| File name: | bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe |
| Full analysis: | https://app.any.run/tasks/aaa4f397-1ee3-4a84-9294-98de7d62c4fc |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2019, 22:12:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | E486EDDFFD13BED33E68D6D8D4052270 |
| SHA1: | 53184DCFCEC948F02564234B5B8755FDDF066376 |
| SHA256: | BF25B330975DC700BE3F1F6B1B3362E34EB84B89725D4936D893CDD4F1499E69 |
| SSDEEP: | 98304:lZnAjm6EkJuUj9NQf7ebPrApx/f14s5JCW+oEo74Am83DwsgYzhW0Mf8:lNl6XYUsfqD2/NhCVohvx3E5CX |
MALICIOUS
Application was dropped or rewritten from another process
- javaTM.exe (PID: 3420)
- Java.exe (PID: 3040)
Writes to a start menu file
- javaTM.exe (PID: 3420)
Loads dropped or rewritten executable
- javaTM.exe (PID: 3420)
- Java.exe (PID: 3040)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 624)
- schtasks.exe (PID: 1940)
- schtasks.exe (PID: 1520)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 940)
- cmd.exe (PID: 3940)
- cmd.exe (PID: 3892)
SUSPICIOUS
Executable content was dropped or overwritten
- javaTM.exe (PID: 3420)
- JavaAlq.exe (PID: 4076)
- bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe (PID: 2928)
Starts CMD.EXE for commands execution
- javaTM.exe (PID: 3420)
- Java.exe (PID: 3040)
Creates files in the user directory
- javaTM.exe (PID: 3420)
- bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe (PID: 2928)
- Java.exe (PID: 3040)
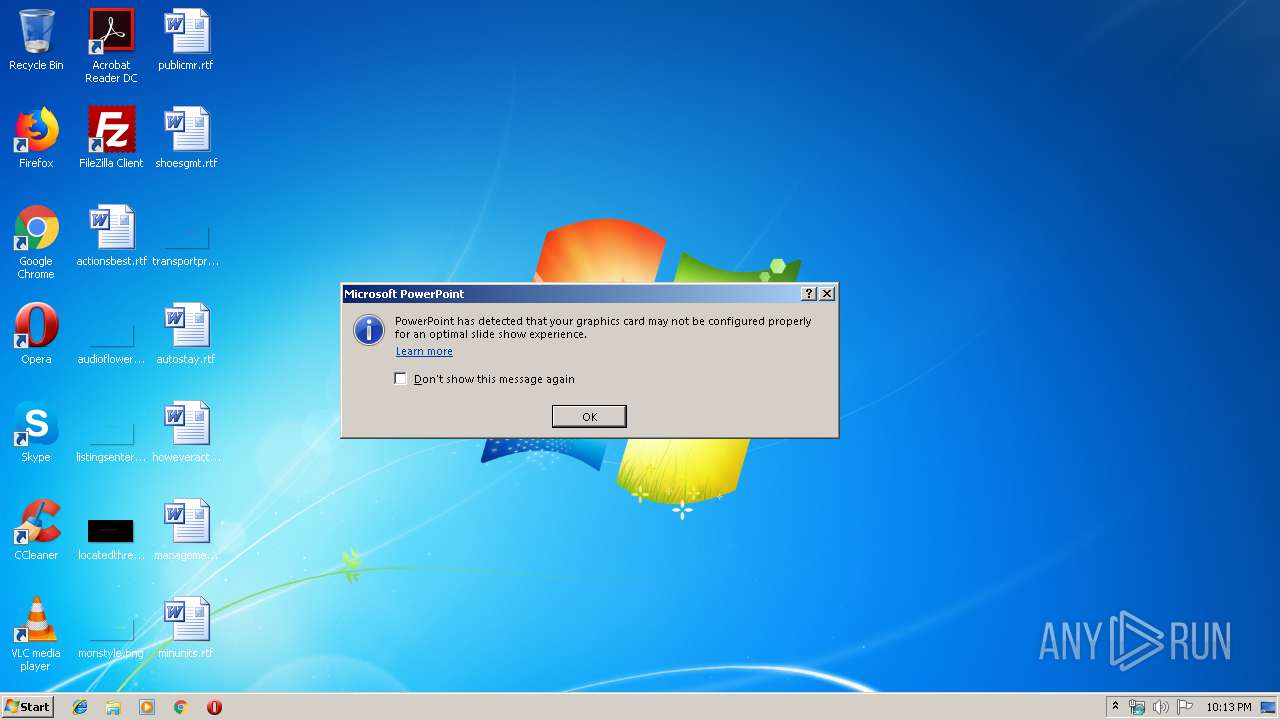
Starts Microsoft Office Application
- bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe (PID: 2928)
Loads Python modules
- Java.exe (PID: 3040)
- javaTM.exe (PID: 3420)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 3344)
Checks supported languages
- POWERPNT.EXE (PID: 3876)
INFO
Dropped object may contain Bitcoin addresses
- bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe (PID: 2928)
Reads Microsoft Office registry keys
- POWERPNT.EXE (PID: 3876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (91.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.3) |
| .exe | | | Win64 Executable (generic) (3) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:08:16 22:26:10+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 22528 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30b4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 13.0.0.0 |
| ProductVersionNumber: | 13.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| Comments: | A build of the Microsoft Windows. |
| CompanyName: | 2.449 KB |
| FileDescription: | Microsoft Office Power Point 97-2003 Slide Show |
| FileVersion: | 13.0.0.0 |
| InternalName: | Microsoft Office Power Point |
| LegalCopyright: | Microsoft Windows |
| LegalTrademarks: | (SO) Microsoft Windows |
| OriginalFileName: | .\dist\Reclamo.exe |
| ProductName: | Documento |
| ProductVersion: | 13.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 16-Aug-2008 20:26:10 |
| Detected languages: |
|
| Comments: | A build of the Microsoft Windows. |
| CompanyName: | 2.449 KB |
| FileDescription: | Microsoft Office Power Point 97-2003 Slide Show |
| FileVersion: | 13.0.0.0 |
| InternalName: | Microsoft Office Power Point |
| LegalCopyright: | Microsoft Windows |
| LegalTrademarks: | (SO) Microsoft Windows |
| OriginalFilename: | .\dist\Reclamo.exe |
| ProductName: | Documento |
| ProductVersion: | 13.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 16-Aug-2008 20:26:10 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000057EC | 0x00005800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.47541 |
.rdata | 0x00007000 | 0x00001190 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.17644 |
.data | 0x00009000 | 0x0001AF58 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.59051 |
.ndata | 0x00024000 | 0x00009000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0002D000 | 0x0000E950 | 0x0000EA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.15135 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.09798 | 722 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.97663 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 5.19556 | 4136 | UNKNOWN | English - United States | RT_ICON |
4 | 6.06732 | 3752 | UNKNOWN | English - United States | RT_ICON |
5 | 6.34925 | 2216 | UNKNOWN | English - United States | RT_ICON |
6 | 4.40438 | 1384 | UNKNOWN | English - United States | RT_ICON |
7 | 5.44021 | 1128 | UNKNOWN | English - United States | RT_ICON |
8 | 2.76352 | 744 | UNKNOWN | English - United States | RT_ICON |
9 | 2.93515 | 296 | UNKNOWN | English - United States | RT_ICON |
103 | 2.88628 | 132 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
51
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | SCHTASKS /Delete /TN "Microsoft_up" /F | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 940 | C:\Windows\system32\cmd.exe /c SCHTASKS /Delete /TN "Microsoft_up" /F | C:\Windows\system32\cmd.exe | — | javaTM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1520 | SCHTASKS /Delete /TN "Microsoft_up" /F | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1748 | ipconfig /all | C:\Windows\system32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1940 | SCHTASKS /create /ST 00:00:01 /SC MINUTE /MO 60 /TR "\"C:\Users\admin\AppData\Roaming/MicroDes/JavaH.exe"\" /TN Microsoft_up | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2928 | "C:\Users\admin\AppData\Local\Temp\bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe" | C:\Users\admin\AppData\Local\Temp\bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe | explorer.exe | ||||||||||||
User: admin Company: 2.449 KB Integrity Level: MEDIUM Description: Microsoft Office Power Point 97-2003 Slide Show Exit code: 0 Version: 13.0.0.0 Modules
| |||||||||||||||
| 3040 | C:\Users\admin\AppData\Roaming/Bin//Jre6/Java.exe | C:\Users\admin\AppData\Roaming\Bin\Jre6\Java.exe | — | javaTM.exe | |||||||||||
User: admin Company: Java(TM) Platfom SE 7 U11 Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 7.0.110.21 Modules
| |||||||||||||||
| 3344 | C:\Windows\system32\cmd.exe /c ipconfig /all | C:\Windows\system32\cmd.exe | — | Java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3420 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\javaTM.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\javaTM.exe | JavaAlq.exe | ||||||||||||
User: admin Company: Java(TM) Platfom SE 7 U11 Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 7.0.110.21 Modules
| |||||||||||||||
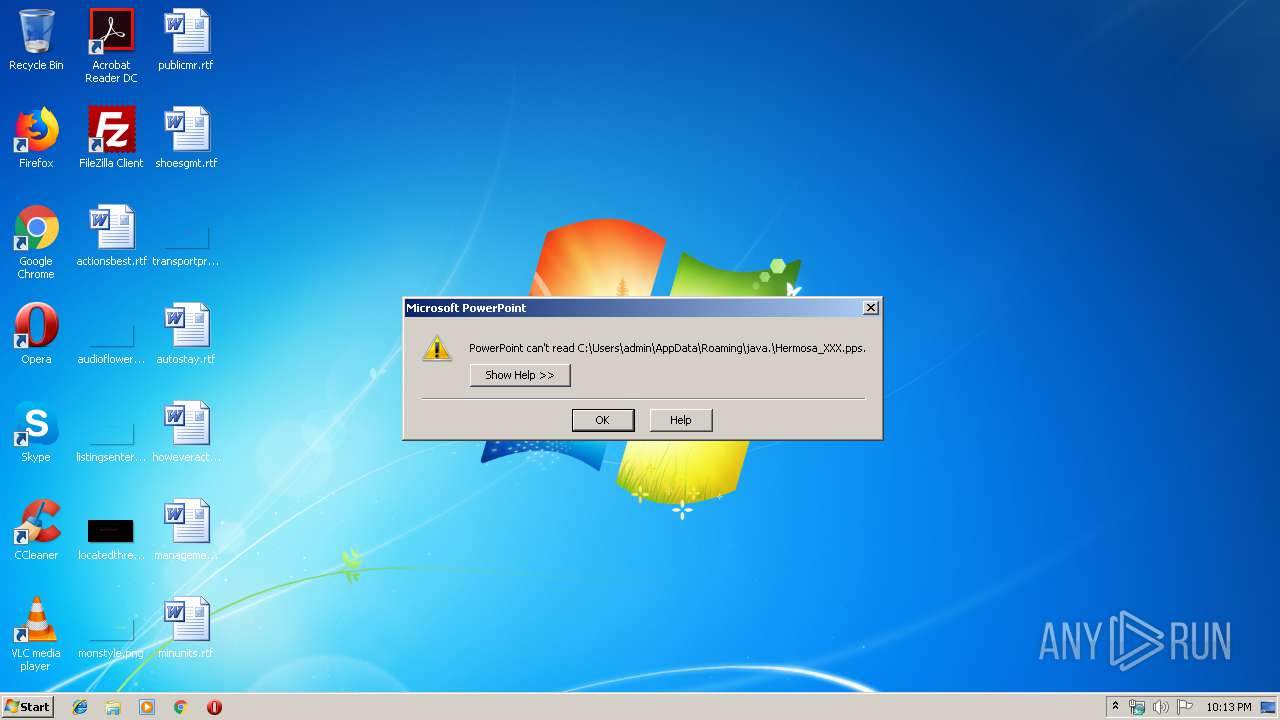
| 3876 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" /s "C:\Users\admin\AppData\Roaming\java.\Hermosa_XXX.pps" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
Total events
1 476
Read events
1 412
Write events
57
Delete events
7
Modification events
| (PID) Process: | (2928) bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | PPTFiles |
Value: 1333919768 | |||
| (PID) Process: | (2928) bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2928) bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3876) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\PowerPoint\Resiliency\StartupItems |
| Operation: | write | Name: | isg |
Value: 69736700240F0000010000000000000000000000 | |||
| (PID) Process: | (3876) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3876) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3876) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3876) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3876) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3876) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
Executable files
100
Suspicious files
1
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3876 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVREBE6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2928 | bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe | C:\Users\admin\AppData\Roaming\java\JavaAlq.exe | executable | |
MD5:— | SHA256:— | |||
| 4076 | JavaAlq.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\java.exe | executable | |
MD5:— | SHA256:— | |||
| 2928 | bf25b330975dc700be3f1f6b1b3362e34eb84b89725d4936d893cdd4f1499e69.exe | C:\Users\admin\AppData\Roaming\java\Hermosa_XXX.pps | document | |
MD5:— | SHA256:— | |||
| 4076 | JavaAlq.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Javak.exe | executable | |
MD5:— | SHA256:— | |||
| 4076 | JavaAlq.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\JavaH.exe | executable | |
MD5:— | SHA256:— | |||
| 4076 | JavaAlq.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\JavaUe.exe | executable | |
MD5:— | SHA256:— | |||
| 4076 | JavaAlq.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\javaTM.exe | executable | |
MD5:— | SHA256:— | |||
| 4076 | JavaAlq.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\JavaD.exe | executable | |
MD5:— | SHA256:— | |||
| 4076 | JavaAlq.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\UJavap.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
java.serveblog.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.serveblog .net |