd32\Help.lnk | lnk | |
MD5:CD198AF07DAA5567C8B66E18FF2A8896 | SHA256:58A2D5A293126B687EFDEAFC8618A1ED6F944B538E6E6B9510B37849FC04A140 | |||
| 6140 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\it_works[1].jpg | image | |
MD5:F2A6CC3DDD6209061C00F8301B364E2E | SHA256:48D0D20F7DE3AF20E835C00710A12AFA55512EE3672B18D649E34DED3FF34846 | |||
| 6140 | hh.exe | C:\Users\admin\AppData\Local\Temp\IMTB527.tmp | binary | |
MD5:37DD1A3FC6A8F6C87C0DEA4894C67293 | SHA256:04BBCBC68D2BD1692A924256596DD3708E19CB9879CB01CC4BBB6BF76FD74374 | |||
| 6140 | hh.exe | C:\Users\admin\AppData\Local\Temp\~DF9935316E4D784643.TMP | binary | |
MD5:72F5C05B7EA8DD6059BF59F50B22DF33 | SHA256:1DC0C8D7304C177AD0E74D3D2F1002EB773F4B180685A7DF6BBE75CCC24B0164 | |||
| 6140 | hh.exe | C:\Users\admin\AppData\Local\Temp\~DF0A37C882312D28F4.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6656 | Tftpd32_Installer_v4.71.exe | C:\Program Files (x86)\Tftpd32\tftpd32.exe | executable | |
MD5:F0566AA73CCAC7A49D3EAA23449E4C15 | SHA256:F0EF282A0CAE736AC88A6434130D358EE8DCF1D85407D4FA2AA83703DF022FC1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
40
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2464 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6940 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6940 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5060 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2464 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2464 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5328 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
tftpd32.exe | Th 6384 :opening comm socket
|
tftpd32.exe | Th 6384 :Console disconnected |
tftpd32.exe | Th 6384 :Verify Console/GUI parameters
|
tftpd32.exe | Th 6384 :Version check OK
|
tftpd32.exe | Th 6664 :Port 17152 may be reused
|
tftpd32.exe | Th 2144 :GUI Version check OK
|
tftpd32.exe | Th 6384 :Console connected |
tftpd32.exe | Th 2144 :connected to console
|
tftpd32.exe | Th 2124 :Scheduler signal received |
tftpd32.exe | Th 2124 :Scheduler signal received |