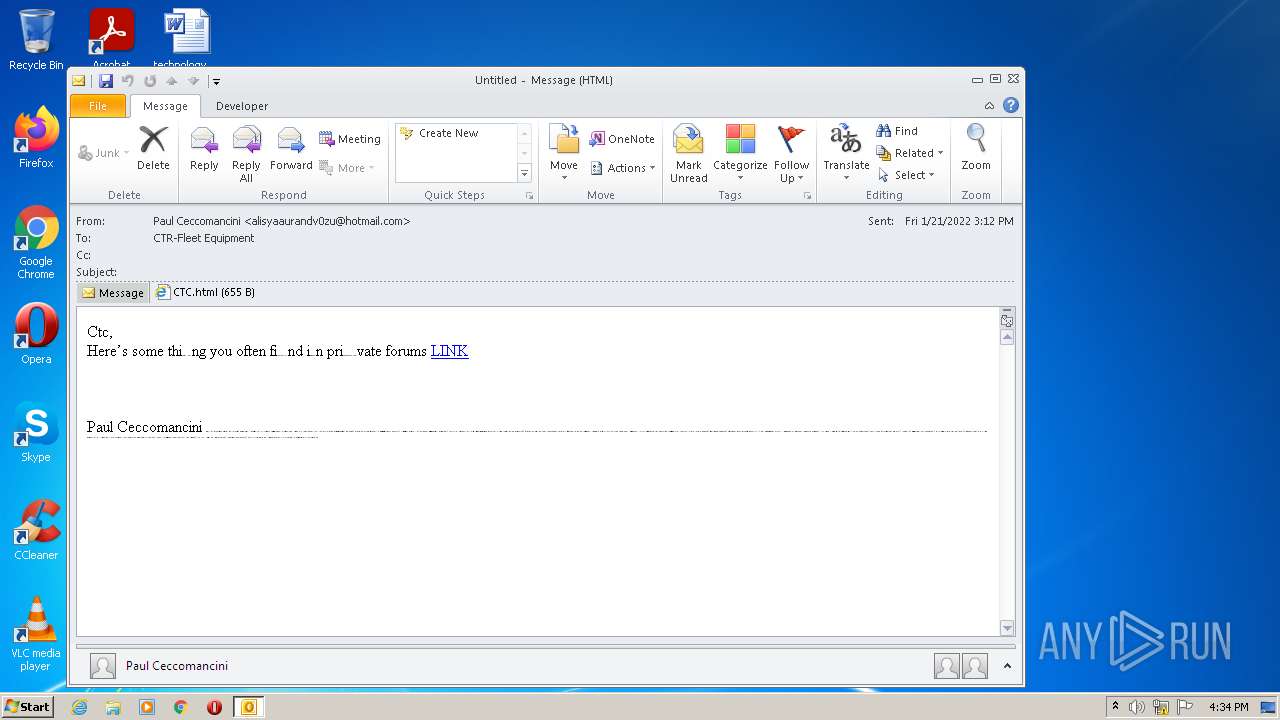
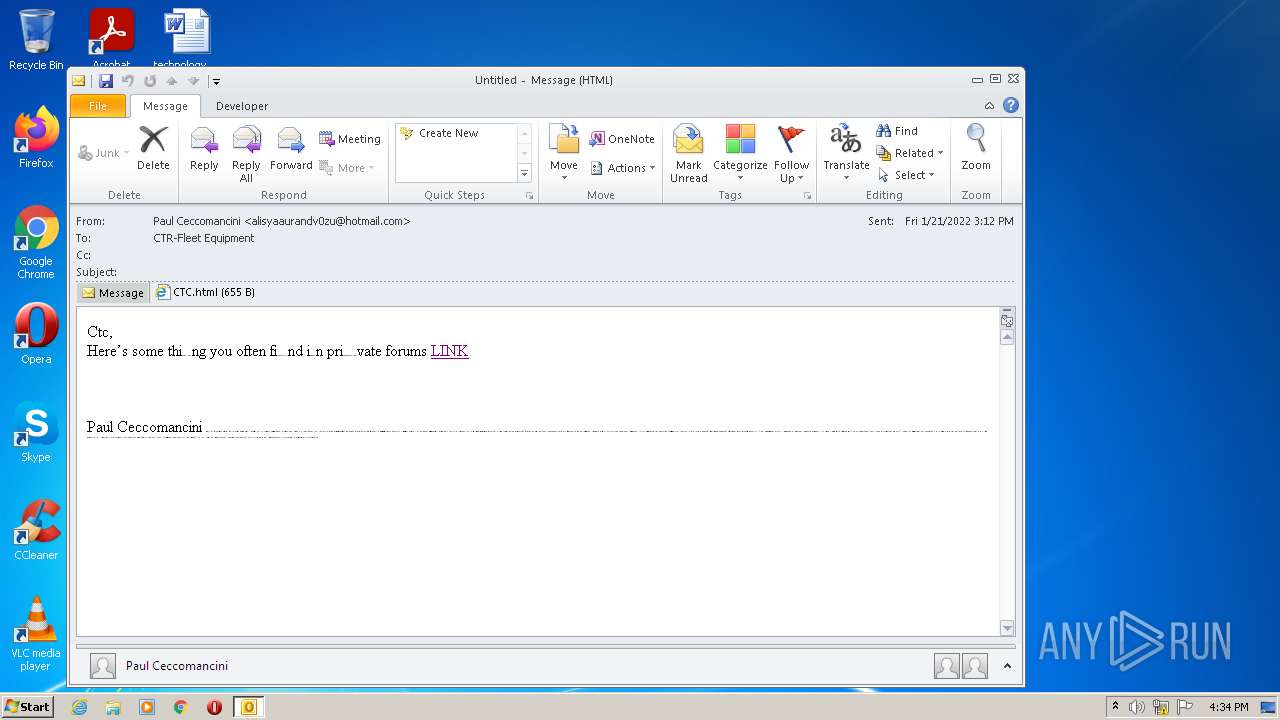
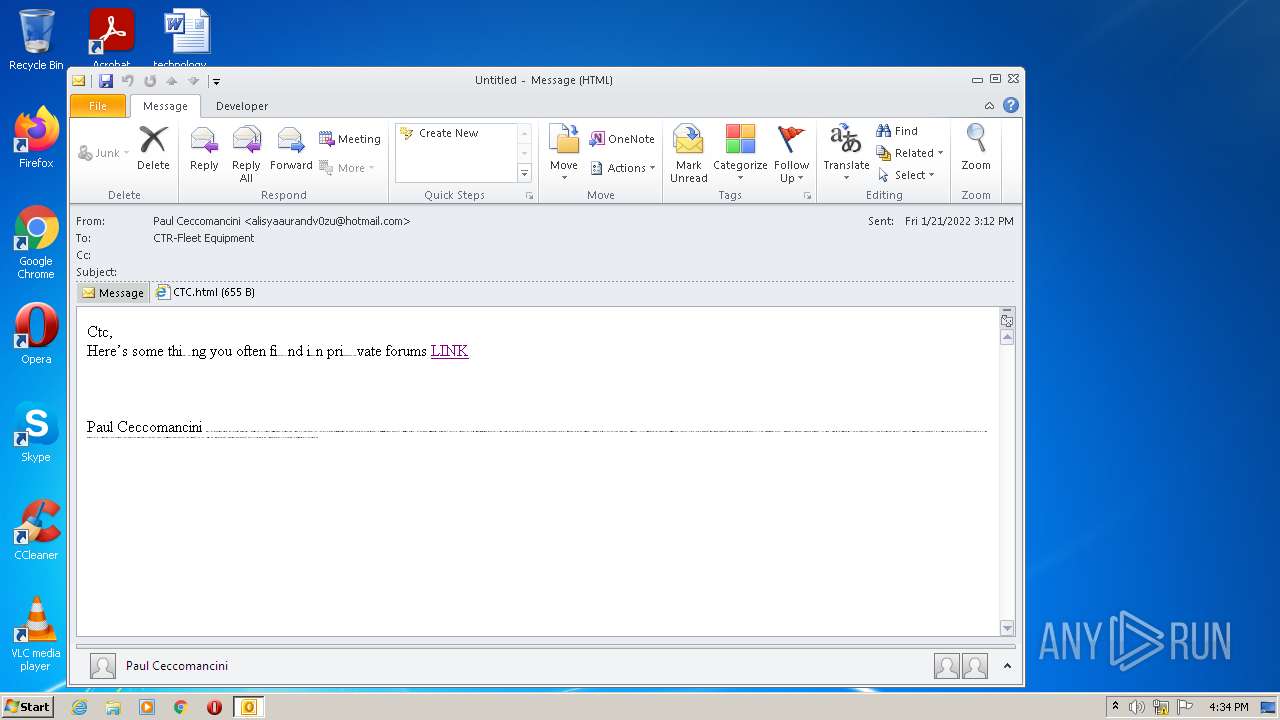
| File name: | phish_alert_sp2_2.0.0.0.eml |
| Full analysis: | https://app.any.run/tasks/775cbe09-eff2-442f-abd3-ef8549beed51 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 16:34:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 3EC6466038BC031F2BB763C1F5CA2677 |
| SHA1: | 277DCC5654D652B77737DAE573BA921E45488576 |
| SHA256: | BF225BE8CA3BC2845E134D06F59AF1D8ECABD694C1E414D3DF724D67A61A5915 |
| SSDEEP: | 384:+nlZEt5csxrS1EyPfYM4WA//u0QxZjIEiOTNR:+nlZEtysxOey4MFAeb3Vvv |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the computer name
- OUTLOOK.EXE (PID: 1252)
Checks supported languages
- OUTLOOK.EXE (PID: 1252)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1252)
Searches for installed software
- OUTLOOK.EXE (PID: 1252)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1252)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2996)
INFO
Reads the computer name
- iexplore.exe (PID: 272)
- iexplore.exe (PID: 2996)
Checks supported languages
- iexplore.exe (PID: 272)
- iexplore.exe (PID: 2996)
Changes internet zones settings
- iexplore.exe (PID: 272)
Application launched itself
- iexplore.exe (PID: 272)
Reads the date of Windows installation
- iexplore.exe (PID: 272)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
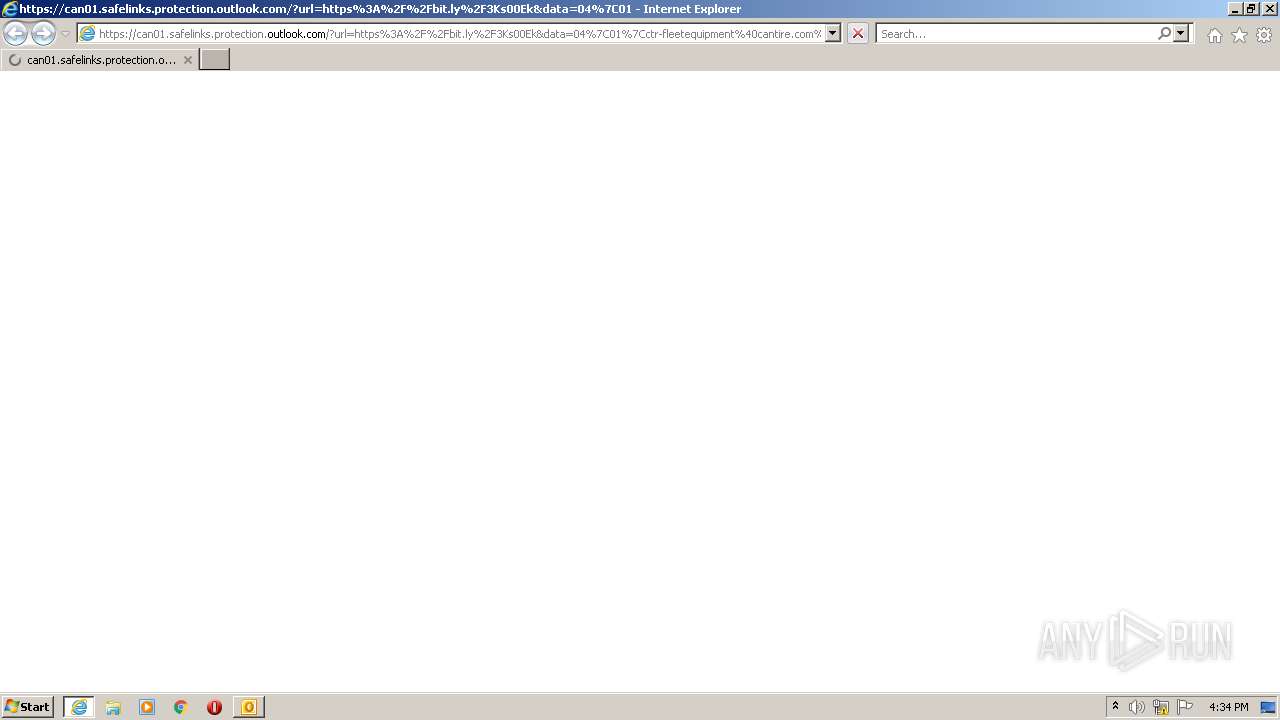
| 272 | "C:\Program Files\Internet Explorer\iexplore.exe" https://can01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fbit.ly%2F3Ks00Ek&data=04%7C01%7Cctr-fleetequipment%40cantire.com%7Cafd492787482409c942d08d9dcf04ae4%7Cbd6704ff1437477c9ac9c30d6f5133c5%7C0%7C0%7C637783747402171616%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C2000&sdata=bV9GevGcSdDbryz8nBSUsBJ96ZalsCeAHe4O0tS%2BQ9Q%3D&reserved=0 | C:\Program Files\Internet Explorer\iexplore.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1252 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\phish_alert_sp2_2.0.0.0.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2996 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:272 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
5 808
Read events
5 143
Write events
644
Delete events
21
Modification events
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
4
Text files
10
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE8EC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{5A108769-22B8-46E6-8C0B-143CEAFDDF28}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_62EF35BE61DD934AA5B39079C482A83C.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_6CF295D2BADE744AA4C133547BBBF6DC.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_9371FA280FF8EC4A83582C1F07625905.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 1252 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_CFEF02B37C20724E916CB3E7D0997470.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
7
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2996 | iexplore.exe | 104.47.61.28:443 | can01.safelinks.protection.outlook.com | Microsoft Corporation | CA | whitelisted |
1252 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
can01.safelinks.protection.outlook.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |