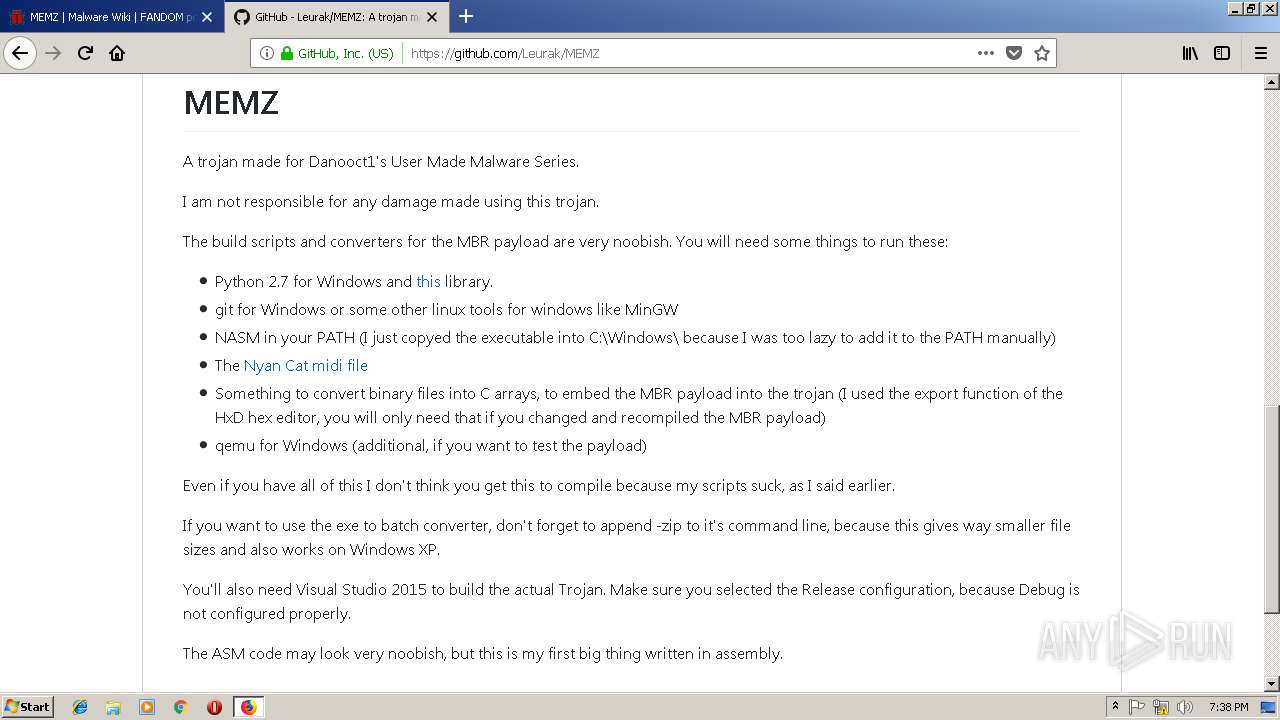
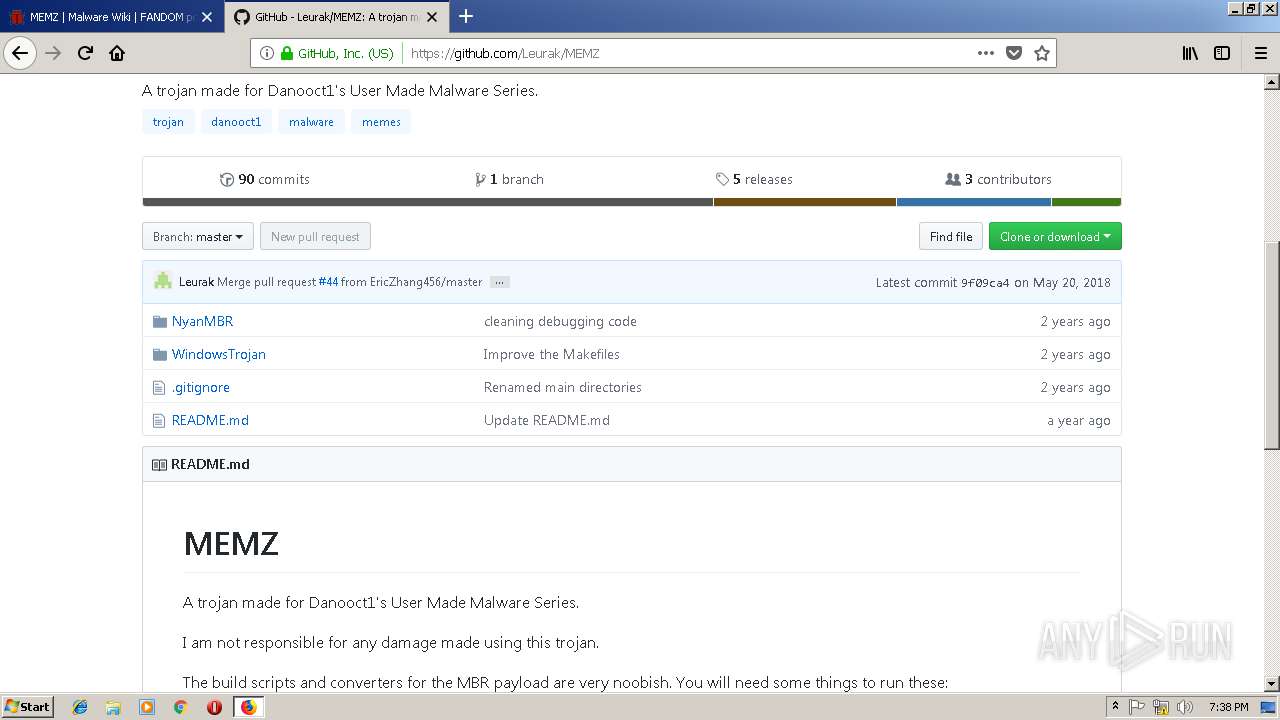
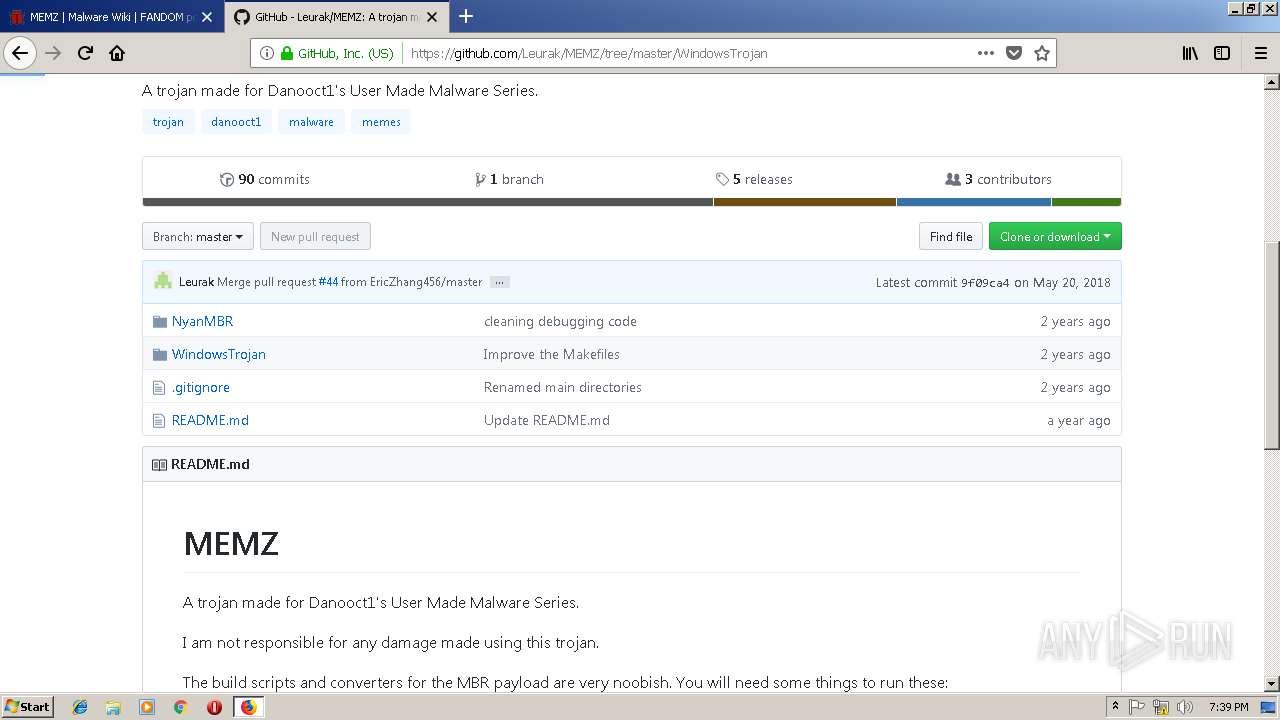
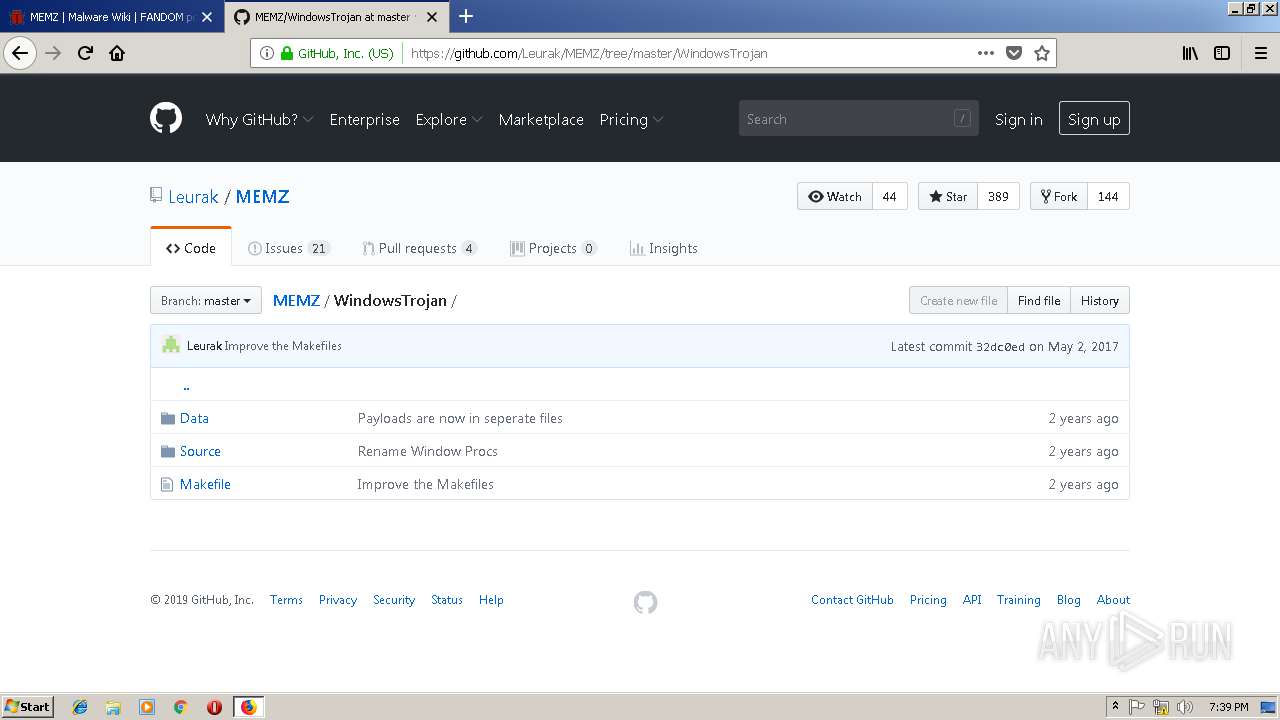
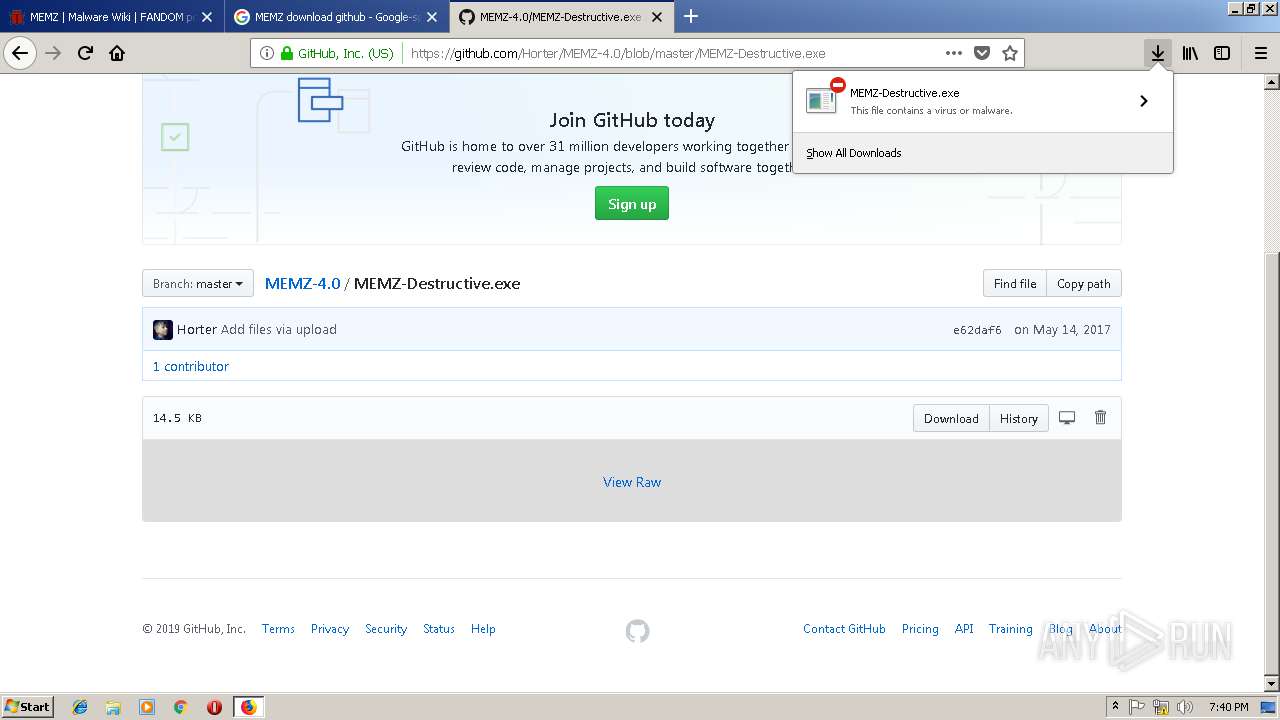
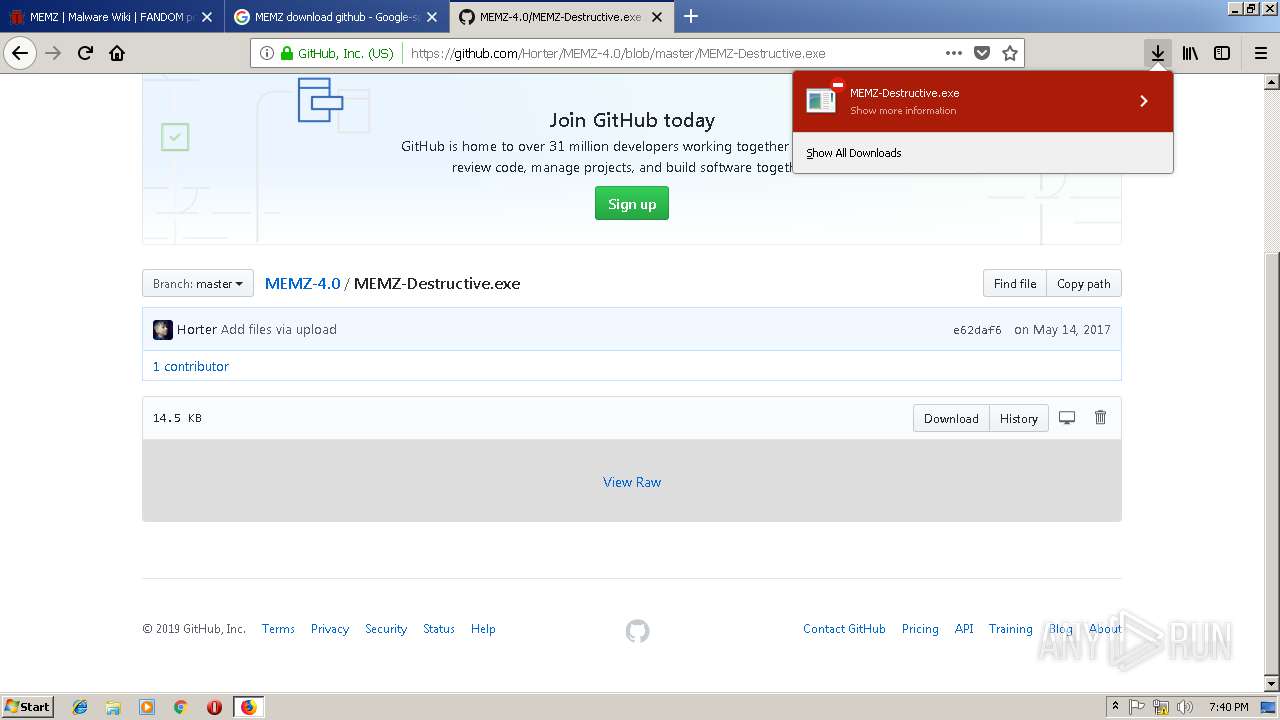
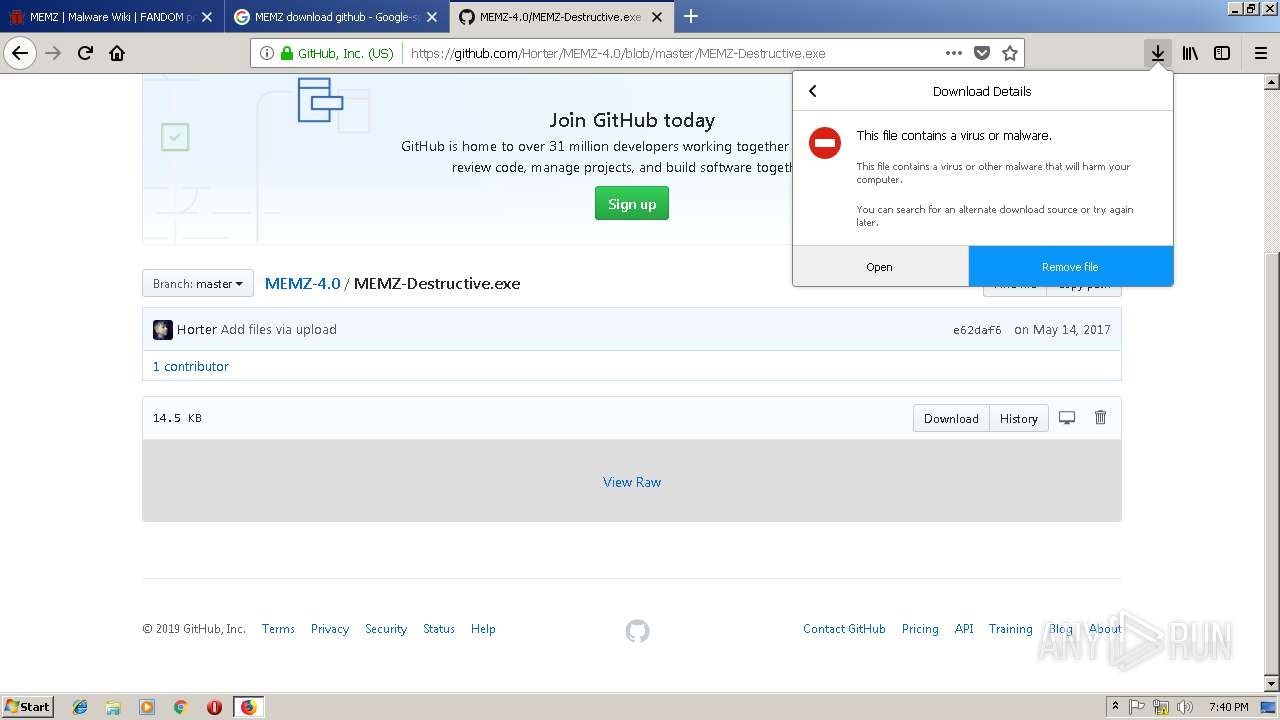
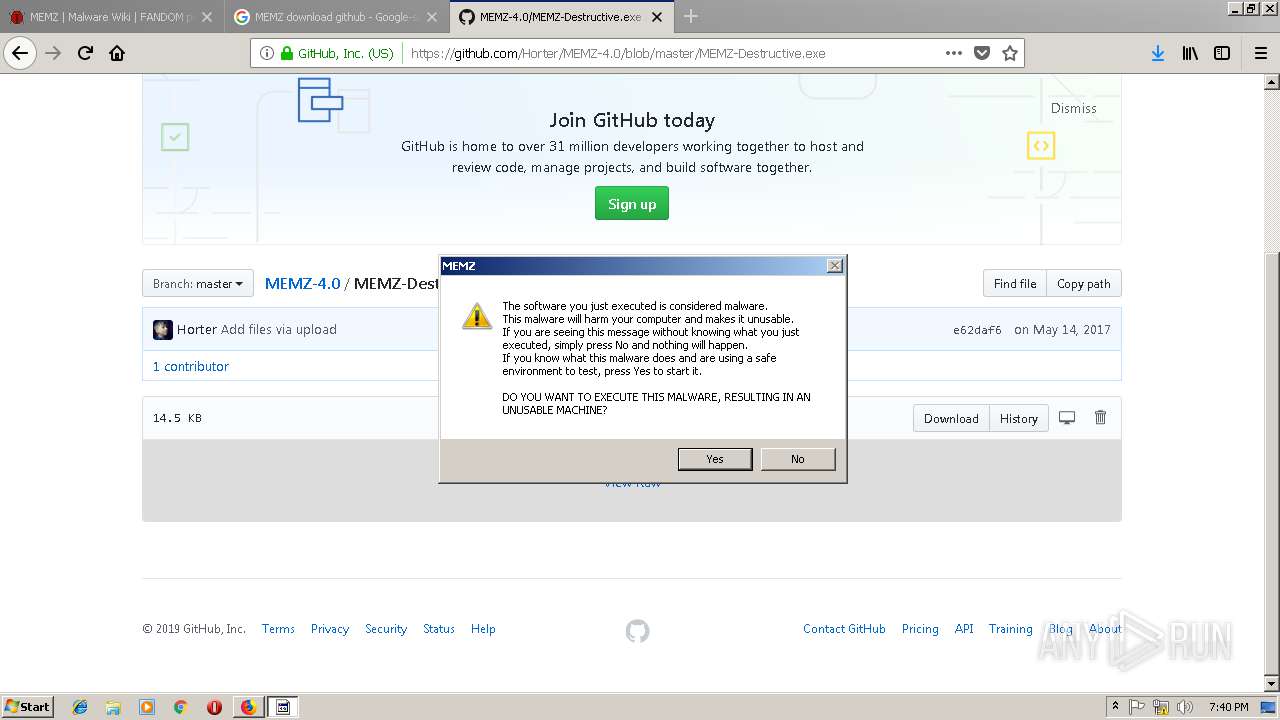
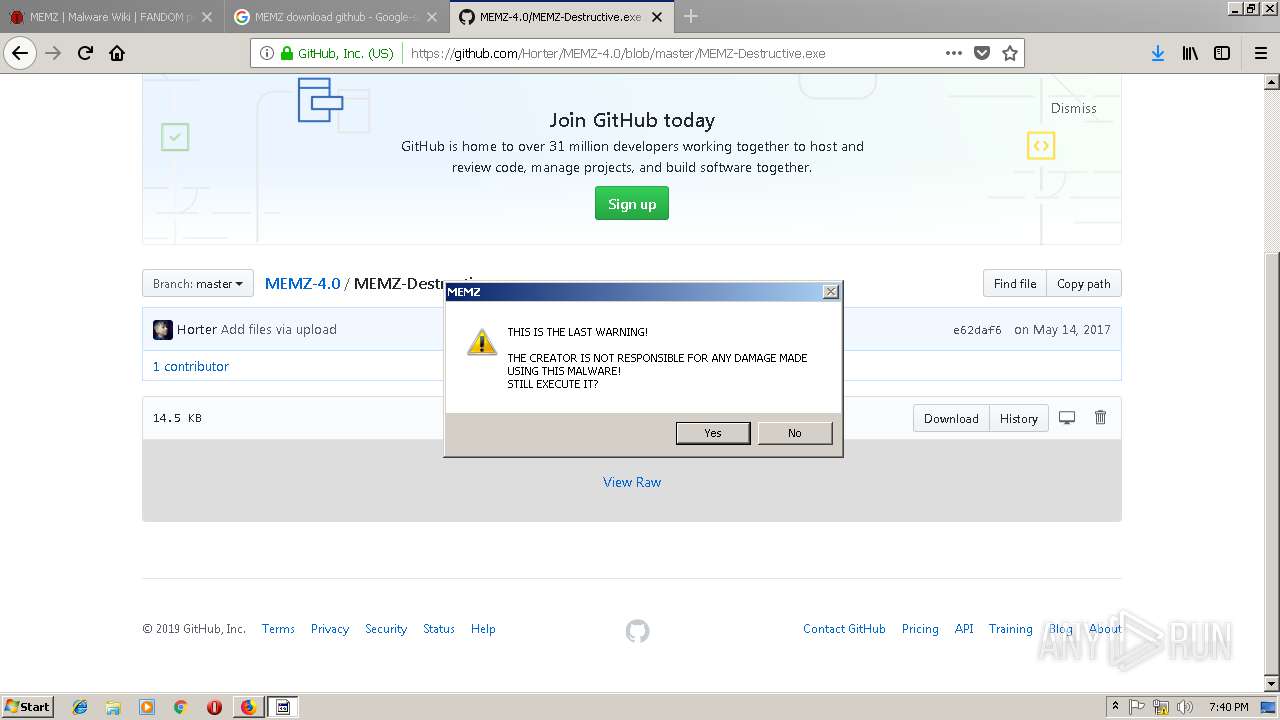
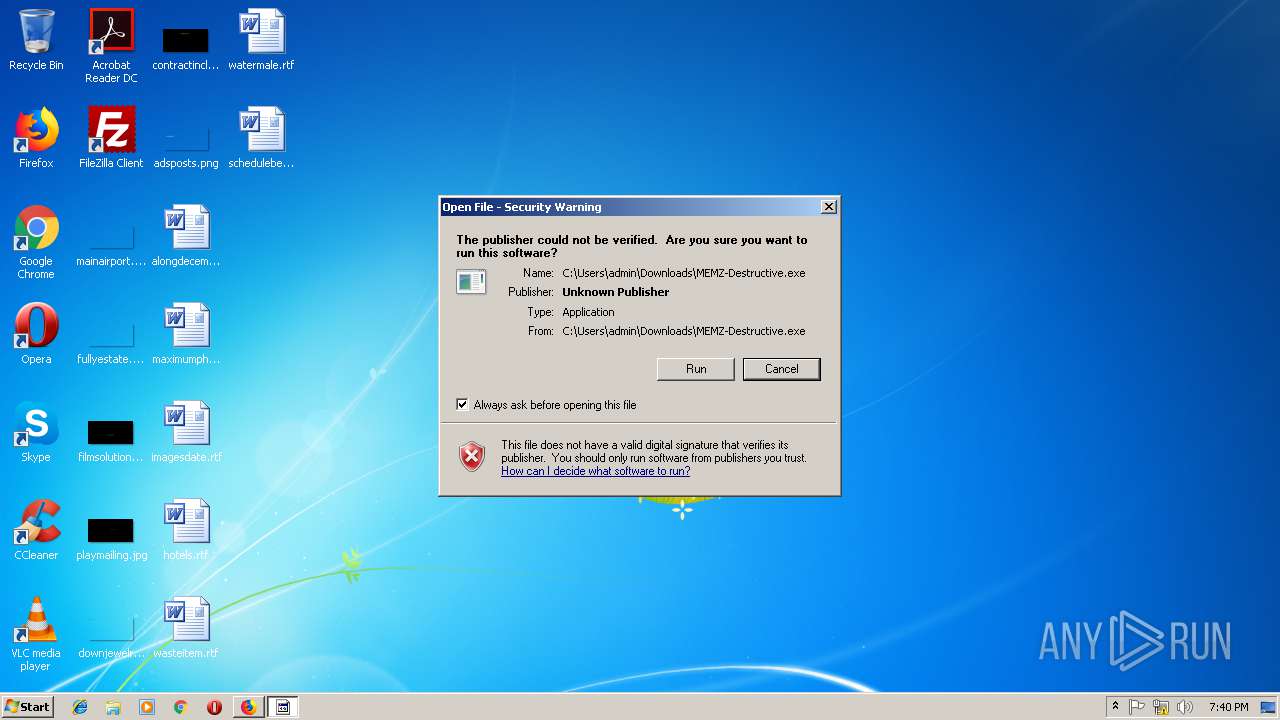
| URL: | http://malware.wikia.com/wiki/MEMZ |
| Full analysis: | https://app.any.run/tasks/7559eb69-ec04-466a-9a56-41571e5f6e87 |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2019, 19:35:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A4514B6518327C60F9F8286B8A8D8A3A |
| SHA1: | 0121420A32607B0CD6CD2FF4029BEF8FEC2477A4 |
| SHA256: | BF30458C42269F49C9A97E4758E915AA6E25F931348C5A644DE00D6C1AB9169B |
| SSDEEP: | 3:N1KTTjdCjRn:Cxmn |
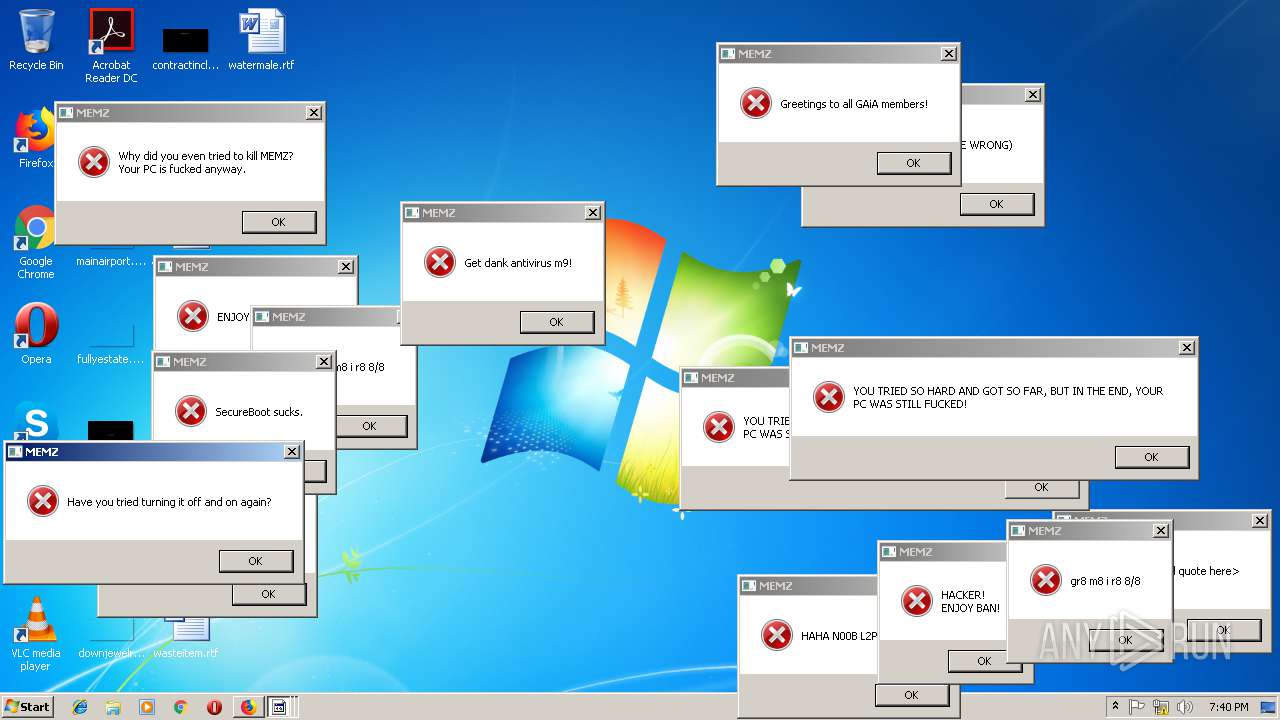
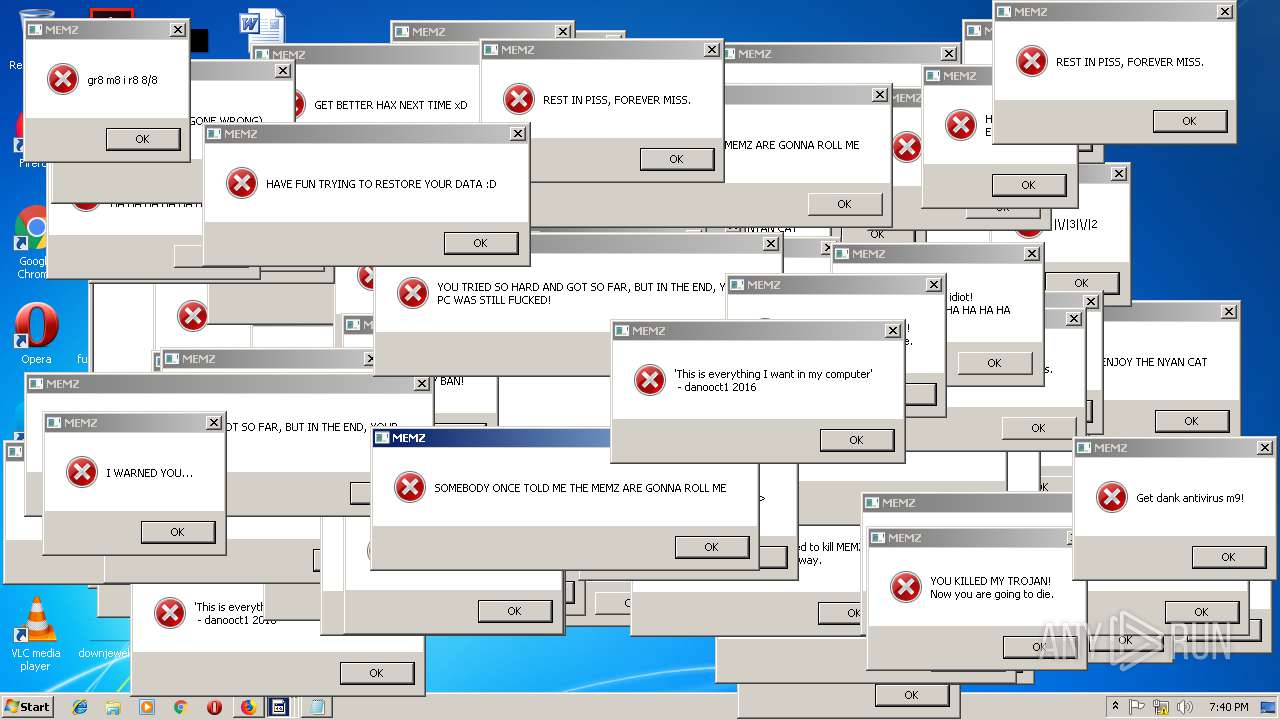
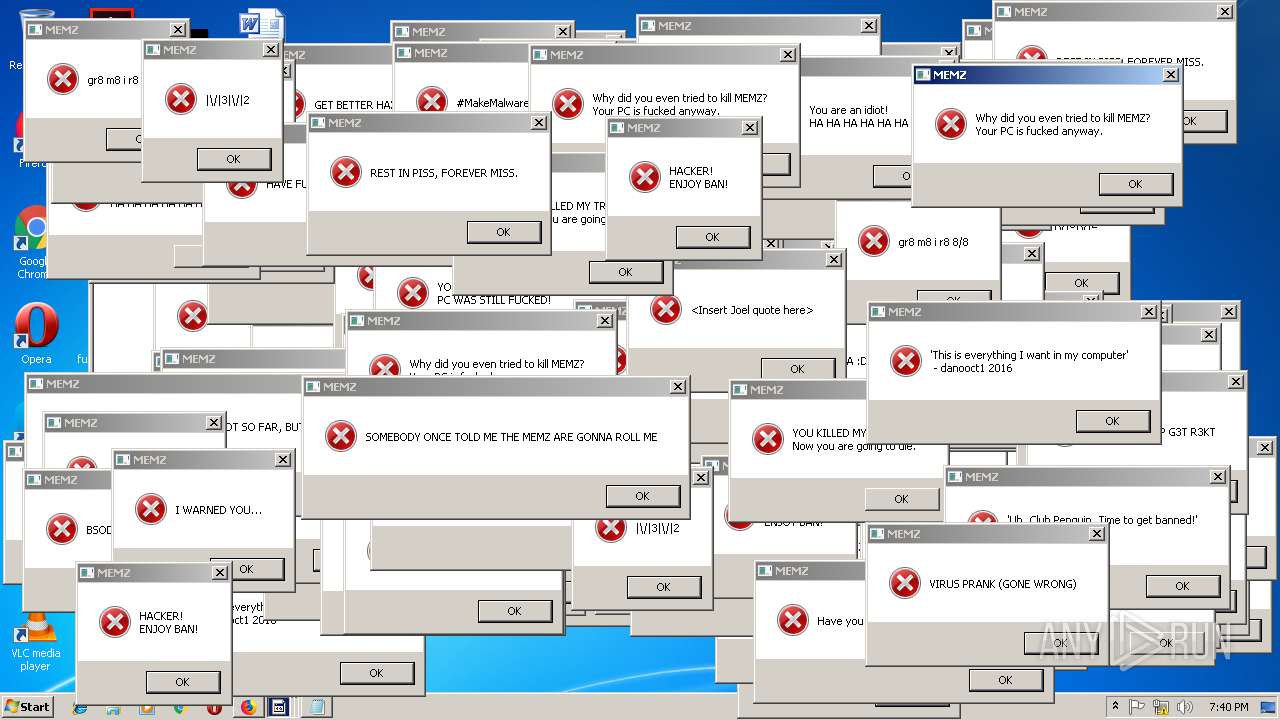
MALICIOUS
Application was dropped or rewritten from another process
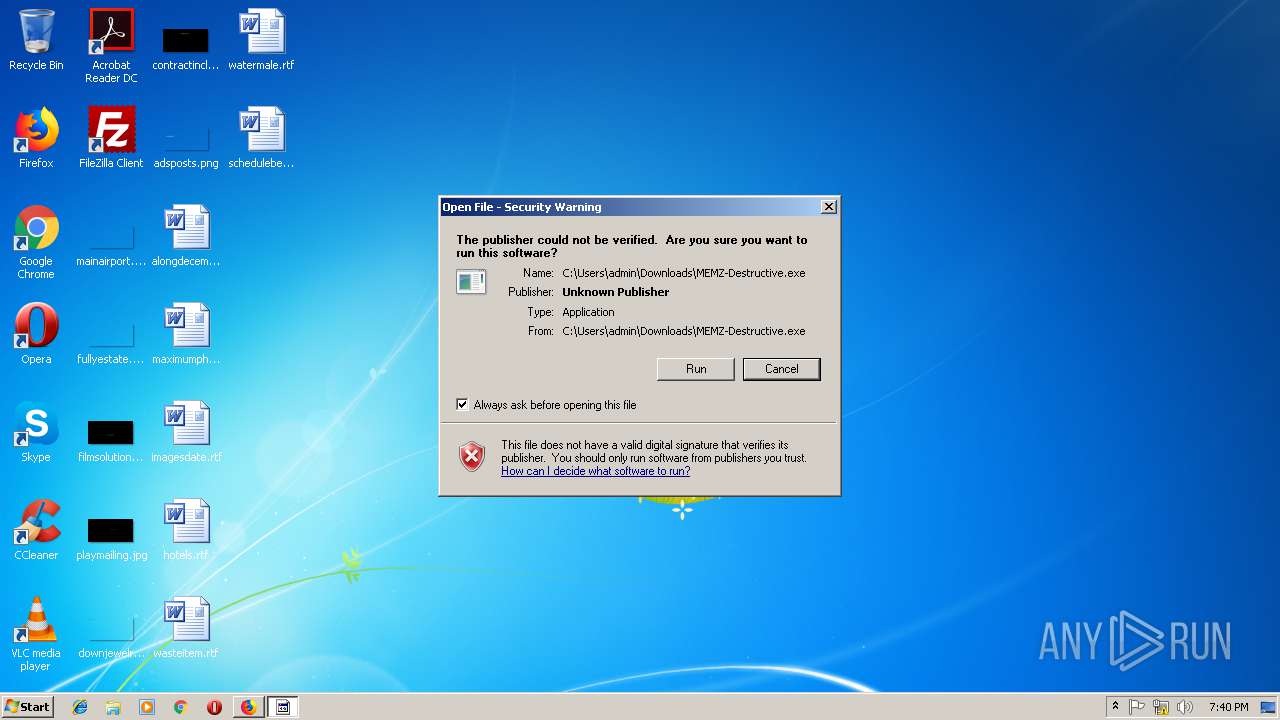
- MEMZ-Destructive.exe (PID: 3428)
- MEMZ-Destructive.exe (PID: 3540)
- MEMZ-Destructive.exe (PID: 3792)
- MEMZ-Destructive.exe (PID: 2296)
- MEMZ-Destructive.exe (PID: 992)
- MEMZ-Destructive.exe (PID: 672)
- MEMZ-Destructive.exe (PID: 2856)
- MEMZ-Destructive.exe (PID: 2396)
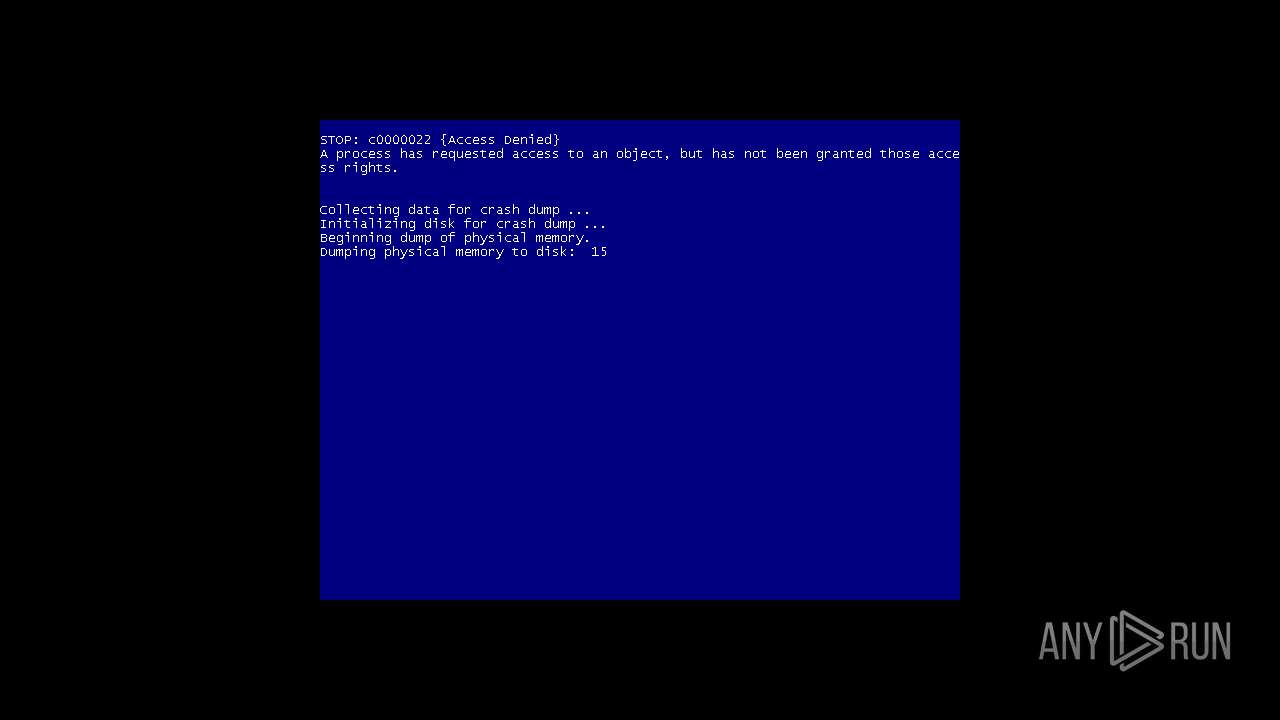
Low-level write access rights to disk partition
- MEMZ-Destructive.exe (PID: 2396)
SUSPICIOUS
Executable content was dropped or overwritten
- firefox.exe (PID: 2844)
Reads the time zone
- firefox.exe (PID: 2844)
Application launched itself
- MEMZ-Destructive.exe (PID: 3540)
Low-level read access rights to disk partition
- MEMZ-Destructive.exe (PID: 2396)
INFO
Reads CPU info
- firefox.exe (PID: 2412)
- firefox.exe (PID: 4060)
- firefox.exe (PID: 2844)
- firefox.exe (PID: 3216)
- firefox.exe (PID: 3332)
- firefox.exe (PID: 3752)
Application launched itself
- firefox.exe (PID: 2844)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 2844)
Reads settings of System Certificates
- firefox.exe (PID: 2844)
Creates files in the user directory
- firefox.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
49
Monitored processes
15
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
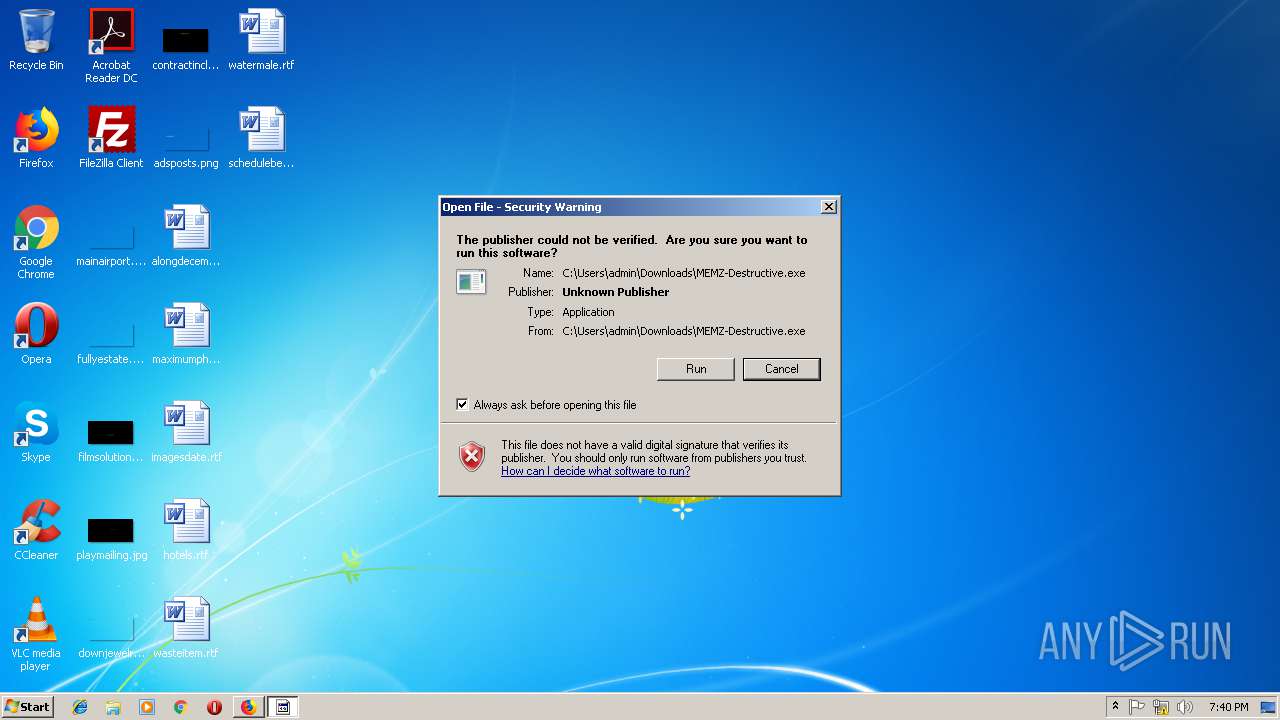
| 672 | "C:\Users\admin\Downloads\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\Downloads\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 992 | "C:\Users\admin\Downloads\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\Downloads\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2296 | "C:\Users\admin\Downloads\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\Downloads\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2320 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\System32\notepad.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | "C:\Users\admin\Downloads\MEMZ-Destructive.exe" /main | C:\Users\admin\Downloads\MEMZ-Destructive.exe | MEMZ-Destructive.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2412 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2844.0.669345918\282011083" -childID 1 -isForBrowser -prefsHandle 1344 -prefsLen 8310 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2844 "\\.\pipe\gecko-crash-server-pipe.2844" 1472 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2844 | "C:\Program Files\Mozilla Firefox\firefox.exe" http://malware.wikia.com/wiki/MEMZ | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2856 | "C:\Users\admin\Downloads\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\Downloads\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3216 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2844.6.1277920831\415660163" -childID 2 -isForBrowser -prefsHandle 2336 -prefsLen 11442 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2844 "\\.\pipe\gecko-crash-server-pipe.2844" 2456 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 3332 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2844.18.2012901595\1329348799" -childID 4 -isForBrowser -prefsHandle 2428 -prefsLen 12017 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2844 "\\.\pipe\gecko-crash-server-pipe.2844" 6608 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
Total events
1 429
Read events
1 405
Write events
24
Delete events
0
Modification events
| (PID) Process: | (2844) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2844) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2844) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2844) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2844) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3540) MEMZ-Destructive.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3540) MEMZ-Destructive.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2396) MEMZ-Destructive.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2396) MEMZ-Destructive.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
4
Suspicious files
974
Text files
237
Unknown types
156
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\cache2\entries\73C952277D16363DF312AFD30A519C0A3B8EB0C4 | compressed | |
MD5:— | SHA256:— | |||
| 2844 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
402
TCP/UDP connections
387
DNS requests
730
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2844 | firefox.exe | GET | 301 | 151.101.192.194:80 | http://dev.wikia.com/load.php?mode=articles&articles=u:dev:MediaWiki:RectangularButtons/code.css&only=styles | US | — | — | suspicious |
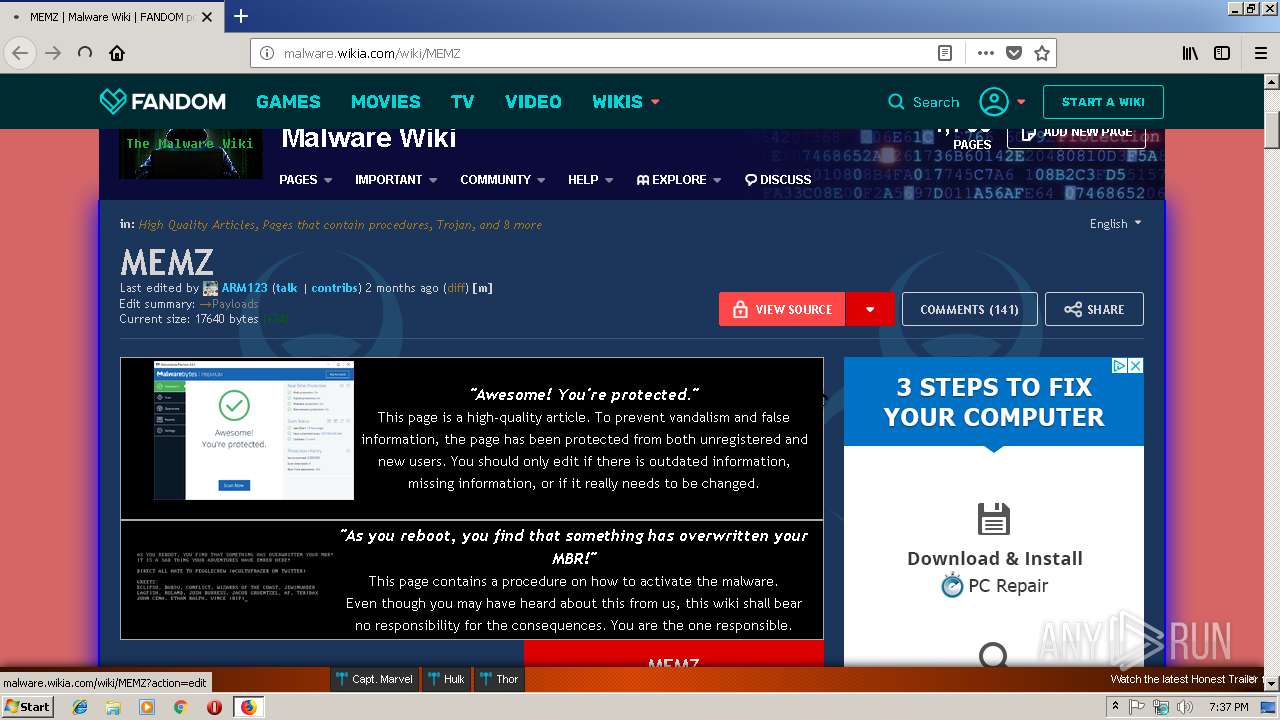
2844 | firefox.exe | GET | 200 | 151.101.0.194:80 | http://malware.wikia.com/wiki/MEMZ | US | html | 42.2 Kb | suspicious |
2844 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2844 | firefox.exe | GET | 200 | 151.101.0.194:80 | http://malware.wikia.com/load.php?cb=8150048150012&debug=false&lang=en&modules=site&only=styles&skin=oasis&* | US | text | 1.47 Kb | suspicious |
2844 | firefox.exe | GET | 200 | 151.101.0.194:80 | http://malware.wikia.com/wikia.php?controller=JSMessages&method=getMessages&format=html&packages=AdEngine%2CArticleVideo%2CConfirmModal%2CEditPageLayout%2CEmbeddableDiscussions%2CImagePlaceholder%2CMediaGallery%2COasis-generic%2CRecirculation&uselang=en&cb=8150048150012.0.0 | US | html | 1.82 Kb | suspicious |
2844 | firefox.exe | GET | 200 | 151.101.0.194:80 | http://malware.wikia.com/load.php?cb=8150048150012&debug=false&lang=en&modules=site&only=scripts&reviewed=1535489818&skin=oasis&* | US | text | 964 b | suspicious |
2844 | firefox.exe | GET | 200 | 151.101.0.194:80 | http://malware.wikia.com/load.php?cb=8150048150012&debug=false&lang=en&modules=ext.siteWideMessages.anon&only=scripts&skin=oasis&* | US | text | 1.07 Kb | suspicious |
2844 | firefox.exe | GET | 200 | 151.101.0.194:80 | http://malware.wikia.com/load.php?cb=8150048150012&debug=false&lang=en&modules=startup&newve=1&only=scripts&skin=oasis&* | US | text | 5.50 Kb | suspicious |
2844 | firefox.exe | GET | 200 | 151.101.0.194:80 | http://malware.wikia.com/load.php?mode=articles&only=styles&articles=u:dev:MediaWiki:ModernProfile/Masthead.css|u:dev:MediaWiki:ModernProfile/Wall.css | US | text | 1.88 Kb | suspicious |
2844 | firefox.exe | GET | 200 | 104.24.28.29:80 | http://puu.sh/pyeX9/83d808d9e1.cur | US | image | 4.19 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2844 | firefox.exe | 151.101.0.194:80 | malware.wikia.com | Fastly | US | suspicious |
2844 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
2844 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2844 | firefox.exe | 35.166.112.39:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
2844 | firefox.exe | 52.35.223.132:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
2844 | firefox.exe | 74.120.188.204:443 | slot1-images.wikia.nocookie.net | — | US | suspicious |
2844 | firefox.exe | 74.120.188.194:443 | slot1-images.wikia.nocookie.net | — | US | unknown |
2844 | firefox.exe | 151.101.2.66:443 | www.fastly-insights.com | Fastly | US | unknown |
2844 | firefox.exe | 151.101.192.194:80 | malware.wikia.com | Fastly | US | suspicious |
2844 | firefox.exe | 151.101.0.194:443 | malware.wikia.com | Fastly | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
malware.wikia.com |
| suspicious |
wikia.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cs9.wac.phicdn.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |